前提
- Windows10
- eksctl
- EKSチュートリアルをなぞる
いざ尋常に
Chocolatelyのインストール
@"%SystemRoot%\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -InputFormat None -ExecutionPolicy Bypass -Command "iex ((New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1'))" && SET "PATH=%PATH%;%ALLUSERSPROFILE%\chocolatey\bin"
eksctlインストール
chocolatey install -y eksctl aws-iam-authenticator
インストール確認
eksctl version
Clusterをデプロイ
eksctl create cluster --name prod --version 1.13 --nodegroup-name standard-workers --node-type t3.medium --nodes 3 --nodes-min 1 --nodes-max 4 --node-ami auto
内部的には、CloudFormationが実行されているみたい
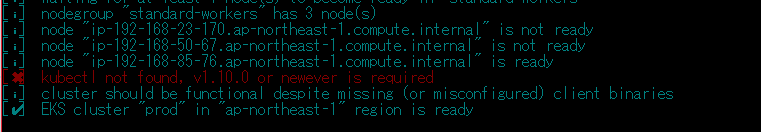
kubectlがインストールされていないみたいだ
kubectlのインストール
Pathを通さなくてもいいように C:\WINDOWS\system32 に作っちゃえ
C:\WINDOWS\system32>curl -LO https://storage.googleapis.com/kubernetes-release/release/v1.15.0/bin/windows/amd64/kubectl.exe
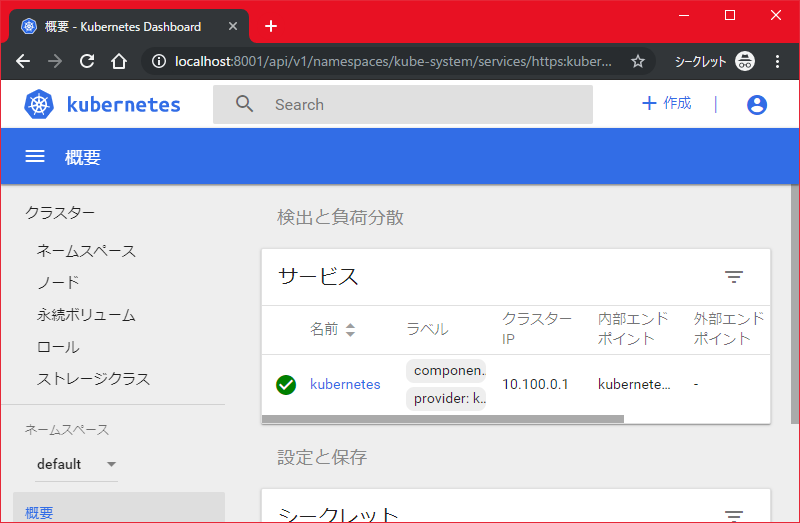
サービスを見てみると、Kubernetesというサービスが上がっている
C:\WINDOWS\system32>kubectl.exe get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.100.0.1 <none> 443/TCP 10m
Dashboard用のyamlファイルをデプロイ
C:\WINDOWS\system32>kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
secret/kubernetes-dashboard-certs created
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
コンテナリソースのモニタリングなどを担当してくれるらしいheapsterをデプロイ
C:\WINDOWS\system32>kubectl apply -f https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/heapster.yaml
serviceaccount/heapster created
deployment.extensions/heapster created
service/heapster created
heapsterのバックエンドデータベースとなるinfluxdbをデプロイ
C:\WINDOWS\system32>kubectl apply -f https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/influxdb.yaml
deployment.extensions/monitoring-influxdb created
service/monitoring-influxdb created
ダッシュボードのheapsterクラスターロールバインディング
C:\WINDOWS\system32>kubectl apply -f https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/rbac/heapster-rbac.yaml
clusterrolebinding.rbac.authorization.k8s.io/heapster created
Dashboardへアクセスできるようにサービスアカウントを作成
eks-admin-service-account.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: eks-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: eks-admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: eks-admin
namespace: kube-system
上で作ったyamlファイルをデプロイ
C:\WINDOWS\system32>kubectl apply -f c:\Users\yuta\Downloads\eks-admin-service-account.yaml
serviceaccount/eks-admin created
clusterrolebinding.rbac.authorization.k8s.io/eks-admin created
Tokenを取得
C:\WINDOWS\system32>kubectl -n kube-system describe secret eks-admin-token-62ksw
Name: eks-admin-token-62ksw
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: eks-admin
kubernetes.io/service-account.uid: cb651adb-cd4b-11e9-b3a3-06c60c4db86a
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJla3MtYWRtaW4tdG9rZW4tNjJrc3ciLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZWtzLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiY2I2NTFhZGItY2Q0Yi0xMWU5LWIzYTMtMDZjNjBjNGRiODZhIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmVrcy1hZG1pbiJ9.knete3qk-RkMIOVeYBtCD1fFxO1uNN2-42CGpRoapeTOBZM3zHmHF6Q1D_NovuALCeRFKaJJpHIiGsoq16iwNfGToUvKfoQPMHcqeMTQ33YUh4iScmbq7XjBIh5wN-Vf6jUzJ9bJhUZ2hNxCVcvjUcRu2JU02phwddusg_nrd3CsPFu3mhuD7HuaYo8ZC66kKBalhe3q4ceWOURjp59ak2b81NR6fjazatv_Y-VQkh57LRouqEbdlb7lWN2tgLpiSzXZYBJkcH3t2qzfsiOGlg4lcuh2_JyJO2byGezzGStfz2ZS7GbJWGgg9VPQ9zM_adMI78kIqiyjV63vakck-Q
Dashboardコンテナへ接続できるようにする(コンソール放置しておく)
C:\WINDOWS\system32>kubectl proxy
Starting to serve on 127.0.0.1:8001
Dashboardへアクセス
http://localhost:8001/api/v1/namespaces/kube-system/services/https:kubernetes-dashboard:/proxy/#!/login