はじめに
前回の記事では、HCP Vault RadarとGitHubを連携して、自動でシークレット(パスワードやAPIキーなど)を検出する方法をご紹介しました。
はじめてのHCP Vault Radar① GitHub連携によるシークレット自動検出
はじめてのHCP Vault Radar② GitHubのPull Requestをマージ前にスキャン/シークレット検出
HCP Vault Radarでは、いくつかのスキャン方式を提供しています。
以下は、HCP Vault Radarが提供するスキャン方式の一覧です。
| # | カテゴリ | 説明 |
|---|---|---|
| 1 | HCP Vault Radar Scan | SaaSからの直接スキャン、トライアル環境で設定可能。 |
| 2 | Vault Radar Agent Scan | Agent経由のスキャン、トライアル環境で設定可能。Agentは1つまで構成可能 |
| 3 | Vault Radar CLI Scan | CLIでのスキャン。マニュアルに「Contact your customer success manager to enable HCP Vault Radar or for a license to run the CLI in offline mode.」と記載あるので一部利用できない可能性あり。 |
今回は、#2 Vault Radar Agent Scan 方式のスキャンを試してみました。

1.事前準備(Vaut Radar Agent起動)
HCP Vault Radarの画面で、「Agent」-「Add an agent pool」を選択します。
Agentは1つのみ登録できると注が記載されていました。
Only one agent pool can be registered per HCP project. Future releases will allow multiple agent pools per project.
AgentPoolの名前を入力します。
次に、Agentをインストールするガイドが表示されます。
設定画面ではMacのガイドのみ記載されていました。
xattr -dr com.apple.quarantine ./vault-radar
cp ~/Downloads/vault-radar /usr/local/bin
vault-radar --version
以下のコマンドを使用してUbuntu環境にインストールします。
https://developer.hashicorp.com/hcp/docs/vault-radar/cli#download-and-install-cli
sudo apt update
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo gpg --dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list
sudo apt update && sudo apt install vault-radar -y
$ vault-radar --version
0.29.0, git sha (e019cde569c73711497249d45d7474c843574de4), go1.24.1 amd64
次に、プロジェクトレベルの、Service Principalを登録します。
Vault Radarからプロジェクト画面に移動し、「Access Control(IAM)」をクリックします。

「Serive Principals」-「Create service principal」をクリックします。
Vault Radar Agentロールを割り当てて、「Create service principal」をクリックします。

Service Principalが登録されたら、「Keys」タブをクリックします。

登録されたClient IDとClient Secretをメモします。

ubuntuで、環境変数を指定して、Vault Radar Agentを起動します。

以下の環境変数を設定します。これらはVault Radar Agentの動作に必要な情報です。
export HCP_PROJECT_ID=<画面に表示されたプロジェクトID>
export HCP_RADAR_AGENT_POOL_ID=<画面に表示されたAgentPoolID>
export HCP_CLIENT_ID=<発行したクライアントID>
export HCP_CLIENT_SECRET=<発行したクライアントシークレット>
export VAULT_RADAR_GIT_TOKEN=<前記事で発行したGitHubのパーソナルアクセストークン>
Agentを起動すると、以下のようなログがでます。
$ vault-radar agent exec
time="2025-07-17T09:13:19Z" level=info msg="starting agent" version="0.29.0, git sha (e019cde569c73711497249d45d7474c843574de4), go1.24.1 amd64"
time="2025-07-17T09:13:19Z" level=info msg="with configuration" agent_pool_id=b56c7f01-6ec7-4953-baf9-05168d27e9d9 project_id=905a2fcf-f712-4a2c-ba1d-2901bdc95d10
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_PROXY_ENABLED source=server value=false
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_POLL_COPY_SECRETS_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="loop started" worker="Resource scan job"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="loop started" worker="Content scan job"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="loop started" worker="Pull Request scan job"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="loop started" worker="HTTP job"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_ENABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="config detected" key=AGENT_SERVICE_DISABLE_LIST source=local_default value="<nil>"
time="2025-07-17T09:13:21Z" level=info msg="loop started" worker="Secrets copy job"
time="2025-07-17T09:13:26Z" level=info msg="config detected" key=AGENT_POLL_RESOURCE_SCAN_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:26Z" level=info msg="config detected" key=AGENT_POLL_HTTP_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:27Z" level=info msg="config detected" key=AGENT_POLL_PULL_REQUEST_SCAN_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:27Z" level=info msg="config detected" key=AGENT_POLL_COPY_SECRETS_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:28Z" level=info msg="config detected" key=AGENT_POLL_CONTENT_SCAN_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:29Z" level=info msg="config detected" key=AGENT_POLL_HTTP_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:33Z" level=info msg="config detected" key=AGENT_POLL_HTTP_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:38Z" level=info msg="config detected" key=AGENT_POLL_HTTP_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:38Z" level=info msg="config detected" key=AGENT_POLL_PULL_REQUEST_SCAN_JOB_ENABLED source=server value=true
time="2025-07-17T09:13:38Z" level=info msg="config detected" key=AGENT_POLL_COPY_SECRETS_JOB_ENABLED source=server value=true
接続が成功すると、Agentのステータスが Connected に変わります。

2.GitHubとの連携
1.データソースを追加します。スキャン方法として、「Vault Radar Agent Scan」を選択し、Continueをクリックします。
2.スキャン対象のデータソースを設定します。今回はGitHub Cloudを選択します
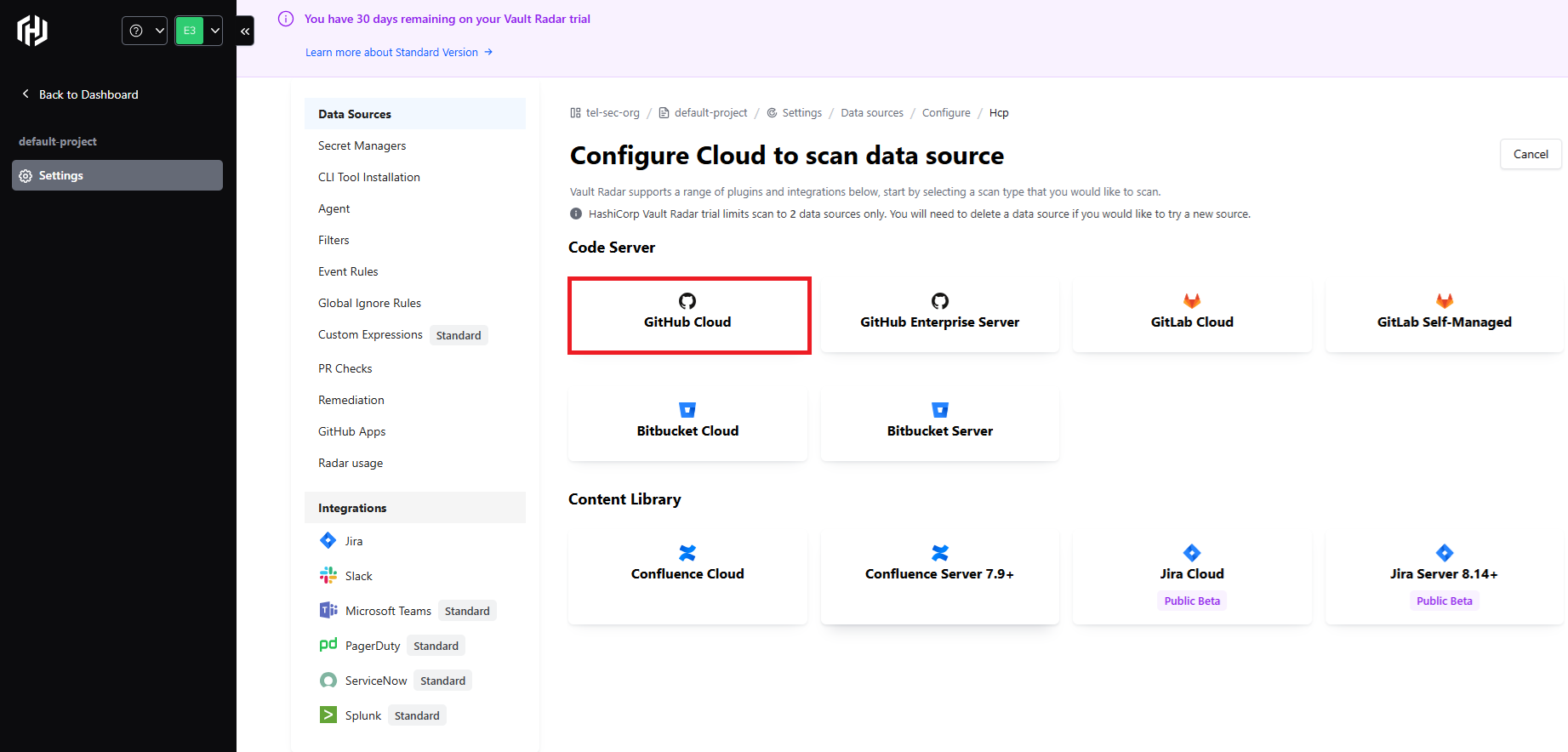
3.GitHubの組織名を指定し、パーソナルアクセストークンを環境変数(env://VAULT_RADAR_GIT_TOKEN)として設定します。
注)「HCP Vault Radar Scan」方式では、この画面でパーソナルアクセストークンを指定していたため、HCP Vault Radar Agent Scan」方式との差異となります。
4.リポジトリを選択します。(あるいは、All active repositoriesを選択します)

以上で、GitHubとの連携ができました。
次に、リポジトリにシークレットを記載し、スキャンしてみます。
3.GitHubへのテストシークレットの登録とプッシュ
前回と同じく、テストシークレットを登録して、GitHubにPushします。
❗ 本物の鍵は絶対に使わないでください。本記事のキーはすべて無効なダミーです。
vault-radar-demo/
├── .env
└── config.js
.env
AWS_ACCESS_KEY_ID=AKIAFAKEKEY1234567890
AWS_SECRET_ACCESS_KEY=wJalrXUtnFAKESECRETKEYEXAMPLE
SENDGRID_API_KEY=SG.fakevalue.1234
config.js
const password = "hunter2";
const dbPassword = "supersecurepassword123";
4.スキャン結果確認
HCP Vault Radar Agent経由で、自動的にスキャンした結果がダッシュボードに表示されます。
スキャン方式は、「Vault Radar Agent Scan」になっていました。
リソース名をクリックすると、詳細情報が確認できます。
シークレットが2つ検出されていました。

GitHubでCommit/Pushすると、Vault Radar Agentに以下のログが出力されます。
time="2025-07-17T10:06:29Z" level=info msg="starting job" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:29Z" level=info msg="Creating risk scan job"
time="2025-07-17T10:06:29Z" level=info msg="sending request" correlation_id=738dc73e-e3bf-4887-9e10-2bd7ac462e16 job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 method=PUT url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/scans" worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="config detected" key=AGENT_POLL_PULL_REQUEST_SCAN_JOB_ENABLED source=server value=true
time="2025-07-17T10:06:30Z" level=info msg="received response" correlation_id=738dc73e-e3bf-4887-9e10-2bd7ac462e16 job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 method=PUT status_code=200 url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/scans" worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="NOT fetching scan config from HCP" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 offline=false radarClient=true radarScanConfig=true worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="NOT fetching scan config from HCP" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 offline=false radarClient=true radarScanConfig=true worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="NOT fetching scan config from HCP" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 offline=false radarClient=true radarScanConfig=true worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="Scanning resource" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 type=git_other uri="git://github.com/e30020/vault-radar-agent-demo.git" worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="starting ScanDriver.Scan" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="start scan heartbeat" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="setting scan deadline" deadline="2025-07-18T10:06:30Z" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="Loaded patterns" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 num_pii=1 num_secret=270 worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="Loaded hyperscan database, somLeft=true, size=3398448, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="Loaded hyperscan database, somLeft=false, size=177928, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="Opening data source" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="cloning repo" clone_dir= clone_url="git://github.com/e30020/vault-radar-agent-demo.git" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 subsystem_name=RepoDataSource worker="Content scan job"
time="2025-07-17T10:06:30Z" level=info msg="config detected" key=AGENT_POLL_RESOURCE_SCAN_JOB_ENABLED source=server value=true
time="2025-07-17T10:06:32Z" level=info msg="Opened data source" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:32Z" level=info msg="Getting and scanning data source contents" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:32Z" level=info msg="Compiling hyperscan database with 109 patterns, somLeft=true" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:32Z" level=info msg="Loaded hyperscan database, somLeft=true, size=84776, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:32Z" level=info msg="Compiling hyperscan database with 0 patterns, somLeft=false" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:32Z" level=info msg="Loaded hyperscan database, somLeft=true, size=3398448, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:32Z" level=info msg="Loaded hyperscan database, somLeft=false, size=177928, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:32Z" level=info msg="Loading the common passwords/credentials from embed file" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:35Z" level=warning msg="GetBranchHeadCommitId failed for git ref (refs/heads/main) : reference 'refs/heads/main' not found" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 subsystem_name=RepoDataSource worker="Content scan job"
time="2025-07-17T10:06:35Z" level=info msg="GetBranchHeadCommitId for git ref (refs/heads/main) returned : " job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 subsystem_name=RepoDataSource worker="Content scan job"
time="2025-07-17T10:06:35Z" level=info msg="config detected" key=AGENT_POLL_COPY_SECRETS_JOB_ENABLED source=server value=true
time="2025-07-17T10:06:36Z" level=info msg="Closing data source" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:36Z" level=info msg="Closed data source" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:36Z" level=info msg="finished ScanDriver.Scan" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:36Z" level=info msg="stop scan heartbeat" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:36Z" level=info msg="sending request" correlation_id=738dc73e-e3bf-4887-9e10-2bd7ac462e16 job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 method=POST url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/scan-results" worker="Content scan job"
time="2025-07-17T10:06:36Z" level=info msg="received response" correlation_id=738dc73e-e3bf-4887-9e10-2bd7ac462e16 job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 method=POST status_code=202 url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/scan-results" worker="Content scan job"
time="2025-07-17T10:06:36Z" level=info msg="Uploaded risks to HCP" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 num_risks=2 worker="Content scan job"
time="2025-07-17T10:06:36Z" level=info msg="sending request" correlation_id=738dc73e-e3bf-4887-9e10-2bd7ac462e16 job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 method=POST url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/user-meters" worker="Content scan job"
time="2025-07-17T10:06:36Z" level=info msg="received response" correlation_id=738dc73e-e3bf-4887-9e10-2bd7ac462e16 job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 method=POST status_code=204 url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/user-meters" worker="Content scan job"
time="2025-07-17T10:06:36Z" level=info msg="job complete" job_id=d29a3c70-2dbc-400b-a102-6bb31e3ea832 worker="Content scan job"
time="2025-07-17T10:06:38Z" level=info msg="config detected" key=AGENT_POLL_HTTP_JOB_ENABLED source=server value=true
time="2025-07-17T10:06:41Z" level=info msg="config detected" key=AGENT_POLL_RESOURCE_SCAN_JOB_ENABLED source=server value=true
time="2025-07-17T10:06:42Z" level=info msg="config detected" key=AGENT_POLL_PULL_REQUEST_SCAN_JOB_ENABLED source=server value=true
time="2025-07-17T10:06:42Z" level=info msg="starting job" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:42Z" level=info msg="Creating risk scan job"
time="2025-07-17T10:06:42Z" level=info msg="sending request" correlation_id=974ec028-d922-495a-bbd8-5144884cf827 job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 method=PUT url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/scans" worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="received response" correlation_id=974ec028-d922-495a-bbd8-5144884cf827 job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 method=PUT status_code=200 url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/scans" worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="NOT fetching scan config from HCP" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 offline=false radarClient=true radarScanConfig=true worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="NOT fetching scan config from HCP" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 offline=false radarClient=true radarScanConfig=true worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="NOT fetching scan config from HCP" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 offline=false radarClient=true radarScanConfig=true worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="Scanning resource" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 type=git_other uri="git://github.com/e30020/vault-radar-agent-demo.git" worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="starting ScanDriver.Scan" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="setting scan deadline" deadline="2025-07-18T10:06:43Z" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="start scan heartbeat" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="Loaded patterns" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 num_pii=1 num_secret=270 worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="Loaded hyperscan database, somLeft=true, size=3398448, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="Loaded hyperscan database, somLeft=false, size=177928, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="Opening data source" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:43Z" level=info msg="cloning repo" clone_dir= clone_url="git://github.com/e30020/vault-radar-agent-demo.git" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 subsystem_name=RepoDataSource worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="Opened data source" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="Getting and scanning data source contents" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="start traversing tip" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 subsystem_name=RepoDataSource worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="waiting for sync contents" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 subsystem_name=RepoDataSource worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="Loaded hyperscan database, somLeft=true, size=84776, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="Compiling hyperscan database with 0 patterns, somLeft=false" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="Loaded hyperscan database, somLeft=true, size=3398448, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="Loaded hyperscan database, somLeft=false, size=177928, info: Version: 5.4.10 Features: Mode: BLOCK" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="finished waiting for sync contents" error="<nil>" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 subsystem_name=RepoDataSource worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="finish traversing tip" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 subsystem_name=RepoDataSource worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="Closing data source" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="Closed data source" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="finished ScanDriver.Scan" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="stop scan heartbeat" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="sending request" correlation_id=974ec028-d922-495a-bbd8-5144884cf827 job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 method=POST url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/scan-results" worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="received response" correlation_id=974ec028-d922-495a-bbd8-5144884cf827 job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 method=POST status_code=202 url="https://api.cloud.hashicorp.com:443/2023-05-01/vault-radar/projects/905a2fcf-f712-4a2c-ba1d-2901bdc95d10/api/scan-results" worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="Uploaded risks to HCP" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 num_risks=2 worker="Resource scan job"
time="2025-07-17T10:06:45Z" level=info msg="job complete" job_id=ceaad526-9d46-4fef-a382-bcfb9249d1f5 worker="Resource scan job"
最後に
今回は、Vault Radar Agent を使って、GitHubのデータをスキャンしてみました。
次回は、 『vault Radar CLI』を使用してスキャンを行い、その手順や結果を解説します。CLIを使用すると、コマンドラインでより柔軟な操作が可能になります。
参考情報
Vault Radar Agent公式ページ(英語)
https://developer.hashicorp.com/hcp/docs/vault-radar/agent/overview








