■ 目的
動的ルーティングのBGP(Border Gateway Protocol)は相互接続で動的にお互いの経路情報をやり取りするために使われる経路制御プロトコルです。
このBGPでOracle Cloud Infrastructure(OCI)へIPSec接続を行いルート情報が伝搬され、オンプレミス,OCIそれぞれのインスタンスが疎通できることを確認します。
ということで、前回設定した YAMAHA NVR700w で OCI へ IPsec VPN 接続した構成を使用して BGP の設定をしてみてみます。
■ 構成図
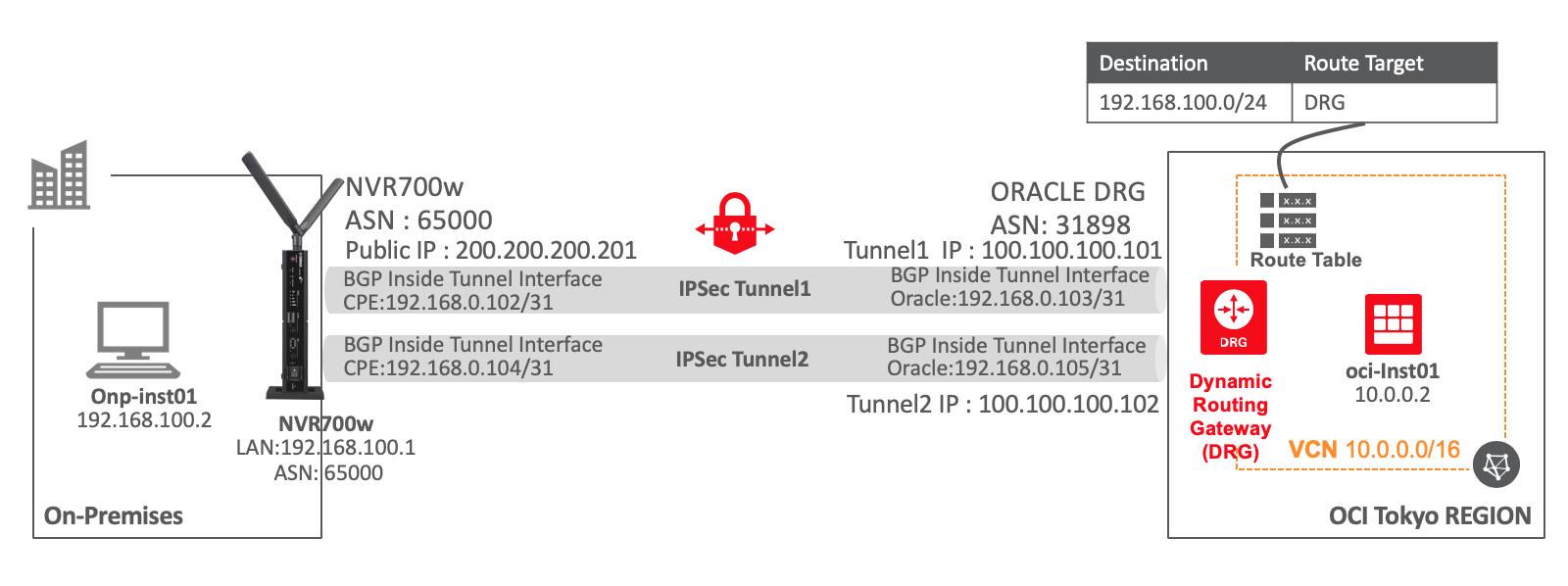
● 手順概要
IPSec接続までは静的ルーティングの手順と同じで、静的ルーティング部分をBGP設定に変更します。
・参考:Oracle Cloud:YAMAHA NVR700wでOCIへIPsec VPN接続してみてみた
■ OCI側IPSecとBGP設定
● IPSec Connection作成
ここでは静的ルートのStatic Route CIDRは空白のままで設定せずBGPの設定を行います。
・Create IPSec Connection設定画面
CPEオブジェクトを作成するときに指定したCPEのパブリックIPアドレスがIKE IDとして使用されるので、CPEがNAT配下にある場合は、NATで払い出されたVPNルーターのPrivate IPを設定します

・IPSec BGP Tunnel1設定画面
[拡張オプション表示]は不要、自動でYAMAHAルーターと接続するときに適切な値が自動設定されます

・IPSec BGP Tunnel2設定画面
[拡張オプション表示]は不要、自動でYAMAHAルーターと接続するときに適切な値が自動設定されます

■ YAMAHA IPSec設定手順
● NVR700wへLOGIN
・ssh、コンソール接続でLOGIN
root@onp-inst01:~ # ssh root@192.168.100.1
root@192.168.100.1's password:
>
・管理ユーザーへ移行
> administrator
Password:
There are changed configuration unsaved in nonvolatile memory!
The administrator password is factory default setting. Please change the password by the 'administrator password' command.
#
● NAT設定
nat descriptor type 1000 masquerade
nat descriptor address outer 1000 200.200.200.201
nat descriptor masquerade static 1000 1 192.168.100.1 udp 500
nat descriptor masquerade static 1000 2 192.168.100.1 esp
● IPSec接続設定
以下のように設定
・ Tunnel1設定
tunnel select 1
description tunnel OCI-VPN1
ipsec tunnel 1
ipsec sa policy 1 1 esp aes256-cbc sha256-hmac
ipsec ike duration ipsec-sa 1 3600
ipsec ike duration isakmp-sa 1 28800
ipsec ike encryption 1 aes256-cbc
ipsec ike group 1 modp1536
ipsec ike hash 1 sha256
ipsec ike keepalive log 1 off
ipsec ike keepalive use 1 on dpd 5 4
ipsec ike local address 1 200.200.200.201
ipsec ike local id 1 0.0.0.0/0
ipsec ike nat-traversal 1 on
ipsec ike pfs 1 on
ipsec ike pre-shared-key 1 text ipsecNVR700wSecretKey01
ipsec ike remote address 1 100.100.100.101
ipsec ike remote id 1 0.0.0.0/0
ip tunnel tcp mss limit auto
tunnel enable 1
・ Tunnel2設定
tunnel select 2
description tunnel OCI-VPN2
ipsec tunnel 2
ipsec sa policy 2 2 esp aes256-cbc sha256-hmac
ipsec ike duration ipsec-sa 2 3600
ipsec ike duration isakmp-sa 2 28800
ipsec ike encryption 2 aes256-cbc
ipsec ike group 2 modp1536
ipsec ike hash 2 sha256
ipsec ike keepalive log 2 off
ipsec ike keepalive use 2 on dpd 5 4
ipsec ike local address 2 200.200.200.201
ipsec ike local id 2 0.0.0.0/0
ipsec ike nat-traversal 2 on
ipsec ike pfs 2 on
ipsec ike pre-shared-key 2 text ipsecNVR700wSecretKey02
ipsec ike remote address 2 100.100.100.102
ipsec ike remote id 2 0.0.0.0/0
ip tunnel tcp mss limit auto
tunnel enable 2
・ LOOPBACKインタフェース設定
CPE の GlobalアドレスをLOOPBACKインタフェースへ登録
ip loopback1 address 200.200.200.201/32
● IPSec設定反映と確認
tunnel2# ipsec auto refresh on
tunnel2# show ipsec sa
Total: isakmp:2 send:2 recv:3
sa sgw isakmp connection dir life[s] remote-id
----------------------------------------------------------------------------
1 1 - isakmp - 28589 100.100.100.101
2 2 - isakmp - 28634 100.100.100.102
3 1 1 tun[0001]esp send 3391 100.100.100.101
4 1 1 tun[0001]esp recv 3391 100.100.100.101
5 2 2 tun[0002]esp send 3436 100.100.100.102
6 2 - tun[0002]esp recv 3392 100.100.100.102
7 2 2 tun[0002]esp recv 3436 100.100.100.102
■ YAMAHA BGP設定手順
● BGP設定
Oracle Cloud のASN は31898になります
詳細設定は構成図を参考して以下のように設定
tunnel select 1
ip tunnel address 192.168.0.102/31
ip tunnel remote address 192.168.0.103
tunnel select 2
ip tunnel address 192.168.0.104/31
ip tunnel remote address 192.168.0.105
bgp use on
bgp autonomous-system 65000
bgp log neighbor
bgp neighbor 1 31898 192.168.0.103 hold-time=180 local-address=192.168.0.102 ignore-capability=on
bgp neighbor 2 31898 192.168.0.105 hold-time=180 local-address=192.168.0.104 ignore-capability=on
bgp import filter 1 equal 0.0.0.0/0
bgp import 31898 static filter 1
● BGP設定反映と確認
# bgp configure refresh
・BGPの疎通には数十秒は時間がかかります。
BGP stateがIdolからEstablishedになればOKです
# show status bgp neighbor
BGP neighbor is 192.168.0.103, remote AS 31898, local AS 65000, external link
BGP version 4, remote router ID 192.168.0.103
BGP state = Established, up for 00:02:19
Last read 00:00:25, hold time is 180, keepalive interval is 60 seconds
Received 3 messages, 0 notifications, 0 in queue
Sent 8 messages, 1 notifications, 0 in queue
Connection established 1; dropped 0
Last reset never
Local host: 192.168.0.102, Local port: 1027
Foreign host: 192.168.0.103, Foreign port: 179
BGP neighbor is 192.168.0.105, remote AS 31898, local AS 65000, external link
BGP version 4, remote router ID 192.168.0.105
BGP state = Established, up for 00:02:27
Last read 00:00:34, hold time is 180, keepalive interval is 60 seconds
Received 3 messages, 0 notifications, 0 in queue
Sent 8 messages, 1 notifications, 0 in queue
Connection established 1; dropped 0
Last reset never
Local host: 192.168.0.104, Local port: 1026
Foreign host: 192.168.0.105, Foreign port: 179
● ルート伝搬確認
OCI側SubnetのCIDR 10.0.0.0/24がルートに追加されていることを確認
tunnel2# show ip route
Destination Gateway Interface Kind Additional Info.
default - PP[01] static filter:500000
default - PP[01] static
10.0.0.0/24 192.168.0.103 TUNNEL[1] BGP path=31898
192.168.100.0/24 192.168.100.1 LAN1 implicit
192.168.0.102/31 - TUNNEL[1] implicit
192.168.0.104/31 - TUNNEL[2] implicit
・・・
● 設定保存
# save
Saving ... CONFIG0 Done .
● BGP Tunnel Interface IP 疎通確認
BGPトンネル用のIPに対して疎通できることを確認
# ping -c 3 192.168.0.102
received from 192.168.0.102: icmp_seq=0 ttl=255 time=0.028ms
received from 192.168.0.102: icmp_seq=1 ttl=255 time=0.014ms
received from 192.168.0.102: icmp_seq=2 ttl=255 time=0.013ms
3 packets transmitted, 3 packets received, 0.0% packet loss
round-trip min/avg/max = 0.013/0.018/0.028 ms
# ping -c 3 192.168.0.103
received from 192.168.0.103: icmp_seq=0 ttl=63 time=40.989ms
received from 192.168.0.103: icmp_seq=1 ttl=63 time=30.870ms
received from 192.168.0.103: icmp_seq=2 ttl=63 time=20.522ms
3 packets transmitted, 3 packets received, 0.0% packet loss
round-trip min/avg/max = 20.522/30.793/40.989 ms
# ping -c 3 192.168.0.104
received from 192.168.0.104: icmp_seq=0 ttl=255 time=0.019ms
received from 192.168.0.104: icmp_seq=1 ttl=255 time=0.014ms
received from 192.168.0.104: icmp_seq=2 ttl=255 time=0.013ms
3 packets transmitted, 3 packets received, 0.0% packet loss
round-trip min/avg/max = 0.013/0.015/0.019 ms
# ping -c 3 192.168.0.105
received from 192.168.0.105: icmp_seq=0 ttl=63 time=28.160ms
received from 192.168.0.105: icmp_seq=1 ttl=63 time=16.867ms
received from 192.168.0.105: icmp_seq=2 ttl=63 time=19.639ms
3 packets transmitted, 3 packets received, 0.0% packet loss
round-trip min/avg/max = 16.867/21.555/28.160 ms
● OCI画面確認
1) ステータス確認
・ IPsec接続情報
IPSec と BGPの Status がUPしていることを確認

・ CPE/Tunnel情報
CPE と Tunnel情報を確認できます

2) Tunnel01確認
・ フェーズ詳細
ISAKMP・IPSecポリシーの認証アルゴリズム、Diffie-Hellmanグループなどパラメータが設定されていることを確認できます

3) Tunnel02確認
・フェーズ詳細
ISAKMP・IPSecポリシーの認証アルゴリズム、Diffie-Hellmanグループなどパラメータが設定されていることを確認できます

■ インスタンス疎通確認
● OCIインスタンス -> オンプレミス インスタンス疎通確認
・ ping疎通確認
[opc@oci-inst01 ~]$ ping -c 3 192.168.100.2
PING 192.168.100.2 (192.168.100.2) 56(84) bytes of data.
64 bytes from 192.168.100.2: icmp_seq=1 ttl=62 time=6.56 ms
64 bytes from 192.168.100.2: icmp_seq=2 ttl=62 time=4.73 ms
64 bytes from 192.168.100.2: icmp_seq=3 ttl=62 time=7.83 ms
--- 192.168.100.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 4.736/6.380/7.836/1.272 ms
・ ssh疎通確認
sshでホスト名が出力されることを確認
[opc@oci-inst01 ~]$ ssh onp-inst01@192.168.100.2 hostname
The authenticity of host '192.168.100.2 (192.168.100.2)' can't be established.
ECDSA key fingerprint is SHA256:IyO/gHz8uoauFpQFb7zZHgWRD4.
ECDSA key fingerprint is MD5:5e:2c:5d:79::fb:22.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.2' (ECDSA) to the list of known hosts.
onp-inst@192.168.100.2's password:
onp-inst01
● オンプレミス インスタンス -> OCIインスタンス疎通確認
・ ping疎通確認
root@onp-inst01:~ # ping -c 3 10.0.0.2
PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data.
64 bytes from 10.0.0.2: icmp_seq=1 ttl=62 time=19.6 ms
64 bytes from 10.0.0.2: icmp_seq=2 ttl=62 time=4.42 ms
64 bytes from 10.0.0.2: icmp_seq=3 ttl=62 time=13.9 ms
--- 10.0.0.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 4.426/12.683/19.668/6.287 ms
・ ssh確認
sshでホスト名が出力されることを確認
root@onp-inst01:~ # ssh -i id_rsa opc@10.0.0.2 hostname
The authenticity of host '10.0.0.2 (10.0.0.2)' can't be established.
ECDSA key fingerprint is SHA256:GfDmeI//qisrVVjZWJAtSouA.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.0.0.2' (ECDSA) to the list of known hosts.
oci-inst01
■ NVR700w Config
NVR700wの最終コンフィグ
# show config
# NVR700W Rev.15.00.23 (Mon Jun 13 12:40:35 2022)
# MAC Address : 00:a0:de:e7:31, 00:a0:de:e7:32
# Memory 256Mbytes, 2LAN, 1ONU, 1WWAN
# main: NVR700W ver=00 serial=M4Y00000 MAC-Address=00:a0:de:e7:31 MAC-Address=00:a0:de:e7:32
# Reporting Date: Dec 11 11:41:37 2022
console character en.ascii
ip route default gateway pdp wan1
ip lan1 address 192.168.100.1/24
ip wan1 address pdp
ip wan1 nat descriptor 31000
wan1 bind wwan 1
wwan select 1
description wwan NTT
wwan always-on on
wwan auth accept chap
wwan auth myname sim@ntt sim
wwan auto connect on
wwan disconnect time off
wwan disconnect input time off
wwan disconnect output time off
wwan access-point name ntt.jp
wwan access limit length off
wwan access limit time off
wwan enable 1
tunnel select 1
description tunnel OCI-VPN1
ipsec tunnel 1
ipsec sa policy 1 1 esp aes256-cbc sha256-hmac
ipsec ike duration ipsec-sa 1 3600
ipsec ike duration isakmp-sa 1 28800
ipsec ike encryption 1 aes256-cbc
ipsec ike group 1 modp1536
ipsec ike hash 1 sha256
ipsec ike keepalive log 1 off
ipsec ike keepalive use 1 on dpd 5 4
ipsec ike local address 1 200.200.200.201
ipsec ike local id 1 0.0.0.0/0
ipsec ike nat-traversal 1 on
ipsec ike pfs 1 on
ipsec ike pre-shared-key 1 text Tunnel01IPSecPasswd
ipsec ike remote address 1 100.100.100.101
ipsec ike remote id 1 0.0.0.0/0
ip tunnel address 192.168.0.102/31
ip tunnel remote address 192.168.0.103
ip tunnel tcp mss limit auto
tunnel enable 1
tunnel select 2
description tunnel OCI-VPN2
ipsec tunnel 2
ipsec sa policy 2 2 esp aes256-cbc sha256-hmac
ipsec ike duration ipsec-sa 2 3600
ipsec ike duration isakmp-sa 2 28800
ipsec ike encryption 2 aes256-cbc
ipsec ike group 2 modp1536
ipsec ike hash 2 sha256
ipsec ike keepalive log 2 off
ipsec ike keepalive use 2 on dpd 5 4
ipsec ike local address 2 200.200.200.201
ipsec ike local id 2 0.0.0.0/0
ipsec ike nat-traversal 2 on
ipsec ike pfs 2 on
ipsec ike pre-shared-key 2 text Tunnel02IPSecPasswd
ipsec ike remote address 2 100.100.100.102
ipsec ike remote id 2 0.0.0.0/0
ip tunnel address 192.168.0.104/31
ip tunnel remote address 192.168.0.105
ip tunnel tcp mss limit auto
tunnel enable 2
ip loopback1 address 200.200.200.201/32
ip filter 500000 restrict * * * * *
nat descriptor type 31000 masquerade
nat descriptor address outer 31000 primary
bgp use on
bgp autonomous-system 65000
bgp log neighbor
bgp neighbor 1 31898 192.168.0.103 hold-time=30 local-address=192.168.0.102 ignore-capability=on
bgp neighbor 2 31898 192.168.0.105 hold-time=30 local-address=192.168.0.104 ignore-capability=on
bgp import filter 1 equal 0.0.0.0/0
bgp import 31898 static filter 1
ipsec auto refresh on
telnetd host lan
dhcp service server
dhcp server rfc2131 compliant except remain-silent
dhcp scope 1 192.168.100.2-192.168.100.191/24
dns host lan1
dns server pdp wan1
dns server select 500401 pdp wan1 any .
dns private address spoof on
dns private name setup.netvolante.jp
analog supplementary-service pseudo call-waiting
analog extension dial prefix sip prefix="9#"
wwan-module use on
■ 参考
・ Oracle Cloud Infrastructureドキュメント
- サイト間VPN
- CPE構成
- ヤマハRTXシリーズ
・ YAMAHAドキュメント
- Oracle Cloud InfrastructureとVPN(IPsec)接続するルーターの設定 : コマンド設定
- ヤマハネットワーク機器の技術資料
- LOOPBACK、NULLインタフェース

