前置き
【前回】vuls v0.5.0 を使ってみた!!(環境構築編)からの続きです。
そのため、vuls が実行できる環境がある前提です。
参考資料
Software Design 2017年10月号 で紹介されている内容をピックアップやってみています!
構成
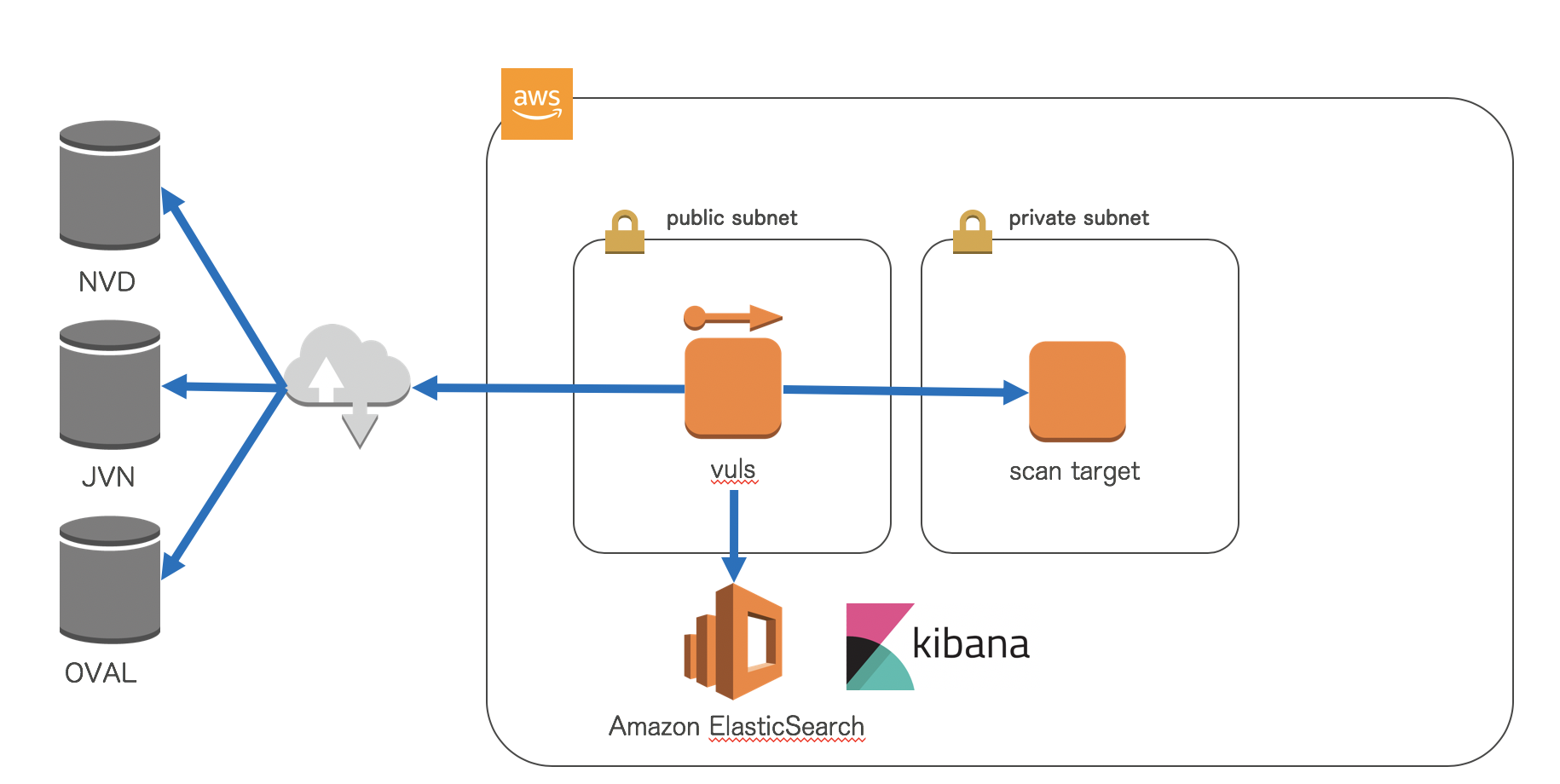
スキャン
[リモートスキャン設定]
1. vuls サーバで 鍵作成
[vuls サーバにて]
$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/centos/.ssh/id_rsa): [Enter]
Enter passphrase (empty for no passphrase): [Enter]
Enter same passphrase again: [Enter]
Your identification has been saved in /home/centos/.ssh/id_rsa.
Your public key has been saved in /home/centos/.ssh/id_rsa.pub.
2. scan target サーバへ鍵の配置
ここに、先ほど作成したkeyの内容を追記します。
[scan target サーバにて]
$ vi ~/.ssh/authorized_keys
3. vuls サーバから scan target サーバへ ssh でログイン
[vuls サーバにて]
$ ssh -l [ユーザ名] -i /home/centos/.ssh/id_rsa [scan target サーバ IPアドレス]
4. 設定ファイルの修正
[vuls サーバにて]
$ vi config.toml
[servers]
[servers.scan-target]
host = "scan target IPアドレス"
port = "22"
user = "ユーザ名"
keyPath = "/home/centos/.ssh/id_rsa"
scanMode = ["fast"]
[vuls サーバにて]
$ vuls configtest
[Aug 29 15:25:38] INFO [localhost] Validating config...
[Aug 29 15:25:38] INFO [localhost] Detecting Server/Container OS...
[Aug 29 15:25:38] INFO [localhost] Detecting OS of servers...
[Aug 29 15:25:39] INFO [localhost] (1/1) Detected: remote: centos 6.5
[Aug 29 15:25:39] INFO [localhost] Detecting OS of containers...
[Aug 29 15:25:39] INFO [localhost] Checking Scan Modes...
[Aug 29 15:25:39] INFO [localhost] Checking dependencies...
[Aug 29 15:25:39] ERROR [scan-target] yum-utils is not installed
[Aug 29 15:25:39] ERROR [localhost] Error: remote, err: [yum-utils is not installed]
[Aug 29 15:25:39] INFO [localhost] Checking sudo settings...
[Aug 29 15:25:39] INFO [localhost] It can be scanned with fast scan mode even if warn or err messages are displayed due to lack of dependent packages or sudo settings in fast-root or deep scan mode
[scat target サーバにて]
$ sudo yum install yum-utils
[vuls サーバにて]
$ vuls configtest
[Aug 29 15:54:19] INFO [localhost] Validating config...
[Aug 29 15:54:19] INFO [localhost] Detecting Server/Container OS...
[Aug 29 15:54:19] INFO [localhost] Detecting OS of servers...
[Aug 29 15:54:19] INFO [localhost] (1/1) Detected: scan-target: centos 6.5
[Aug 29 15:54:19] INFO [localhost] Detecting OS of containers...
[Aug 29 15:54:19] INFO [localhost] Checking Scan Modes...
[Aug 29 15:54:19] INFO [localhost] Checking dependencies...
[Aug 29 15:54:19] INFO [scan-target] Dependencies ... Pass
[Aug 29 15:54:19] INFO [localhost] Checking sudo settings...
[Aug 29 15:54:19] INFO [scan-target] Sudo... Pass
[Aug 29 15:54:19] INFO [localhost] It can be scanned with fast scan mode even if warn or err messages are displayed due to lack of dependent packages or sudo settings in fast-root or deep scan mode
[Aug 29 15:54:19] INFO [localhost] Scannable servers are below...
scan-target
5. スキャン実行
[vuls サーバにて]
$ vuls scan scan-target
[Aug 29 16:02:00] INFO [localhost] Start scanning
[Aug 29 16:02:00] INFO [localhost] config: /home/centos/config.toml
[Aug 29 16:02:00] INFO [localhost] Validating config...
[Aug 29 16:02:00] INFO [localhost] Detecting Server/Container OS...
[Aug 29 16:02:00] INFO [localhost] Detecting OS of servers...
[Aug 29 16:02:00] INFO [localhost] (1/1) Detected: scan-target: centos 6.5
[Aug 29 16:02:00] INFO [localhost] Detecting OS of containers...
[Aug 29 16:02:00] INFO [localhost] Checking Scan Modes...
[Aug 29 16:02:00] INFO [localhost] Detecting Platforms...
[Aug 29 16:02:00] INFO [localhost] (1/1) scan-target is running on aws
[Aug 29 16:02:00] INFO [localhost] Scanning vulnerabilities...
[Aug 29 16:02:00] INFO [localhost] Scanning vulnerable OS packages...
[Aug 29 16:02:00] INFO [scan-target] Scanning in fast mode
One Line Summary
================
scan-target centos6.5 198 installed, 139 updatable
To view the detail, vuls tui is useful.
To send a report, run vuls report -h.
スキャンモード
スキャンモードについて
v0.5.0 から3種類あります。
https://vuls.io/docs/en/architecture-fast-deep.html
- fast:Fast scan mode scans without root privilege, no dependencies, almost no load on the scan target server.
- fast-root:Fast scan mode scans with root privilege, almost no load on the scan target server.
- deep:Deep scan mode scans with root privilege. Certain commands can lead to high load such as fetch chagnelogs of many updatable packages.
指定方法
[vuls サーバにて]
$ vi config.toml
[servers]
[servers.scan-target]
host = "scan target IPアドレス"
port = "22"
user = "ユーザ名"
keyPath = "/home/centos/.ssh/id_rsa"
scanMode = ["fast" | "fast-root" | "deep"]
結果確認
TUI(Terminal-Based User Interface)
デフォルトで搭載されている確認方法です。
$ vuls tui
Ctrl + C で画面から抜けれます。
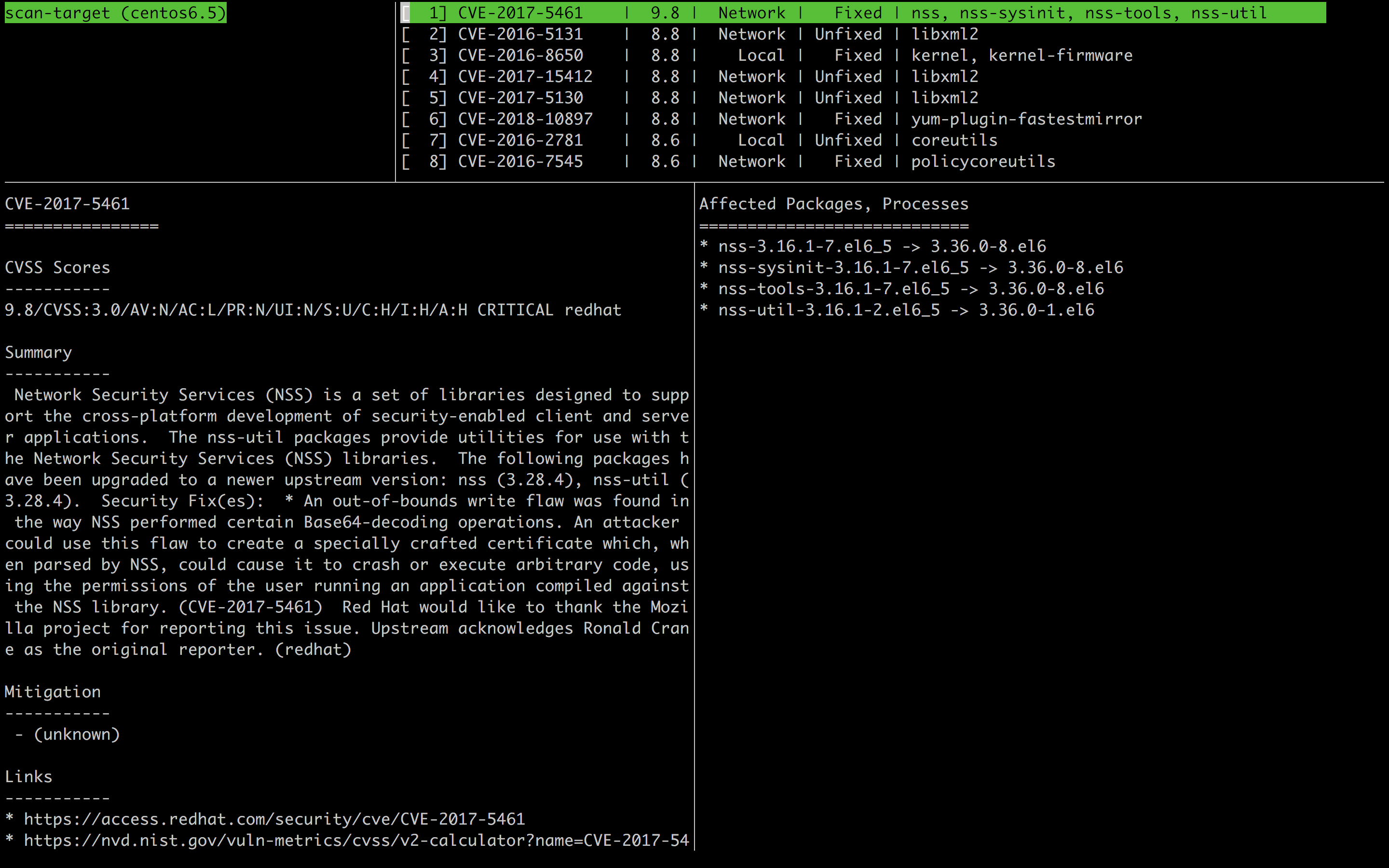
- 左上:スキャンした対象名(OSバージョン)
- 左下:各脆弱性の詳細情報
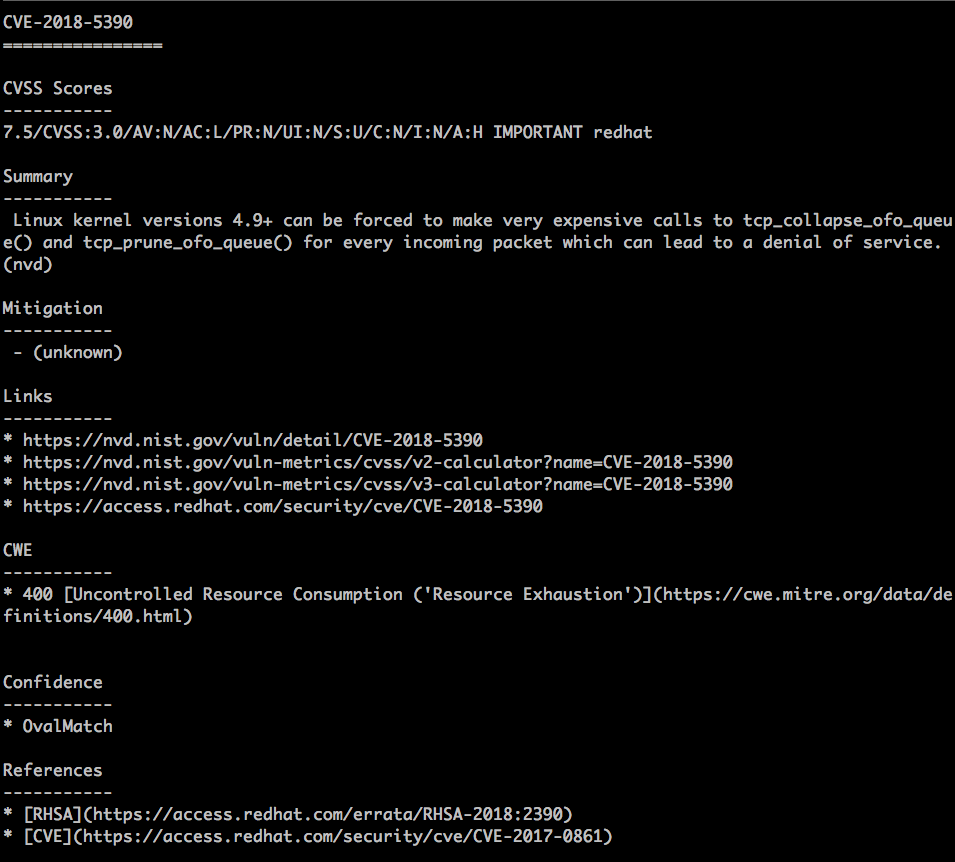
- CVE:共通脆弱性識別子CVE(Common Vulnerabilities and Exposures)の脆弱性ID
- CVSS Scores:共通脆弱性評価システム(Common Vulnerability Scoring System) の深刻度 0 - 10.0
- Summary:脆弱性情報のサマリ
- Mitigation:緩和策
- Links:脆弱性データベースへのリンク
- CWE:共通脆弱性タイプ (Common Weakness Enumeration) のカテゴリ
- Confidence:検知した方法
- References:脆弱性情報のリンク
- 右上:検出された脆弱性の一覧
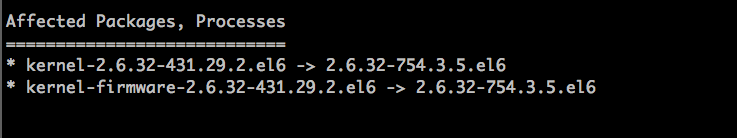
- 右下:検知された脆弱性に影響のあるパッケージ、プロセス -> 解消されるバージョン
可視化
VulsRepo
1. VulsRepo インストール
VulsRepo
[日本語翻訳ドキュメント]https://vuls.io/docs/ja/vulsrepo.html)
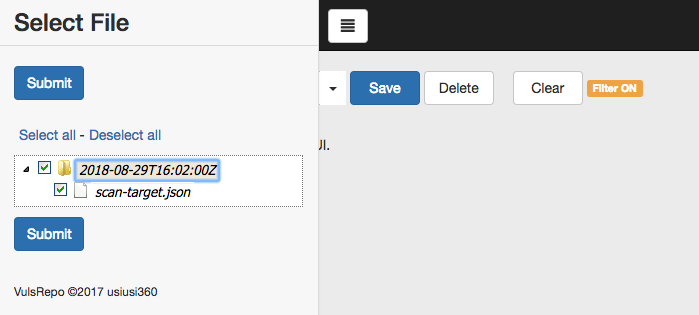
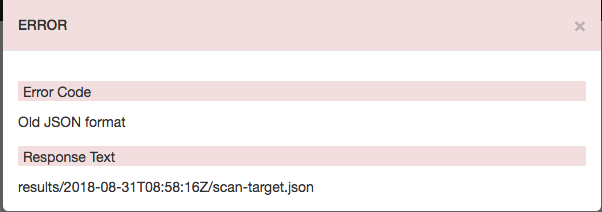
2. ファイルを指定
- エラーとなってしまった
- ファイルはありそう....
[centos@ip-192-168-0-68 ~]$ ls -l /home/centos/results/2018-08-29T16:02:00Z
合計 3336
-rw-------. 1 centos centos 3412750 8月 29 16:02 scan-target.json
[centos@ip-192-168-0-68 ~]$
※ 何かがおかしい...
Elasticsearch+Kibana
1. vuls-log-converter インストール
$ sudo yum install epel-release
$ sudo yum install nodejs
$ sudo yum install -y npm --enablerepo=epel
$ sudo npm i -g vuls-log-converter
2. ファイル変換
[centos@ip-192-168-0-68 ~]$ vulslogconv -t csv -i /home/centos/results/current/ -o ./output.csv
[INFO] : Convert start.
TypeError: Cannot convert undefined or null to object
at getFlatObj (/usr/lib/node_modules/vuls-log-converter/bin/vuls-log-converter.js:102:16)
at /usr/lib/node_modules/vuls-log-converter/bin/vuls-log-converter.js:612:24
at Array.forEach (native)
at /usr/lib/node_modules/vuls-log-converter/bin/vuls-log-converter.js:610:18
[centos@ip-192-168-0-68 ~]$
※ 何かがおかしい...
3. ElasticSearch へ転送
[centos@ip-192-168-0-68 ~]$ vulslogconv -t els -i /home/centos/results/current/ -e https://search-vuls-es-vzksv25i3yzf6c5x6qevgzlx44.ap-northeast-1.es.amazonaws.com
[INFO] : Convert start.
TypeError: Cannot convert undefined or null to object
at getFlatObj (/usr/lib/node_modules/vuls-log-converter/bin/vuls-log-converter.js:102:16)
at /usr/lib/node_modules/vuls-log-converter/bin/vuls-log-converter.js:612:24
at Array.forEach (native)
at /usr/lib/node_modules/vuls-log-converter/bin/vuls-log-converter.js:610:18
[centos@ip-192-168-0-68 ~]$
※ 何かがおかしい...
まとめ
可視化の部分がグダグタになってしまった。
もう少し調べながらやるしかない!