はじめに
site-to-site VPN を使うことで、オンプレミスネットワークと VPC 間でセキュアな接続が出来ます。今回は、ソフトウェアルーターの VyOS を使って、site-to-site VPN の手順を紹介します。
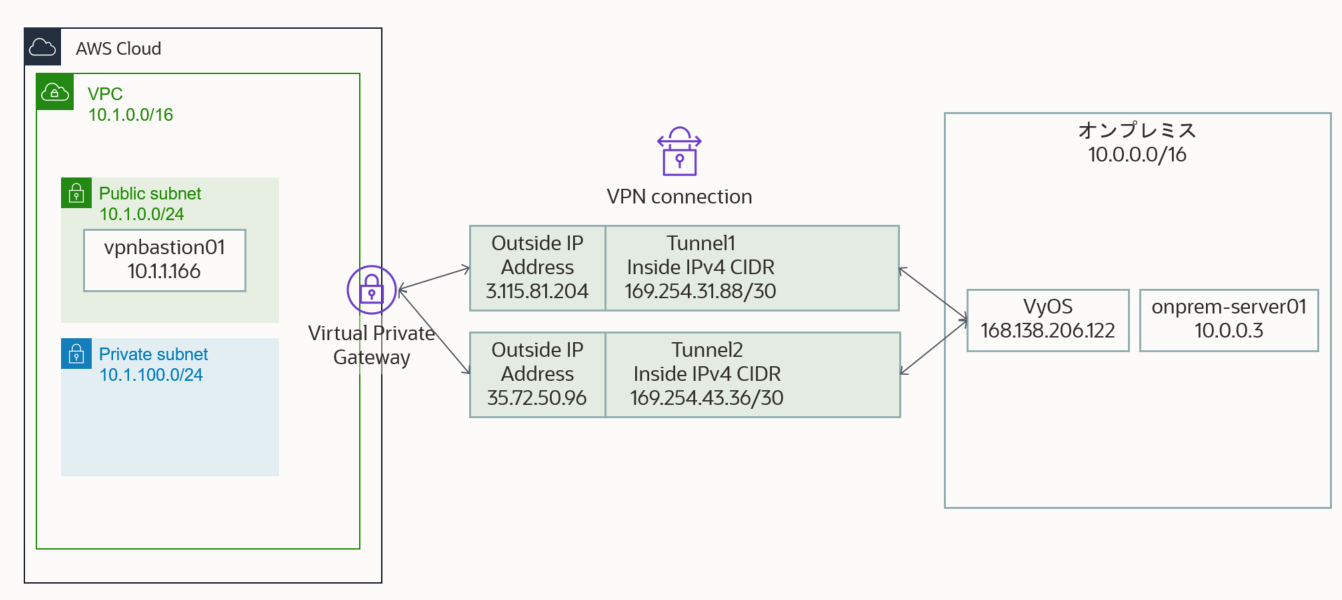
NW構成図
オンプレミス (10.0.0.0/16) と AWS VPC (10.1.0.0/16) 間で、VPN を設定します。
図の中の Public IP は既に削除しているので、アクセスできません
オンプレミス側に、VyOS を作成
適当にオンプレミス側でVyOS の仮想マシンを作成します。詳細は Google さんに聞いてみましょう。
Customer Gateway を作成
AWS側で、VyOS に対応する Customer Gateway を作成します
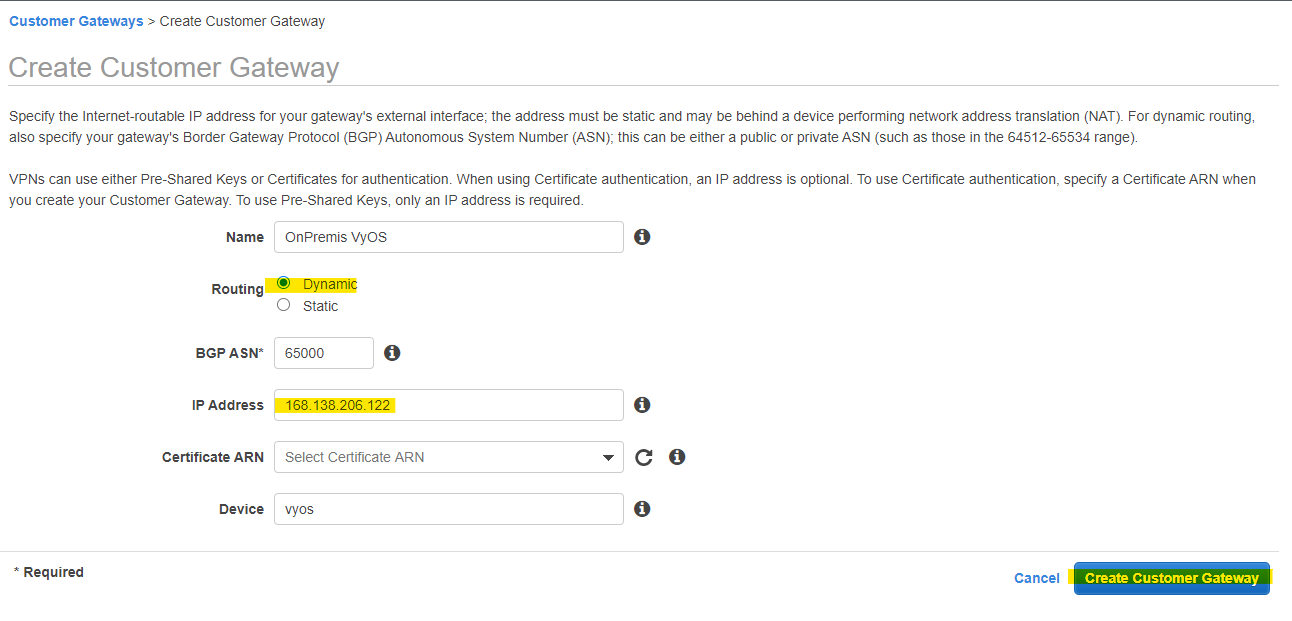
Create
VyOS の Public IP などを指定して、Create します
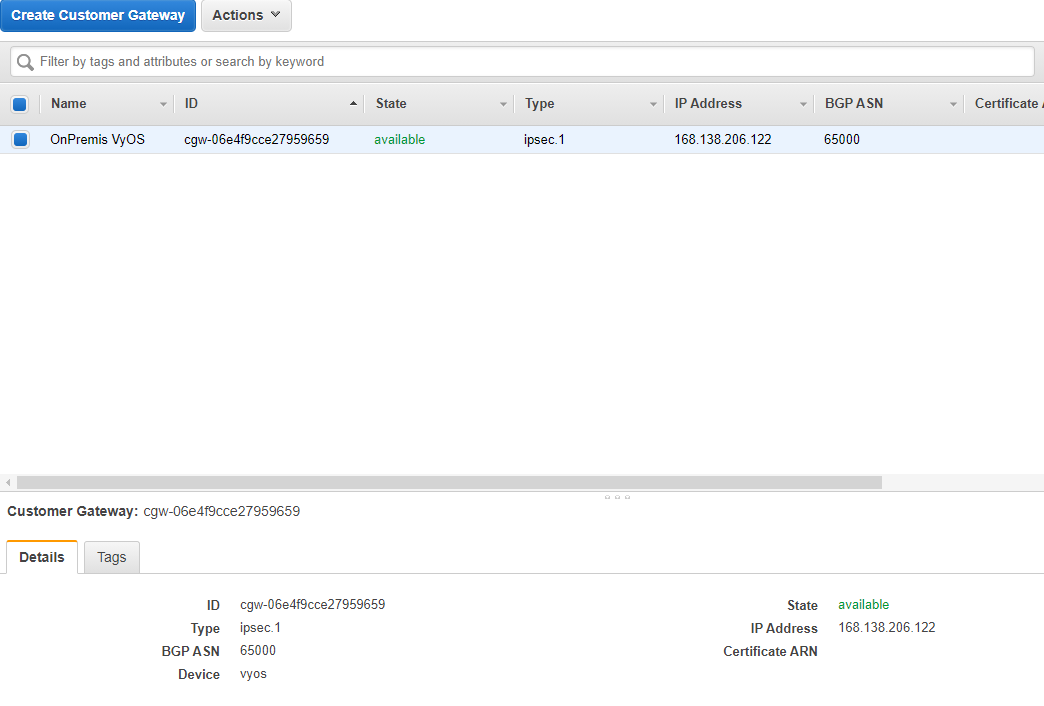
作成完了
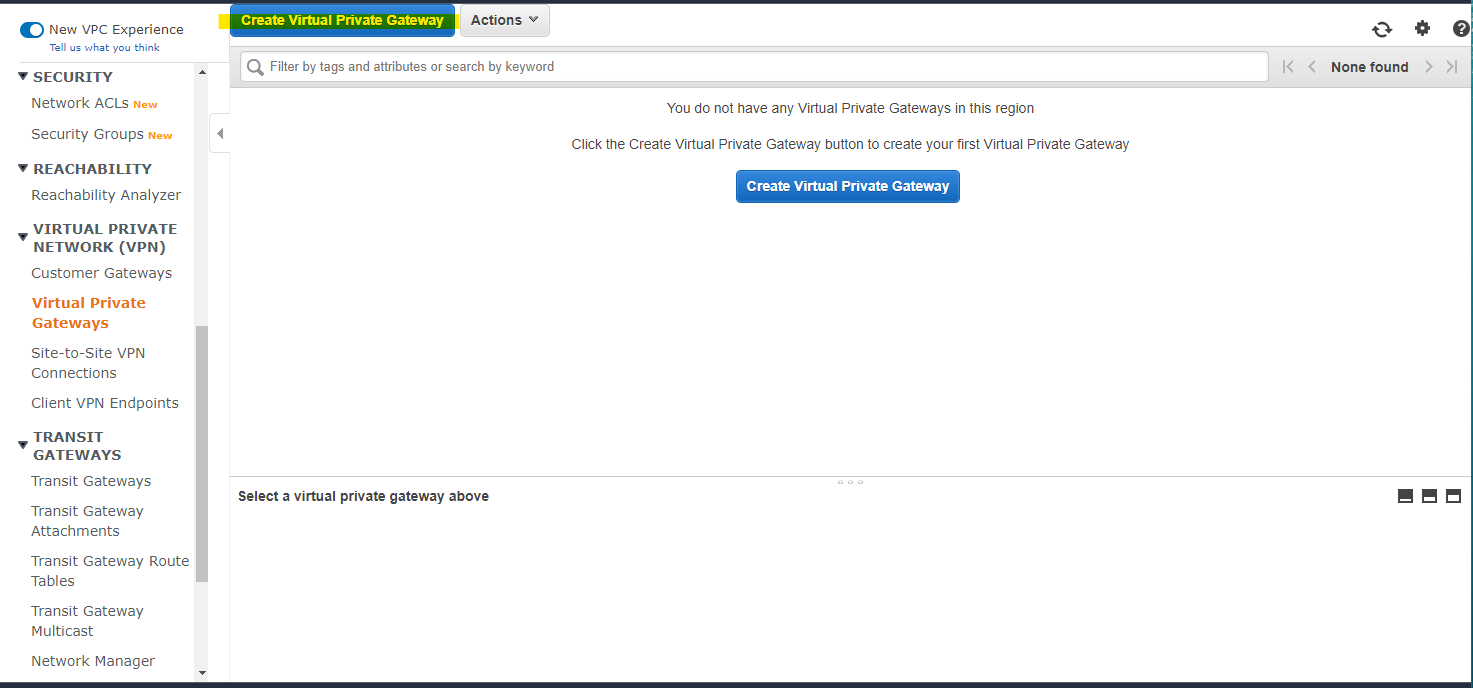
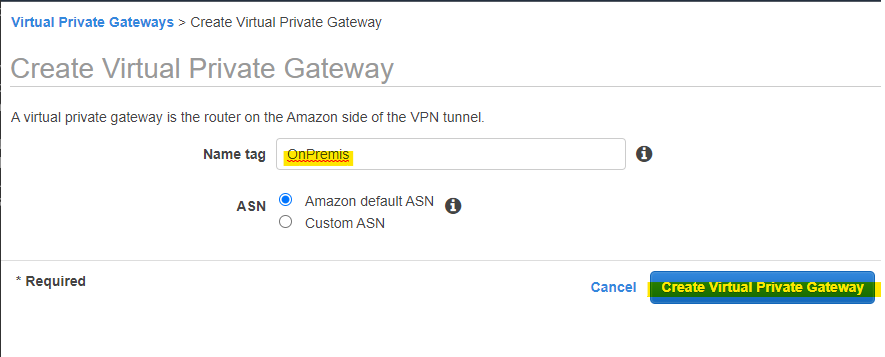
Virtual Private Gateway 作成
今回の記事では、Virtual Private Gateway を作成します。Transit Gateway でも大丈夫です。
Create
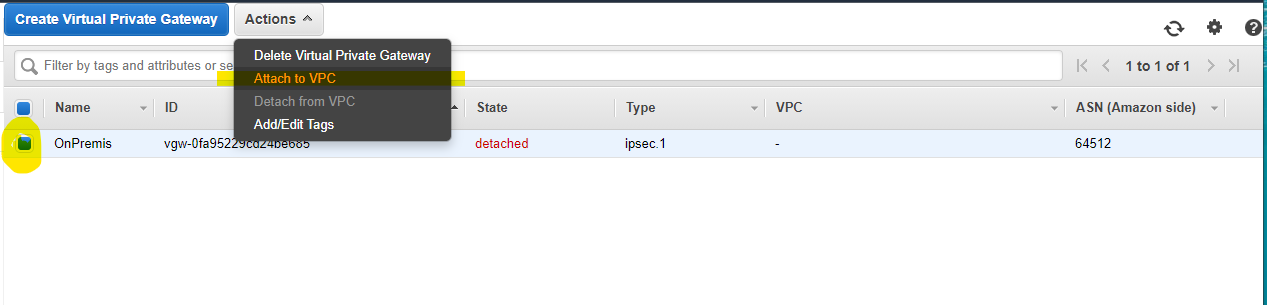
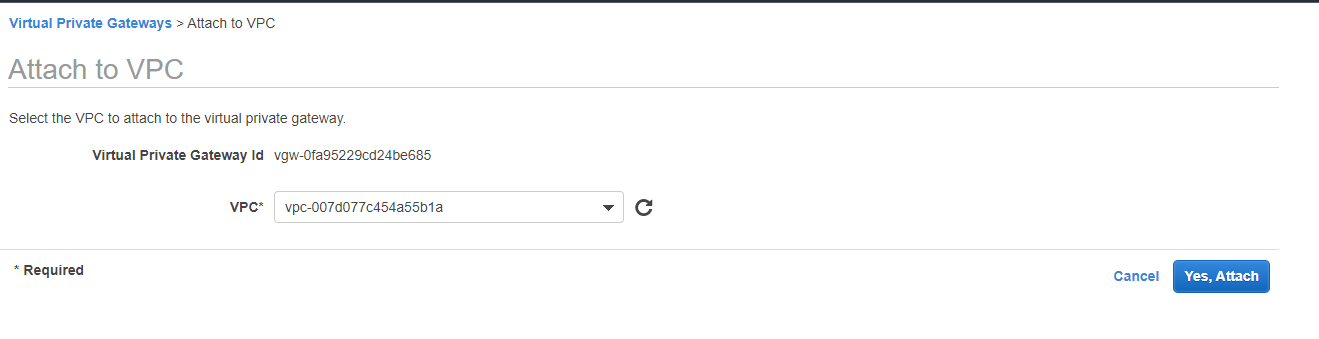
Attach to VPC
Yes, Attach
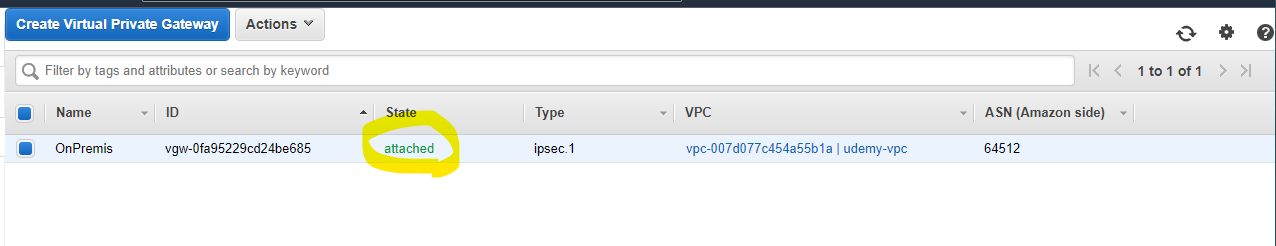
State が attached に変わります
Route Table の設定
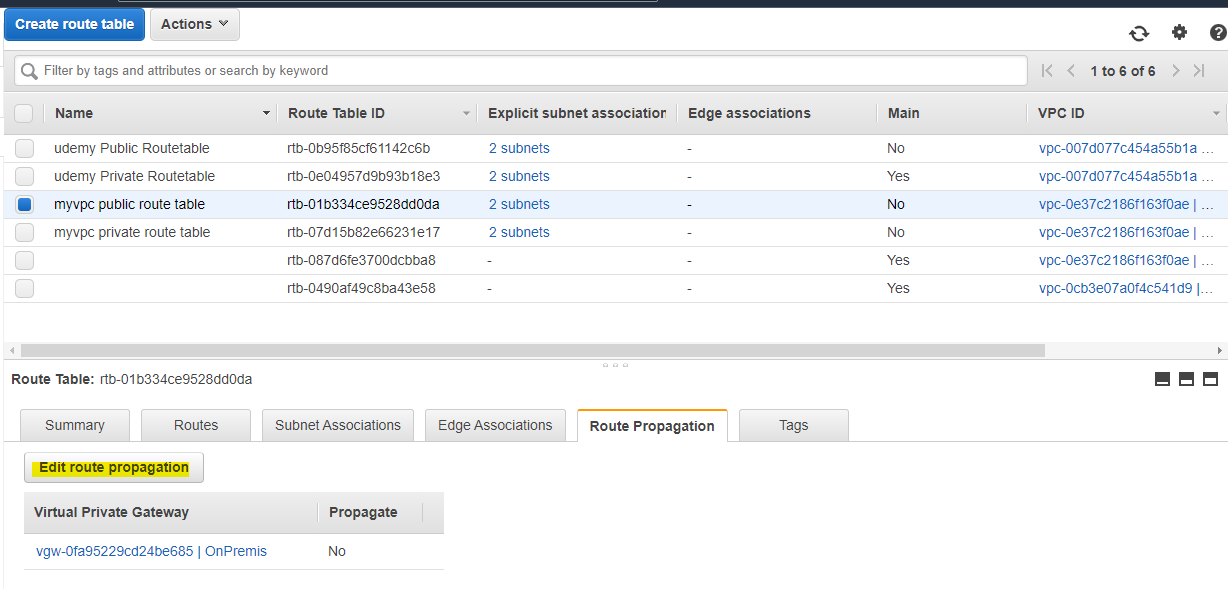
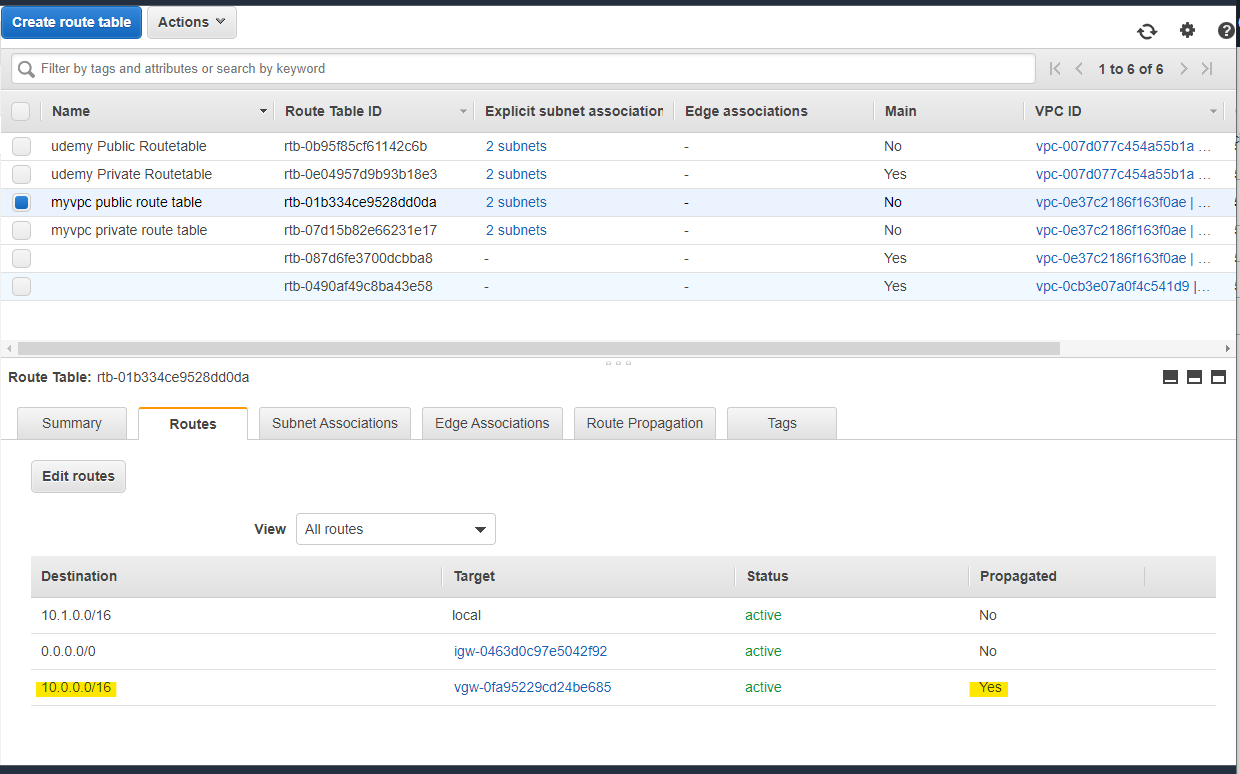
Site-to-Site VPN のルートを自動的に Route Table に伝搬(Route Propagation) できます。対象の Route Table を選択して、Edit route propagation を押します。
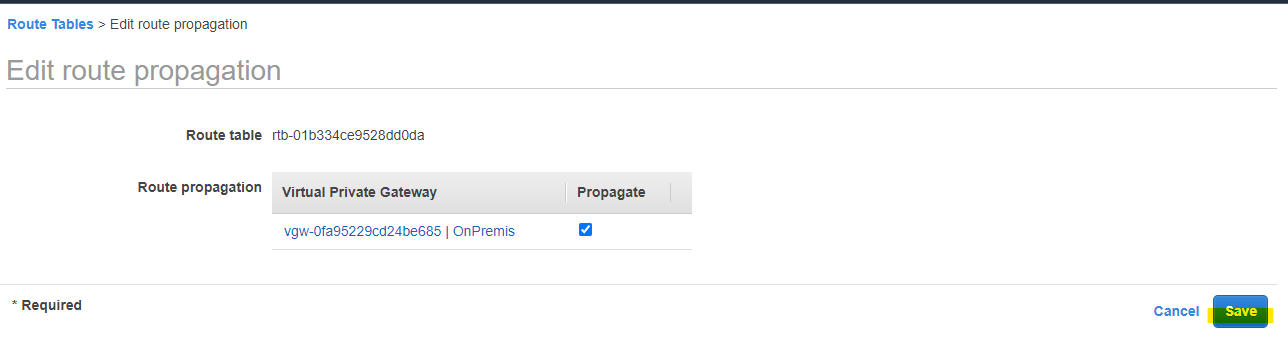
作成した Virtual Private Gateway を選択を選択して、Save を押します
この段階では、まだ ルート伝搬されません
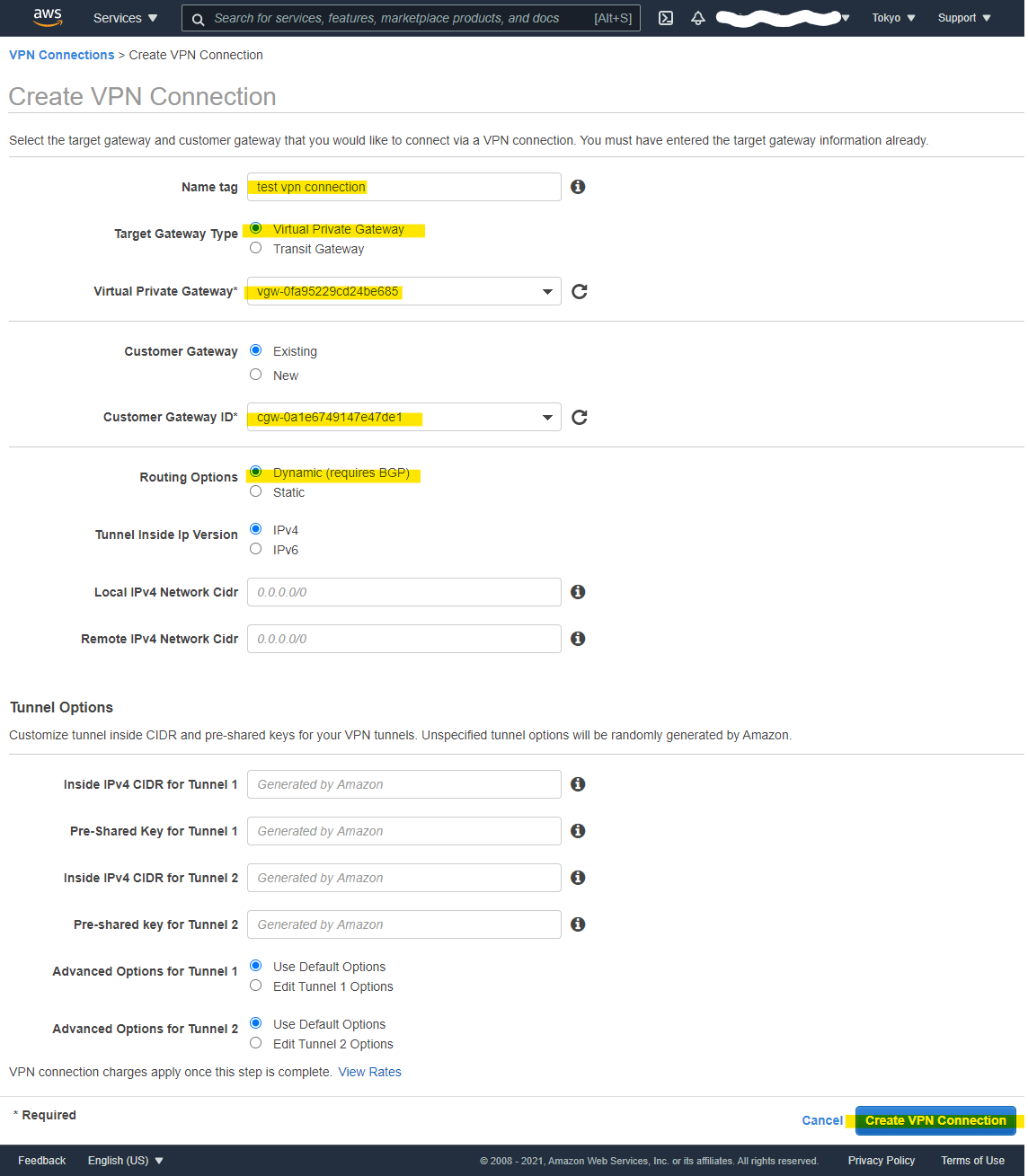
Site-to-Site VPN Connection を作成
Create
Create
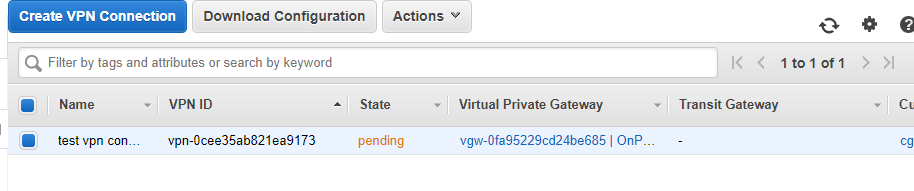
Pending になります。available に一定時間後変わります
オンプレミス側 : VyOS の設定
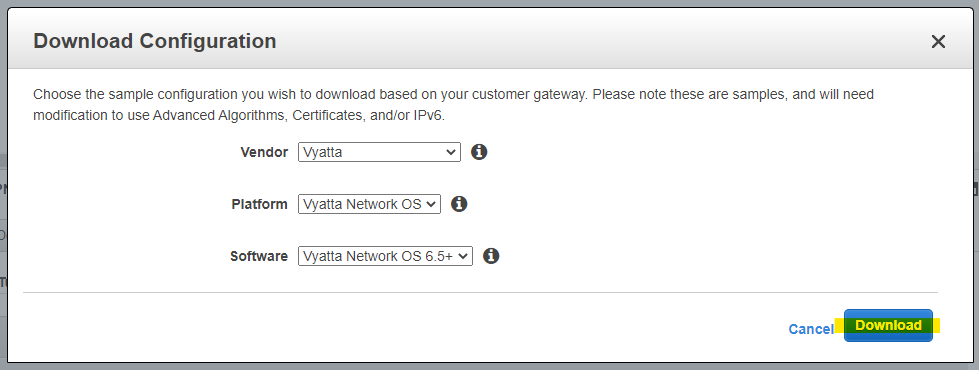
VyOS の設定テンプレートは、AWS マネージメントコンソールからダウンロードできます。
Download Configuration
Download
VyOS に SSH 接続して、configure mode に変更
vyos@vyos:~$ configure
[edit]
vyos@vyos#
この記事の環境では、ダウンロードした config ファイルから、一部変更が必要です。次の local-address の部分が、Customer Gateway の Public IP から、Private IP に変更します。
# before
set vpn ipsec site-to-site peer 3.115.81.204 local-address '168.138.206.122'
set vpn ipsec site-to-site peer 35.72.50.96 local-address '168.138.206.122'
# after
set vpn ipsec site-to-site peer 3.115.81.204 local-address '10.0.0.2'
set vpn ipsec site-to-site peer 35.72.50.96 local-address '10.0.0.2'
変更した設定ファイルの内容を投入したのちに、設定を保存します。config ファイルの内容は、精査して問題なさそうか確認してください。
commit
save
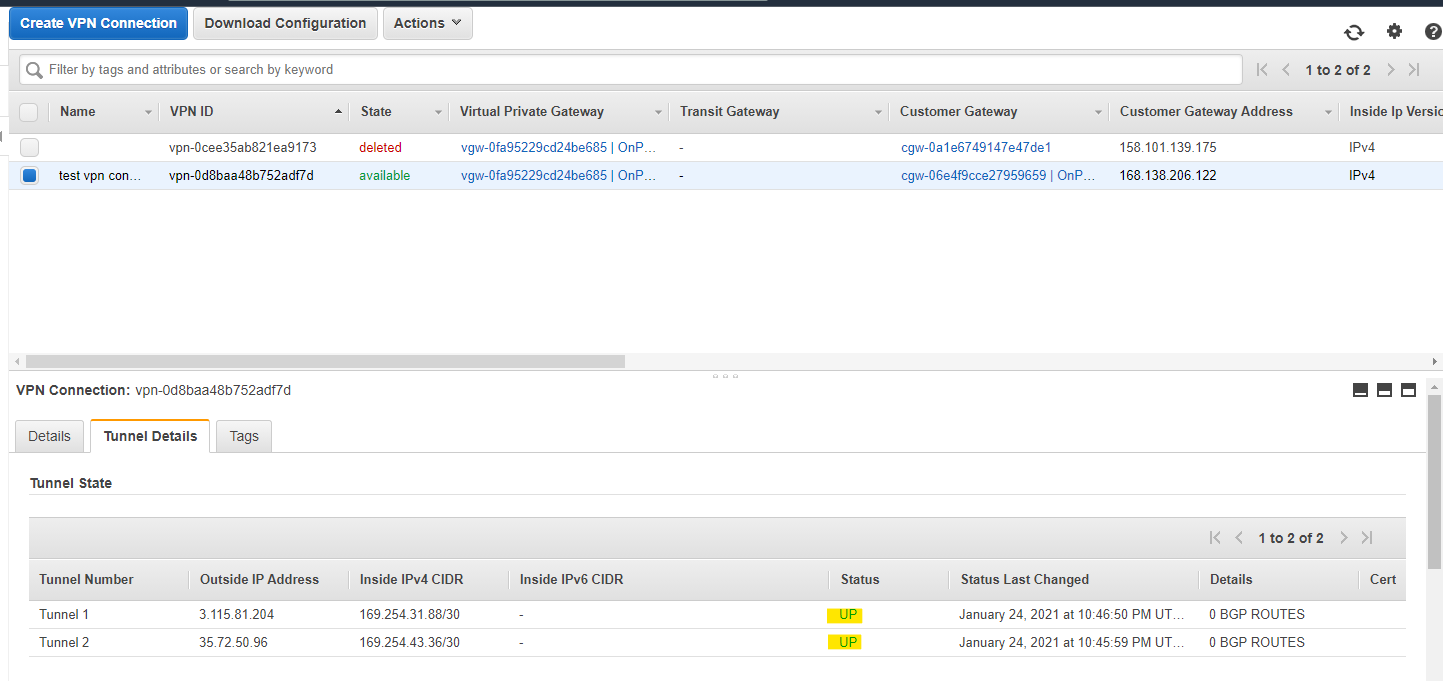
2 つのトンネル Status が UP になる
AWS VPC の CIDR 全体が、オンプレミスのルーター側に広告されています。10.1.0.0/16 の Next Hop が表示されています。
vyos@vyos:~$ show ip bgp
BGP table version is 1, local router ID is 10.0.0.2, vrf id 0
Default local pref 100, local AS 65000
Status codes: s suppressed, d damped, h history, * valid, > best, = multipath,
i internal, r RIB-failure, S Stale, R Removed
Nexthop codes: @NNN nexthop's vrf id, < announce-nh-self
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
* 10.1.0.0/16 169.254.31.89 200 0 64512 i
* *> 169.254.43.37 100 0 64512 i
Displayed 1 routes and 2 total paths
vyos@vyos:~$
Next Hop に Ping 可能
vyos@vyos:~$ ping 169.254.31.89
PING 169.254.31.89 (169.254.31.89) 56(84) bytes of data.
64 bytes from 169.254.31.89: icmp_seq=1 ttl=254 time=3.34 ms
64 bytes from 169.254.31.89: icmp_seq=2 ttl=254 time=3.28 ms
^C
--- 169.254.31.89 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 3.286/3.314/3.342/0.028 ms
vyos@vyos:~$
vyos@vyos:~$ ping 169.254.43.37
PING 169.254.43.37 (169.254.43.37) 56(84) bytes of data.
64 bytes from 169.254.43.37: icmp_seq=1 ttl=254 time=4.11 ms
64 bytes from 169.254.43.37: icmp_seq=2 ttl=254 time=3.94 ms
64 bytes from 169.254.43.37: icmp_seq=3 ttl=254 time=4.11 ms
^C
--- 169.254.43.37 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 3.944/4.056/4.112/0.079 ms
vyos@vyos:~$
VyOS のルーティングテーブルにも、正常に VPC の CIDR が反映されています
vyos@vyos:~$ ip route show
default via 10.0.0.1 dev eth0 proto static metric 20
10.0.0.0/24 dev eth0 proto kernel scope link src 10.0.0.2
10.1.0.0/16 via 169.254.43.37 dev vti1 proto bgp metric 20
169.254.31.88/30 dev vti0 proto kernel scope link src 169.254.31.90
169.254.43.36/30 dev vti1 proto kernel scope link src 169.254.43.38
vyos@vyos:~$
オンプレミス側のネットワークを AWS 側に広告する設定をいれます
set protocols bgp 65000 address-family ipv4-unicast network 10.0.0.0/16
commit
save
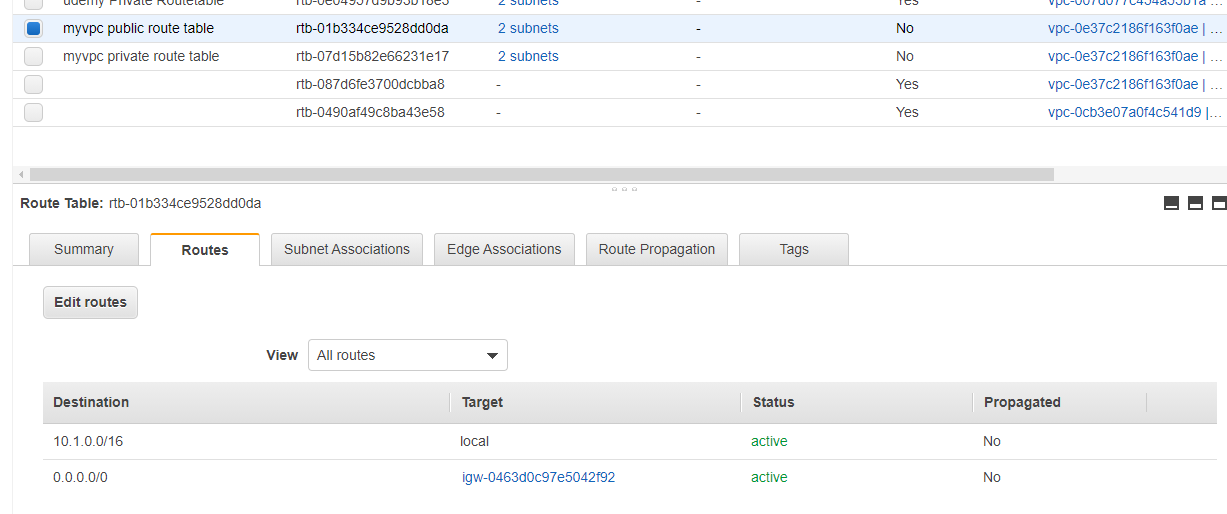
設定を入れたタイミングで、AWS の Route Table に、オンプレミス側のネットワークが自動的に伝搬されています
通信確認
OnPremis → AWS Ping
[opc@onprem-server01 ~]$ ping 10.1.1.166
PING 10.1.1.166 (10.1.1.166) 56(84) bytes of data.
64 bytes from 10.1.1.166: icmp_seq=1 ttl=253 time=7.27 ms
64 bytes from 10.1.1.166: icmp_seq=2 ttl=253 time=7.00 ms
64 bytes from 10.1.1.166: icmp_seq=3 ttl=253 time=6.87 ms
^C
--- 10.1.1.166 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 6.871/7.049/7.270/0.165 ms
[opc@onprem-server01 ~]$
OnPremis → AWS SSH
[opc@onprem-server01 ~]$ ssh ec2-user@10.1.1.166
Last login: Sun Jan 24 14:14:24 2021 from 10.0.0.3
__| __|_ )
_| ( / Amazon Linux 2 AMI
___|\___|___|
https://aws.amazon.com/amazon-linux-2/
2 package(s) needed for security, out of 5 available
Run "sudo yum update" to apply all updates.
[ec2-user@ip-10-1-1-166 ~]$
付録 : VyOS の Configure
この記事で動作確認したもの。VPN Connection は既に削除しているので、セキュリティ的に問題なし
! Amazon Web Services
! Virtual Private Cloud
! AWS utilizes unique identifiers to manipulate the configuration of
! a VPN Connection. Each VPN Connection is assigned an identifier and is
! associated with two other identifiers, namely the
! Customer Gateway Identifier and Virtual Private Gateway Identifier.
!
! Your VPN Connection ID : vpn-0d8baa48b752adf7d
! Your Virtual Private Gateway ID : vgw-0fa95229cd24be685
! Your Customer Gateway ID : cgw-06e4f9cce27959659
!
!
! This configuration consists of two tunnels. Both tunnels must be
! configured on your Customer Gateway.
!
! --------------------------------------------------------------------------------
! IPSec Tunnel #1
! --------------------------------------------------------------------------------
! #1: Internet Key Exchange (IKE) Configuration
!
! A policy is established for the supported ISAKMP encryption,
! authentication, Diffie-Hellman, lifetime, and key parameters.
! Please note, these sample configurations are for the minimum requirement of AES128, SHA1, and DH Group 2.
! Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
! You will need to modify these sample configuration files to take advantage of AES256, SHA256, or other DH groups like 2, 14-18, 22, 23, and 24.
! NOTE: If you customized tunnel options when creating or modifying your VPN connection, you may need to modify these sample configurations to match the custom settings for your tunnels.
!
! Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
! The address of the external interface for your customer gateway must be a static address.
! Your customer gateway may reside behind a device performing network address translation (NAT).
! To ensure that NAT traversal (NAT-T) can function, you must adjust your firewall !rules to unblock UDP port 4500. If not behind NAT, we recommend disabling NAT-T.
!
set vpn ipsec ike-group AWS lifetime '28800'
set vpn ipsec ike-group AWS proposal 1 dh-group '2'
set vpn ipsec ike-group AWS proposal 1 encryption 'aes128'
set vpn ipsec ike-group AWS proposal 1 hash 'sha1'
set vpn ipsec site-to-site peer 3.115.81.204 authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer 3.115.81.204 authentication pre-shared-secret 'your secret1'
set vpn ipsec site-to-site peer 3.115.81.204 description 'VPC tunnel 1'
set vpn ipsec site-to-site peer 3.115.81.204 ike-group 'AWS'
set vpn ipsec site-to-site peer 3.115.81.204 local-address '10.0.0.2'
set vpn ipsec site-to-site peer 3.115.81.204 vti bind 'vti0'
set vpn ipsec site-to-site peer 3.115.81.204 vti esp-group 'AWS'
! #2: IPSec Configuration
!
! The IPSec (Phase 2) proposal defines the protocol, authentication,
! encryption, and lifetime parameters for our IPSec security association.
! Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
! Please note, you may use these additionally supported IPSec parameters for encryption like AES256 and other DH groups like 2, 5, 14-18, 22, 23, and 24.
! Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
!
set vpn ipsec ipsec-interfaces interface 'eth0'
set vpn ipsec esp-group AWS compression 'disable'
set vpn ipsec esp-group AWS lifetime '3600'
set vpn ipsec esp-group AWS mode 'tunnel'
set vpn ipsec esp-group AWS pfs 'enable'
set vpn ipsec esp-group AWS proposal 1 encryption 'aes128'
set vpn ipsec esp-group AWS proposal 1 hash 'sha1'
! This option enables IPSec Dead Peer Detection, which causes periodic
! messages to be sent to ensure a Security Association remains operational.
!
set vpn ipsec ike-group AWS dead-peer-detection action 'restart'
set vpn ipsec ike-group AWS dead-peer-detection interval '15'
set vpn ipsec ike-group AWS dead-peer-detection timeout '30'
! --------------------------------------------------------------------------------
! #3: Tunnel Interface Configuration
!
! The tunnel interface is configured with the internal IP address.
set interfaces vti vti0 address '169.254.31.90/30'
set interfaces vti vti0 description 'VPC tunnel 1'
set interfaces vti vti0 mtu '1436'
! --------------------------------------------------------------------------------
! #4: Border Gateway Protocol (BGP) Configuration
!
! BGP is used within the tunnel to exchange prefixes between the
! Virtual Private Gateway and your Customer Gateway. The Virtual Private Gateway
! will announce the prefix corresponding to your VPC.
!
! Your Customer Gateway may announce a default route (0.0.0.0/0),
! which can be done with the 'network' statement.
!
! The BGP timers are adjusted to provide more rapid detection of outages.
!
! The local BGP Autonomous System Number (ASN) (65000) is configured
! as part of your Customer Gateway. If the ASN must be changed, the
! Customer Gateway and VPN Connection will need to be recreated with AWS.
!
set protocols bgp 65000 neighbor 169.254.31.89 remote-as '64512'
set protocols bgp 65000 neighbor 169.254.31.89 soft-reconfiguration 'inbound'
set protocols bgp 65000 neighbor 169.254.31.89 timers holdtime '30'
set protocols bgp 65000 neighbor 169.254.31.89 timers keepalive '10'
! To advertise additional prefixes to Amazon VPC, replace the 0.0.0.0/0 from the
! the following line with the prefix you wish to advertise. Make sure the prefix is present
! in the routing table of the device with a valid next-hop.
set protocols bgp 65000 network 0.0.0.0/0
! --------------------------------------------------------------------------------
! IPSec Tunnel #2
! --------------------------------------------------------------------------------
! #1: Internet Key Exchange (IKE) Configuration
!
! A policy is established for the supported ISAKMP encryption,
! authentication, Diffie-Hellman, lifetime, and key parameters.
! Please note, these sample configurations are for the minimum requirement of AES128, SHA1, and DH Group 2.
! Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
! You will need to modify these sample configuration files to take advantage of AES256, SHA256, or other DH groups like 2, 14-18, 22, 23, and 24.
! NOTE: If you customized tunnel options when creating or modifying your VPN connection, you may need to modify these sample configurations to match the custom settings for your tunnels.
!
! Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
! The address of the external interface for your customer gateway must be a static address.
! Your customer gateway may reside behind a device performing network address translation (NAT).
! To ensure that NAT traversal (NAT-T) can function, you must adjust your firewall !rules to unblock UDP port 4500. If not behind NAT, we recommend disabling NAT-T.
!
set vpn ipsec ike-group AWS lifetime '28800'
set vpn ipsec ike-group AWS proposal 1 dh-group '2'
set vpn ipsec ike-group AWS proposal 1 encryption 'aes128'
set vpn ipsec ike-group AWS proposal 1 hash 'sha1'
set vpn ipsec site-to-site peer 35.72.50.96 authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer 35.72.50.96 authentication pre-shared-secret 'your secret2'
set vpn ipsec site-to-site peer 35.72.50.96 description 'VPC tunnel 2'
set vpn ipsec site-to-site peer 35.72.50.96 ike-group 'AWS'
set vpn ipsec site-to-site peer 35.72.50.96 local-address '10.0.0.2'
set vpn ipsec site-to-site peer 35.72.50.96 vti bind 'vti1'
set vpn ipsec site-to-site peer 35.72.50.96 vti esp-group 'AWS'
! #2: IPSec Configuration
!
! The IPSec (Phase 2) proposal defines the protocol, authentication,
! encryption, and lifetime parameters for our IPSec security association.
! Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
! Please note, you may use these additionally supported IPSec parameters for encryption like AES256 and other DH groups like 2, 5, 14-18, 22, 23, and 24.
! Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
!
set vpn ipsec ipsec-interfaces interface 'eth0'
set vpn ipsec esp-group AWS compression 'disable'
set vpn ipsec esp-group AWS lifetime '3600'
set vpn ipsec esp-group AWS mode 'tunnel'
set vpn ipsec esp-group AWS pfs 'enable'
set vpn ipsec esp-group AWS proposal 1 encryption 'aes128'
set vpn ipsec esp-group AWS proposal 1 hash 'sha1'
! This option enables IPSec Dead Peer Detection, which causes periodic
! messages to be sent to ensure a Security Association remains operational.
!
set vpn ipsec ike-group AWS dead-peer-detection action 'restart'
set vpn ipsec ike-group AWS dead-peer-detection interval '15'
set vpn ipsec ike-group AWS dead-peer-detection timeout '30'
! --------------------------------------------------------------------------------
! #3: Tunnel Interface Configuration
!
! The tunnel interface is configured with the internal IP address.
set interfaces vti vti1 address '169.254.43.38/30'
set interfaces vti vti1 description 'VPC tunnel 2'
set interfaces vti vti1 mtu '1436'
! --------------------------------------------------------------------------------
! #4: Border Gateway Protocol (BGP) Configuration
!
! BGP is used within the tunnel to exchange prefixes between the
! Virtual Private Gateway and your Customer Gateway. The Virtual Private Gateway
! will announce the prefix corresponding to your VPC.
!
! Your Customer Gateway may announce a default route (0.0.0.0/0),
! which can be done with the 'network' statement.
!
! The BGP timers are adjusted to provide more rapid detection of outages.
!
! The local BGP Autonomous System Number (ASN) (65000) is configured
! as part of your Customer Gateway. If the ASN must be changed, the
! Customer Gateway and VPN Connection will need to be recreated with AWS.
!
set protocols bgp 65000 neighbor 169.254.43.37 remote-as '64512'
set protocols bgp 65000 neighbor 169.254.43.37 soft-reconfiguration 'inbound'
set protocols bgp 65000 neighbor 169.254.43.37 timers holdtime '30'
set protocols bgp 65000 neighbor 169.254.43.37 timers keepalive '10'
! To advertise additional prefixes to Amazon VPC, replace the 0.0.0.0/0 from the
! the following line with the prefix you wish to advertise. Make sure the prefix is present
! in the routing table of the device with a valid next-hop.
set protocols bgp 65000 network 0.0.0.0/0
! Additional Notes and Questions
! - Amazon Virtual Private Cloud Getting Started Guide:
! http://docs.amazonwebservices.com/AmazonVPC/latest/GettingStartedGuide
! - Amazon Virtual Private Cloud Network Administrator Guide:
! http://docs.amazonwebservices.com/AmazonVPC/latest/NetworkAdminGuide
! - XSL Version: 2009-07-15-1119716
参考URL
AWS Site-to-Site VPN とは
https://docs.aws.amazon.com/ja_jp/vpn/latest/s2svpn/VPC_VPN.html
Amazon Virtual Private Cloud ネットワーク管理者ガイド (Amzon でテスト済みの Customer Gateway Device あり)
https://docs.aws.amazon.com/ja_jp/vpc/latest/adminguide/vpc-nag.pdf