Sysdig SecureではCI/CDパイプライン上でコンテナイメージのスキャンを実施できます。
今回はSysdig Secure Jenkinsプラグインを使用した、Jenkins上でのイメージスキャン手順をご紹介します。
参照URL:
ブログ記事:Sysdigを用いたJenkins上でのコンテナイメージのスキャン
https://sysdig.jp/blog/docker-scanning-jenkins/
Sysdig Secureドキュメント
https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Docker on DockerとしてJenkinsをインストール
Docker on DockerとしてJenkinsをインストールすると、Dcockerコンテナとして稼働しているJenkins上でDockerコマンドを実行できます。
インストール手順は下記サイトを参照しています。
Install Jenkins as Docker
https://www.jenkins.io/doc/book/installing/docker/
Docker内にブリッジネットワークを作成します。
docker network create jenkins
以下のdocker runコマンドでdocker:dind Dockerイメージをダウンロードし、実行します。
docker run \
--name jenkins-docker \
--rm \
--detach \
--privileged \
--network jenkins \
--network-alias docker \
--env DOCKER_TLS_CERTDIR=/certs \
--volume jenkins-docker-certs:/certs/client \
--volume jenkins-data:/var/jenkins_home \
--publish 2376:2376 \
docker:dind \
--storage-driver overlay2
下記内容でDockerfileを作成します。
vi Dockerfile
FROM jenkins/jenkins:2.375.2
USER root
RUN apt-get update && apt-get install -y lsb-release
RUN curl -fsSLo /usr/share/keyrings/docker-archive-keyring.asc \
https://download.docker.com/linux/debian/gpg
RUN echo "deb [arch=$(dpkg --print-architecture) \
signed-by=/usr/share/keyrings/docker-archive-keyring.asc] \
https://download.docker.com/linux/debian \
$(lsb_release -cs) stable" > /etc/apt/sources.list.d/docker.list
RUN apt-get update && apt-get install -y docker-ce-cli
USER jenkins
RUN jenkins-plugin-cli --plugins "blueocean docker-workflow"
DockerfileからDockerイメージを作成します。
docker build -t myjenkins-blueocean:2.375.2-1 .
DockerイメージからDockerコンテナを起動します。
docker run \
--name jenkins-blueocean \
--restart=on-failure \
--detach \
--network jenkins \
--env DOCKER_HOST=tcp://docker:2376 \
--env DOCKER_CERT_PATH=/certs/client \
--env DOCKER_TLS_VERIFY=1 \
--publish 8080:8080 \
--publish 50000:50000 \
--volume jenkins-data:/var/jenkins_home \
--volume jenkins-docker-certs:/certs/client:ro \
myjenkins-blueocean:2.375.2-1
Jenkins GUIにアクセスします。今回はAWS EC2上のUbuntuでDockerコンテナを起動しているので、アクセス先は下記URLとなります。
http://<EC2のパブリックIPアドレス>:8080
JenkinsのGUIにログインするためのAdminのパスワードは下記コマンドで確認できます。
sudo docker exec jenkins-blueocean cat /var/jenkins_home/secrets/initialAdminPassword
Sysdig Jenkins Pluginのインストール
Available pluginsページに移動し、"sysdig"で検索します。
"Sysdig Secure Container Image Scanner"プラグインを選択します。
"Download now and install after restart" をクリックします。
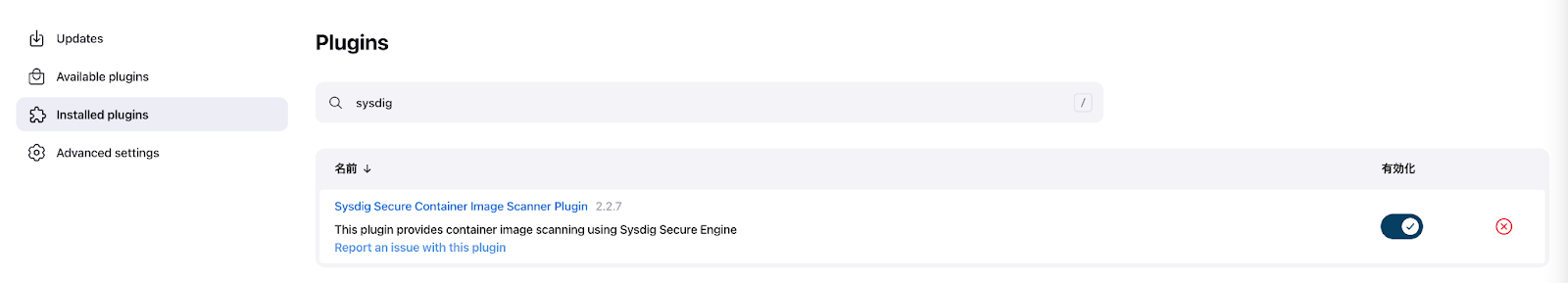
Installed pluginsページでプラグインがインストールされていることを確認します。
クレデンシャル作成
2つのクレデンシャルを作成します。
Sysdig Secure API Tokenのクレデンシャル作成
Jenkins の管理 > クレデンシャル管理 > System > グローバルドメインに移動します。
"Add Credentials"をクリックし、以下の値を設定します。
- パスワード: Sysdig Secure API Tokenの値を入力します
- ID: sysdig-secure-api-token
- 説明: Sysdig Secure API Token
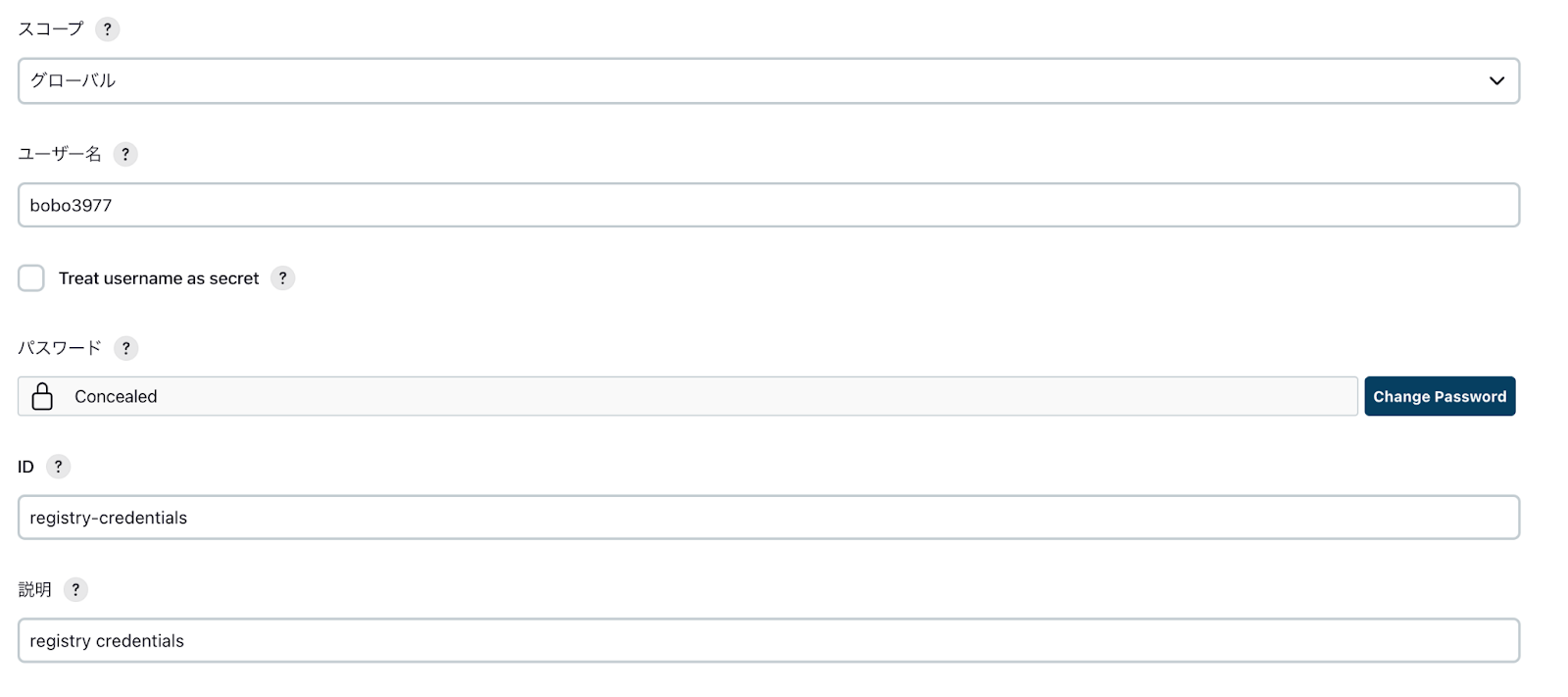
レジストリのクレデンシャル作成
イメージのアップロード先となるレジストリ(例:Docker Hub)のクレデンシャルを作成します。
"Add Credentials"をクリックし、以下の値を設定します。
- ユーザー名: レジストリのユーザ名
- パスワード: レジストリのパスワード
- ID: registry-credentials
- 説明: Registry Credentials
Sysdig Jenkins プラグイン設定
Jenkins の管理 > システム設定に移動します。
画面をスクロールダウンし、Sysdig Secure Pluginセクションに移動します。
以下の値を入力します。
- Sysdig Secure Endpoint URL: Sysdig Secure EndpointのURL(例:https://app.us4.sysdig.com)
Sysdig Secure Endpoint URLの値は利用しているSysdig SaaSリージョンにより異なります。
https://docs.sysdig.com/en/docs/administration/saas-regions-and-ip-ranges/
- Sysdig Secure API Credentials: 先ほど作成したSysdig Secure API Tokenクレデンシャルを選択します
-
Force usage of new scanning engineにチェックを入れます。
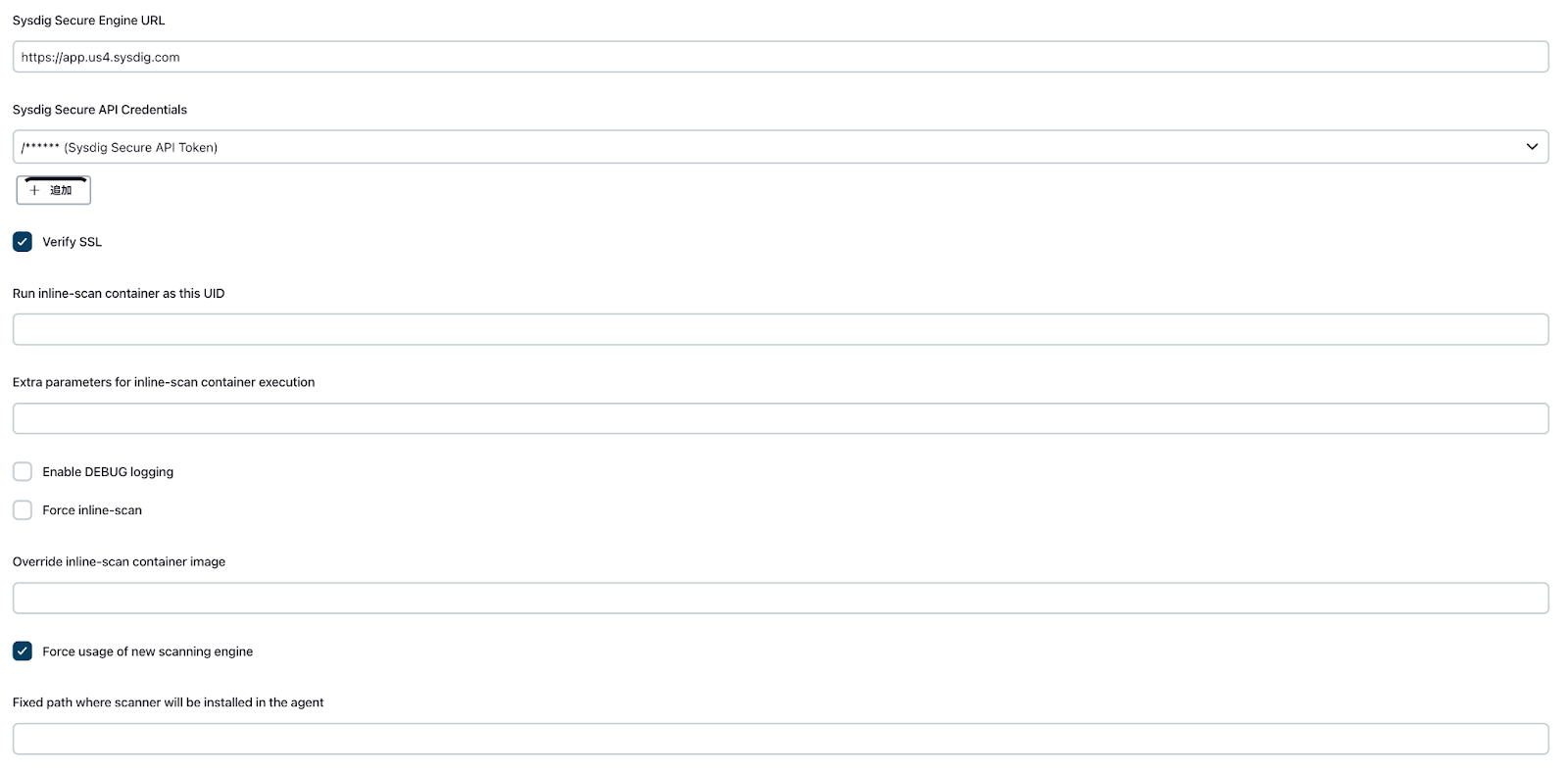
Sysdig Jenkins プラグインの利用
パイプラインプロジェクトを作成します。
新規ジョブ作成を選択します。
ジョブ名を入力します。
パイプラインを選択します。
下記サンプルスクリプトをScriptセクションに貼り付けます。
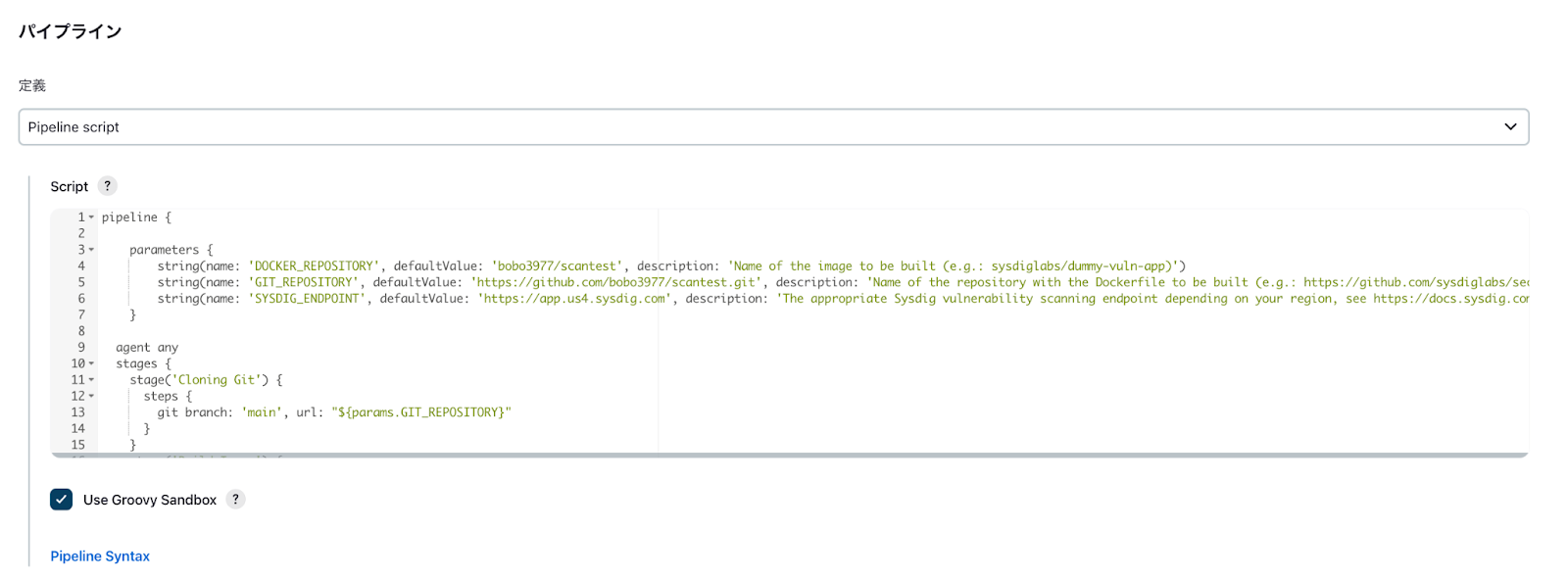
サンプルスクリプト
このサンプルスクリプトでは以下のパイプラインを実行します。
- 指定したGitリポジトリをクローン
- リポジトリ内のDockerfileからイメージを作成
- 作成したイメージをSysdig Secureでスキャン
- スキャン結果が問題なければ指定したレジストリにイメージをアップロード
下記の値はご自身の環境に合わせて修正してください。
- image:作成するイメージ名
- registryCredential:先ほど作成したレジストリ用のクレデンシャルID名
- repository:イメージの元となるDockerfileを格納してあるリポジトリ
- api_endpoint:Sysdig Secure EndpointのURL(例:https://app.us4.sysdig.com)
pipeline {
environment {
image = "docker.io/<YOUR IMAGE NAME>" + ":$BUILD_NUMBER"
registryCredential = "registry-credentials"
repository = 'https://github.com/<YOUR REPOSITORY NAME>.git'
api_endpoint = '<YOUR SYSDIG SECURE API ENDPOINT>'
myimage = ''
}
agent any
stages {
stage('Cloning Git') {
steps {
git branch: 'main', url: repository
}
}
stage('Building image') {
steps{
script {
myimage = docker.build(image, "./")
}
}
}
stage('Scanning Image') {
steps {
sysdigImageScan engineCredentialsId: 'sysdig-secure-api-token', imageName: "docker://" + image, engineURL: api_endpoint
}
}
stage('Deploy Image') {
steps{
script {
docker.withRegistry('', registryCredential) {
myimage.push()
myimage.push('latest')
}
}
}
}
}
}
今回のイメージスキャンテストで使用したDockerファイルは以下の2種類になります。リポジトリ直下にDockerfileを配置しています。
vi Dockerfile
FROM alpine
vi Dockerfile
FROM nginx
プロジェクトのビルド
ビルドを実行します。
パイプラインの結果
脆弱性を含んだイメージの場合はSysdig Secureによるコンテナイメージのスキャン結果がFAILとなり、パイプラインも失敗します。
#7 FAILURE - nginxイメージを使用した場合
#6 SCCESS - alpineイメージを使用した場合
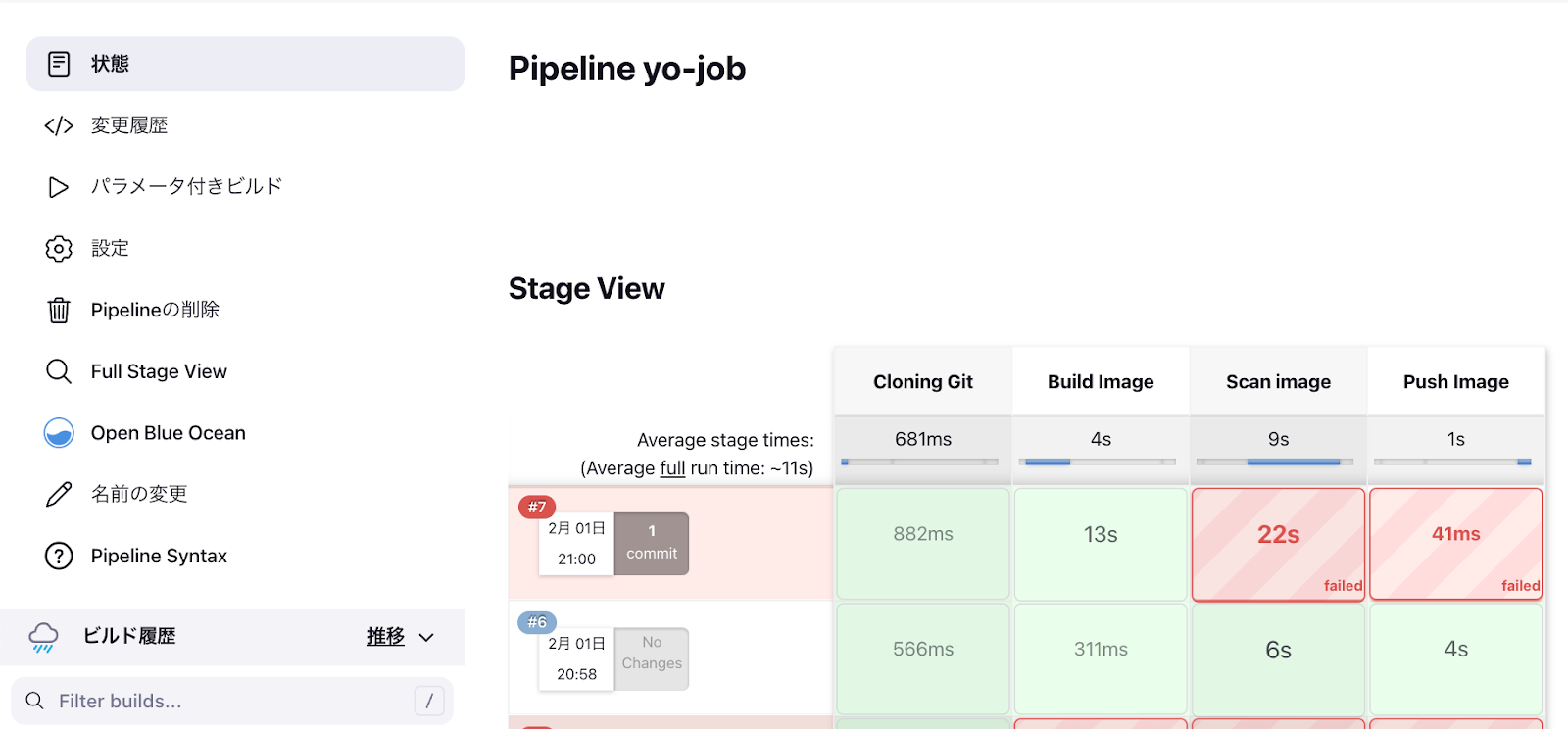
下記のコンソールログにイメージのスキャン結果が含まれていることに注目してください。
コンソールログ (FAILURE) - nginxイメージ
ログ
Started by user admin
[Pipeline] Start of Pipeline
[Pipeline] node
Running on Jenkins in /var/jenkins_home/workspace/yo-job
[Pipeline] {
[Pipeline] withEnv
[Pipeline] {
[Pipeline] stage
[Pipeline] { (Cloning Git)
[Pipeline] git
The recommended git tool is: NONE
No credentials specified
> git rev-parse --resolve-git-dir /var/jenkins_home/workspace/yo-job/.git # timeout=10
Fetching changes from the remote Git repository
> git config remote.origin.url https://github.com/bobo3977/scantest.git # timeout=10
Fetching upstream changes from https://github.com/bobo3977/scantest.git
> git --version # timeout=10
> git --version # 'git version 2.30.2'
> git fetch --tags --force --progress -- https://github.com/bobo3977/scantest.git +refs/heads/*:refs/remotes/origin/* # timeout=10
> git rev-parse refs/remotes/origin/main^{commit} # timeout=10
Checking out Revision 4b7f92c715ec55c42379773590819a3a6fa24eab (refs/remotes/origin/main)
> git config core.sparsecheckout # timeout=10
> git checkout -f 4b7f92c715ec55c42379773590819a3a6fa24eab # timeout=10
> git branch -a -v --no-abbrev # timeout=10
> git branch -D main # timeout=10
> git checkout -b main 4b7f92c715ec55c42379773590819a3a6fa24eab # timeout=10
Commit message: "Update Dockerfile"
> git rev-list --no-walk 4b7f92c715ec55c42379773590819a3a6fa24eab # timeout=10
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Building image)
[Pipeline] script
[Pipeline] {
[Pipeline] isUnix
[Pipeline] withEnv
[Pipeline] {
[Pipeline] sh
+ docker build -t docker.io/bobo3977/scantest:7 ./
#1 [internal] load build definition from Dockerfile
#1 transferring dockerfile: 48B done
#1 DONE 0.0s
#2 [internal] load .dockerignore
#2 transferring context: 2B done
#2 DONE 0.0s
#3 [internal] load metadata for docker.io/library/nginx:latest
#3 DONE 0.5s
#4 [1/1] FROM docker.io/library/nginx@sha256:b8f2383a95879e1ae064940d9a200f67a6c79e710ed82ac42263397367e7cc4e
#4 CACHED
#5 exporting to image
#5 exporting layers done
#5 writing image sha256:9c1aca5e6459514af244d4a62f592c50cce60b061afdebc7c3128b99fa088c65 done
#5 naming to docker.io/bobo3977/scantest:7 done
#5 DONE 0.0s
[Pipeline] }
[Pipeline] // withEnv
[Pipeline] }
[Pipeline] // script
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Scanning Image)
[Pipeline] sysdigImageScan
2023-02-03T05:16:09.165 INFO SysdigSecurePlugin Jenkins version: 2.375.2
2023-02-03T05:16:09.165 INFO SysdigSecurePlugin Sysdig Secure Container Image Scanner Plugin version: 2.2.7
2023-02-03T05:16:09.165 INFO SysdigSecurePlugin Using new-scanning engine
2023-02-03T05:16:09.165 INFO SysdigSecurePlugin Image Name: docker://docker.io/bobo3977/scantest:7
2023-02-03T05:16:09.165 INFO SysdigSecurePlugin Debug: false
2023-02-03T05:16:09.165 INFO SysdigSecurePlugin EngineURL: https://app.us4.sysdig.com
2023-02-03T05:16:09.165 INFO SysdigSecurePlugin EngineVerify: true
2023-02-03T05:16:09.166 INFO SysdigSecurePlugin Policies:
2023-02-03T05:16:09.166 INFO SysdigSecurePlugin InlineScanExtraParams:
2023-02-03T05:16:09.166 INFO SysdigSecurePlugin BailOnFail: true
2023-02-03T05:16:09.166 INFO SysdigSecurePlugin BailOnPluginFail: true
2023-02-03T05:16:09.166 INFO SysdigSecurePlugin Downloading inlinescan v1.3.3
2023-02-03T05:16:09.166 INFO SysdigSecurePlugin Linux
2023-02-03T05:16:12.546 INFO SysdigSecurePlugin Inlinescan binary downloaded to /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/bin/inlinescan-1.3.3.bin
2023-02-03T05:16:12.546 INFO SysdigSecurePlugin Executing: /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/bin/inlinescan-1.3.3.bin --apiurl=https://app.us4.sysdig.com --dbpath=/var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/db --cachepath=/var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/cache --output-json=/var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/inlinescan.json --console-log docker://docker.io/bobo3977/scantest:7
2023-02-03T05:16:12.547 INFO SysdigSecurePlugin Waiting for scanner execution to be completed...
2023-02-03T05:16:13.046 INFO SysdigSecurePlugin 2023-02-03T05:16:12Z Starting analysis with Sysdig scanner version 1.3.3
2023-02-03T05:16:13.047 INFO SysdigSecurePlugin 2023-02-03T05:16:12Z Retrieving MainDB...
2023-02-03T05:16:13.047 INFO SysdigSecurePlugin F Using path for the cache: /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/cache/inlineScannerCache.db
2023-02-03T05:16:13.047 INFO SysdigSecurePlugin 2023-02-03T05:16:12Z INF Retrieving MainDB
2023-02-03T05:16:13.047 INFO SysdigSecurePlugin 2023-02-03T05:16:12Z WRN error, overwrite current MainDB error="stat /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/main.db.meta.json: no such file or directory"
2023-02-03T05:16:13.047 INFO SysdigSecurePlugin 2023-02-03T05:16:12Z INF Downloading a new MainDB to /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/db/sysdig-db-data
2023-02-03T05:16:14.548 INFO SysdigSecurePlugin 2023-02-03T05:16:14Z INF DB correctly downloaded dbTimestamp=2023-02-02T22:27:40Z dbVersion=V1
2023-02-03T05:16:14.548 INFO SysdigSecurePlugin 2023-02-03T05:16:14Z INF Got updated DB file on path /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/db/sysdig-db-data: 131383376 bytes downloaded
2023-02-03T05:16:14.548 INFO SysdigSecurePlugin 2023-02-03T05:16:14Z INF Loading MainDB from: /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675401369166/db/sysdig-db-data
2023-02-03T05:16:14.548 INFO SysdigSecurePlugin 2023-02-03T05:16:14Z INF Done: MainDB loaded
2023-02-03T05:16:15.048 INFO SysdigSecurePlugin 2023-02-03T05:16:14Z INF GET pkgMeta indexedAt on index changed from 0001-01-01 00:00:00 +0000 UTC to 2023-02-01 14:19:38.821 +0000 UTC on GetPkgMetaIndexedAt
2023-02-03T05:16:15.048 INFO SysdigSecurePlugin 2023-02-03T05:16:14Z INF Retrieving image imgName=docker://docker.io/bobo3977/scantest:7
2023-02-03T05:16:15.048 INFO SysdigSecurePlugin 2023-02-03T05:16:14Z WRN failed to create containers-storage loader, will continue without this image loader error="error creating default store object: chown /var/jenkins_home/.local/share/containers/storage/vfs: operation not permitted"
2023-02-03T05:16:17.049 INFO SysdigSecurePlugin 2023-02-03T05:16:16Z INF Done: image retrieved imgName=docker://docker.io/bobo3977/scantest:7
2023-02-03T05:16:17.049 INFO SysdigSecurePlugin 2023-02-03T05:16:16Z INF Start analyzing image
2023-02-03T05:16:19.549 INFO SysdigSecurePlugin 2023-02-03T05:16:19Z INF Start matching vulnerabilities
2023-02-03T05:16:19.550 INFO SysdigSecurePlugin 2023-02-03T05:16:19Z INF Matched 142 OS packages and 0 nonOS packages
2023-02-03T05:16:19.550 INFO SysdigSecurePlugin 2023-02-03T05:16:19Z INF Start policies evaluation
2023-02-03T05:16:19.550 INFO SysdigSecurePlugin 2023-02-03T05:16:19Z INF End policies evaluation result=failed
2023-02-03T05:16:19.812 INFO SysdigSecurePlugin Scanner exit code: 1
2023-02-03T05:16:20.020 INFO SysdigSecurePlugin Sysdig Secure Container Image Scanner Plugin step result - FAIL
2023-02-03T05:16:20.021 INFO SysdigSecurePlugin Policy evaluation summary for docker.io/bobo3977/scantest:7 - stop: 13 (+0 whitelisted), warn: 0 (+0 whitelisted), go: 0 (+0 whitelisted), final: STOP
Archiving artifacts
2023-02-03T05:16:20.034 INFO SysdigSecurePlugin Completed Sysdig Secure Container Image Scanner step
2023-02-03T05:16:20.034 WARN SysdigSecurePlugin Failing Sysdig Secure Container Image Scanner Plugin step due to final result FAIL
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Deploy Image)
Stage "Deploy Image" skipped due to earlier failure(s)
[Pipeline] }
[Pipeline] // stage
[Pipeline] }
[Pipeline] // withEnv
[Pipeline] }
[Pipeline] // node
[Pipeline] End of Pipeline
ERROR: Failing Sysdig Secure Container Image Scanner Plugin step due to final result FAIL
Finished: FAILURE
コンソールログ (SUCCESS) - alpineイメージ
ログ
Started by user admin
[Pipeline] Start of Pipeline
[Pipeline] node
Running on Jenkins in /var/jenkins_home/workspace/yo-job
[Pipeline] {
[Pipeline] withEnv
[Pipeline] {
[Pipeline] stage
[Pipeline] { (Cloning Git)
[Pipeline] git
The recommended git tool is: NONE
No credentials specified
> git rev-parse --resolve-git-dir /var/jenkins_home/workspace/yo-job/.git # timeout=10
Fetching changes from the remote Git repository
> git config remote.origin.url https://github.com/sysdiglabs/secure-inline-scan-examples.git # timeout=10
Fetching upstream changes from https://github.com/sysdiglabs/secure-inline-scan-examples.git
> git --version # timeout=10
> git --version # 'git version 2.30.2'
> git fetch --tags --force --progress -- https://github.com/sysdiglabs/secure-inline-scan-examples.git +refs/heads/*:refs/remotes/origin/* # timeout=10
> git rev-parse refs/remotes/origin/main^{commit} # timeout=10
Checking out Revision 6f6356f7a11d6ca2598293b036bb1190ddc00912 (refs/remotes/origin/main)
> git config core.sparsecheckout # timeout=10
> git checkout -f 6f6356f7a11d6ca2598293b036bb1190ddc00912 # timeout=10
> git branch -a -v --no-abbrev # timeout=10
> git branch -D main # timeout=10
> git checkout -b main 6f6356f7a11d6ca2598293b036bb1190ddc00912 # timeout=10
Commit message: "Make the scanner to fail always with log4j vulnerability (#48)"
> git rev-list --no-walk 6f6356f7a11d6ca2598293b036bb1190ddc00912 # timeout=10
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Building image)
[Pipeline] script
[Pipeline] {
[Pipeline] isUnix
[Pipeline] withEnv
[Pipeline] {
[Pipeline] sh
+ docker build -t docker.io/bobo3977/scantest:2 ./jenkins/new-scan-engine/
#1 [internal] load build definition from Dockerfile
#1 transferring dockerfile: 48B done
#1 DONE 0.0s
#2 [internal] load .dockerignore
#2 transferring context: 2B done
#2 DONE 0.0s
#3 [internal] load metadata for docker.io/library/alpine:latest
#3 DONE 0.5s
#4 [1/1] FROM docker.io/library/alpine@sha256:f271e74b17ced29b915d351685fd4644785c6d1559dd1f2d4189a5e851ef753a
#4 CACHED
#5 exporting to image
#5 exporting layers done
#5 writing image sha256:ac8cc5d3abf3588fd292bc9a77710299682d125d839b6c76957a13ef8c615ddd done
#5 naming to docker.io/bobo3977/scantest:2 done
#5 DONE 0.0s
[Pipeline] }
[Pipeline] // withEnv
[Pipeline] }
[Pipeline] // script
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Scanning Image)
[Pipeline] sysdigImageScan
2023-02-03T04:50:18.573 INFO SysdigSecurePlugin Jenkins version: 2.375.2
2023-02-03T04:50:18.573 INFO SysdigSecurePlugin Sysdig Secure Container Image Scanner Plugin version: 2.2.7
2023-02-03T04:50:18.573 INFO SysdigSecurePlugin Using new-scanning engine
2023-02-03T04:50:18.573 INFO SysdigSecurePlugin Image Name: docker://docker.io/bobo3977/scantest:2
2023-02-03T04:50:18.573 INFO SysdigSecurePlugin Debug: false
2023-02-03T04:50:18.573 INFO SysdigSecurePlugin EngineURL: https://app.us4.sysdig.com
2023-02-03T04:50:18.573 INFO SysdigSecurePlugin EngineVerify: true
2023-02-03T04:50:18.573 INFO SysdigSecurePlugin Policies:
2023-02-03T04:50:18.573 INFO SysdigSecurePlugin InlineScanExtraParams:
2023-02-03T04:50:18.574 INFO SysdigSecurePlugin BailOnFail: true
2023-02-03T04:50:18.574 INFO SysdigSecurePlugin BailOnPluginFail: true
2023-02-03T04:50:18.574 INFO SysdigSecurePlugin Downloading inlinescan v1.3.3
2023-02-03T04:50:18.574 INFO SysdigSecurePlugin Linux
2023-02-03T04:50:21.456 INFO SysdigSecurePlugin Inlinescan binary downloaded to /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/bin/inlinescan-1.3.3.bin
2023-02-03T04:50:21.457 INFO SysdigSecurePlugin Executing: /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/bin/inlinescan-1.3.3.bin --apiurl=https://app.us4.sysdig.com --dbpath=/var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/db --cachepath=/var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/cache --output-json=/var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/inlinescan.json --console-log docker://docker.io/bobo3977/scantest:2
2023-02-03T04:50:21.458 INFO SysdigSecurePlugin Waiting for scanner execution to be completed...
2023-02-03T04:50:21.957 INFO SysdigSecurePlugin 2023-02-03T04:50:21Z Starting analysis with Sysdig scanner version 1.3.3
2023-02-03T04:50:21.957 INFO SysdigSecurePlugin 2023-02-03T04:50:21Z Retrieving MainDB...
2023-02-03T04:50:21.957 INFO SysdigSecurePlugin F Using path for the cache: /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/cache/inlineScannerCache.db
2023-02-03T04:50:21.957 INFO SysdigSecurePlugin 2023-02-03T04:50:21Z INF Retrieving MainDB
2023-02-03T04:50:21.957 INFO SysdigSecurePlugin 2023-02-03T04:50:21Z WRN error, overwrite current MainDB error="stat /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/main.db.meta.json: no such file or directory"
2023-02-03T04:50:21.957 INFO SysdigSecurePlugin 2023-02-03T04:50:21Z INF Downloading a new MainDB to /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/db/sysdig-db-data
2023-02-03T04:50:23.458 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF DB correctly downloaded dbTimestamp=2023-02-02T22:27:40Z dbVersion=V1
2023-02-03T04:50:23.458 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF Got updated DB file on path /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/db/sysdig-db-data: 131383376 bytes downloaded
2023-02-03T04:50:23.458 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF Loading MainDB from: /var/jenkins_home/workspace/yo-job/sysdig-secure-scan-1675399818574/db/sysdig-db-data
2023-02-03T04:50:23.458 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF Done: MainDB loaded
2023-02-03T04:50:23.458 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF GET pkgMeta indexedAt on index changed from 0001-01-01 00:00:00 +0000 UTC to 2023-02-01 14:19:38.821 +0000 UTC on GetPkgMetaIndexedAt
2023-02-03T04:50:23.458 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF Retrieving image imgName=docker://docker.io/bobo3977/scantest:2
2023-02-03T04:50:23.459 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z WRN failed to create containers-storage loader, will continue without this image loader error="error creating default store object: chown /var/jenkins_home/.local/share/containers/storage/vfs: operation not permitted"
2023-02-03T04:50:23.959 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF Done: image retrieved imgName=docker://docker.io/bobo3977/scantest:2
2023-02-03T04:50:23.959 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF Start analyzing image
2023-02-03T04:50:23.959 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF Start matching vulnerabilities
2023-02-03T04:50:23.959 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF Matched 15 OS packages and 0 nonOS packages
2023-02-03T04:50:23.959 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF Start policies evaluation
2023-02-03T04:50:23.959 INFO SysdigSecurePlugin 2023-02-03T04:50:23Z INF End policies evaluation result=passed
2023-02-03T04:50:24.131 INFO SysdigSecurePlugin Scanner exit code: 0
2023-02-03T04:50:24.162 INFO SysdigSecurePlugin Sysdig Secure Container Image Scanner Plugin step result - PASS
2023-02-03T04:50:24.163 INFO SysdigSecurePlugin Policy evaluation summary for sha256:737b582af61d9f04f52a6337d43721bd434b8454a0f2e0fec53c63905034bfe3 - stop: 0 (+0 whitelisted), warn: 0 (+0 whitelisted), go: 0 (+0 whitelisted), final: GO
2023-02-03T04:50:24.163 WARN SysdigSecurePlugin Repo_Tag element not found in gate output, using imageId: sha256:737b582af61d9f04f52a6337d43721bd434b8454a0f2e0fec53c63905034bfe3
Archiving artifacts
2023-02-03T04:50:24.167 INFO SysdigSecurePlugin Completed Sysdig Secure Container Image Scanner step
2023-02-03T04:50:24.168 INFO SysdigSecurePlugin Marking Sysdig Secure Container Image Scanner step as successful, final result PASS
[Pipeline] }
[Pipeline] // stage
[Pipeline] stage
[Pipeline] { (Deploy Image)
[Pipeline] script
[Pipeline] {
[Pipeline] withEnv
[Pipeline] {
[Pipeline] withDockerRegistry
$ docker login -u bobo3977 -p ******** https://index.docker.io/v1/
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /var/jenkins_home/workspace/yo-job@tmp/728d8440-1b96-40a6-9ca7-9e6dee707b0f/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
[Pipeline] {
[Pipeline] isUnix
[Pipeline] withEnv
[Pipeline] {
[Pipeline] sh
+ docker tag docker.io/bobo3977/scantest:2 docker.io/bobo3977/scantest:2
[Pipeline] }
[Pipeline] // withEnv
[Pipeline] isUnix
[Pipeline] withEnv
[Pipeline] {
[Pipeline] sh
+ docker push docker.io/bobo3977/scantest:2
The push refers to repository [docker.io/bobo3977/scantest]
8e012198eea1: Preparing
8e012198eea1: Layer already exists
2: digest: sha256:737b582af61d9f04f52a6337d43721bd434b8454a0f2e0fec53c63905034bfe3 size: 527
[Pipeline] }
[Pipeline] // withEnv
[Pipeline] isUnix
[Pipeline] withEnv
[Pipeline] {
[Pipeline] sh
+ docker tag docker.io/bobo3977/scantest:2 docker.io/bobo3977/scantest:latest
[Pipeline] }
[Pipeline] // withEnv
[Pipeline] isUnix
[Pipeline] withEnv
[Pipeline] {
[Pipeline] sh
+ docker push docker.io/bobo3977/scantest:latest
The push refers to repository [docker.io/bobo3977/scantest]
8e012198eea1: Preparing
8e012198eea1: Layer already exists
latest: digest: sha256:737b582af61d9f04f52a6337d43721bd434b8454a0f2e0fec53c63905034bfe3 size: 527
[Pipeline] }
[Pipeline] // withEnv
[Pipeline] }
[Pipeline] // withDockerRegistry
[Pipeline] }
[Pipeline] // withEnv
[Pipeline] }
[Pipeline] // script
[Pipeline] }
[Pipeline] // stage
[Pipeline] }
[Pipeline] // withEnv
[Pipeline] }
[Pipeline] // node
[Pipeline] End of Pipeline
Finished: SUCCESS
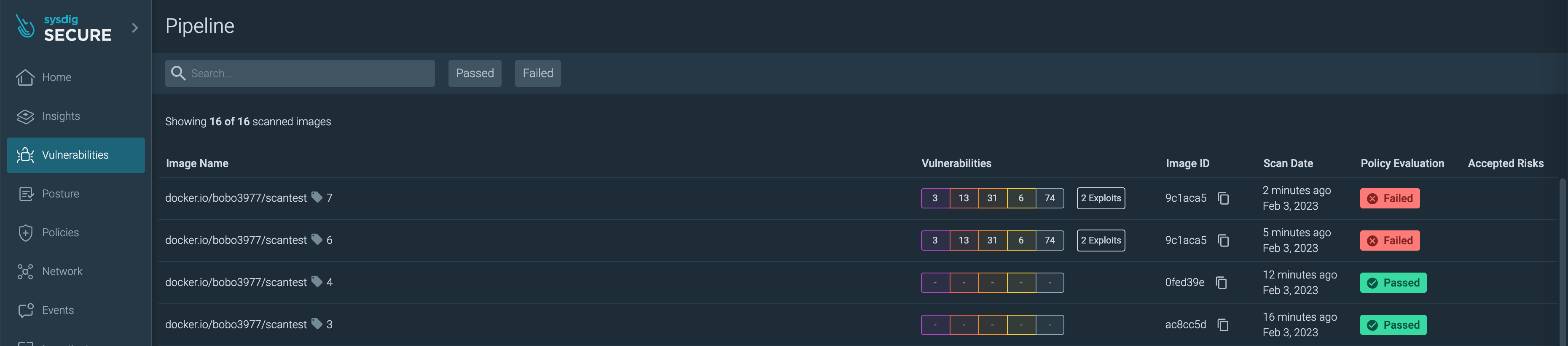
Sysdig Secure UIでの確認
Sysdig Secure UIにログインします。
Vulnerabilities > Pipelineに移動します。
スキャン結果の一覧を確認します。
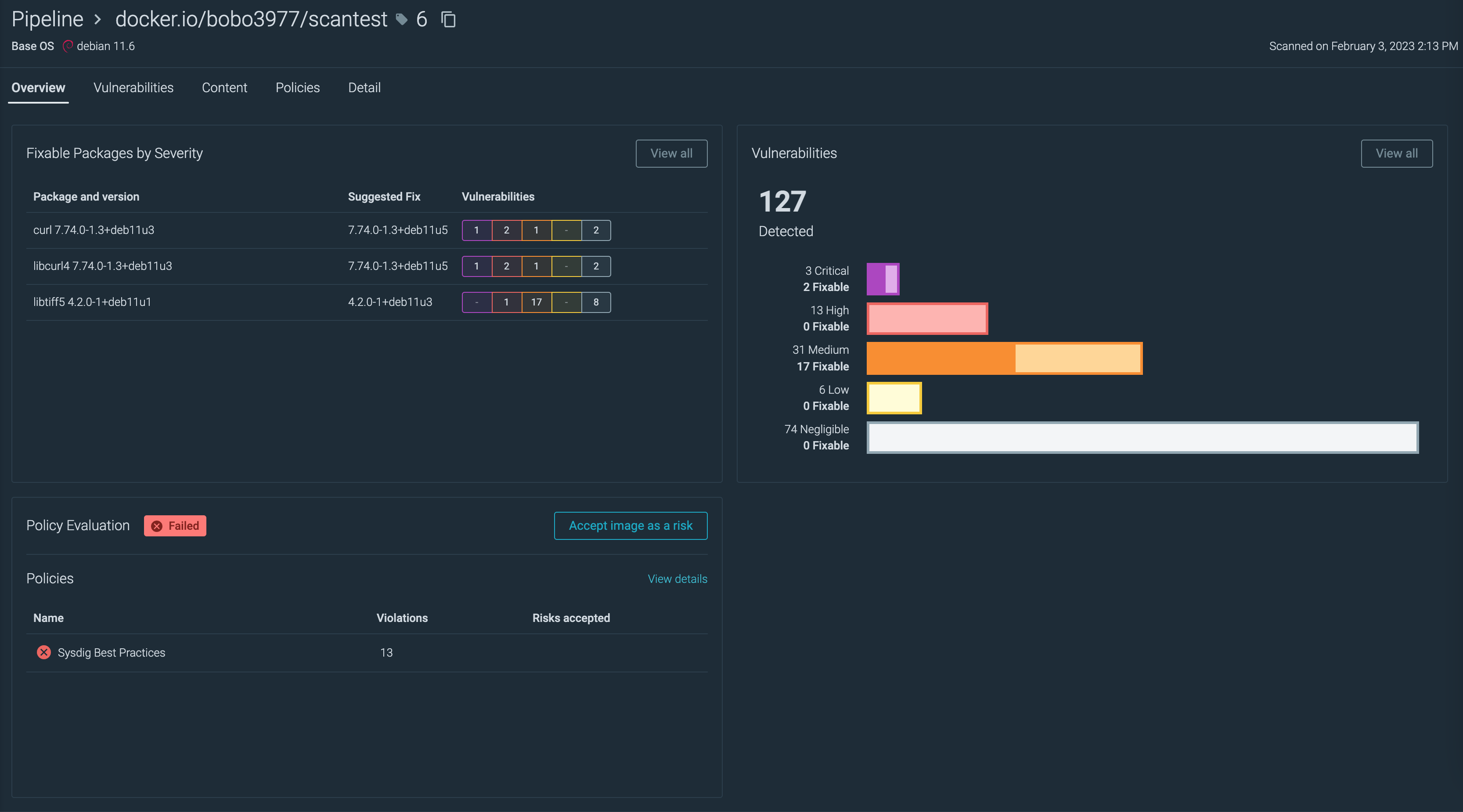
スキャン結果で失敗したイメージの詳細画面
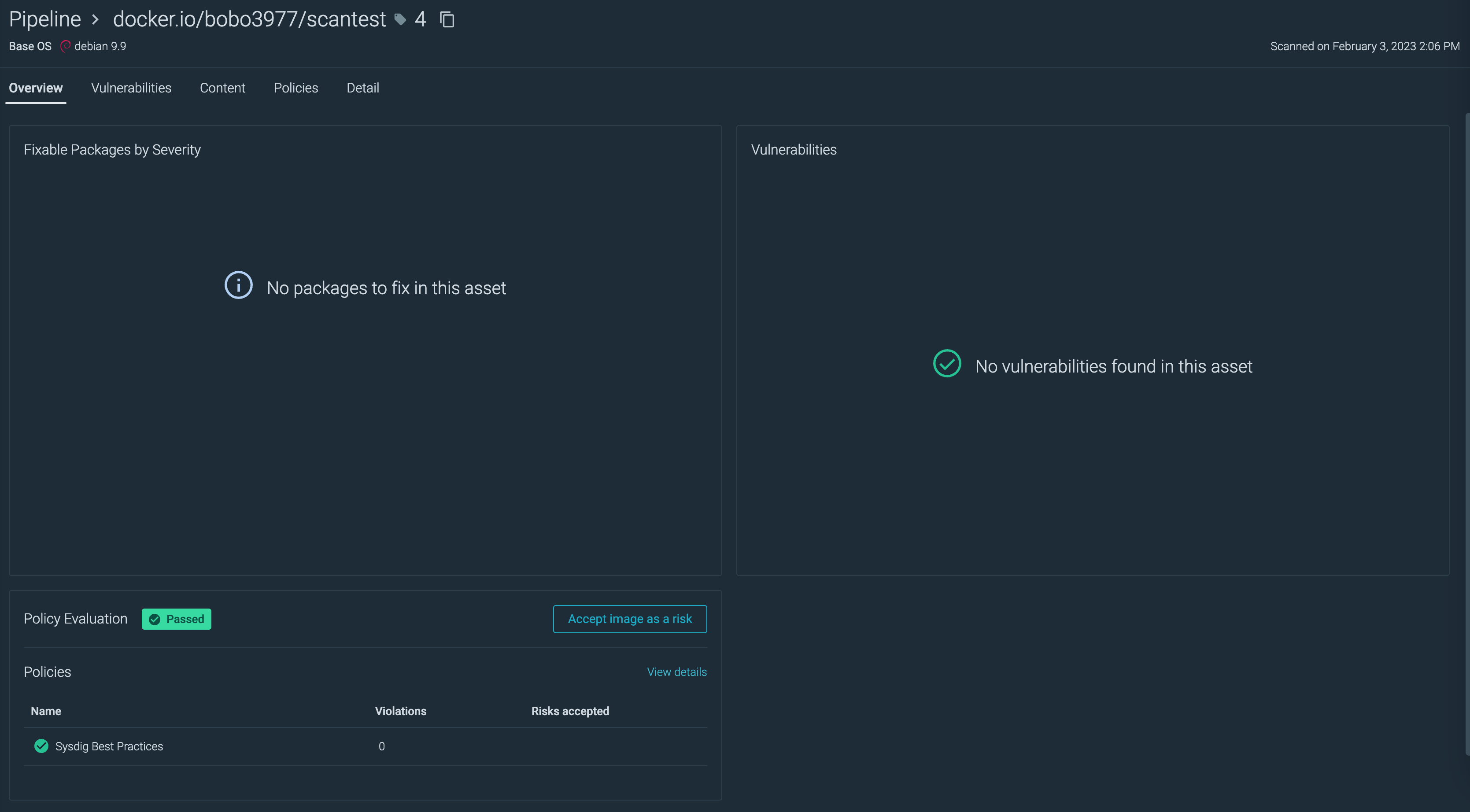
スキャン結果で成功したイメージの詳細画面
まとめ
Sysdig Secure Jenkinsプラグインを使用することで、JenkinsのCI/CDパイプライン上で簡単にコンテナイメージスキャンを実施できることが確認できました。