概要
FUJITSU Si-R G100を使用してOCI IPSecにVPN接続する設定例を以前に投稿しました。
FUJITSU Si-Rを使用したOCI IPSec VPN接続例
この記事はIKEv1で設定しましたが今回はIKEv2を使用しています。
何がいいの?
ガイド資料ではIKEv1を使った設定例が紹介されておりますがIKEv2を使った設定例の情報はありません。将来IKEv1サポート終了した場合においてもIKEv2に設定することにより資産の有効活用が可能です。
構成

設定例(Static)
- OCI
OCIコンソール ナビゲーションメニューからネットワーキング>>サイト間VPNを選択します。
作成については以下のサイトをご参照ください。
サイト間VPNの設定
https://docs.oracle.com/ja-jp/iaas/Content/Network/Tasks/settingupIPsec.htm
ここでは作成済みの設定となります。
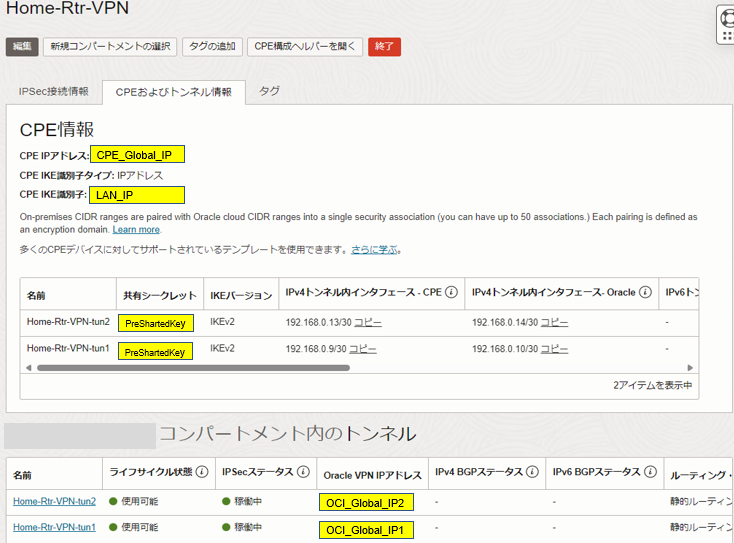
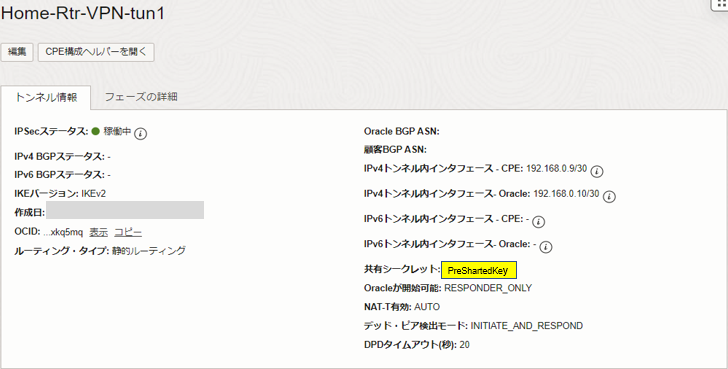
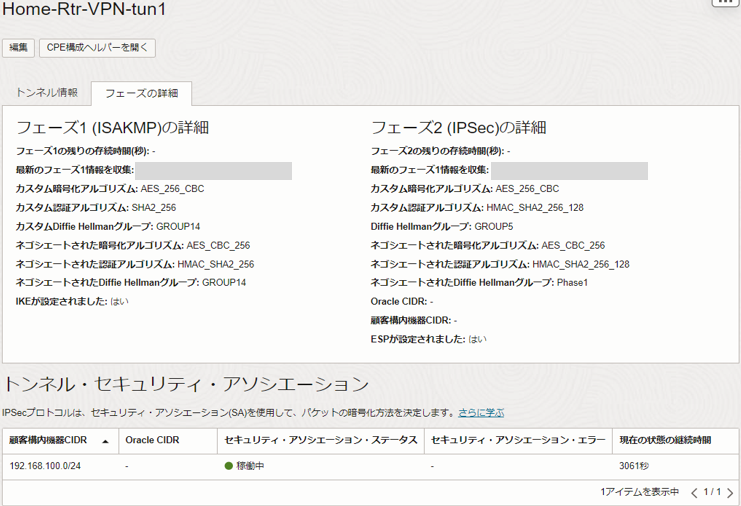
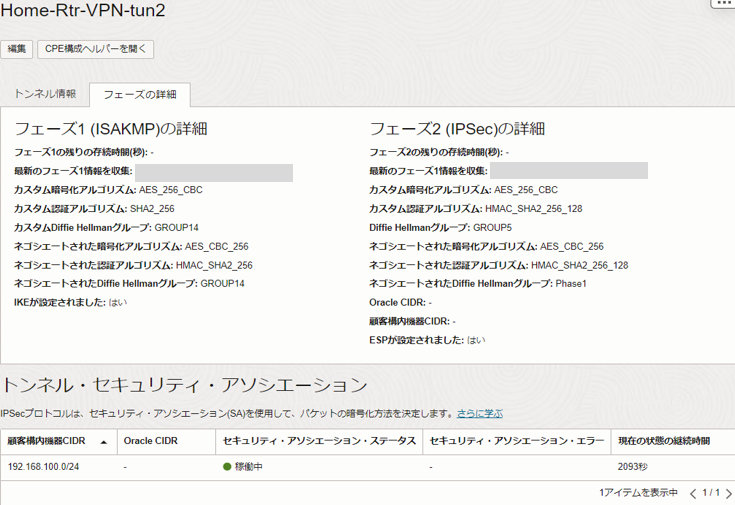
OCIコンソール ナビゲーションメニューからネットワーキング>>サイト間VPNから対象のVPNを選択


- Si-R G100
Software VersionはV02.54です。
作成については以下のサイトをご参照ください。
拠点間VPNゲートウェイ:IKEv1 IPsec VTI VPN (L3VPN)で接続する拠点側VPN装置の設定(富士通 Si-R G)
https://pfs.nifcloud.com/guide/cp/vpngw/cn_g110_vti_ikev1.htm
ここでは作成済みの設定となります。
Si-R G100(config)# show running-config
ether 1 1 vlan untag 1
ether 2 1 vlan untag 2
ether 2 2 vlan untag 2
ether 2 3 vlan untag 2
ether 2 4 vlan untag 2
lan 0 ip address 【LAN_IP】 3
lan 0 ip route 0 default 【LAN_GW】 1 1
lan 0 ip nat mode multi any 1 5m
lan 0 ip nat static 0 192.168.100.1 4500 any 4500 17
lan 0 ip nat static 1 192.168.100.1 500 any 500 17
lan 0 ip nat static 2 192.168.100.1 any any any 50
lan 0 ip nat wellknown 0 500 off
lan 0 vlan 1
lan 1 ip address 192.168.100.1/24 3
lan 1 vlan 2
remote 0 name ipsec1
remote 0 ap 0 name ipsec1
remote 0 ap 0 datalink type ipsec
remote 0 ap 0 keep connect
remote 0 ap 0 ipsec type ikev2
remote 0 ap 0 ipsec ike protocol esp
remote 0 ap 0 ipsec ike encrypt aes-cbc-256
remote 0 ap 0 ipsec ike auth hmac-sha256
remote 0 ap 0 ipsec ike pfs modp1536
remote 0 ap 0 ipsec ike lifetime 1h
remote 0 ap 0 ipsec ike newsa initiator 3m 0
remote 0 ap 0 ipsec ike esn disable
remote 0 ap 0 ike local-idtype address
remote 0 ap 0 ike remote-idtype address
remote 0 ap 0 ike shared key text 【PreShartedKey】 encrypted
remote 0 ap 0 ike proposal 0 encrypt aes-cbc-256
remote 0 ap 0 ike proposal 0 hash hmac-sha256
remote 0 ap 0 ike proposal 0 pfs modp2048
remote 0 ap 0 ike proposal 0 prf hmac-sha256
remote 0 ap 0 ike proposal 0 lifetime 8h
remote 0 ap 0 ike nat-traversal use on
remote 0 ap 0 ike dpd use on
remote 0 ap 0 tunnel local 192.168.100.1
remote 0 ap 0 tunnel remote 【OCI_Global_IP1】
remote 0 ip address local 192.168.0.9
remote 0 ip address remote 192.168.0.10
remote 0 ip route 0 10.105.0.0/16 1 1
remote 0 ip msschange 1300
remote 1 name ipsec2
remote 1 ap 0 name ipsec2
remote 1 ap 0 datalink type ipsec
remote 1 ap 0 keep connect
remote 1 ap 0 ipsec type ikev2
remote 1 ap 0 ipsec ike protocol esp
remote 1 ap 0 ipsec ike encrypt aes-cbc-256
remote 1 ap 0 ipsec ike auth hmac-sha256
remote 1 ap 0 ipsec ike pfs modp1536
remote 1 ap 0 ipsec ike lifetime 1h
remote 1 ap 0 ipsec ike newsa initiator 3m 0
remote 1 ap 0 ipsec ike esn disable
remote 1 ap 0 ike local-idtype address
remote 1 ap 0 ike remote-idtype address
remote 1 ap 0 ike shared key text 【PreShartedKey】 encrypted
remote 1 ap 0 ike proposal 0 encrypt aes-cbc-256
remote 1 ap 0 ike proposal 0 hash hmac-sha256
remote 1 ap 0 ike proposal 0 pfs modp2048
remote 1 ap 0 ike proposal 0 prf hmac-sha256
remote 1 ap 0 ike proposal 0 lifetime 8h
remote 1 ap 0 ike nat-traversal use on
remote 1 ap 0 ike dpd use on
remote 1 ap 0 tunnel local 192.168.100.1
remote 1 ap 0 tunnel remote 【OCI_Global_IP2】
remote 1 ip address local 192.168.0.13
remote 1 ip address remote 192.168.0.14
remote 1 ip route 0 10.105.0.0/16 10 10
remote 1 ip msschange 1300
routemanage ip redist bgp static on
routemanage ip redist bgp connected on
syslog facility 23
time auto server 0.0.0.0 dhcp
time zone 0900
proxydns domain 0 any * any to 0
proxydns address 0 any to 0
resource system vlan 4089-4094
consoleinfo autologout 8h
telnetinfo autologout 5m
terminal pager enable
terminal charset SJIS
alias history "show logging command brief"
Si-R G100(config)#
結果
- IPSec状況抜粋
Si-R G100(config)# show ipsec sa
[IPsec SA Information]
[1] Remote Name(ipsec1), rmt0, ap0
Side(Initiator), Gateway(192.168.100.1, 【OCI_Global_IP1】), IN
Protocol(ESP), Enctype(aes-cbc-256), Authtype(hmac-sha256), PFS(off)
Status(mature), Spi=99121124(0x05e877e4), ESN(disable)
Created(Apr 15 18:29:20 2024), NewSA(3420secs, 0Kbyte)
Lifetime(3600secs), Current(2163secs), Remain(1437secs)
Lifebyte(0Kbyte), Current(0Kbyte), Remain(0Kbyte)
[2] Remote Name(ipsec1), rmt0, ap0
Side(Initiator), Gateway(【OCI_Global_IP1】, 192.168.100.1), OUT
Protocol(ESP), Enctype(aes-cbc-256), Authtype(hmac-sha256), PFS(off)
Status(mature), Spi=385186241(0x16f579c1), ESN(disable)
Created(Apr 15 18:29:20 2024), NewSA(3420secs, 0Kbyte)
Lifetime(3600secs), Current(2163secs), Remain(1437secs)
Lifebyte(0Kbyte), Current(289Kbyte), Remain(0Kbyte)
[3] Remote Name(ipsec2), rmt1, ap0
Side(Initiator), Gateway(192.168.100.1, 【OCI_Global_IP2】), IN
Protocol(ESP), Enctype(aes-cbc-256), Authtype(hmac-sha256), PFS(off)
Status(mature), Spi=54635016(0x0341aa08), ESN(disable)
Created(Apr 15 18:29:19 2024), NewSA(3420secs, 0Kbyte)
Lifetime(3600secs), Current(2164secs), Remain(1436secs)
Lifebyte(0Kbyte), Current(256Kbyte), Remain(0Kbyte)
[4] Remote Name(ipsec2), rmt1, ap0
Side(Initiator), Gateway(【OCI_Global_IP2】, 192.168.100.1), OUT
Protocol(ESP), Enctype(aes-cbc-256), Authtype(hmac-sha256), PFS(off)
Status(mature), Spi=453303787(0x1b04ddeb), ESN(disable)
Created(Apr 15 18:29:19 2024), NewSA(3420secs, 0Kbyte)
Lifetime(3600secs), Current(2164secs), Remain(1436secs)
Lifebyte(0Kbyte), Current(0Kbyte), Remain(0Kbyte)
[IKE SA Information]
[1] Destination(【OCI_Global_IP2】.4500), Source(192.168.100.1.4500), rmt1
Cookies(9da868f90a2c7792:c1d315c71f7532ee)
Side(Initiator), Status(ESTABLISHED),
IKE Version(2), Authmethod(shared-key), PRF(hmac-sha256), DPD(enable)
Enctype(aes-cbc-256), Hashtype(hmac-sha256), PFS(modp2048), EAP(disable)
Created(Apr 15 18:29:19 2024)
Lifetime(28800secs), Current(2164secs), Remain(26636secs)
[2] Destination(【OCI_Global_IP1】.4500), Source(192.168.100.1.4500), rmt0
Cookies(63416ff054dcc907:bab41977e7150da3)
Side(Initiator), Status(ESTABLISHED),
IKE Version(2), Authmethod(shared-key), PRF(hmac-sha256), DPD(enable)
Enctype(aes-cbc-256), Hashtype(hmac-sha256), PFS(modp2048), EAP(disable)
Created(Apr 15 18:29:20 2024)
Lifetime(28800secs), Current(2163secs), Remain(26637secs)
Si-R G100(config)#
Si-R G100(config)# show access-point
remote 0 ap 0 : ipsec1.ipsec1
status : connected
since : Apr 15 18:29:20 2024
speed : not available
send traffic : not available
receive traffic : not available
type : IPsec/IKE
IKE Version : 2
IKE SA : established
IPsec SA : established
remote 1 ap 0 : ipsec2.ipsec2
status : connected
since : Apr 15 18:29:19 2024
speed : not available
send traffic : not available
receive traffic : not available
type : IPsec/IKE
IKE Version : 2
IKE SA : established
IPsec SA : established
Si-R G100(config)#
- ルートテーブル
Si-R G100(config)# show ip route
FP Destination/Mask Gateway Distance UpTime Interface
--- ------------------ --------------- -------- --------- ------------------
*S 0.0.0.0/0 【LAN GW】 1 00:55:01 lan0
*S 10.105.0.0/16 192.168.0.10 1 00:35:28 rmt0
*L 192.168.0.9/32 192.168.0.9 0 00:35:28 rmt0
*C 192.168.0.10/32 192.168.0.9 0 00:35:28 rmt0
*L 192.168.0.13/32 192.168.0.13 0 00:35:29 rmt1
*C 192.168.0.14/32 192.168.0.13 0 00:35:29 rmt1
*C 192.168.100.0/24 192.168.100.1 0 00:54:56 lan1
*C 【LANセグメント】/24【LAN IP】 0 00:55:01 lan0
Si-R G100(config)#
- Pingテスト
OCIサーバーからオンプレサーバーへのping結果
[user@linux ~]$ ping 192.168.100.102
PING 192.168.100.102 (192.168.100.102) 56(84) bytes of data.
64 bytes from 192.168.100.102: icmp_seq=1 ttl=125 time=188 ms
64 bytes from 192.168.100.102: icmp_seq=2 ttl=125 time=187 ms
64 bytes from 192.168.100.102: icmp_seq=3 ttl=125 time=206 ms
64 bytes from 192.168.100.102: icmp_seq=4 ttl=125 time=185 ms
64 bytes from 192.168.100.102: icmp_seq=5 ttl=125 time=225 ms
64 bytes from 192.168.100.102: icmp_seq=6 ttl=125 time=183 ms
64 bytes from 192.168.100.102: icmp_seq=7 ttl=125 time=191 ms
^C
--- 192.168.100.102 ping statistics ---
7 packets transmitted, 7 received, 0% packet loss, time 6005ms
rtt min/avg/max/mdev = 183.302/195.081/225.166/14.127 ms
[opc@syd-vm-08-linux-rundeck ~]$
オンプレサーバーからOCIサーバーへのping結果
C:\path\to>ping 10.105.2.100 -t
10.105.2.100 に ping を送信しています 32 バイトのデータ:
10.105.2.100 からの応答: バイト数 =32 時間 =198ms TTL=60
10.105.2.100 からの応答: バイト数 =32 時間 =179ms TTL=60
10.105.2.100 からの応答: バイト数 =32 時間 =197ms TTL=60
10.105.2.100 からの応答: バイト数 =32 時間 =182ms TTL=60
10.105.2.100 からの応答: バイト数 =32 時間 =184ms TTL=60
10.105.2.100 からの応答: バイト数 =32 時間 =187ms TTL=60
10.105.2.100 の ping 統計:
パケット数: 送信 = 6、受信 = 6、損失 = 0 (0% の損失)、
ラウンド トリップの概算時間 (ミリ秒):
最小 = 179ms、最大 = 198ms、平均 = 187ms