はじめに
この記事は Datadog Advent Calendar 2022 の11日目の記事です。
Stratus-Red-Team(SRT)とは?

- Datadogが運営するOSSプロジェクトの一つ。
- Stratus-Red-Team Github Repository
- MaintainerはDatadogのCloud Security ResearcherであるChristophe Tafani-Dereeper氏
- クラウド環境向けにレッドチーム的な試験が簡単なCLI操作で行えます。
- (当然ながら)悪用厳禁
- サンドボックス環境など、他に影響が出ない環境での利用を想定
- SRTは、攻撃を行う対象を作成して(Warm-Up)、攻撃して(Detonate)、後片付け(Clean-Up)までを実行できるので、攻撃対象を用意する必要がありません。

SRTが用意している攻撃テクニック
- 攻撃テクニックのリスト 下記stratus listコマンドでも一覧表示が可能
- AWS、Azure、GCP用、Kubernetes用があり、現在の所AWSが多め
- それぞれの攻撃シナリオにMITRE ATT&CK TACTICSとのマッピングがされている
テクニック一覧
~ $ stratus list
View the list of all available attack techniques at: https://stratus-red-team.cloud/attack-techniques/list/
+------------------------------------------------------------+------------------------------------------------------------------+------------+----------------------+
| TECHNIQUE ID | TECHNIQUE NAME | PLATFORM | MITRE ATT&CK TACTIC |
+------------------------------------------------------------+------------------------------------------------------------------+------------+----------------------+
| aws.credential-access.ec2-get-password-data | Retrieve EC2 Password Data | AWS | Credential Access |
| aws.credential-access.ec2-steal-instance-credentials | Steal EC2 Instance Credentials | AWS | Credential Access |
| aws.credential-access.secretsmanager-retrieve-secrets | Retrieve a High Number of Secrets Manager secrets | AWS | Credential Access |
| aws.credential-access.ssm-retrieve-securestring-parameters | Retrieve And Decrypt SSM Parameters | AWS | Credential Access |
| aws.defense-evasion.cloudtrail-delete | Delete CloudTrail Trail | AWS | Defense Evasion |
| aws.defense-evasion.cloudtrail-event-selectors | Disable CloudTrail Logging Through Event Selectors | AWS | Defense Evasion |
| aws.defense-evasion.cloudtrail-lifecycle-rule | CloudTrail Logs Impairment Through S3 Lifecycle Rule | AWS | Defense Evasion |
| aws.defense-evasion.cloudtrail-stop | Stop CloudTrail Trail | AWS | Defense Evasion |
| aws.defense-evasion.organizations-leave | Attempt to Leave the AWS Organization | AWS | Defense Evasion |
| aws.defense-evasion.vpc-remove-flow-logs | Remove VPC Flow Logs | AWS | Defense Evasion |
| aws.discovery.ec2-enumerate-from-instance | Execute Discovery Commands on an EC2 Instance | AWS | Discovery |
| aws.discovery.ec2-download-user-data | Download EC2 Instance User Data | AWS | Discovery |
| aws.execution.ec2-launch-unusual-instances | Launch Unusual EC2 instances | AWS | Execution |
| aws.execution.ec2-user-data | Execute Commands on EC2 Instance via User Data | AWS | Execution |
| | | | Privilege Escalation |
| aws.exfiltration.ec2-security-group-open-port-22-ingress | Open Ingress Port 22 on a Security Group | AWS | Exfiltration |
| aws.exfiltration.ec2-share-ami | Exfiltrate an AMI by Sharing It | AWS | Exfiltration |
| aws.exfiltration.ec2-share-ebs-snapshot | Exfiltrate EBS Snapshot by Sharing It | AWS | Exfiltration |
| aws.exfiltration.rds-share-snapshot | Exfiltrate RDS Snapshot by Sharing | AWS | Exfiltration |
| aws.exfiltration.s3-backdoor-bucket-policy | Backdoor an S3 Bucket via its Bucket Policy | AWS | Exfiltration |
| aws.initial-access.console-login-without-mfa | Console Login without MFA | AWS | Initial Access |
| aws.persistence.iam-backdoor-role | Backdoor an IAM Role | AWS | Persistence |
| aws.persistence.iam-backdoor-user | Create an Access Key on an IAM User | AWS | Persistence |
| | | | Privilege Escalation |
| aws.persistence.iam-create-admin-user | Create an administrative IAM User | AWS | Persistence |
| | | | Privilege Escalation |
| aws.persistence.iam-create-user-login-profile | Create a Login Profile on an IAM User | AWS | Persistence |
| | | | Privilege Escalation |
| aws.persistence.lambda-backdoor-function | Backdoor Lambda Function Through Resource-Based Policy | AWS | Persistence |
| aws.persistence.lambda-overwrite-code | Overwrite Lambda Function Code | AWS | Persistence |
| aws.persistence.rolesanywhere-create-trust-anchor | Create an IAM Roles Anywhere trust anchor | AWS | Persistence |
| | | | Privilege Escalation |
| azure.execution.vm-custom-script-extension | Execute Command on Virtual Machine using Custom Script Extension | azure | Execution |
| azure.execution.vm-run-command | Execute Commands on Virtual Machine using Run Command | azure | Execution |
| azure.exfiltration.disk-export | Export Disk Through SAS URL | azure | Exfiltration |
| gcp.persistence.create-admin-service-account | Create an Admin GCP Service Account | GCP | Persistence |
| | | | Privilege Escalation |
| gcp.persistence.create-service-account-key | Create a GCP Service Account Key | GCP | Persistence |
| | | | Privilege Escalation |
| gcp.privilege-escalation.impersonate-service-accounts | Impersonate GCP Service Accounts | GCP | Privilege Escalation |
| k8s.credential-access.dump-secrets | Dump All Secrets | kubernetes | Credential Access |
| k8s.credential-access.steal-serviceaccount-token | Steal Pod Service Account Token | kubernetes | Credential Access |
| k8s.persistence.create-admin-clusterrole | Create Admin ClusterRole | kubernetes | Persistence |
| | | | Privilege Escalation |
| k8s.persistence.create-client-certificate | Create Client Certificate Credential | kubernetes | Persistence |
| k8s.persistence.create-token | Create Long-Lived Token | kubernetes | Persistence |
| k8s.privilege-escalation.hostpath-volume | Container breakout via hostPath volume mount | kubernetes | Privilege Escalation |
| k8s.privilege-escalation.nodes-proxy | Privilege escalation through node/proxy permissions | kubernetes | Privilege Escalation |
| k8s.privilege-escalation.privileged-pod | Run a Privileged Pod | kubernetes | Privilege Escalation |
+------------------------------------------------------------+------------------------------------------------------------------+------------+----------------------+
インストール
- Getting Startedガイドに従って実施。簡単なので割愛します。
シナリオ1:Assume RoleしたEC2から探索コマンドを実行する
- SRT攻撃シナリオ名: Execute Discovery Commands on an EC2 Instance
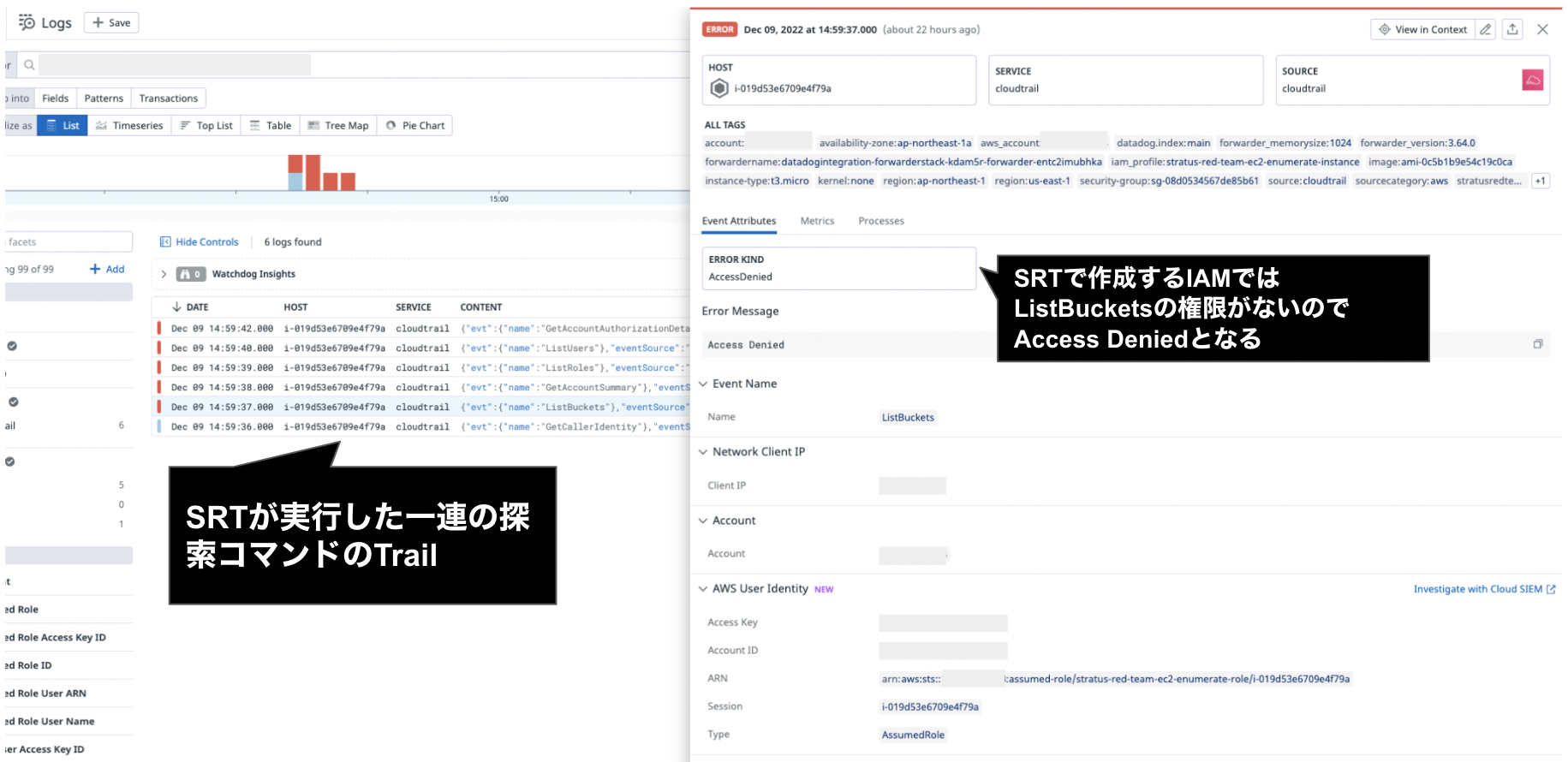
- この攻撃シナリオをSRTで実行すると、攻撃対象として準備したEC2上で、下記のような探索目的のコマンドを実行します。
sts:GetCallerIdentity
s3:ListBuckets
iam:GetAccountSummary
iam:ListRoles
iam:ListUsers
iam:GetAccountAuthorizationDetails
ec2:DescribeSnapshots
cloudtrail:DescribeTrails
guardduty:ListDetectors
1. 準備
stratus warmupコマンドで、EC2を作成する
~ $ stratus warmup aws.discovery.ec2-enumerate-from-instance
実行結果
2022/12/06 16:44:55 Checking your authentication against AWS
2022/12/06 16:44:55 Warming up aws.discovery.ec2-enumerate-from-instance
2022/12/06 16:44:55 Applying Terraform to spin up technique prerequisites
2022/12/06 16:46:52 Instance id i-07bf85c179adb9fa5 in ap-northeast-1a ready
2. 探索コマンドの実行
stratus detonateコマンドで、探索コマンドを実行させる
~ $ stratus detonate aws.discovery.ec2-enumerate-from-instance
実行結果
2022/12/06 16:50:01 Checking your authentication against AWS
2022/12/06 16:50:01 Not warming up - aws.discovery.ec2-enumerate-from-instance is already warm. Use --force to force
2022/12/06 16:50:01 Running commands through SSM on i-07bf85c179adb9fa5:
- aws sts get-caller-identity || true
- aws s3 ls || true
- aws iam get-account-summary || true
- aws iam list-roles || true
- aws iam list-users || true
- aws iam get-account-authorization-details >/dev/null || true
- aws ec2 describe-snapshots || true
- aws cloudtrail describe-trails || true
- aws guardduty list-detectors || true
3. Datadog Logsでの見え方
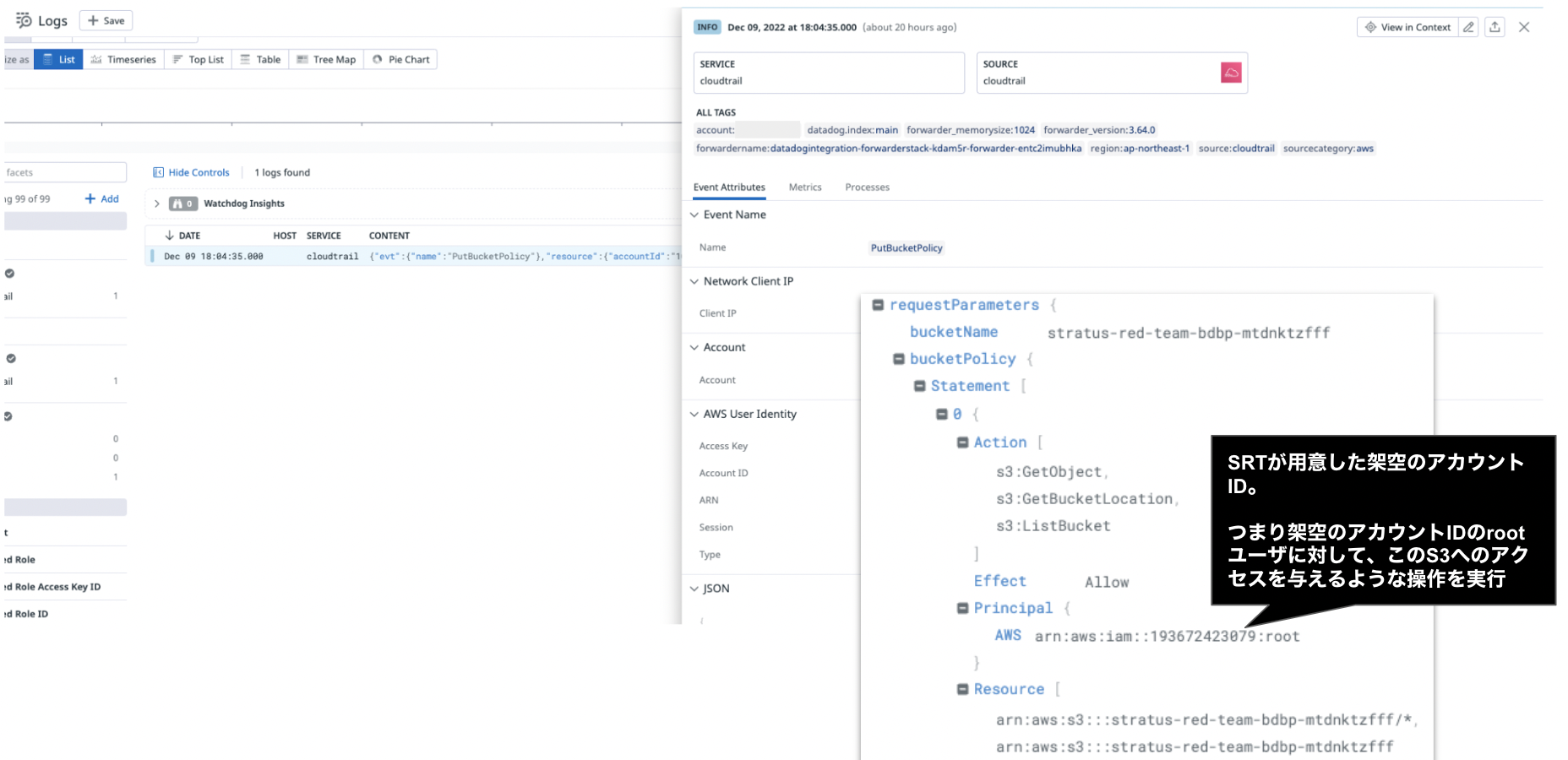
シナリオ2:S3バケットポリシーを操作して外部のアカウントからアクセス可能にする
- SRT攻撃シナリオ名: Backdoor an S3 Bucket via its Bucket Policy
1. 準備
stratus warmupコマンドで、EC2を作成する
~ $ stratus warmup aws.discovery.ec2-enumerate-from-instance
2022/12/06 16:44:55 Checking your authentication against AWS
2022/12/06 16:44:55 Warming up aws.discovery.ec2-enumerate-from-instance
2022/12/06 16:44:55 Applying Terraform to spin up technique prerequisites
2022/12/06 16:46:52 Instance id i-07bf85c179adb9fa5 in ap-northeast-1a ready
2. S3 bucket policyの作成
stratus detonateコマンドで、s3 bucket policyを作成する
~ $ stratus detonate aws.exfiltration.s3-backdoor-bucket-policy
実行結果
2022/12/09 18:04:33 Checking your authentication against AWS
2022/12/09 18:04:34 Not warming up - aws.exfiltration.s3-backdoor-bucket-policy is already warm. Use --force to force
2022/12/09 18:04:34 Backdooring bucket policy of stratus-red-team-bdbp-mtdnktzfff
3. Datadog Logsでの見え方
後片付け
cleanupコマンドを実行することで、作成したリソースの削除を行う。STATUSがCOLDに戻る。
~ $ stratus cleanup aws.discovery.ec2-enumerate-from-instance
2022/12/06 17:10:21 Cleaning up aws.discovery.ec2-enumerate-from-instance
2022/12/06 17:10:21 Cleaning up technique prerequisites with terraform destroy
+-------------------------------------------+-----------------------------------------------+--------+
| ID | NAME | STATUS |
+-------------------------------------------+-----------------------------------------------+--------+
| aws.discovery.ec2-enumerate-from-instance | Execute Discovery Commands on an EC2 Instance | COLD |
+-------------------------------------------+-----------------------------------------------+--------+
~ $ stratus cleanup aws.exfiltration.s3-backdoor-bucket-policy
2022/12/09 18:24:06 Cleaning up aws.exfiltration.s3-backdoor-bucket-policy
2022/12/09 18:24:06 Reverting detonation of technique aws.exfiltration.s3-backdoor-bucket-policy
2022/12/09 18:24:06 Removing malicious bucket policy on stratus-red-team-bdbp-mtdnktzfff
2022/12/09 18:24:07 Cleaning up technique prerequisites with terraform destroy
+--------------------------------------------+---------------------------------------------+--------+
| ID | NAME | STATUS |
+--------------------------------------------+---------------------------------------------+--------+
| aws.exfiltration.s3-backdoor-bucket-policy | Backdoor an S3 Bucket via its Bucket Policy | COLD |
+--------------------------------------------+---------------------------------------------+--------+
感想
- 細かい準備が不要で、自己完結的なテストをすぐに試せるのが素晴らしい。
- 攻撃テクニックの実行に対して、既存の検知の仕組みがどのように動作するか(あるいはしないのか)を1対1で確認可能。
- SRTの攻撃テクニックの説明には、その攻撃を実行するのに必要な権限も記載されているので、対策の具体化に活かしやすい。
- 今回試した攻撃テクニックは、状況によっては正当な操作・不正な操作のどちらもあり得る内容のため、CSPMのようなコンプライアンス型の対策ではカバーされない。
- CSPMで検知できる攻撃テクニックもSRTで用意されている。例: Open Ingress Port 22 on a Security Group
- その権限を用いた操作を検知できる監視の仕組みが必要だが、それが不正な操作なのか正当な操作なのか区別できる運用面の考慮することで、より精度の高い検知が可能になる。
- 今回試した攻撃テクニックは、状況によっては正当な操作・不正な操作のどちらもあり得る内容のため、CSPMのようなコンプライアンス型の対策ではカバーされない。
くれぐれもご注意
- SRTでは、攻撃対象のクラウドリソースを自分で作成して、自分で攻撃する動きとなるため、そのクラウドアカウントを複数ユーザで共有している場合は要注意。
- CloudTrailなどアカウント内のクラウドリソースの操作に対して監視の仕組みを入れていたりすると、迷惑をかけてしまう可能性あり。