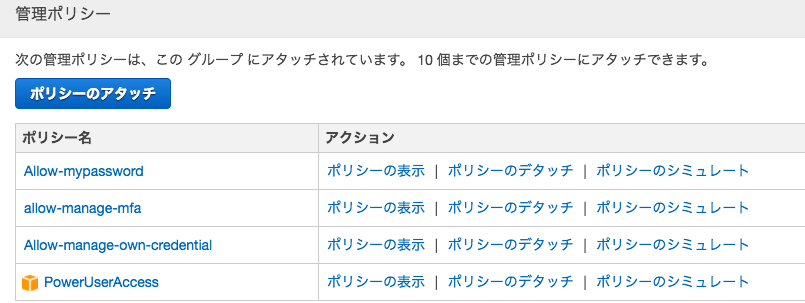
勉強用の共有アカウントでadminより弱い(PowerUser)けど
MFA設定+自分のアクセスキーの発行・更新+パスワードの変更ができるユーザーが作りたかったのでネットを漁って設定を探した
-グループを作成
Allow-mypassword
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "iam:GetAccountPasswordPolicy",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "iam:ChangePassword",
"Resource": "arn:aws:iam::*:user/${aws:username}"
}
]
}
allow-manage-mfa
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowUsersToCreateDeleteTheirOwnVirtualMFADevices",
"Effect": "Allow",
"Action": [
"iam:*VirtualMFADevice"
],
"Resource": [
"arn:aws:iam::*:mfa/${aws:username}"
]
},
{
"Sid": "AllowUsersToEnableSyncDisableTheirOwnMFADevices",
"Effect": "Allow",
"Action": [
"iam:DeactivateMFADevice",
"iam:EnableMFADevice",
"iam:ListMFADevices",
"iam:ResyncMFADevice"
],
"Resource": [
"arn:aws:iam::*:user/${aws:username}"
]
},
{
"Sid": "AllowUsersToListVirtualMFADevices",
"Effect": "Allow",
"Action": [
"iam:ListVirtualMFADevices"
],
"Resource": [
"arn:aws:iam::*:mfa/*"
]
},
{
"Sid": "AllowUsersToListUsersInConsole",
"Effect": "Allow",
"Action": [
"iam:ListUsers"
],
"Resource": [
"arn:aws:iam::*:user/*"
]
}
]
}
allow-manage-own-credential
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowUsersAllActionsForCredentials",
"Effect": "Allow",
"Action": [
"iam:*LoginProfile",
"iam:*AccessKey*",
"iam:*SigningCertificate*"
],
"Resource": [
"arn:aws:iam::*:user/${aws:username}"
]
},
{
"Sid": "AllowUsersToSeeStatsOnIAMConsoleDashboard",
"Effect": "Allow",
"Action": [
"iam:GetAccount*",
"iam:ListAccount*"
],
"Resource": [
"*"
]
},
{
"Sid": "AllowUsersToListUsersInConsole",
"Effect": "Allow",
"Action": [
"iam:ListUsers"
],
"Resource": [
"arn:aws:iam::*:user/*"
]
}
]
}
まだうまく行くかは試していない(見た目は大丈夫そう)
これから実際に配布して使って貰う予定
→使ってみたらやりたいことは一応できたが、やりたかったECSのクラスター作成がポリシーのアタッチができないのでコケた。のでもう一つポリシーのアタッチをできるポリシーを追加した。
allow-manage-policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iam:Get*",
"iam:List*",
"iam:PassRole",
"iam:CreateRole",
"iam:CreateInstanceProfile",
"iam:AddRoleToInstanceProfile",
"iam:AttachRolePolicy"
],
"Resource": "*"
}
]
}
やりたかったこと、何人かのユーザに個別ユーザでログインさせて、自分のパス変更、MFA設定、アクセスキーの発行をさせて、それからECSのクラスターで色々テストをしてほしかった。