はじめに
シスコは サポート 契約のあるパートナーや、ユーザーが利用可能な Support APIを公開しています。
Cisco Support APIs
Cisco Support APIは、受発注に関わるものや、サポートに関わるものなど多く存在しますが、今回は、シスコアカウントがあれば、手軽に使える Cisco PSIRT OpenVuln APIを使ってみます。
Cisco PSIRT OpenVuln とは
OpenVuln API は簡単に言うと、Cisco PSIRT(Product Security Incident Response Team) の情報、脆弱性情報を REST API を使って、様々なフォーマットで、効率的に取得できる API です。
これを使うと、REST APIで、特定のIOS version の脆弱性情報や、セキュリティアドバイザリの詳細などを取得することができます。
アカウントセットアップ
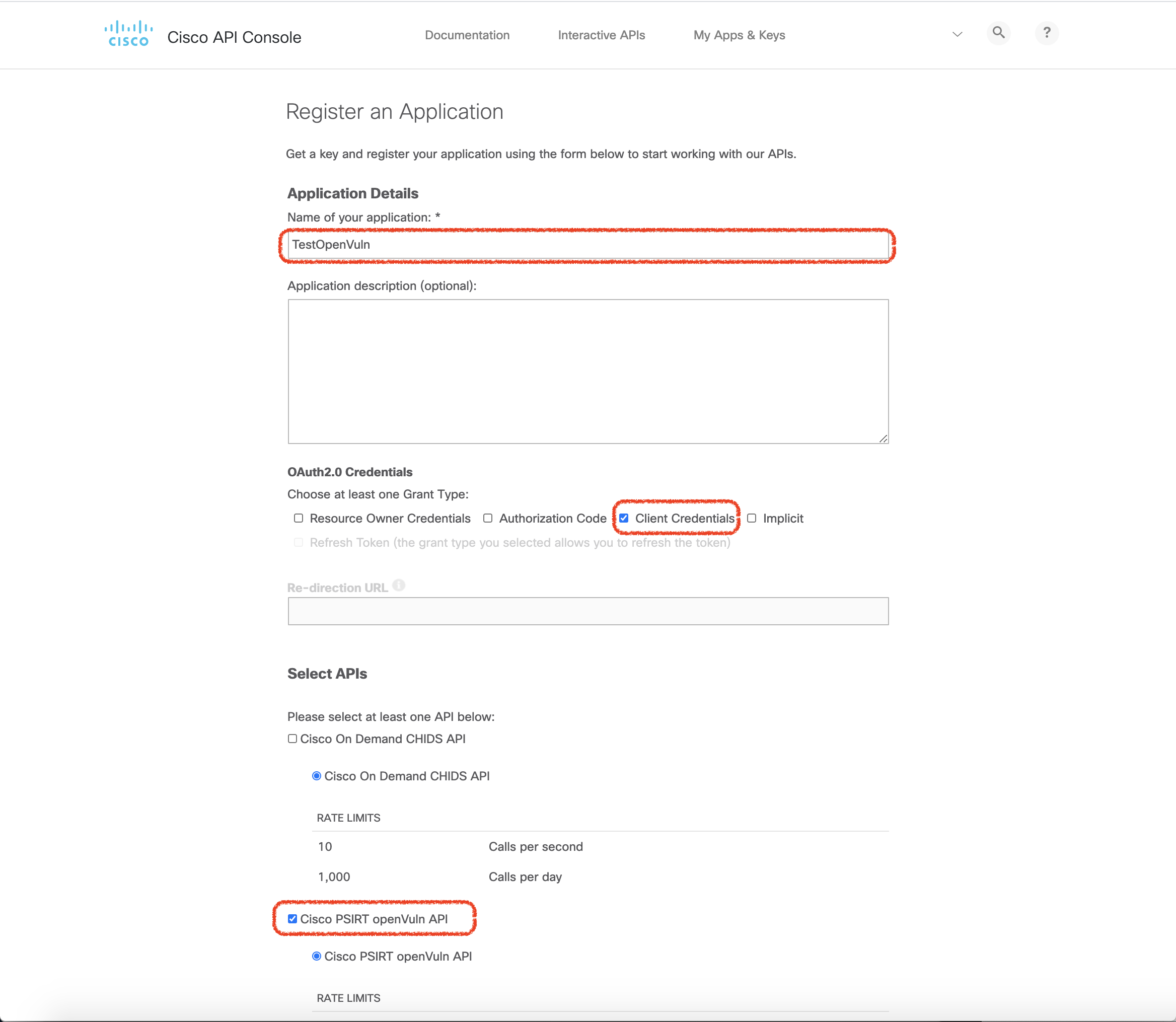
まず、Cisco Support API を利用する場合は、 https://apiconsole.cisco.com へアクセスし、APIを有効にする必要があります。
手順
- https://apiconsole.cisco.com へアクセスし Cisco.com アカウントでログイン
- My Apps & Keys タブをクリック
- Register an Application で、アプリケーション名など必要事項を記入(赤枠の部分を埋めます)し、登録
そうすることで、API 利用に必要な KEY と SECRET が発行されます
Python モジュール openVulnQuery を使う
アカウントの設定が完了すれば、 REST API で情報取得ができます。
今回は、コマンドラインツールとしても使える、openVulnQuery が便利なので、これを使ってみます。
GitHub - CiscoPSIRT/openVulnQuery: A Python-based client for the Cisco openVuln API
インストール & セットアップ
Pip でインストールをするだけです。
pip install openVulnQuery
私の環境では、下記の通り PATH を通ってないよとエラーが出たのでコマンドラインツールとして利用するために、 .bash_profile に PATHを追加
WARNING: The script chardetect is installed in '/Users/USER_ID/Library/Python/3.8/bin' which is not on PATH.
:
export PATH="/Users/USER_ID/Library/Python/3.8/bin:$PATH"
:
openVulnQuery を使うためには、環境変数で、KEY と Secret を渡すか、もしくは、json 形式のファイルに KEY と Secret を記載して、オプションで渡すことで APIにアクセスをします。
- 環境変数で渡す場合
$export CLIENT_ID="xxxxxxx"
$export CLIENT_SECRET="yyyyyyy"
- JSON形式のファイルで渡す場合
下記の形式の credential 用のファイルを、一つ作成します。
{
"CLIENT_ID": "xxxxxxx",
"CLIENT_SECRET": "yyyyyyyy"
}
openVulnQuery の使い方
openVlunQuery に、credential file を --config で指定して、実行すれば、データが取得できます。
$ openVulnQuery -h
usage: openVulnQuery [-h]
(--all | --advisory <advisory-id> | --cve <CVE-id> | --latest number | --severity [critical, high, medium, low] | --year year | --product product_name | --ios_xe iosxe_version | --ios ios_version | --nxos nxos_version | --aci aci_version)
[--csv filepath | --json filepath] [--first_published YYYY-MM-DD:YYYY-MM-DD | --last_published YYYY-MM-DD:YYYY-MM-DD] [-c] [-f [...]] [--user-agent string]
[--config filepath]
詳細
Cisco OpenVuln API Command Line Interface
optional arguments:
-h, --help show this help message and exit
--all Retrieves all advisiories
--advisory <advisory-id>
Retrieve advisories by advisory id
--cve <CVE-id> Retrieve advisories by cve id
--latest number Retrieves latest (number) advisories
--severity [critical, high, medium, low]
Retrieve advisories by severity (low, medium, high, critical)
--year year Retrieve advisories by year
--product product_name
Retrieve advisories by product names
--ios_xe iosxe_version
Retrieve advisories affecting user inputted ios_xe version.Only one version at a time is allowed.
--ios ios_version Retrieve advisories affecting user inputted ios version.Only one version at a time is allowed.
--nxos nxos_version Retrieve advisories affecting user inputted NX-OS (in standalone mode) version.Only one version at a time is allowed.
--aci aci_version Retrieve advisories affecting user inputted NX-OS (in ACI mode) version.Only one version at a time is allowed.
--csv filepath Output to CSV with file path
--json filepath Output to JSON with file path
--first_published YYYY-MM-DD:YYYY-MM-DD
Filter advisories based on first_published date YYYY-MM-DD:YYYY-MM-DD USAGE: followed by severity or all
--last_published YYYY-MM-DD:YYYY-MM-DD, --last_updated YYYY-MM-DD:YYYY-MM-DD
Filter advisories based on last_published date YYYY-MM-DD:YYYY-MM-DD USAGE: followed by severity or all
-c, --count Count of any field or fields
-f [ ...], --fields [ ...]
Separate fields by spaces to return advisory information. Allowed values are: advisory_id, advisory_title, bug_ids, cves, cvrfUrl, cvss_base_score, cwe,
first_fixed, first_published, ios_release, ips_signatures, last_updated, product_names, publication_url, sir, summary
--user-agent string Announced User-Agent hedar value (towards service)
--config filepath Path to JSON file with config (otherwise fallback to environment variables CLIENT_ID and CLIENT_SECRET, or config.py variables, or fail)
例1) IOS-XE version 16.2.2 に該当するセキュリティアドバイザリIDとタイトルを一覧表示
openVulnQuery --ios_xe 16.2.2 -f advisory_id advisory_title
出力結果
[
{
"advisory_id": "cisco-sa-info-disclosure-V4BmJBNF",
"advisory_title": "Cisco IOS and IOS XE Software Information Disclosure Vulnerability"
},
{
"advisory_id": "cisco-sa-iosxe-isdn-q931-dos-67eUZBTf",
"advisory_title": "Cisco IOS and IOS XE Software ISDN Q.931 Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-rommon-secboot-7JgVLVYC",
"advisory_title": "Cisco IOS XE ROM Monitor Software Vulnerability"
},
{
"advisory_id": "cisco-sa-ios-lua-rce-7VeJX4f",
"advisory_title": "Cisco IOS XE Software Arbitrary Code Execution Vulnerability"
},
{
"advisory_id": "cisco-sa-esp20-arp-dos-GvHVggqJ",
"advisory_title": "Cisco IOS XE Software for Cisco ASR 1000 Series 20-Gbps Embedded Services Processor IP ARP Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-iosxe-rsp3-rce-jVHg8Z7c",
"advisory_title": "Cisco IOS XE Software for Cisco ASR 900 Series Route Switch Processor 3 Arbitrary Code Execution Vulnerabilities"
},
{
"advisory_id": "cisco-sa-ios-webui-priv-esc-K8zvEWM",
"advisory_title": "Cisco IOS XE Software Privilege Escalation Vulnerabilities"
},
{
"advisory_id": "cisco-sa-ios-xe-webui-multi-vfTkk7yr",
"advisory_title": "Cisco IOS XE Software Web Management Framework Vulnerabilities"
},
{
"advisory_id": "cisco-sa-webui-auth-bypass-6j2BYUc7",
"advisory_title": "Cisco IOS XE Software Web UI Authorization Bypass Vulnerability"
},
{
"advisory_id": "cisco-sa-zbfw-94ckG4G",
"advisory_title": "Cisco IOS XE Software Zone-Based Firewall Denial of Service Vulnerabilities"
},
{
"advisory_id": "cisco-sa-telnetd-EFJrEzPx",
"advisory_title": "Telnet Vulnerability Affecting Cisco Products: June 2020"
},
{
"advisory_id": "cisco-sa-tcl-dos-MAZQUnMF",
"advisory_title": "Cisco IOS and IOS XE Software Tcl Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-ikev2-9p23Jj2a",
"advisory_title": "Cisco IOS and IOS XE Software Internet Key Exchange Version 2 Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-ssh-dos-Un22sd2A",
"advisory_title": "Cisco IOS and IOS XE Software Secure Shell Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-sip-Cv28sQw2",
"advisory_title": "Cisco IOS and IOS XE Software Session Initiation Protocol Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-tcl-ace-C9KuVKmm",
"advisory_title": "Cisco IOS and IOS XE Software Tcl Arbitrary Code Execution Vulnerability"
},
{
"advisory_id": "cisco-sa-iosxe-ewlc-dos-TkuPVmZN",
"advisory_title": "Cisco IOS XE Software Catalyst 9800 Series Wireless Controllers Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-iosxe-digsig-bypass-FYQ3bmVq",
"advisory_title": "Cisco IOS XE Software Digital Signature Verification Bypass Vulnerability"
},
{
"advisory_id": "cisco-sa-priv-esc1-OKMKFRhV",
"advisory_title": "Cisco IOS XE Software Privilege Escalation Vulnerability"
},
{
"advisory_id": "cisco-sa-priv-esc3-GMgnGCHx",
"advisory_title": "Cisco IOS XE Software Privilege Escalation Vulnerability"
},
{
"advisory_id": "cisco-sa-web-cmdinj2-fOnjk2LD",
"advisory_title": "Cisco IOS XE Software Web UI Command Injection Vulnerability"
},
{
"advisory_id": "cisco-sa-webui-PZgQxjfG",
"advisory_title": "Cisco IOS XE Software Web UI Privilege Escalation Vulnerability"
},
{
"advisory_id": "cisco-sa-sxp-68TEVzR",
"advisory_title": "Cisco IOS, IOS XE, and NX-OS Software Security Group Tag Exchange Protocol Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-ios-nxos-onepk-rce-6Hhyt4dC",
"advisory_title": "Cisco IOS, IOS XE, IOS XR, and NX-OS Software One Platform Kit Remote Code Execution Vulnerability"
},
{
"advisory_id": "cisco-sa-20190828-iosxe-rest-auth-bypass",
"advisory_title": "Cisco REST API Container for IOS XE Software Authentication Bypass Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-sip-dos",
"advisory_title": "Cisco IOS and IOS XE Software Session Initiation Protocol Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-tsec",
"advisory_title": "Cisco IOS and IOS XE Software Change of Authorization Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-http-client",
"advisory_title": "Cisco IOS and IOS XE Software HTTP Client Information Disclosure Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-identd-dos",
"advisory_title": "Cisco IOS and IOS XE Software IP Ident Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-sbxss",
"advisory_title": "Cisco IOS and IOS XE Software Stored Banner Cross-Site Scripting Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-iosxe-codeexec",
"advisory_title": "Cisco IOS XE Software Arbitrary Code Execution Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-awr",
"advisory_title": "Cisco IOS XE Software ASIC Register Write Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-iosxe-fsdos",
"advisory_title": "Cisco IOS XE Software Filesystem Exhaustion Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-sip-alg",
"advisory_title": "Cisco IOS XE Software NAT Session Initiation Protocol Application Layer Gateway Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-utd",
"advisory_title": "Cisco IOS XE Software Unified Threat Defense Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20190925-vman",
"advisory_title": "Cisco NX-OS and IOS XE Software Virtual Service Image Signature Bypass Vulnerability"
},
{
"advisory_id": "cisco-sa-20160525-ipv6",
"advisory_title": "Cisco Products IPv6 Neighbor Discovery Crafted Packet Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20190612-iosxe-csrf",
"advisory_title": "Cisco IOS XE Software Web UI Cross-Site Request Forgery Vulnerability"
},
{
"advisory_id": "cisco-sa-20190513-webui",
"advisory_title": "Cisco IOS XE Software Web UI Command Injection Vulnerability"
},
{
"advisory_id": "cisco-sa-20170629-snmp",
"advisory_title": "SNMP Remote Code Execution Vulnerabilities in Cisco IOS and IOS XE Software"
},
{
"advisory_id": "cisco-sa-20190327-ios-infoleak",
"advisory_title": "Cisco IOS and IOS XE Software Hot Standby Router Protocol Information Leak Vulnerability"
},
{
"advisory_id": "cisco-sa-20190327-ipsla-dos",
"advisory_title": "Cisco IOS and IOS XE Software IP Service Level Agreement Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20190327-isdn",
"advisory_title": "Cisco IOS and IOS XE Software ISDN Interface Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20190327-pnp-cert",
"advisory_title": "Cisco IOS and IOS XE Software Network Plug-and-Play Agent Certificate Validation Vulnerability"
},
{
"advisory_id": "cisco-sa-20190327-nbar",
"advisory_title": "Cisco IOS and IOS XE Software Network-Based Application Recognition Denial of Service Vulnerabilities"
},
{
"advisory_id": "cisco-sa-20190327-call-home-cert",
"advisory_title": "Cisco IOS and IOS XE Software Smart Call Home Certificate Validation Vulnerability"
},
{
"advisory_id": "cisco-sa-20190327-afu",
"advisory_title": "Cisco IOS XE Software Arbitrary File Upload Vulnerability"
},
{
"advisory_id": "cisco-sa-20190327-xecmd",
"advisory_title": "Cisco IOS XE Software Command Injection Vulnerability"
},
{
"advisory_id": "cisco-sa-20190327-iosxe-cmdinj",
"advisory_title": "Cisco IOS XE Software Command Injection Vulnerability"
},
{
"advisory_id": "cisco-sa-20190327-mgmtacl",
"advisory_title": "Cisco IOS XE Software Gigabit Ethernet Management Interface Access Control List Bypass Vulnerability"
},
{
"advisory_id": "cisco-sa-20190109-tcp",
"advisory_title": "Cisco IOS and IOS XE Software TCP Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-ipsec",
"advisory_title": "Cisco IOS XE Software and Cisco ASA 5500-X Series Adaptive Security Appliance IPsec Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-cdp-dos",
"advisory_title": "Cisco IOS and IOS XE Software Cisco Discovery Protocol Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-ipv6hbh",
"advisory_title": "Cisco IOS and IOS XE Software IPv6 Hop-by-Hop Options Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-ospfv3-dos",
"advisory_title": "Cisco IOS and IOS XE Software OSPFv3 Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-pnp-memleak",
"advisory_title": "Cisco IOS and IOS XE Software Plug and Play Agent Memory Leak Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-sm1t3e3",
"advisory_title": "Cisco IOS and IOS XE Software SM-1T3/E3 Service Module Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-vtp",
"advisory_title": "Cisco IOS and IOS XE Software VLAN Trunking Protocol Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-iosxe-cmdinj",
"advisory_title": "Cisco IOS XE Software Command Injection Vulnerabilities"
},
{
"advisory_id": "cisco-sa-20180926-digsig",
"advisory_title": "Cisco IOS XE Software Digital Signature Verification Bypass Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-webdos",
"advisory_title": "Cisco IOS XE Software HTTP Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-macsec",
"advisory_title": "Cisco IOS XE Software MACsec MKA Using EAP-TLS Authentication Bypass Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-sip-alg",
"advisory_title": "Cisco IOS XE Software NAT Session Initiation Protocol Application Layer Gateway Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-shell-access",
"advisory_title": "Cisco IOS XE Software Shell Access Authentication Bypass Vulnerability"
},
{
"advisory_id": "cisco-sa-20180926-webuidos",
"advisory_title": "Cisco IOS XE Software Web UI Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-smi",
"advisory_title": "Cisco IOS and IOS XE Software Smart Install Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-smi2",
"advisory_title": "Cisco IOS and IOS XE Software Smart Install Remote Code Execution Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-lldp",
"advisory_title": "Cisco IOS, IOS XE, and IOS XR Software Link Layer Discovery Protocol Buffer Overflow Vulnerabilities"
},
{
"advisory_id": "cisco-sa-20180328-qos",
"advisory_title": "Cisco IOS and IOS XE Software Quality of Service Remote Code Execution Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-dhcpr1",
"advisory_title": "Cisco IOS and IOS XE Software DHCP Version 4 Relay Heap Overflow Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-dhcpr2",
"advisory_title": "Cisco IOS and IOS XE Software DHCP Version 4 Relay Reply Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-ike",
"advisory_title": "Cisco IOS and IOS XE Software Internet Key Exchange Memory Leak Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-ipv4",
"advisory_title": "Cisco IOS XE Software for Cisco Catalyst Switches IPv4 Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-igmp",
"advisory_title": "Cisco IOS XE Software Internet Group Management Protocol Memory Leak Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-snmp-dos",
"advisory_title": "Cisco IOS XE Software Simple Network Management Protocol Double-Free Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20180328-privesc1",
"advisory_title": "Cisco IOS XE Software User EXEC Mode Root Shell Access Vulnerabilities"
},
{
"advisory_id": "cisco-sa-20180328-xepriv",
"advisory_title": "Cisco IOS XE Software Web UI Remote Access Privilege Escalation Vulnerability"
},
{
"advisory_id": "cisco-sa-20170419-energywise",
"advisory_title": "Cisco IOS and IOS XE Software EnergyWise Denial of Service Vulnerabilities"
},
{
"advisory_id": "cisco-sa-20170726-anicrl",
"advisory_title": "Cisco IOS XE Software Autonomic Networking Infrastructure Certificate Revocation Vulnerability"
},
{
"advisory_id": "cisco-sa-20171103-bgp",
"advisory_title": "Cisco IOS XE Software Ethernet Virtual Private Network Border Gateway Protocol Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20170927-ike",
"advisory_title": "Cisco IOS and IOS XE Software Internet Key Exchange Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20170927-pnp",
"advisory_title": "Cisco IOS and IOS XE Software Plug-and-Play PKI API Certificate Validation Vulnerability"
},
{
"advisory_id": "cisco-sa-20170727-ospf",
"advisory_title": "Multiple Cisco Products OSPF LSA Manipulation Vulnerability"
},
{
"advisory_id": "cisco-sa-20170726-aniacp",
"advisory_title": "Cisco IOS and IOS XE Software Autonomic Control Plane Channel Information Disclosure Vulnerability"
},
{
"advisory_id": "cisco-sa-20170726-anidos",
"advisory_title": "Cisco IOS and IOS XE Software Autonomic Networking Infrastructure Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20170320-ani",
"advisory_title": "Cisco IOS and IOS XE Software Autonomic Networking Infrastructure Registrar Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20170320-aniipv6",
"advisory_title": "Cisco IOS and IOS XE Software IPv6 Denial of Service Vulnerability"
},
{
"advisory_id": "cisco-sa-20161115-iosxe",
"advisory_title": "Cisco IOS XE Software Directory Traversal Vulnerability"
},
{
"advisory_id": "cisco-sa-20160916-ikev1",
"advisory_title": "IKEv1 Information Disclosure Vulnerability in Multiple Cisco Products"
}
]
例2) CVE ID "CVE-2010-3043" で セキュリティアドバイザリの内容を確認
openVulnQuery --cve CVE-2010-3043
出力結果
[
{
"advisory_id": "cisco-sa-20110201-webex",
"advisory_title": "Multiple Cisco WebEx Player Vulnerabilities",
"bug_ids": [
"NA"
],
"cves": [
"CVE-2010-3041",
"CVE-2010-3042",
"CVE-2010-3043",
"CVE-2010-3044",
"CVE-2010-3269"
],
"cvrfUrl": "https://tools.cisco.com/security/center/contentxml/CiscoSecurityAdvisory/cisco-sa-20110201-webex/cvrf/cisco-sa-20110201-webex_cvrf.xml",
"cvss_base_score": "9.3",
"cwe": [
"CWE-94"
],
"first_published": "2011-02-01T16:00:00",
"ips_signatures": [
{
"legacy_ips_id": "cisco-sa-20110201-webex",
"legacy_ips_url": "https://tools.cisco.com/security/center/viewIpsSignature.x?signatureId=36910&signatureSubId=0&softwareVersion=6.0&releaseVersion=S682",
"release_version": "S682",
"software_version": "6.0"
}
],
"last_updated": "2011-02-01T16:00:00",
"product_names": [
"NA"
],
"publication_url": "http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20110201-webex",
"sir": "Critical",
"summary": "<p>Multiple buffer overflow vulnerabilities exist in the Cisco WebEx\n\t Recording Format (WRF) and Advanced Recording Format (ARF) Players. In some\n\t cases, exploitation of the vulnerabilities could allow a remote attacker to\n\t execute arbitrary code on the system of a targeted user.</p> \n <p> </p> \n <p> The Cisco WebEx Players are applications that are used to\n\t play back WebEx meeting recordings that have been recorded on the computer of\n\t an on-line meeting attendee. The players can be automatically installed when\n\t the user accesses a recording file that is hosted on a WebEx server. The player\n\t can also be manually installed for offline playback after downloading the\n\t application from <a target=\"_blank\" href=\"http://www.webex.com\">www.webex.com</a>\n<img alt=\"leavingcisco.com\" height=\"18\" width=\"18\" src=\"http://www.cisco.com/images/exit.gif\" />.</p> \n <p> </p> \n <p> If the WebEx recording player was automatically installed,\n\t it will be automatically upgraded to the latest, non-vulnerable version when\n\t users access a recording file that is hosted on a WebEx server. If the WebEx\n\t recording player was manually installed, users will need to manually install a\n\t new version of the player after downloading the latest version from\n\t <a target=\"_blank\" href=\"http://www.webex.com\">www.webex.com</a>\n<img alt=\"leavingcisco.com\" height=\"18\" width=\"18\" src=\"http://www.cisco.com/images/exit.gif\" />.</p> \n <p> </p> \n <p> Cisco has released software updates that address these vulnerabilities.</p> \n <p>This advisory is posted at\n\t <a style=\"WORD-BREAK:BREAK-ALL;\" href=\"http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20110201-webex\">http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20110201-webex</a>.\n\t </p> \n \n\n"
}
]
例3) 2020年にリリースされた Security Impact Rating (sir) が Critical な PSIRT の数を調べる
openVulnQuery --year 2020 -f sir | grep -c "Critical"
出力結果
25
まとめ
このような形で 必要な PSIRT の情報を入手することができます。
運用中の多くのネットワーク機器の脆弱性情報を API を使うことで、まとめて取得できるため、活用いただけるシーンは多いのではないかと思います。今回は、コマンドラインでの例を中心に記載しましたが、Python ライブラリとしてプログラムの中に組み込むことで、より効率的な情報収集や、その他アプリケーションとの連携が可能です