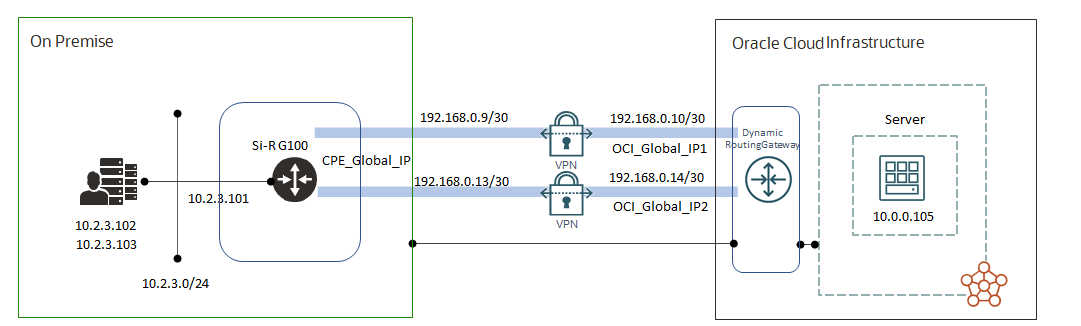
概要
FUJITSU Si-R G100を使用してOCI IPSecにVPN接続する設定例です。
(追記)
IKEv2を使用した設定例はこちら
構成
設定例(Static)
- OCI
OCIメニューからネットワーキング>>顧客接続性>>サイト間VPNを選択します。
作成については以下のサイトをご参照ください。
サイト間VPNの設定
https://docs.oracle.com/ja-jp/iaas/Content/Network/Tasks/settingupIPsec.htm
ここでは作成済みの設定となります。
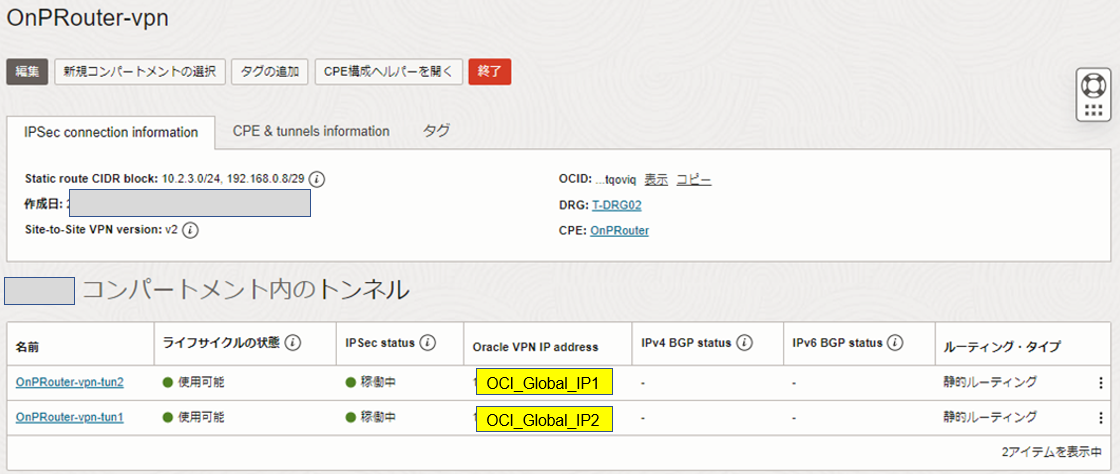
ネットワーキング>>顧客接続性>>サイト間VPN>>作成したVPN
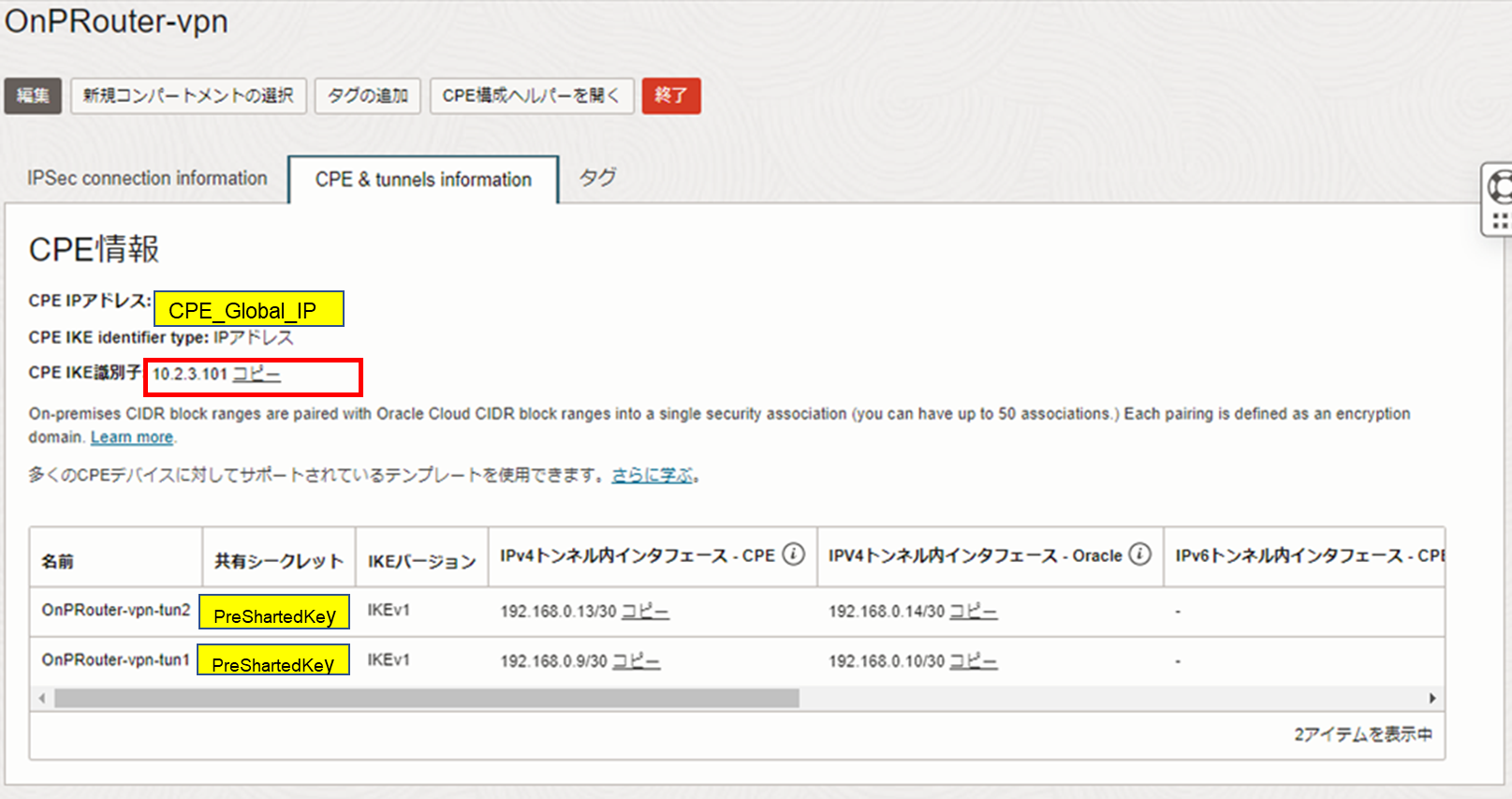
IKE識別子はCPEの機種やネットワーク構成(NAT機器配下にCPEがある)によって異なります。
今回は、CPE LANアドレスをここに指定します
ネットワーキング>>顧客接続性>>サイト間VPN>>作成したVPN>>トンネル1
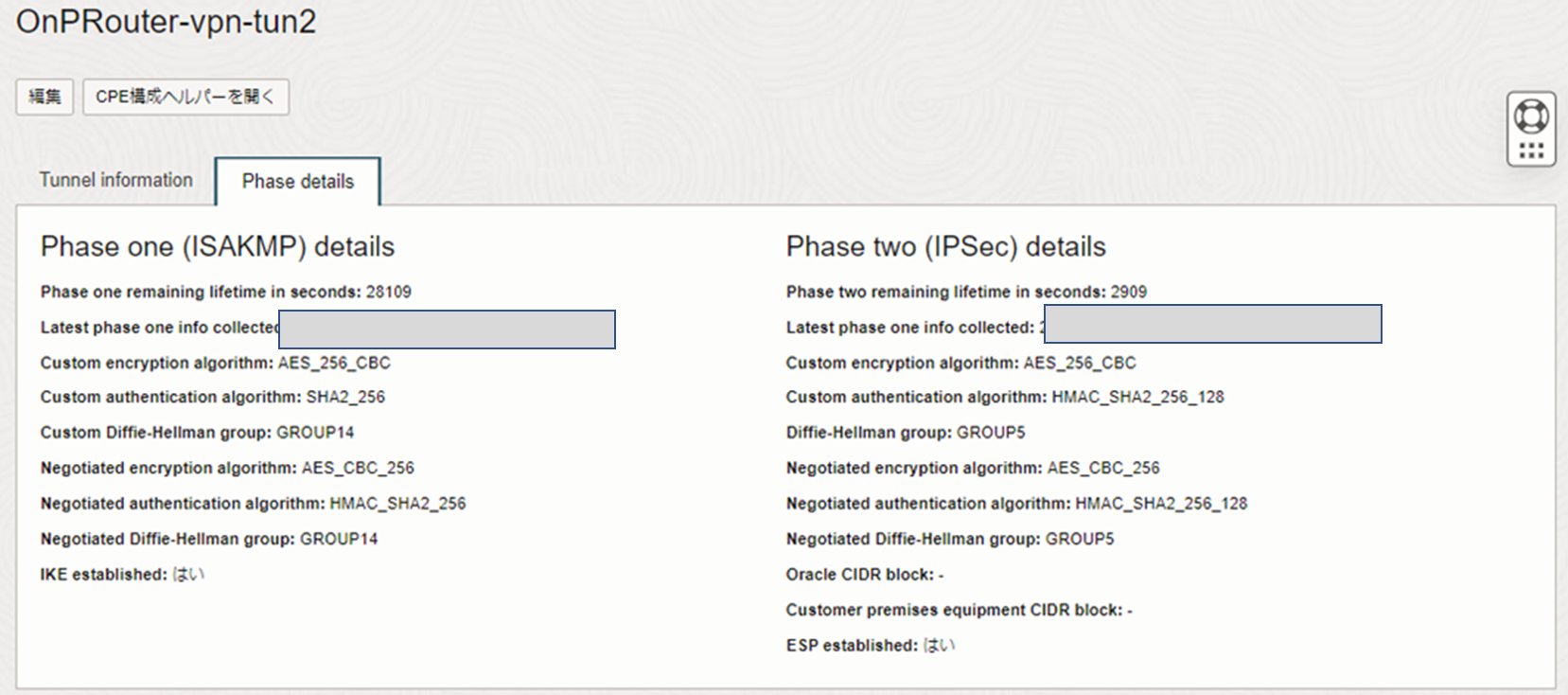
ネットワーキング>>顧客接続性>>サイト間VPN>>作成したVPN>>トンネル2
- Si-R G100
Software VersionはV02.54です。
作成については以下のサイトをご参照ください。
拠点間VPNゲートウェイ:IKEv1 IPsec VTI VPN (L3VPN)で接続する拠点側VPN装置の設定(富士通 Si-R G)
https://pfs.nifcloud.com/guide/cp/vpngw/cn_g110_vti_ikev1.htm
ここでは作成済みの設定となります。
Si-R G100(config)# show running-config
ether 1 1 vlan untag 1
ether 2 1 vlan untag 2
ether 2 2 vlan untag 2
ether 2 3 vlan untag 2
ether 2 4 vlan untag 2
lan 1 ip address 10.2.3.101/24 3
lan 1 vlan 2
!インターネットはPPPoEによる接続
remote 0 name PPPoE
remote 0 mtu 1454
remote 0 ap 0 name PPPoE
remote 0 ap 0 datalink bind vlan 1
remote 0 ap 0 ppp auth send 【PPPoEユーザーID】【PPPoEユーザーパスワード】 encrypted
remote 0 ap 0 keep connect
remote 0 ppp ipcp vjcomp disable
remote 0 ip route 0 default 1 1
remote 0 ip nat mode multi any 1 5m
remote 0 ip nat static 0 10.2.3.101 4500 any 4500 17
remote 0 ip nat static 1 10.2.3.101 500 any 500 17
remote 0 ip nat static 2 10.2.3.101 any any any 50
remote 0 ip nat wellknown 0 500 off
remote 0 ip msschange 1414
remote 1 name ipsec1
remote 1 ap 0 name ipsec1
remote 1 ap 0 datalink type ipsec
remote 1 ap 0 keep connect
remote 1 ap 0 ipsec type ike
remote 1 ap 0 ipsec ike protocol esp
remote 1 ap 0 ipsec ike encrypt aes-cbc-256
remote 1 ap 0 ipsec ike auth hmac-sha256
remote 1 ap 0 ipsec ike pfs modp1536
remote 1 ap 0 ipsec ike lifetime 10m
remote 1 ap 0 ipsec ike esn disable
remote 1 ap 0 ike shared key text 【PreShartedKey】 encrypted
remote 1 ap 0 ike proposal 0 encrypt aes-cbc-256
remote 1 ap 0 ike proposal 0 hash hmac-sha256
remote 1 ap 0 ike proposal 0 pfs modp2048
remote 1 ap 0 ike proposal 0 lifetime 12m
remote 1 ap 0 ike dpd use on
remote 1 ap 0 tunnel local 10.2.3.101
remote 1 ap 0 tunnel remote 【OCI_Global_IP1】
remote 1 ip address local 192.168.0.9
remote 1 ip address remote 192.168.0.10
remote 1 ip route 0 10.0.0.0/25 1 1
remote 1 ip msschange 1300
remote 2 name ipsec2
remote 2 ap 0 name ipsec2
remote 2 ap 0 datalink type ipsec
remote 2 ap 0 keep connect
remote 2 ap 0 ipsec type ike
remote 2 ap 0 ipsec ike protocol esp
remote 2 ap 0 ipsec ike encrypt aes-cbc-256
remote 2 ap 0 ipsec ike auth hmac-sha256
remote 2 ap 0 ipsec ike pfs modp1536
remote 2 ap 0 ipsec ike lifetime 10m
remote 2 ap 0 ipsec ike esn disable
remote 2 ap 0 ike shared key text 【PreShartedKey】 encrypted
remote 2 ap 0 ike proposal 0 encrypt aes-cbc-256
remote 2 ap 0 ike proposal 0 hash hmac-sha256
remote 2 ap 0 ike proposal 0 pfs modp2048
remote 2 ap 0 ike proposal 0 lifetime 12m
remote 2 ap 0 ike dpd use on
remote 2 ap 0 tunnel local 10.2.3.101
remote 2 ap 0 tunnel remote 【OCI_Global_IP2】
remote 2 ip address local 192.168.0.13
remote 2 ip address remote 192.168.0.14
remote 2 ip route 0 10.0.0.0/25 10 10
routemanage ip redist bgp static on
routemanage ip redist bgp connected on
syslog facility 23
time auto server 0.0.0.0 dhcp
time zone 0900
proxydns domain 0 any * any to 0
proxydns address 0 any to 0
resource system vlan 4089-4094
consoleinfo autologout 8h
telnetinfo autologout 5m
terminal pager enable
terminal charset SJIS
alias history "show logging command brief"
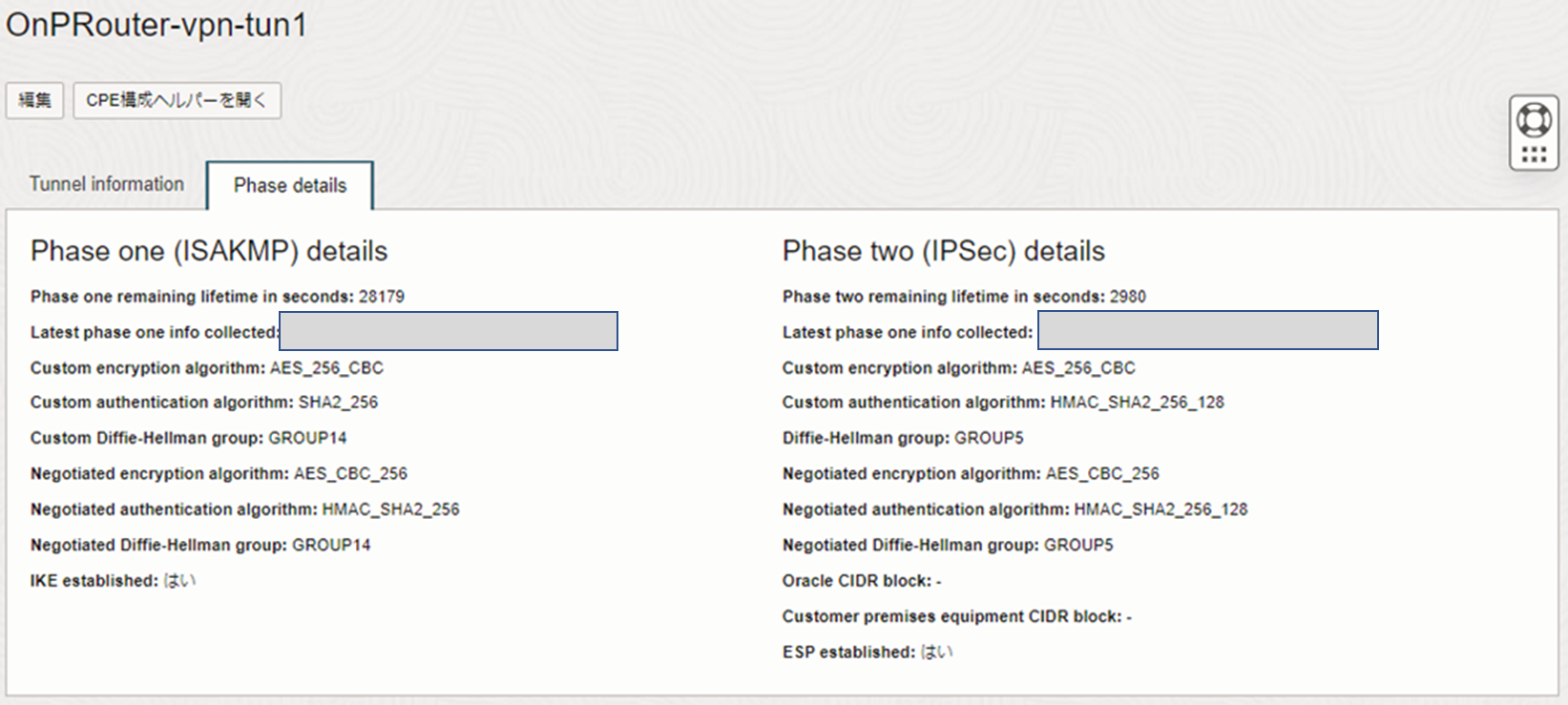
IPSec状況抜粋
Si-R G100(config)# show ipsec sa ike
[IKE SA Information]
[1] Destination(【OCI_Global_IP1】.500), Source(10.2.3.101.500), rmt2
Cookies(b6b21e5329108bc4:f6277f7fcbd440da)
Side(Responder), Status(ESTABLISHED), Exchangetype(MAIN)
IKE Version(1), Authmethod(shared-key), DPD(enable)
Enctype(aes-cbc-256), Hashtype(hmac-sha256), PFS(modp2048)
Created(Mar 16 18:58:16 2023)
Lifetime(28800secs), Current(449secs), Remain(28351secs)
[2] Destination(【OCI_Global_IP2】.500), Source(10.2.3.101.500), rmt1
Cookies(b169bc7d36b6b3c7:c2add2db343d6dcd)
Side(Responder), Status(ESTABLISHED), Exchangetype(MAIN)
IKE Version(1), Authmethod(shared-key), DPD(enable)
Enctype(aes-cbc-256), Hashtype(hmac-sha256), PFS(modp2048)
Created(Mar 16 18:58:15 2023)
Lifetime(28800secs), Current(450secs), Remain(28350secs)
Si-R G100(config)# show ipsec sa protocol
[IPsec SA Information]
[1] Remote Name(ipsec2), rmt2, ap0
Side(Initiator), Gateway(【OCI_Global_IP1】, 10.2.3.101), OUT
Protocol(ESP), Enctype(aes-cbc-256), Authtype(hmac-sha256), PFS(modp1536)
Status(mature), Spi=196539585(0x0bb6f4c1)
Created(Mar 16 18:50:47 2023), NewSA(510secs, 0Kbyte)
Lifetime(600secs), Current(282secs), Remain(318secs)
Lifebyte(0Kbyte), Current(0Kbyte), Remain(0Kbyte)
[2] Remote Name(ipsec2), rmt2, ap0
Side(Initiator), Gateway(10.2.3.101, 【OCI_Global_IP1】), IN
Protocol(ESP), Enctype(aes-cbc-256), Authtype(hmac-sha256), PFS(modp1536)
Status(mature), Spi=195870500(0x0bacbf24)
Created(Mar 16 18:50:47 2023), NewSA(510secs, 0Kbyte)
Lifetime(600secs), Current(282secs), Remain(318secs)
Lifebyte(0Kbyte), Current(0Kbyte), Remain(0Kbyte)
[3] Remote Name(ipsec1), rmt1, ap0
Side(Initiator), Gateway(【OCI_Global_IP2】, 10.2.3.101), OUT
Protocol(ESP), Enctype(aes-cbc-256), Authtype(hmac-sha256), PFS(modp1536
)
Status(mature), Spi=1304837327(0x4dc63ccf)
Created(Mar 16 18:50:47 2023), NewSA(510secs, 0Kbyte)
Lifetime(600secs), Current(282secs), Remain(318secs)
Lifebyte(0Kbyte), Current(0Kbyte), Remain(0Kbyte)
[4] Remote Name(ipsec1), rmt1, ap0
Side(Initiator), Gateway(10.2.3.101, 【OCI_Global_IP2】), IN
Protocol(ESP), Enctype(aes-cbc-256), Authtype(hmac-sha256), PFS(modp1536)
Status(mature), Spi=259779952(0x0f7bed70)
Created(Mar 16 18:50:47 2023), NewSA(510secs, 0Kbyte)
Lifetime(600secs), Current(282secs), Remain(318secs)
Lifebyte(0Kbyte), Current(0Kbyte), Remain(0Kbyte)
- Pingテスト
オンプレサーバーからOCIサーバーへのping結果
Server.
C:\path\to>ping 10.0.0.105
Pinging 10.0.0.105 with 32 bytes of data:
Reply from 10.0.0.105: bytes=32 time=7ms TTL=60
Reply from 10.0.0.105: bytes=32 time=8ms TTL=60
Reply from 10.0.0.105: bytes=32 time=7ms TTL=60
Reply from 10.0.0.105: bytes=32 time=17ms TTL=60
Ping statistics for 10.0.0.105:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 7ms, Maximum = 17ms, Average = 9ms
OCIサーバーからオンプレサーバーへのping結果
Server.
[user@linux ~]$ ping 10.2.3.103
PING 10.2.3.103 (10.2.3.103) 56(84) bytes of data.
64 bytes from 10.2.3.103: icmp_seq=1 ttl=61 time=12.1 ms
64 bytes from 10.2.3.103: icmp_seq=2 ttl=61 time=7.33 ms
64 bytes from 10.2.3.103: icmp_seq=3 ttl=61 time=7.50 ms
64 bytes from 10.2.3.103: icmp_seq=4 ttl=61 time=8.01 ms
^C
--- 10.2.3.103 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 7.332/8.737/12.110/1.966 ms