VPCトラフィクミラーリングでネットワークトラフィックを検査する。
EC2を2インスタンス使用して、片方のネットワーク利用をもう片方でモニタする。
概要についての簡単な説明は↓を参考にさせていただきました。
【初心者】AWS VPC Traffic Mirroring を使ってみる
1.CloudFormationによる環境準備#
AWSTemplateFormatVersion: '2010-09-09'
Description: 'For making 2 of Amazon Linux (EC2) on a VPC. '
Mappings:
AWSInstanceType2Arch:
t3.medium:
Arch: HVM64
t3.micro:
Arch: HVM64
t3.small:
Arch: HVM64
AWSRegionArch2AMI:
ap-northeast-1:
HVM64: ami-0a1c2ec61571737db
us-east-1:
HVM64: ami-0a887e401f7654935
us-west-2:
HVM64: ami-0e8c04af2729ff1bb
Outputs:
AZ01:
Description: Availability Zone of the Client EC2 instance 01
Value: !Join
- ''
- - !GetAtt 'ClientInstance.AvailabilityZone'
AZ02:
Description: Availability Zone of the Client EC2 instance 02
Value: !Join
- ''
- - !GetAtt 'ClientInstance2.AvailabilityZone'
IP01:
Description: Client EC2 IPaddress 01
Value: !Join
- ''
- - !GetAtt 'ClientInstance.PublicIp'
IP02:
Description: Client EC2 IPaddress 02
Value: !Join
- ''
- - !GetAtt 'ClientInstance2.PublicIp'
Parameters:
InstanceType:
AllowedValues:
- t3.micro
- t3.small
- t3.medium
ConstraintDescription: must be a valid EC2 instance type.
Default: t3.small
Description: Amazon Linux instance type
Type: String
SSHLocation:
AllowedPattern: (\d{1,3})\.(\d{1,3})\.(\d{1,3})\.(\d{1,3})/(\d{1,2})
ConstraintDescription: must be a valid IP CIDR range of the form x.x.x.x/x.
Default: '0.0.0.0/0'
Description: ' The IP address range that can be used to SSH to the EC2 instances'
MaxLength: '18'
MinLength: '9'
Type: String
Resources:
AttachGateway:
Properties:
InternetGatewayId: !Ref 'InternetGateway'
VpcId: !Ref 'ClientVPC'
Type: AWS::EC2::VPCGatewayAttachment
ClientInstance:
Properties:
ImageId: !FindInMap
- AWSRegionArch2AMI
- !Ref 'AWS::Region'
- !FindInMap
- AWSInstanceType2Arch
- !Ref 'InstanceType'
- Arch
InstanceType: !Ref 'InstanceType'
NetworkInterfaces:
- AssociatePublicIpAddress: 'true'
DeleteOnTermination: 'true'
DeviceIndex: '0'
GroupSet:
- !Ref 'InstanceSecurityGroup'
SubnetId: !Ref 'ClientSubnet'
Tags:
- Key: Application
Value: !Ref 'AWS::StackId'
- Key: Name
Value: Client01
- Key: Workshop
Value: TrafficMirroring
UserData: !Base64
Fn::Join:
- ''
- - "#!/bin/bash -xe\n"
- "yum update -y\n"
- "amazon-linux-extras install -y epel\n"
- "yum install -y nc\n"
- "\n"
Type: AWS::EC2::Instance
ClientInstance2:
Properties:
ImageId: !FindInMap
- AWSRegionArch2AMI
- !Ref 'AWS::Region'
- !FindInMap
- AWSInstanceType2Arch
- !Ref 'InstanceType'
- Arch
InstanceType: !Ref 'InstanceType'
NetworkInterfaces:
- AssociatePublicIpAddress: 'true'
DeleteOnTermination: 'true'
DeviceIndex: '0'
GroupSet:
- !Ref 'InstanceSecurityGroup'
SubnetId: !Ref 'ClientSubnet'
Tags:
- Key: Application
Value: !Ref 'AWS::StackId'
- Key: Name
Value: Client02
- Key: Workshop
Value: TrafficMirroring
UserData: !Base64
Fn::Join:
- ''
- - "#!/bin/bash -xe\n"
- "yum update -y\n"
- "amazon-linux-extras install -y epel\n"
- "yum install -y wireshark\n"
- "\n"
Type: AWS::EC2::Instance
ClientSubnet:
Properties:
AvailabilityZone: ap-northeast-1c
CidrBlock: 10.100.0.0/24
MapPublicIpOnLaunch: 'true'
Tags:
- Key: Application
Value: !Ref 'AWS::StackId'
- Key: Name
Value: ClientPublic
VpcId: !Ref 'ClientVPC'
Type: AWS::EC2::Subnet
ClientVPC:
Properties:
CidrBlock: 10.100.0.0/16
EnableDnsHostnames: 'true'
EnableDnsSupport: 'true'
Tags:
- Key: Application
Value: !Ref 'AWS::StackId'
- Key: Name
Value: ClientVPC
Type: AWS::EC2::VPC
InboundAllAclEntry:
Properties:
CidrBlock: 10.100.0.0/16
Egress: 'false'
NetworkAclId: !Ref 'NetworkAcl'
Protocol: '-1'
RuleAction: allow
RuleNumber: '120'
Type: AWS::EC2::NetworkAclEntry
InboundResponsePortsNetworkAclEntry:
Properties:
CidrBlock: '0.0.0.0/0'
Egress: 'false'
NetworkAclId: !Ref 'NetworkAcl'
PortRange:
From: '1024'
To: '65535'
Protocol: '6'
RuleAction: allow
RuleNumber: '102'
Type: AWS::EC2::NetworkAclEntry
InboundSSHNetworkAclEntry:
Properties:
CidrBlock: '0.0.0.0/0'
Egress: 'false'
NetworkAclId: !Ref 'NetworkAcl'
PortRange:
From: '22'
To: '22'
Protocol: '6'
RuleAction: allow
RuleNumber: '101'
Type: AWS::EC2::NetworkAclEntry
InstanceSecurityGroup:
Properties:
GroupDescription: Enable SSH access via port 22
SecurityGroupIngress:
- CidrIp: !Ref 'SSHLocation'
FromPort: '22'
IpProtocol: tcp
ToPort: '22'
- CidrIp: 10.100.0.0/16
IpProtocol: '-1'
VpcId: !Ref 'ClientVPC'
Type: AWS::EC2::SecurityGroup
InternetGateway:
Properties:
Tags:
- Key: Application
Value: !Ref 'AWS::StackId'
Type: AWS::EC2::InternetGateway
NetworkAcl:
Properties:
Tags:
- Key: Application
Value: !Ref 'AWS::StackId'
VpcId: !Ref 'ClientVPC'
Type: AWS::EC2::NetworkAcl
OutBoundRDPNetworkAclEntry:
Properties:
CidrBlock: '0.0.0.0/0'
Egress: 'true'
NetworkAclId: !Ref 'NetworkAcl'
Protocol: '-1'
RuleAction: allow
RuleNumber: '100'
Type: AWS::EC2::NetworkAclEntry
Route:
DependsOn: AttachGateway
Properties:
DestinationCidrBlock: '0.0.0.0/0'
GatewayId: !Ref 'InternetGateway'
RouteTableId: !Ref 'RouteTable'
Type: AWS::EC2::Route
RouteTable:
Properties:
Tags:
- Key: Application
Value: !Ref 'AWS::StackId'
VpcId: !Ref 'ClientVPC'
Type: AWS::EC2::RouteTable
SubnetNetworkAclAssociation:
Properties:
NetworkAclId: !Ref 'NetworkAcl'
SubnetId: !Ref 'ClientSubnet'
Type: AWS::EC2::SubnetNetworkAclAssociation
SubnetRouteTableAssociation:
Properties:
RouteTableId: !Ref 'RouteTable'
SubnetId: !Ref 'ClientSubnet'
Type: AWS::EC2::SubnetRouteTableAssociation
2.SSMによる環境準備#
SSMには高速セットアップ機能があります。これを使ってインスタンスのSSM設定の自動構成します。
[新機能] Systems Manager Quick Setup ですばやく設定可能になりました!

3.トラフィックミラーリングの設定#
2つのEC2が記録作成されているはずなので、ネットワークインターフェース eth0の情報を記録しておく。
「ターゲットをミラーリングする」
「ターゲットタイプ:ネットワークインタフェース」で、先に記憶しておいたClient02のENIを選択する。

「フィルターをミラーリングする」
「インバウンド」「アウトバウンド」ルールを次のようにする。
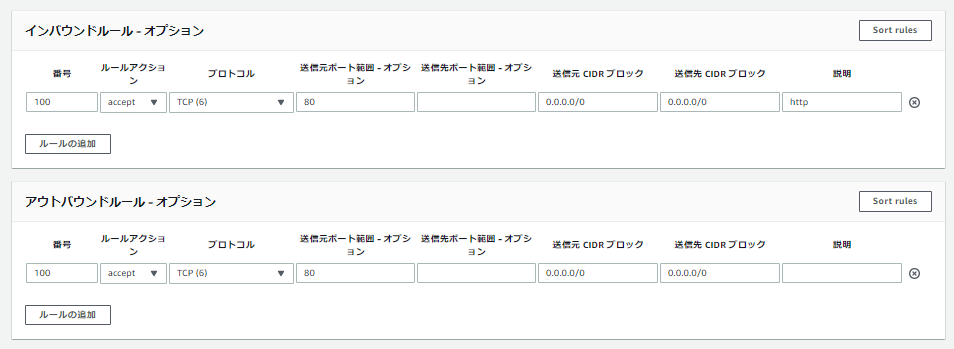
「セッションをミラーリングする」
ミラーソースとして、Client01のENI、ミラーターゲットとして、「ターゲットをミラーリングする」で作ったものを指定。
フィルタはどのパケットをミラーリングするかであり、「フィルターをミラーリングする」で作ったものを指定。

4.EC2でパケットモニタリングする#
Client02で、トラフィックミラーリングでコピーされたパケットを確認しながら、Client01を操作する。
curl checkip.amazonaws.com
sudo tcpdump -i eth0 -n port 4789
cpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:26:56.151185 IP 10.100.0.223.65431 > 10.100.0.177.4789: VXLAN, flags [I] (0x08), vni 7348185
IP 18.209.184.162.http > 10.100.0.223.33962: Flags [S.], seq 2590301871, ack 2020809952, win 26847, options [mss 1460,sackOK,TS val 3553538939 ecr 284377333,nop,wscale 8], length 0
14:26:56.320805 IP 10.100.0.223.65431 > 10.100.0.177.4789: VXLAN, flags [I] (0x08), vni 7348185
IP 18.209.184.162.http > 10.100.0.223.33962: Flags [.], ack 86, win 115, options [nop,nop,TS val 3553539139 ecr 284377503], length 0
14:26:56.321122 IP 10.100.0.223.65431 > 10.100.0.177.4789: VXLAN, flags [I] (0x08), vni 7348185
IP 18.209.184.162.http > 10.100.0.223.33962: Flags [P.], seq 1:141, ack 86, win 115, options [nop,nop,TS val 3553539139 ecr 284377503], length 140: HTTP: HTTP/1.1 200 OK
14:26:56.491205 IP 10.100.0.223.65431 > 10.100.0.177.4789: VXLAN, flags [I] (0x08), vni 7348185
IP 18.209.184.162.http > 10.100.0.223.33962: Flags [F.], seq 141, ack 87, win 115, options [nop,nop,TS val 3553539310 ecr 284377672], length 0
4 packets captured
4 packets received by filter
0 packets dropped by kernel