ZRouterのVPNソフトを整理していて、strongSwanも追加してみたので、試してみました。
strongSwanは5.xで設定ファイルを作り替えて、旧式のipsec.conf形式と新式のswanctl.conf形式があります。今回試した5.9は両方サポートされているようですが、将来旧式はサポートされなくなるのではないでしょうか。ネットを検索するとまだ旧式の情報のほうが多く混沌としています。
ikev1で新式で設定してみます。
対向はAndroid 9のスマホでシステムが提供するVPN機能を使い、おうち内のプライベートネットワークにいます。
設定ファイルは以下の三つです。
charon {
include swanctl/swanctl.conf
}
connections {
rw {
local_addrs = 192.168.0.101
local-psk {
auth = psk
}
remote-psk {
auth = psk
}
remote-xauth {
auth = xauth
}
children {
net {
local_ts = 10.1.0.0/16
updown = /usr/local/libexec/ipsec/_updown iptables
esp_proposals = aes128gcm128-x25519
}
}
pools = carol-pool
version = 1
proposals = aes256-sha384-modp1024
}
}
pools {
carol-pool {
addrs = 10.1.0.128/20
}
}
: PSK "1234"
carol : XAUTH "1234"
これらのファイルはZRouterでビルドするときはvendorの下に置いてあります。
これで、/usr/local/libexec/ipsecのcharonを起動します。
起動しただけだと設定が有効にならないので下記を実行します。
# cd /usr/local/sbin
# ./swanctl --load-conns
loaded connection 'rw'
successfully loaded 1 connections, 0 unloaded
# ./swanctl --load-pools
loaded pool 'carol-pool'
successfully loaded 1 pools, 0 unloaded
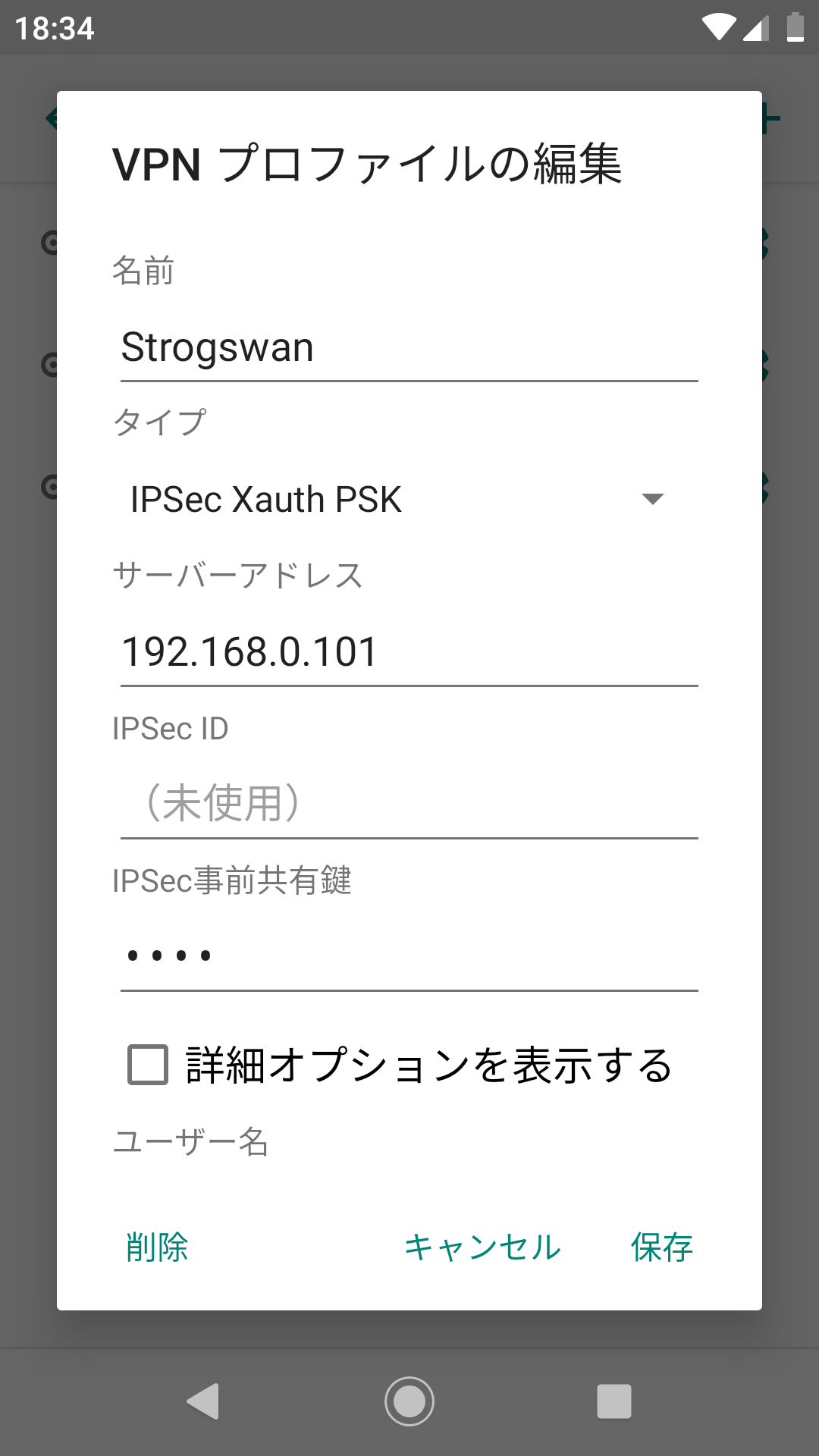
これでAndroidのVPNプロファイルでタイプを"IPSec Xauth PSK"にしてサーバーアドレス(192.168.0.101)、IPSecの事前共有鍵(1234)、ユーザー名(carol)、パスワードを(1234)を設定して接続してみます。
# ./charon
00[DMN] Starting IKE charon daemon (strongSwan 5.9.2, FreeBSD 12.3-STABLE, mips)
00[NET] could not open socket: Address family not supported by protocol family
00[NET] could not open IPv6 socket, IPv6 disabled
00[CFG] loading ca certificates from '/usr/local/etc/ipsec.d/cacerts'
00[LIB] opening directory '/usr/local/etc/ipsec.d/cacerts' failed: No such file or directory
00[CFG] reading directory failed
00[CFG] loading aa certificates from '/usr/local/etc/ipsec.d/aacerts'
00[LIB] opening directory '/usr/local/etc/ipsec.d/aacerts' failed: No such file or directory
00[CFG] reading directory failed
00[CFG] loading ocsp signer certificates from '/usr/local/etc/ipsec.d/ocspcerts'
00[LIB] opening directory '/usr/local/etc/ipsec.d/ocspcerts' failed: No such file or directory
00[CFG] reading directory failed
00[CFG] loading attribute certificates from '/usr/local/etc/ipsec.d/acerts'
00[LIB] opening directory '/usr/local/etc/ipsec.d/acerts' failed: No such file or directory
00[CFG] reading directory failed
00[CFG] loading crls from '/usr/local/etc/ipsec.d/crls'
00[LIB] opening directory '/usr/local/etc/ipsec.d/crls' failed: No such file or directory
00[CFG] reading directory failed
00[CFG] loading secrets from '/usr/local/etc/ipsec.secrets'
00[CFG] loaded IKE secret for %any
00[CFG] loaded EAP secret for carol
00[LIB] loaded plugins: charon aes des blowfish rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem openssl fips-prf curve25519 xcbc cmac hmac drbg attr kernel-pfkey kernel-pfroute resolve socket-default stroke vici updown eap-identity eap-md5 eap-mschapv2 eap-tls eap-ttls eap-peap xauth-generic xauth-eap xauth-pam whitelist addrblock counters
00[JOB] spawning 16 worker threads
14[CFG] added vici connection: rw
16[CFG] added vici pool carol-pool: 10.1.0.128, 3967 entries
13[NET] received packet: from 192.168.0.132[500] to 192.168.0.101[500] (756 bytes)
13[ENC] parsed ID_PROT request 0 [ SA V V V V V V V V ]
13[IKE] received NAT-T (RFC 3947) vendor ID
13[IKE] received draft-ietf-ipsec-nat-t-ike-02 vendor ID
15[MGR] ignoring request with ID 1529237285, already processing
13[IKE] received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
13[IKE] received draft-ietf-ipsec-nat-t-ike-00 vendor ID
13[IKE] received XAuth vendor ID
13[IKE] received Cisco Unity vendor ID
13[IKE] received FRAGMENTATION vendor ID
13[IKE] received DPD vendor ID
13[IKE] 192.168.0.132 is initiating a Main Mode IKE_SA
13[CFG] selected proposal: IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024
13[ENC] generating ID_PROT response 0 [ SA V V V V ]
13[NET] sending packet: from 192.168.0.101[500] to 192.168.0.132[500] (160 bytes)
13[NET] received packet: from 192.168.0.132[500] to 192.168.0.101[500] (284 bytes)
13[ENC] parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
13[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
13[NET] sending packet: from 192.168.0.101[500] to 192.168.0.132[500] (300 bytes)
13[NET] received packet: from 192.168.0.132[500] to 192.168.0.101[500] (124 bytes)
13[ENC] parsed ID_PROT request 0 [ ID HASH ]
13[CFG] looking for XAuthInitPSK peer configs matching 192.168.0.101...192.168.0.132[192.168.0.132]
13[CFG] selected peer config "rw"
13[ENC] generating ID_PROT response 0 [ ID HASH ]
13[NET] sending packet: from 192.168.0.101[500] to 192.168.0.132[500] (108 bytes)
13[ENC] generating TRANSACTION request 3288601449 [ HASH CPRQ(X_USER X_PWD) ]
13[NET] sending packet: from 192.168.0.101[500] to 192.168.0.132[500] (108 bytes)
12[NET] received packet: from 192.168.0.132[500] to 192.168.0.101[500] (124 bytes)
12[ENC] parsed TRANSACTION response 3288601449 [ HASH CPRP(X_USER X_PWD) ]
12[IKE] XAuth authentication of 'carol' successful
12[ENC] generating TRANSACTION request 1576041085 [ HASH CPS(X_STATUS) ]
12[NET] sending packet: from 192.168.0.101[500] to 192.168.0.132[500] (108 bytes)
15[NET] received packet: from 192.168.0.132[500] to 192.168.0.101[500] (140 bytes)
15[ENC] parsed INFORMATIONAL_V1 request 3745820331 [ HASH N(INITIAL_CONTACT) ]
13[NET] received packet: from 192.168.0.132[500] to 192.168.0.101[500] (156 bytes)
13[IKE] queueing TRANSACTION request as tasks still active
12[NET] received packet: from 192.168.0.132[500] to 192.168.0.101[500] (124 bytes)
12[ENC] parsed TRANSACTION response 1576041085 [ HASH CPA(X_STATUS) ]
12[IKE] IKE_SA rw[1] established between 192.168.0.101[192.168.0.101]...192.168.0.132[192.168.0.132]
12[IKE] scheduling rekeying in 13686s
12[IKE] maximum IKE_SA lifetime 15126s
12[ENC] parsed TRANSACTION request 3229359350 [ HASH CPRQ(ADDR MASK DNS NBNS U_BANNER U_DEFDOM U_SPLITDNS U_SPLITINC U_LOCALLAN VER) ]
12[IKE] peer requested virtual IP %any
12[CFG] assigning new lease to 'carol'
12[IKE] assigning virtual IP 10.1.0.128 to peer 'carol'
12[ENC] generating TRANSACTION response 3229359350 [ HASH CPRP(ADDR) ]
12[NET] sending packet: from 192.168.0.101[500] to 192.168.0.132[500] (108 bytes)
13[NET] received packet: from 192.168.0.132[500] to 192.168.0.101[500] (140 bytes)
13[ENC] parsed INFORMATIONAL_V1 request 3338742428 [ HASH D ]
13[IKE] received DELETE for IKE_SA rw[1]
13[IKE] deleting IKE_SA rw[1] between 192.168.0.101[192.168.0.101]...192.168.0.132[192.168.0.132]
13[CFG] lease 10.1.0.128 by 'carol' went offline
結構苦戦しました。
まずはまったのはswanctlで--load-connsをしないと、まったく処理されません。これをすると今度はCipherのプロポーザルに失敗するので、ログを見て最初のやつにswanctl.confのproposalsを合わせました。あと新式の書き方で有効にする方法が分からなかったので、KEYは旧式のipsec.secretsに書いて見ました。それからpoolsを追加して有効にしてやっと「接続されました」。
設定ファイルを作って焼いてでは効率が悪いので、/usr/local/etcをunionfsでmountして、設定ファイルだけ書き換えて何度も試しました。
mkdir /tmp/local_etc
mount_unionfs /tmp/local_etc /usr/local/etc
実際使うにはまだ設定が必要だと思われます。またこの設定ではAndroid以外はつながらないと思います。
あ、あと/usr/local/lib/ipsecにldconfigでpathを通すのもお忘れなく。
メモリ64MのOnion Omegaで試しましたが、問題なかったです。
WiFiとVPNは安全じゃない通信路で安全に通信させるという、同じ役割があり、同じ技術が所々で使われています。