Sysdig SecureではCI/CDパイプライン上でコンテナイメージのスキャンを実施できます。
以前の記事では、Sysdig Secure Jenkinsプラグインを使用したイメージスキャン手順をご紹介しました。
今回はsysdig-cli-scannerを使用したJenkins CI/CDパイプラインでのイメージスキャン手順をご紹介します。sysdig-cli-scannerはローカル環境でイメージスキャンを実行できるバイナリソフトウェアです。
参照URL:
ブログ記事:Sysdigを用いたJenkins上でのコンテナイメージのスキャン
https://sysdig.jp/blog/docker-scanning-jenkins/
Sysdig Secureドキュメント
https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Docker on DockerとしてJenkinsをインストール
Docker on DockerとしてJenkinsをインストールすると、Dcockerコンテナとして稼働しているJenkins上でDockerコマンドを実行できます。
インストール手順は下記サイトを参照しています。
Install Jenkins as Docker
https://www.jenkins.io/doc/book/installing/docker/
Docker内にブリッジネットワークを作成します。
docker network create jenkins
以下のdocker runコマンドでdocker:dind Dockerイメージをダウンロードし、実行します。
docker run \
--name jenkins-docker \
--rm \
--detach \
--privileged \
--network jenkins \
--network-alias docker \
--env DOCKER_TLS_CERTDIR=/certs \
--volume jenkins-docker-certs:/certs/client \
--volume jenkins-data:/var/jenkins_home \
--publish 2376:2376 \
docker:dind \
--storage-driver overlay2
下記内容でDockerfileを作成します。
vi Dockerfile
FROM jenkins/jenkins:2.375.2
USER root
RUN apt-get update && apt-get install -y lsb-release
RUN curl -fsSLo /usr/share/keyrings/docker-archive-keyring.asc \
https://download.docker.com/linux/debian/gpg
RUN echo "deb [arch=$(dpkg --print-architecture) \
signed-by=/usr/share/keyrings/docker-archive-keyring.asc] \
https://download.docker.com/linux/debian \
$(lsb_release -cs) stable" > /etc/apt/sources.list.d/docker.list
RUN apt-get update && apt-get install -y docker-ce-cli
USER jenkins
RUN jenkins-plugin-cli --plugins "blueocean docker-workflow"
DockerfileからDockerイメージを作成します。
docker build -t myjenkins-blueocean:2.375.2-1 .
DockerイメージからDockerコンテナを起動します。
docker run \
--name jenkins-blueocean \
--restart=on-failure \
--detach \
--network jenkins \
--env DOCKER_HOST=tcp://docker:2376 \
--env DOCKER_CERT_PATH=/certs/client \
--env DOCKER_TLS_VERIFY=1 \
--publish 8080:8080 \
--publish 50000:50000 \
--volume jenkins-data:/var/jenkins_home \
--volume jenkins-docker-certs:/certs/client:ro \
myjenkins-blueocean:2.375.2-1
Jenkins GUIにアクセスします。今回はAWS EC2上のUbuntuでDockerコンテナを起動しているので、アクセス先は下記URLとなります。
http://<EC2のパブリックIPアドレス>:8080
JenkinsのGUIにログインするためのAdminのパスワードは下記コマンドで確認できます。
sudo docker exec jenkins-blueocean cat /var/jenkins_home/secrets/initialAdminPassword
クレデンシャル作成
2つのクレデンシャルを作成します。
Sysdig Secure API Tokenのクレデンシャル作成
Jenkins の管理 > クレデンシャル管理 > System > グローバルドメインに移動します。
"Add Credentials"をクリックし、以下の値を設定します。
- パスワード: Sysdig Secure API Tokenの値を入力します
- ID: sysdig-secure-api-token
- 説明: Sysdig Secure API Token
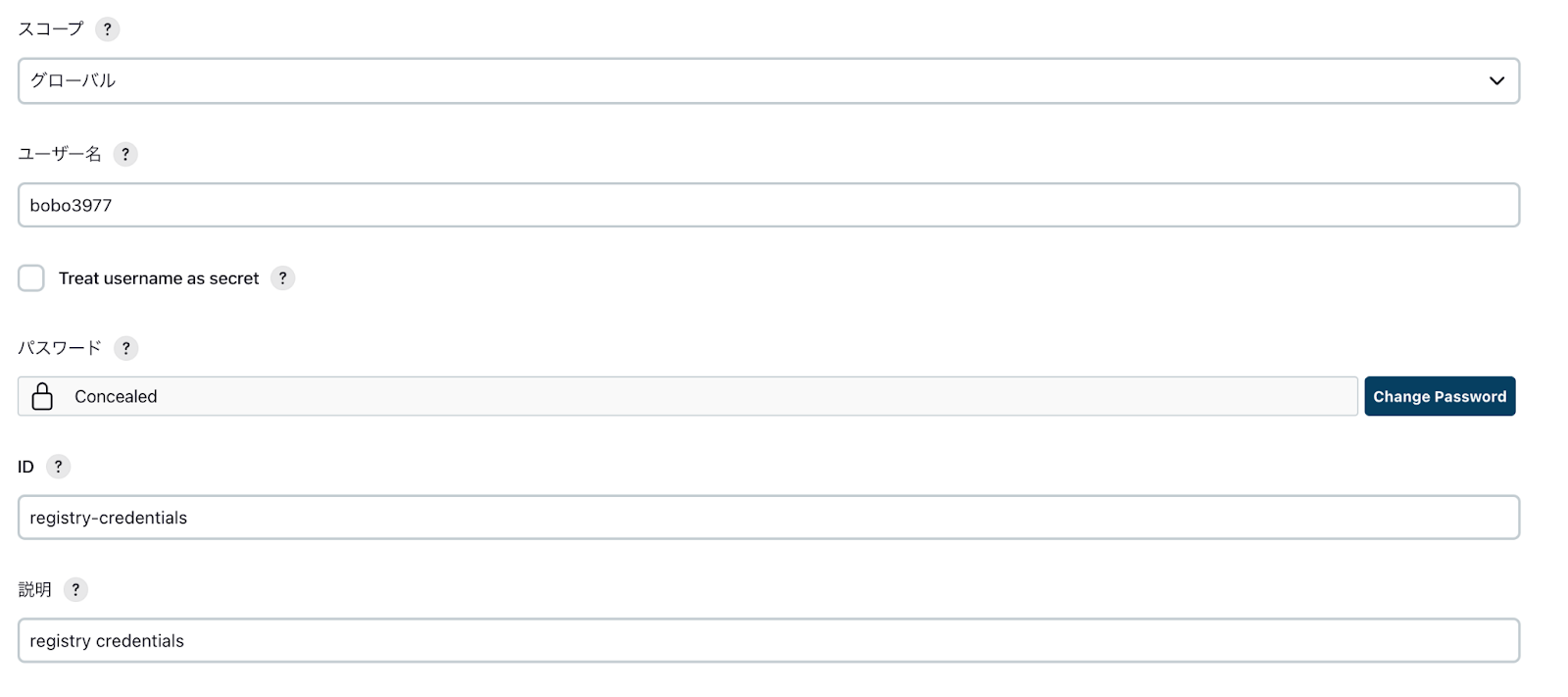
レジストリのクレデンシャル作成
イメージのアップロード先となるレジストリ(例:Docker Hub)のクレデンシャルを作成します。
"Add Credentials"をクリックし、以下の値を設定します。
- ユーザー名: レジストリのユーザ名
- パスワード: レジストリのパスワード
- ID: registry-credentials
- 説明: Registry Credentials
パイプラインプロジェクトの作成
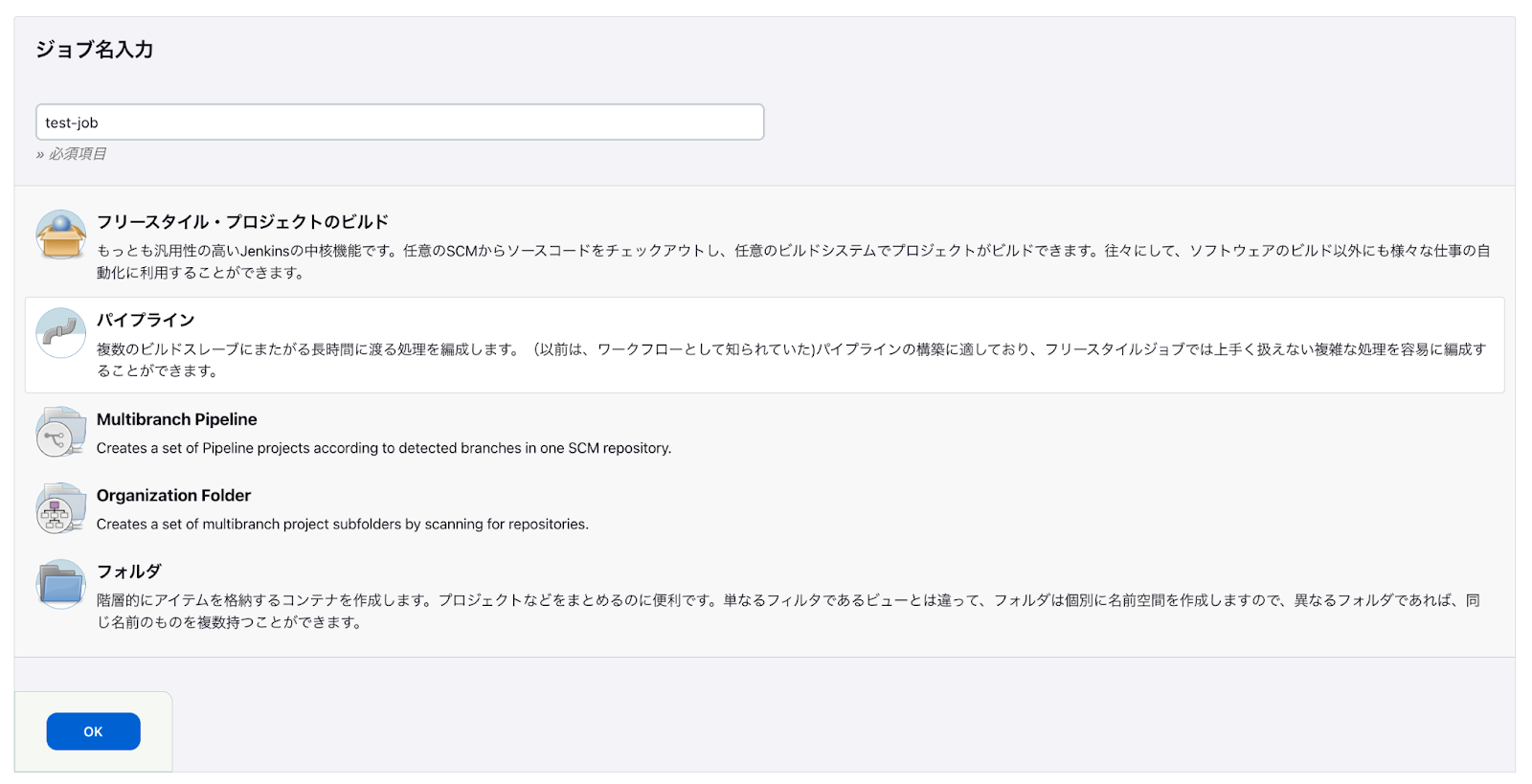
パイプラインプロジェクトを作成します。
新規ジョブ作成を選択します。
ジョブ名を入力します。
パイプラインを選択します。
下記サンプルスクリプトをScriptセクションに貼り付けます。
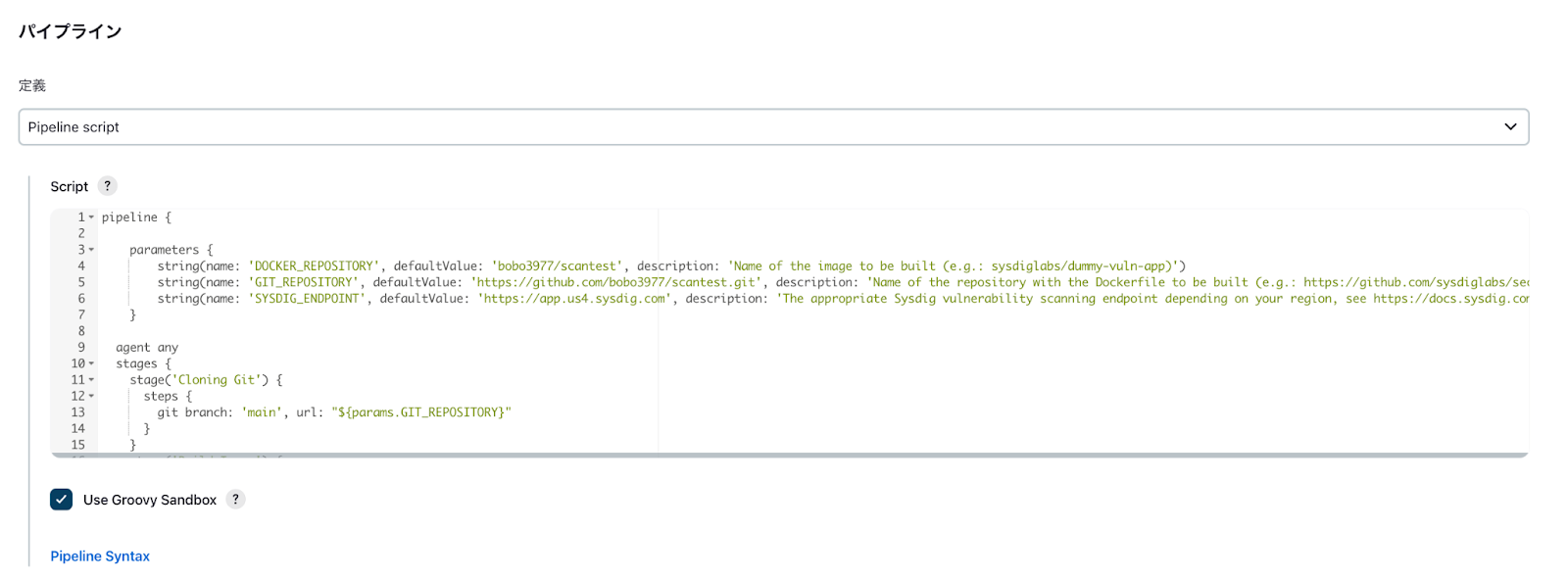
サンプルスクリプト
このサンプルスクリプトでは以下のパイプラインを実行します。
- 指定したGitリポジトリ(今回はPublicリポジトリを使用)をクローン
- リポジトリ内のDockerfileからイメージを作成
- 作成したイメージをSysdig Secureでスキャン
- スキャン結果が問題なければ指定したレジストリにイメージをアップロード
下記の値はご自身の環境に合わせて修正してください。
- image:作成するイメージ名
- registryCredential:先ほど作成したレジストリ用のクレデンシャルID名
- repository:イメージの元となるDockerfileを格納してあるリポジトリ
- api_endpoint:Sysdig Secure EndpointのURL(例:https://app.us4.sysdig.com)
pipeline {
parameters {
string(name: 'DOCKER_REPOSITORY', defaultValue: 'bobo3977/scantest', description: 'Name of the image to be built (e.g.: sysdiglabs/dummy-vuln-app)')
string(name: 'GIT_REPOSITORY', defaultValue: 'https://github.com/bobo3977/scantest.git', description: 'Name of the repository with the Dockerfile to be built (e.g.: https://github.com/sysdiglabs/secure-inline-scan-examples.git)')
string(name: 'SYSDIG_ENDPOINT', defaultValue: 'https://app.us4.sysdig.com', description: 'The appropriate Sysdig vulnerability scanning endpoint depending on your region, see https://docs.sysdig.com/en/docs/administration/saas-regions-and-ip-ranges (e.g.: https://github.com/sysdiglabs/secure-inline-scan-examples.git)')
}
agent any
stages {
stage('Cloning Git') {
steps {
git branch: 'main', url: "${params.GIT_REPOSITORY}"
}
}
stage('Build Image') {
steps {
sh "docker build -t ${DOCKER_REPOSITORY} ./"
}
}
stage('Scan image') {
steps {
withCredentials([usernamePassword(credentialsId: 'sysdig-secure-api-token', passwordVariable: 'SECURE_API_TOKEN', usernameVariable: '')]) {
sh '''
VERSION=$(curl -L -s https://download.sysdig.com/scanning/sysdig-cli-scanner/latest_version.txt)
curl -LO "https://download.sysdig.com/scanning/bin/sysdig-cli-scanner/${VERSION}/linux/amd64/sysdig-cli-scanner"
chmod +x ./sysdig-cli-scanner
./sysdig-cli-scanner --apiurl ${SYSDIG_ENDPOINT} docker://${DOCKER_REPOSITORY}
'''
}
}
}
stage('Push Image') {
steps {
withCredentials([usernamePassword(credentialsId: 'registry-credentials', passwordVariable: 'password', usernameVariable: 'username')]){
sh '''
docker login -u ${username} -p ${password}
docker push ${DOCKER_REPOSITORY}
'''
}
}
}
}
}
今回のイメージスキャンテストで使用したDockerファイルは以下の2種類になります。リポジトリ直下にDockerfileを配置しています。
vi Dockerfile
FROM alpine
vi Dockerfile
FROM nginx
プロジェクトのビルド
ビルドを実行します。
パイプラインの結果
脆弱性を含んだイメージの場合はSysdig Secureによるコンテナイメージのスキャン結果がFAILとなり、パイプラインも失敗します。
#3 FAILURE - nginxイメージを使用した場合
#2 SCCESS - alpineイメージを使用した場合
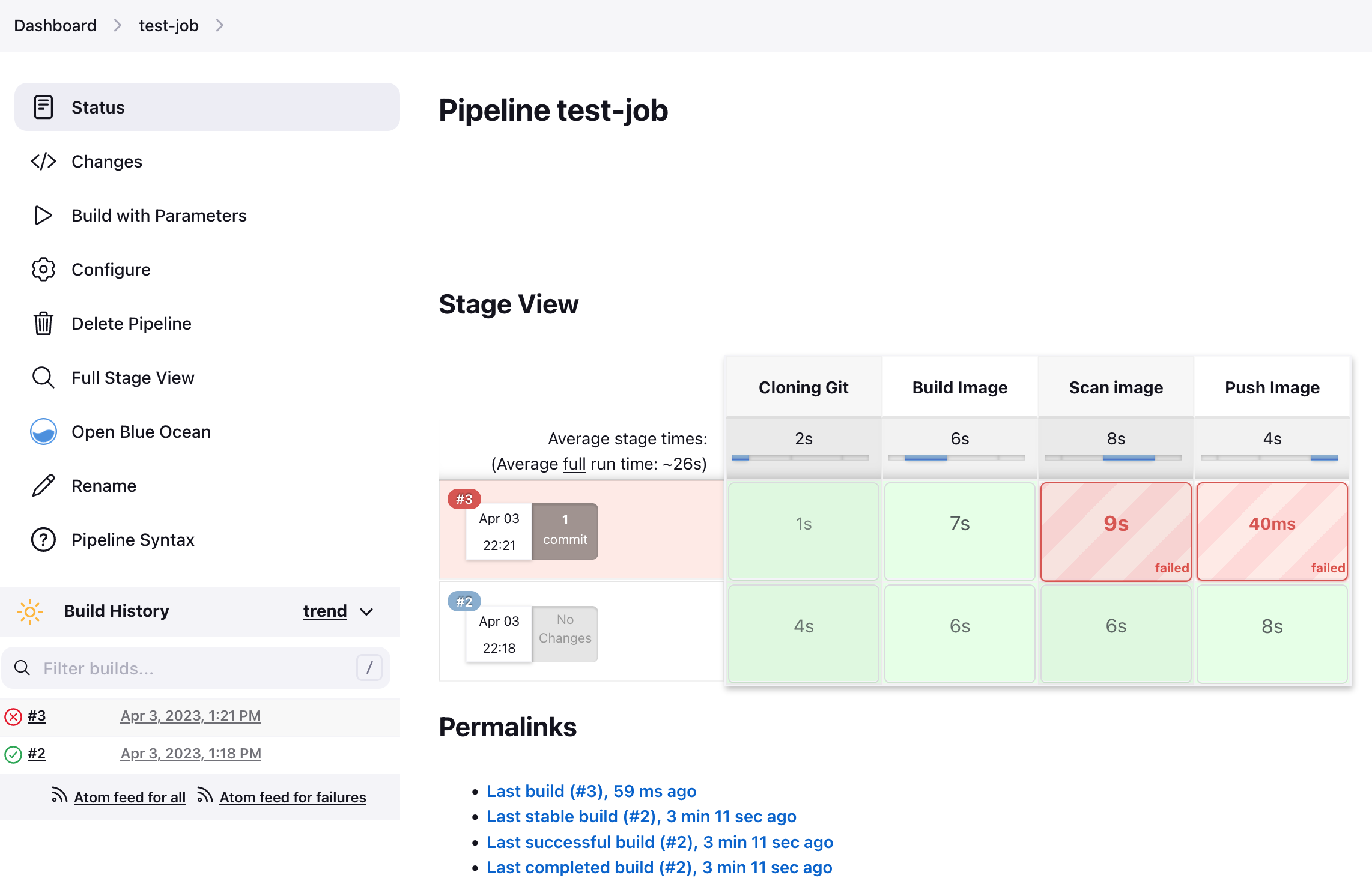
下記のコンソールログにイメージのスキャン結果が含まれていることに注目してください。
コンソールログ (FAILURE) - nginxイメージ
ログ
Started by user admin
[Pipeline] Start of Pipeline
[Pipeline] node
Running on Jenkins in /var/jenkins_home/workspace/test-job
[Pipeline] {
[Pipeline] stage
[Pipeline] { (Cloning Git)
[Pipeline] git
The recommended git tool is: NONE
No credentials specified
> git rev-parse --resolve-git-dir /var/jenkins_home/workspace/test-job/.git # timeout=10
Fetching changes from the remote Git repository
> git config remote.origin.url https://github.com/bobo3977/scantest.git # timeout=10
Fetching upstream changes from https://github.com/bobo3977/scantest.git
> git --version # timeout=10
> git --version # 'git version 2.30.2'
> git fetch --tags --force --progress -- https://github.com/bobo3977/scantest.git +refs/heads/*:refs/remotes/origin/* # timeout=10
> git rev-parse refs/remotes/origin/main^{commit} # timeout=10
Checking out Revision 26c95337d30ecb611982cba1907339369666d985 (refs/remotes/origin/main)
> git config core.sparsecheckout # timeout=10
> git checkout -f 26c95337d30ecb611982cba1907339369666d985 # timeout=10
> git branch -a -v --no-abbrev # timeout=10
> git branch -D main # timeout=10
> git checkout -b main 26c95337d30ecb611982cba1907339369666d985 # timeout=10
Commit message: "Update Dockerfile"
> git rev-list --no-walk 06b5677c2c510652408015f597be72a982e89217 # timeout=10
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Build Image)
[Pipeline] sh
+ docker build -t bobo3977/scantest ./
#1 [internal] load build definition from Dockerfile
#1 transferring dockerfile: 48B done
#1 DONE 0.0s
#2 [internal] load .dockerignore
#2 transferring context: 2B done
#2 DONE 0.0s
#3 [internal] load metadata for docker.io/library/nginx:latest
#3 ...
#4 [auth] library/nginx:pull token for registry-1.docker.io
#4 DONE 0.0s
#3 [internal] load metadata for docker.io/library/nginx:latest
#3 DONE 1.9s
#5 [1/1] FROM docker.io/library/nginx@sha256:2ab30d6ac53580a6db8b657abf0f68d75360ff5cc1670a85acb5bd85ba1b19c0
#5 resolve docker.io/library/nginx@sha256:2ab30d6ac53580a6db8b657abf0f68d75360ff5cc1670a85acb5bd85ba1b19c0 0.0s done
#5 sha256:2ab30d6ac53580a6db8b657abf0f68d75360ff5cc1670a85acb5bd85ba1b19c0 1.86kB / 1.86kB done
#5 sha256:bfb112db4075460ec042ce13e0b9c3ebd982f93ae0be155496d050bb70006750 1.57kB / 1.57kB done
#5 sha256:7f7f30930c6b1fa9e421ba5d234c3030a838740a22a42899d3df5f87e00ea94f 0B / 25.58MB 0.1s
#5 sha256:080ed0ed8312deca92e9a769b518cdfa20f5278359bd156f3469dd8fa532db6b 7.92kB / 7.92kB done
#5 sha256:f1f26f5702560b7e591bef5c4d840f76a232bf13fd5aefc4e22077a1ae4440c7 0B / 31.41MB 0.1s
#5 sha256:2836b727df80c28853d6c505a2c3a5959316e48b1cff42d98e70cb905b166c82 0B / 626B 0.1s
#5 sha256:7f7f30930c6b1fa9e421ba5d234c3030a838740a22a42899d3df5f87e00ea94f 6.29MB / 25.58MB 0.2s
#5 sha256:7f7f30930c6b1fa9e421ba5d234c3030a838740a22a42899d3df5f87e00ea94f 25.58MB / 25.58MB 0.3s
#5 sha256:f1f26f5702560b7e591bef5c4d840f76a232bf13fd5aefc4e22077a1ae4440c7 13.63MB / 31.41MB 0.3s
#5 sha256:2836b727df80c28853d6c505a2c3a5959316e48b1cff42d98e70cb905b166c82 626B / 626B 0.2s done
#5 sha256:e1eeb0f1c06b25695a5b9df587edf4bf12a5af9432696811dd8d5fcfd01d7949 0B / 956B 0.3s
#5 sha256:7f7f30930c6b1fa9e421ba5d234c3030a838740a22a42899d3df5f87e00ea94f 25.58MB / 25.58MB 0.3s done
#5 sha256:f1f26f5702560b7e591bef5c4d840f76a232bf13fd5aefc4e22077a1ae4440c7 31.41MB / 31.41MB 0.5s done
#5 sha256:e1eeb0f1c06b25695a5b9df587edf4bf12a5af9432696811dd8d5fcfd01d7949 956B / 956B 0.4s done
#5 sha256:9862f2ee2e8cd9dab487d7dc2152a3f76cb503772dfb8e830973264340d6233e 0B / 1.40kB 0.5s
#5 sha256:86b2457cc2b0d68200061e3420623c010de5e6fb184e18328a46ef22dbba490a 0B / 772B 0.5s
#5 sha256:9862f2ee2e8cd9dab487d7dc2152a3f76cb503772dfb8e830973264340d6233e 1.40kB / 1.40kB 0.6s done
#5 sha256:86b2457cc2b0d68200061e3420623c010de5e6fb184e18328a46ef22dbba490a 772B / 772B 0.5s done
#5 extracting sha256:f1f26f5702560b7e591bef5c4d840f76a232bf13fd5aefc4e22077a1ae4440c7 0.1s
#5 extracting sha256:f1f26f5702560b7e591bef5c4d840f76a232bf13fd5aefc4e22077a1ae4440c7 0.9s done
#5 extracting sha256:7f7f30930c6b1fa9e421ba5d234c3030a838740a22a42899d3df5f87e00ea94f 0.1s
#5 extracting sha256:7f7f30930c6b1fa9e421ba5d234c3030a838740a22a42899d3df5f87e00ea94f 0.5s done
#5 extracting sha256:2836b727df80c28853d6c505a2c3a5959316e48b1cff42d98e70cb905b166c82
#5 extracting sha256:2836b727df80c28853d6c505a2c3a5959316e48b1cff42d98e70cb905b166c82 done
#5 extracting sha256:e1eeb0f1c06b25695a5b9df587edf4bf12a5af9432696811dd8d5fcfd01d7949 done
#5 extracting sha256:86b2457cc2b0d68200061e3420623c010de5e6fb184e18328a46ef22dbba490a done
#5 extracting sha256:9862f2ee2e8cd9dab487d7dc2152a3f76cb503772dfb8e830973264340d6233e
#5 extracting sha256:9862f2ee2e8cd9dab487d7dc2152a3f76cb503772dfb8e830973264340d6233e done
#5 DONE 2.4s
#6 exporting to image
#6 exporting layers done
#6 writing image sha256:a478b43304dfb8019f688650c4d5515e917df8cf16460e127f66b59a4ccd92d9 done
#6 naming to docker.io/bobo3977/scantest done
#6 DONE 0.0s
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Scan image)
[Pipeline] withCredentials
Masking supported pattern matches of $SECURE_API_TOKEN
[Pipeline] {
[Pipeline] sh
+ curl -L -s https://download.sysdig.com/scanning/sysdig-cli-scanner/latest_version.txt
+ VERSION=1.3.6
+ curl -LO https://download.sysdig.com/scanning/bin/sysdig-cli-scanner/1.3.6/linux/amd64/sysdig-cli-scanner
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
4 30.8M 4 1387k 0 0 1331k 0 0:00:23 0:00:01 0:00:22 1330k
60 30.8M 60 18.5M 0 0 9321k 0 0:00:03 0:00:02 0:00:01 9317k
100 30.8M 100 30.8M 0 0 11.2M 0 0:00:02 0:00:02 --:--:-- 11.2M
+ chmod +x ./sysdig-cli-scanner
+ ./sysdig-cli-scanner --apiurl https://app.us4.sysdig.com docker://bobo3977/scantest
2023-04-03T13:21:25Z Starting analysis with Sysdig scanner version 1.3.6
2023-04-03T13:21:25Z Retrieving MainDB...
2023-04-03T13:21:25Z Done, using cached DB
2023-04-03T13:21:25Z Loading MainDB...
2023-04-03T13:21:25Z Done
2023-04-03T13:21:25Z Retrieving image...
2023-04-03T13:21:28Z Done
2023-04-03T13:21:28Z Scan started...
2023-04-03T13:21:31Z Uploading result to backend...
2023-04-03T13:21:31Z Done
2023-04-03T13:21:31Z Total execution time 5.854479281s
Type: dockerImage
ImageID: sha256:a478b43304dfb8019f688650c4d5515e917df8cf16460e127f66b59a4ccd92d9
Digest:
BaseOS: debian 11.6
PullString: bobo3977/scantest
119 vulnerabilities found
3 Critical (0 fixable)
21 High (0 fixable)
19 Medium (0 fixable)
6 Low (0 fixable)
70 Negligible (0 fixable)
POLICIES EVALUATION
Policy: Sysdig Best Practices FAILED (19 failures - 0 risks accepted)
Policies evaluation FAILED at 2023-04-03T13:21:31Z
Full image results here: https://app.us4.sysdig.com/secure/#/scanning/assets/results/17526f652486933d55a4862a58134630/overview (id 17526f652486933d55a4862a58134630)
Execution logs written to: /var/jenkins_home/workspace/test-job/scan-logs
[Pipeline] }
[Pipeline] // withCredentials
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Push Image)
Stage "Push Image" skipped due to earlier failure(s)
[Pipeline] }
[Pipeline] // stage
[Pipeline] }
[Pipeline] // node
[Pipeline] End of Pipeline
ERROR: script returned exit code 1
Finished: FAILURE
コンソールログ (SUCCESS) - alpineイメージ
ログ
Started by user admin
[Pipeline] Start of Pipeline
[Pipeline] node
Running on Jenkins in /var/jenkins_home/workspace/test-job
[Pipeline] {
[Pipeline] stage
[Pipeline] { (Cloning Git)
[Pipeline] git
The recommended git tool is: NONE
No credentials specified
> git rev-parse --resolve-git-dir /var/jenkins_home/workspace/test-job/.git # timeout=10
Fetching changes from the remote Git repository
> git config remote.origin.url https://github.com/bobo3977/scantest.git # timeout=10
Fetching upstream changes from https://github.com/bobo3977/scantest.git
> git --version # timeout=10
> git --version # 'git version 2.30.2'
> git fetch --tags --force --progress -- https://github.com/bobo3977/scantest.git +refs/heads/*:refs/remotes/origin/* # timeout=10
> git rev-parse refs/remotes/origin/main^{commit} # timeout=10
Checking out Revision 06b5677c2c510652408015f597be72a982e89217 (refs/remotes/origin/main)
> git config core.sparsecheckout # timeout=10
> git checkout -f 06b5677c2c510652408015f597be72a982e89217 # timeout=10
> git branch -a -v --no-abbrev # timeout=10
> git checkout -b main 06b5677c2c510652408015f597be72a982e89217 # timeout=10
Commit message: "Create Dockerfile"
First time build. Skipping changelog.
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Build Image)
[Pipeline] sh
+ docker build -t bobo3977/scantest ./
#1 [internal] load .dockerignore
#1 transferring context: 2B done
#1 DONE 0.0s
#2 [internal] load build definition from Dockerfile
#2 transferring dockerfile: 49B done
#2 DONE 0.0s
#3 [internal] load metadata for docker.io/library/alpine:latest
#3 DONE 1.9s
#4 [1/1] FROM docker.io/library/alpine@sha256:124c7d2707904eea7431fffe91522a01e5a861a624ee31d03372cc1d138a3126
#4 resolve docker.io/library/alpine@sha256:124c7d2707904eea7431fffe91522a01e5a861a624ee31d03372cc1d138a3126 0.0s done
#4 sha256:f56be85fc22e46face30e2c3de3f7fe7c15f8fd7c4e5add29d7f64b87abdaa09 0B / 3.37MB 0.1s
#4 sha256:124c7d2707904eea7431fffe91522a01e5a861a624ee31d03372cc1d138a3126 1.64kB / 1.64kB done
#4 sha256:b6ca290b6b4cdcca5b3db3ffa338ee0285c11744b4a6abaa9627746ee3291d8d 528B / 528B done
#4 sha256:9ed4aefc74f6792b5a804d1d146fe4b4a2299147b0f50eaf2b08435d7b38c27e 1.47kB / 1.47kB done
#4 sha256:f56be85fc22e46face30e2c3de3f7fe7c15f8fd7c4e5add29d7f64b87abdaa09 3.19MB / 3.37MB 0.2s
#4 sha256:f56be85fc22e46face30e2c3de3f7fe7c15f8fd7c4e5add29d7f64b87abdaa09 3.37MB / 3.37MB 0.2s done
#4 extracting sha256:f56be85fc22e46face30e2c3de3f7fe7c15f8fd7c4e5add29d7f64b87abdaa09 0.1s
#4 extracting sha256:f56be85fc22e46face30e2c3de3f7fe7c15f8fd7c4e5add29d7f64b87abdaa09 0.1s done
#4 DONE 0.4s
#5 exporting to image
#5 exporting layers done
#5 writing image sha256:ab4749513a49df5516bf0ed69c03025fde28b20fab2d77a55f4735826feb9584 done
#5 naming to docker.io/bobo3977/scantest done
#5 DONE 0.0s
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Scan image)
[Pipeline] withCredentials
Masking supported pattern matches of $SECURE_API_TOKEN
[Pipeline] {
[Pipeline] sh
+ curl -L -s https://download.sysdig.com/scanning/sysdig-cli-scanner/latest_version.txt
+ VERSION=1.3.6
+ curl -LO https://download.sysdig.com/scanning/bin/sysdig-cli-scanner/1.3.6/linux/amd64/sysdig-cli-scanner
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
16 30.8M 16 5334k 0 0 4081k 0 0:00:07 0:00:01 0:00:06 4078k
73 30.8M 73 22.6M 0 0 9.7M 0 0:00:03 0:00:02 0:00:01 9.7M
100 30.8M 100 30.8M 0 0 11.1M 0 0:00:02 0:00:02 --:--:-- 11.0M
+ chmod +x ./sysdig-cli-scanner
+ ./sysdig-cli-scanner --apiurl https://app.us4.sysdig.com docker://bobo3977/scantest
2023-04-03T13:18:16Z Starting analysis with Sysdig scanner version 1.3.6
2023-04-03T13:18:16Z Retrieving MainDB...
2023-04-03T13:18:18Z Done 149.4 MB
2023-04-03T13:18:18Z Loading MainDB...
2023-04-03T13:18:18Z Done
2023-04-03T13:18:18Z Retrieving image...
2023-04-03T13:18:18Z Done
2023-04-03T13:18:18Z Scan started...
2023-04-03T13:18:18Z Uploading result to backend...
2023-04-03T13:18:19Z Done
2023-04-03T13:18:19Z Total execution time 3.003651415s
Type: dockerImage
ImageID: sha256:ab4749513a49df5516bf0ed69c03025fde28b20fab2d77a55f4735826feb9584
Digest:
BaseOS: alpine 3.17.3
PullString: bobo3977/scantest
0 vulnerabilities found
POLICIES EVALUATION
Policy: Sysdig Best Practices PASSED (0 failures - 0 risks accepted)
Policies evaluation PASSED at 2023-04-03T13:18:19Z
Full image results here: https://app.us4.sysdig.com/secure/#/scanning/assets/results/17526f3868f78138bfe978a2f1b71c80/overview (id 17526f3868f78138bfe978a2f1b71c80)
Execution logs written to: /var/jenkins_home/workspace/test-job/scan-logs
[Pipeline] }
[Pipeline] // withCredentials
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Push Image)
[Pipeline] withCredentials
Masking supported pattern matches of $password
[Pipeline] {
[Pipeline] sh
+ docker login -u bobo3977 -p ****
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /var/jenkins_home/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
+ docker push bobo3977/scantest
Using default tag: latest
The push refers to repository [docker.io/bobo3977/scantest]
f1417ff83b31: Preparing
f1417ff83b31: Mounted from library/alpine
latest: digest: sha256:2ee850a14e3618667fce4b7ce48b453023d3d1df9cea380fe5f88fac7557efd1 size: 527
[Pipeline] }
[Pipeline] // withCredentials
[Pipeline] }
[Pipeline] // stage
[Pipeline] }
[Pipeline] // node
[Pipeline] End of Pipeline
Finished: SUCCESS
Sysdig Secure UIでの確認
Sysdig Secure UIにログインします。
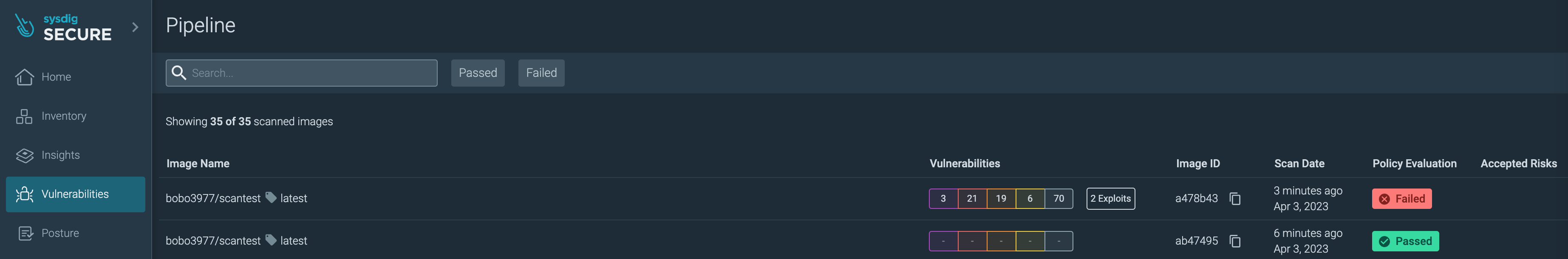
Vulnerabilities > Pipelineに移動します。
スキャン結果の一覧を確認します。
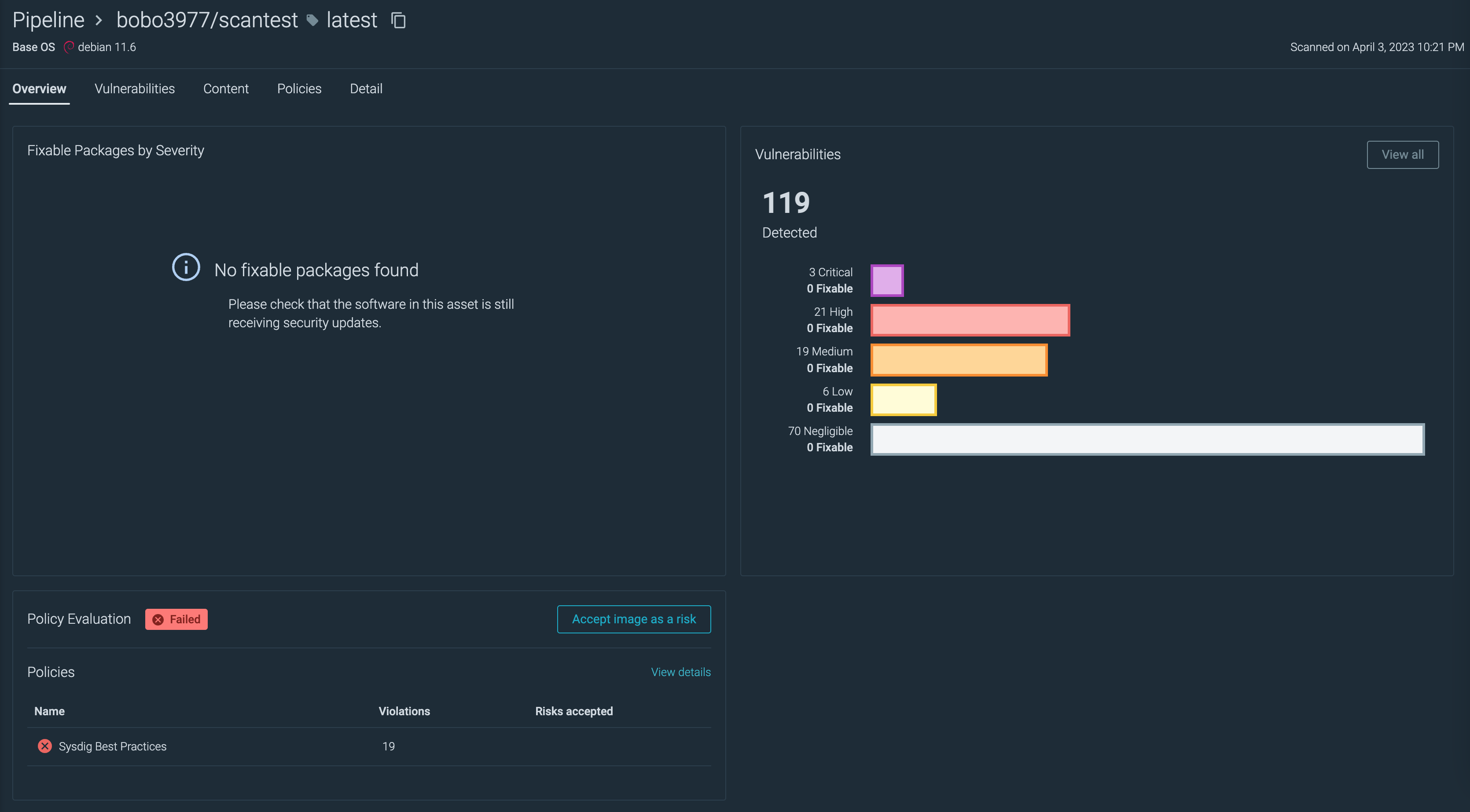
スキャン結果で失敗したイメージの詳細画面
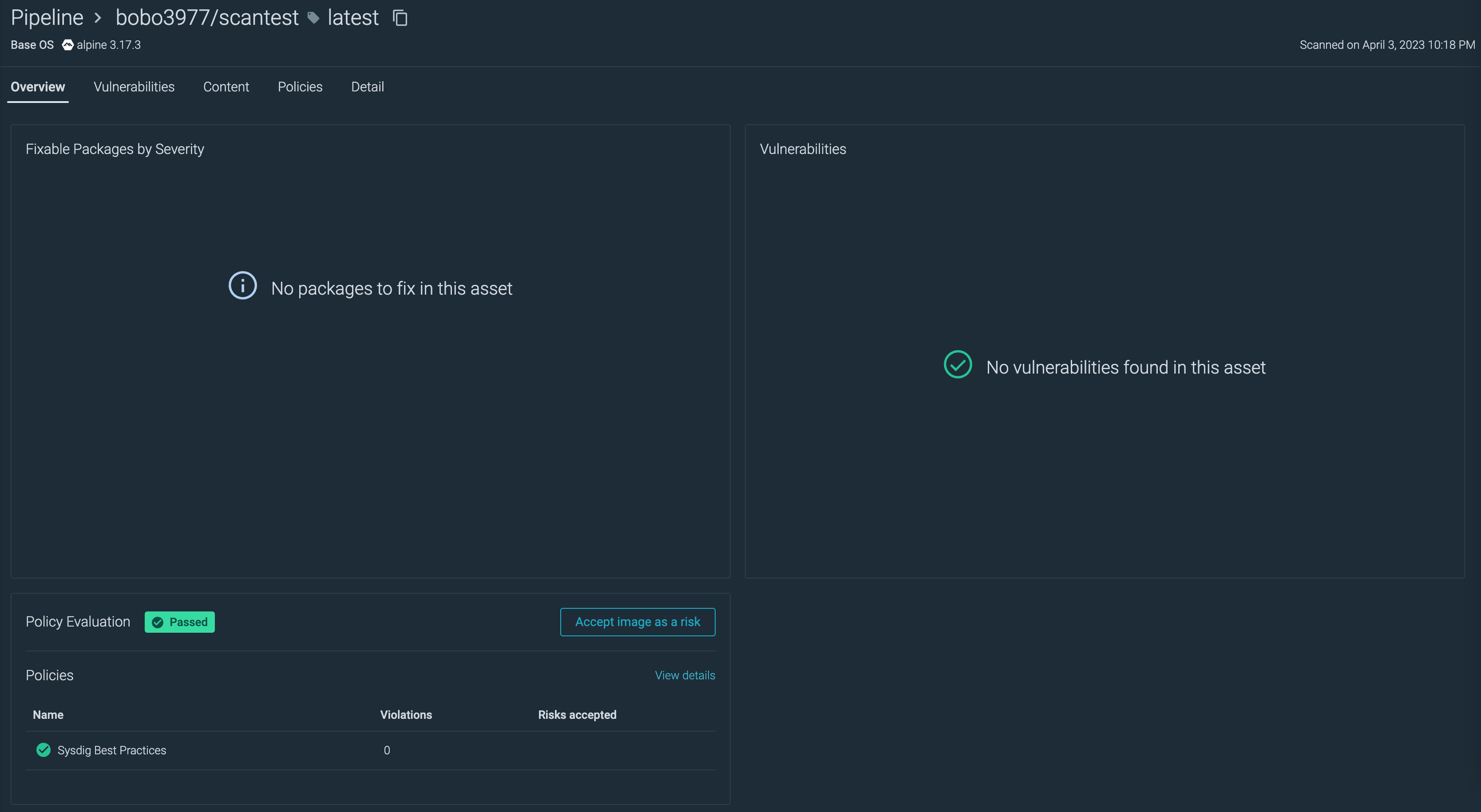
スキャン結果で成功したイメージの詳細画面
まとめ
Sysdig CLI Scannerを使用することで、JenkinsのCI/CDパイプライン上で簡単にコンテナイメージスキャンを実施できることが確認できました。