はじめに
記事について
OpenWrt向け広告ブロック・DNS暗号化の情報記事です
AdGuard Home、NextDNS、AdBlock、DNS over HTTPS/TLS(DoH/DoT)の設定スクリプトを掲載しています
初心者対応構成
- スクリプトでの自動設定
-
UCI (ttyd)、Webコンソール (LuCi)、ファイラー (SFTP)にて比較作業がおススメ

デバイスアクセス
PowerShellの開始
- キー入力:
Win+x>a>はい
UCI(SSH)アクセス
ssh -o StrictHostKeyChecking=no -oHostKeyAlgorithms=+ssh-rsa root@192.168.1.1
- root@192.168.1.1's password:
初期値:パスワード無し
OpenSSHのインストールが無い場合
- 機能の確認
※Windows 10 Fall Creators Update(1709)以降標準搭載
Get-WindowsCapability -Online | Where-Object Name -like 'OpenSSH*'
- 機能のインストール
Add-WindowsCapability -Online -Name OpenSSH.Server~~~~0.0.1.0
以下排他利用推奨
- AdGuard HomeとNextDNS
- AdGuard HomeとAdBlock
- AdGuard HomeとDNS over HTTPS (DoH)
- AdGuard HomeとDNS over TLS (DoT)
- NextDNSとAdBlock
- NextDNSとDNS over HTTPS (DoH)
- NextDNSとDNS over TLS (DoT)
- AdBlockとDNS over HTTPS (DoH)
- AdBlockとDNS over TLS (DoT)
- DNS over HTTPS (DoH)とDNS over TLS (DoT)
推奨条件
- AdGuard Home
- フラッシュ容量: 12MB以上
- メモリ: 1GB以上推奨
- 自宅固定ルーター向け
- AdBlock(fast)
- フラッシュ容量が小さい場合推奨
- 低スペック機向け
- NextDNS
- デバイス性能が低い場合推奨
- トラベルルーター、モバイルルーター向け
- 外出先での利用
AdGuard Home and NextDNS
参考
応答速度(レイテンシ)
- AdGuard Home
- 速度: 1〜5ms(ローカル処理)
- NextDNS
- 速度: 20〜50ms(インターネット経由、エニーキャスト)
スループット(処理能力)
- AdGuard Home
- 性能: 数万qps(クエリ/秒)可能
- ルーターのCPU/メモリ性能に依存
- NextDNS
- 性能: ネットワーク帯域とサーバー負荷次第
- 無料プランは月30万クエリまで
フィルタリング精度
- AdGuard Home
- 無制限にフィルタリスト追加可能
- 正規表現対応
- 独自ルール作成可能
- NextDNS
- 用意されたリストから選択
- カスタマイズに制限あり
リソース消費
- AdGuard Home
- 常時50〜200MB程度のメモリ使用
- CPU数%使用
- 外部通信不要
- NextDNS
- ルーターのCPU/メモリをほぼ使わない
- 全てのDNSクエリが外部送信される
- 通信量増加
プライバシー
- AdGuard Home
- 完全にローカル処理
- クエリログは自分だけが管理
- 第三者にデータ送信なし
- NextDNS
- クエリデータが外部サーバーに送信される
- 匿名化オプションあり
- GDPR準拠
- ログ保持期間を選択可能
管理・運用
- AdGuard Home
- 詳細な統計情報
- リアルタイムログ
- 定期的なアップデート必要
- フィルタリストの更新管理必要
- NextDNS
- メンテナンスフリー
- 自動アップデート
- 複数デバイスで同一設定を共有可能
- 設定変更はWeb経由のみ
コスト
- AdGuard Home
- 完全無料、無制限
- NextDNS
- 月30万クエリまで無料、超過後は有料(月$1.99〜)
利用シーン
- AdGuard Home
- 自宅の固定ルーターに最適
- 常時稼働環境向け
- NextDNS
- トラベルルーター、モバイルルーターに最適
- どこでも同じ設定
- デバイスを変えても設定が保持される
- インターネット接続が必須
アドガードホームをNextDNSクライアントとして使用する
AGHはフィルタリングを無効にしてNextDNSクライアントとして使用することをお勧めします
- upstream_dns:
# ネクストDNSエンドポイント
quic://<ID>.dns.nextdns.io
tls://<ID>.dns.nextdns.io
https://dns.nextdns.io/<ID>
- upstream_mode:
fastest_addr
NextDNS
設定
NextDNS
#!/bin/sh
I18N="ja"
NEXTDNS_CONFIG_ID="YOUR_CONFIG_ID"
PKGS="luci-i18n-nextdns-${I18N}"
command -v opkg && opkg update && opkg install $PKGS
command -v apk && apk update && apk add $PKGS
uci set dhcp.@dnsmasq[0].noresolv='1'
uci -q delete dhcp.@dnsmasq[0].server
uci add_list dhcp.@dnsmasq[0].server='127.0.0.1#5342'
uci commit dhcp
uci set nextdns.main=nextdns
uci set nextdns.main.enabled='1'
uci set nextdns.main.config_id="${NEXTDNS_CONFIG_ID}"
uci set nextdns.main.setup_router='1'
uci set nextdns.main.report_client_info='1'
uci set nextdns.main.log_queries='1'
uci commit nextdns
/etc/init.d/nextdns enable
/etc/init.d/nextdns start
/etc/init.d/dnsmasq restart
/etc/init.d/rpcd restart
echo "NextDNS設定完了"
echo "https://my.nextdns.io/${NEXTDNS_CONFIG_ID}/logs でログを確認してください"
※ログ取得まで新規登録から結構時間が掛かった
AdGuardHome
aios2用(新版)
aios2用(MAP-E / DS-LITE 対応)
| 機能比較 | OpenWrt | aios2 |
|---|---|---|
| 対応導入形態 | ||
| パッケージ | ○ | ○ |
| 公式バイナリ | × | ○ |
| 基本機能 | ||
| インストール方法 | コマンド実行 | メニュー選択 |
| 設定ファイル生成 | 手動 | 自動 |
| 認証情報設定 | Web初回起動時 | インストール時 |
| 日本環境最適化 | ||
| 日本向けDNSサーバー | × | ◯ |
| AdGuard言語フィルタ | × | ◯ |
| 設定機能 | ||
| リソースチェック | 手動 | 自動 |
| DHCPオプション | 手動 | 自動 |
| ファイアウォール | 手動 | 自動 |
| リムーブ | 手動 | 初期値復元 |
| パスワード変更 | ||
| htpasswd | × | ◯ |
| バックアップ | ||
| 既存設定バックアップ | × | /etc/config/*.bak |
| バグ対応 | ||
| ルーター自己DNS解決 | × (192.168.1.1) | ○ (0.0.0.0) |
設定ファイルなど
-
実行ファイル
adguardhome.sh -
設定ファイル
adguardhome.yaml -
スタンドアロン実行
mkdir -p /tmp && wget --no-check-certificate -O /tmp/adguardhome.sh "https://site-u.pages.dev/www/custom-scripts/adguardhome.sh" && chmod +x /tmp/adguardhome.sh && sh /tmp/adguardhome.sh
aios用(旧版)
aios用
opkg、apk対応
official版、OpenWrt版対応
yaml設定ファイル未対応
#!/bin/sh
TMP=/tmp/aios
mkdir -p "$TMP"
cat <<'EOF' > "$TMP"/standalone-blocker-adguardhome.sh
#!/bin/sh
# OpenWrt 19.07+ configuration
# Reference: https://openwrt.org/docs/guide-user/services/dns/adguard-home
# https://github.com/AdguardTeam/AdGuardHome
# This script file can be used standalone.
SCRIPT_VERSION="2025.07.21-00-00"
# set -ex
REQUIRED_MEM="50" # unit: MB
REQUIRED_FLASH="100" # unit: MB
LAN="${LAN:-br-lan}"
DNS_PORT="${DNS_PORT:-53}"
DNS_BACKUP_PORT="${DNS_BACKUP_PORT:-54}"
NET_ADDR=""
NET_ADDR6_LIST=""
SERVICE_NAME=""
INSTALL_MODE=""
ARCH=""
AGH=""
PACKAGE_MANAGER=""
FAMILY_TYPE=""
check_system() {
if /etc/AdGuardHome/AdGuardHome --version >/dev/null 2>&1 || /usr/bin/AdGuardHome --version >/dev/null 2>&1; then
printf "\033[1;33mAdGuard Home is already installed. Exiting.\033[0m\n"
remove_adguardhome
exit 0
fi
printf "\033[1;34mChecking system requirements\033[0m\n"
LAN="$(ubus call network.interface.lan status 2>/dev/null | jsonfilter -e '@.l3_device')"
if [ -z "$LAN" ]; then
printf "\033[1;31mLAN interface not found. Aborting.\033[0m\n"
exit 1
fi
if command -v opkg >/dev/null 2>&1; then
PACKAGE_MANAGER="opkg"
elif command -v apk >/dev/null 2>&1; then
PACKAGE_MANAGER="apk"
else
printf "\033[1;31mNo supported package manager (apk or opkg) found.\033[0m\n"
printf "\033[1;31mThis script is designed for OpenWrt systems only.\033[0m\n"
exit 1
fi
MEM_TOTAL_KB=$(awk '/^MemTotal:/ {print $2}' /proc/meminfo)
MEM_FREE_KB=$(awk '/^MemAvailable:/ {print $2}' /proc/meminfo)
BUFFERS_KB=$(awk '/^Buffers:/ {print $2}' /proc/meminfo)
CACHED_KB=$(awk '/^Cached:/ {print $2}' /proc/meminfo)
if [ -n "$MEM_FREE_KB" ]; then
MEM_FREE_MB=$((MEM_FREE_KB / 1024))
else
MEM_FREE_MB=$(((BUFFERS_KB + CACHED_KB) / 1024))
fi
MEM_TOTAL_MB=$((MEM_TOTAL_KB / 1024))
DF_OUT=$(df -k / | awk 'NR==2 {print $2, $4}')
FLASH_TOTAL_KB=$(printf '%s\n' "$DF_OUT" | awk '{print $1}')
FLASH_FREE_KB=$(printf '%s\n' "$DF_OUT" | awk '{print $2}')
FLASH_FREE_MB=$((FLASH_FREE_KB / 1024))
FLASH_TOTAL_MB=$((FLASH_TOTAL_KB / 1024))
if [ "$MEM_FREE_MB" -lt "$REQUIRED_MEM" ]; then
mem_col="1;31"
else
mem_col="1;32"
fi
if [ "$FLASH_FREE_MB" -lt "$REQUIRED_FLASH" ]; then
flash_col="1;31"
else
flash_col="1;32"
fi
printf "Memory: Free \033[%sm%s MB\033[0m / Total %s MB\n" \
"$mem_col" "$MEM_FREE_MB" "$MEM_TOTAL_MB"
printf "Flash: Free \033[%sm%s MB\033[0m / Total %s MB\n" \
"$flash_col" "$FLASH_FREE_MB" "$FLASH_TOTAL_MB"
printf "LAN interface: %s\n" "$LAN"
printf "Package manager: %s\n" "$PACKAGE_MANAGER"
if [ "$MEM_FREE_MB" -lt "$REQUIRED_MEM" ]; then
printf "\033[1;31mError: Insufficient memory. At least %sMB RAM is required.\033[0m\n" \
"$REQUIRED_MEM"
exit 1
fi
if [ "$FLASH_FREE_MB" -lt "$REQUIRED_FLASH" ]; then
printf "\033[1;31mError: Insufficient flash storage. At least %sMB free space is required.\033[0m\n" \
"$REQUIRED_FLASH"
exit 1
fi
}
install_prompt() {
printf "\033[1;34mSystem resources are sufficient for AdGuard Home installation. Proceeding with setup.\033[0m\n"
if [ -n "$1" ]; then
case "$1" in
official) INSTALL_MODE="official"; return ;;
openwrt) INSTALL_MODE="openwrt"; return ;;
remove) remove_adguardhome ;;
exit) exit 0 ;;
*) printf "\033[1;31mWarning: Unrecognized argument '$1'. Proceeding with interactive prompt.\033[0m\n" ;;
esac
fi
while true; do
printf "[1] Install OpenWrt package\n"
printf "[2] Install Official binary\n"
printf "[0] Exit\n"
printf "Please select (1, 2 or 0): "
read -r choice
case "$choice" in
1|openwrt) INSTALL_MODE="openwrt"; break ;;
2|official) INSTALL_MODE="official"; break ;;
0|exit)
printf "\033[1;33mInstallation cancelled.\033[0m\n"
exit 0
;;
*) printf "\033[1;31mInvalid choice '$choice'. Please enter 1, 2, or 0.\033[0m\n" ;;
esac
done
}
install_cacertificates() {
case "$PACKAGE_MANAGER" in
apk)
apk update >/dev/null 2>&1
apk add ca-certificates >/dev/null 2>&1
;;
opkg)
opkg update --verbosity=0 >/dev/null 2>&1
opkg install --verbosity=0 ca-bundle >/dev/null 2>&1
;;
esac
}
install_openwrt() {
printf "Installing adguardhome (OpenWrt package)\n"
case "$PACKAGE_MANAGER" in
apk)
PKG_VER=$(apk search adguardhome | grep "^adguardhome-" | sed 's/^adguardhome-//' | sed 's/-r[0-9]*$//')
if [ -n "$PKG_VER" ]; then
apk add adguardhome || {
printf "\033[1;31mNetwork error during apk add. Aborting.\033[0m\n"
exit 1
}
printf "\033[1;32madguardhome %s has been installed\033[0m\n" "$PKG_VER"
else
printf "\033[1;31mPackage 'adguardhome' not found in apk repository, falling back to official\033[0m\n"
install_official
fi
;;
opkg)
PKG_VER=$(opkg list | grep "^adguardhome " | awk '{print $3}')
if [ -n "$PKG_VER" ]; then
opkg install --verbosity=0 adguardhome || {
printf "\033[1;31mNetwork error during opkg install. Aborting.\033[0m\n"
exit 1
}
printf "\033[1;32madguardhome %s has been installed\033[0m\n" "$PKG_VER"
else
printf "\033[1;31mPackage 'adguardhome' not found in opkg repository, falling back to official\033[0m\n"
install_official
fi
;;
esac
SERVICE_NAME="adguardhome"
}
install_official() {
CA="--no-check-certificate"
URL="https://api.github.com/repos/AdguardTeam/AdGuardHome/releases/latest"
VER=$( { wget -q -O - "$URL" || wget -q "$CA" -O - "$URL"; } | jsonfilter -e '@.tag_name' )
[ -n "$VER" ] || { printf "\033[1;31mError: Failed to get AdGuardHome version from GitHub API.\033[0m\n"; exit 1; }
mkdir -p /etc/AdGuardHome
case "$(uname -m)" in
aarch64|arm64) ARCH=arm64 ;;
armv7l) ARCH=armv7 ;;
armv6l) ARCH=armv6 ;;
armv5l) ARCH=armv5 ;;
x86_64|amd64) ARCH=amd64 ;;
i386|i686) ARCH=386 ;;
mips) ARCH=mipsle ;;
mips64) ARCH=mips64le ;;
*) printf "Unsupported arch: %s\n" "$(uname -m)"; exit 1 ;;
esac
TAR="AdGuardHome_linux_${ARCH}.tar.gz"
URL2="https://github.com/AdguardTeam/AdGuardHome/releases/download/${VER}/${TAR}"
DEST="/etc/AdGuardHome/${TAR}"
printf "Downloading AdGuardHome (official binary)\n"
if ! { wget -q -O "$DEST" "$URL2" || wget -q "$CA" -O "$DEST" "$URL2"; }; then
printf '\033[1;31mDownload failed. Please check network connection.\033[0m\n'
exit 1
fi
printf "\033[1;32mAdGuardHome %s has been downloaded\033[0m\n" "$VER"
tar -C /etc/ -xzf "/etc/AdGuardHome/${TAR}"
rm "/etc/AdGuardHome/${TAR}"
chmod +x /etc/AdGuardHome/AdGuardHome
SERVICE_NAME="AdGuardHome"
/etc/AdGuardHome/AdGuardHome -s install >/dev/null 2>&1 || {
printf "\033[1;31mInitialization failed. Check AdGuardHome.yaml and port availability.\033[0m\n"
exit 1
}
chmod 700 /etc/"$SERVICE_NAME"
}
get_iface_addrs() {
local flag=0
if ip -4 -o addr show dev "$LAN" scope global | grep -q 'inet '; then
NET_ADDR=$(ip -4 -o addr show dev "$LAN" scope global | awk 'NR==1{sub(/\/.*/,"",$4); print $4}')
flag=$((flag | 1))
else
printf "\033[1;33mWarning: No IPv4 address on %s\033[0m\n" "$LAN"
fi
if ip -6 -o addr show dev "$LAN" scope global | grep -q 'inet6 '; then
NET_ADDR6_LIST=$(ip -6 -o addr show dev "$LAN" scope global | grep -v temporary | awk 'match($4,/^(2|fd|fc)/){sub(/\/.*/,"",$4); print $4;}')
flag=$((flag | 2))
else
printf "\033[1;33mWarning: No IPv6 address on %s\033[0m\n" "$LAN"
fi
case $flag in
3) FAMILY_TYPE=any ;;
1) FAMILY_TYPE=ipv4 ;;
2) FAMILY_TYPE=ipv6 ;;
*) FAMILY_TYPE="" ;;
esac
}
common_config() {
cp /etc/config/network /etc/config/network.adguard.bak
cp /etc/config/dhcp /etc/config/dhcp.adguard.bak
cp /etc/config/firewall /etc/config/firewall.adguard.bak
uci set dhcp.@dnsmasq[0].noresolv="1"
uci set dhcp.@dnsmasq[0].cachesize="0"
uci set dhcp.@dnsmasq[0].rebind_protection='0'
# uci set dhcp.@dnsmasq[0].rebind_protection='1' # keep enabled
# uci set dhcp.@dnsmasq[0].rebind_localhost='1' # protect localhost
# uci add_list dhcp.@dnsmasq[0].rebind_domain='lan' # allow internal domain
uci set dhcp.@dnsmasq[0].port="${DNS_BACKUP_PORT}"
uci set dhcp.@dnsmasq[0].domain="lan"
uci set dhcp.@dnsmasq[0].local="/lan/"
uci set dhcp.@dnsmasq[0].expandhosts="1"
uci -q del dhcp.@dnsmasq[0].server || true
uci add_list dhcp.@dnsmasq[0].server="127.0.0.1#${DNS_PORT}"
uci add_list dhcp.@dnsmasq[0].server="::1#${DNS_PORT}"
uci -q del dhcp.lan.dhcp_option || true
uci add_list dhcp.lan.dhcp_option="6,${NET_ADDR}"
uci -q del dhcp.lan.dhcp_option6 || true
if [ -n "$NET_ADDR6_LIST" ]; then
for ip in $NET_ADDR6_LIST; do
uci add_list dhcp.lan.dhcp_option6="option6:dns=[${ip}]"
done
fi
uci commit dhcp
/etc/init.d/dnsmasq restart || {
printf "\033[1;31mFailed to restart dnsmasq\033[0m\n"
printf "\033[1;31mTo remove AdGuard Home, run:\033[0m\n"
printf "\033[1;31msh %s/standalone-blocker-adguardhome.sh remove_adguardhome auto\033[0m\n" "$TMP"
exit 1
}
/etc/init.d/odhcpd restart || {
printf "\033[1;31mFailed to restart odhcpd\033[0m\n"
printf "\033[1;31mTo remove AdGuard Home, run:\033[0m\n"
printf "\033[1;31msh %s/standalone-blocker-adguardhome.sh remove_adguardhome auto\033[0m\n" "$TMP"
exit 1
}
/etc/init.d/"$SERVICE_NAME" enable
/etc/init.d/"$SERVICE_NAME" start
printf "Router IPv4: %s\n" "$NET_ADDR"
if [ -z "$NET_ADDR6_LIST" ]; then
printf "\033[1;33mRouter IPv6: none found\033[0m\n"
else
printf "Router IPv6: %s\n" "$NET_ADDR6_LIST"
fi
printf "\033[1;32mSystem configuration completed\033[0m\n"
}
common_config_firewall() {
rule_name="adguardhome_dns_${DNS_PORT}"
uci -q delete firewall."$rule_name" || true
if [ -z "$FAMILY_TYPE" ]; then
printf "\033[1;31mNo valid IP address family detected. Skipping firewall rule setup.\033[0m\n"
return
fi
uci set firewall."$rule_name"=redirect
uci set firewall."$rule_name".name="AdGuardHome DNS Redirect (${FAMILY_TYPE})"
uci set firewall."$rule_name".family="$FAMILY_TYPE"
uci set firewall."$rule_name".src="lan"
uci set firewall."$rule_name".dest="lan"
uci add_list firewall."$rule_name".proto="tcp"
uci add_list firewall."$rule_name".proto="udp"
uci set firewall."$rule_name".src_dport="$DNS_PORT"
uci set firewall."$rule_name".dest_port="$DNS_PORT"
uci set firewall."$rule_name".target="DNAT"
uci commit firewall
/etc/init.d/firewall restart || {
printf "\033[1;31mFailed to restart firewall\033[0m\n"
printf "\033[1;31mTo remove AdGuard Home, run:\033[0m\n"
printf "\033[1;31msh %s/standalone-blocker-adguardhome.sh remove_adguardhome auto\033[0m\n" "$TMP"
exit 1
}
printf "\033[1;32mFirewall configuration completed\033[0m\n"
}
remove_adguardhome() {
local auto_confirm="$1"
printf "\033[1;34mRemoving AdGuard Home\033[0m\n"
if /etc/AdGuardHome/AdGuardHome --version >/dev/null 2>&1; then
INSTALL_TYPE="official"; AGH="AdGuardHome"
elif /usr/bin/AdGuardHome --version >/dev/null 2>&1; then
INSTALL_TYPE="openwrt"; AGH="adguardhome"
else
printf "\033[1;31mAdGuard Home not found\033[0m\n"
return 1
fi
printf "Found AdGuard Home (%s version)\n" "$INSTALL_TYPE"
if [ "$auto_confirm" != "auto" ]; then
printf "Do you want to remove it? (y/N): "
read -r confirm
case "$confirm" in
[yY]*) ;;
*) printf "\033[1;33mCancelled\033[0m\n"; return 0 ;;
esac
else
printf "\033[1;33mAuto-removing due to installation error\033[0m\n"
fi
/etc/init.d/"${AGH}" stop 2>/dev/null || true
/etc/init.d/"${AGH}" disable 2>/dev/null || true
if [ "$INSTALL_TYPE" = "official" ]; then
"/etc/${AGH}/${AGH}" -s uninstall 2>/dev/null || true
else
if command -v apk >/dev/null 2>&1; then
apk del "$AGH" 2>/dev/null || true
else
opkg remove --verbosity=0 "$AGH" 2>/dev/null || true
fi
fi
if [ -d "/etc/${AGH}" ] || [ -f "/etc/adguardhome.yaml" ]; then
if [ "$auto_confirm" != "auto" ]; then
printf "Do you want to delete the AdGuard Home configuration file(s)? (y/N): "
read -r cfg
case "$cfg" in
[yY]*) rm -rf "/etc/${AGH}" /etc/adguardhome.yaml ;;
esac
else
rm -rf "/etc/${AGH}" /etc/adguardhome.yaml
fi
fi
for cfg in network dhcp firewall; do
bak="/etc/config/${cfg}.adguard.bak"
if [ -f "$bak" ]; then
printf "\033[1;34mRestoring %s configuration\033[0m\n" "$cfg"
cp "$bak" "/etc/config/${cfg}"
rm -f "$bak"
fi
done
uci commit network
uci commit dhcp
uci commit firewall
/etc/init.d/dnsmasq restart || { printf "\033[1;31mFailed to restart dnsmasq\033[0m\n"; exit 1; }
/etc/init.d/odhcpd restart || { printf "\033[1;31mFailed to restart odhcpd\033[0m\n"; exit 1; }
/etc/init.d/firewall restart || { printf "\033[1;31mFailed to restart firewall\033[0m\n"; exit 1; }
printf "\033[1;32mAdGuard Home has been removed successfully.\033[0m\n"
if [ "$auto_confirm" != "auto" ]; then
printf "\033[33mPress any key to reboot.\033[0m\n"
read -r -n1 -s
reboot
else
printf "\033[1;33mAuto-rebooting\033[0m\n"
reboot
fi
exit 0
}
get_access() {
local cfg port addr
if [ -f "/etc/AdGuardHome/AdGuardHome.yaml" ]; then
cfg="/etc/AdGuardHome/AdGuardHome.yaml"
elif [ -f "/etc/adguardhome.yaml" ]; then
cfg="/etc/adguardhome.yaml"
fi
if [ -n "$cfg" ]; then
addr=$(awk '
$1=="http:" {flag=1; next}
flag && /^[[:space:]]*address:/ {print $2; exit}
' "$cfg" 2>/dev/null)
port="${addr##*:}"
[ -z "$port" ] && port=
fi
[ -z "$port" ] && port=3000
if command -v qrencode >/dev/null 2>&1; then
printf "\033[1;32mWeb interface IPv4: http://${NET_ADDR}:${port}/\033[0m\n"
printf "http://${NET_ADDR}:${port}/\n" | qrencode -t UTF8 -v 3
if [ -n "$NET_ADDR6_LIST" ]; then
set -- $NET_ADDR6_LIST
printf "\033[1;32mWeb interface IPv6: http://[%s]:%s/\033[0m\n" "$1" "$port"
printf "http://[%s]:%s/\n" "$1" "$port" | qrencode -t UTF8 -v 3
fi
else
printf "\033[1;32mWeb interface IPv4: http://${NET_ADDR}:${port}/\033[0m\n"
if [ -n "$NET_ADDR6_LIST" ]; then
set -- $NET_ADDR6_LIST
printf "\033[1;32mWeb interface IPv6: http://[%s]:%s/\033[0m\n" "$1" "$port"
fi
fi
}
adguardhome_main() {
check_system
install_prompt "$@"
install_cacertificates
install_"$INSTALL_MODE"
get_iface_addrs
common_config
common_config_firewall
printf "\n\033[1;32mAdGuard Home installation and configuration completed successfully.\033[0m\n\n"
get_access
}
adguardhome_main "$@"
EOF
chmod +x "$TMP"/standalone-blocker-adguardhome.sh
sh "$TMP"/standalone-blocker-adguardhome.sh
- 管理画面ログイン
http://192.168.1.1:3000/
- DNS BIND MODE
# Set default bind mode: "loopback" or "gua"
DNS_BIND_MODE="${DNS_BIND_MODE:-loopback}"
common_config() {
# Option | DNS_BIND_MODE
#
# By setting DNS_BIND_MODE, you can switch dnsmasq’s upstream DNS between
# “loopback” mode (127.0.0.1#53 / ::1#53) and
# “gua” mode (router’s global IP#53).
#
# ・loopback (default)
# – dnsmasq → always resolves via local loopback to AdGuard Home
# – Ideal for environments where AdGuard Home is bound to localhost only
#
# ・gua
# – dnsmasq → resolves via the router’s global IPv4/IPv6 addresses
# – Useful for MAP-E/DS-Lite/WireGuard tunnels or
# direct DNS access from external clients
#
# Usage:
# export DNS_BIND_MODE="${DNS_BIND_MODE:-loopback}"
printf "\033[1;34mBacking up configuration files\033[0m\n"
cp /etc/config/network /etc/config/network.adguard.bak
cp /etc/config/dhcp /etc/config/dhcp.adguard.bak
cp /etc/config/firewall /etc/config/firewall.adguard.bak
[ "$INSTALL_MODE" = "official" ] && {
/etc/AdGuardHome/AdGuardHome -s install >/dev/null 2>&1 || {
printf "\033[1;31mInitialization failed. Check AdGuardHome.yaml and port availability.\033[0m\n"
exit 1
}
}
chmod 700 /etc/"$SERVICE_NAME"
/etc/init.d/"$SERVICE_NAME" enable
/etc/init.d/"$SERVICE_NAME" start
uci set dhcp.@dnsmasq[0].noresolv="1"
uci set dhcp.@dnsmasq[0].cachesize="0"
uci set dhcp.@dnsmasq[0].rebind_protection='0'
# uci set dhcp.@dnsmasq[0].rebind_protection='1' # keep enabled
# uci set dhcp.@dnsmasq[0].rebind_localhost='1' # protect localhost
# uci add_list dhcp.@dnsmasq[0].rebind_domain='lan' # allow internal domain
uci set dhcp.@dnsmasq[0].port="54"
uci set dhcp.@dnsmasq[0].domain="lan"
uci set dhcp.@dnsmasq[0].local="/lan/"
uci set dhcp.@dnsmasq[0].expandhosts="1"
uci -q del dhcp.@dnsmasq[0].server || true
if [ "$DNS_BIND_MODE" = "gua" ]; then
uci add_list dhcp.@dnsmasq[0].server="${NET_ADDR}#53"
for ip6 in $NET_ADDR6_LIST; do
uci add_list dhcp.@dnsmasq[0].server="${ip6}#53"
done
else
uci add_list dhcp.@dnsmasq[0].server='127.0.0.1#53'
uci add_list dhcp.@dnsmasq[0].server='::1#53'
fi
uci -q del dhcp.lan.dhcp_option || true
uci add_list dhcp.lan.dhcp_option="6,${NET_ADDR}"
uci set dhcp.@dnsmasq[0].dns="::"
uci -q del dhcp.lan.dhcp_option6 || true
if [ -n "$NET_ADDR6_LIST" ]; then
for ip6 in $NET_ADDR6_LIST; do
uci add_list dhcp.lan.dhcp_option6="option6:dns=[${ip6}]"
done
fi
uci commit dhcp
/etc/init.d/dnsmasq restart || {
printf "\033[1;31mFailed to restart dnsmasq\033[0m\n"
printf "\033[1;31mCritical error: Auto-removing AdGuard Home and rebooting in 10 seconds (Ctrl+C to cancel)\033[0m\n"
sleep 10
remove_adguardhome "auto"
reboot
exit 1
}
/etc/init.d/odhcpd restart || {
printf "\033[1;31mFailed to restart odhcpd\033[0m\n"
printf "\033[1;31mCritical error: Auto-removing AdGuard Home and rebooting in 10 seconds (Ctrl+C to cancel)\033[0m\n"
sleep 10
remove_adguardhome "auto"
reboot
exit 1
}
printf "\033[1;32mRouter IPv4: %s\033[0m\n" "$NET_ADDR"
if [ -z "$NET_ADDR6_LIST" ]; then
printf "\033[1;33mRouter IPv6: none found\033[0m\n"
else
printf "Router IPv6: %s\n" "$NET_ADDR6_LIST"
fi
}
config-software用(旧版)
config-software用
これ一つで以下の以下の機能を満たす(おススメ)
- 広告ブロック
- ペアレンタルコントロール
- DNS over HTTPS (DoH)
- DNS over TLS (DoT)
- 少なくとも 50MB の空き RAM
- 少なくとも 100MB のディスク/フラッシュ空き容量 (フラッシュ/ストレージ要件を参照)
- より高性能なルーター、つまりプロセッサ クロック速度が高いデュアルコアを推奨します
スクリプト
インストール
- adguard
- htpasswd
- libaprutil
- libapr
- libexpat
- libuuid1
アドイン
スクリプト実行
mkdir -p /etc/config-software; wget --no-check-certificate -O /etc/config-software/adguard-config.sh https://raw.githubusercontent.com/site-u2023/config-software/main/adguard-config.sh; sh /etc/config-software/adguard-config.sh
※強制終了:Ctrl+c
※LANインターフェイス名=lan
AdGuardHome自動構成の設定内容
利用可能サイズ確認
- フラッシュ
※参考利用フラッシュ: WXR-5950AX12 71.3M - 60.0M = 11.3M
df -Th | fgrep 'overlayfs:/overlay' | awk '{ print $5 }'
- メモリー
free | fgrep 'Mem:' | awk '{ print $4 }'
- インストール
- パッケージインストール
-
ネイティブインストール
Releases
※最新バージョン自動設定
#! /bin/sh
# Backup
cp /etc/config/network /etc/config/network.adguard.bak
cp /etc/config/dhcp /etc/config/dhcp.adguard.bak
cp /etc/config/firewall /etc/config/firewall.adguard.bak
# Check version & Install
OPENWRT_RELEAS=$(grep 'DISTRIB_RELEASE' /etc/openwrt_release | cut -d"'" -f2 | cut -c 1-2)
if [[ "${OPENWRT_RELEAS}" = "24" || "${OPENWRT_RELEAS}" = "23" || "${OPENWRT_RELEAS}" = "22" || "${OPENWRT_RELEAS}" = "21" ]]; then
opkg update
opkg install adguardhome
exit
elif [[ "${OPENWRT_RELEAS}" = "SN" ]]; then
apk update
apk add adguardhome
exit
fi
- インストール確認
AdGuardHome -s status
- デバイス設定
service adguardhome enable
service adguardhome start
NET_ADDR=$(/sbin/ip -o -4 addr list br-lan | awk 'NR==1{ split($4, ip_addr, "/"); print ip_addr[1] }')
NET_ADDR6=$(/sbin/ip -o -6 addr list br-lan scope global | awk 'NR==1{ split($4, ip_addr, "/"); print ip_addr[1] }')
echo "Router IPv4 : ""${NET_ADDR}"
echo "Router IPv6 : ""${NET_ADDR6}"
uci set dhcp.@dnsmasq[0].noresolv="0"
uci set dhcp.@dnsmasq[0].cachesize="1000"
uci set dhcp.@dnsmasq[0].rebind_protection='0'
uci set dhcp.@dnsmasq[0].port="54"
uci -q delete dhcp.@dnsmasq[0].server
uci add_list dhcp.@dnsmasq[0].server="${NET_ADDR}"
uci -q delete dhcp.lan.dhcp_option
uci -q delete dhcp.lan.dns
uci add_list dhcp.lan.dhcp_option='6,'"${NET_ADDR}"
uci add_list dhcp.lan.dhcp_option='3,'"${NET_ADDR}"
for OUTPUT in $(ip -o -6 addr list br-lan scope global | awk '{ split($4, ip_addr, "/"); print ip_addr[1] }')
do
echo "Adding $OUTPUT to IPV6 DNS"
uci add_list dhcp.lan.dns=$OUTPUT
done
uci commit dhcp
/etc/init.d/dnsmasq restart
# DNSインターセプト@IPTables(ファイアウォール3)
# IPV4
uci set firewall.adguardhome_dns_53='redirect'
uci set firewall.adguardhome_dns_53.src='lan'
uci set firewall.adguardhome_dns_53.proto='tcp udp'
uci set firewall.adguardhome_dns_53.src_dport='53'
uci set firewall.adguardhome_dns_53.target='DNAT'
uci set firewall.adguardhome_dns_53.name='Adguard Home'
uci set firewall.adguardhome_dns_53.dest='lan'
uci set firewall.adguardhome_dns_53.dest_port='53'
# IPV6
uci set firewall.adguardhome_dns_53.family="any"
uci commit firewall
/etc/init.d/firewall restart
#reboot
- 疎通確認
nslookup one.one.one.one localhost
-
- 192.168.1.1:3000
- QRコード : 192.168.1.1:3000

- QRコード : 192.168.1.1:8080

-
初期設定
- 管理用ウェブインターフェイス
-
すべてのインターフェイスポート8080※80以外の任意
-
- DNSサーバ
-
すべてのインターフェイスポート53
-
- ユーザー名
任意 - パスワード
任意 - パスワード(確認用)
任意
- 管理用ウェブインターフェイス
-
直接設定ファイルに記述する場合
# サービス停止
service adguardhome stop
# 設定ファイルに記述
vi /etc/adguardhome.yaml
# サービス開始
service adguardhome start
- DNS設定
- 上流DNSサーバ
既知のDNSプロバイダーの一覧
- 上流DNSサーバ
# LAN domain intercept
[/lan/]127.0.0.1:54
[//]127.0.0.1:54
# DNS-over-QUIC
quic://unfiltered.adguard-dns.com
# DNS-over-TLS
tls://1dot1dot1dot1.cloudflare-dns.com
tls://dns.google
# DNS-over-HTTPS(coercion HTTP/3)
h3://dns.cloudflare.com/dns-query
h3://dns.google/dns-query
h3://unfiltered.adguard-dns.com/dns-query
# DNS-over-HTTPS
# https://dns.cloudflare.com/dns-query
# https://dns.google/dns-query
# https://unfiltered.adguard-dns.com/dns-query
# NTP service
[/jp.pool.ntp.org/]1.1.1.1
[/pool.ntp.org/]1.0.0.1
[/jp.pool.ntp.org/]2606:4700:4700::1111
[/pool.ntp.org/]2606:4700:4700::1001
- ブートストラップDNSサーバ
1.1.1.1
1.0.0.1
2606:4700:4700::1111
2606:4700:4700::1001
- プライベートリバースDNSサーバー
192.168.1.1:54
-
プライベートリバースDNSリゾルバを使用
-
クライアントのIPアドレスの逆解決を有効にする
-
DNSブロックリスト
- ブロックリストに追加する
- カスタムリストを追加する
- 新しいブロックリスト
- カスタムリストを追加する
- ブロックリストに追加する
-
フィルターリスト
-
AdGuard Japanese filterの参考手順
AdGuard Japanese filter
https://raw.githubusercontent.com/AdguardTeam/FiltersRegistry/master/filters/filter_7_Japanese/filter.txt
- 280blockerの参考手順
280blocker
https://280blocker.net/files/280blocker_domain_ag_202307.txt
# `202307`は翌月の年月を入力
- 豆腐フィルタの参考手順
豆腐フィルタ
https://raw.githubusercontent.com/tofukko/filter/master/Adblock_Plus_list.txt
-
AdGuard DNS filter
-
AdAway Default Blocklist
-
AdGuard Japanese filter
-
280blocker
-
豆腐フィルタ
-
確認
- Toolz
- AdGuard
- Cloudflar
- DNS leak test
-
IP/DNS Detect
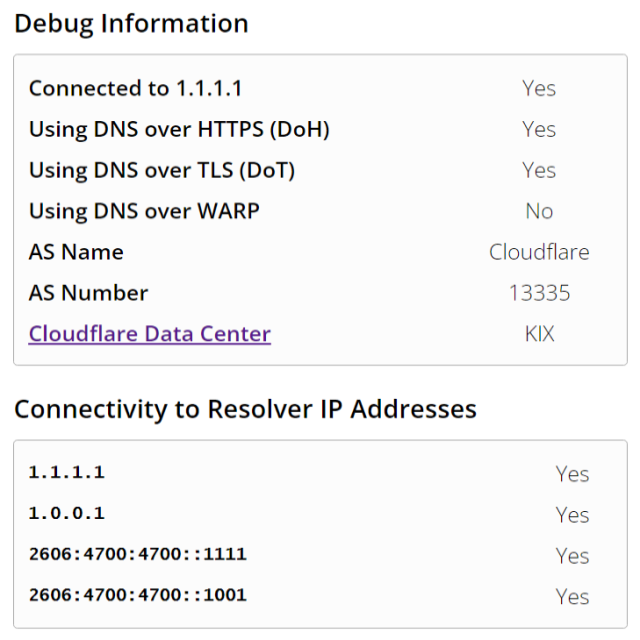
- Mac App Store
-
カスタムフィルタ
- フィルタ
- カスタム・フィルタリングルール
※yutubeの参考手順
- カスタム・フィルタリングルール
- フィルタ
# ブロック
||amazon.co.jp
# 解除
@@||youtube.com
ウェブパスワードをリセットする
アンインストール
service adguardhome stop
service adguardhome disable
# Check version & Remove
OPENWRT_RELEAS=$(grep 'DISTRIB_RELEASE' /etc/openwrt_release | cut -d"'" -f2 | cut -c 1-2)
if [[ "${OPENWRT_RELEAS}" = "24" || "${OPENWRT_RELEAS}" = "23" || "${OPENWRT_RELEAS}" = "22" || "${OPENWRT_RELEAS}" = "21" ]]; then
opkg remove adguardhome
elif [[ "${OPENWRT_RELEAS}" = "SN" ]]; then
apk del adguardhome
exit
fi
uci -q delete dhcp.@dnsmasq[0].noresolv
uci -q delete dhcp.@dnsmasq[0].cachesize
uci set dhcp.@dnsmasq[0].rebind_protection='1'
uci -q delete dhcp.@dnsmasq[0].server
uci -q delete dhcp.@dnsmasq[0].port
uci -q delete dhcp.lan.dhcp_option
uci -q delete dhcp.lan.dns
uci add_list dhcp.lan.dhcp_option="6,1.1.1.1,1.0.0.1"
uci add_list dhcp.lan.dhcp_option="6,8.8.8.8,8.8.4.4"
uci add_list dhcp.lan.dns="2606:4700:4700::1111"
uci add_list dhcp.lan.dns="2606:4700:4700::1001"
uci add_list dhcp.lan.dns="2001:4860:4860::8888"
uci add_list dhcp.lan.dns="2001:4860:4860::8844"
uci set network.wan.peerdns="0"
uci set network.wan6.peerdns="0"
uci -q delete network.wan.dns
uci -q delete network.wan6.dns
uci -q delete firewall.adguardhome_dns_53
uci commit
# reboot
AdBlock
AdBlock
ワンコピペ自動スクリプト
フィルター
スクリプト
アドイン
スクリプト実行
mkdir -p /etc/config-software; wget --no-check-certificate -O /etc/config-software/adblock-config.sh https://raw.githubusercontent.com/site-u2023/config-software/main/adblock-config.sh; sh /etc/config-software/adblock-config.sh
※強制終了:Ctrl+c
AdBlock自動構成の設定内容
設定
opkg update
opkg install adblock
opkg install luci-i18n-adblock-ja
opkg install tcpdump-mini
uci set adblock.global.adb_backupdir="/etc/adblock"
cp /etc/adblock/adblock.sources.gz /etc/adblock/adblock.sources.tofu.gz
gunzip /etc/adblock/adblock.sources.tofu.gz
sed -i -e '$d' /etc/adblock/adblock.sources.tofu
cat <<"EOF" >> /etc/adblock/adblock.sources.tofu
},
"tofu": {
"url": "https://raw.githubusercontent.com/tofukko/filter/master/Adblock_Plus_list.txt",
"rule": "BEGIN{FS=\"[|^]\"}/^\\|\\|([[:alnum:]_-]{1,63}\\.)+[[:alpha:]]+\\^(\\$third-party)?$/{print tolower($3)}",
"size": "XL",
"focus": "tofu",
"descurl": "https://github.com/tofukko/filter"
}
}
EOF
gzip /etc/adblock/adblock.sources.tofu
uci set adblock.global.adb_srcarc="/etc/adblock/adblock.sources.tofu.gz"
uci set adblock.global.adb_enabled="1"
uci set adblock.global.adb_backup="1"
uci set adblock.global.adb_backupdir="/etc/adblock"
uci set adblock.global.adb_backup_mode="1"
uci add_list adblock.global.adb_sources='tofu'
uci commit adblock
/etc/init.d/adblock enable
/etc/init.d/adblock start
確認
AdBlock-fast
AdBlock-fast自動構成の設定内容
- 設定
#! /bin/sh
opkg update
opkg install adblock-fast
opkg install luci-app-adblock-fast
opkg install luci-i18n-adblock-fast-ja
opkg install ip6tables-mod-nat
opkg install kmod-ipt-nat6
opkg --force-overwrite install gawk grep sed coreutils-sort
uci set adblock-fast.config.enabled=1
uci set adblock-fast.config.procd_trigger_wan6='1'
uci set adblock-fast.file_url=file_url
uci set adblock-fast.file_url.url='https://raw.githubusercontent.com/tofukko/filter/master/Adblock_Plus_list.txt'
uci set adblock-fast.file_url.action='block'
uci set adblock-fast.file_url.enabled='1'
uci commit adblock-fast
service adblock-fast enable
service adblock-fast start
確認
DNS over HTTPS (DoH)
設定
自動構成の設定内容
設定
opkg update
opkg install https-dns-proxy
opkg install luci-app-https-dns-proxy
opkg install luci-i18n-https-dns-proxy-ja
/etc/init.d/rpcd restart
#
while uci -q delete https-dns-proxy.@https-dns-proxy[0]; do :; done
uci set https-dns-proxy.dns="https-dns-proxy"
uci set https-dns-proxy.dns.bootstrap_dns="1.1.1.1,1.0.0.1"
uci set https-dns-proxy.dns.resolver_url="https://cloudflare-dns.com/dns-query"
uci set https-dns-proxy.dns.listen_addr="127.0.0.1"
uci set https-dns-proxy.dns.listen_port="5053"
uci commit https-dns-proxy
/etc/init.d/https-dns-proxy restart
確認
nslookup one.one.one.one localhost
DNS over TLS (DoT)
設定
自動構成の設定内容
設定
opkg update
opkg install stubby
/etc/init.d/dnsmasq stop
uci set dhcp.@dnsmasq[0].noresolv="1"
uci set dhcp.@dnsmasq[0].localuse="1"
uci -q delete dhcp.@dnsmasq[0].server
uci -q get stubby.global.listen_address \
| sed -e "s/\s/\n/g;s/@/#/g" \
| while read -r STUBBY_SERV
do uci add_list dhcp.@dnsmasq[0].server="${STUBBY_SERV}"
done
uci set network.wan.peerdns='0'
uci set network.wan.dns='127.0.0.1'
uci set network.wan6.peerdns='0'
uci set network.wan6.dns='0::1'
uci commit
/etc/init.d/dnsmasq start
/etc/init.d/network reload
# ブート失敗対策
sed -i "/exit 0/d" /etc/rc.local
echo "/etc/init.d/stubby restart" >> /etc/rc.local
echo "exit 0" >> /etc/rc.local
確認
nslookup one.one.one.one localhost
ペアレンタルコントロール
設定
インターネットアクセスの時間制限
マックアドレス@ファイアーウォール制御
参考
uci add firewall rule
uci set firewall.@rule[-1].name="Filter-Parental-Controls"
uci set firewall.@rule[-1].src="lan"
uci set firewall.@rule[-1].src_mac="00:11:22:33:44:55"
uci set firewall.@rule[-1].dest="wan"
uci set firewall.@rule[-1].start_time="21:30:00"
uci set firewall.@rule[-1].stop_time="07:00:00"
uci set firewall.@rule[-1].weekdays="Mon Tue Wed Thu Fri"
uci set firewall.@rule[-1].target="REJECT"
uci commit firewall
/etc/init.d/firewall restart
タイムコントロール
パーソナル OpenWrt OPKG サーバー
マックアドレス制御
sed -i 's/option check_signature/# option check_signature/g' /etc/opkg.conf
echo "src/gz custom_generic https://raw.githubusercontent.com/lrdrdn/my-opkg-repo/main/generic" >> /etc/opkg/customfeeds.conf
echo "src/gz custom_arch https://raw.githubusercontent.com/lrdrdn/my-opkg-repo/main/$(grep "OPENWRT_ARCH" /etc/os-release | awk -F '"' '{print $2}')" >> /etc/opkg/customfeeds.conf
opkg update
opkg install luci-app-timecontrol
/etc/init.d/rpcd reload
無線スケジュール
WiFi制御
opkg update
opkg install wifischedule
opkg install luci-app-wifischedule
opkg install luci-i18n-wifischedule-ja
CRON
WiFi(SSID別)制御
/etc/init.d/cron enable
# WiFi 5G OFF 00:00
echo "00 00 * * * uci set wireless.default_radio0.disabled=1; uci commit; wifi" >> /etc/crontabs/root
# WiFi 5G ON 08:00
echo "00 08 * * * uci set wireless.default_radio0.disabled=0; uci commit; wifi" >> /etc/crontabs/root
/etc/init.d/cron restart
フラッシュ&インストールシステム
あとがき
- AdGuard
自動化スクリプトに暗号化パスワードも入れ込めるんだけど、いかんせんアパッチ入れないとならない
とり諦め・・・ << 解決
容量自動判定はインストールサイズを根拠にしているが、インストール出来るから運用できるのとは違うかと思われ
まあログは取らなきゃいいだけだけど