(自分用)
ある日メールがawsから届く
8月7日
Hello,
We have detected activity that indicates your AWS account has been compromised. Please take the necessary steps to re-secure your account.
To protect you from unauthorized usage and charges, failure to reply or follow these steps within five days may result in the suspension of your account, and disruption of AWS service.
To re-secure your account, I have included below the necessary steps for you to re-secure the account. Please bear with us, as this is a long email, but rest assured every step in it is important to your account's security. You'll need to complete the following:
- Update your root account password.
- DELETE the exposed key
8月8日
Hello,
We have detected activity that indicates your AWS account has been compromised. Please take the necessary steps to re-secure your account. We have been unable to reach you by phone.
For your convenience, I’ve summarized the information in this email.
8月11日
Hi there,
We've recently tried to contact you via email and telephone with regards to your account compromise.
Please review the correspondence sent to you via email which includes steps required to securing your account.
We are going to resolve this case for administrative reasons.
Please feel free to reach out to us via this case at any time.
8月13日にメールの内容を把握。
メールの通りに、
ルートユーザーパスワード変更
IAMユーザーアクセスキーを変更。再設定。
結果、アラートが消えない
対応したのが5日経過していたから?
AWSサポートにメールする。
後日更新
8月13日メールが届く
Dear AWS Customer,
Thank you for deleting your compromised AWS Access Key(s) of account ending with 0000. Please ensure that no unauthorized resources remain on your account, and we ask that you pay special attention to IAM users and EC2 instances. Please take steps to prevent any new credentials from being published in this manner again.
Thank you for trusting your business to AWS. We work hard to keep you safe!
Sincerely,
Amazon Web Services
This message was produced and distributed by Amazon Web Services, Inc. and affiliates, 410 Terry Ave. North, Seattle, WA 98109-5210.
これからは注意してください的な
それでもアラートは消えない
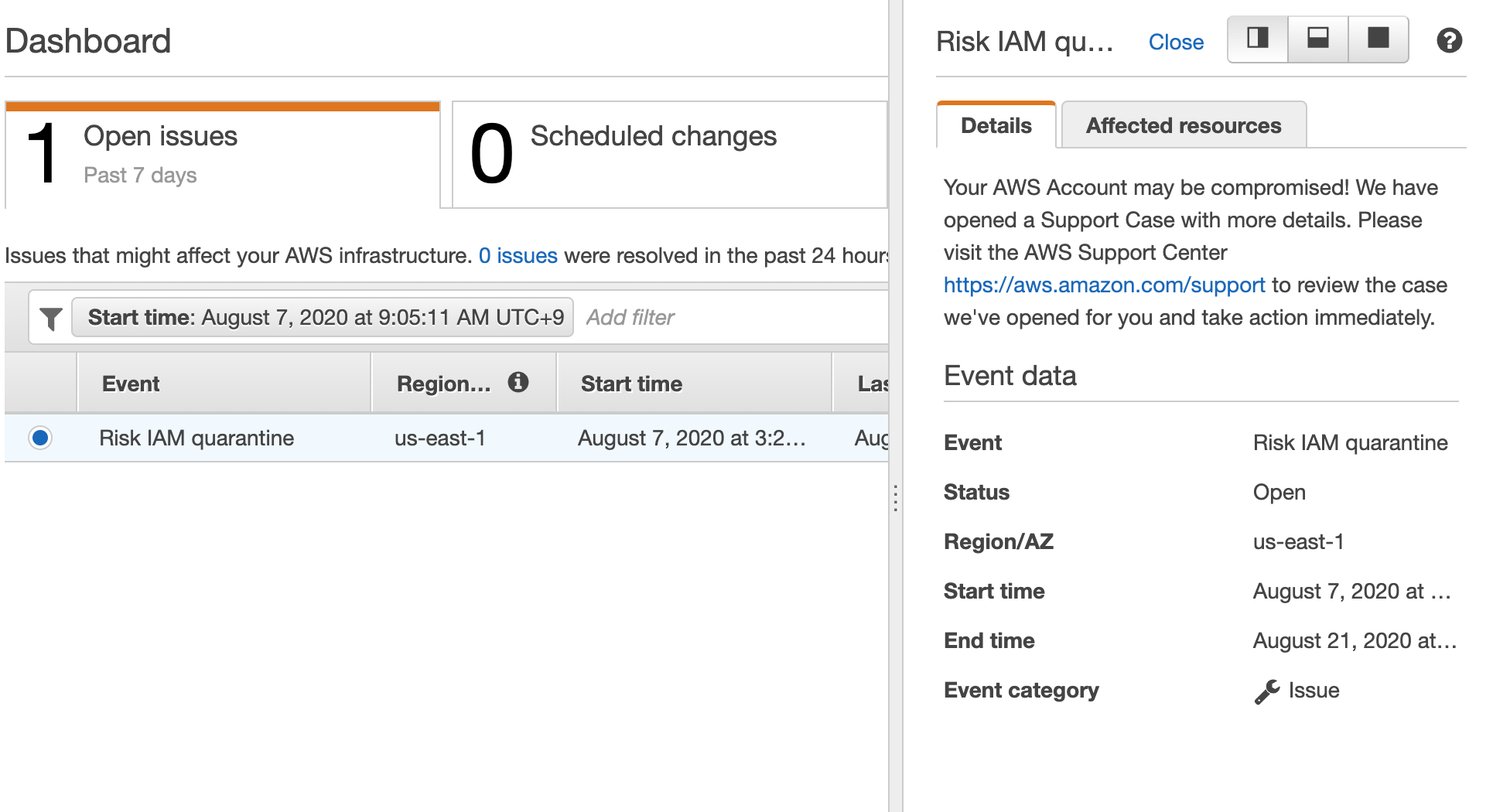
AWSサポート - Your support cases - Detailsで確認すると、
AWSExposedCredentialPolicy_DO_NOT_REMOVEポリシーが付与されて、
権限がdenyになるようになっていた。AWSすごすぎる

原因は、rails app にて、fog gem を利用してs3にアクセスするように仕込んだアクセスキーを環境変数化しないままpublicなgithubにあげてしまったことによる。
自業自得だなー。
漏洩したキーを変更。IAMユーザー削除、再作成。ルートユーザーパスワード変更。を行う
- AWS_ACCESS_KEY_ID(再発行)
- AWS_SECRET_ACCESS_KEY(再発行)
- ルートユーザパスワード変更
- IAMユーザ削除
- IAMユーザ再作成
- ポリシー削除
