AWS Route 53 Resolver と Transit Gateway を利用して、複数の AWS VPC が異なる AWS アカウントで管理されている場合、VPC 間の名前解決には Amazon Route 53 Resolver が便利です。
1.CloudFormationによるVPC,Transit Gatewayの作成#
| リージョン | vpc |
|---|---|
| リージョン1 | vpc-A |
| リージョン2 | vpc-BC |
{
"AWSTemplateFormatVersion": "2010-09-09",
"Description": "Hands-On AWS Transit Gateway with Amazon Route 53 Resolver: Creates a Virginia VPC-A and Transit Gateway then check your TGW id for the other TGW Attachements.",
"Outputs": {
"VirginiaTGWId": {
"Value": {
"Ref": "VirginiaTGW"
}
},
"vpcAId": {
"Value": {
"Ref": "VPCA"
}
},
"vpcACIDRRange": {
"Value": {
"Ref": "vpcACIDRRange"
}
},
"vpcAInstanceId": {
"Value": {
"Ref": "vpcAInstance"
}
}
},
"Parameters": {
"Ec2ImageId": {
"Type": "AWS::SSM::Parameter::Value<String>",
"Default": "/aws/service/ami-amazon-linux-latest/amzn2-ami-hvm-x86_64-gp2"
},
"vpcACIDRRange": {
"Description": "The IP address range for your new VPC-A.",
"Type": "String",
"MinLength": "9",
"MaxLength": "18",
"Default": "192.168.0.0/16",
"AllowedPattern": "(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})/(\\d{1,2})",
"ConstraintDescription": "must be a valid IP CIDR range of the form x.x.x.x/x."
},
"vpcAEC2PublicSubnetCIDRRange": {
"Description": "The IP address range for a subnet in VPC-A.",
"Type": "String",
"MinLength": "9",
"MaxLength": "18",
"Default": "192.168.1.0/24",
"AllowedPattern": "(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})/(\\d{1,2})",
"ConstraintDescription": "must be a valid IP CIDR range of the form x.x.x.x/x."
},
"vpcAEC2PrivateSubnetCIDRRange": {
"Description": "The IP address range for a subnet in VPC-A.",
"Type": "String",
"MinLength": "9",
"MaxLength": "18",
"Default": "192.168.0.0/24",
"AllowedPattern": "(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})/(\\d{1,2})",
"ConstraintDescription": "must be a valid IP CIDR range of the form x.x.x.x/x."
}
},
"Resources": {
"AttachGateway": {
"Type": "AWS::EC2::VPCGatewayAttachment",
"Properties": {
"VpcId": {
"Ref": "VPCA"
},
"InternetGatewayId": {
"Ref": "myInternetGateway"
}
}
},
"EIP": {
"Type": "AWS::EC2::EIP",
"Properties": {
"Domain": "VPCA"
}
},
"IAMIP3UK0E": {
"Type": "AWS::IAM::InstanceProfile",
"Properties": {
"Path": "/",
"Roles": [
{
"Ref": "IAMR3XJT6"
}
]
}
},
"IAMR3XJT6": {
"Type": "AWS::IAM::Role",
"Properties": {
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": [
"ec2.amazonaws.com"
]
},
"Action": [
"sts:AssumeRole"
]
}
]
},
"ManagedPolicyArns": [
"arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore"
],
"Path": "/"
}
},
"myInternetGateway": {
"Type": "AWS::EC2::InternetGateway"
},
"NAT": {
"Type": "AWS::EC2::NatGateway",
"Properties": {
"AllocationId": {
"Fn::GetAtt": [
"EIP",
"AllocationId"
]
},
"SubnetId": {
"Ref": "vpcAPublicSubnet"
},
"Tags": [
{
"Key": "Name",
"Value": "VPCA-NatGw"
}
]
}
},
"PrivateRoute": {
"Type": "AWS::EC2::Route",
"Properties": {
"RouteTableId": {
"Ref": "vpcAPrivateRouteTable"
},
"DestinationCidrBlock": "0.0.0.0/0",
"NatGatewayId": {
"Ref": "NAT"
}
}
},
"PrivateRoute10": {
"Type": "AWS::EC2::Route",
"DependsOn": "VirginiaTGWvpcAattach",
"Properties": {
"RouteTableId": {
"Ref": "vpcAPrivateRouteTable"
},
"DestinationCidrBlock": "10.0.0.0/16",
"TransitGatewayId": {
"Ref": "VirginiaTGW"
}
}
},
"PrivateRoute172": {
"Type": "AWS::EC2::Route",
"DependsOn": "VirginiaTGWvpcAattach",
"Properties": {
"RouteTableId": {
"Ref": "vpcAPrivateRouteTable"
},
"DestinationCidrBlock": "172.16.0.0/16",
"TransitGatewayId": {
"Ref": "VirginiaTGW"
}
}
},
"PrivateSubnetRouteTableAssociation": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"SubnetId": {
"Ref": "vpcAPrivateSubnet"
},
"RouteTableId": {
"Ref": "vpcAPrivateRouteTable"
}
}
},
"PublicSubnetRouteTableAssociation": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"SubnetId": {
"Ref": "vpcAPublicSubnet"
},
"RouteTableId": {
"Ref": "vpcAPublicRouteTable"
}
}
},
"Route": {
"Type": "AWS::EC2::Route",
"DependsOn": "AttachGateway",
"Properties": {
"RouteTableId": {
"Ref": "vpcAPublicRouteTable"
},
"DestinationCidrBlock": "0.0.0.0/0",
"GatewayId": {
"Ref": "myInternetGateway"
}
}
},
"VirginiaTGW": {
"Type": "AWS::EC2::TransitGateway",
"Properties": {
"AmazonSideAsn": "64512",
"AutoAcceptSharedAttachments": "enable",
"DefaultRouteTableAssociation": "enable",
"DefaultRouteTablePropagation": "enable",
"Description": "Virginia-TGW-ASN-64512",
"DnsSupport": "enable",
"Tags": [
{
"Key": "Name",
"Value": "VirginiaTGW"
}
],
"VpnEcmpSupport": "disable"
}
},
"VirginiaTGWvpcAattach": {
"Type": "AWS::EC2::TransitGatewayAttachment",
"Properties": {
"SubnetIds": [
{
"Ref": "vpcAPrivateSubnet"
}
],
"Tags": [
{
"Key": "Name",
"Value": "Virginia-TGW-VPC-A-Attachement"
}
],
"TransitGatewayId": {
"Ref": "VirginiaTGW"
},
"VpcId": {
"Ref": "VPCA"
}
}
},
"VPCA": {
"Type": "AWS::EC2::VPC",
"Properties": {
"CidrBlock": {
"Ref": "vpcACIDRRange"
},
"EnableDnsSupport": true,
"EnableDnsHostnames": true,
"InstanceTenancy": "default",
"Tags": [
{
"Key": "Name",
"Value": "VPCA"
}
]
}
},
"vpcAEC2SecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Public instance security group",
"VpcId": {
"Ref": "VPCA"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": 8,
"ToPort": -1,
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "udp",
"FromPort": "33434",
"ToPort": "33523",
"CidrIp": "0.0.0.0/0"
}
]
}
},
"vpcAInstance": {
"Type": "AWS::EC2::Instance",
"Properties": {
"IamInstanceProfile": {
"Ref": "IAMIP3UK0E"
},
"ImageId": {
"Ref": "Ec2ImageId"
},
"InstanceType": "t2.micro",
"PrivateIpAddress": "192.168.0.10",
"SecurityGroupIds": [
{
"Ref": "vpcAEC2SecurityGroup"
}
],
"SubnetId": {
"Ref": "vpcAPrivateSubnet"
},
"Tags": [
{
"Key": "Name",
"Value": "vpcAInstance"
}
]
}
},
"vpcAPrivateRouteTable": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "VPCA"
},
"Tags": [
{
"Key": "Name",
"Value": "vpcAPrivateRouteTable"
}
]
}
},
"vpcAPrivateSubnet": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"CidrBlock": {
"Ref": "vpcAEC2PrivateSubnetCIDRRange"
},
"VpcId": {
"Ref": "VPCA"
},
"AvailabilityZone": "us-east-1a",
"Tags": [
{
"Key": "Name",
"Value": "vpcAPrivateSubnet"
}
]
}
},
"vpcAPublicRouteTable": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "VPCA"
},
"Tags": [
{
"Key": "Name",
"Value": "vpcAPublicRouteTable"
}
]
}
},
"vpcAPublicSubnet": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"CidrBlock": {
"Ref": "vpcAEC2PublicSubnetCIDRRange"
},
"VpcId": {
"Ref": "VPCA"
},
"AvailabilityZone": "us-east-1a",
"Tags": [
{
"Key": "Name",
"Value": "vpcAPublicSubnet"
}
]
}
}
}
}
{
"AWSTemplateFormatVersion": "2010-09-09",
"Description": "Hands-On AWS Transit Gateway with Amazon Route 53 Resolver: Creates Oregon VPC-B/C and then creates a Transit Gateway, Attache with an existing VPC that you specify.",
"Outputs": {
"vpcBInstanceId": {
"Value": {
"Ref": "vpcBInstance"
}
},
"vpcCInstanceId": {
"Value": {
"Ref": "vpcCInstance"
}
},
"vpcCId": {
"Value": {
"Ref": "VPCC"
}
}
},
"Parameters": {
"Ec2ImageId": {
"Type": "AWS::SSM::Parameter::Value<String>",
"Default": "/aws/service/ami-amazon-linux-latest/amzn2-ami-hvm-x86_64-gp2"
},
"vpcBCIDRRange": {
"Description": "The IP address range for your new VPC-B.",
"Type": "String",
"MinLength": "9",
"MaxLength": "18",
"Default": "10.0.0.0/16",
"AllowedPattern": "(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})/(\\d{1,2})",
"ConstraintDescription": "must be a valid IP CIDR range of the form x.x.x.x/x."
},
"vpcBEC2PublicSubnetCIDRRange": {
"Description": "The IP address range for a subnet in VPC-B.",
"Type": "String",
"MinLength": "9",
"MaxLength": "18",
"Default": "10.0.1.0/24",
"AllowedPattern": "(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})/(\\d{1,2})",
"ConstraintDescription": "must be a valid IP CIDR range of the form x.x.x.x/x."
},
"vpcBEC2PrivateSubnetCIDRRange": {
"Description": "The IP address range for a subnet in VPC-B.",
"Type": "String",
"MinLength": "9",
"MaxLength": "18",
"Default": "10.0.0.0/24",
"AllowedPattern": "(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})/(\\d{1,2})",
"ConstraintDescription": "must be a valid IP CIDR range of the form x.x.x.x/x."
},
"vpcCCIDRRange": {
"Description": "The IP address range for your new VPC-C.",
"Type": "String",
"MinLength": "9",
"MaxLength": "18",
"Default": "172.16.0.0/16",
"AllowedPattern": "(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})/(\\d{1,2})",
"ConstraintDescription": "must be a valid IP CIDR range of the form x.x.x.x/x."
},
"vpcCEC2PublicSubnetCIDRRange": {
"Description": "The IP address range for a subnet in VPC-C.",
"Type": "String",
"MinLength": "9",
"MaxLength": "18",
"Default": "172.16.1.0/24",
"AllowedPattern": "(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})/(\\d{1,2})",
"ConstraintDescription": "must be a valid IP CIDR range of the form x.x.x.x/x."
},
"vpcCEC2PrivateSubnetCIDRRange": {
"Description": "The IP address range for a subnet in VPC-C.",
"Type": "String",
"MinLength": "9",
"MaxLength": "18",
"Default": "172.16.0.0/24",
"AllowedPattern": "(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3})/(\\d{1,2})",
"ConstraintDescription": "must be a valid IP CIDR range of the form x.x.x.x/x."
}
},
"Resources": {
"EIPtoVpcBNat": {
"Type": "AWS::EC2::EIP",
"Properties": {
"Domain": "VPCB"
}
},
"EIPtoVpcCNat": {
"Type": "AWS::EC2::EIP",
"Properties": {
"Domain": "VPCB"
}
},
"IAMIP3UK0F": {
"Type": "AWS::IAM::InstanceProfile",
"Properties": {
"Path": "/",
"Roles": [
{
"Ref": "IAMR3XJT7"
}
]
}
},
"IAMR3XJT7": {
"Type": "AWS::IAM::Role",
"Properties": {
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": [
"ec2.amazonaws.com"
]
},
"Action": [
"sts:AssumeRole"
]
}
]
},
"ManagedPolicyArns": [
"arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore"
],
"Path": "/"
}
},
"OregonTGW": {
"Type": "AWS::EC2::TransitGateway",
"Properties": {
"AmazonSideAsn": "64513",
"AutoAcceptSharedAttachments": "enable",
"DefaultRouteTableAssociation": "enable",
"DefaultRouteTablePropagation": "enable",
"Description": "Oregon-TGW-ASN-64513",
"DnsSupport": "enable",
"Tags": [
{
"Key": "Name",
"Value": "OregonTGW"
}
],
"VpnEcmpSupport": "disable"
}
},
"OregonTGWvpcBattach": {
"Type": "AWS::EC2::TransitGatewayAttachment",
"Properties": {
"SubnetIds": [
{
"Ref": "vpcBPrivateSubnet"
}
],
"Tags": [
{
"Key": "Name",
"Value": "Oregon-TGW-VPC-B-Attachement"
}
],
"TransitGatewayId": {
"Ref": "OregonTGW"
},
"VpcId": {
"Ref": "VPCB"
}
}
},
"OregonTGWvpcCattach": {
"Type": "AWS::EC2::TransitGatewayAttachment",
"Properties": {
"SubnetIds": [
{
"Ref": "vpcCPrivateSubnet"
}
],
"Tags": [
{
"Key": "Name",
"Value": "Oregon-TGW-VPC-C-Attachement"
}
],
"TransitGatewayId": {
"Ref": "OregonTGW"
},
"VpcId": {
"Ref": "VPCC"
}
}
},
"PrivateSubnetBRouteTableAssociation": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"SubnetId": {
"Ref": "vpcBPrivateSubnet"
},
"RouteTableId": {
"Ref": "vpcBPrivateRouteTable"
}
}
},
"PrivateSubnetCRouteTableAssociation": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"SubnetId": {
"Ref": "vpcCPrivateSubnet"
},
"RouteTableId": {
"Ref": "vpcCPrivateRouteTable"
}
}
},
"PublicRouteVPCB": {
"Type": "AWS::EC2::Route",
"DependsOn": "vpcBAttachGateway",
"Properties": {
"RouteTableId": {
"Ref": "vpcBPublicRouteTable"
},
"DestinationCidrBlock": "0.0.0.0/0",
"GatewayId": {
"Ref": "vpcBInternetGateway"
}
}
},
"PublicRouteVPCC": {
"Type": "AWS::EC2::Route",
"DependsOn": "vpcCAttachGateway",
"Properties": {
"RouteTableId": {
"Ref": "vpcCPublicRouteTable"
},
"DestinationCidrBlock": "0.0.0.0/0",
"GatewayId": {
"Ref": "vpcCInternetGateway"
}
}
},
"PublicSubnetBRouteTableAssociation": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"SubnetId": {
"Ref": "vpcBPublicSubnet"
},
"RouteTableId": {
"Ref": "vpcBPublicRouteTable"
}
}
},
"PublicSubnetCRouteTableAssociation": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"SubnetId": {
"Ref": "vpcCPublicSubnet"
},
"RouteTableId": {
"Ref": "vpcCPublicRouteTable"
}
}
},
"VPCB": {
"Type": "AWS::EC2::VPC",
"Properties": {
"CidrBlock": {
"Ref": "vpcBCIDRRange"
},
"EnableDnsSupport": true,
"EnableDnsHostnames": true,
"InstanceTenancy": "default",
"Tags": [
{
"Key": "Name",
"Value": "VPCB"
}
]
}
},
"vpcBAttachGateway": {
"Type": "AWS::EC2::VPCGatewayAttachment",
"Properties": {
"VpcId": {
"Ref": "VPCB"
},
"InternetGatewayId": {
"Ref": "vpcBInternetGateway"
}
}
},
"vpcBEC2SecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Public instance security group",
"VpcId": {
"Ref": "VPCB"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": 8,
"ToPort": -1,
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "udp",
"FromPort": "33434",
"ToPort": "33523",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "udp",
"FromPort": "53",
"ToPort": "53",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "53",
"ToPort": "53",
"CidrIp": "0.0.0.0/0"
}
]
}
},
"vpcBInstance": {
"Type": "AWS::EC2::Instance",
"Properties": {
"IamInstanceProfile": {
"Ref": "IAMIP3UK0F"
},
"ImageId": {
"Ref": "Ec2ImageId"
},
"InstanceType": "t2.micro",
"PrivateIpAddress": "10.0.0.10",
"SecurityGroupIds": [
{
"Ref": "vpcBEC2SecurityGroup"
}
],
"SubnetId": {
"Ref": "vpcBPrivateSubnet"
},
"Tags": [
{
"Key": "Name",
"Value": "vpcBInstance"
}
]
}
},
"vpcBInternetGateway": {
"Type": "AWS::EC2::InternetGateway"
},
"vpcBNAT": {
"Type": "AWS::EC2::NatGateway",
"Properties": {
"AllocationId": {
"Fn::GetAtt": [
"EIPtoVpcBNat",
"AllocationId"
]
},
"SubnetId": {
"Ref": "vpcBPublicSubnet"
},
"Tags": [
{
"Key": "Name",
"Value": "VPCB-NatGw"
}
]
}
},
"vpcBPrivateRoute": {
"Type": "AWS::EC2::Route",
"Properties": {
"RouteTableId": {
"Ref": "vpcBPrivateRouteTable"
},
"DestinationCidrBlock": "0.0.0.0/0",
"NatGatewayId": {
"Ref": "vpcBNAT"
}
}
},
"vpcBPrivateRoute172": {
"Type": "AWS::EC2::Route",
"DependsOn": "OregonTGWvpcBattach",
"Properties": {
"RouteTableId": {
"Ref": "vpcBPrivateRouteTable"
},
"DestinationCidrBlock": "172.16.0.0/16",
"TransitGatewayId": {
"Ref": "OregonTGW"
}
}
},
"vpcBPrivateRoute192": {
"Type": "AWS::EC2::Route",
"DependsOn": "OregonTGWvpcBattach",
"Properties": {
"RouteTableId": {
"Ref": "vpcBPrivateRouteTable"
},
"DestinationCidrBlock": "192.168.0.0/16",
"TransitGatewayId": {
"Ref": "OregonTGW"
}
}
},
"vpcBPrivateRouteTable": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "VPCB"
},
"Tags": [
{
"Key": "Name",
"Value": "vpcBPrivateRouteTable"
}
]
}
},
"vpcBPrivateSubnet": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"VpcId": {
"Ref": "VPCB"
},
"CidrBlock": {
"Ref": "vpcBEC2PrivateSubnetCIDRRange"
},
"AvailabilityZone": "us-west-2a",
"Tags": [
{
"Key": "Name",
"Value": "vpcBPrivateSubnet"
}
]
}
},
"vpcBPublicRouteTable": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "VPCB"
},
"Tags": [
{
"Key": "Name",
"Value": "vpcBPublicRouteTable"
}
]
}
},
"vpcBPublicSubnet": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"VpcId": {
"Ref": "VPCB"
},
"CidrBlock": {
"Ref": "vpcBEC2PublicSubnetCIDRRange"
},
"AvailabilityZone": "us-west-2a",
"Tags": [
{
"Key": "Name",
"Value": "vpcBPublicSubnet"
}
]
}
},
"VPCC": {
"Type": "AWS::EC2::VPC",
"Properties": {
"CidrBlock": {
"Ref": "vpcCCIDRRange"
},
"EnableDnsSupport": true,
"EnableDnsHostnames": true,
"InstanceTenancy": "default",
"Tags": [
{
"Key": "Name",
"Value": "VPCC"
}
]
}
},
"vpcCAttachGateway": {
"Type": "AWS::EC2::VPCGatewayAttachment",
"Properties": {
"VpcId": {
"Ref": "VPCC"
},
"InternetGatewayId": {
"Ref": "vpcCInternetGateway"
}
}
},
"vpcCEC2SecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Public instance security group",
"VpcId": {
"Ref": "VPCC"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": 8,
"ToPort": -1,
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "udp",
"FromPort": "33434",
"ToPort": "33523",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "udp",
"FromPort": "53",
"ToPort": "53",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "53",
"ToPort": "53",
"CidrIp": "0.0.0.0/0"
}
]
}
},
"vpcCInstance": {
"Type": "AWS::EC2::Instance",
"Properties": {
"IamInstanceProfile": {
"Ref": "IAMIP3UK0F"
},
"ImageId": {
"Ref": "Ec2ImageId"
},
"InstanceType": "t2.micro",
"PrivateIpAddress": "172.16.0.10",
"SecurityGroupIds": [
{
"Ref": "vpcCEC2SecurityGroup"
}
],
"SubnetId": {
"Ref": "vpcCPrivateSubnet"
},
"Tags": [
{
"Key": "Name",
"Value": "vpcCInstance"
}
]
}
},
"vpcCInternetGateway": {
"Type": "AWS::EC2::InternetGateway"
},
"vpcCNAT": {
"Type": "AWS::EC2::NatGateway",
"Properties": {
"AllocationId": {
"Fn::GetAtt": [
"EIPtoVpcCNat",
"AllocationId"
]
},
"SubnetId": {
"Ref": "vpcCPublicSubnet"
},
"Tags": [
{
"Key": "Name",
"Value": "VPCC-NatGw"
}
]
}
},
"vpcCPrivateRoute": {
"Type": "AWS::EC2::Route",
"Properties": {
"RouteTableId": {
"Ref": "vpcCPrivateRouteTable"
},
"DestinationCidrBlock": "0.0.0.0/0",
"NatGatewayId": {
"Ref": "vpcCNAT"
}
}
},
"vpcCPrivateRoute10": {
"Type": "AWS::EC2::Route",
"DependsOn": "OregonTGWvpcCattach",
"Properties": {
"RouteTableId": {
"Ref": "vpcCPrivateRouteTable"
},
"DestinationCidrBlock": "10.0.0.0/16",
"TransitGatewayId": {
"Ref": "OregonTGW"
}
}
},
"vpcCPrivateRoute192": {
"Type": "AWS::EC2::Route",
"DependsOn": "OregonTGWvpcCattach",
"Properties": {
"RouteTableId": {
"Ref": "vpcCPrivateRouteTable"
},
"DestinationCidrBlock": "192.168.0.0/16",
"TransitGatewayId": {
"Ref": "OregonTGW"
}
}
},
"vpcCPrivateRouteTable": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "VPCC"
},
"Tags": [
{
"Key": "Name",
"Value": "vpcCPrivateRouteTable"
}
]
}
},
"vpcCPrivateSubnet": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"VpcId": {
"Ref": "VPCC"
},
"CidrBlock": {
"Ref": "vpcCEC2PrivateSubnetCIDRRange"
},
"AvailabilityZone": "us-west-2a",
"Tags": [
{
"Key": "Name",
"Value": "vpcCPrivateSubnet"
}
]
}
},
"vpcCPublicRouteTable": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "VPCC"
},
"Tags": [
{
"Key": "Name",
"Value": "vpcCPublicRouteTable"
}
]
}
},
"vpcCPublicSubnet": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"VpcId": {
"Ref": "VPCC"
},
"CidrBlock": {
"Ref": "vpcCEC2PublicSubnetCIDRRange"
},
"AvailabilityZone": "us-west-2a",
"Tags": [
{
"Key": "Name",
"Value": "vpcCPublicSubnet"
}
]
}
}
}
}
2.2つ Transit Gatewayに対 し、リージョン間ピアリングを行う#
「Create Transit Gateway 接続」から「Create Transit Gateway Attachment」
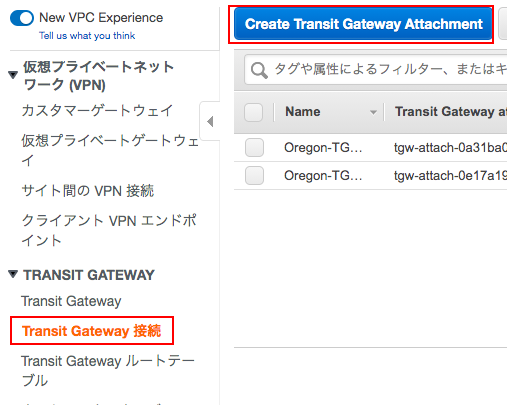
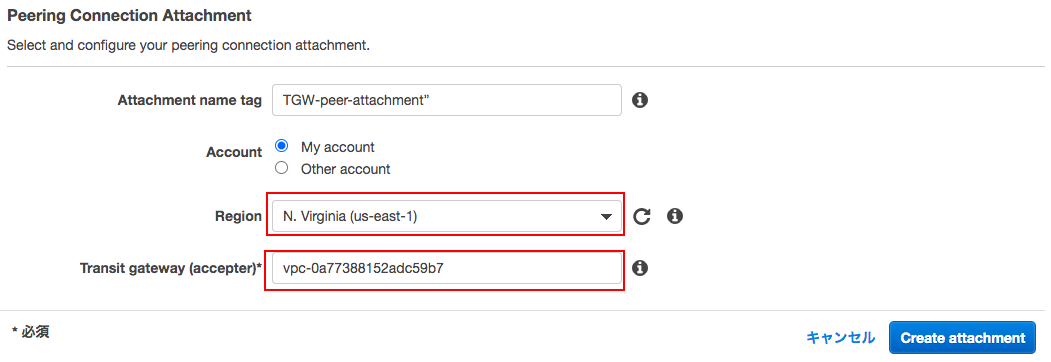
「Transit Gateway ID」を選択して、「Attachment type」には、「Peering Connection」を指定。
「Region」にvpcーAのもの、「Transit gateway (accepter)*」にvpc-AのTransit Gateway IDを入力。
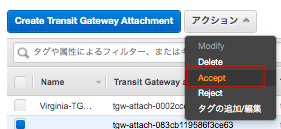
vpcーAのリージョンに移動し、承認作業「Accept」を行う。(数分間要します。)
承認されたら、peer-attachmentのアタッチメントが表示された状態で 、右のAssociated route tableに表示されたTransit Gateway Route TableのIDを開き、VPC-B(10.0.0.0/16)とVPC-C(172.16.0.0/16)への静的経路を追加する。
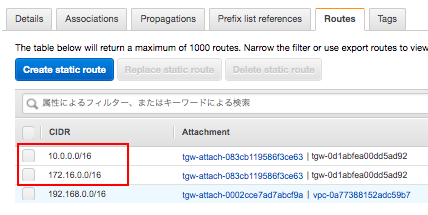
※もう片方のリージョンでも同様にVPC-A(192.168.0.0/16)への静的経路を追加する。
EC2にコンソール接続し、pingで疎通確認をしておく。
3.Route 53 プライベートホストゾーンとRoute 53 インバウンド Resolverの設定をする#
ドメイン名:example.jp プライベートゾーンでホストを作成する。
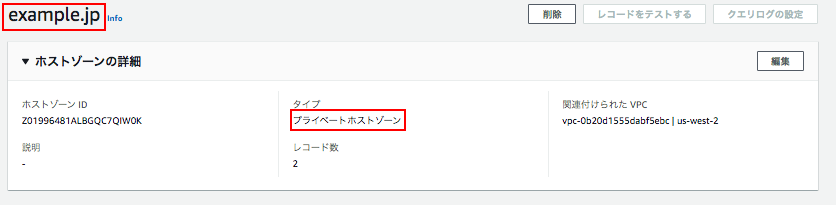
次にレコードを「シンプルルーティング」で作成する。今回でいうとvpc-cのホストに作成することとなる。
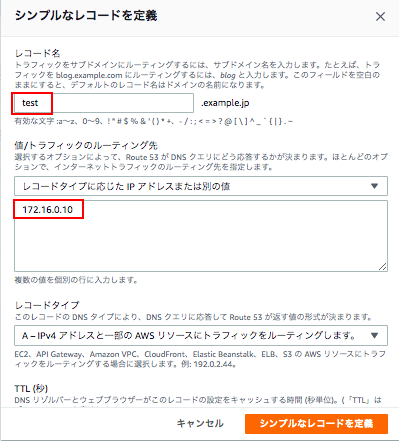
vpc-cのEC2にログインし、名前解決できているか確認する。
sh-4.2$ dig test.example.jp. +short
172.16.0.10
Route53でインバウンドエンドポイントを開き、エンドポイントを作成していく。
ステップ 1 エンドポイントの設定
インバウンドのみ:お使いのネットワークまたは別のVPCからVPCへのDNSクエリを許可するエンドポイントの設定。
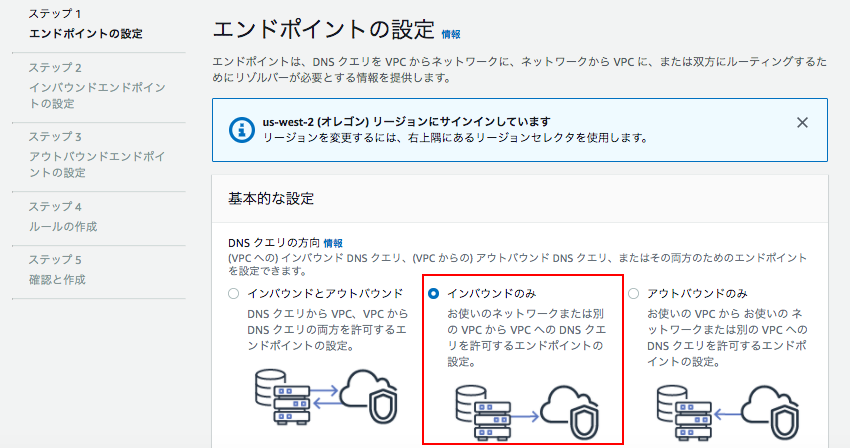
ステップ 2 インバウンドエンドポイントの設定
ここでは、「vpc-c」がエンドポイントとなるため、vpc-cの情報を入力する。
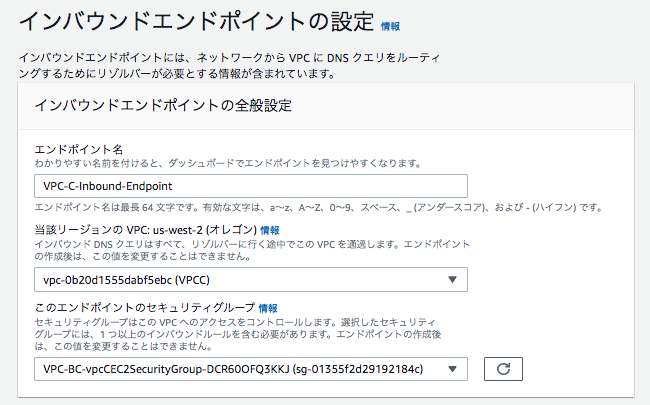
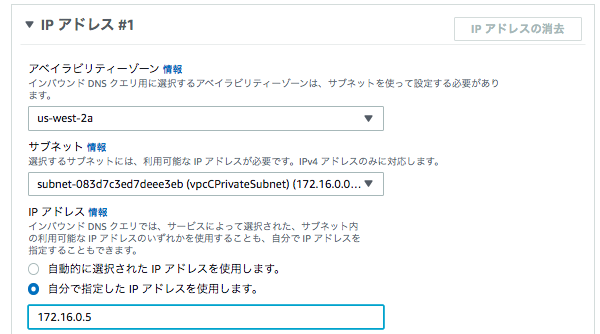
IPアドレス#1
サブネット:vpcCPrivateSubnet
IPアドレス:自分で指定 172.16.0.5
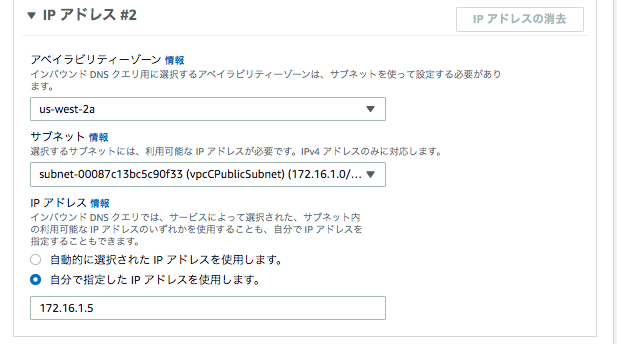
IPアドレス#2
サブネット:vpcCPublicSubnet
IPアドレス:自分で指定 172.16.1.5
他の情報はデフォルトで作成を完了させる。
4.VPCで参照用DNSを変更する#
最後にVPC-AとVPC-BにDHCPオプションセットを関連づけし、名前解決要求をVPC-CのRoute 53 Resolver Inbound Endpointへ振り向ける。
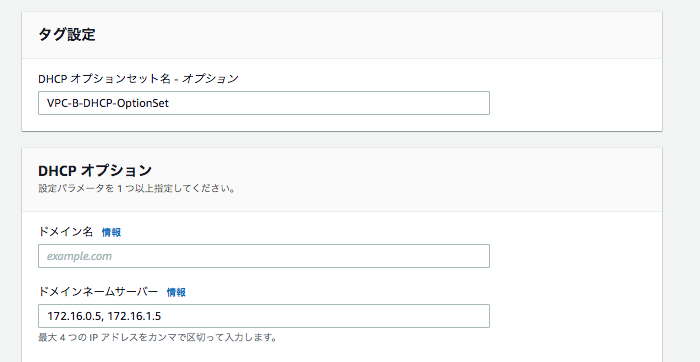
VPC-AとVPC-BにDHCPオプションセットをアタッチする。
各VPCから名前解決ができる事を確認します。
sh-4.2$ sudo service network restart
Restarting network (via systemctl): [ OK ]
sh-4.2$ cat /etc/resolv.conf
options timeout:2 attempts:5
; generated by /usr/sbin/dhclient-script
nameserver 172.16.0.5
nameserver 172.16.1.5
sh-4.2$ test.example.co.jp +short
172.16.0.10