CloudWatch設定ログ確認
【設定】CloudWatch ログを有効化・ログレベルERROR・リクエスト/レスポンスをすべてログ 【APIエラー】なし
(XXX) Extended Request Id: Dt6vFHHzNjMFahw=
(XXX) Method request path: {}
(XXX) Method request query string: {}
(XXX) Method request headers: {sec-fetch-mode=navigate, referer=https://ap-northeast-1.console.aws.amazon.com/apigateway/home?region=ap-northeast-1, sec-fetch-site=cross-site, accept-language=ja,en-US;q=0.9,en;q=0.8, User-Agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36, X-Forwarded-Proto=http
(XXX) Method request body before transformations:
(XXX) Endpoint request URI: https://【apiid】.execute-api.ap-northeast-1.amazonaws.com/dev/sample
(XXX) Endpoint request headers: {x-amzn-apigateway-api-id=【apiid】, Accept=application/json, User-Agent=AmazonAPIGateway_【apiid】, X-Amzn-Trace-Id=Root=1-5ddbd7fa-0c4187109fb1208005c00fa0}
(XXX) Endpoint request body after transformations:
(XXX) Endpoint response headers: {Date=Mon, 25 Nov 2019 13:32:42 GMT, Content-Type=application/json, Content-Length=70, Connection=keep-alive, x-amzn-RequestId=615c0930-90de-45c7-94bc-22cfc09e7dd5, Access-Control-Allow-Origin=*, x-amz-apigw-id=Dt6vFFtCtjMFuAQ=, X-Amzn-Trace-Id=Root=1-5ddbd7fa-0c4187109fb1208005c00fa0;Sampled=0}
(XXX) Endpoint response body before transformations: {"statusCode": 200, "body": "\"Hello from LambdaMethod:getTextData\""}
(XXX) Method response body after transformations: {"statusCode": 200, "body": "\"Hello from LambdaMethod:getTextData\""}
(XXX) Method response headers: {X-Amzn-Trace-Id=Root=1-5ddbd7fa-0c4187109fb1208005c00fa0;Sampled=0, Content-Type=application/json}
【設定】CloudWatch ログを有効化・ログレベルINFO・リクエスト/レスポンスをすべてログ 【APIエラー】なし
(XXX) Extended Request Id: Dt7aFGdjNjMFYyA=
(XXX) Verifying Usage Plan for request: XXX. API Key: API Stage: 【apiid】/test
(XXX) API Key authorized because method 'GET /backend' does not require API Key. Request will not contribute to throttle or quota limits
(XXX) Starting execution for request: XXX
(XXX) HTTP Method: GET, Resource Path: /backend
(XXX) Method request path: {}
(XXX) Method request query string: {}
(XXX) Method request headers: {sec-fetch-mode=navigate, sec-fetch-site=none, accept-language=ja,en-US;q=0.9,en;q=0.8, User-Agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36, X-Forwarded-Proto=https, Host=【apiid】.execute-api.ap-northeast-1.amazonaws.com, sec-fetch-user=?1, X-Forwarded-Port=44
(XXX) Method request body before transformations:
(XXX) Endpoint request URI: https://【apiid】.execute-api.ap-northeast-1.amazonaws.com/dev/sample
(XXX) Endpoint request headers: {x-amzn-apigateway-api-id=【apiid】, Accept=application/json, User-Agent=AmazonAPIGateway_【apiid】, X-Amzn-Trace-Id=Root=1-5ddbd90d-c9908810aa6d94f0d26dfdc8}
(XXX) Endpoint request body after transformations:
(XXX) Sending request to https://【apiid】.execute-api.ap-northeast-1.amazonaws.com/dev/sample
(XXX) Received response. Status: 200, Integration latency: 52 ms
(XXX) Endpoint response headers: {Date=Mon, 25 Nov 2019 13:37:17 GMT, Content-Type=application/json, Content-Length=70, Connection=keep-alive, x-amzn-RequestId=4e45fba4-1dc3-4fb1-ba93-14ca9d3cf019, Access-Control-Allow-Origin=*, x-amz-apigw-id=Dt7aGHjFtjMFaiQ=, X-Amzn-Trace-Id=Root=1-5ddbd90d-c9908810aa6d94f0d26dfdc8;Sampled=0}
(XXX) Endpoint response body before transformations: {"statusCode": 200, "body": "\"Hello from LambdaMethod:getTextData\""}
(XXX) Method response body after transformations: {"statusCode": 200, "body": "\"Hello from LambdaMethod:getTextData\""}
(XXX) Method response headers: {X-Amzn-Trace-Id=Root=1-5ddbd90d-c9908810aa6d94f0d26dfdc8;Sampled=0, Content-Type=application/json}
(XXX) Successfully completed execution
(XXX) Method completed with status: 200
【設定】CloudWatch ログを有効化・ログレベルINFO・リクエスト 【APIエラー】なし
(XXX) Extended Request Id: Dt75sGkLNjMFY4g=
(XXX) Verifying Usage Plan for request: XXX. API Key: API Stage: 【apiid】/test
(XXX) API Key authorized because method 'GET /backend' does not require API Key. Request will not contribute to throttle or quota limits
(XXX) Starting execution for request: XXX
(XXX) HTTP Method: GET, Resource Path: /backend
(XXX) Successfully completed execution
(XXX) Method completed with status: 200
【設定】CloudWatch ログを有効化・ログレベルERROR・リクエスト 【APIエラー】なし
ログなし
【設定】CloudWatch ログを有効化・ログレベルERROR・リクエスト 【APIエラー】あり
(XXX) Extended Request Id: Dt90EE2ANjMFU2Q=
(XXX) Request parameter validation failed. Missing parameters: [aa]
【設定】CloudWatch ログを有効化・ログレベルINFO・リクエスト 【APIエラー】あり
(XXX) Extended Request Id: Dt-CZFF3NjMFSuw=
(XXX) Verifying Usage Plan for request: XXX. API Key: API Stage: 【apiid】/test
(XXX) API Key authorized because method 'GET /backend' does not require API Key. Request will not contribute to throttle or quota limits
(XXX) Starting execution for request: XXX
(XXX) HTTP Method: GET, Resource Path: /backend
(XXX) Request parameter validation failed. Missing parameters: [aa]
(XXX) Method completed with status: 400
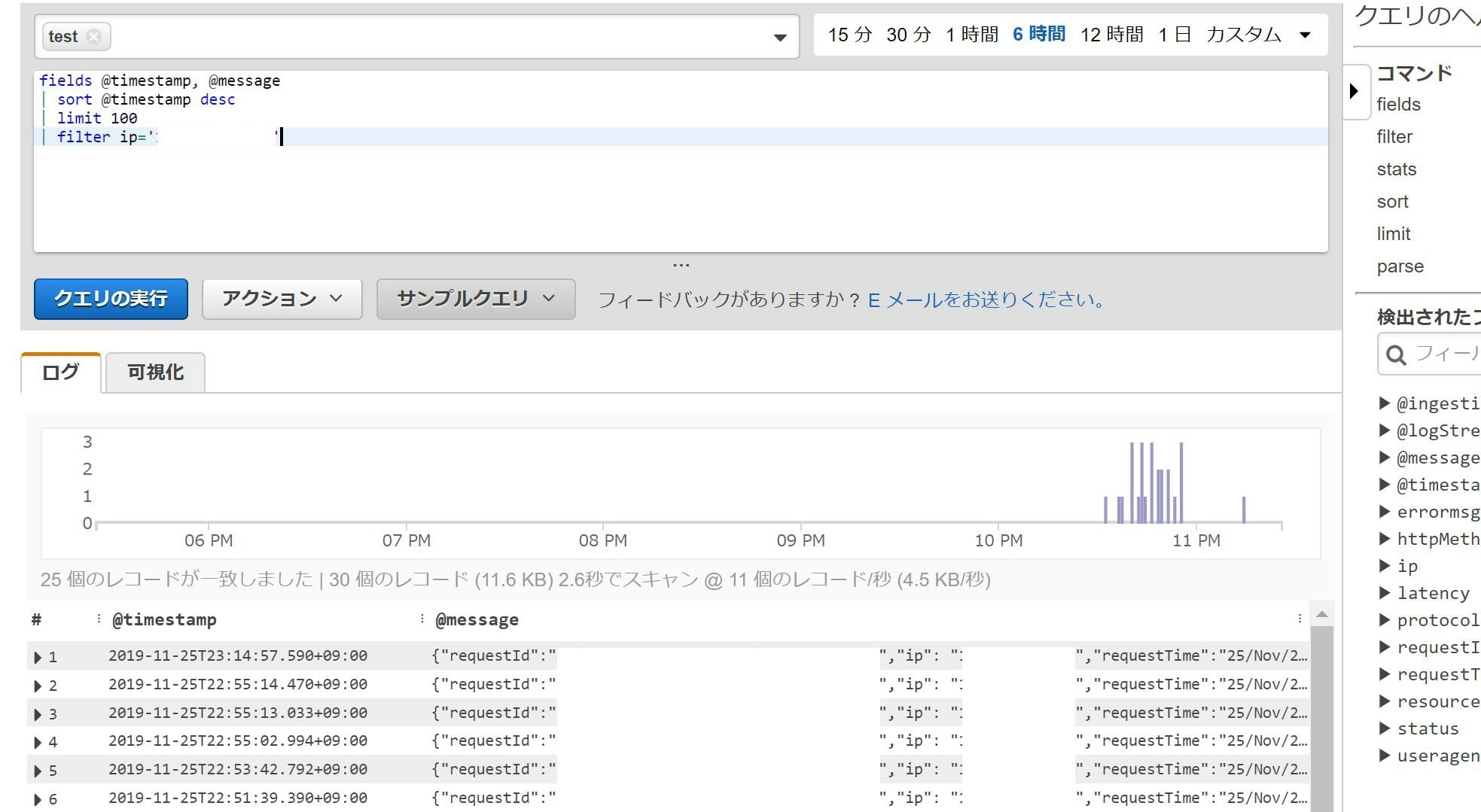
カスタムアクセスのログ記録
ログの形式(個人的にこれぐらいあればいいんじゃないかと)
{
"requestId":"$context.requestId",
"ip": "$context.identity.sourceIp",
"requestTime":"$context.requestTime",
"httpMethod":"$context.httpMethod",
"resourcePath":"$context.resourcePath",
"status":"$context.status",
"protocol":"$context.protocol",
"errormsg":"$context.error.message",
"useragent":"$context.identity.userAgent",
"latency":"$context.responseLatency"
}
出力結果(エラー時)
{
"requestId": "4ad3c1e9-0ec4-418e-aacb-76779745107f",
"ip": "XXX.XXX.XXX.XXX",
"requestTime": "25/Nov/2019:14:14:57 +0000",
"httpMethod": "GET",
"resourcePath": "/backend",
"status": "400",
"protocol": "HTTP/1.1",
"errormsg": "Missing required request parameters: [aa]",
"useragent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36",
"latency": "9"
}
CloudWatchログインサイト
ログの保持期間も検討しないと。。★調べ中★
・ロググループごとにログが削除される期間を設定できる。
・ロググループごとに指定期間のログをS3へエクスポートできる。(バッチの設定はできない)
⇒Lambdaで1日一回つついて、期限が切れているログをS3へはくというのが、
便利だなと思いました。
https://www.ipa.go.jp/files/000052999.pdf
https://dev.classmethod.jp/cloud/aws/export-cloudwatch-logs-to-s3/
http://chuu-information.com/cloud/post-569/
https://www.webprofessional.jp/monitoring-of-aws-cloudwatch/