Juniper vSRX はセキュア インターネット ゲートウェイ製品です。
ネットワーク管理者は、高度なルーティング機能を備えた業界トップクラスの性能を誇るvSRX 仮想ファイアウォールを使用して、脅威に先んじ、ワークロードを保護しながら、高度な接続と IPsec および VPN 終端サービスを提供できます。
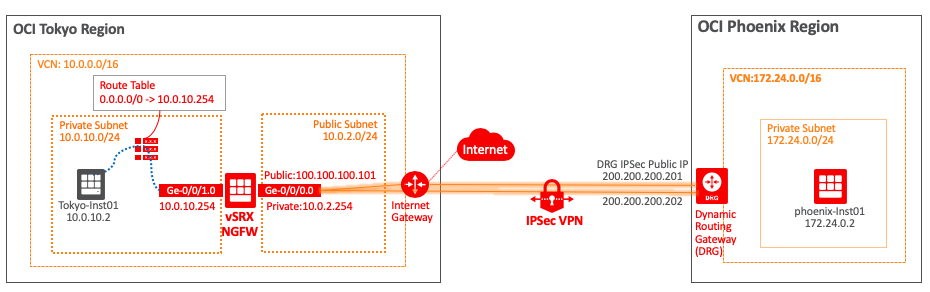
ということで、問い合わせも多いJuniper SRX と同等のIPSec接続設定をvSRX を用いてOracle Cloud Infrastructure(OCI)とのIPSec接続の設定してみてみます。
vSRXの導入は次の記事を参考とし、本手順はIPSec接続から行います。
Juniper vSRX Virtual FirewallをOracle Cloudにインストールしてみてみた
■OCI IPSec設定
●Customer-Premises Equipment作成
OCIの[Networking] > [ICustomer-Premises Equipment] 画面から[Create Customer-Premises Equipmentn]をクリックし以下内容を設定
・NAME:適当な名前を設定
・DRG:IPsec接続させる作成済みのDRGを設定
・STATIC ROUTE CIDER:対向側(FortiGate)のCIDERを設定 *後から追加変更削除可能です
・CPE IKE IDENTIFIER : FortiGateのWAN側Private IPを設定
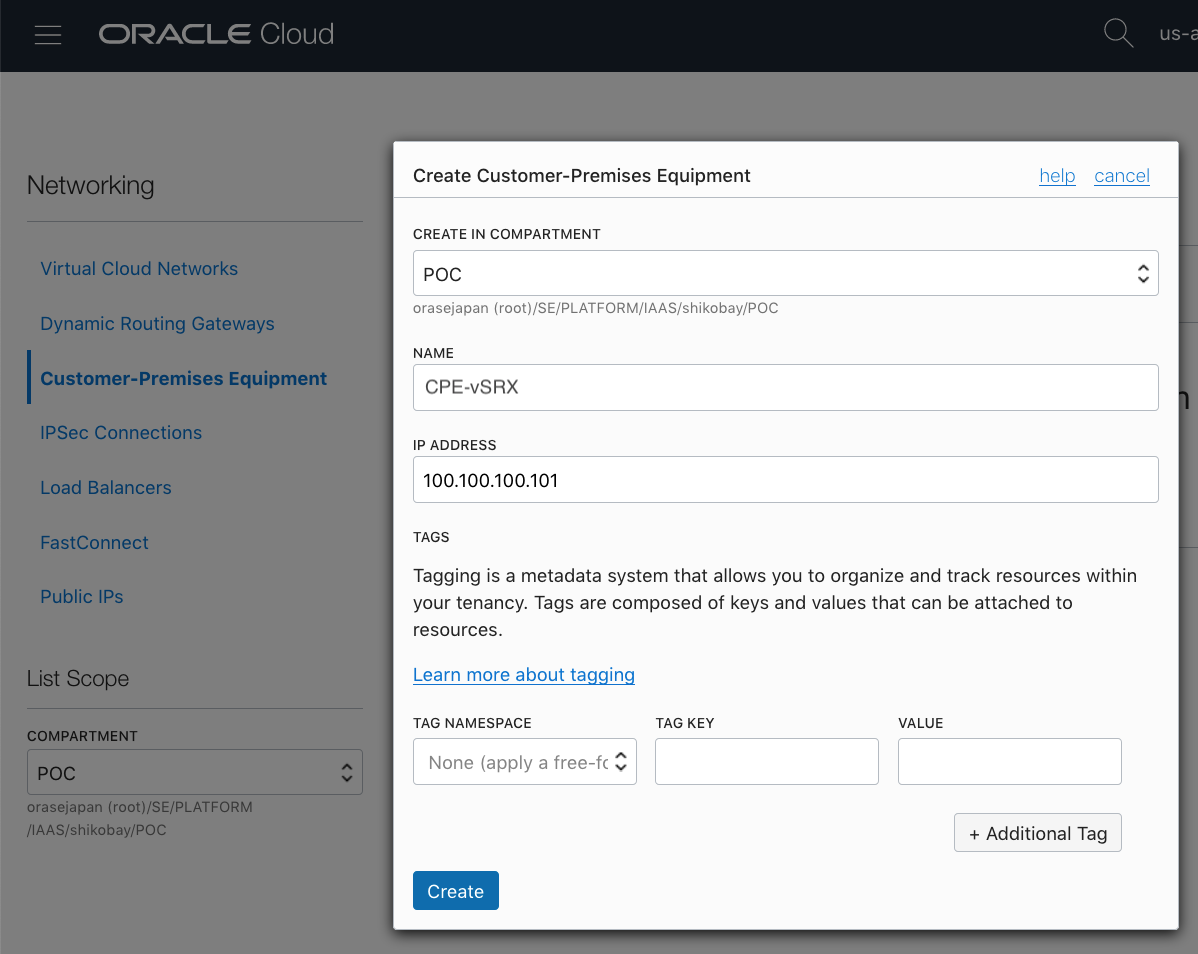 [Create Premises Equipment]をクリックして作成
[Create Premises Equipment]をクリックして作成
●IPSec Connection作成
①OCIの[Networking] > [IPsec Connetion] 画面から[Create IPsec Connection]をクリックし以下内容を設定
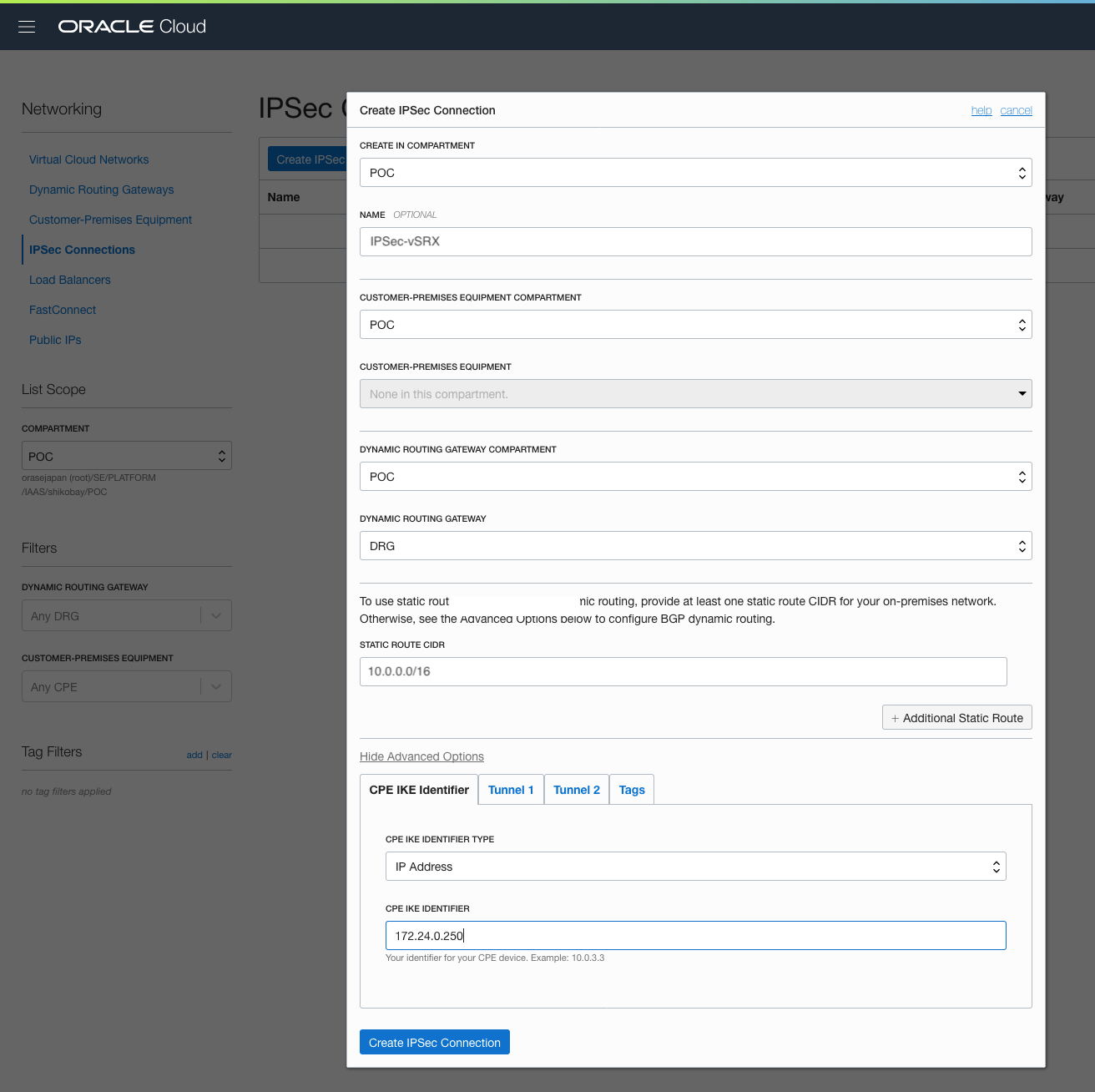
[Create IPsec Connection]をクリックして作成
②作成したIPsec ConnetionのVPN IP Addressを確認
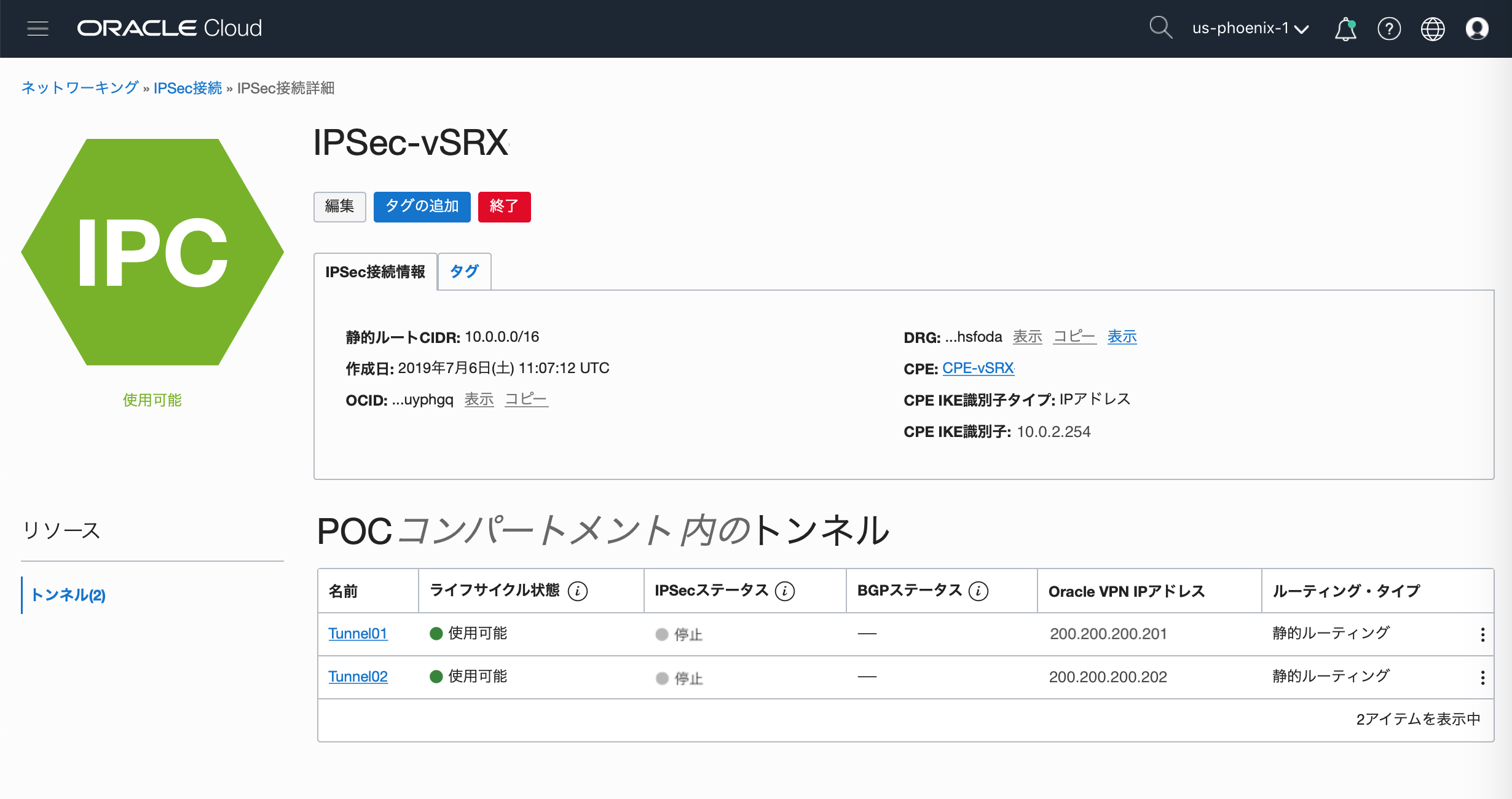
③作成したIPsec ConnetionのShared Secretを確認
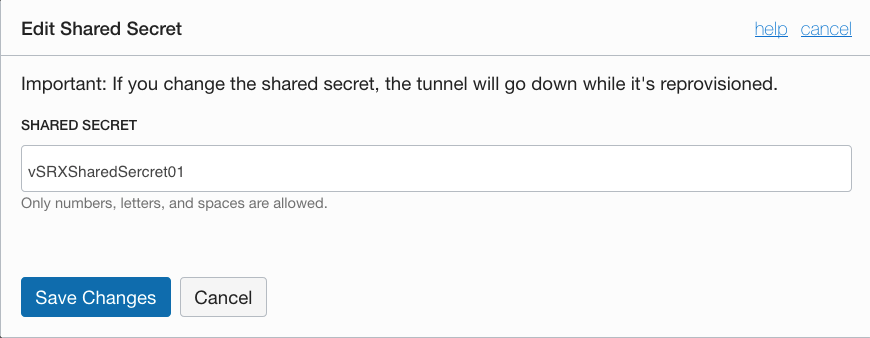
・Tunnel1(200.200.200.201)のShared Secret
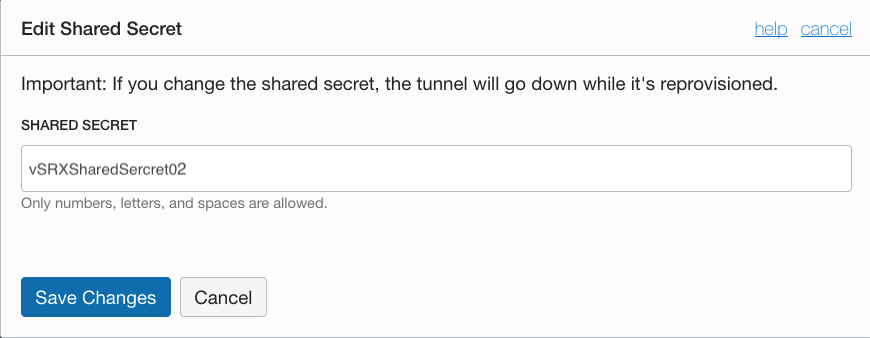
・Tunnel2(200.200.200.202)のShared Secret
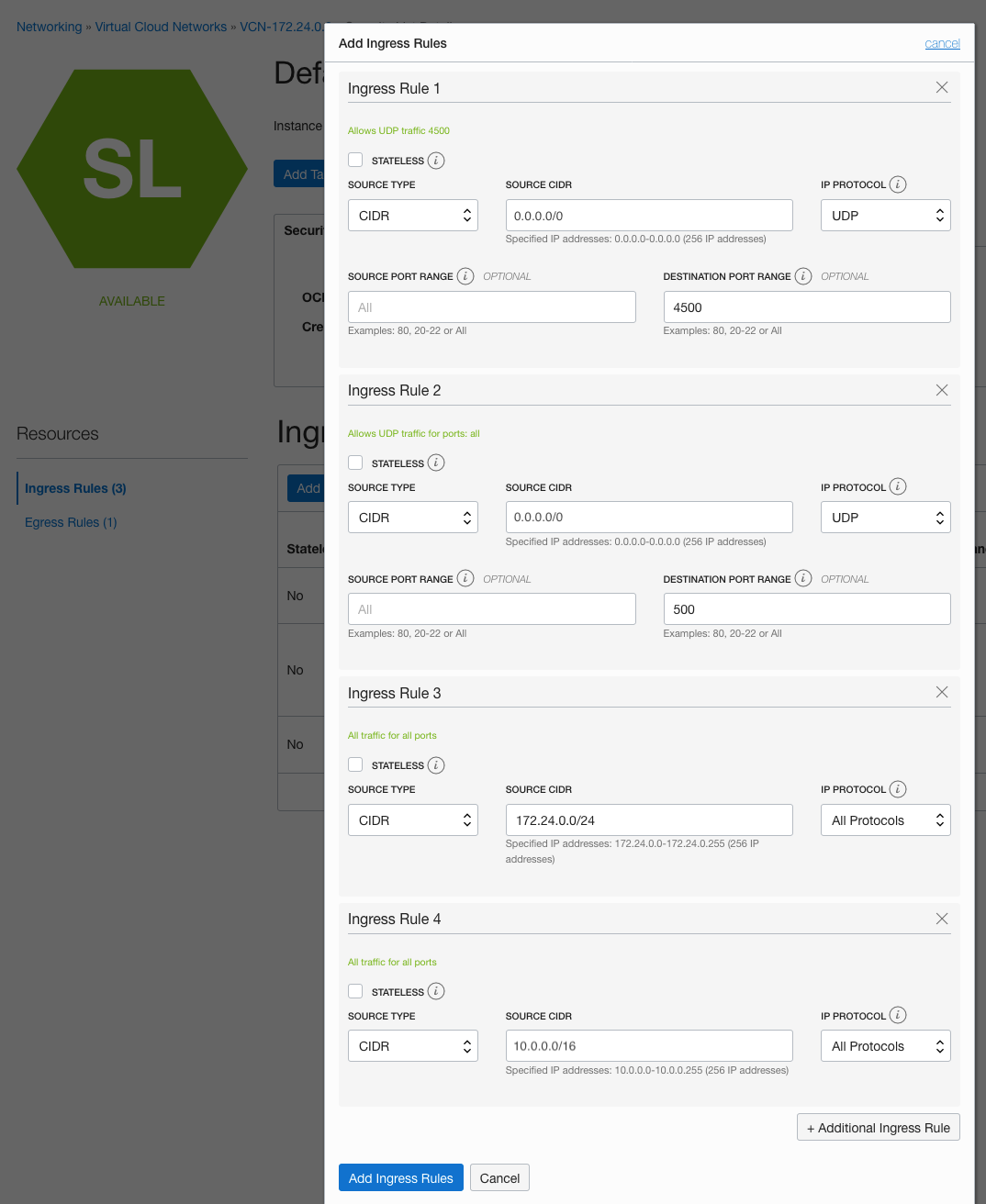
●Security List設定
IPSecに必要な 4500と500のUDP Portと対向の10.0.0.0/16と通信できるようにSecurity Listを設定
■vSRX IPSec設定
以下の設定コマンドを入力し、インターフェイス及びゾーンの作成と、スタティックルート(静的ルート)の設定を行います。
●管理者モードへ移行
root@% cli
root> configure exclusive
warning: uncommitted changes will be discarded on exit
Entering configuration mode
[edit]
root#
●IPsec IKE Phase1設定
以下の設定コマンドを入力し、IKE Phase1の設定を行います。
set security ike proposal oracle-ike-proposal authentication-method pre-shared-keys
set security ike proposal oracle-ike-proposal authentication-algorithm sha-384
set security ike proposal oracle-ike-proposal encryption-algorithm aes-256-cbc
set security ike proposal oracle-ike-proposal lifetime-seconds 28800
set security ike proposal oracle-ike-proposal dh-group group5
set security ike policy ike_pol_oracle-vpn01 mode main
set security ike policy ike_pol_oracle-vpn01 proposals oracle-ike-proposal
set security ike policy ike_pol_oracle-vpn01 pre-shared-key ascii-text vSRXSharedSercret01
set security ike gateway gw_oracle01 ike-policy ike_pol_oracle-vpn01
set security ike gateway gw_oracle01 dead-peer-detection
set security ike gateway gw_oracle01 external-interface ge-0/0/0.0
set security ike gateway gw_oracle01 address 200.200.200.201
set security ike policy ike_pol_oracle-vpn02 mode main
set security ike policy ike_pol_oracle-vpn02 proposals oracle-ike-proposal
set security ike policy ike_pol_oracle-vpn02 pre-shared-key ascii-text vSRXSharedSercret02
set security ike gateway gw_oracle02 ike-policy ike_pol_oracle-vpn02
set security ike gateway gw_oracle02 dead-peer-detection
set security ike gateway gw_oracle02 external-interface ge-0/0/0.0
set security ike gateway gw_oracle02 address 200.200.200.202
●IPsec IKE Phase2設定
以下の設定コマンドを入力し、IKE Phase2の設定を行います。
set security ipsec proposal vpn-monitor-options
set security ipsec proposal oracle-ipsec-proposal protocol esp
set security ipsec proposal oracle-ipsec-proposal authentication-algorithm hmac-sha1-96
set security ipsec proposal oracle-ipsec-proposal encryption-algorithm aes-256-cbc
set security ipsec proposal oracle-ipsec-proposal lifetime-seconds 3600
set security ipsec policy ipsec-pol-ipsec_pol_oracle-vpn perfect-forward-secrecy keys group5
set security ipsec policy ipsec-pol-ipsec_pol_oracle-vpn proposals oracle-ipsec-proposal
set security ipsec vpn oracle-vpn01 bind-interface st0.1
set security ipsec vpn oracle-vpn01 vpn-monitor
set security ipsec vpn oracle-vpn01 ike gateway gw_oracle01
set security ipsec vpn oracle-vpn01 ike ipsec-policy ipsec-pol-ipsec_pol_oracle-vpn
set security ipsec vpn oracle-vpn01 establish-tunnels immediately
set security ipsec vpn oracle-vpn02 bind-interface st0.2
set security ipsec vpn oracle-vpn02 vpn-monitor
set security ipsec vpn oracle-vpn02 ike gateway gw_oracle02
set security ipsec vpn oracle-vpn02 ike ipsec-policy ipsec-pol-ipsec_pol_oracle-vpn
set security ipsec vpn oracle-vpn02 establish-tunnels immediately
●Zone インターフェイス設定
・LAN側インターフェイス Zone設定
set security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services ssh
set security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services ping
・WAN側インターフェイス Zone設定
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services ping
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services ssh
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services ike
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services http
・VPNインターフェイス Zone設定
set security zones security-zone vpn interfaces st0.1
set security zones security-zone vpn interfaces st0.2
●Policy設定
・trustゾーンとvpnゾーン間の通信を許可
set security policies from-zone trust to-zone vpn policy permit-all match source-address any
set security policies from-zone trust to-zone vpn policy permit-all match destination-address any
set security policies from-zone trust to-zone vpn policy permit-all match application any
set security policies from-zone trust to-zone vpn policy permit-all then permit
set security policies from-zone vpn to-zone trust policy permit-all match source-address any
set security policies from-zone vpn to-zone trust policy permit-all match destination-address any
set security policies from-zone vpn to-zone trust policy permit-all match application any
set security policies from-zone vpn to-zone trust policy permit-all then permit
・trustゾーンとuntrustゾーン間の通信を許可
set security policies from-zone trust to-zone trust policy default-permit match source-address any
set security policies from-zone trust to-zone trust policy default-permit match destination-address any
set security policies from-zone trust to-zone trust policy default-permit match application any
set security policies from-zone trust to-zone trust policy default-permit then permit
set security policies from-zone trust to-zone untrust policy default-permit match source-address any
set security policies from-zone trust to-zone untrust policy default-permit match destination-address any set security policies from-zone trust to-zone untrust policy default-permit match application any
set security policies from-zone trust to-zone untrust policy default-permit then permit
set security zones security-zone trust tcp-rst
・untrustゾーンからtrustゾーンへの通信はuntrust interfaces ge-0/0/0.0に個別設定したプロトコルのみ許可
set security policies from-zone untrust to-zone trust policy default-deny match source-address any
set security policies from-zone untrust to-zone trust policy default-deny match destination-address any
set security policies from-zone untrust to-zone trust policy default-deny match application any
set security policies from-zone untrust to-zone trust policy default-deny then deny
set security zones security-zone trust tcp-rst
●設定保存
[edit]
root# commit
commit complete
■IPSec接続確認
以下のコマンドを入力して、IKE SA, IPsec SAが正常に確立していることを確認
root> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
39237 UP 86c315a81cc3 d8e9489d8d90 Main 200.200.200.201
39237 UP f56d3577d51f a4e83b20ea89 Main 200.200.200.202
●SA が確立されていることを確認
接続済みであればパケットがカウントされていきます
root> show security ipsec statistics
ESP Statistics:
Encrypted bytes: 258704
Decrypted bytes: 95284
Encrypted packets: 1702
Decrypted packets: 1700
・・・
root> show security ipsec statistics
ESP Statistics:
Encrypted bytes: 264176
Decrypted bytes: 97300
Encrypted packets: 1738
Decrypted packets: 1736
・・・
.IPSec接続情報を出力して確認
root> show security ipsec security-associations detail
ID: 131073 Virtual-system: root, VPN Name: oracle-vpn01
Local Gateway: 10.0.2.201, Remote Gateway: 200.200.200.201
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv1
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1
Port: 4500, Nego#: 91, Fail#: 0, Def-Del#: 0 Flag: 0x600a29
Tunnel events:
Sat Jul 06 2019 23:57:42 +0900: IPSec SA negotiation successfully completed (1 times)
Sat Jul 06 2019 23:57:32 +0900: VPN monitoring detected tunnel as down. Existing IPSec SAs cleared (1 times)
Sat Jul 06 2019 23:55:42 +0900: IPSec SA negotiation successfully completed (1 times)
Sat Jul 06 2019 23:55:32 +0900: VPN monitoring detected tunnel as down. Existing IPSec SAs cleared (1 times)
Sat Jul 06 2019 23:53:42 +0900: IPSec SA negotiation successfully completed (1 times)
Sat Jul 06 2019 23:53:32 +0900: VPN monitoring detected tunnel as down. Existing IPSec SAs cleared (1 times)
Sat Jul 06 2019 23:51:42 +0900: IPSec SA negotiation successfully completed (1 times)
Sat Jul 06 2019 23:51:32 +0900: VPN monitoring detected tunnel as down. Existing IPSec SAs cleared (1 times)
Sat Jul 06 2019 20:57:33 +0900: IKE SA negotiation successfully completed (35 times)
Direction: inbound, SPI: a50d0109, AUX-SPI: 0
, VPN Monitoring: UP
Hard lifetime: Expires in 3514 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2905 seconds
Mode: Tunnel(10 10), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 6e79af70, AUX-SPI: 0
, VPN Monitoring: UP
Hard lifetime: Expires in 3514 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2905 seconds
Mode: Tunnel(10 10), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
ID: 131074 Virtual-system: root, VPN Name: oracle-vpn02
Local Gateway: 10.0.2.201, Remote Gateway: 200.200.200.202
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv1
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.2
Port: 500, Nego#: 86, Fail#: 0, Def-Del#: 0 Flag: 0x600a29
Tunnel events:
Sat Jul 06 2019 23:58:22 +0900: IPSec SA negotiation successfully completed (1 times)
Sat Jul 06 2019 23:58:12 +0900: VPN monitoring detected tunnel as down. Existing IPSec SAs cleared (1 times)
Sat Jul 06 2019 23:56:32 +0900: IPSec SA negotiation successfully completed (1 times)
Sat Jul 06 2019 23:56:22 +0900: VPN monitoring detected tunnel as down. Existing IPSec SAs cleared (1 times)
Sat Jul 06 2019 23:54:32 +0900: IPSec SA negotiation successfully completed (1 times)
Sat Jul 06 2019 23:54:22 +0900: VPN monitoring detected tunnel as down. Existing IPSec SAs cleared (1 times)
Sat Jul 06 2019 23:52:32 +0900: IPSec SA negotiation successfully completed (1 times)
Sat Jul 06 2019 23:52:22 +0900: VPN monitoring detected tunnel as down. Existing IPSec SAs cleared (1 times)
Sat Jul 06 2019 21:09:13 +0900: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: 96feb2a0, AUX-SPI: 0
, VPN Monitoring: UP
Hard lifetime: Expires in 3554 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2911 seconds
Mode: Tunnel(10 10), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 85b0170f, AUX-SPI: 0
, VPN Monitoring: UP
Hard lifetime: Expires in 3554 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2911 seconds
Mode: Tunnel(10 10), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
●DRG IPsec Connection Status UP確認
IPsec ConnectionのStatusがUPしていることを確認
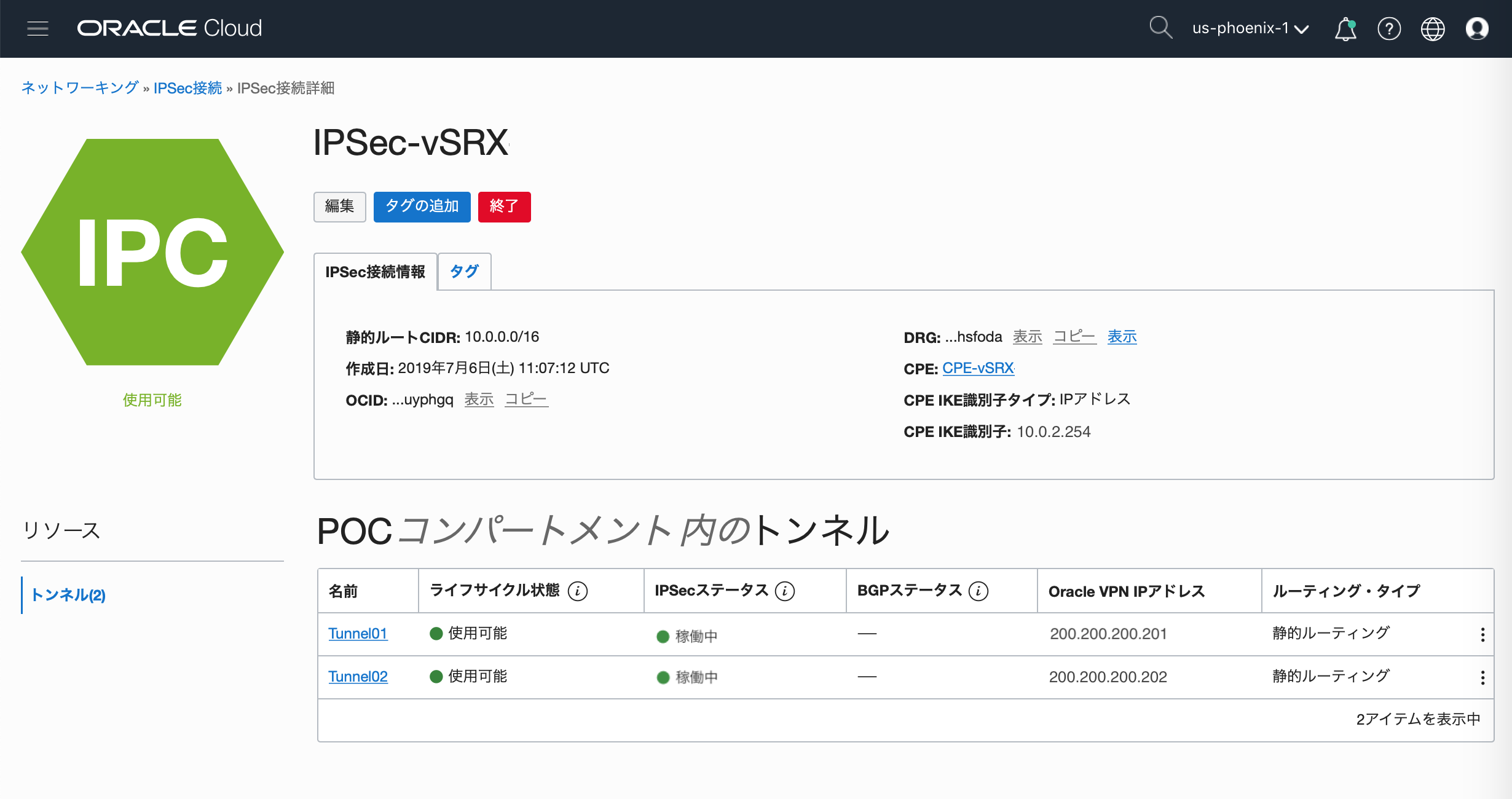
■接続確認
IPSec通信が確立できていることを確認するためにそれぞれのNetwork上にあるインスタン同士が通信できることを確認します
●ssh接続確認
・Tokyo --> Phoenix間インスタンス ssh接続確認
[opc@tokyo-inst01 ~]$ ssh -i <ssh鍵> opc@172.24.0.2 hostname
phoenix-inst1
・Phoenix --> Tokyo間インスタンス ssh接続確認
[opc@phoenix-inst1 ~]$ ssh -i <ssh鍵> opc@10.0.10.2 hostname
tokyo-inst01
■VPN Connect Metric確認
OCIコンソソールで各トンネルのIPSec接続のメトリックでStatus,Error,Sent/ReceivedのMonitoring情報を確認できます

■参考
・【SRX】JUNOS ハンズオントレーニング資料 SRXシリーズ サービス ゲートウェイ コース
・vSRX Deployment Guide for KVM
・vSRX Documentation