■ 目的
稀に、Private Network に Non-RFC1918 アドレス(Illegal Public Address)を利用したいということがあるかもわかりません。
その時に利用される IPは[1.1.1.1]など、いわゆる非正規(イリーガル)グローバルアドレス=公式には他社が登録しているけど、Internet上に広告していないのでこっそり利用可能ですが、
今後、Oracle Cloud Infrastructure(OCI)のPublic IPのサービスや他社Cloud(Office365、salesforce.com等)等の利用の際に、正規で利用されている事業者のアドレスと重複する可能性があります。
そのため、Non-RFC1918(非正規 グローバルアドレス,Illegal Public Address)は、自己責任で実装となります。
ということで、オンプレミスとOCIのVCN それぞれNon-RFC1918 CIDRを使用した構成でIPSec接続をおこない、使用するIPは例でよくつかわれる "1.2.3.4" と 有名どころなPublic IP "8.8.8.8" をインスタンスに設定して双方向で通信接続できるかやってみてみます。
■ 構成と構築
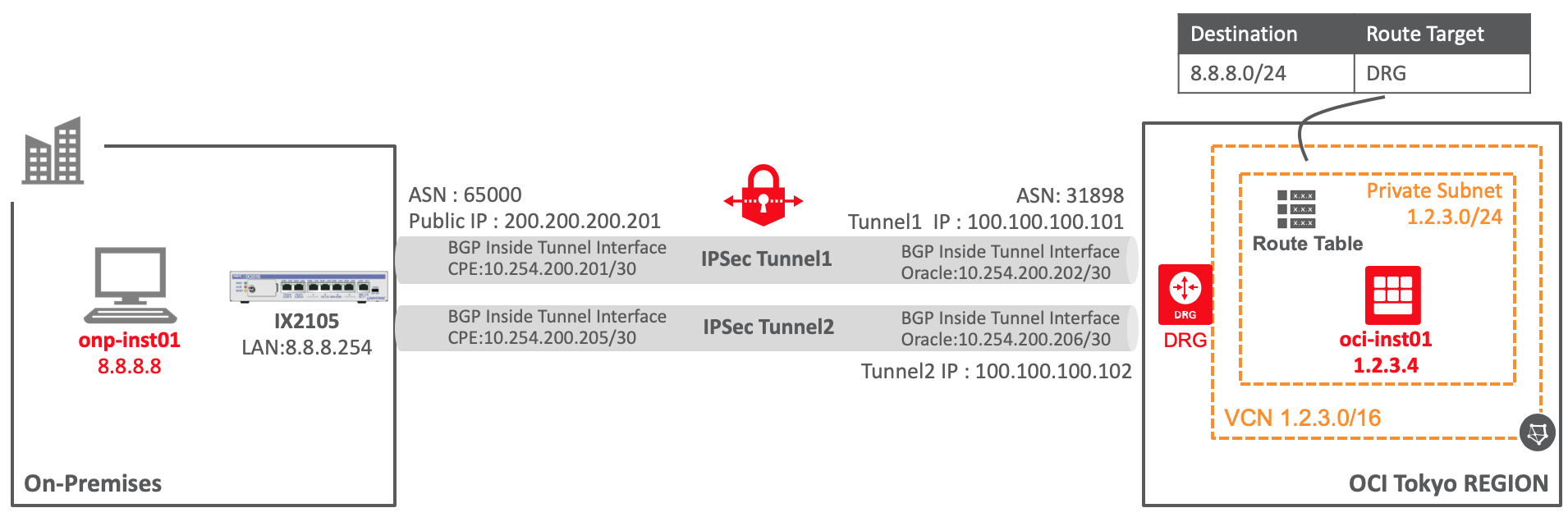 手順はいつものとおり図のように構築します
使用ルーターは、NEC UNIVERGE IX2105を使用します
手順はいつものとおり図のように構築します
使用ルーターは、NEC UNIVERGE IX2105を使用します
■ Router設定
以下のようにNEC UNIVERGE IX2105を設定
Router# configure
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)# show config
Using 3938 out of 524288 bytes
! NEC Portable Internetwork Core Operating System Software
! IX Series IX2105 (magellan-sec) Software, Version 9.2.20, RELEASE SOFTWARE
! Compiled Aug 19-Wed-2015 16:25:46 JST #2
! Last updated Jul 12-Fri-2019 08:47:16 JST
!
!
hostname Router
timezone +09 00
!
!
!
username admin password hash 6B1R4JK2 administrator
!
!
!
!
!
!
logging buffered 131072
logging subsystem all warn
logging timestamp datetime
!
!
ip ufs-cache enable
ip multipath per-flow
ip route default GigaEthernet0.1
ip dhcp enable
ip prefix-list as-path-in 10 permit any
ip prefix-list as-path-out 10 permit any
ip access-list sec-list permit ip src any dest any
ip access-list web-http-acl permit ip src any dest 8.8.8.212/32
ip access-list web_console permit ip src any dest 8.8.8.212/32
!
!
!
ike nat-traversal
!
ike proposal ike-prop encryption aes-256 hash sha2-256 group 1536-bit
!
ike policy ike-pol1 peer 100.100.100.101 key IPSecKey01 ike-prop
!
ike policy ike-pol2 peer 100.100.100.102 key IPSecKey02 ike-prop
!
ipsec autokey-proposal ipsec-prop esp-aes-256 esp-sha lifetime time 3600
!
ipsec autokey-map ipsec-map1 sec-list peer 100.100.100.101 ipsec-prop pfs 1536-bit
!
ipsec autokey-map ipsec-map2 sec-list peer 100.100.100.102 ipsec-prop pfs 1536-bit
!
!
!
!
!
!
!
!
!
proxy-dns ip enable
proxy-dns interface GigaEthernet0.1 priority 254
!
telnet-server ip enable
!
!
http-server username admin
http-server ip access-list web-http-acl
http-server ip enable
!
web-console interface lan1 GigaEthernet1.0
!
!
!
vrrp enable
!
!
!
watch-group watch_tunnel0 10
event 20 ip unreach-host 8.8.8.212 Tunnel0.0 source GigaEthernet1.0
action 20 ipsec clear-sa Tunnel0.0
!
network-monitor watch_tunnel0 enable
!
watch-group watch_tunnel1 10
event 20 ip unreach-host 8.8.8.212 Tunnel1.0 source GigaEthernet1.0
action 20 ipsec clear-sa Tunnel1.0
!
network-monitor watch_tunnel1 enable
!
!
route-map bgp permit 65000
!
route-map rmap-in permit 10
match ip address prefix-list as-path-in
set as-path prepend 31898 31898
!
route-map rmap-out permit 10
match ip address prefix-list as-path-out
set as-path prepend 65000 65000
!
ppp profile web-ppp-gigaethernet0.1
authentication myname frt645gf@ntt.ne.jp
authentication password frt645gf@ntt.ne.jp passwd
!
ip dhcp profile web-dhcp-gigaethernet1.0
dns-server 8.8.8.212
!
router bgp 65000
neighbor 10.254.200.202 remote-as 31898
neighbor 10.254.200.202 timers 10 30
neighbor 10.254.200.206 remote-as 31898
neighbor 10.254.200.206 timers 10 30
address-family ipv4 unicast
neighbor 10.254.200.206 route-map rmap-in in
neighbor 10.254.200.206 route-map rmap-out out
network 8.8.8.0/24
!
device GigaEthernet0
!
device GigaEthernet1
!
interface GigaEthernet0.0
no ip address
shutdown
!
interface GigaEthernet1.0
description LAN1
ip address 8.8.8.212/24
ip dhcp binding web-dhcp-gigaethernet1.0
vrrp 254 ip 8.8.8.254
vrrp 254 priority 95
vrrp 254 ip virtual-host
no shutdown
!
interface GigaEthernet0.1
description WAN1
encapsulation pppoe
auto-connect
ppp binding web-ppp-gigaethernet0.1
ip address ipcp
ip tcp adjust-mss auto
ip napt enable
no shutdown
!
interface Loopback0.0
no ip address
!
interface Null0.0
no ip address
!
interface Tunnel0.0
tunnel mode ipsec
ip address 10.254.200.201/30
ip tcp adjust-mss auto
ipsec policy tunnel ipsec-map1 df-bit ignore pre-fragment out
no shutdown
!
interface Tunnel1.0
tunnel mode ipsec
ip address 10.254.200.205/30
ip tcp adjust-mss auto
ipsec policy tunnel ipsec-map2 df-bit ignore pre-fragment out
no shutdown
■ OCI IPSec 接続確認

■ BGP設定確認
● Route情報確認
Router(config)# show ip route
IP Routing Table - 8 entries, 4 hidden, 2036 frees
Entries: 5 Connected, 1 Static, 0 RIP, 0 OSPF, 2 BGP
Codes: C - Connected, S - Static, R - RIP, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, B - BGP
* - Candidate default, s - Summary
Timers: Age
S* 0.0.0.0/0 [1/1] is directly connected, GigaEthernet0.1, 16:34:07
1.0.0.0/8 is subnetted, 2 subnets
B 1.2.3.0/24 [20/0] via 10.254.200.202, Tunnel0.0, 0:28:28
B 1.2.10.0/24 [20/0] via 10.254.200.202, Tunnel0.0, 0:28:28
8.0.0.0/8 is subnetted, 2 subnets
C 8.8.8.0/24 [0/1] is directly connected, GigaEthernet1.0, 0:29:16
C 8.8.8.254/32 [0/1] is directly connected, Virtual254, 0:29:12
10.254.0.0/16 is subnetted, 2 subnets
C 10.254.200.202/30 [0/1] is directly connected, Tunnel0.0, 16:20:22
C 10.254.200.206/30 [0/1] is directly connected, Tunnel1.0, 16:20:22
● BGP情報確認
・すべてのBGP接続のステータスを確認
Router(config)# show ip bgp summary
BGP router ID 10.254.200.205, local AS number 65000
4 BGP AS-PATH entries
Neighbor V AS MsgRcvd MsgSent Up/DownTime State
10.254.200.202 4 31898 6381 5836 0:23:39 ESTABLISHED
10.254.200.206 4 31898 6421 5839 0:23:39 ESTABLISHED
Total number of neighbors 2
・ BGP情報確認
Router(config)# show ip bgp
BGP table version is 28, local router ID is 10.254.200.205
Local AS number 65000
Status codes: s - suppressed, * - valid, h - history
> - best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Path
* 1.2.3.0/24 10.254.200.206 31898 31898 31898 i
*> 10.254.200.202 31898 i
* 1.2.10.0/24 10.254.200.206 31898 31898 31898 i
*> 10.254.200.202 31898 i
*> 8.8.8.0/24 0.0.0.0 1 i
10.254.200.0/24 0.0.0.0 0 i
Total number of prefixes 6
・ NeighborのBGPおよび TCP 接続に関する情報を確認
Router(config)# show ip bgp neighbors 10.254.200.202 advertised-routes
BGP table version is 28, local router ID is 10.254.200.205
Local AS number 65000
Status codes: s - suppressed, * - valid, h - history
> - best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Path
*> 8.8.8.0/24 10.254.200.201 1 i
Total number of prefixes 1
Router(config)# show ip bgp neighbors 10.254.200.202 received-routes
BGP table version is 28, local router ID is 10.254.200.205
Local AS number 65000
Status codes: s - suppressed, * - valid, h - history
> - best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Path
*> 1.2.3.0/24 10.254.200.202 31898 i
*> 1.2.10.0/24 10.254.200.202 31898 i
Total number of prefixes 2
Router(config)# show ip bgp neighbors 10.254.200.206 advertised-routes
BGP table version is 28, local router ID is 10.254.200.205
Local AS number 65000
Status codes: s - suppressed, * - valid, h - history
> - best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Path
*> 8.8.8.0/24 10.254.200.205 1 65000 65000 i
Total number of prefixes 1
Router(config)# show ip bgp neighbors 10.254.200.206 received-routes
BGP table version is 28, local router ID is 10.254.200.205
Local AS number 65000
Status codes: s - suppressed, * - valid, h - history
> - best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Path
* 1.2.3.0/24 10.254.200.206 31898 31898 31898 i
* 1.2.10.0/24 10.254.200.206 31898 31898 31898 i
Total number of prefixes 2
■ 接続確認
● On-Premises -> OCI接続確認
・ traceroute確認
onp-inst01:~ root# traceroute 1.2.3.4
traceroute to 1.2.3.4 (1.2.3.4), 64 hops max, 52 byte packets
1 8.8.8.254 (8.8.8.254) 1.799 ms 3.034 ms 1.227 ms
2 * * *
3 1.2.3.4 (1.2.3.4) 5.682 ms 6.982 ms 5.358 ms
・ ping確認
onp-inst01:~ root# ping 1.2.3.4 -c 10
PING 1.2.3.4 (1.2.3.4): 56 data bytes
64 bytes from 1.2.3.4: icmp_seq=0 ttl=62 time=7.716 ms
64 bytes from 1.2.3.4: icmp_seq=1 ttl=62 time=10.973 ms
64 bytes from 1.2.3.4: icmp_seq=2 ttl=62 time=6.656 ms
64 bytes from 1.2.3.4: icmp_seq=3 ttl=62 time=6.813 ms
64 bytes from 1.2.3.4: icmp_seq=4 ttl=62 time=6.135 ms
64 bytes from 1.2.3.4: icmp_seq=5 ttl=62 time=7.018 ms
64 bytes from 1.2.3.4: icmp_seq=6 ttl=62 time=8.734 ms
64 bytes from 1.2.3.4: icmp_seq=7 ttl=62 time=6.887 ms
64 bytes from 1.2.3.4: icmp_seq=8 ttl=62 time=6.592 ms
64 bytes from 1.2.3.4: icmp_seq=9 ttl=62 time=6.771 ms
--- 1.2.3.4 ping statistics ---
10 packets transmitted, 10 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 6.135/7.429/10.973/1.364 ms
・ ssh接続確認
onp-inst01:~ root# ssh -i id_rsa opc@1.2.3.4
The authenticity of host '1.2.3.4 (1.2.3.4)' can't be established.
ECDSA key fingerprint is SHA256:agH9jrx4S2Kw2G.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '1.2.3.4' (ECDSA) to the list of known hosts.
Last login: Fri Jul 12 15:59:12 2019 from 8.8.8.2
[opc@oci-inst01 ~]$ hostname
oci-inst01
● OCI -> On-Premises接続確認
・ traceroute確認
[opc@oci-inst01 ~]$ traceroute 8.8.8.8
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 60 byte packets
1 * * *
2 * * *
3 8.8.8.8 (8.8.8.8) 5.647 ms 6.229 ms 5.597 ms
・ ping確認
[opc@oci-inst01 ~]$ ping 8.8.8.8 -c 10
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=62 time=83.4 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=62 time=107 ms
64 bytes from 8.8.8.8: icmp_seq=3 ttl=62 time=25.2 ms
64 bytes from 8.8.8.8: icmp_seq=4 ttl=62 time=49.4 ms
64 bytes from 8.8.8.8: icmp_seq=5 ttl=62 time=71.9 ms
64 bytes from 8.8.8.8: icmp_seq=6 ttl=62 time=92.6 ms
64 bytes from 8.8.8.8: icmp_seq=7 ttl=62 time=63.8 ms
64 bytes from 8.8.8.8: icmp_seq=8 ttl=62 time=8.43 ms
64 bytes from 8.8.8.8: icmp_seq=9 ttl=62 time=135 ms
64 bytes from 8.8.8.8: icmp_seq=10 ttl=62 time=79.0 ms
--- 8.8.8.8 ping statistics ---
10 packets transmitted, 10 received, 0% packet loss, time 9015ms
rtt min/avg/max/mdev = 8.434/71.753/135.776/35.721 ms
・ ssh接続確認
[opc@oci-inst01 ~]$ ssh root@8.8.8.8
The authenticity of host '8.8.8.8 (8.8.8.8)' can't be established.
ECDSA key fingerprint is SHA256:FkidRp3f180gTMol.
ECDSA key fingerprint is MD5:98:4f:41:7c:24:b1:.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '8.8.8.8' (ECDSA) to the list of known hosts.
Password:
Last login: Sat Jul 13 01:00:23 2019 from 1.2.3.4
onp-inst01:~ root# hostname
onp-inst01.local
■ 参考
● OCI利用IP Address
Oracle Cloud Infrastructure(OCI)で使用される IP Address は次のようなものがあります
・Networking Overview
・Public IP Address Ranges
・Public IP Addresses for VCNs and the Oracle Services Network
・FastConnect Public Peering Advertised Routes
・Object Storage IP Addresses
・Network Setup for DB Systems: Requirements for IP Address Space