■目的
AWSとIPSecで接続する場合、Software VPN Routerが必要です。
Software VPN RouterはOSSのLibreswan等を使用することで可能ですが、
企業用途での使用による安定稼働と障害時の保守サポート、セキュリティを考慮すると商用ベンダー製品を使用することが求められます。
ということで、今回は AWS Marketplaceにある Cisco ASAvを使用してみてみます。
■接続イメージ

■各種情報
| ソース | パラメータ | 値 |
|---|---|---|
| ASAv | ${outsideInterfaceName} | management |
| OCI IPSec Connection | ${ipAddress1} | 200.200.200.201 |
| OCI IPSec Connection | ${sharedSecret1} | ASAvSHAREDSECRET01 |
| OCI IPSec Connection | ${ipAddress2} | 200.200.200.202 |
| OCI IPSec Connection | $${sharedSecret2} | ASAvSHAREDSECRET02 |
| OCI VCN | ${OracleInsideTunnelIPAddress1} | 10.0.0.0 255.255.0.0 |
| OCI VCN | ${OracleInsideTunnelIPAddress2} | 10.0.0.0 255.255.0.0 |
| ASAv VTI | ${CpeInsideTunnelIpAddressWithMask1} | 192.168.0.101 255.255.255.252 |
| ASAv VTI | ${CpeInsideTunnelIpAddressWithMask2} | 192.168.0.201 255.255.255.252 |
| ASAv VTI | ${tunnelInterfaceName1} | ORACLE-VPN1 |
| ASAv VTI | ${tunnelInterfaceName2} | ORACLE-VPN2 |
■ ASAvインスタンス作成
● 「EC2ダッシュボート」画面
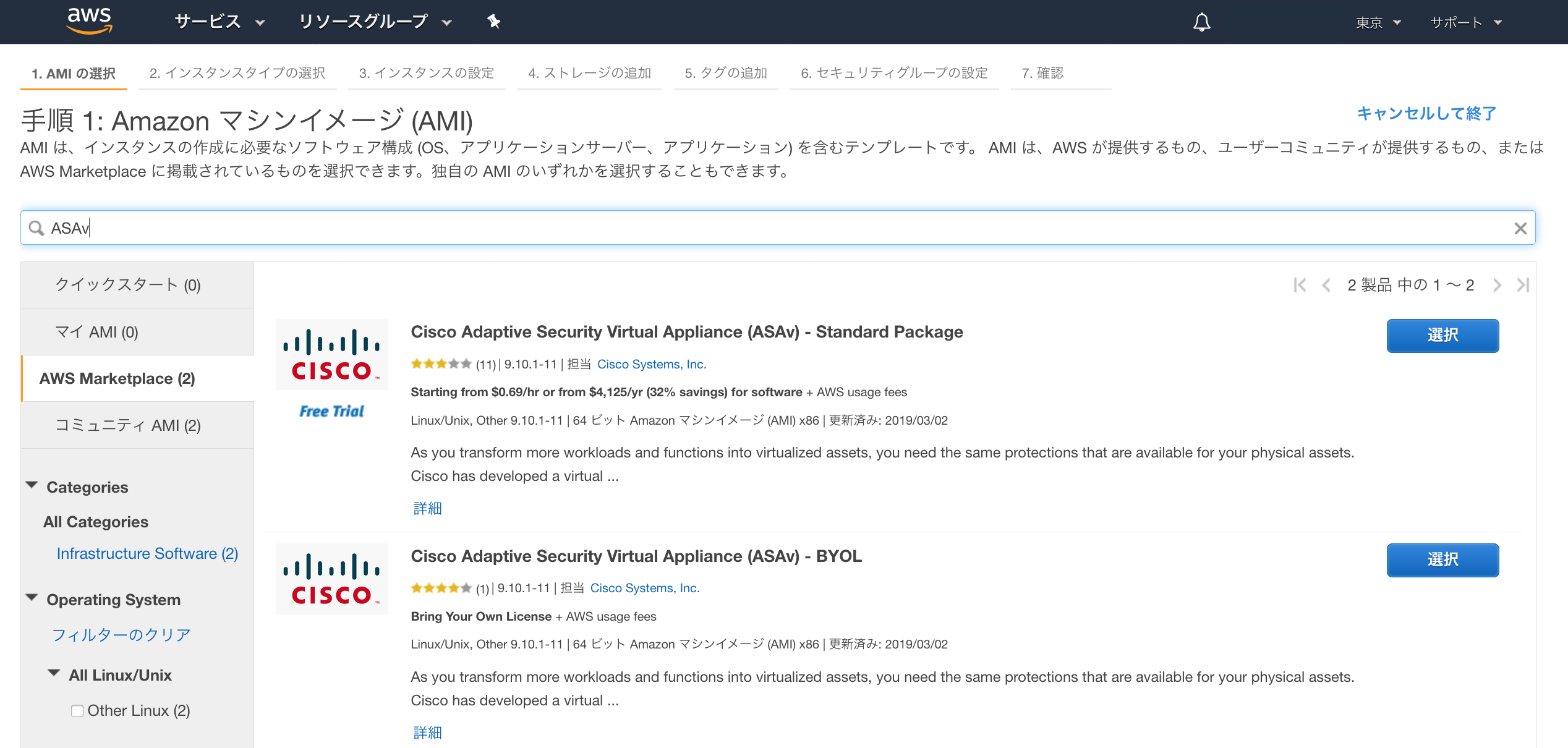
・AWS Marketplace からASAvを検索
AWS Marketplace から、ASAvを検索し、使用するASAvの[選択]ボタンをクリック
・ASAvの内容を確認し[Continue]ボタンをクリック

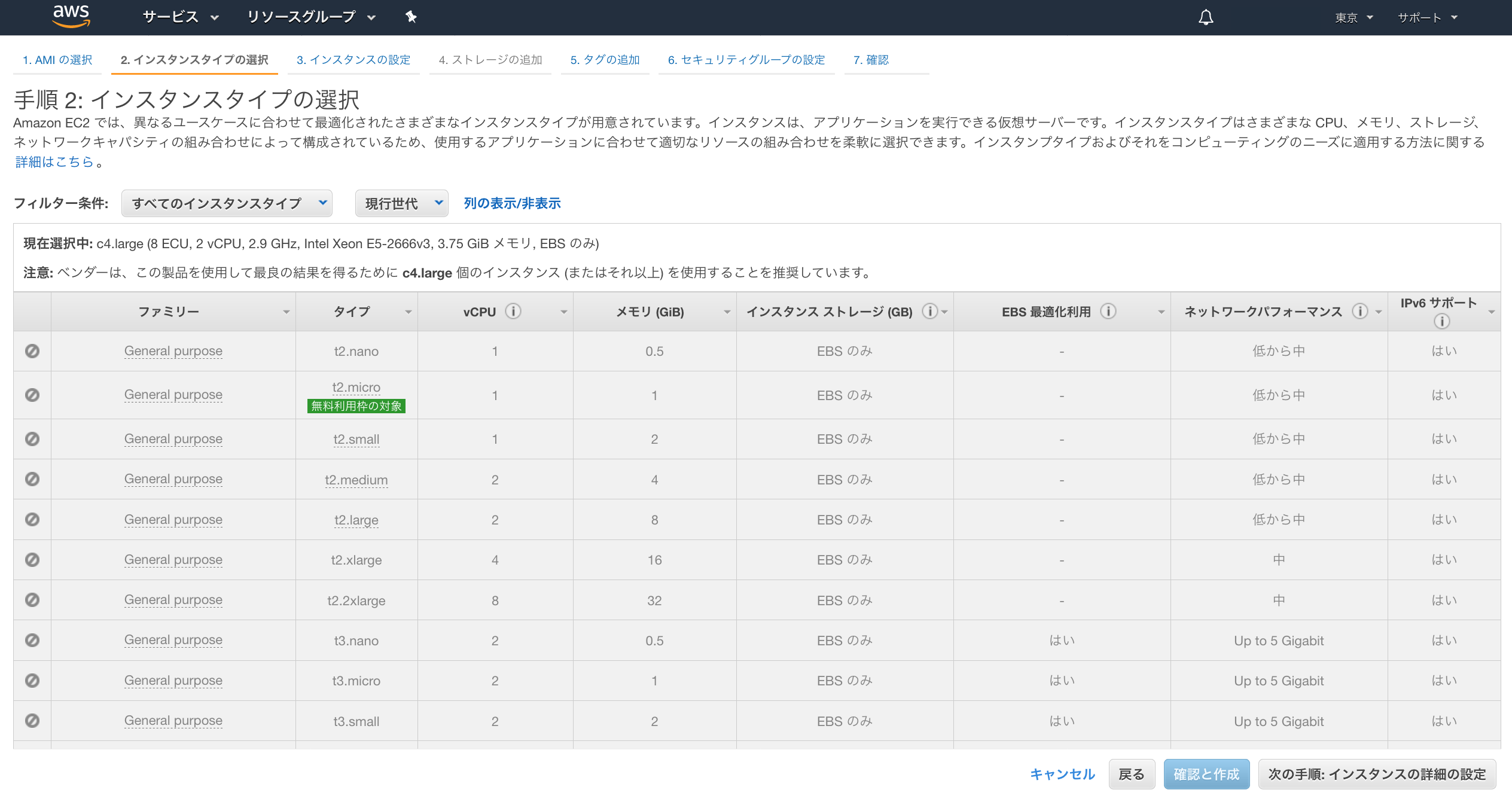
● 「手順 2: インスタンスタイプの選択」画面
・インスタンスタイプを選択し、[次の手順:インスタンスお詳細の設定]をクリック
ここでは、c4.largeを選択
● 「手順 3: インスタンスの詳細の設定」画面
サブネット:Management Subnetを選択
ネットワークインターフェース: [デバイスの追加]をクリックし、eth1を追加
eth0:Management Subnet
eth1:LAN Subnet

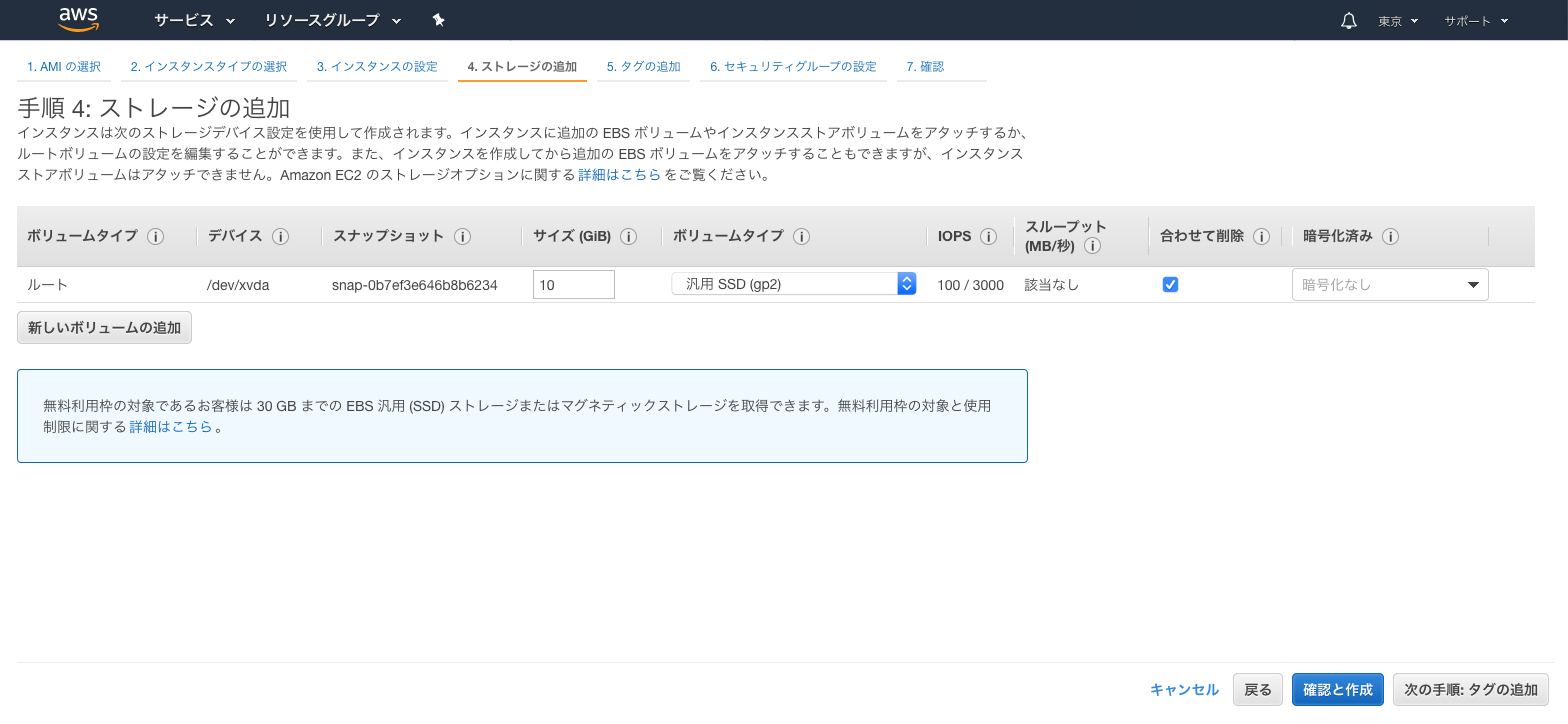
● 「手順 4: ストレージの追加」画面
● 「手順 5: タグの追加」画面
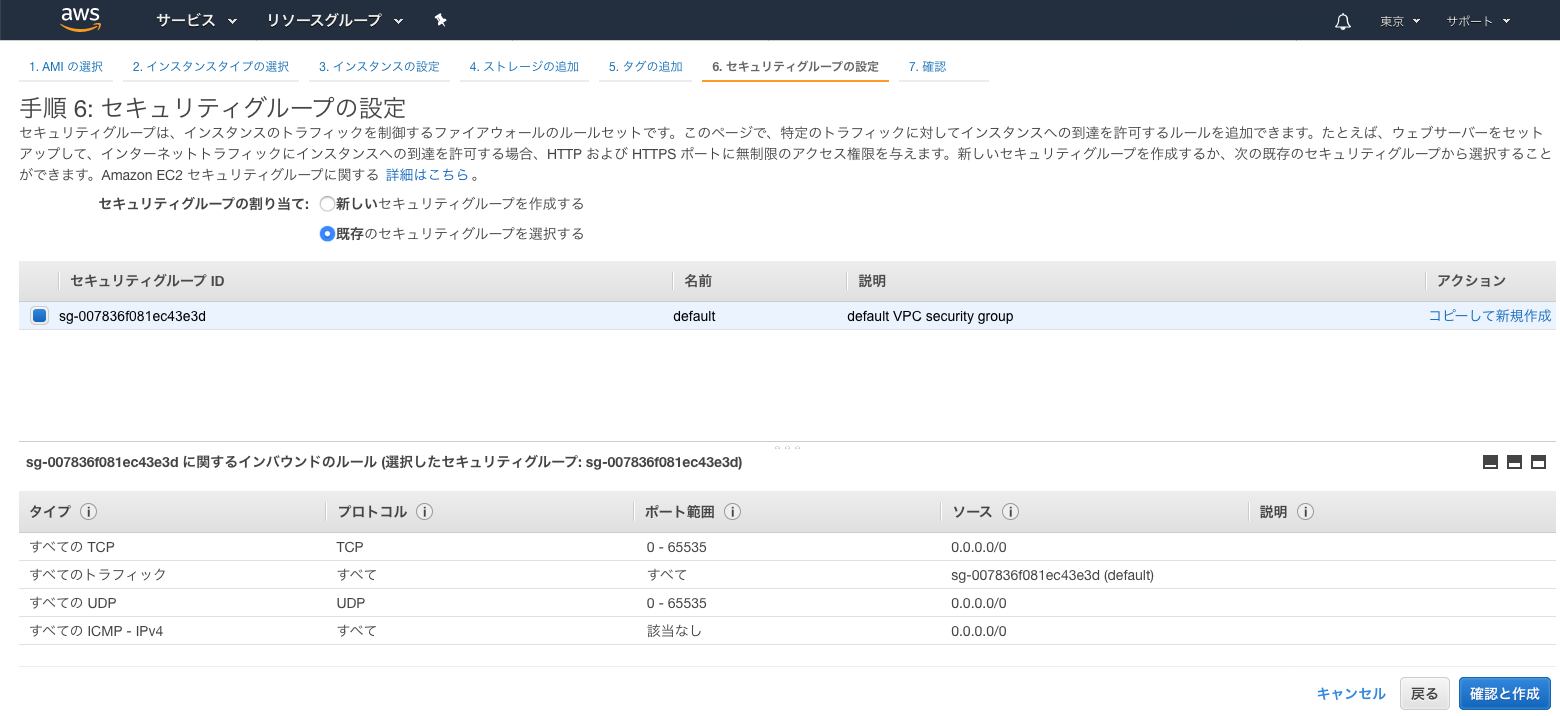
● 「手順 6: セキュリティグループの設定」画面
IPSec用の UDP:4500,500 IP:50を通すように設定
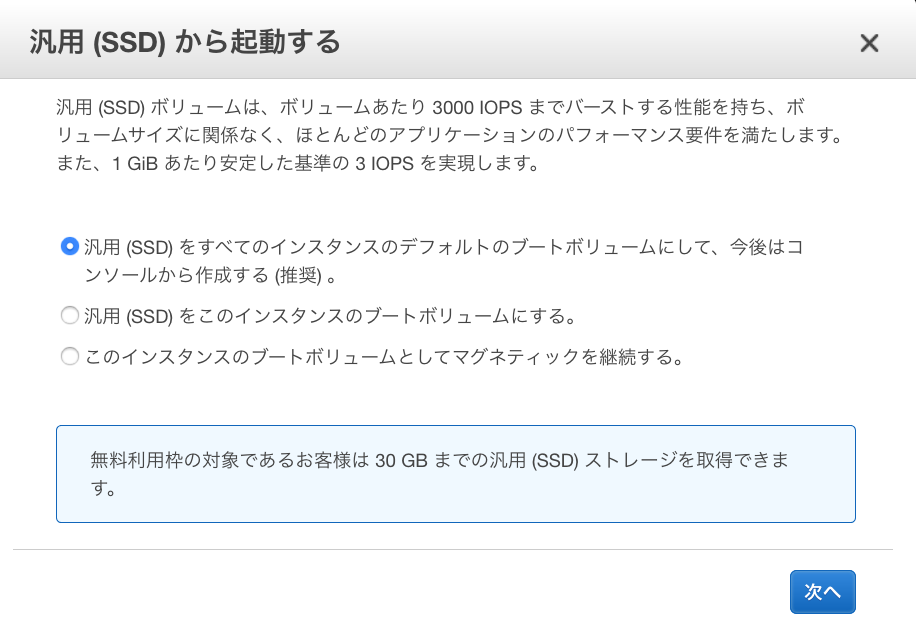
● 「汎用(SSD)から起動する」画面
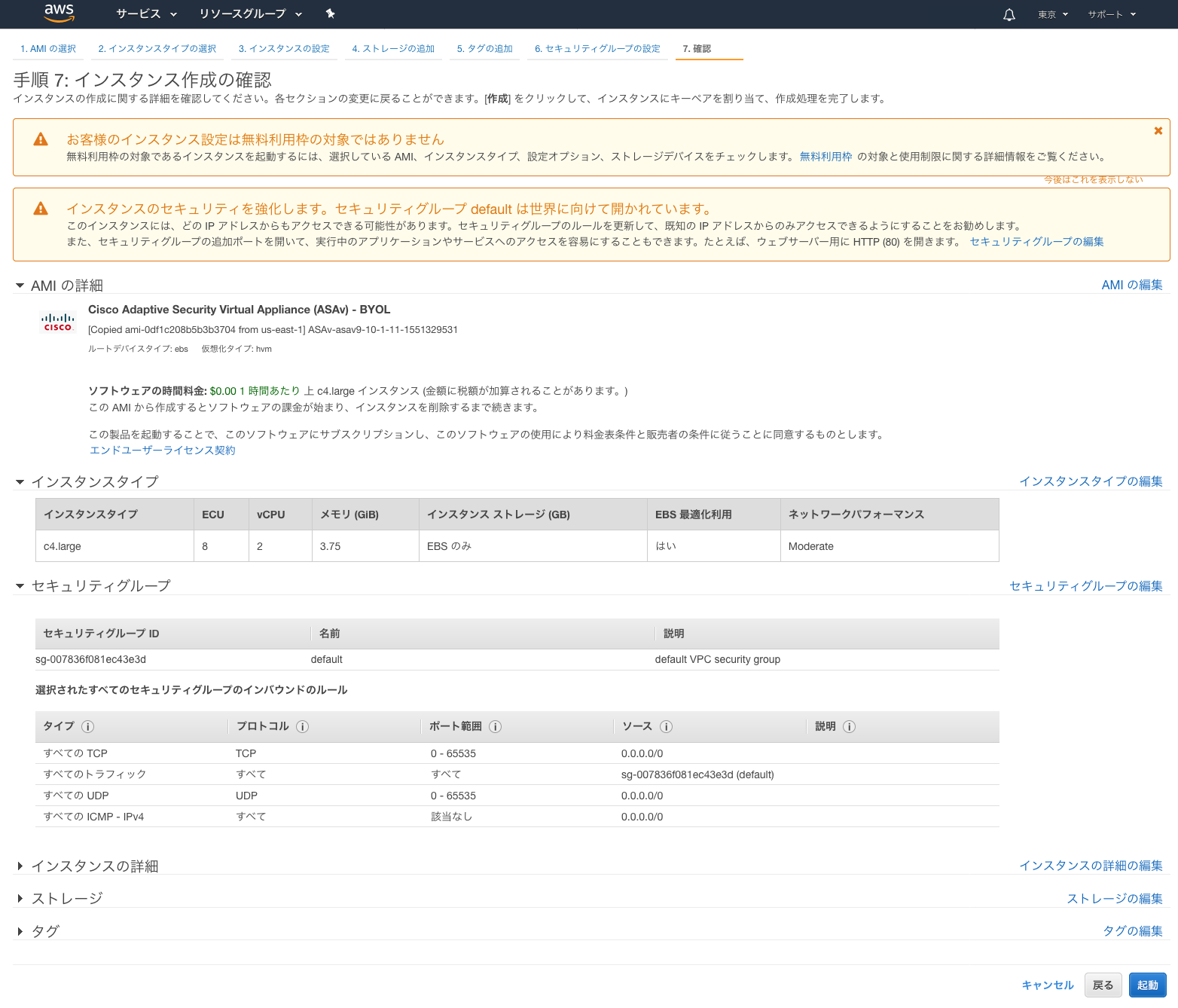
● 「手順 7: インスタンス作成の確認」画面
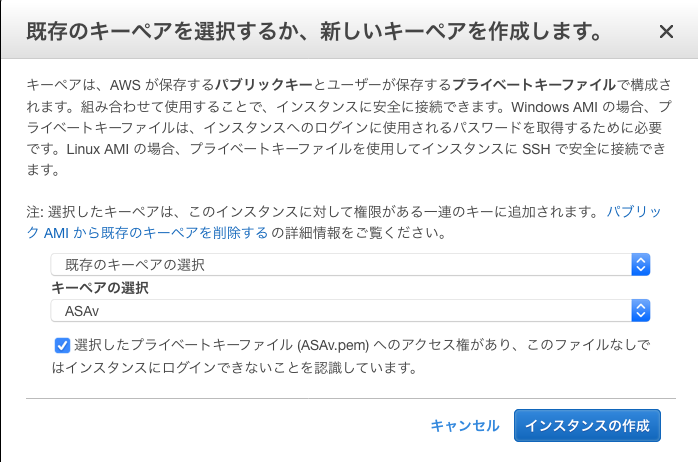
● 「既存のキーペアを選択するか、新しいキーペアを作成します。」画面
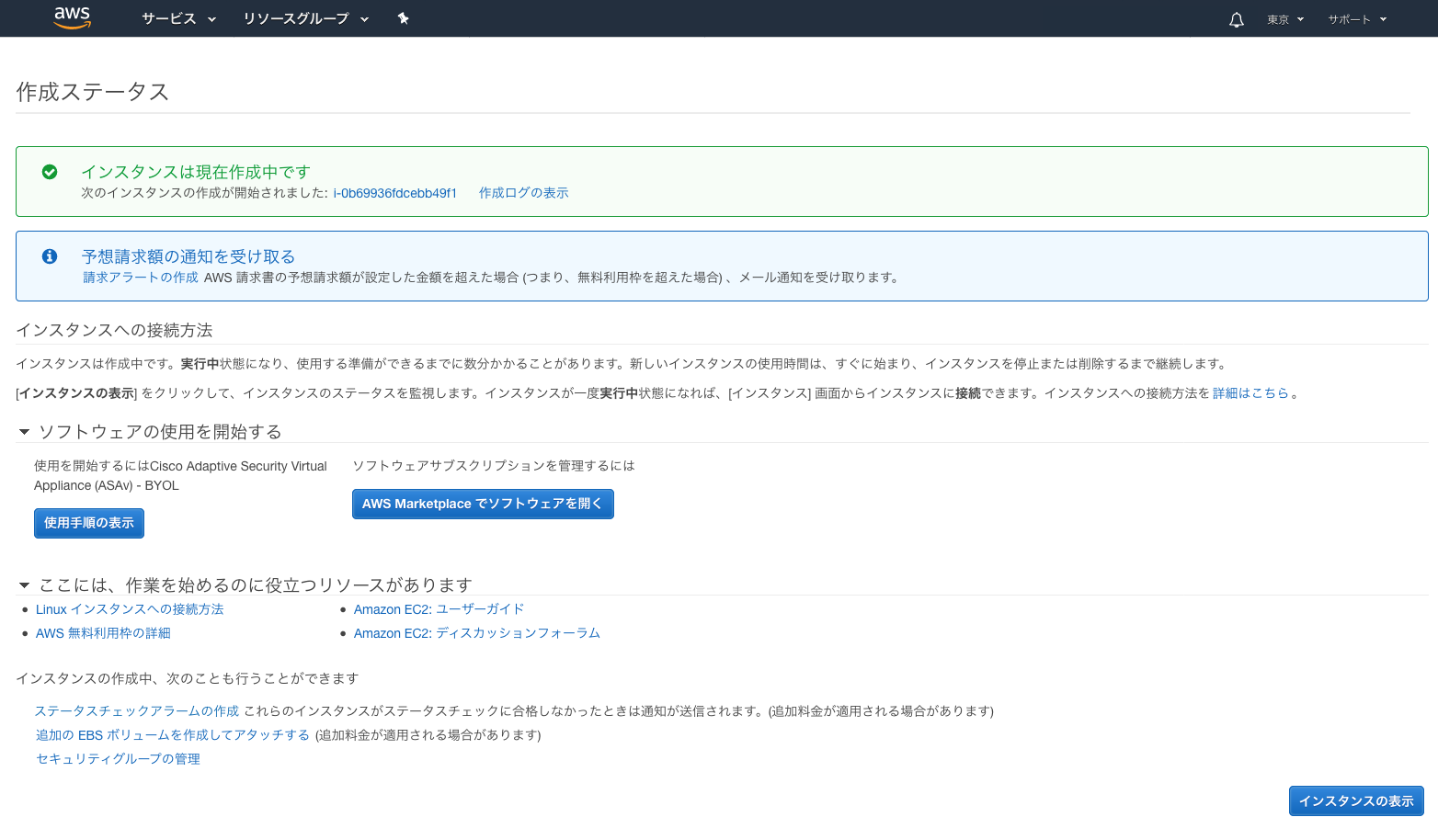
● 「作成ステータス」画面
■ ASAvインスタンス追加設定
● Elastic IPSec設定
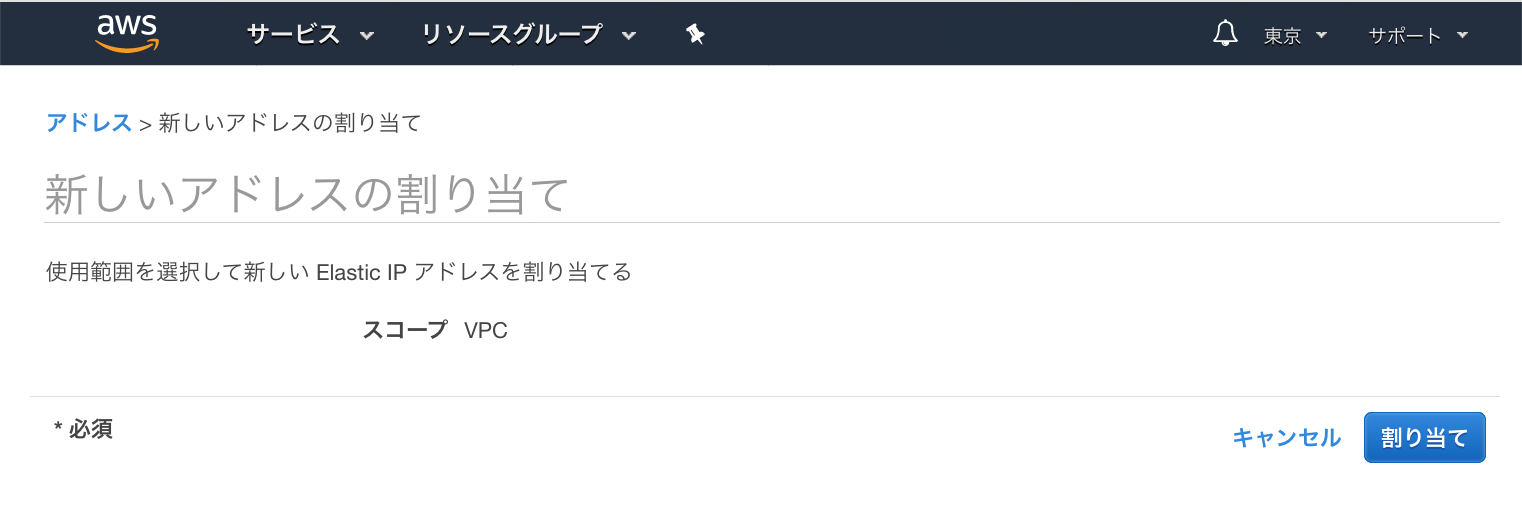
Public IPを作成し、Management Subnetのインターフェースeth0に設定します
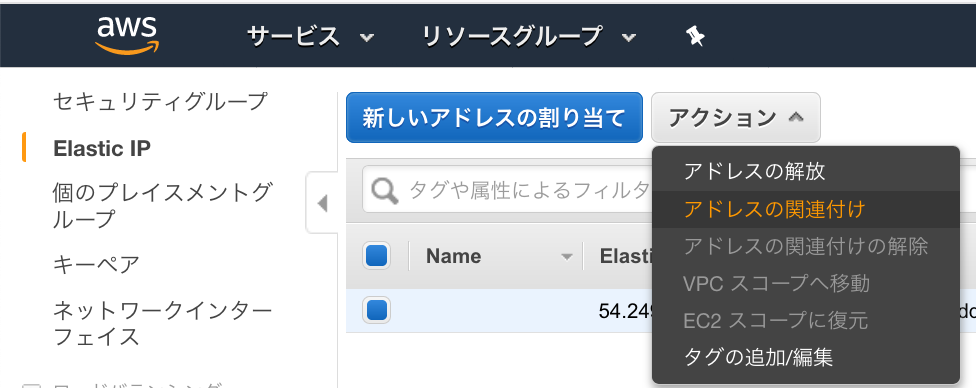
・Elastic IP 画面から、[新しいアドレスの割り当て]をクリック
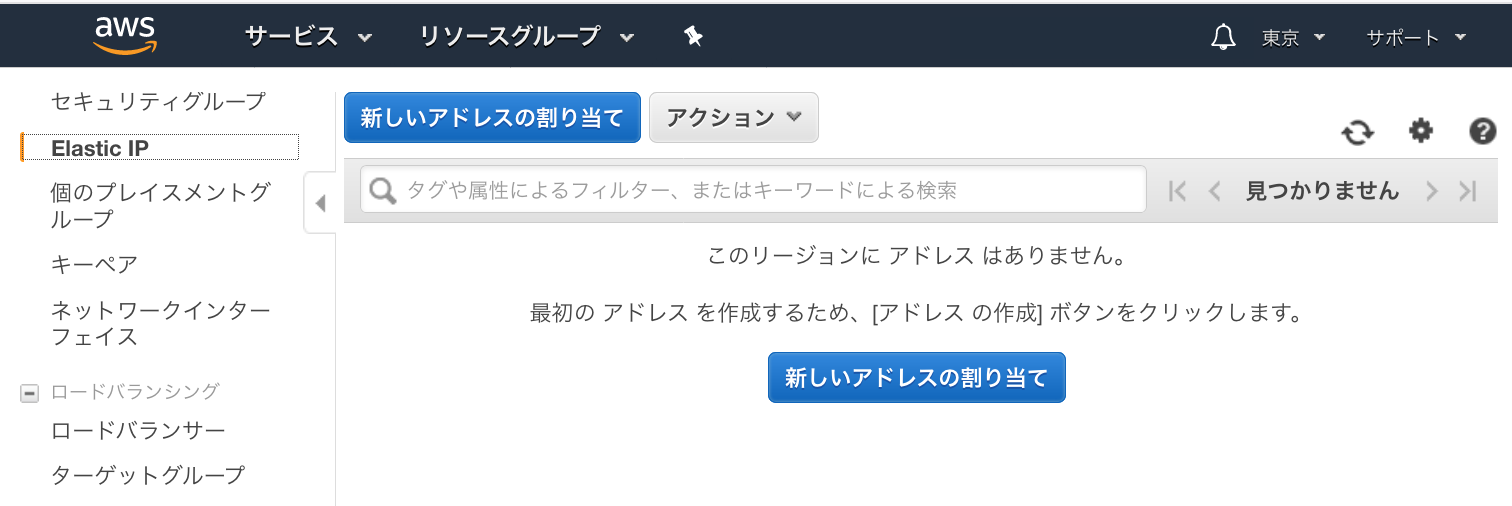
・割り当てられたPublic IPを確認し、[閉じる]をクリック
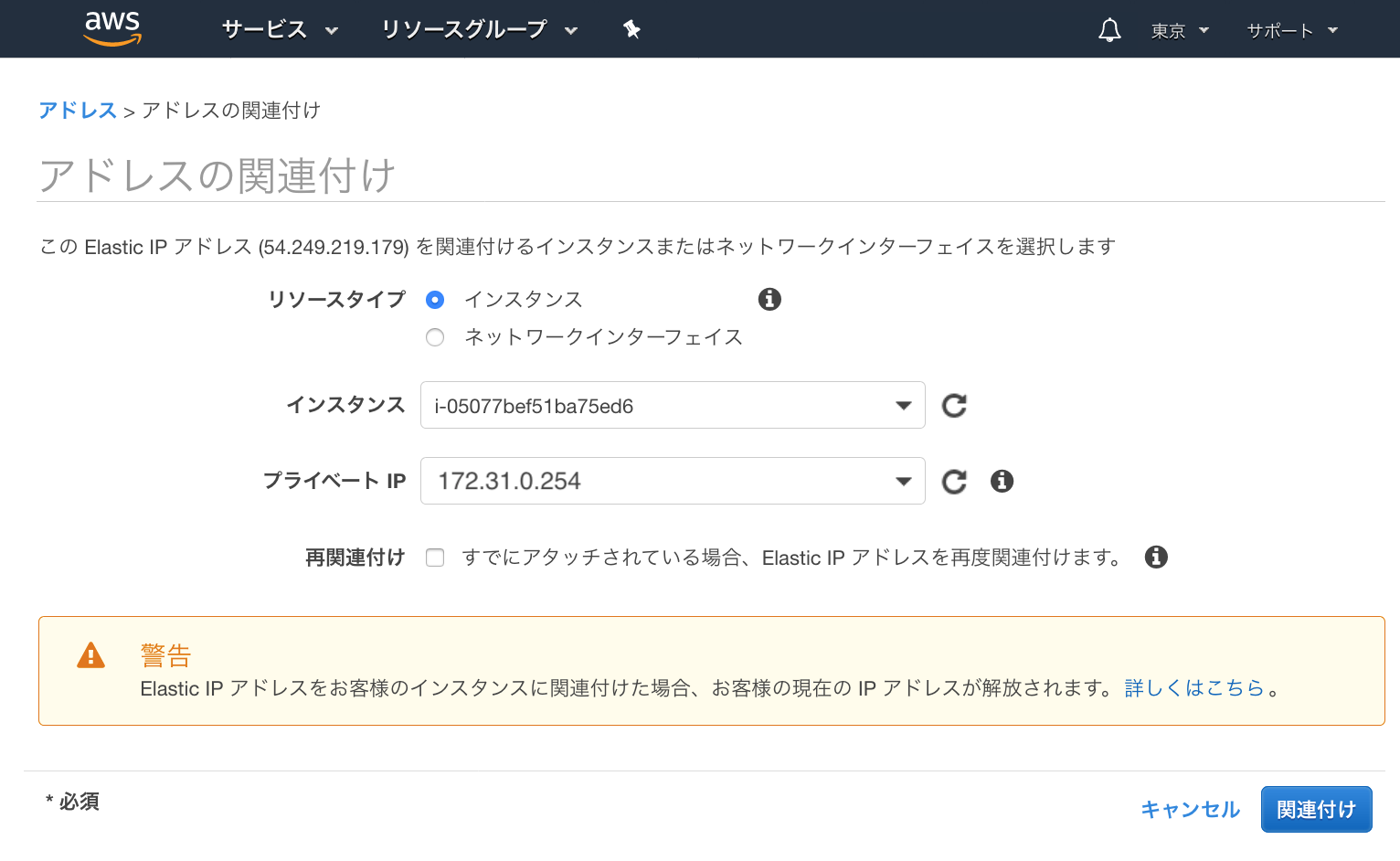
・作成したPublic IPを選択し、[関連付け]をクリック
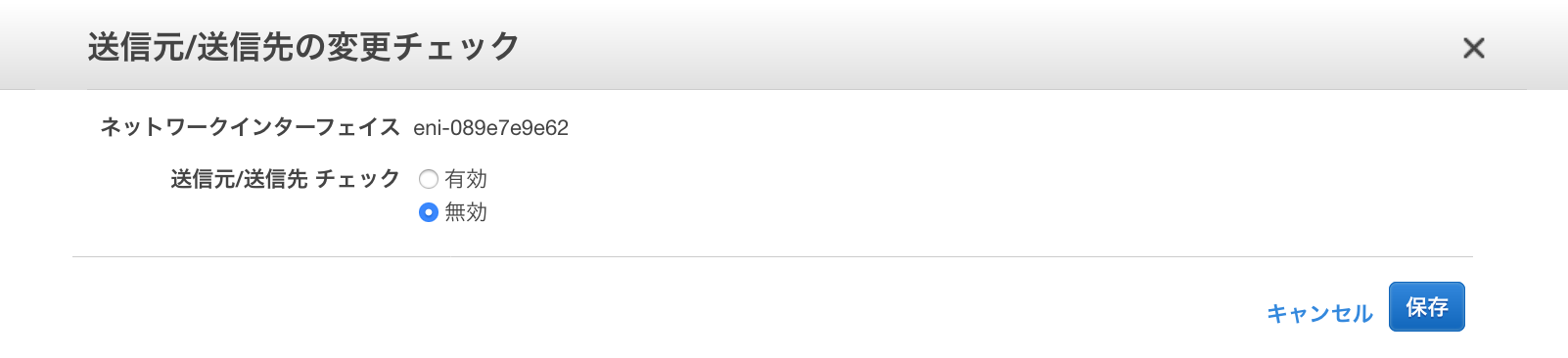
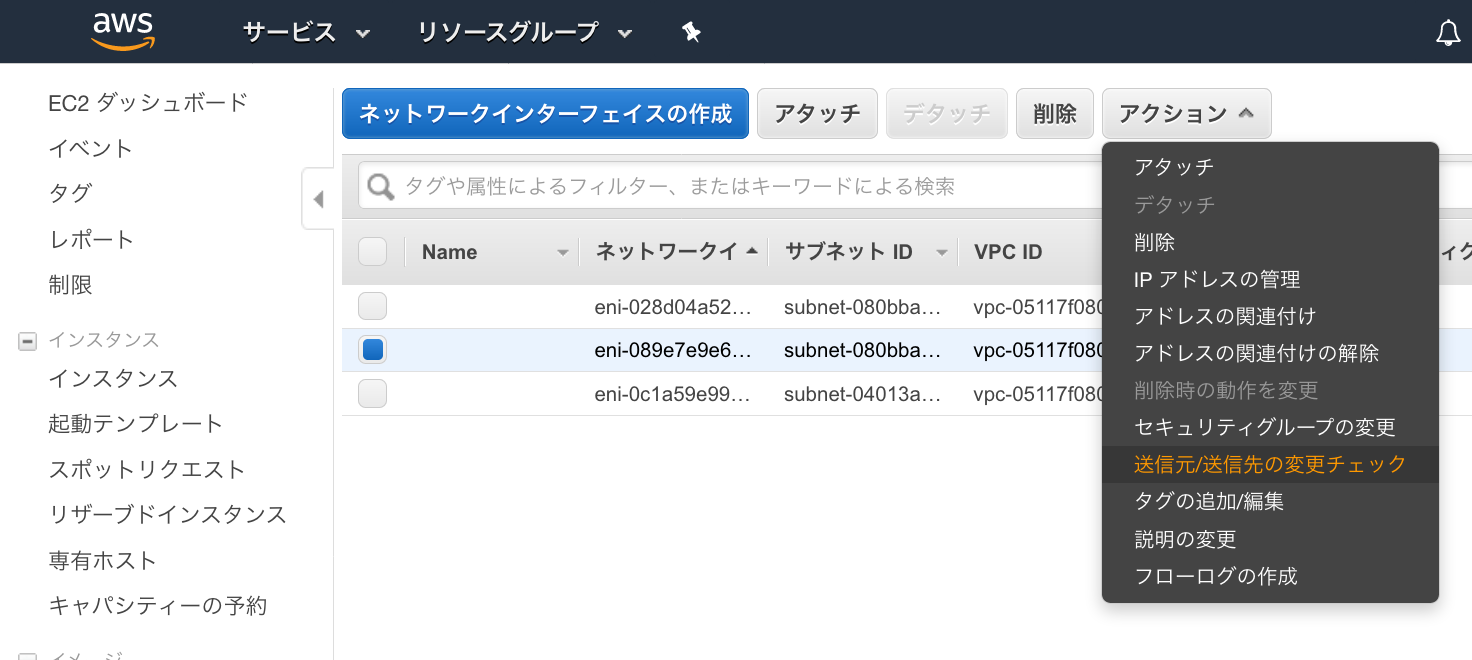
● ネットワークインターフェースの追加設定
eth0とeth1のネットワークインターフェースの送信元/送信先の変更チェックを無効にしてRutingできるようにします。
①ネットワークインターフェース画面の[送信元/送信先の変更チェック]をクリック
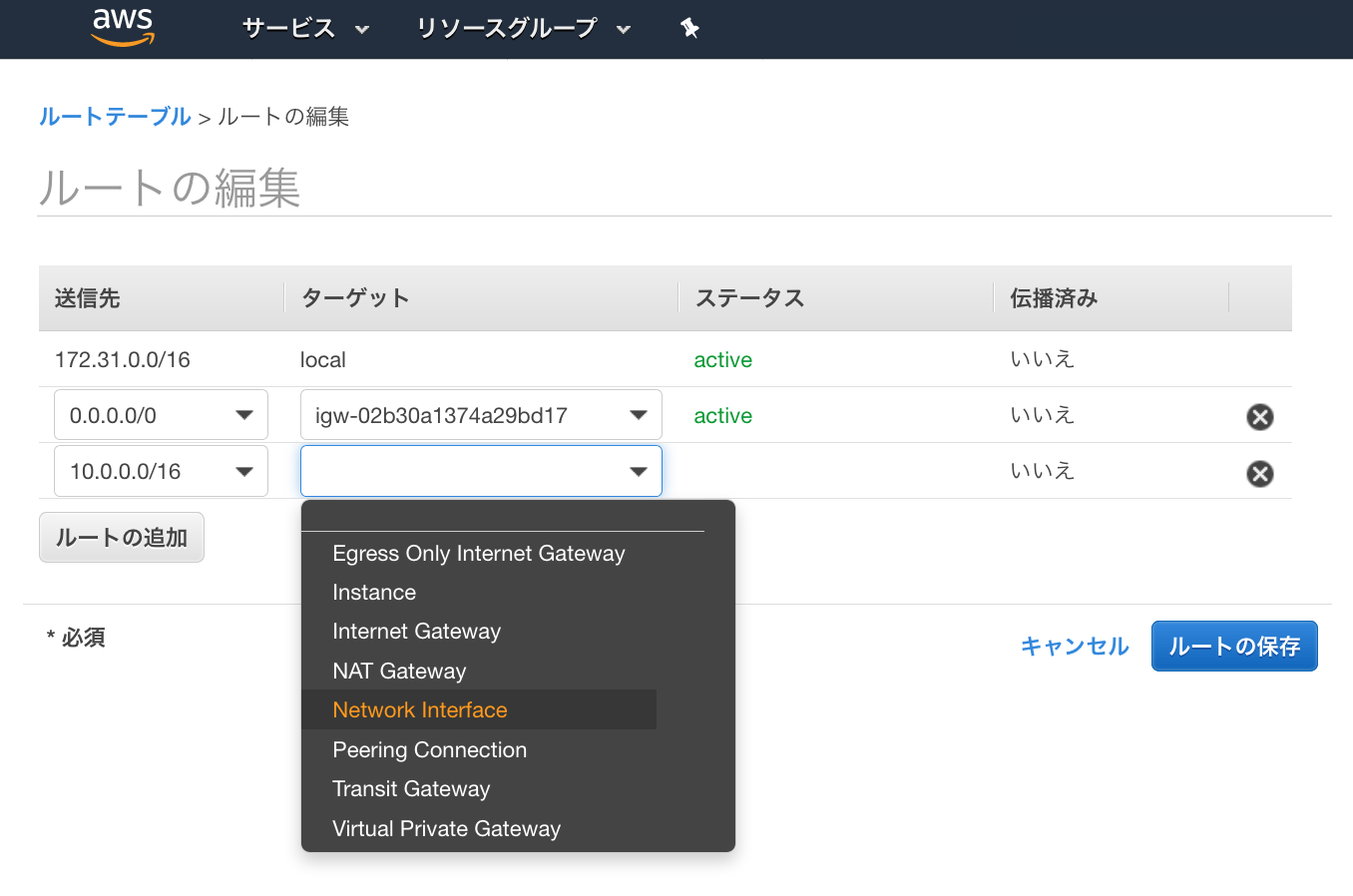
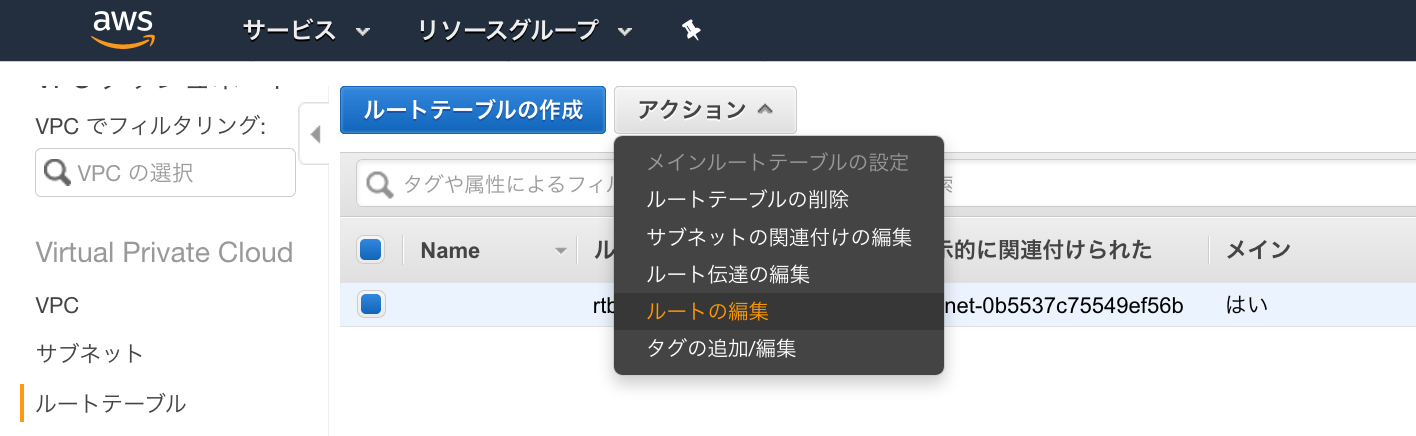
● ルートテーブルの編集
①対象ルートテーブルを選択し、[ルートテーブルの編集]をクリック
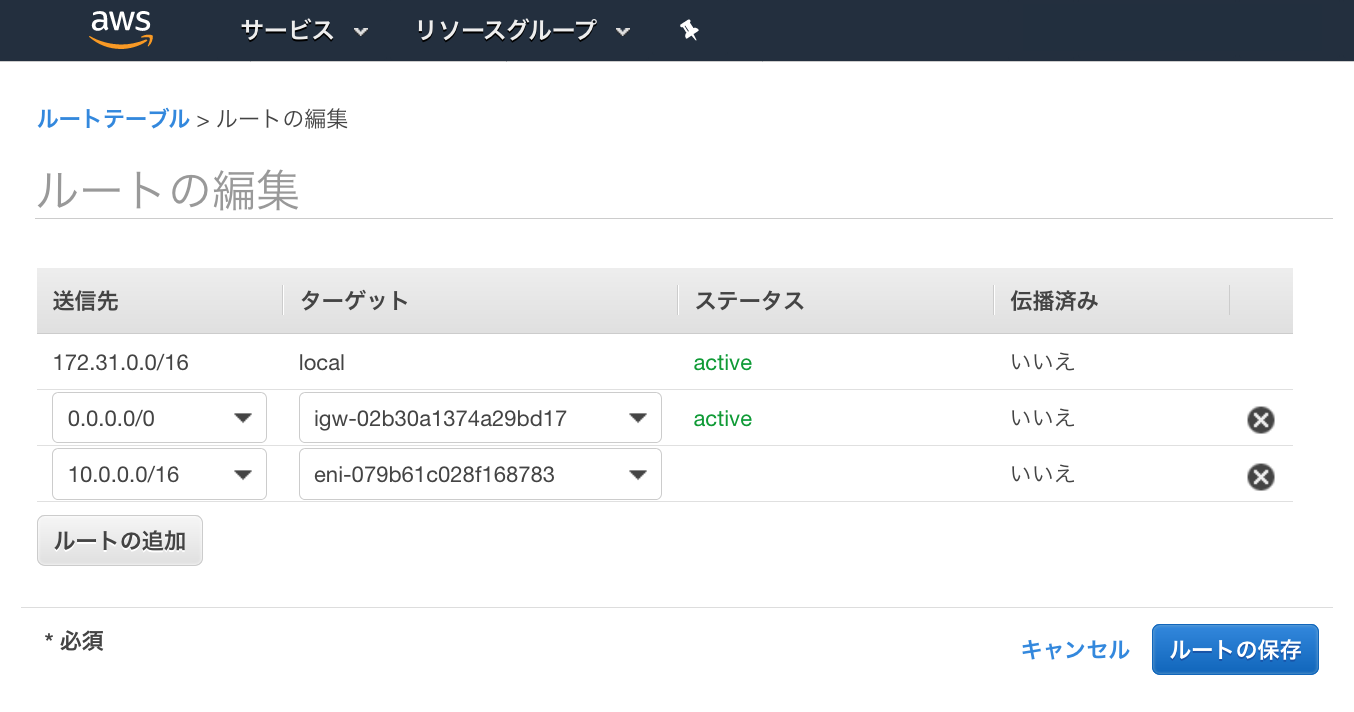
③ASAvのLAN Subnet側のインターフェースを選択し設定
■ ASAv初期設定
IPSec設定するまでの必要な設定を行います
●ASAvへssh接続
[ec2-user@ip-172-31-1-10 ~]$ ssh -i ASAv.pem admin@100.100.100.101
The authenticity of host '100.100.100.101 (100.100.100.101)' can't be established.
RSA key fingerprint is SHA256:q5DFmkA+UtEGvr0/LtdNUqIE.
RSA key fingerprint is MD5:dd:bb:be:ef:cf:64:ce:8d.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '100.100.100.101' (RSA) to the list of known hosts.
User admin logged in to ciscoasa
Logins over the last 1 days: 1.
Failed logins since the last login: 0.
Type help or '?' for a list of available commands.
ciscoasa>
●特権 EXEC モード開始
ASAvの設定するため、特権 EXEC モード開始
初期パスワードはNullなので、あとで変更します
ciscoasa> enable
Password:
ciscoasa# configure terminal
ciscoasa(config)#
●初期running-config確認
ciscoasa(config)# show running-config
: Saved
:
: Serial Number: TESTASAV910
: Hardware: ASAv, 4096 MB RAM, CPU Xeon E5 series 2900 MHz, 1 CPU (2 cores)
:
ASA Version 9.10(1)11
!
hostname ciscoasa
enable password ***** pbkdf2
names
no mac-address auto
!
interface GigabitEthernet0/0
shutdown
no nameif
security-level 0
ip address dhcp setroute
!
interface Management0/0
nameif management
security-level 100
ip address dhcp setroute
!
ftp mode passive
pager lines 23
mtu management 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 8192
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
no snmp-server location
no snmp-server contact
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpool policy
auto-import
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 0509
12d40vsi 41203230 f0wea7a0 02424d31 few09223 cmas39v9 23908sdv 123287b6
28sd7hv0 30090603 55040613 iropwefj 19301706 0355040a 13105175 6f566164
103v8v7v 696d6974 6564311b 30190603 55040313 1251756f 56616469 7320526f
cd9200u9 97718153 31a99ff6 qw90d8g8 e1a3931d cc8a265a 0938d0ce d70d8016
109vd8b8 874c8d8a a5d54697 f22c10b9 dseeiuvv 01506943 9ef4b2ef 6df8ecda
48d40vsi 30090603 55040313 02424d31 few09223 cmas39v9 23908sdv 123287b6
6564311b 30090603 55040613 iropwefj 19301706 0355040a 13105175 6f566164
6564311b 696d6974 6564311b 30190603 55040313 1251756f 56616469 7320526f
0355040a 97718153 31a99ff6 qw90d8g8 e1a3931d cc8a265a 0938d0ce d70d8016
0355040a 874c8d8a a5d54697 f22c10b9 dseeiuvv 01506943 9ef4b2ef 6df8ecda
cc8a265a df918f54 2a0b25c1 2619c452 230ev8b9 18r23c38 woqpfi9b
quit
telnet timeout 5
ssh stricthostkeycheck
ssh 0.0.0.0 0.0.0.0 management
ssh timeout 30
ssh version 1 2
ssh key-exchange group dh-group1-sha1
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
username admin privilege 15
username admin attributes
service-type admin
ssh authentication publickey 1a:de:80:4d:02:3c:32:b9:e5:bd:0f:ef hashed
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect ip-options
inspect netbios
inspect rtsp
inspect sunrpc
inspect tftp
inspect xdmcp
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect esmtp
inspect sqlnet
inspect sip
inspect skinny
policy-map type inspect dns migrated_dns_map_2
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
!
service-policy global_policy global
prompt hostname context
call-home
profile License
destination address http https://tools.cisco.com/~
destination transport-method http
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/~
destination address email asavtest@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:e39a65w4bdr9f68b7shy6b5d0e03
: end
● interface設定
追加した2つ目のLAN Subnet側のeth1interface(GigabitEthernet0/0)にはIPが設定されないため、次のコマンドで設定します
① GigabitEthernet0/0設定
ciscoasa(config)# interface GigabitEthernet0/0
ciscoasa(config)# security-level 100
ciscoasa(config)# ip address 172.31.1.254 255.255.255.0
ciscoasa(config)# no shutdown
② GigabitEthernet0/0設定確認
・IP確認
ciscoasa(config-pmap-c)# show ip
System IP Addresses:
Interface Name IP address Subnet mask Method
GigabitEthernet0/0 LAN 172.31.1.254 255.255.255.0 CONFIG
Management0/0 management 172.31.0.254 255.255.255.0 DHCP
Current IP Addresses:
Interface Name IP address Subnet mask Method
GigabitEthernet0/0 LAN 172.31.1.254 255.255.255.0 CONFIG
Management0/0 management 172.31.0.254 255.255.255.0 DHCP
・Interface確認
ciscoasa(config-pmap-c)# show nameif
Interface Name Security
GigabitEthernet0/0 LAN 100
Management0/0 management 100
・ACL設定(必要に応じて)
access-list 101 permit ip any any
access-group 101 in int management
access-group 101 in int LAN
●HTTPサーバ設定
必要に応じて設定
ciscoasa(config)# http server enable
ciscoasa(config)# http 0 0 management
●パスワード設定
ciscoasa(config)# enable password <Password>
ciscoasa(config)# username admin password <Password>
●設定保存
ciscoasa(config)# write memory
Building configuration...
Cryptochecksum: bec0c504 5d2a4283 321aa0e5 4efeced5
7311 bytes copied in 0.60 secs
[OK]
●HTTPサーバ(Cisco ASDM)接続確認
https:///admin/
にブラウザでアクセスして接続できることを確認
■OCI 設定
● Customer-Premises Equipment作成
OCIの[Networking] > [ICustomer-Premises Equipment] 画面から[Create Customer-Premises Equipmentn]をクリックし以下内容を設定
・NAME:適当な名前を設定
・DRG:IPsec接続させる作成済みのDRGを設定
・STATIC ROUTE CIDER:CPE側(ASAv)のCIDERを設定
・CPE IKE IDENTIFIER : ASAvのWAN側Private IPを設定

[Create Premises Equipment]をクリックして作成
●IPSec Connection作成
①OCIの[Networking] > [IPsec Connetion] 画面から[Create IPsec COnnection]をクリックし以下内容を設定
[Create IPsec Connection]をクリックして作成

②作成したIPsec ConnetionのVPN IP Addressを確認
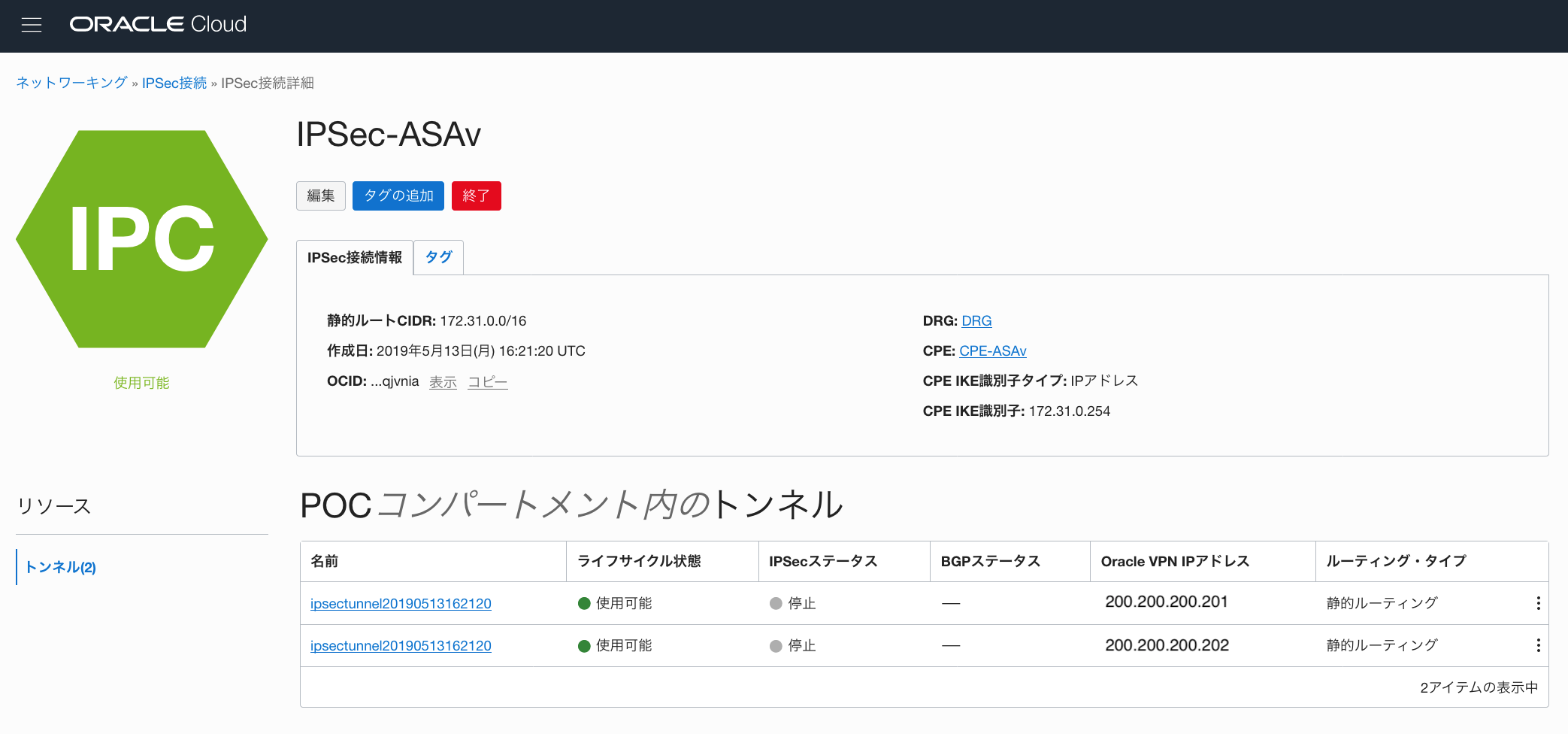
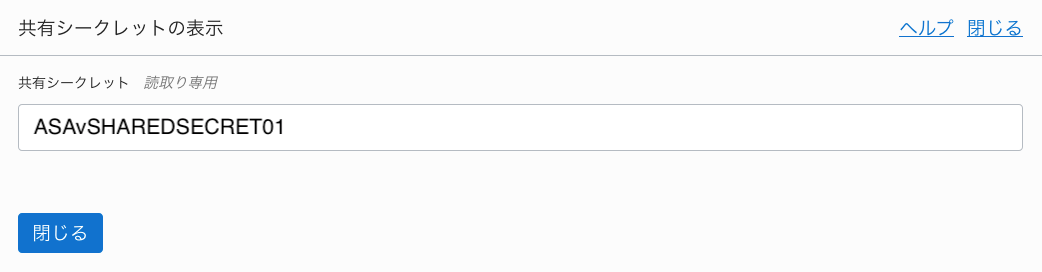
③作成したIPsec ConnetionのShared Secretを確認
・Tunnel1(200.200.200.201)のShared Secret
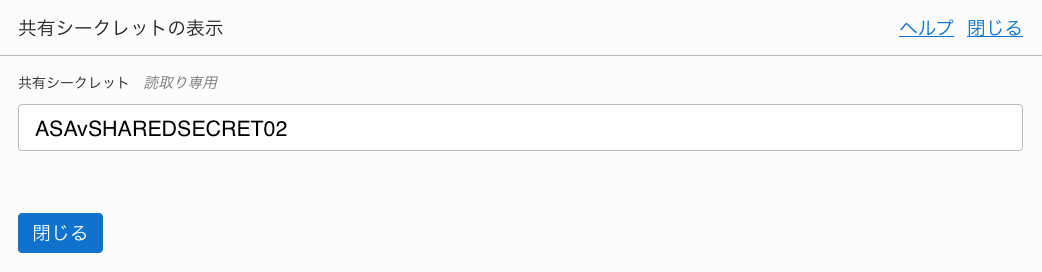
・Tunnel2(200.200.200.202)のShared Secret
■ ASAv IPsec設定
Cisco ASAバージョン9.7.1以降では、ルート・ベースの構成がサポートされているので、Route-Basedで設定します
● IPsec設定
以下内容を実行して設定
crypto ikev1 enable management
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 28800
crypto ipsec ikev1 transform-set oracle-vcn-transform esp-aes-256 esp-sha-hmac
crypto ipsec profile oracle-vcn-vpn-policy
set ikev1 transform-set oracle-vcn-transform
set pfs group5
set security-association lifetime seconds 3600
tunnel-group 200.200.200.201 type ipsec-l2l
tunnel-性 200.200.200.201 ipsec-attributes
ikev1 pre-shared-key ASAvSHAREDSECRET01
tunnel-group 200.200.200.202 type ipsec-l2l
tunnel-group 200.200.200.202 ipsec-attributes
ikev1 pre-shared-key ASAvSHAREDSECRET02
interface tunnel1
nameif ORACLE-VPN1
ip address 192.168.0.101 255.255.255.252
tunnel source interface management
tunnel destination 200.200.200.201
tunnel mode ipsec ipv4
tunnel protection ipsec profile oracle-vcn-vpn-policy
interface tunnel2
nameif ORACLE-VPN2
ip address 192.168.0.201 255.255.255.252
tunnel source interface management
tunnel destination 200.200.200.202
tunnel mode ipsec ipv4
tunnel protection ipsec profile oracle-vcn-vpn-policy
route ORACLE-VPN1 10.0.0.0 255.255.0.0 192.168.0.102 1 track 100
route ORACLE-VPN2 10.0.0.0 255.255.0.0 192.168.0.202 100
sla monitor 10
type echo protocol ipIcmpEcho 200.200.200.201 interface management
frequency 5
sla monitor schedule 10 life forever start-time now
track 1 rtr 10 reachability
● IPsec設定確認
・IPsec IKEフェーズ1確認
2つのIKE PeerのStateがMM_ACTIVEになっていればOK
ciscoasa(config)# show crypto isakmp sa
IKEv1 SAs:
Active SA: 2
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 2
1 IKE Peer: 200.200.200.202
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
2 IKE Peer: 200.200.200.201
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAs
・IPsec IKEフェーズ2確認
以下の「 X 」の値がカウントされていることを確認
# pkts encaps: X, #pkts encrypt: X, #pkts digest: X
# pkts decaps: X, #pkts decrypt: X, #pkts verify: X
### ・show crypto ipsec sa
ciscoasa(config)# show crypto ipsec sa
interface: ORACLE-VPN1
Crypto map tag: __vti-crypto-map-4-0-1, seq num: 65280, local addr: 172.31.0.254
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 200.200.200.202
#pkts encaps: 14, #pkts encrypt: 14, #pkts digest: 14
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 14, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 172.31.0.254/4500, remote crypto endpt.: 200.200.200.202/4500
path mtu 1500, ipsec overhead 82(52), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 6CEB899A
current inbound spi : 67C67143
inbound esp sas:
spi: 0x67C67143 (1741058371)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, NAT-T-Encaps, PFS Group 5, IKEv1, VTI, }
slot: 0, conn_id: 193, crypto-map: __vti-crypto-map-4-0-1
sa timing: remaining key lifetime (kB/sec): (4374000/3089)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0x6CEB899A (1827375514)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, NAT-T-Encaps, PFS Group 5, IKEv1, VTI, }
slot: 0, conn_id: 193, crypto-map: __vti-crypto-map-4-0-1
sa timing: remaining key lifetime (kB/sec): (4373998/3089)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
interface: ORACLE-VPN2
Crypto map tag: __vti-crypto-map-5-0-2, seq num: 65280, local addr: 172.31.0.254
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 200.200.200.201
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 172.31.0.254/4500, remote crypto endpt.: 200.200.200.201/4500
path mtu 1500, ipsec overhead 82(52), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 957EE5E5
current inbound spi : 9A0C3747
inbound esp sas:
spi: 0x9A0C3747 (2584491847)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, NAT-T-Encaps, PFS Group 5, IKEv1, VTI, }
slot: 0, conn_id: 199, crypto-map: __vti-crypto-map-5-0-2
sa timing: remaining key lifetime (kB/sec): (4374000/3489)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0x957EE5E5 (2508121573)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, NAT-T-Encaps, PFS Group 5, IKEv1, VTI, }
slot: 0, conn_id: 199, crypto-map: __vti-crypto-map-5-0-2
sa timing: remaining key lifetime (kB/sec): (4374000/3489)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
・アクティブ・セッション確認
ciscoasa(config)# show crypto engine connections active
・VTIインタフェース確認
ciscoasa(config)# show nameif
Interface Name Security
GigabitEthernet0/0 LAN 100
Management0/0 management 100
Tunnel1 ORACLE-VPN1 0
Tunnel2 ORACLE-VPN2 0
・VTIインタフェース IP確認
ciscoasa(config)# show ip
System IP Addresses:
Interface Name IP address Subnet mask Method
GigabitEthernet0/0 LAN 172.31.1.254 255.255.255.0 CONFIG
Management0/0 management 172.31.0.254 255.255.255.0 DHCP
Tunnel1 ORACLE-VPN1 169.254.101.1 255.255.255.252 manual
Tunnel2 ORACLE-VPN2 169.254.102.1 255.255.255.252 manual
Current IP Addresses:
Interface Name IP address Subnet mask Method
GigabitEthernet0/0 LAN 172.31.1.254 255.255.255.0 CONFIG
Management0/0 management 172.31.0.254 255.255.255.0 DHCP
Tunnel1 ORACLE-VPN1 169.254.101.1 255.255.255.252 manual
Tunnel2 ORACLE-VPN2 169.254.102.1 255.255.255.252 manual
● running-config確認
ciscoasa(config)# show running-config
: Saved
:
: Serial Number: TESTASAV910
: Hardware: ASAv, 4096 MB RAM, CPU Xeon E5 series 2900 MHz, 1 CPU (2 cores)
:
ASA Version 9.10(1)11
!
hostname ciscoasa
enable password ***** pbkdf2
passwd ***** encrypted
names
no mac-address auto
!
interface GigabitEthernet0/0
nameif LAN
security-level 100
ip address 172.31.1.254 255.255.255.0
!
interface Management0/0
nameif management
security-level 100
ip address dhcp setroute
!
interface Tunnel1
nameif ORACLE-VPN1
ip address 169.254.101.1 255.255.255.252
tunnel source interface management
tunnel destination 200.200.200.201
tunnel mode ipsec ipv4
tunnel protection ipsec profile oracle-vcn-vpn-policy
!
interface Tunnel2
nameif ORACLE-VPN2
ip address 169.254.102.1 255.255.255.252
tunnel source interface management
tunnel destination 200.200.200.202
tunnel mode ipsec ipv4
tunnel protection ipsec profile oracle-vcn-vpn-policy
!
ftp mode passive
pager lines 23
mtu management 1500
mtu LAN 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 8192
route ORACLE-VPN1 10.0.0.0 255.255.0.0 10.0.0.1 1 track 1
route ORACLE-VPN2 10.0.0.0 255.255.0.0 10.0.0.1 100
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
http server enable
http 0.0.0.0 0.0.0.0 management
no snmp-server location
no snmp-server contact
sla monitor 10
type echo protocol ipIcmpEcho 200.200.200.202 interface management
frequency 5
sla monitor schedule 10 life forever start-time now
crypto ipsec ikev1 transform-set oracle-vcn-transform esp-aes-256 esp-sha-hmac
crypto ipsec profile oracle-vcn-vpn-policy
set ikev1 transform-set oracle-vcn-transform
set pfs group5
set security-association lifetime seconds 3600
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpool policy
auto-import
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 0509
12d40vsi 41203230 f0wea7a0 02424d31 few09223 cmas39v9 23908sdv 123287b6
28sd7hv0 30090603 55040613 iropwefj 19301706 0355040a 13105175 6f566164
103v8v7v 696d6974 6564311b 30190603 55040313 1251756f 56616469 7320526f
cd9200u9 97718153 31a99ff6 qw90d8g8 e1a3931d cc8a265a 0938d0ce d70d8016
109vd8b8 874c8d8a a5d54697 f22c10b9 dseeiuvv 01506943 9ef4b2ef 6df8ecda
48d40vsi 30090603 55040313 02424d31 few09223 cmas39v9 23908sdv 123287b6
6564311b 30090603 55040613 iropwefj 19301706 0355040a 13105175 6f566164
6564311b 696d6974 6564311b 30190603 55040313 1251756f 56616469 7320526f
0355040a 97718153 31a99ff6 qw90d8g8 e1a3931d cc8a265a 0938d0ce d70d8016
0355040a 874c8d8a a5d54697 f22c10b9 dseeiuvv 01506943 9ef4b2ef 6df8ecda
cc8a265a df918f54 2a0b25c1 2619c452 230ev8b9 18r23c38 woqpfi9b
quit
crypto ikev1 enable management
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 28800
!
track 1 rtr 10 reachability
telnet timeout 5
ssh stricthostkeycheck
ssh 0.0.0.0 0.0.0.0 management
ssh timeout 30
ssh version 1 2
ssh key-exchange group dh-group1-sha1
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
username admin password ***** pbkdf2 privilege 15
username admin attributes
service-type admin
ssh authentication publickey 1a:de:80:85:4d:02:3c:32:b9:e5:bd:0f:ef hashed
tunnel-group 200.200.200.202 type ipsec-l2l
tunnel-group 200.200.200.202 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 200.200.200.201 type ipsec-l2l
tunnel-group 200.200.200.201 ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect ip-options
inspect netbios
inspect rtsp
inspect sunrpc
inspect tftp
inspect xdmcp
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect esmtp
inspect sqlnet
inspect sip
inspect skinny
policy-map type inspect dns migrated_dns_map_2
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
!
service-policy global_policy global
prompt hostname context
call-home reporting anonymous prompt 2
call-home
profile License
destination address http https://tools.cisco.com/~
destination transport-method http
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/~
destination address email asavtest@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:e39a65w4bdr9f68b7shy6b5d0e03
: end
■ OCI側IPSec動作確認
●IPSecステータスがUPしていることを確認

■IPSec接続疎通確認
● ping疎通確認
・AWS Instance -> OCI Instance
[root@ip-172-31-1-10 ~]# ping 10.0.0.2 -c 10
PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data.
64 bytes from 10.0.0.2: icmp_seq=1 ttl=63 time=4.34 ms
64 bytes from 10.0.0.2: icmp_seq=2 ttl=63 time=4.47 ms
64 bytes from 10.0.0.2: icmp_seq=3 ttl=63 time=4.50 ms
64 bytes from 10.0.0.2: icmp_seq=4 ttl=63 time=4.46 ms
64 bytes from 10.0.0.2: icmp_seq=5 ttl=63 time=4.40 ms
64 bytes from 10.0.0.2: icmp_seq=6 ttl=63 time=4.48 ms
64 bytes from 10.0.0.2: icmp_seq=7 ttl=63 time=5.12 ms
64 bytes from 10.0.0.2: icmp_seq=8 ttl=63 time=4.41 ms
64 bytes from 10.0.0.2: icmp_seq=9 ttl=63 time=4.10 ms
64 bytes from 10.0.0.2: icmp_seq=10 ttl=63 time=4.14 ms
--- 10.0.0.2 ping statistics ---
10 packets transmitted, 10 received, 0% packet loss, time 9014ms
rtt min/avg/max/mdev = 4.106/4.447/5.122/0.276 ms
・OCI Instance -> AWS Instance
[root@oci-inst01 ~]# ping 172.31.1.10 -c 10
PING 172.31.1.10 (172.31.1.10) 56(84) bytes of data.
64 bytes from 172.31.1.10: icmp_seq=1 ttl=254 time=4.07 ms
64 bytes from 172.31.1.10: icmp_seq=2 ttl=254 time=4.16 ms
64 bytes from 172.31.1.10: icmp_seq=3 ttl=254 time=4.02 ms
64 bytes from 172.31.1.10: icmp_seq=4 ttl=254 time=4.17 ms
64 bytes from 172.31.1.10: icmp_seq=5 ttl=254 time=4.33 ms
64 bytes from 172.31.1.10: icmp_seq=6 ttl=254 time=4.14 ms
64 bytes from 172.31.1.10: icmp_seq=7 ttl=254 time=4.31 ms
64 bytes from 172.31.1.10: icmp_seq=8 ttl=254 time=4.09 ms
64 bytes from 172.31.1.10: icmp_seq=9 ttl=254 time=10.3 ms
64 bytes from 172.31.1.10: icmp_seq=10 ttl=254 time=3.91 ms
--- 172.31.1.10 ping statistics ---
10 packets transmitted, 10 received, 0% packet loss, time 9011ms
rtt min/avg/max/mdev = 3.914/4.758/10.352/1.869 ms
● ssh接続確認
・OCI Instance -> AWS Instance
[opc@oci-inst01 ~]$ ssh -i ASAv.pem ec2-user@172.31.1.10 hostname
ec2-inst01
・AWS Instance -> OCI Instance
[ec2-user@ip-172-31-1-10 ~]$ ssh -i id_rsa opc@10.0.0.2 hostname
oci-inst01
■Appendix
●マニュアル
・Cisco 適応型セキュリティ仮想アプライア ンス(ASAv)クイック スタート ガイド
●White Paper
・[Deploying VPN IPsec Tunnels with Cisco ASA/ASAv VTI - Oracle Cloud]
(https://cloud.oracle.com/iaas/whitepapers/deploy_vpn_ipsec_on_oci_asa_with_vti_11.pdf)