■目的
重複するNetworkどうしは接続することができません。
プライベートアドレスの重複は、企業の合併やCloud化に伴うOn-PremisesとPublic CloudとのHyblid Cloudによるネットワークの再編等で、 しばしば発生します。
ということでIP変換を行い重複しないように双方向NAT(Twice NAT)で通信できるようにしてみてみます。
Twice NATは、 RFC2663で定義されている用語で、 始点アドレスと終点アドレスの両方を書き換える方式です
この方式を使う典型例は、プライベートアドレスが衝突しているネットワークを扱うときです。
Twice NATは、1台のNATデバイスで「内部の送信元アドレス変換」と「外部の送信元アドレス変換」を同時に行うことができます。
双方向にアドレスが変換されることから、内部ホストも外部ホストの双方ともお互いのIPアドレスを知ることなく通信することが可能です。
■構成

まず順方向で1のディスクリプターを適用し、 その後、逆方向で2のディスクリプターを適用します。
この設定にしたがえば、N1(On-Premises)からはN2(OCI)が10.200.200.0/24に見え、 N2(OCI)からはN1(On-Premises)が10.100.100.0/24に見えるようになります。
例えば、N1(On-Premises)からN2(OCI)に対して、 次のようなパケットを送信すると、
始点アドレス: 192.168.100.2
終点アドレス: 10.200.200.2
N2(OCI)に届くときには、次のように変換されることになります。
始点アドレス: 10.100.100.2
終点アドレス: 192.168.100.2
■事前準備
YAMAHA NVR700wを使用してOracle Cloud にIPsec VPN接続しておきます。
・参考:YAMAHA NVR700wでOCIへIPsec VPN接続してみてみた
■NVR700W手順
●Twice NAT設定
「reverse」は、 NATディスクリプターを逆方向に適用するキーワードです
「reverse」を使用してNATディスクリプターを双方向で適用させる場合は、 順方向と逆方向の両側のNATディスクリプターのタイプを「nat」にする必要があり、IPSecのTunnelに順方向で1のディスクリプターを適用し、 その後、逆方向で2のディスクリプターを適用します
tunnel select 1
ip tunnel nat descriptor 1 reverse 2
tunnel select 2
ip tunnel nat descriptor 1 reverse 2
nat descriptor type 1 nat
nat descriptor address outer 1 10.200.200.1-10.200.200.254
nat descriptor static 1 31000 10.200.200.1=192.168.100.1 254
nat descriptor type 2 nat
nat descriptor address outer 2 10.100.100.1-10.100.100.254
nat descriptor static 2 31000 10.100.100.1=192.168.100.1 254
●Rute追加設定
ip route 10.100.100.0/24 gateway tunnel 1 hide gateway tunnel 2 hide
●Route設定確認
# show ip route
Destination Gateway Interface Kind Additional Info.
default 200.200.200.201 WAN1(PDP) static
10.100.100.0/24 - TUNNEL[1] static
10.100.100.0/24 - TUNNEL[2] static
・・・
192.168.100.0/24 192.168.100.254 LAN1 implicit
■OCI設定
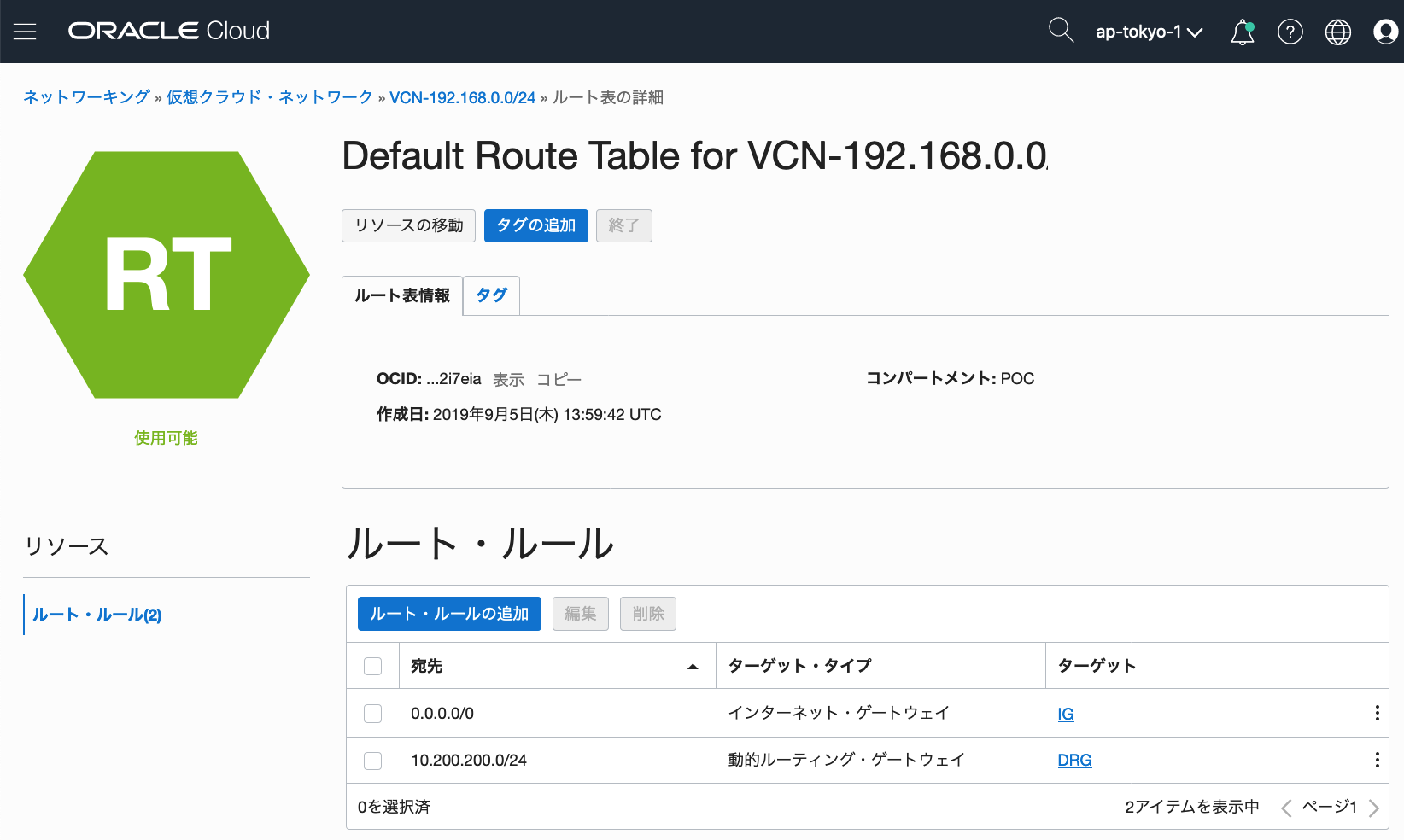
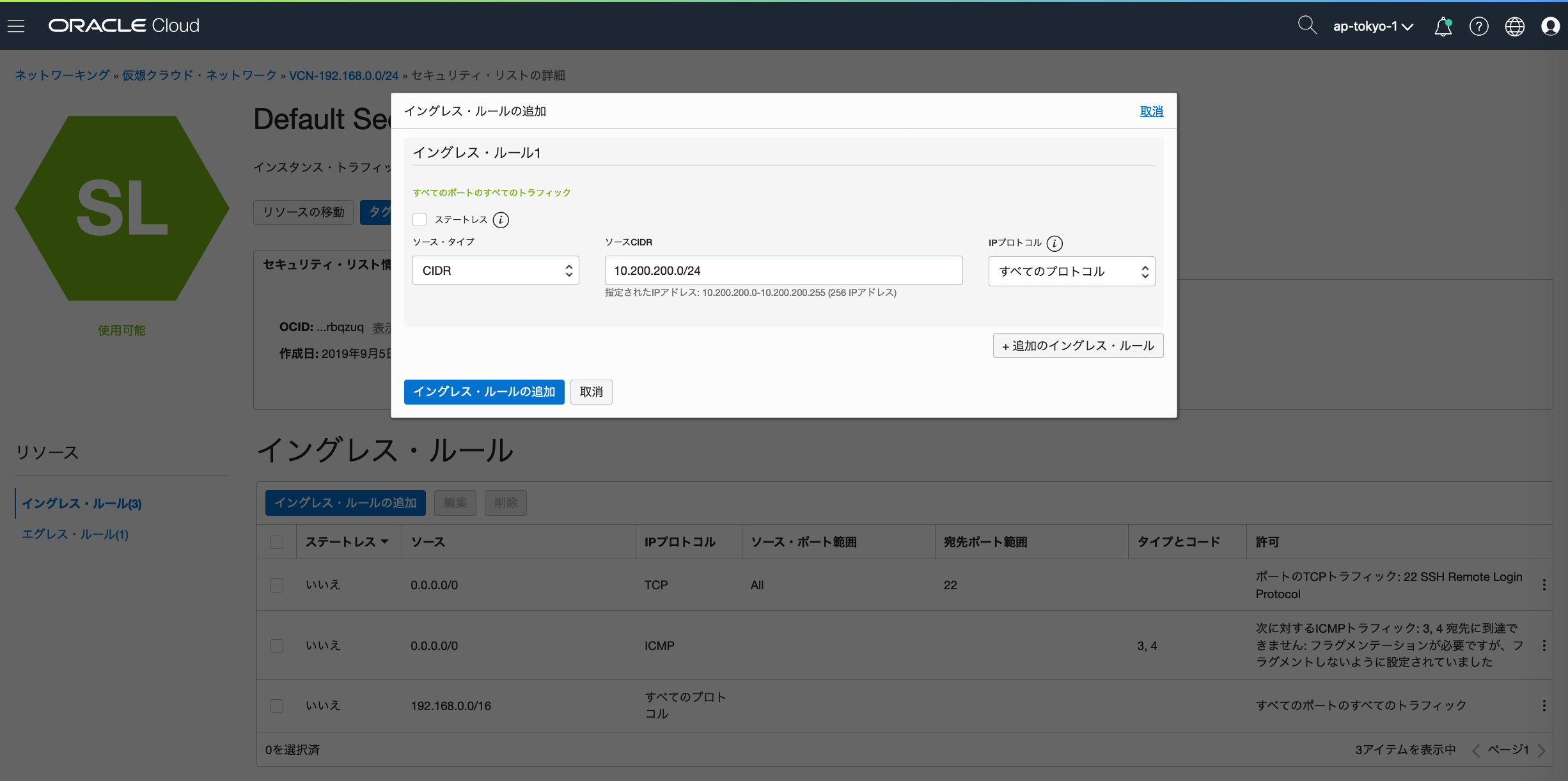
On-Premise側の192.168.100.0/24は10.200.200.0/24に変換されるため、
Route TableとSecurity Listを設定して10.200.200.0/24が疎通できる様に設定
●Route Table設定
●Security List設定
10.200.200.0/24が通る様にFirewallを設定
■接続確認
●On-Premise -> OCI 接続確認
・ping確認
root@onp-inst01:~ $ ping 10.100.100.2 -c 3
PING 10.100.100.2 (10.100.100.2) 56(84) bytes of data.
64 bytes from 10.100.100.2: icmp_seq=1 ttl=62 time=79.6 ms
64 bytes from 10.100.100.2: icmp_seq=2 ttl=62 time=91.8 ms
64 bytes from 10.100.100.2: icmp_seq=3 ttl=62 time=81.7 ms
--- 10.100.100.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 79.670/84.413/91.856/5.338 ms
・ssh接続確認
root@onp-inst01:~ $ ssh -i id_rsa opc@10.100.100.2
The authenticity of host '10.100.100.2 (10.100.100.2)' can't be established.
ECDSA key fingerprint is SHA256:b/NwTgHlSIbcMf/OpndkI+beEyf7TfT1f.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.100.100.2' (ECDSA) to the list of known hosts.
Last login: Sun Sep 8 11:21:47 2019 from 10.200.200.2
[opc@oci-inst01 ~]$ hostname
oci-inst01
●OCI -> On-Premises確認
・ping確認
[opc@oci-inst01 ~]$ ping 10.200.200.2 -c 3
PING 10.200.200.2 (10.200.200.2) 56(84) bytes of data.
64 bytes from 10.200.200.2: icmp_seq=1 ttl=62 time=109 ms
64 bytes from 10.200.200.2: icmp_seq=2 ttl=62 time=101 ms
64 bytes from 10.200.200.2: icmp_seq=3 ttl=62 time=113 ms
--- 10.200.200.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 101.981/108.291/113.045/4.648 ms
・ssh接続確認
[opc@oci-inst01 ~]$ ssh root@10.200.200.2
The authenticity of host '10.200.200.2 (10.200.200.2)' can't be established.
ECDSA key fingerprint is SHA256:IyO/duiavlgoauEpbkK35CP3QT9QF.
ECDSA key fingerprint is MD5:2e:2b:3c:5c:68:e3:34:80:a2:5b:e7.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.200.200.2' (ECDSA) to the list of known hosts.
root@10.200.200.2's password:
Linux onp-inst01 4.14.79-v7+ #1159 SMP Sun Nov 4 17:50:20 GMT 2018 armv7l
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Sep 8 23:08:09 2019 from 192.168.100.2
pi@onp-inst01:~ $ hostname
onp-inst01
■参考
●Config
# show config
# NVR700W Rev.15.00.16 (Thu Jun 20 19:48:42 2019)
# MAC Address : 00:a0:ef:a1, 00:a0:de:e7:59:45
# Memory 256Mbytes, 2LAN, 1ONU, 1WWAN
# main: NVR700W ver=00 serial=NVR700W MAC-Address=00:a0:ef:a1 MAC-Addr
ess=00:a0:ef:a2
# Reporting Date: Sep 8 20:25:23 2019
hboard,lan-map,config login-timer=300
console character en.ascii
ip route default gateway pdp wan1
ip route 10.100.100.0/24 gateway tunnel 1 hide gateway tunnel 2 hide
ip lan1 address 192.168.100.254/24
ip wan1 address pdp
ip wan1 secure filter in 300003 300020 300021 300022 300023 300024 300025 30003
0 300032
ip wan1 secure filter out 300013 300020 300021 300022 300023 300024 300025 3000
26 300027 300099 dynamic 300080 300081 300082 300083 300084 300085 300098 30009
9
ip wan1 nat descriptor 31000
wan1 bind wwan 1
wwan select 1
description wwan AION
wwan always-on on
wwan auth accept chap
wwan auth myname aion@aion sim
wwan auto connect on
wwan disconnect time off
wwan disconnect input time off
wwan disconnect output time off
wwan access-point name 4gn.jp
wwan access limit length off
wwan access limit time off
wwan enable 1
tunnel select 1
description tunnel OCI-VPN1
ipsec tunnel 1
ipsec sa policy 1 1 esp aes256-cbc sha-hmac
ipsec ike duration ipsec-sa 1 3600
ipsec ike duration isakmp-sa 1 28800
ipsec ike encryption 1 aes256-cbc
ipsec ike group 1 modp1536
ipsec ike hash 1 sha256
ipsec ike keepalive log 1 off
ipsec ike keepalive use 1 on dpd 5 4
ipsec ike local address 1 200.200.200.201
ipsec ike local id 1 0.0.0.0/0
ipsec ike nat-traversal 1 on
ipsec ike pfs 1 on
ipsec ike pre-shared-key 1 text IPSecPassword
ipsec ike remote address 1 100.100.100.101
ipsec ike remote id 1 0.0.0.0/0
ip tunnel address 192.168.0.101/30
ip tunnel remote address 192.168.0.102
ip tunnel nat descriptor 1 reverse 2
ip tunnel tcp mss limit auto
tunnel enable 1
tunnel select 2
description tunnel OCI-VPN2
ipsec tunnel 2
ipsec sa policy 2 2 esp aes256-cbc sha-hmac
ipsec ike duration ipsec-sa 2 3600
ipsec ike duration isakmp-sa 2 28800
ipsec ike encryption 2 aes256-cbc
ipsec ike group 2 modp1536
ipsec ike hash 2 sha256
ipsec ike keepalive log 2 off
ipsec ike keepalive use 2 on dpd 5 4
ipsec ike local address 2 200.200.200.201
ipsec ike local id 2 0.0.0.0/0
ipsec ike nat-traversal 2 on
ipsec ike pfs 2 on
ipsec ike pre-shared-key 2 text IPSecPassword
ipsec ike remote address 2 100.100.100.102
ipsec ike remote id 2 0.0.0.0/0
ip tunnel address 192.168.0.105/30
ip tunnel remote address 192.168.0.106
ip tunnel nat descriptor 1 reverse 2
ip tunnel tcp mss limit auto
tunnel enable 2
ip filter 300000 reject 10.0.0.0/8 * * * *
ip filter 300001 reject 172.16.0.0/12 * * * *
ip filter 300002 reject 192.168.0.0/16 * * * *
ip filter 300003 reject 192.168.100.0/24 * * * *
ip filter 300010 reject * 10.0.0.0/8 * * *
ip filter 300011 reject * 172.16.0.0/12 * * *
ip filter 300012 reject * 192.168.0.0/16 * * *
ip filter 300013 reject * 192.168.100.0/24 * * *
ip filter 300020 reject * * udp,tcp 135 *
ip filter 300021 reject * * udp,tcp * 135
ip filter 300022 reject * * udp,tcp netbios_ns-netbios_ssn *
ip filter 300023 reject * * udp,tcp * netbios_ns-netbios_ssn
ip filter 300024 reject * * udp,tcp 445 *
ip filter 300025 reject * * udp,tcp * 445
ip filter 300026 restrict * * tcpfin * www,21,nntp
ip filter 300027 restrict * * tcprst * www,21,nntp
ip filter 300030 pass * 192.168.100.0/24 icmp * *
ip filter 300031 pass * 192.168.100.0/24 established * *
ip filter 300032 pass * 192.168.100.0/24 tcp * ident
ip filter 300033 pass * 192.168.100.0/24 tcp ftpdata *
ip filter 300034 pass * 192.168.100.0/24 tcp,udp * domain
ip filter 300035 pass * 192.168.100.0/24 udp domain *
ip filter 300036 pass * 192.168.100.0/24 udp * ntp
ip filter 300037 pass * 192.168.100.0/24 udp ntp *
ip filter 300099 pass * * * * *
ip filter 500000 restrict * * * * *
ip filter dynamic 300080 * * ftp
ip filter dynamic 300081 * * domain
ip filter dynamic 300082 * * www
ip filter dynamic 300083 * * smtp
ip filter dynamic 300084 * * pop3
ip filter dynamic 300085 * * submission
ip filter dynamic 300098 * * tcp
ip filter dynamic 300099 * * udp
nat descriptor type 1 nat
nat descriptor address outer 1 10.200.200.1-10.200.200.254
nat descriptor static 1 31000 10.200.200.1=192.168.100.1 254
nat descriptor type 2 nat
nat descriptor address outer 2 10.100.100.1-10.100.100.254
nat descriptor static 2 31000 10.100.100.1=192.168.100.1 254
nat descriptor type 31000 masquerade
nat descriptor address outer 31000 primary
nat descriptor masquerade static 31000 1 192.168.100.254 udp 500
nat descriptor masquerade static 31000 2 192.168.100.254 esp
ipsec auto refresh on
telnetd service off
dhcp service server
dhcp server rfc2131 compliant except remain-silent
dhcp scope 1 192.168.100.2-192.168.100.249/24
dns host lan1
dns server pdp wan1
dns server select 500401 pdp wan1 any .
dns private address spoof on
dns private name setup.netvolante.jp
analog supplementary-service pseudo call-waiting
analog extension dial prefix sip prefix="9#"
sshd service on
sshd host key generate *
statistics traffic on
wwan-module use on
●資料
・ヤマハネットワーク機器の技術資料:Twice NAT機能
・Twice NAT機能を利用した拠点間接続 : コマンド設定