自己署名証明書の作成
利用可能な曲線を確認します
$ openssl ecparam -list_curves
secp112r1 : SECG/WTLS curve over a 112 bit prime field
secp112r2 : SECG curve over a 112 bit prime field
secp128r1 : SECG curve over a 128 bit prime field
secp128r2 : SECG curve over a 128 bit prime field
secp160k1 : SECG curve over a 160 bit prime field
secp160r1 : SECG curve over a 160 bit prime field
secp160r2 : SECG/WTLS curve over a 160 bit prime field
secp192k1 : SECG curve over a 192 bit prime field
secp224k1 : SECG curve over a 224 bit prime field
secp224r1 : NIST/SECG curve over a 224 bit prime field
secp256k1 : SECG curve over a 256 bit prime field
secp384r1 : NIST/SECG curve over a 384 bit prime field
secp521r1 : NIST/SECG curve over a 521 bit prime field
prime192v1: NIST/X9.62/SECG curve over a 192 bit prime field
prime192v2: X9.62 curve over a 192 bit prime field
prime192v3: X9.62 curve over a 192 bit prime field
prime239v1: X9.62 curve over a 239 bit prime field
prime239v2: X9.62 curve over a 239 bit prime field
prime239v3: X9.62 curve over a 239 bit prime field
prime256v1: X9.62/SECG curve over a 256 bit prime field
sect113r1 : SECG curve over a 113 bit binary field
sect113r2 : SECG curve over a 113 bit binary field
sect131r1 : SECG/WTLS curve over a 131 bit binary field
sect131r2 : SECG curve over a 131 bit binary field
sect163k1 : NIST/SECG/WTLS curve over a 163 bit binary field
sect163r1 : SECG curve over a 163 bit binary field
sect163r2 : NIST/SECG curve over a 163 bit binary field
sect193r1 : SECG curve over a 193 bit binary field
sect193r2 : SECG curve over a 193 bit binary field
sect233k1 : NIST/SECG/WTLS curve over a 233 bit binary field
sect233r1 : NIST/SECG/WTLS curve over a 233 bit binary field
sect239k1 : SECG curve over a 239 bit binary field
sect283k1 : NIST/SECG curve over a 283 bit binary field
sect283r1 : NIST/SECG curve over a 283 bit binary field
sect409k1 : NIST/SECG curve over a 409 bit binary field
sect409r1 : NIST/SECG curve over a 409 bit binary field
sect571k1 : NIST/SECG curve over a 571 bit binary field
sect571r1 : NIST/SECG curve over a 571 bit binary field
c2pnb163v1: X9.62 curve over a 163 bit binary field
c2pnb163v2: X9.62 curve over a 163 bit binary field
c2pnb163v3: X9.62 curve over a 163 bit binary field
c2pnb176v1: X9.62 curve over a 176 bit binary field
c2tnb191v1: X9.62 curve over a 191 bit binary field
c2tnb191v2: X9.62 curve over a 191 bit binary field
c2tnb191v3: X9.62 curve over a 191 bit binary field
c2pnb208w1: X9.62 curve over a 208 bit binary field
c2tnb239v1: X9.62 curve over a 239 bit binary field
c2tnb239v2: X9.62 curve over a 239 bit binary field
c2tnb239v3: X9.62 curve over a 239 bit binary field
c2pnb272w1: X9.62 curve over a 272 bit binary field
c2pnb304w1: X9.62 curve over a 304 bit binary field
c2tnb359v1: X9.62 curve over a 359 bit binary field
c2pnb368w1: X9.62 curve over a 368 bit binary field
c2tnb431r1: X9.62 curve over a 431 bit binary field
wap-wsg-idm-ecid-wtls1: WTLS curve over a 113 bit binary field
wap-wsg-idm-ecid-wtls3: NIST/SECG/WTLS curve over a 163 bit binary field
wap-wsg-idm-ecid-wtls4: SECG curve over a 113 bit binary field
wap-wsg-idm-ecid-wtls5: X9.62 curve over a 163 bit binary field
wap-wsg-idm-ecid-wtls6: SECG/WTLS curve over a 112 bit prime field
wap-wsg-idm-ecid-wtls7: SECG/WTLS curve over a 160 bit prime field
wap-wsg-idm-ecid-wtls8: WTLS curve over a 112 bit prime field
wap-wsg-idm-ecid-wtls9: WTLS curve over a 160 bit prime field
wap-wsg-idm-ecid-wtls10: NIST/SECG/WTLS curve over a 233 bit binary field
wap-wsg-idm-ecid-wtls11: NIST/SECG/WTLS curve over a 233 bit binary field
wap-wsg-idm-ecid-wtls12: WTLS curvs over a 224 bit prime field
Oakley-EC2N-3:
IPSec/IKE/Oakley curve #3 over a 155 bit binary field.
Not suitable for ECDSA.
Questionable extension field!
Oakley-EC2N-4:
IPSec/IKE/Oakley curve #4 over a 185 bit binary field.
Not suitable for ECDSA.
Questionable extension field!
鍵を作成します
$ openssl ecparam -out ca.key -name prime256v1 -genkey
$ cat ca.key
-----BEGIN EC PARAMETERS-----
BggqhkjOPQMBBw==
-----END EC PARAMETERS-----
-----BEGIN EC PRIVATE KEY-----
MHcCAQEEIKafrGic/O/+bcPsnvnRJa0nbt7WPJVQLJbDy+dkIe8loAoGCCqGSM49
AwEHoUQDQgAED8mXaMkaVZ8tmjY0SnU7RVQW59at/Lk2tgj2i929cpF/e1DkGEyG
hjfAYmxk6DRkHKaDLHf4QrzEOBlqX5IuPQ==
-----END EC PRIVATE KEY-----
自己署名証明書を作成します
$ openssl req -config openssl.cnf \
-new \
-x509 \
-key ca.key \
-sha256 \
-days 365 \
-subj "/C=JP/ST=Tokyo/O=organization/CN=ECC Test CA" \
-extensions v3_ca \
-out ca.pem
作成した証明書を確認してみます
$ cat ca.pem
-----BEGIN CERTIFICATE-----
MIIB2jCCAYGgAwIBAgIJAODRYY3w41lHMAoGCCqGSM49BAMCMEoxCzAJBgNVBAYT
AkpQMQ4wDAYDVQQIDAVUb2t5bzEVMBMGA1UECgwMb3JnYW5pemF0aW9uMRQwEgYD
VQQDDAtFQ0MgVGVzdCBDQTAeFw0xNDA4MTQxMjQyNDJaFw0xNTA4MTQxMjQyNDJa
MEoxCzAJBgNVBAYTAkpQMQ4wDAYDVQQIDAVUb2t5bzEVMBMGA1UECgwMb3JnYW5p
emF0aW9uMRQwEgYDVQQDDAtFQ0MgVGVzdCBDQTBZMBMGByqGSM49AgEGCCqGSM49
AwEHA0IABA/Jl2jJGlWfLZo2NEp1O0VUFufWrfy5NrYI9ovdvXKRf3tQ5BhMhoY3
wGJsZOg0ZBymgyx3+EK8xDgZal+SLj2jUDBOMB0GA1UdDgQWBBTEEtX0yIN2FMj/
hcrvBUHdLcWr7zAfBgNVHSMEGDAWgBTEEtX0yIN2FMj/hcrvBUHdLcWr7zAMBgNV
HRMEBTADAQH/MAoGCCqGSM49BAMCA0cAMEQCIHW9TXny/1hZiPQpemI5KbffX3VN
84vUHtLE9Gf1PQlEAiBUbXcShPnCQRaOqdgtNl3EkIOwRa9Q4+VFx1EMZB5ZWQ==
-----END CERTIFICATE-----
$ openssl x509 -noout -text -in ca.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 16199836596888099143 (0xe0d1618df0e35947)
Signature Algorithm: ecdsa-with-SHA256
Issuer: C=JP, ST=Tokyo, O=organization, CN=ECC Test CA
Validity
Not Before: Aug 14 12:42:42 2014 GMT
Not After : Aug 14 12:42:42 2015 GMT
Subject: C=JP, ST=Tokyo, O=organization, CN=ECC Test CA
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:0f:c9:97:68:c9:1a:55:9f:2d:9a:36:34:4a:75:
3b:45:54:16:e7:d6:ad:fc:b9:36:b6:08:f6:8b:dd:
bd:72:91:7f:7b:50:e4:18:4c:86:86:37:c0:62:6c:
64:e8:34:64:1c:a6:83:2c:77:f8:42:bc:c4:38:19:
6a:5f:92:2e:3d
ASN1 OID: prime256v1
X509v3 extensions:
X509v3 Subject Key Identifier:
C4:12:D5:F4:C8:83:76:14:C8:FF:85:CA:EF:05:41:DD:2D:C5:AB:EF
X509v3 Authority Key Identifier:
keyid:C4:12:D5:F4:C8:83:76:14:C8:FF:85:CA:EF:05:41:DD:2D:C5:AB:EF
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: ecdsa-with-SHA256
30:44:02:20:75:bd:4d:79:f2:ff:58:59:88:f4:29:7a:62:39:
29:b7:df:5f:75:4d:f3:8b:d4:1e:d2:c4:f4:67:f5:3d:09:44:
02:20:54:6d:77:12:84:f9:c2:41:16:8e:a9:d8:2d:36:5d:c4:
90:83:b0:45:af:50:e3:e5:45:c7:51:0c:64:1e:59:59
サーバ証明書の発行
上記で作成した自己署名証明書と鍵を使用して、サーバ証明書を発行してみます
先ほどと同様の手順で鍵を作成します
$ openssl ecparam -out server.key -name prime256v1 -genkey
$ cat server.key
-----BEGIN EC PARAMETERS-----
BggqhkjOPQMBBw==
-----END EC PARAMETERS-----
-----BEGIN EC PRIVATE KEY-----
MHcCAQEEIPmBI5L8xtpkh1oo7VDk8kBzq8MdR4RSOVaXDcm6JS10oAoGCCqGSM49
AwEHoUQDQgAEIjDDdiJNfenuvW2uoZkEGEfcpm+2rlIPEUwb8BaIEZ3Iqds/MDYd
y8iUrnJTe7AAI0SCGTIms5nhWbxCFsCoqg==
-----END EC PRIVATE KEY-----
鍵を使用して、CSR を作成します
$ openssl req -config openssl.cnf \
-new \
-sha256 \
-key server.key \
-outform PEM \
-keyform PEM \
-out req.pem \
-subj "/C=JP/ST=Tokyo/O=organization/CN=example.com"
$ cat req.pem
-----BEGIN CERTIFICATE REQUEST-----
MIIBBDCBrAIBADBKMQswCQYDVQQGEwJKUDEOMAwGA1UECAwFVG9reW8xFTATBgNV
BAoMDG9yZ2FuaXphdGlvbjEUMBIGA1UEAwwLZXhhbXBsZS5jb20wWTATBgcqhkjO
PQIBBggqhkjOPQMBBwNCAAQiMMN2Ik196e69ba6hmQQYR9ymb7auUg8RTBvwFogR
ncip2z8wNh3LyJSuclN7sAAjRIIZMiazmeFZvEIWwKiqoAAwCQYHKoZIzj0EAQNI
ADBFAiApdqlKqA+ltWygjfj4iU04Nd0CttEIiC+gQn8WxolPPwIhAKqnbsWmpBsO
etyzJ5RvRVffhsv5hCnfWw/cnAF9aAnL
-----END CERTIFICATE REQUEST-----
$ openssl req -noout -text -in req.pem
Certificate Request:
Data:
Version: 0 (0x0)
Subject: C=JP, ST=Tokyo, O=organization, CN=example.com
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:22:30:c3:76:22:4d:7d:e9:ee:bd:6d:ae:a1:99:
04:18:47:dc:a6:6f:b6:ae:52:0f:11:4c:1b:f0:16:
88:11:9d:c8:a9:db:3f:30:36:1d:cb:c8:94:ae:72:
53:7b:b0:00:23:44:82:19:32:26:b3:99:e1:59:bc:
42:16:c0:a8:aa
ASN1 OID: prime256v1
Attributes:
a0:00
Signature Algorithm: ecdsa-with-SHA1
30:45:02:20:29:76:a9:4a:a8:0f:a5:b5:6c:a0:8d:f8:f8:89:
4d:38:35:dd:02:b6:d1:08:88:2f:a0:42:7f:16:c6:89:4f:3f:
02:21:00:aa:a7:6e:c5:a6:a4:1b:0e:7a:dc:b3:27:94:6f:45:
57:df:86:cb:f9:84:29:df:5b:0f:dc:9c:01:7d:68:09:cb
証明書を発行します
$ openssl ca -config openssl.cnf \
-in req.pem \
-keyfile ca.key \
-cert ca.pem \
-extensions usr_cert \
-out server.pem
Using configuration from openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 0 (0x0)
Validity
Not Before: Aug 14 12:54:39 2014 GMT
Not After : Aug 14 12:54:39 2015 GMT
Subject:
countryName = JP
stateOrProvinceName = Tokyo
organizationName = organization
commonName = example.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
7D:4C:53:50:C4:88:5E:53:6D:BE:1D:AD:C7:B8:28:4A:C6:9C:EC:60
X509v3 Authority Key Identifier:
keyid:C4:12:D5:F4:C8:83:76:14:C8:FF:85:CA:EF:05:41:DD:2D:C5:AB:EF
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
Certificate is to be certified until Aug 14 12:54:39 2015 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
発行した証明書を確認してみます
$ cat server.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 0 (0x0)
Signature Algorithm: ecdsa-with-SHA256
Issuer: C=JP, ST=Tokyo, O=organization, CN=ECC Test CA
Validity
Not Before: Aug 14 12:54:39 2014 GMT
Not After : Aug 14 12:54:39 2015 GMT
Subject: C=JP, ST=Tokyo, O=organization, CN=example.com
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:22:30:c3:76:22:4d:7d:e9:ee:bd:6d:ae:a1:99:
04:18:47:dc:a6:6f:b6:ae:52:0f:11:4c:1b:f0:16:
88:11:9d:c8:a9:db:3f:30:36:1d:cb:c8:94:ae:72:
53:7b:b0:00:23:44:82:19:32:26:b3:99:e1:59:bc:
42:16:c0:a8:aa
ASN1 OID: prime256v1
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
7D:4C:53:50:C4:88:5E:53:6D:BE:1D:AD:C7:B8:28:4A:C6:9C:EC:60
X509v3 Authority Key Identifier:
keyid:C4:12:D5:F4:C8:83:76:14:C8:FF:85:CA:EF:05:41:DD:2D:C5:AB:EF
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
Signature Algorithm: ecdsa-with-SHA256
30:46:02:21:00:90:89:6b:3f:25:97:7a:3c:3f:c2:53:26:68:
4d:6d:ef:ab:01:c5:89:f4:ac:1e:18:54:33:a5:3e:ec:ab:74:
17:02:21:00:c7:fc:30:33:05:79:60:59:fe:b4:bd:af:1e:45:
14:5f:1c:86:6a:ca:e8:31:bd:6e:1d:38:67:52:3e:dd:b2:f1
-----BEGIN CERTIFICATE-----
MIICIDCCAcWgAwIBAgIBADAKBggqhkjOPQQDAjBKMQswCQYDVQQGEwJKUDEOMAwG
A1UECAwFVG9reW8xFTATBgNVBAoMDG9yZ2FuaXphdGlvbjEUMBIGA1UEAwwLRUND
IFRlc3QgQ0EwHhcNMTQwODE0MTI1NDM5WhcNMTUwODE0MTI1NDM5WjBKMQswCQYD
VQQGEwJKUDEOMAwGA1UECAwFVG9reW8xFTATBgNVBAoMDG9yZ2FuaXphdGlvbjEU
MBIGA1UEAwwLZXhhbXBsZS5jb20wWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAAQi
MMN2Ik196e69ba6hmQQYR9ymb7auUg8RTBvwFogRncip2z8wNh3LyJSuclN7sAAj
RIIZMiazmeFZvEIWwKiqo4GbMIGYMAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8W
HU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBR9TFNQxIhe
U22+Ha3HuChKxpzsYDAfBgNVHSMEGDAWgBTEEtX0yIN2FMj/hcrvBUHdLcWr7zAd
BgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwCgYIKoZIzj0EAwIDSQAwRgIh
AJCJaz8ll3o8P8JTJmhNbe+rAcWJ9KweGFQzpT7sq3QXAiEAx/wwMwV5YFn+tL2v
HkUUXxyGasroMb1uHThnUj7dsvE=
-----END CERTIFICATE-----
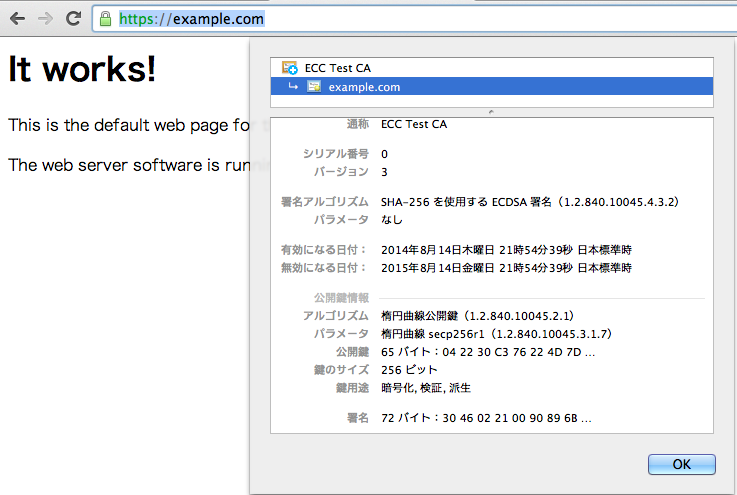
HTTP Over TLS で確認
Apache2 に入れて、ブラウザから確認してみます
補足
はじめて証明書を発行するとき
$ mkdir -p demoCA/newcerts
$ touch demoCA/index.txt
$ echo 00 > demoCA/serial
openssl.cnf の dir, database 等はデフォルトの下記の設定
openssl.cnf
dir = ./demoCA
database = $dir/index.txt
new_certs_dir = $dir/newcerts
serial = $dir/serial
今回作成した証明書用の openssl.cnf の設定
[ CA_default ] セクションの default_md を sha256 に変更
openssl.cnf
default_md = sha256
[ usr_cert ] セクションに extendedKeyUsage を追記
openssl.cnf
extendedKeyUsage = serverAuth, clientAuth
Subject Alternative Name を追加する場合は、[ names ] セクションに DNS 名等を記載して、[ usr_cert ] セクションに subjectAltName を追記する
openssl.cnf
[ usr_cert ]
・
・
・
subjectAltName=@names
[ names ]
DNS.1 = example.com
DNS.2 = www.example.com