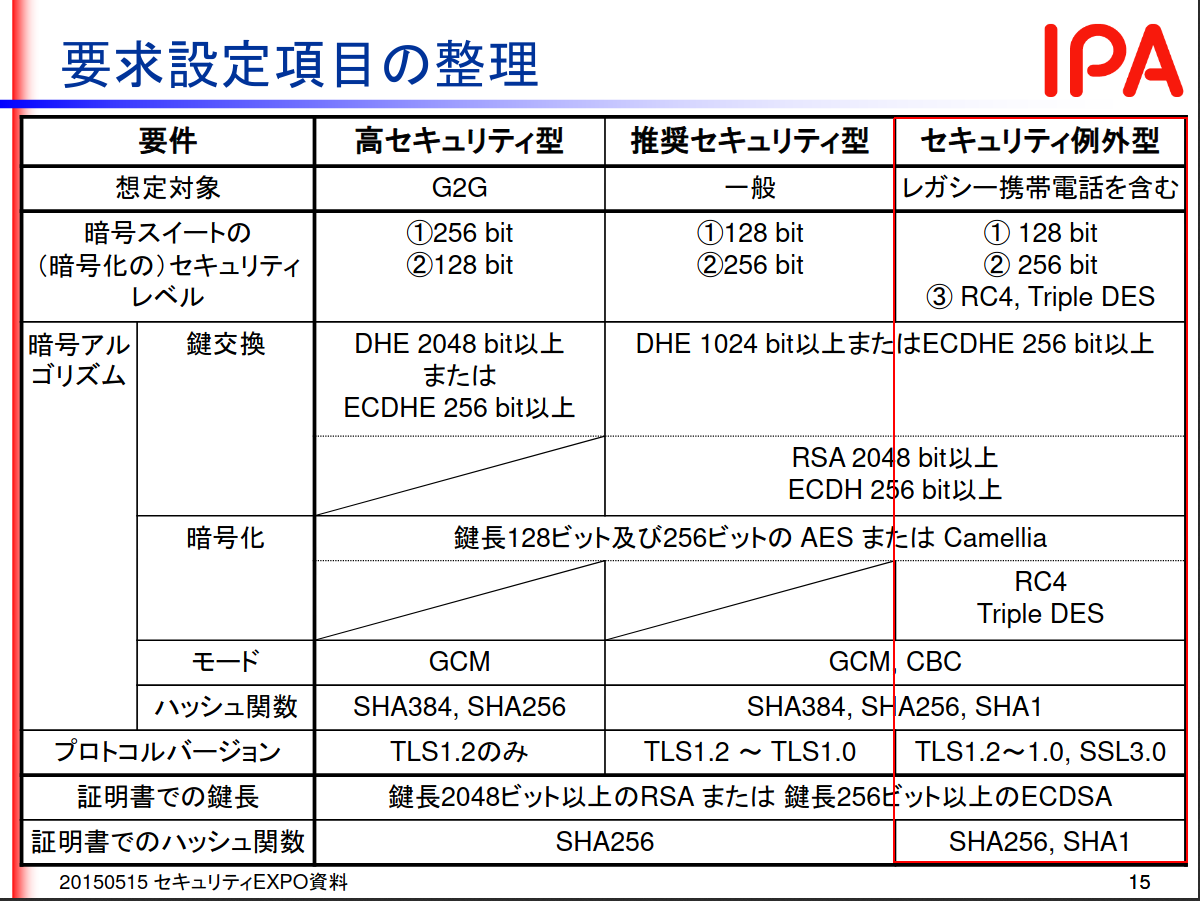
-
@SECLEVEL=0が必要。
nginx
server {
listen 80;
listen 443 ssl;
server_name localhost;
#ssl_verify_client on;
ssl_certificate /etc/nginx/certs/server.crt;
ssl_certificate_key /etc/nginx/certs/server.key;
ssl_client_certificate /etc/nginx/certs/ca.crt;
+ ssl_ciphers 'HIGH:!aNULL:!MD5@SECLEVEL=0';
# IE11だとなぜかTLSv1.2を有効にしていると接続できない。
+ ssl_protocols TLSv1 TLSv1.1 TLSv1.3;
location / {
root /usr/share/nginx/html;
index index.html index.htm;
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root /usr/share/nginx/html;
}
}
Ubuntu 20.04 (OepnSSL 1.1.1)
- SSLCipherSuite にて
@SECLEVEL=0の指定を追加する。
<IfModule mod_ssl.c>
<VirtualHost _default_:443>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
SSLEngine on
SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem
SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key
- SSLCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
+ SSLCipherSuite @SECLEVEL=0:kEECDH:kRSA:kEDH:kPSK:kDHEPSK:kECDHEPSK:!DES:!RC2:!IDEA:-SEED:!eNULL:!aNULL:!MD5:-SHA384:-CAMELLIA:-ARIA:-AESCCM8
# もしくは
+ SSLCipherSuite @SECLEVEL=0:HIGH:MEDIUM:!MD5:!RC4:!3DES
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory /usr/lib/cgi-bin>
SSLOptions +StdEnvVars
</Directory>
</VirtualHost>
</IfModule>
Ubuntu 16.04 (OepnSSL 1.0.2e)
- OpenSSL 1.1.1で出来ていた
@SECLEVEL=0:の指定は出来ないので注意。 - CentOS7も OpenSSL 1.0.2の様子。
- OpenSSL 1.0.2までは XPのIE6 でアクセスが可能。(※
LOWの指定が1.1.0で削除された。40ビット及び56ビット暗号のサポートをlibsslから削除) - ブラウザごとの使用できる暗号化bitは List of browsers that support 128-bit and 256-bit encryption
- 私が愛した openssl (SSL/TLS 編) - してみんとて は随分まとまっていて感謝
<IfModule mod_ssl.c>
<VirtualHost _default_:443>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
SSLEngine on
SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem
SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key
+ SSLCipherSuite kEECDH:kRSA:kEDH:kPSK:kDHEPSK:kECDHEPSK:!DES:!RC2:!IDEA:-SEED:!eNULL:!aNULL:!MD5:-SHA384:-CAMELLIA:-ARIA:-AESCCM8
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory /usr/lib/cgi-bin>
SSLOptions +StdEnvVars
</Directory>
</VirtualHost>
</IfModule>
CentOS 8
- mod_ssl の SECLEVEL を下げれば動く。
- /docs/man1.1.1/man3/SSL_CTX_set_security_level.html
Level 0
Everything is permitted. This retains compatibility with previous versions of OpenSSL.
Apacheをhttps有効で起動しようとするも起動できない場合。
/var/log/httpd/ssl_error_logを確認。
key too smallへの対処
SSL Library Error: error:140AB18F:SSL routines:SSL_CTX_use_certificate:ee key too small
と出た場合、SSLCertificateKeyFileなどを旧サーバーからコピーして動かした場合だと思います。
なお、apacheでの定義は以下 /etc/httpd/conf.d/ssl.conf
SSLCertificateFile /etc/pki/tls/certs/localhost.crt
SSLCertificateKeyFile /etc/pki/tls/private/localhost.key
エラーメッセージ確認
# 起動
/usr/sbin/httpd -D FOREGROUND
# ログ確認
tail -f /var/log/httpd/ssl_error_log
SSL Library Error: error:140AB18F:SSL routines:SSL_CTX_use_certificate:ee key too small
CentOS 8 (7?) 以降、このエラーが出る。
対処 (SECLEVELを下げる)
debianの場合、以下
- CipherString = DEFAULT@SECLEVEL=2
+ CipherString = DEFAULT@SECLEVEL=1
Ubuntu21.04の場合 Ubuntu 20.04 - how to set lower SSL security level? - Ask Ubuntu
※ openssl version -a でビルド時のオプションがわかる。md5はopenssl 1.1.1では含まれていない。
# ファイルの先頭に記述
openssl_conf = openssl_init
(略)
# ファイルの最後に記述
[openssl_init]
ssl_conf = ssl_sect
[ssl_sect]
system_default = system_default_sect
[system_default_sect]
CipherString = DEFAULT@SECLEVEL=0
CentOS 8 の場合、以下
- DEFAULT
+ LEGACY
update-crypto-policies
-
/etc/crypto-policies/back-ends/*.configが一斉に修正される。
もしくはStrong crypto defaults in RHEL 8 and deprecation of weak crypto algorithms - Red Hat Customer Portal
update-crypto-policies --set LEGACY
ca md too weak への対処
SSL Library Error: error:140AB18E:SSL routines:SSL_CTX_use_certificate:ca md too weak
この場合は、SECLEVEL を さらに下げる。
- @SECLEVEL=1:kEECDH:kRSA:kEDH:kPSK:kDHEPSK:kECDHEPSK:!DES:!RC2:!IDEA:-SEED:!eNULL:!aNULL:!MD5:-SHA384:-CAMELLIA:-ARIA:-AESCCM8
+ @SECLEVEL=0:kEECDH:kRSA:kEDH:kPSK:kDHEPSK:kECDHEPSK:!DES:!RC2:!IDEA:-SEED:!eNULL:!aNULL:!MD5:-SHA384:-CAMELLIA:-ARIA:-AESCCM8
-
update-crypto-policiesを実施しても/etc/crypto-policies/back-ends/openssl.configの内容は変わらなかった。-
update-crypto-policies --set LEGACYの場合は書き換わる。
-
IPA
nginx のログに追加
http {
include /etc/nginx/mime.types;
default_type application/octet-stream;
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
+ '$ssl_client_verify '
+ '$ssl_cipher '
+ '$ssl_protocol '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
#tcp_nopush on;
keepalive_timeout 65;
#gzip on;
include /etc/nginx/conf.d/*.conf;
}
- $ssl_client_verify
-
SUCCESSかNONE
-
- $ssl_cipher
- ECDHE-RSA-AES128-GCM-SHA256
- $ssl_protocol
- TLSv1.2