事象:kubernetes-dashboard.yamlを kubectl apply しようとしてエラーを出る
kubernetes-dashboard-minimalの権限周りでエラーになる
$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
secret "kubernetes-dashboard-certs" created
serviceaccount "kubernetes-dashboard" created
rolebinding.rbac.authorization.k8s.io "kubernetes-dashboard-minimal" created
deployment.apps "kubernetes-dashboard" created
service "kubernetes-dashboard" created
Error from server (Forbidden): error when creating "https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml": roles.rbac.authorization.k8s.io "kubernetes-dashboard-minimal" is forbidden: attempt to grant extra privileges: [PolicyRule{APIGroups:[""], Resources:["secrets"],
:
:
Got error: exit status 1
解決: 自分のアカウント(メールアドレス)を管理者として設定する
$ kubectl create clusterrolebinding cluster-admin-binding \
--clusterrole cluster-admin --user $(gcloud config get-value account)
clusterrolebinding.rbac.authorization.k8s.io/cluster-admin-binding created
参考: https://github.com/kubernetes/dashboard/issues/2415\#issuecomment-391648932
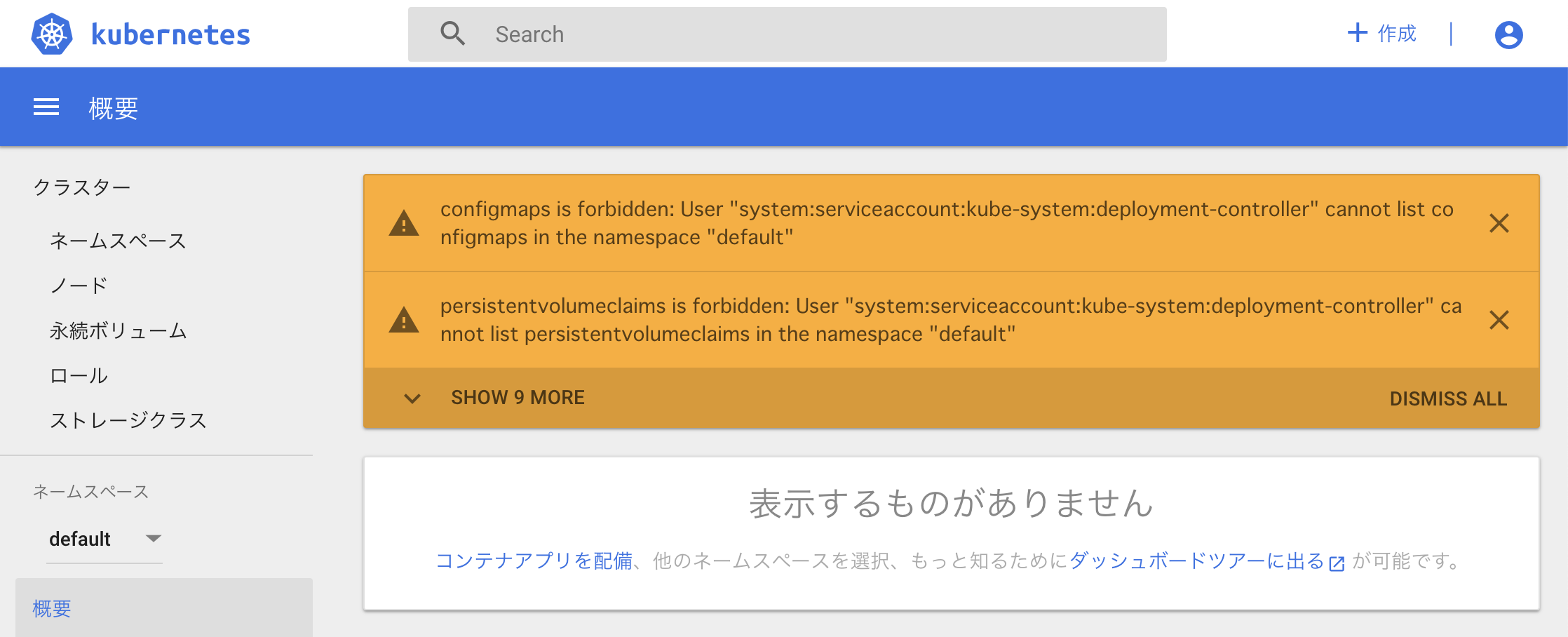
事象:ダッシュボードは開けるがリソースにアクセスできない
エラーメッセージ
configmaps is forbidden: User "system:serviceaccount:kube-system:deployment-controller" cannot list configmaps in the namespace "default"
close
warning
persistentvolumeclaims is forbidden: User "system:serviceaccount:kube-system:deployment-controller" cannot list persistentvolumeclaims in the namespace "default"
解決: 管理者権限を追加して、管理者のトークンでアクセスする
add-admin-user.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kube-system
# 適用
$ kubectl create -f add-admin-user.yaml
# NAMEの確認
$ kubectl get secrets -n kube-system | grep admin-user
admin-user-token-rr88x kubernetes.io/service-account-token 3 4h
# NAMEの確認
$ kubectl describe secret admin-user-token-rr88x -n kube-system
Name: admin-user-token-rr88x
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin-user
kubernetes.io/service-account.uid: ef10a79f-XXXX-11e9-a17f-42010X92005e
Type: kubernetes.io/service-account-token
Data
====
namespace: 11 bytes
token: eyJhbGciXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXx
token: をトークンとして指定してサインイン
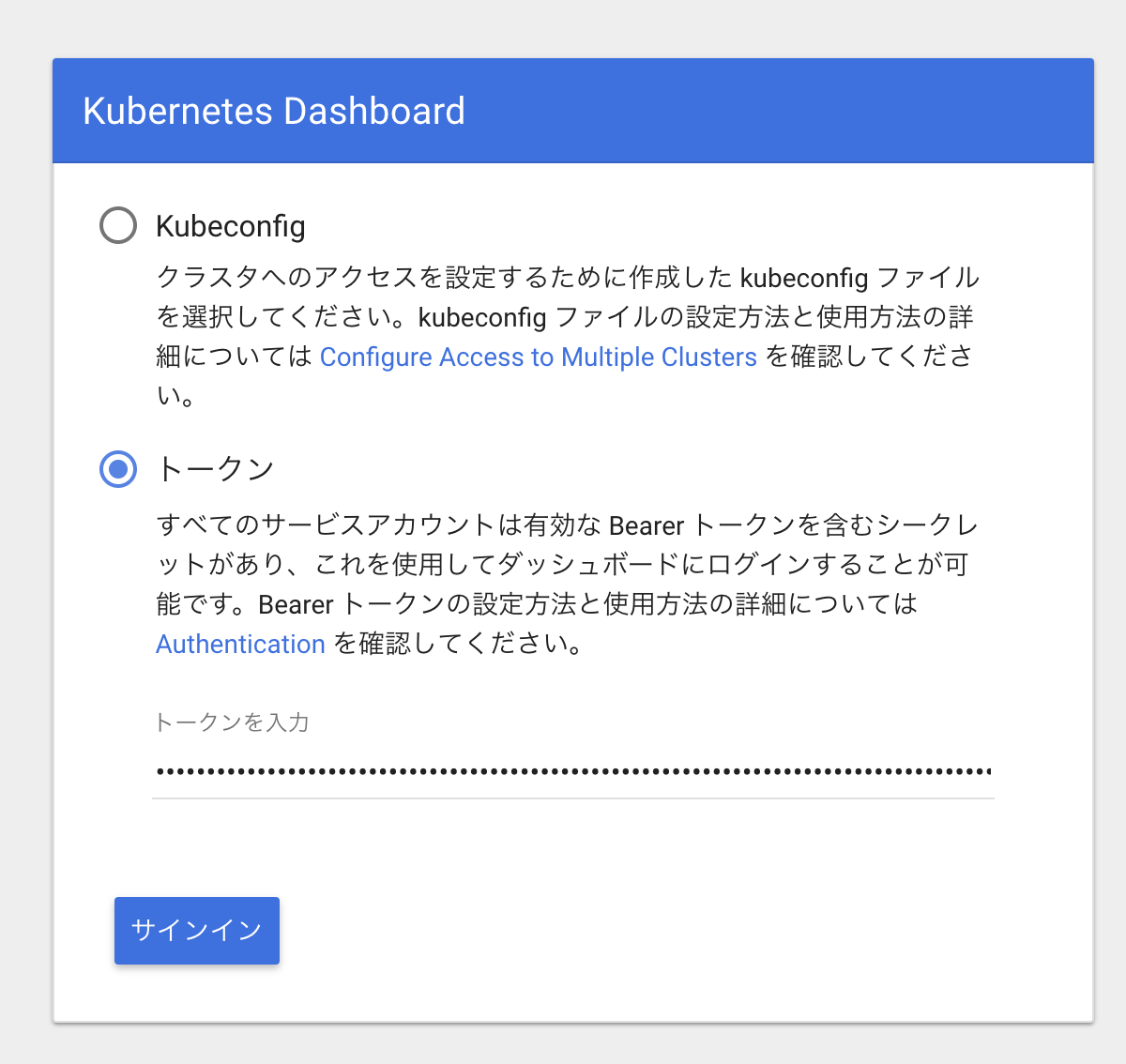
参考: https://qiita.com/sugimount/items/689b7cd172c7eaf1235f
メモ: admin-userのトークンを一発で取得するコマンド
$ kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | awk '/^admin-user-token-/{print $1}') | awk '$1=="token:"{print $2}'
eyJhbGciXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXx