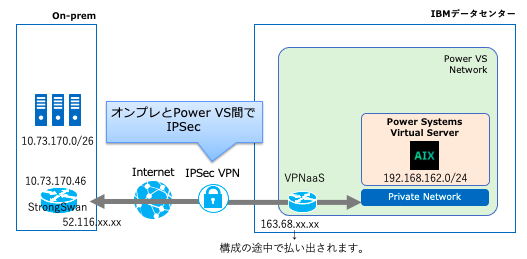
この記事のオンプレ側IPSec終端として、下記の構成でStrongSwanも試したのでメモ。
StrongSwan導入先のOSはCentOS7。
# cat /etc/sysctl.conf
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_synack_retries = 2
net.ipv4.ip_forward = 1
net.ipv6.conf.all.forwarding = 1
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0
# sysctl -p
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_synack_retries = 2
net.ipv4.ip_forward = 1
net.ipv6.conf.all.forwarding = 1
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0
# systemctl start strongswan
# systemctl enable strongswan
Created symlink from /etc/systemd/system/multi-user.target.wants/strongswan.service to /usr/lib/systemd/system/strongswan.service.
#
StrongSwanインストール
# yum install epel-release
# yum install strongswan
# strongswan version
Linux strongSwan U5.7.2/K3.10.0-1160.36.2.el7.x86_64
University of Applied Sciences Rapperswil, Switzerland
See 'strongswan --copyright' for copyright information.
# cd /etc/strongswan
#
StrongSwan設定ファイル
(繋がったので良しとしていますが、改善の余地はあるかもしれません)
leftが自分、rightが対向。
ike、espの書式は、encryption-integrity[-prf]-dhgroup
https://wiki.strongswan.org/projects/strongswan/wiki/connsection
今回の例では、対向のVPNaaS側の設定が、「Authentication=sha-256, Encryption=aes-256-cbc, Dh Group=2」だったので、aes256-sha256-modp1024としている。
# cat ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
charondebug="all"
uniqueids=never
# Add connections here.
conn classic2power
type=tunnel
auto=start
keyexchange=ikev1
authby=psk
left=52.116.xx.xx
leftsubnet=10.73.170.0/26
leftid=52.116.xx.xx
right=163.68.xx.xx
rightsubnet=192.168.162.0/24
rightid=163.68.xx.xx
ike=aes256-sha256-modp1024
esp=aes256-sha256-modp1024
keyingtries=%forever
ikelifetime=28800s
lifetime=28800s
dpddelay=10s
dpdtimeout=50s
dpdaction=restart
#
# cat ipsec.secrets
# ipsec.secrets - strongSwan IPsec secrets file
52.116.xx.xx 163.68.xx.xx : PSK "mypassword"
#
疎通確認
最初、ikeやespを正しく設定できておらず、下記の状態になってIPSecが確立できていなかった。
# strongswan status
Security Associations (0 up, 0 connecting):
none
#
下記で、パケットはやり取りできている(FW設定等が原因ではない)が、NO_PROPOSAL_CHOSEN errorが届いている事が分かったので、ikeやespの値を見直したところ、繋がった。
# strongswan up classic2power
initiating Main Mode IKE_SA classic2power[3] to 163.68.xx.xx
generating ID_PROT request 0 [ SA V V V V V ]
sending packet: from 52.116.xx.xx[500] to 163.68.xx.xx[500] (240 bytes)
received packet: from 163.68.xx.xx[500] to 52.116.xx.xx[500] (102 bytes)
parsed INFORMATIONAL_V1 request 3789418228 [ N(NO_PROP) ]
received NO_PROPOSAL_CHOSEN error notify
establishing connection 'classic2power' failed
#
IPSec確立後
# strongswan status
Security Associations (1 up, 0 connecting):
classic2power[1]: ESTABLISHED 9 minutes ago, 52.116.xx.xx[52.116.xx.xx]...163.68.xx.xx[163.68.xx.xx]
classic2power{1}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: cc195b89_i 3ee558ed_o
classic2power{1}: 10.73.170.0/26 === 192.168.162.0/24
#
IPSecトンネルの向こう(rightsubnet)にいるサーバーにpingが通った。
# ping 192.168.162.57
PING 192.168.162.57 (192.168.162.57) 56(84) bytes of data.
64 bytes from 192.168.162.57: icmp_seq=1 ttl=251 time=143 ms
64 bytes from 192.168.162.57: icmp_seq=2 ttl=251 time=142 ms
StrongSwanサーバーと同じサブネットにある別サーバーも、「IPSecトンネルの向こうにいるサブネットへのパケットはStrongSwanサーバーに渡す」という静的経路を設定することで、通信可能となる。
10.73.170.46がStrongSwanサーバーのIP。
# route add -net 192.168.162.0 gw 10.73.170.46 netmask 255.255.255.0 eth0
# netstat -nr|grep 192.168
192.168.162.0 10.73.170.46 255.255.255.0 UG 0 0 0 eth0
# ping 192.168.162.57
PING 192.168.162.57 (192.168.162.57) 56(84) bytes of data.
64 bytes from 192.168.162.57: icmp_seq=1 ttl=250 time=158 ms
64 bytes from 192.168.162.57: icmp_seq=2 ttl=250 time=143 ms
64 bytes from 192.168.162.57: icmp_seq=3 ttl=250 time=143 ms
以上