導入
本記事は以下の続きとなります。未読の方はそちらを先にご確認ください。
この記事で得られること
- 攻撃の“前段階”でどんなことがなされているかの理解
- 主要OSINT/スキャンツール/サイトの実践的な使い方
⚠️ 注意(必読)
本コースで学ぶ技術は、悪用すると法的問題や社会的被害を生む可能性があります。学習・実験は必ず許可された環境(サンドボックス化された学習 VM など)で行ってください。無許可のハッキングは違法です。
🧭 第3章の概要
本章では、攻撃前段階にあたる「情報収集」と「脆弱性スキャン」について扱います。
攻撃者視点では「偵察」、防御者視点では「攻撃対象の特定・可視化」にあたる重要なフェーズです。
3章詳細:
- 受動的な情報収集(Passive Reconnaissance)(3.1章)👈本記事
- 能動的な情報収集(Active Reconnaissance)(3.2章)
- 脆弱性スキャンの実行(3.3章)
- スキャン結果の解析(3.4章)
能動的と受動的偵察の違いについて
偵察活動は「対象への関与度」で大きく2種類に分かれます。
| 種類 | 概要 | 主な手法 |
|---|---|---|
| 能動的偵察 | 攻撃者がターゲットと直接通信して情報を取得する | ホスト/ユーザ列挙、ポートスキャン、アプリ列挙、パケットクラフトなど |
| 受動的偵察 | 公開情報や既存データを分析して間接的に情報を取得する | OSINT、ドメイン列挙、パケット解析、盗聴など |
繰り返しにはなりますが、本記事では後者の能動的偵察の実践的なツールの使い方を学びます。
🔍 実践学習①:OSINTツールを使った情報収集
OSINTとは
OSINT(Open Source Intelligence)の略で、一般に公開された情報を収集・分析し、
意思決定の材料とする手法です。
典型的にはSNS、検索エンジン、公開リポジトリ、証明書情報などが対象となります。
実施ツール
- OSINT Framework
- WhatsMyName(ユーザー名列挙検索)
- SpiderFoot(自動OSINTスキャナー)
- Recon-ng(コマンドライン型偵察ツール)
SpiderFoot
200以上のモジュールを備えた自動スキャン型OSINTツール
受動的偵察に適しており、API経由のモジュール利用も可能
- 実践内容:
- SpiderFoot を CLI で起動し、ブラウザから管理画面にアクセスします。
┌──(kali㉿Kali)-[~] └─$ spiderfoot -l 127.0.0.1:5001 ************************************************************* Use SpiderFoot by starting your web browser of choice and browse to http://127.0.0.1:5001/ ************************************************************* 2025-09-08 09:30:46,977 [INFO] sf : Starting web server at 127.0.0.1:5001 ... 2025-09-08 09:30:46,986 [WARNING] sf : ******************************************************************** Warning: passwd file contains no passwords. Authentication disabled. Please consider adding authentication to protect this instance! Refer to https://www.spiderfoot.net/documentation/#security. ******************************************************************** -
New Scanからターゲット(ドメインやIPアドレス、メールアドレスなどを指定)と任意のスキャン名を設定し、使い方やモジュールといった単位からスキャンをする内容を選択
⚠️ 注意:アクティブスキャンを有効化すると、不正アクセスとみなされる場合があります。

- モジュールとは機能単位(プラグイン)のことで、spiderfootには200種類以上のモジュールが含まれています。

┌──(kali㉿Kali)-[~] └─$ spiderfoot -M sfp_abstractapi Look up domain, phone and IP address information from AbstractAPI. sfp_abusech Check if a host/domain, IP address or netblock is malicious according to Abuse.ch. sfp_abuseipdb Check if an IP address is malicious according to AbuseIPDB.com blacklist. sfp_abusix Check if a netblock or IP address is in the Abusix Mail Intelligence blacklist. sfp_accounts Look for possible associated accounts on nearly 200 websites like Ebay, Slashdot, reddit, etc. sfp_adblock Check if linked pages would be blocked by AdBlock Plus. 2025-09-08 09:56:39,342 [INFO] sf : Modules available: sfp_adguard_dns Check if a host would be blocked by AdGuard DNS. sfp_ahmia Search Tor 'Ahmia' search engine for mentions of the target. sfp_alienvault Obtain information from AlienVault Open Threat Exchange (OTX) sfp_alienvaultiprep Check if an IP or netblock is malicious according to the AlienVault IP Reputation database. sfp_apple_itunes Search Apple iTunes for mobile apps. sfp_archiveorg Identifies historic versions of interesting files/pages from the Wayback Machine. sfp_arin Queries ARIN registry for contact information. sfp_azureblobstorage Search for potential Azure blobs associated with the target and attempt to list their contents. sfp_badpackets Obtain information about any malicious activities involving IP addresses found sfp_base64 Identify Base64-encoded strings in URLs, often revealing interesting hidden information. sfp_bgpview Obtain network information from BGPView API. sfp_binaryedge Obtain information from BinaryEdge.io Internet scanning systems, including breaches, vulnerabilities, torrents and passive DNS. sfp_bingsearch Obtain information from bing to identify sub-domains and links. sfp_bingsharedip Search Bing for hosts sharing the same IP. ~~~省略~~~
- モジュールとは機能単位(プラグイン)のことで、spiderfootには200種類以上のモジュールが含まれています。
- 実行結果の確認(レポートとしても出力可能です。)
ここではh4cker.orgというドメインがドメインネームに限らずどこで利用されているかが表示されています。

- SpiderFoot を CLI で起動し、ブラウザから管理画面にアクセスします。
Recon-ng
Recon-ngはPythonベースのモジュール型偵察ツールで、CLIで操作します。
-
実践内容:
- Recon-ngの起動
┌──(kali㉿Kali)-[~] └─$ recon-ng [*] Version check disabled. _/_/_/ _/_/_/_/ _/_/_/ _/_/_/ _/ _/ _/ _/ _/_/_/ _/ _/ _/ _/ _/ _/ _/_/ _/ _/_/ _/ _/ _/_/_/ _/_/_/ _/ _/ _/ _/ _/ _/ _/_/_/_/ _/ _/ _/ _/ _/_/_/ _/ _/ _/ _/ _/ _/ _/ _/_/ _/ _/_/ _/ _/ _/ _/ _/_/_/_/ _/_/_/ _/_/_/ _/ _/ _/ _/ _/_/_/ /\ / \\ /\ Sponsored by... /\ /\/ \\V \/\ / \\/ // \\\\\ \\ \/\ // // BLACK HILLS \/ \\ www.blackhillsinfosec.com ____ ____ ____ ____ _____ _ ____ ____ ____ |____] | ___/ |____| | | | |____ |____ | | | \_ | | |____ | | ____| |____ |____ www.practisec.com [recon-ng v5.1.2, Tim Tomes (@lanmaster53)] [2] Recon modules [1] Discovery modules -
workspace単位で偵察内容などに応じて作業場所を分けて実行
- helpを使いながら進めると勝手がわかります。
- ここではundergroundというworkspaceを作って作業をしてます。
-
marketplaceからモジュールを導入
- 導入したときのログはありませんが、モジュールリストのログを残しておきます。
- 実行結果を表示
- 今回はhackertargetというHackerTarget.com APIで検索可能なホスト名探索のモジュールでhackxor.netという値を検索して7件ヒットしていることを確認してます。
- 同様の内容をbingモジュールでも実行していますが今回はヒットしてません。
[recon-ng][default] > workspaces list +-----------------------------------+ | Workspaces | Modified | +-----------------------------------+ | default | 2025-09-05 15:00:35 | | test | 2025-09-05 15:03:32 | | underground | 2025-09-05 15:38:53 | +-----------------------------------+ [recon-ng][default] > workspaces load underground [recon-ng][underground] > dashboard +----------------------------------------------------+ | Activity Summary | +----------------------------------------------------+ | Module | Runs | +----------------------------------------------------+ | discovery/info_disclosure/interesting_files | 1 | | recon/domains-hosts/bing_domain_web | 1 | | recon/domains-hosts/hackertarget | 1 | +----------------------------------------------------+ +----------------------------+ | Results Summary | +----------------------------+ | Category | Quantity | +----------------------------+ | Domains | 0 | | Companies | 0 | | Netblocks | 0 | | Locations | 0 | | Vulnerabilities | 0 | | Ports | 0 | | Hosts | 7 | | Contacts | 0 | | Credentials | 0 | | Leaks | 0 | | Pushpins | 0 | | Profiles | 0 | | Repositories | 0 | +----------------------------+ [recon-ng][underground] > marketplace search +--------------------------------------------------------------------------------------------------+ | Path | Version | Status | Updated | D | K | +--------------------------------------------------------------------------------------------------+ | discovery/info_disclosure/cache_snoop | 1.1 | not installed | 2020-10-13 | | | | discovery/info_disclosure/interesting_files | 1.2 | installed | 2021-10-04 | | | | exploitation/injection/command_injector | 1.0 | not installed | 2019-06-24 | | | | exploitation/injection/xpath_bruter | 1.2 | not installed | 2019-10-08 | | | | import/csv_file | 1.1 | not installed | 2019-08-09 | | | | import/list | 1.1 | not installed | 2019-06-24 | | | | import/masscan | 1.0 | not installed | 2020-04-07 | | | | import/nmap | 1.1 | not installed | 2020-10-06 | | | | recon/companies-contacts/bing_linkedin_cache | 1.0 | not installed | 2019-06-24 | | * | | recon/companies-contacts/censys_email_address | 2.1 | not installed | 2022-01-31 | * | * | | recon/companies-contacts/pen | 1.1 | not installed | 2019-10-15 | | | | recon/companies-domains/censys_subdomains | 2.1 | not installed | 2022-01-31 | * | * | | recon/companies-domains/pen | 1.1 | not installed | 2019-10-15 | | | | recon/companies-domains/viewdns_reverse_whois | 1.1 | not installed | 2021-08-24 | | | | recon/companies-domains/whoxy_dns | 1.1 | not installed | 2020-06-17 | | * | | recon/companies-multi/censys_org | 2.1 | not installed | 2022-01-31 | * | * | | recon/companies-multi/censys_tls_subjects | 2.1 | not installed | 2022-01-31 | * | * | | recon/companies-multi/github_miner | 1.1 | not installed | 2020-05-15 | | * | | recon/companies-multi/shodan_org | 1.1 | not installed | 2020-07-01 | * | * | | recon/companies-multi/whois_miner | 1.1 | not installed | 2019-10-15 | | | | recon/contacts-contacts/abc | 1.0 | not installed | 2019-10-11 | * | | | recon/contacts-contacts/mailtester | 1.0 | not installed | 2019-06-24 | | | | recon/contacts-contacts/mangle | 1.0 | not installed | 2019-06-24 | | | | recon/contacts-contacts/unmangle | 1.1 | not installed | 2019-10-27 | | | | recon/contacts-credentials/hibp_breach | 1.2 | not installed | 2019-09-10 | | * | | recon/contacts-credentials/hibp_paste | 1.1 | not installed | 2019-09-10 | | * | | recon/contacts-domains/censys_email_to_domains | 2.1 | not installed | 2022-01-31 | * | * | | recon/contacts-domains/migrate_contacts | 1.1 | not installed | 2020-05-17 | | | | recon/contacts-profiles/fullcontact | 1.1 | not installed | 2019-07-24 | | * | | recon/credentials-credentials/adobe | 1.0 | not installed | 2019-06-24 | | | | recon/credentials-credentials/bozocrack | 1.0 | not installed | 2019-06-24 | | | | recon/credentials-credentials/hashes_org | 1.0 | not installed | 2019-06-24 | | * | | recon/domains-companies/censys_companies | 2.1 | not installed | 2022-01-31 | * | * | | recon/domains-companies/pen | 1.1 | not installed | 2019-10-15 | | | | recon/domains-companies/whoxy_whois | 1.1 | not installed | 2020-06-24 | | * | | recon/domains-contacts/hunter_io | 1.3 | not installed | 2020-04-14 | | * | | recon/domains-contacts/metacrawler | 1.1 | not installed | 2019-06-24 | * | | | recon/domains-contacts/pen | 1.1 | not installed | 2019-10-15 | | | | recon/domains-contacts/pgp_search | 1.4 | not installed | 2019-10-16 | | | | recon/domains-contacts/whois_pocs | 1.0 | not installed | 2019-06-24 | | | | recon/domains-contacts/wikileaker | 1.0 | not installed | 2020-04-08 | | | | recon/domains-domains/brute_suffix | 1.1 | not installed | 2020-05-17 | | | | recon/domains-hosts/binaryedge | 1.2 | not installed | 2020-06-18 | | * | | recon/domains-hosts/bing_domain_api | 1.0 | not installed | 2019-06-24 | | * | | recon/domains-hosts/bing_domain_web | 1.1 | installed | 2019-07-04 | | | | recon/domains-hosts/brute_hosts | 1.0 | not installed | 2019-06-24 | | | | recon/domains-hosts/builtwith | 1.1 | not installed | 2021-08-24 | | * | | recon/domains-hosts/censys_domain | 2.1 | not installed | 2022-01-31 | * | * | | recon/domains-hosts/certificate_transparency | 1.3 | not installed | 2019-09-16 | | | | recon/domains-hosts/google_site_web | 1.0 | not installed | 2019-06-24 | | | | recon/domains-hosts/hackertarget | 1.1 | installed | 2020-05-17 | | | | recon/domains-hosts/mx_spf_ip | 1.0 | not installed | 2019-06-24 | | | | recon/domains-hosts/netcraft | 1.1 | not installed | 2020-02-05 | | | | recon/domains-hosts/shodan_hostname | 1.1 | not installed | 2020-07-01 | * | * | | recon/domains-hosts/spyse_subdomains | 1.1 | not installed | 2021-08-24 | | * | | recon/domains-hosts/ssl_san | 1.0 | not installed | 2019-06-24 | | | | recon/domains-hosts/threatcrowd | 1.0 | not installed | 2019-06-24 | | | | recon/domains-hosts/threatminer | 1.0 | not installed | 2019-06-24 | | | | recon/domains-vulnerabilities/ghdb | 1.1 | not installed | 2019-06-26 | | | | recon/domains-vulnerabilities/xssed | 1.1 | not installed | 2020-10-18 | | | | recon/hosts-domains/migrate_hosts | 1.1 | not installed | 2020-05-17 | | | | recon/hosts-hosts/bing_ip | 1.0 | not installed | 2019-06-24 | | * | | recon/hosts-hosts/censys_hostname | 2.1 | not installed | 2022-01-31 | * | * | | recon/hosts-hosts/censys_ip | 2.1 | not installed | 2022-01-31 | * | * | | recon/hosts-hosts/censys_query | 2.1 | not installed | 2022-01-31 | * | * | | recon/hosts-hosts/ipinfodb | 1.2 | not installed | 2021-08-24 | | * | | recon/hosts-hosts/ipstack | 1.0 | not installed | 2019-06-24 | | * | | recon/hosts-hosts/resolve | 1.0 | not installed | 2019-06-24 | | | | recon/hosts-hosts/reverse_resolve | 1.0 | not installed | 2019-06-24 | | | | recon/hosts-hosts/ssltools | 1.0 | not installed | 2019-06-24 | | | | recon/hosts-hosts/virustotal | 1.0 | not installed | 2019-06-24 | | * | | recon/hosts-locations/migrate_hosts | 1.0 | not installed | 2019-06-24 | | | | recon/hosts-ports/binaryedge | 1.0 | not installed | 2019-06-24 | | * | | recon/hosts-ports/shodan_ip | 1.2 | not installed | 2020-07-01 | * | * | | recon/locations-locations/geocode | 1.0 | not installed | 2019-06-24 | | * | | recon/locations-locations/reverse_geocode | 1.0 | not installed | 2019-06-24 | | * | | recon/locations-pushpins/flickr | 1.0 | not installed | 2019-06-24 | | * | | recon/locations-pushpins/shodan | 1.1 | not installed | 2020-07-07 | * | * | | recon/locations-pushpins/twitter | 1.1 | not installed | 2019-10-17 | | * | | recon/locations-pushpins/youtube | 1.2 | not installed | 2020-09-02 | | * | | recon/netblocks-companies/censys_netblock_company | 2.1 | not installed | 2022-01-31 | * | * | | recon/netblocks-companies/whois_orgs | 1.0 | not installed | 2019-06-24 | | | | recon/netblocks-hosts/censys_netblock | 2.1 | not installed | 2022-01-31 | * | * | | recon/netblocks-hosts/reverse_resolve | 1.0 | not installed | 2019-06-24 | | | | recon/netblocks-hosts/shodan_net | 1.2 | not installed | 2020-07-21 | * | * | | recon/netblocks-hosts/virustotal | 1.0 | not installed | 2019-06-24 | | * | | recon/netblocks-ports/census_2012 | 1.0 | not installed | 2019-06-24 | | | | recon/netblocks-ports/censysio | 1.0 | not installed | 2019-06-24 | | * | | recon/ports-hosts/migrate_ports | 1.0 | not installed | 2019-06-24 | | | | recon/ports-hosts/ssl_scan | 1.1 | not installed | 2021-08-24 | | | | recon/profiles-contacts/bing_linkedin_contacts | 1.2 | not installed | 2021-08-24 | | * | | recon/profiles-contacts/dev_diver | 1.1 | not installed | 2020-05-15 | | | | recon/profiles-contacts/github_users | 1.0 | not installed | 2019-06-24 | | * | | recon/profiles-profiles/namechk | 1.0 | not installed | 2019-06-24 | | * | | recon/profiles-profiles/profiler | 1.2 | not installed | 2023-12-30 | | | | recon/profiles-profiles/twitter_mentioned | 1.0 | not installed | 2019-06-24 | | * | | recon/profiles-profiles/twitter_mentions | 1.0 | not installed | 2019-06-24 | | * | | recon/profiles-repositories/github_repos | 1.1 | not installed | 2020-05-15 | | * | | recon/repositories-profiles/github_commits | 1.0 | not installed | 2019-06-24 | | * | | recon/repositories-vulnerabilities/gists_search | 1.0 | not installed | 2019-06-24 | | | | recon/repositories-vulnerabilities/github_dorks | 1.0 | not installed | 2019-06-24 | | * | | reporting/csv | 1.0 | not installed | 2019-06-24 | | | | reporting/html | 1.0 | not installed | 2019-06-24 | | | | reporting/json | 1.0 | not installed | 2019-06-24 | | | | reporting/list | 1.0 | not installed | 2019-06-24 | | | | reporting/proxifier | 1.0 | not installed | 2019-06-24 | | | | reporting/pushpin | 1.0 | not installed | 2019-06-24 | | * | | reporting/xlsx | 1.0 | not installed | 2019-06-24 | | | | reporting/xml | 1.1 | not installed | 2019-06-24 | | | +--------------------------------------------------------------------------------------------------+ D = Has dependencies. See info for details. K = Requires keys. See info for details. [recon-ng][underground] > modules load ha [recon-ng][underground][hackertarget] > info Name: HackerTarget Lookup Author: Michael Henriksen (@michenriksen) Version: 1.1 Description: Uses the HackerTarget.com API to find host names. Updates the 'hosts' table with the results. Options: Name Current Value Required Description ------ ------------- -------- ----------- SOURCE hackxor.net yes source of input (see 'info' for details) Source Options: default SELECT DISTINCT domain FROM domains WHERE domain IS NOT NULL <string> string representing a single input <path> path to a file containing a list of inputs query <sql> database query returning one column of inputs [recon-ng][underground][hackertarget] > run ----------- HACKXOR.NET ----------- [*] Country: None [*] Host: Host: research1.hackxor.net [*] Ip_Address: 138.68.117.124 [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- [*] Country: None [*] Host: dreaded.hackxor.net [*] Ip_Address: 138.68.117.124 [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- [*] Country: None [*] Host: hkrb.hackxor.net [*] Ip_Address: 138.68.117.124 [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- [*] Country: None [*] Host: hmrc.hackxor.net [*] Ip_Address: 138.68.117.124 [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- [*] Country: None [*] Host: intranet.hackxor.net [*] Ip_Address: 10.60.10.18 [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- [*] Country: None [*] Host: research1.hackxor.net [*] Ip_Address: 138.68.117.124 [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- [*] Country: None [*] Host: transparency.hackxor.net [*] Ip_Address: 138.68.117.124 [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- ------- SUMMARY ------- [*] 7 total (0 new) hosts found. [recon-ng][underground][hackertarget] > [recon-ng][underground][hackertarget] > back [recon-ng][underground] > modules load bi [recon-ng][underground][bing_domain_web] > info Name: Bing Hostname Enumerator Author: Tim Tomes (@lanmaster53) Version: 1.1 Description: Harvests hosts from Bing.com by using the 'site' search operator. Updates the 'hosts' table with the results. Options: Name Current Value Required Description ------ ------------- -------- ----------- SOURCE hackxor.net yes source of input (see 'info' for details) Source Options: default SELECT DISTINCT domain FROM domains WHERE domain IS NOT NULL <string> string representing a single input <path> path to a file containing a list of inputs query <sql> database query returning one column of inputs [recon-ng][underground][bing_domain_web] > run ----------- HACKXOR.NET ----------- [*] URL: https://www.bing.com/search?first=0&q=domain%3Ahackxor.net [recon-ng][underground][bing_domain_web] >
- また、上記の実行結果についてはGUIでも確認可能で、recon-webでサービスを起動したのちに、ブラウザから確認する必要があります。
┌──(kali㉿Kali)-[~] └─$ recon-web ************************************************************************* * Welcome to Recon-web, the analytics and reporting engine for Recon-ng! * This is a web-based user interface. Open the URL below in your browser to begin. * Recon-web includes the Recon-API, which can be accessed via the `/api/` URL. ************************************************************************* [*] Marketplace disabled. [*] Version check disabled. * Workspace initialized: default WARNING: This is a development server. Do not use it in a production deployment. Use a production WSGI server instead. * Running on http://127.0.0.1:5000 Press CTRL+C to quit
- Recon-ngの起動
🌐 実践学習②:DNSルックアップとWhoisによる調査
DNS調査
汎用的なLinuxコマンドを使用して調査します。
-
nslookup:A/AAAA/NS/MX/TXTなど各種レコード確認 -
dig:詳細なDNS応答を取得可能 -
whois:ドメイン所有者、管理者連絡先、登録先情報を照会 -
実践内容:
- nslookupのオプションも含めた使い方を学習
- NSレコードを返答する方法
┌──(kali㉿Kali)-[~] └─$ nslookup > cisco.com Server: 10.0.2.3 Address: 10.0.2.3#53 Non-authoritative answer: Name: cisco.com Address: 72.163.4.185 Name: cisco.com Address: 2001:420:1101:1::185 > > set type=ns > cisco.com ;; communications error to 10.0.2.3#53: timed out Server: 10.0.2.3 Address: 10.0.2.3#53 Non-authoritative answer: cisco.com nameserver = ns1.cisco.com. cisco.com nameserver = ns2.cisco.com. cisco.com nameserver = a28-64.akam.net. cisco.com nameserver = ns3.cisco.com. cisco.com nameserver = a3-64.akam.net. -
nslookup 対象ドメイン 名前解決のサーバーアドレスと記載し、DNSサーバーを指定する方法┌──(kali㉿Kali)-[~] └─$ nslookup netacad.com 8.8.8.8 Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: Name: netacad.com Address: 34.225.28.71 Name: netacad.com Address: 3.214.84.64 -
type=anyと記載することでNSレコードにとどまらず、さまざまなレコード(AAAAレコード、MXレコード、TXTレコードなど)を表示する方法┌──(kali㉿Kali)-[~] └─$ nslookup > server 8.8.8.8 Default server: 8.8.8.8 Address: 8.8.8.8#53 > set type=any > netacad.com ;; Connection to 8.8.8.8#53(8.8.8.8) for netacad.com failed: timed out. Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: Name: netacad.com Address: 34.225.28.71 Name: netacad.com Address: 3.214.84.64 netacad.com nameserver = ns-1911.awsdns-46.co.uk. netacad.com nameserver = ns-240.awsdns-30.com. netacad.com nameserver = ns-748.awsdns-29.net. netacad.com nameserver = ns-1476.awsdns-56.org. netacad.com origin = ns-1476.awsdns-56.org mail addr = awsdns-hostmaster.amazon.com serial = 1 refresh = 7200 retry = 900 expire = 1209600 minimum = 86400 netacad.com mail exchanger = 20 alt2.aspmx.l.google.com. netacad.com mail exchanger = 30 aspmx2.googlemail.com. netacad.com mail exchanger = 20 alt1.aspmx.l.google.com. netacad.com mail exchanger = 30 aspmx3.googlemail.com. netacad.com mail exchanger = 10 aspmx.l.google.com. netacad.com text = "facebook-domain-verification=9a8xflw2lo4qxwm9cq3rk3d0etc8bu" netacad.com text = "google-site-verification=TxuIwljruI4G9oKaeL5KB7LvXjIRJg2vOiy8RKy02Ak" netacad.com text = "google-site-verification=g7CVgKXjcGaA02xXIzPksT9HPpA9_LY0_UabO_DRTgc" netacad.com text = "5c9ty312qzlq7yyvly7mmk11nrfpp6kn" netacad.com text = "v=spf1 include:_spf.google.com include:amazonses.com ~all" netacad.com text = "93hd7nffv5d7h3vbwrc14q6n5cjkjbc2" netacad.com text = "identrust_validate=GHH1lQD22HMNen8L8V2x96QqwXOWYA8Y7Tu58KT1JnGv" Authoritative answers can be found from:
- NSレコードを返答する方法
- whoisコマンドの実行
- コマンド自体はシンプルだが、ドメインの登録場所、技術及び管理担当者の連絡先情報、物理的な所在地が確認できハッキングの足掛かりとなることもある。
-
whois 代表IPアドレスと入力することでグローバルアドレスの範囲を確認することも可能。
┌──(kali㉿Kali)-[~] └─$ whois cisco.com Domain Name: CISCO.COM Registry Domain ID: 4987030_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.markmonitor.com Registrar URL: http://www.markmonitor.com Updated Date: 2025-04-13T10:06:28Z Creation Date: 1987-05-14T04:00:00Z Registry Expiry Date: 2026-05-15T04:00:00Z Registrar: MarkMonitor Inc. Registrar IANA ID: 292 Registrar Abuse Contact Email: abusecomplaints@markmonitor.com Registrar Abuse Contact Phone: +1.2086851750 Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited Domain Status: serverDeleteProhibited https://icann.org/epp#serverDeleteProhibited Domain Status: serverTransferProhibited https://icann.org/epp#serverTransferProhibited Domain Status: serverUpdateProhibited https://icann.org/epp#serverUpdateProhibited Name Server: A28-64.AKAM.NET Name Server: A3-64.AKAM.NET Name Server: NS1.CISCO.COM Name Server: NS2.CISCO.COM Name Server: NS3.CISCO.COM DNSSEC: unsigned URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/ >>> Last update of whois database: 2025-09-08T08:10:13Z <<< ┌──(kali㉿Kali)-[~] └─$ whois netacad.com Domain Name: NETACAD.COM Registry Domain ID: 2667618_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.markmonitor.com Registrar URL: http://www.markmonitor.com Updated Date: 2022-06-25T22:51:07Z Creation Date: 1998-12-07T05:00:00Z Registry Expiry Date: 2025-12-06T05:00:00Z Registrar: MarkMonitor Inc. Registrar IANA ID: 292 Registrar Abuse Contact Email: abusecomplaints@markmonitor.com Registrar Abuse Contact Phone: +1.2086851750 Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited Name Server: NS-1476.AWSDNS-56.ORG Name Server: NS-1911.AWSDNS-46.CO.UK Name Server: NS-240.AWSDNS-30.COM Name Server: NS-748.AWSDNS-29.NET DNSSEC: unsigned URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/ >>> Last update of whois database: 2025-09-08T08:10:26Z <<< ┌──(kali㉿Kali)-[~] └─$ whois 72.163.5.20 NetRange: 72.163.0.0 - 72.163.255.255 CIDR: 72.163.0.0/16 NetName: CISCO-GEN-7 NetHandle: NET-72-163-0-0-1 Parent: NET72 (NET-72-0-0-0-0) NetType: Direct Allocation OriginAS: Organization: CISCO SYSTEMS, INC. (CS-2831) RegDate: 2006-10-24 Updated: 2024-03-08 Comment: Geofeed https://www.cisco.com/web/automation/CiscoAS109_geoip.csv Ref: https://rdap.arin.net/registry/ip/72.163.0.0 OrgName: CISCO SYSTEMS, INC. OrgId: CS-2831 Address: 251 LITTLE FALLS DRIVE City: WILMINGTON StateProv: DE PostalCode: 19808 Country: US RegDate: 2023-06-07 Updated: 2024-02-16 Ref: https://rdap.arin.net/registry/entity/CS-2831 OrgNOCHandle: GATC-ARIN OrgNOCName: GIS ARIN Technical Contact OrgNOCPhone: +1-408-526-8888 OrgNOCEmail: arin-tech@cisco.com OrgNOCRef: https://rdap.arin.net/registry/entity/GATC-ARIN OrgAbuseHandle: CISCO6-ARIN OrgAbuseName: Cisco CSIRT OrgAbusePhone: +1-408-527-3227 OrgAbuseEmail: csirt-notify@cisco.com OrgAbuseRef: https://rdap.arin.net/registry/entity/CISCO6-ARIN OrgTechHandle: GATC-ARIN OrgTechName: GIS ARIN Technical Contact OrgTechPhone: +1-408-526-8888 OrgTechEmail: arin-tech@cisco.com OrgTechRef: https://rdap.arin.net/registry/entity/GATC-ARIN - digコマンドの実行
- デフォルトではAレコードのみ表示を確認
┌──(kali㉿Kali)-[~] └─$ dig cisco.com ; <<>> DiG 9.18.16-1-Debian <<>> cisco.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 5896 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;cisco.com. IN A ;; ANSWER SECTION: cisco.com. 1785 IN A 72.163.4.185 ;; Query time: 20 msec ;; SERVER: 10.0.2.3#53(10.0.2.3) (UDP) ;; WHEN: Mon Sep 08 08:32:34 UTC 2025 ;; MSG SIZE rcvd: 54 ┌──(kali㉿Kali)-[~] └─$ nslookup cisco.com Server: 10.0.2.3 Address: 10.0.2.3#53 Non-authoritative answer: Name: cisco.com Address: 72.163.4.185 Name: cisco.com Address: 2001:420:1101:1::185 ┌──(kali㉿Kali)-[~] └─$ dig cisco.com AAAA ; <<>> DiG 9.18.16-1-Debian <<>> cisco.com AAAA ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 33025 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;cisco.com. IN AAAA ;; ANSWER SECTION: cisco.com. 972 IN AAAA 2001:420:1101:1::185 ;; Query time: 8 msec ;; SERVER: 10.0.2.3#53(10.0.2.3) (UDP) ;; WHEN: Mon Sep 08 09:11:00 UTC 2025 ;; MSG SIZE rcvd: 66 - digもnslookup同様DNSサーバーを任意に変更可能で問い合わせレコードも変更可能
┌──(kali㉿Kali)-[~] └─$ dig cisco.com 8.8.8.8 ns ; <<>> DiG 9.18.16-1-Debian <<>> cisco.com 8.8.8.8 ns ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38902 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;cisco.com. IN A ;; ANSWER SECTION: cisco.com. 913 IN A 72.163.4.185 ;; Query time: 8 msec ;; SERVER: 10.0.2.3#53(10.0.2.3) (UDP) ;; WHEN: Mon Sep 08 09:13:55 UTC 2025 ;; MSG SIZE rcvd: 54 ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 39540 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;8.8.8.8. IN NS ;; AUTHORITY SECTION: . 86399 IN SOA a.root-servers.net. nstld.verisign-grs.com. 2025090800 1800 900 604800 86400 ;; Query time: 16 msec ;; SERVER: 10.0.2.3#53(10.0.2.3) (UDP) ;; WHEN: Mon Sep 08 09:13:55 UTC 2025 ;; MSG SIZE rcvd: 111 ┌──(kali㉿Kali)-[~] └─$ dig netacad.com any ; <<>> DiG 9.18.16-1-Debian <<>> netacad.com any ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 46521 ;; flags: qr rd ra; QUERY: 1, ANSWER: 19, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;netacad.com. IN ANY ;; ANSWER SECTION: netacad.com. 60 IN A 3.214.84.64 netacad.com. 60 IN A 34.225.28.71 netacad.com. 21600 IN NS ns-748.awsdns-29.net. netacad.com. 21600 IN NS ns-240.awsdns-30.com. netacad.com. 21600 IN NS ns-1476.awsdns-56.org. netacad.com. 21600 IN NS ns-1911.awsdns-46.co.uk. netacad.com. 900 IN SOA ns-1476.awsdns-56.org. awsdns-hostmaster.amazon.com. 1 7200 900 1209600 86400 netacad.com. 60 IN MX 20 alt2.aspmx.l.google.com. netacad.com. 60 IN MX 30 aspmx2.googlemail.com. netacad.com. 60 IN MX 20 alt1.aspmx.l.google.com. netacad.com. 60 IN MX 10 aspmx.l.google.com. netacad.com. 60 IN MX 30 aspmx3.googlemail.com. netacad.com. 60 IN TXT "google-site-verification=g7CVgKXjcGaA02xXIzPksT9HPpA9_LY0_UabO_DRTgc" netacad.com. 60 IN TXT "93hd7nffv5d7h3vbwrc14q6n5cjkjbc2" netacad.com. 60 IN TXT "identrust_validate=GHH1lQD22HMNen8L8V2x96QqwXOWYA8Y7Tu58KT1JnGv" netacad.com. 60 IN TXT "v=spf1 include:_spf.google.com include:amazonses.com ~all" netacad.com. 60 IN TXT "google-site-verification=TxuIwljruI4G9oKaeL5KB7LvXjIRJg2vOiy8RKy02Ak" netacad.com. 60 IN TXT "5c9ty312qzlq7yyvly7mmk11nrfpp6kn" netacad.com. 60 IN TXT "facebook-domain-verification=9a8xflw2lo4qxwm9cq3rk3d0etc8bu" ;; Query time: 24 msec ;; SERVER: 10.0.2.3#53(10.0.2.3) (TCP) ;; WHEN: Mon Sep 08 09:14:20 UTC 2025 ;; MSG SIZE rcvd: 870 - DNSの逆引きも可能で、使い方としては通常のDNSルックアップ後に
whoisでアドレス範囲を確認し、確認したいアドレスに対して逆引きするといった使い方が主- nslookupでも同様のことが可能。
┌──(kali㉿Kali)-[~] └─$ dig -x 72.163.5.201 ; <<>> DiG 9.18.16-1-Debian <<>> -x 72.163.5.201 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23699 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;201.5.163.72.in-addr.arpa. IN PTR ;; ANSWER SECTION: 201.5.163.72.in-addr.arpa. 1800 IN PTR [ns1.cisco.com](http://ns1.cisco.com/). ;; Query time: 176 msec ;; SERVER: 10.0.2.3#53(10.0.2.3) (UDP) ;; WHEN: Mon Sep 08 09:18:10 UTC 2025 ;; MSG SIZE rcvd: 81 ┌──(kali㉿Kali)-[~] └─$ dig -x 72.163.1.1 ; <<>> DiG 9.18.16-1-Debian <<>> -x 72.163.1.1 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 62832 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;1.1.163.72.in-addr.arpa. IN PTR ;; ANSWER SECTION: 1.1.163.72.in-addr.arpa. 1800 IN PTR hsrp-72-163-1-1.cisco.com. ;; Query time: 148 msec ;; SERVER: 10.0.2.3#53(10.0.2.3) (UDP) ;; WHEN: Mon Sep 08 09:19:42 UTC 2025 ;; MSG SIZE rcvd: 91
- デフォルトではAレコードのみ表示を確認
- nslookupのオプションも含めた使い方を学習
🧑💻 実践学習③:SSL証明書・メタデータ・暗号情報の偵察
SSL証明書の調査
-
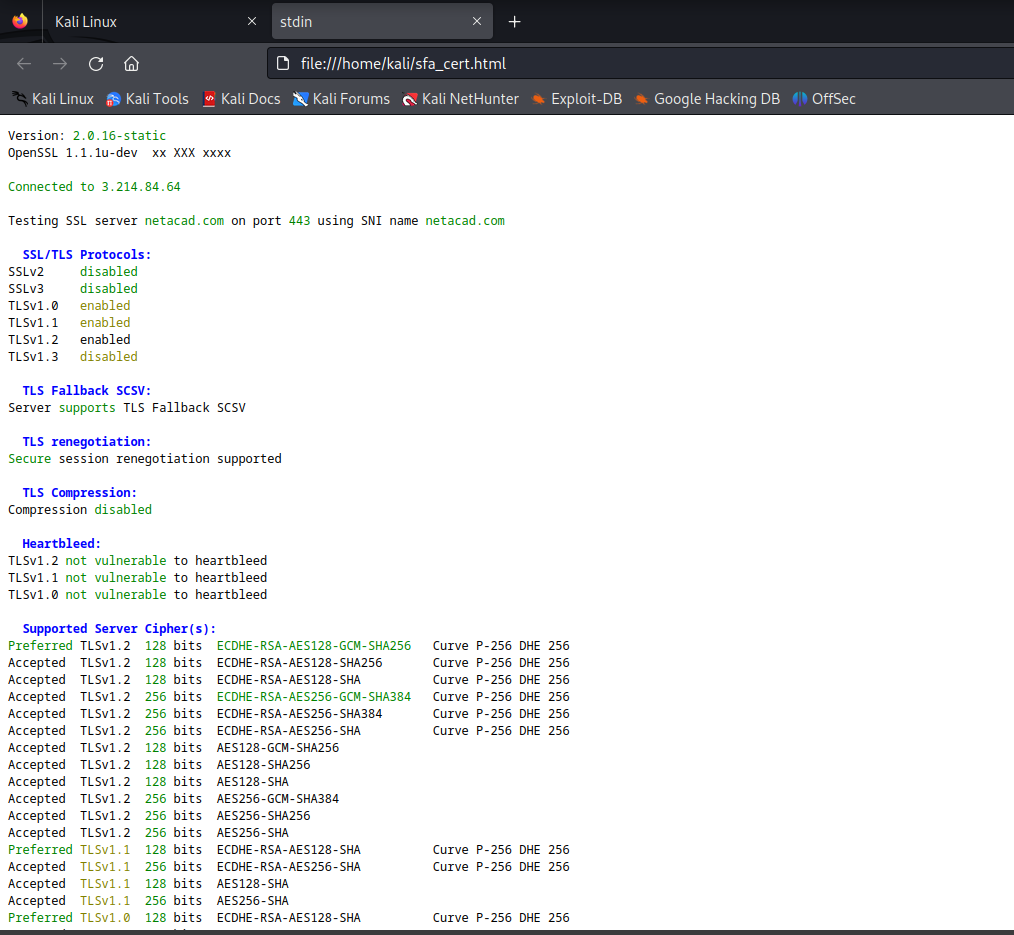
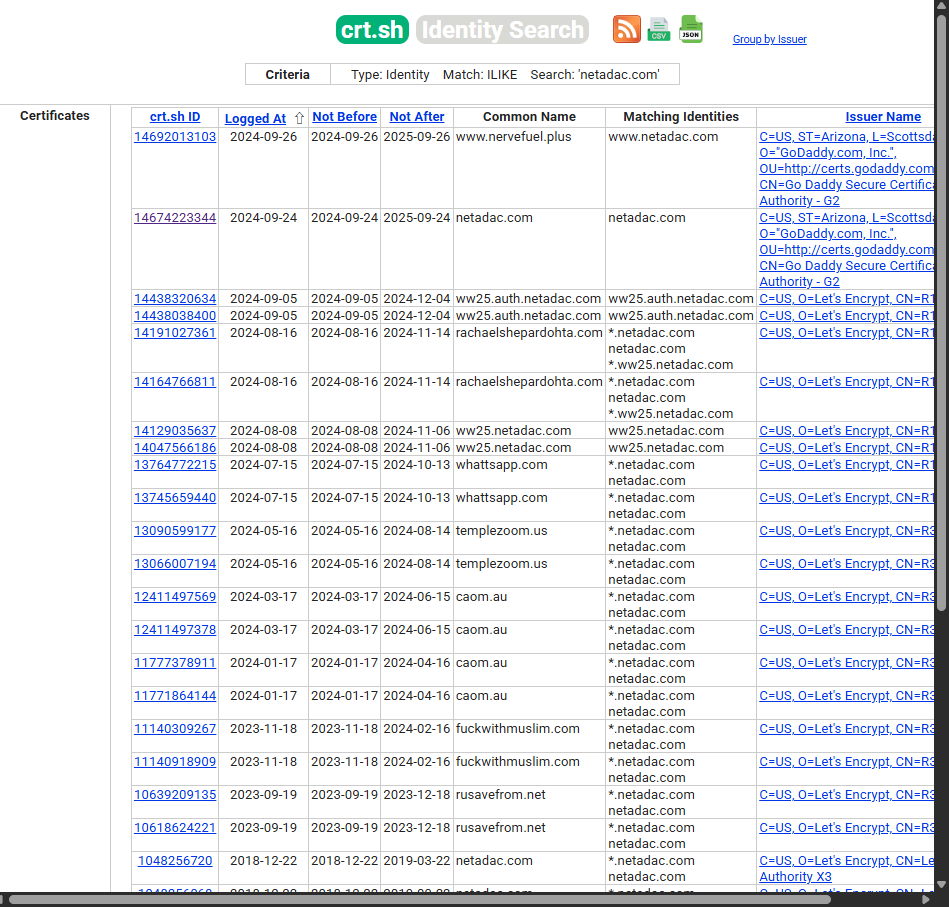
crt.sh でドメイン証明書を検索し、サブドメインや運用形態を推定(以下実行例)
-
ツールで確認する場合には
sslscan+ahaで証明書をHTMLレポート化- 実行ログとキャプチャ画面は以下の通り
┌──(kali㉿Kali)-[~] └─$ sslscan netacad.com Version: 2.0.16-static OpenSSL 1.1.1u-dev xx XXX xxxx Connected to 34.225.28.71 Testing SSL server netacad.com on port 443 using SNI name netacad.com SSL/TLS Protocols: SSLv2 disabled SSLv3 disabled TLSv1.0 enabled TLSv1.1 enabled TLSv1.2 enabled TLSv1.3 disabled TLS Fallback SCSV: Server supports TLS Fallback SCSV TLS renegotiation: Secure session renegotiation supported TLS Compression: Compression disabled Heartbleed: TLSv1.2 not vulnerable to heartbleed TLSv1.1 not vulnerable to heartbleed TLSv1.0 not vulnerable to heartbleed Supported Server Cipher(s): Preferred TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve P-256 DHE 256 Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA256 Curve P-256 DHE 256 Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256 Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-GCM-SHA384 Curve P-256 DHE 256 Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA384 Curve P-256 DHE 256 Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256 Accepted TLSv1.2 128 bits AES128-GCM-SHA256 Accepted TLSv1.2 128 bits AES128-SHA256 Accepted TLSv1.2 128 bits AES128-SHA Accepted TLSv1.2 256 bits AES256-GCM-SHA384 Accepted TLSv1.2 256 bits AES256-SHA256 Accepted TLSv1.2 256 bits AES256-SHA Preferred TLSv1.1 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256 Accepted TLSv1.1 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256 Accepted TLSv1.1 128 bits AES128-SHA Accepted TLSv1.1 256 bits AES256-SHA Preferred TLSv1.0 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256 Accepted TLSv1.0 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256 Accepted TLSv1.0 128 bits AES128-SHA Accepted TLSv1.0 256 bits AES256-SHA Server Key Exchange Group(s): TLSv1.2 128 bits secp256r1 (NIST P-256) TLSv1.2 192 bits secp384r1 (NIST P-384) TLSv1.2 260 bits secp521r1 (NIST P-521) SSL Certificate: Signature Algorithm: sha256WithRSAEncryption RSA Key Strength: 2048 Subject: netacad.com Altnames: DNS:netacad.com, DNS:*.netacad.com Issuer: Amazon RSA 2048 M02 Not valid before: Jan 4 00:00:00 2025 GMT Not valid after: Feb 2 23:59:59 2026 GMT ┌──(kali㉿Kali)-[~] └─$ sslscan netacad.com | aha > sfa_cert.html
🧩 パスワードダンプ・メタデータ・Google Dork
代表的な調査ツール:
| カテゴリ | ツール例 |
|---|---|
| パスワード漏洩探索 | h8mail, WhatBreach, LeakLooker, Buster, Scavenger, PwnDB |
| メタデータ解析 | ExifTool |
| 戦略的検索 | Google Dork + GHDB(Google Hacking Database) |
ExifToolによる解析例:
┌──(kali㉿Kali)-[~]
└─$ exiftool /home/kali/Downloads/000345_part.pdf
ExifTool Version Number : 12.64
File Name : 000345_part.pdf
Directory : /home/kali/Downloads
File Size : 299 kB
File Modification Date/Time : 2025:09:11 07:57:49+00:00
File Access Date/Time : 2025:09:11 08:01:53+00:00
File Inode Change Date/Time : 2025:09:11 07:57:49+00:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.7
Linearized : No
Page Count : 11
Language : ja-JP
XMP Toolkit : 3.1-701
Producer : Microsoft® PowerPoint® 2016
Creator Tool : Microsoft® PowerPoint® 2016
Create Date : 2020:07:19 18:18:59+09:00
Modify Date : 2020:07:19 18:18:59+09:00
Document ID : uuid:6FB5A1FE-AE0F-437A-8E7E-2DC81C4CA16E
Instance ID : uuid:6FB5A1FE-AE0F-437A-8E7E-2DC81C4CA16E
Creator : Microsoft® PowerPoint® 2016
※ディレクトリを指定したり、csvへの出力も可能
┌──(kali㉿Kali)-[~]
└─$ exiftool /home/kali/Downloads/
======== /home/kali/Downloads/000345_part.pdf
ExifTool Version Number : 12.64
File Name : 000345_part.pdf
Directory : /home/kali/Downloads
File Size : 299 kB
File Modification Date/Time : 2025:09:11 07:57:49+00:00
File Access Date/Time : 2025:09:11 08:01:53+00:00
File Inode Change Date/Time : 2025:09:11 07:57:49+00:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.7
Linearized : No
Page Count : 11
Language : ja-JP
XMP Toolkit : 3.1-701
Producer : Microsoft® PowerPoint® 2016
Creator Tool : Microsoft® PowerPoint® 2016
Create Date : 2020:07:19 18:18:59+09:00
Modify Date : 2020:07:19 18:18:59+09:00
Document ID : uuid:6FB5A1FE-AE0F-437A-8E7E-2DC81C4CA16E
Instance ID : uuid:6FB5A1FE-AE0F-437A-8E7E-2DC81C4CA16E
Creator : Microsoft® PowerPoint® 2016
======== /home/kali/Downloads/DLP.docx
ExifTool Version Number : 12.64
File Name : DLP.docx
Directory : /home/kali/Downloads
File Size : 95 kB
File Modification Date/Time : 2025:09:11 07:58:19+00:00
File Access Date/Time : 2025:09:11 08:02:31+00:00
File Inode Change Date/Time : 2025:09:11 07:58:19+00:00
File Permissions : -rw-r--r--
File Type : DOCX
File Type Extension : docx
MIME Type : application/vnd.openxmlformats-officedocument.wordprocessingml.document
Zip Required Version : 20
Zip Bit Flag : 0x0006
Zip Compression : Deflated
Zip Modify Date : 1980:01:01 00:00:00
Zip CRC : 0x17656e67
Zip Compressed Size : 486
Zip Uncompressed Size : 2259
Zip File Name : [Content_Types].xml
Template : Normal
Total Edit Time : 1 minute
Pages : 16
Words : 3137
Characters : 17882
Application : Microsoft Office Word
Doc Security : None
Lines : 149
Paragraphs : 41
Scale Crop : No
Heading Pairs : Title, 1
Titles Of Parts :
Company : Microsoft
Links Up To Date : No
Characters With Spaces : 20978
Shared Doc : No
Hyperlinks Changed : No
App Version : 14.0000
Creator : seepelom
Last Modified By : kamanga
Revision Number : 2
Last Printed : 2012:06:26 12:37:00Z
Create Date : 2015:10:02 07:20:00Z
Modify Date : 2015:10:02 07:20:00Z
1 directories scanned
2 image files read
┌──(kali㉿Kali)-[~]
└─$ exiftool -csv /home/kali/Downloads/ > /home/kali/Downloads/out.csv
1 directories scanned
3 image files read
Google Dork例:
"define('DB_USER'," "define('DB_PASSWORD'," ext:txt
⇒PHP設定ファイル内のDBユーザー・パスワード定義っを含むテキスト検索
db_password filetype:env
※ファイル拡張子 .env のファイルの中で db_password という文字列を含むものを探す
🧱 ウェブアーカイブ(Wayback Machine)
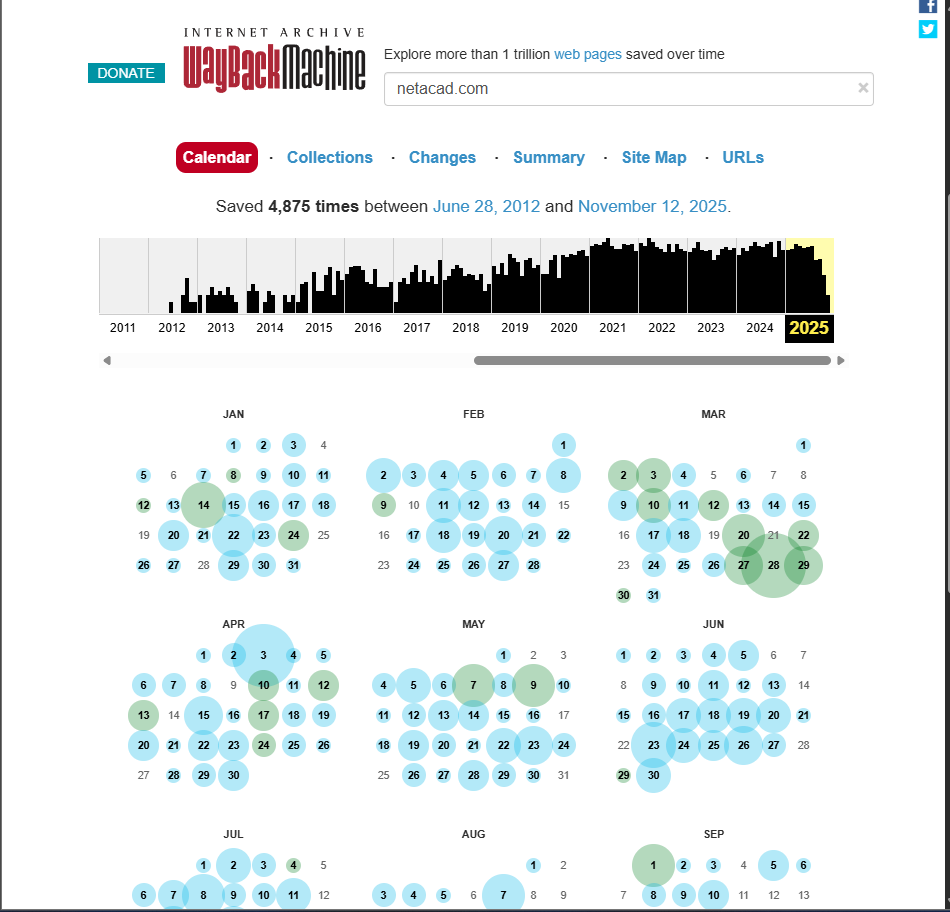
- archive.org/web で過去サイトの構造・ソースを閲覧可能
- 過去の構成ファイルや古いソフト構成から脆弱性を特定できる
- カレンダー表示・差分比較・サイトマップ探索などが可能
🌍 ShodanによるIoTスキャン
Shodanは、インターネット上のデバイス(IoT、Webカメラ、サーバなど)を検索できる専用検索エンジン。
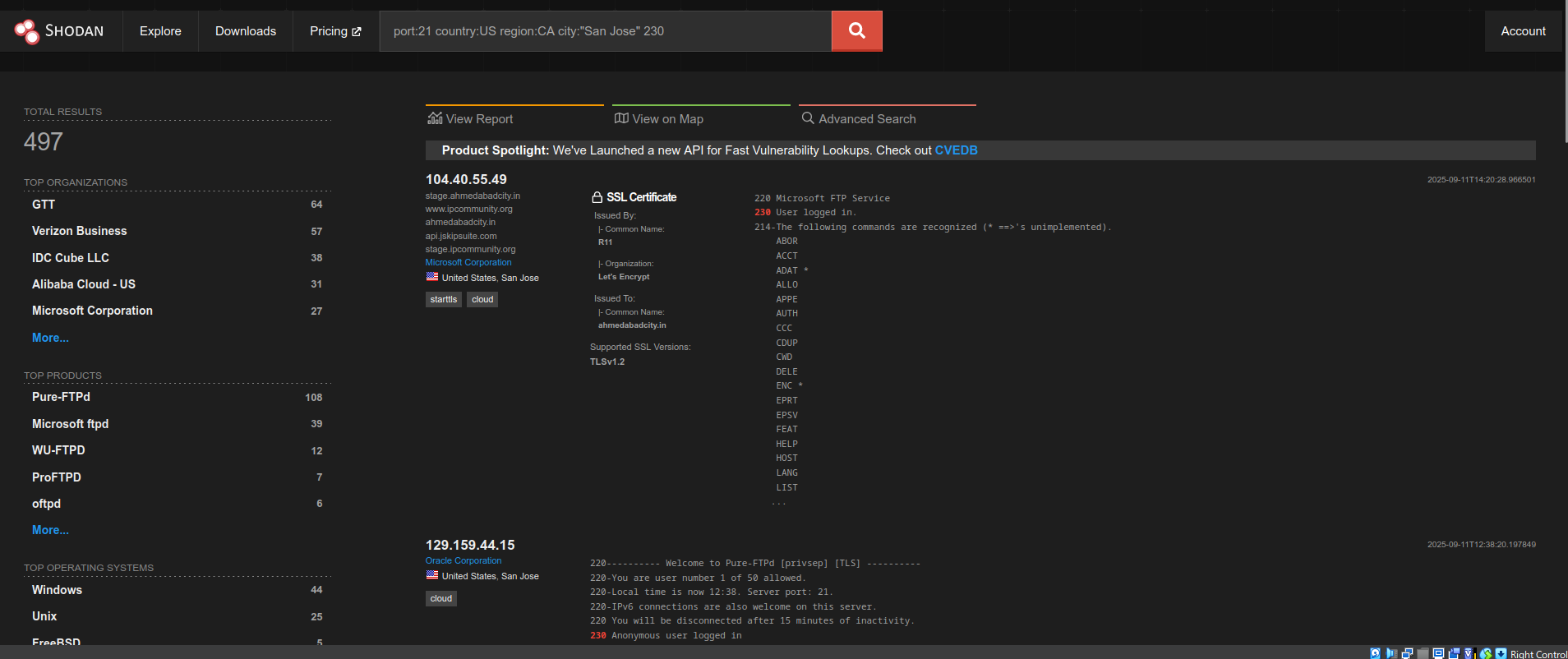
検索例:
port:21 country:US region:CA city:"San Jose" 230
※FTPのTCPポートで場所を限定し、FTPのログイン成功の応答コードを指定しての検索
出力結果では、匿名FTPサーバーや特定ベンダーの機器などを発見可能。
また、Honeypot検出やHTTP応答ヘッダの確認も容易(実行例は割愛)
有料機能も多いが、CLIでの実行も可能です。
┌──(kali㉿Kali)-[~]
└─$ shodan init /APIキー/
Successfully initialized
┌──(kali㉿Kali)-[~]
└─$ shodan search webcam
Error: Access denied (403 Forbidden)
※有料機能のため利用できませんでした。
┌──(kali㉿Kali)-[~]
└─$ shodan info
Query credits available: 0
Scan credits available: 0
┌──(kali㉿Kali)-[~]
└─$ shodan myip
/送信元IPが表示/
┌──(kali㉿Kali)-[~]
└─$ shodan stats webcam
Top 10 Results for Facet: country
US 871
CN 437
DE 331
GB 193
JP 159
SG 146
RU 112
KR 89
IT 88
FR 78
Top 10 Results for Facet: org
Linode 898
Aliyun Computing Co., LTD 318
Linode, LLC 177
139.162.0.0/16 139
Alibaba Cloud (Singapore) Private Limited 95
Deutsche Telekom AG 85
Hoster.KZ 69
Aliyun Computing Co.LTD 58
Kaopu Cloud HK Limited 53
Scaleway - Warsaw, Poland 50
🧾 本記事のまとめ
| 学習項目 | 目的 | 使用ツール |
|---|---|---|
| 受動的情報収集 | 公開情報からのインテリジェンス獲得 | OSINT Framework / SpiderFoot / Recon-ng |
| DNS・Whois調査 | ドメイン構成と所有者情報の把握 | nslookup / dig / whois |
| SSL証明書調査 | 証明書の脆弱性確認 | crt.sh / sslscan |
| メタデータ収集 | 文書や画像内の情報漏洩確認 | ExifTool |
| Dork検索 | 機密情報の誤公開チェック | GHDB / Google Dork |
| アーカイブ探索 | 過去構成や痕跡の確認 | Wayback Machine |
| IoT探索 | 公開デバイス・脆弱ホスト確認 | Shodan |
📍次回予告
→ 「能動的な情報収集」や「脆弱性スキャン(Nmapなど)」、「スキャン結果の分析」についてまとめる予定です。(文章量が多く、今回のように記事を分割する可能性があります。)
次の記事はこちら