先日(2016/07/08) Datadogでセキュリティインシデントが発生したとのことです。
AWS Integration の設定について、アクセスキーでの設定ではなく、IAM Roleの委任での設定が推奨されるとの通知がありました。
自環境では IAM User でのデータ収集を行っており、IAM Roleでの設定は行っていなかったので設定を変更しました。
事前準備
IAM Role 作成に必要になる JSON ファイルを準備します。
ポリシーファイル作成
DatadogAWSIntegrationPolicy.json
- IAM role に付与するポリシー群
- 最新情報は以下を参照
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"autoscaling:Describe*",
"cloudtrail:DescribeTrails",
"cloudtrail:GetTrailStatus",
"cloudwatch:Describe*",
"cloudwatch:Get*",
"cloudwatch:List*",
"dynamodb:list*",
"dynamodb:describe*",
"ec2:Describe*",
"ec2:Get*",
"ecs:Describe*",
"ecs:List*",
"elasticache:Describe*",
"elasticache:List*",
"elasticloadbalancing:Describe*",
"elasticmapreduce:List*",
"elasticmapreduce:Describe*",
"kinesis:List*",
"kinesis:Describe*",
"logs:Get*",
"logs:Describe*",
"logs:FilterLogEvents",
"logs:TestMetricFilter",
"rds:Describe*",
"rds:List*",
"route53:List*",
"ses:Get*",
"sns:List*",
"sns:Publish",
"sqs:GetQueueAttributes",
"sqs:ListQueues",
"sqs:ReceiveMessage",
"support:*"
],
"Effect": "Allow",
"Resource": "*"
}
]
}
AssumeRolePolicyDocument.json.base
- Trust Relationships の内容(ID部分は後続手順にて置換)
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::__DDACCOUNTID__:root"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "__DDEXTERNALID__"
}
}
}
]
}
各設定値(名称)
各リソースの名称は以下を使用します。
| 種別 | 名称 |
|---|---|
| PolicyName | DatadogAWSIntegrationPolicy |
| PolicyDocument | DatadogAWSIntegrationPolicy.json |
| RoleName | DatadogAWSIntegrationRole |
| AssumeRolePolicyDocument | AssumeRolePolicyDocument.json |
$ PolicyName="DatadogAWSIntegrationPolicy" ; echo "PolicyName: ${PolicyName}"
PolicyName: DatadogAWSIntegrationPolicy
$ PolicyDocument="DatadogAWSIntegrationPolicy.json" ; echo "PolicyDocument: ${PolicyDocument}"
PolicyDocument: DatadogAWSIntegrationPolicy.json
$ RoleName="DatadogAWSIntegrationRole" ; echo "RoleName: ${RoleName}"
RoleName: DatadogAWSIntegrationRole
$ AssumeRolePolicyDocument="AssumeRolePolicyDocument.json" ; echo "AssumeRolePolicyDocument: ${AssumeRolePolicyDocument}"
AssumeRolePolicyDocument: AssumeRolePolicyDocument.json
IAM role 作成
ポリシー作成
$ aws iam create-policy --policy-name ${PolicyName} --policy-document file://${PolicyDocument}
{
"Policy": {
"PolicyName": "DatadogAWSIntegrationPolicy",
"CreateDate": "2016-07-DDTHH:MM:SS.923Z",
"AttachmentCount": 0,
"IsAttachable": true,
"PolicyId": "ANPXXXXXXXXXXXXXXXXXX",
"DefaultVersionId": "v1",
"Path": "/",
"Arn": "arn:aws:iam::5XXXXXXXXXXX:policy/DatadogAWSIntegrationPolicy",
"UpdateDate": "2016-07-DDTHH:MM:SS.923Z"
}
}
ARN設定
- 上記 create-policy の結果からARNを""部分に設定(もしくはCLIで代入)
$ ARN="arn:aws:iam::5XXXXXXXXXXX:policy/DatadogAWSIntegrationPolicy" ; echo "ARN: ${ARN}"
# CLIで代入
# ARN=$(aws iam list-policies --scope Local | jq -r '.Policies[] | select(.PolicyName == "'${PolicyName}'") | .Arn') ; echo "ARN: ${ARN}"
ARN: arn:aws:iam::5XXXXXXXXXXX:policy/DatadogAWSIntegrationPolicy
Datadogから必要情報を取得
AccountID
- 公式に記載有り
$ DDACID=464622532012 ; echo "DatadogAccountID: ${DDACID}"
DatadogAccountID: 464622532012
ExternalID
- 設定から取得
- Integrations -> AmazonWebService -> Configure

- Add another account -> AWS External ID

- 払い出されたIDを代入
$ DDEXTID="4fXXXXXXXXXXXXXXXXXXXXXXXXXXXX" ; echo "DatadogExternalID: ${DDEXTID}"
DatadogExternalID: 4fXXXXXXXXXXXXXXXXXXXXXXXXXXXX
PolicyDocument.json 生成(置換)
$ sed -e "s%__DDACCOUNTID__%${DDACID}%" -e "s%__DDEXTERNALID__%${DDEXTID}%" ${AssumeRolePolicyDocument}.base > ${AssumeRolePolicyDocument}
diff ${AssumeRolePolicyDocument}.base ${AssumeRolePolicyDocument}
7c7
< "AWS": "arn:aws:iam::__DDACCOUNTID__:root"
---
> "AWS": "arn:aws:iam::464622532012:root"
12c12
< "sts:ExternalId": "__DDEXTERNALID__"
---
> "sts:ExternalId": "4fXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
IAMロール作成
# IAMロール作成
$ aws iam create-role --role-name ${RoleName} --assume-role-policy-document file://${AssumeRolePolicyDocument}
{
"Role": {
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
}
}
]
},
"RoleId": "AROXXXXXXXXXXXXXXXXXX",
"CreateDate": "2016-07-DDTHH:MM:SS.552Z",
"RoleName": "DatadogAWSIntegrationRole",
"Path": "/",
"Arn": "arn:aws:iam::9XXXXXXXXXXX:role/DatadogAWSIntegrationRole"
}
}
# ポリシー付与
$ aws iam attach-role-policy --role-name ${RoleName} --policy-arn ${ARN}
# ポリシー付与確認
$ aws iam list-attached-role-policies --role-name ${RoleName}
{
"AttachedPolicies": [
{
"PolicyName": "DatadogAWSIntegrationPolicy",
"PolicyArn": "arn:aws:iam::5XXXXXXXXXXX:policy/DatadogAWSIntegrationPolicy"
}
]
}
IAM 作成結果
- Policy

- IAM role

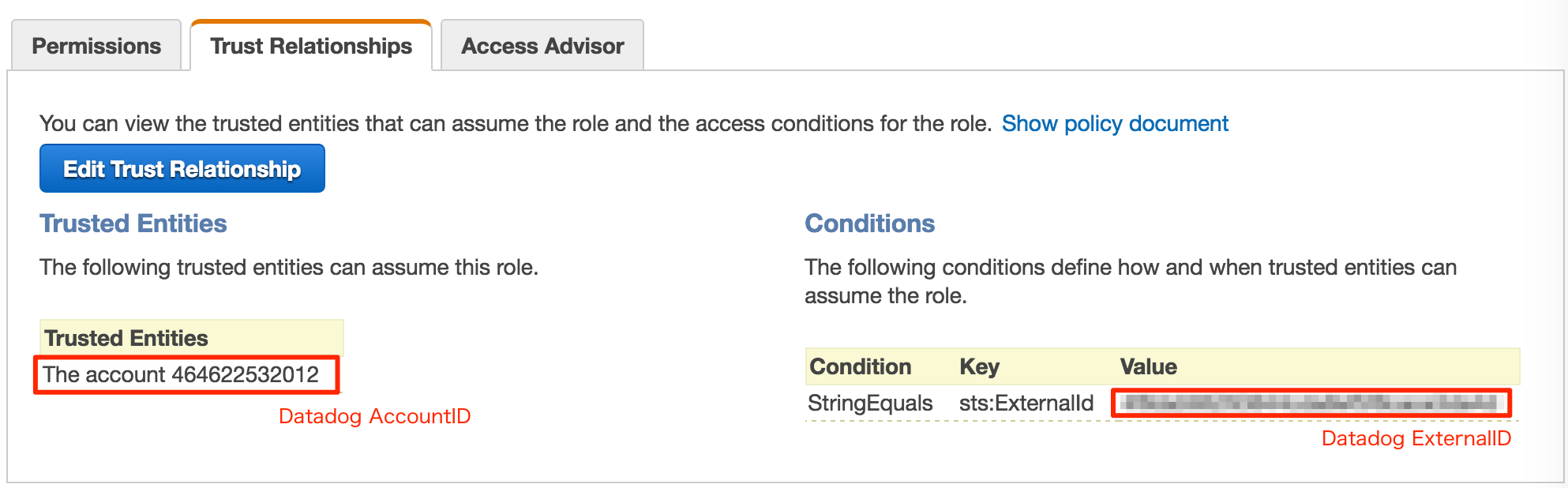
Datadog Integration に設定
- 作成したIAMロールをインテグレーションに設定

結果
対象AWSアカウントからの情報取得が行われます。