初めに
どうも、クソ雑魚のなんちゃてエンジニアです。
本記事は CyberDefenders (以下リンク参考)の「DumpMe」にチャレンジした際のWriteupになります
※本チャレンジについてはRed側のペネトレというよりはBlue側の分析力を問われるものになります。
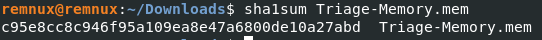
What is the SHA1 hash of Triage-Memory.mem (memory dump)?
Ans: C95E8CC8C946F95A109EA8E47A6800DE10A27ABD
What volatility profile is the most appropriate for this machine? (ex: Win10x86_14393)
imageinfoを見ます。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem imageinfo
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/remnux/Downloads/Triage-Memory.mem)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf800029f80a0L
Number of Processors : 2
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff800029f9d00L
KPCR for CPU 1 : 0xfffff880009ee000L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2019-03-22 05:46:00 UTC+0000
Image local date and time : 2019-03-22 01:46:00 -0400
回答文字数制限で2択くらいで絞れます。
Ans: Win7SP1x64
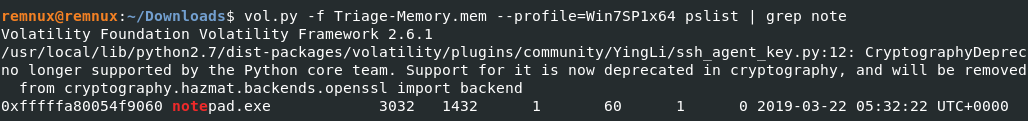
What was the process ID of notepad.exe?
Ans: 3032
Name the child process of wscript.exe.
pstreeで確認します。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 pstree
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Name Pid PPid Thds Hnds Time
-------------------------------------------------- ------ ------ ------ ------ ----
0xfffffa8003de39c0:explorer.exe 1432 1308 28 976 2019-03-22 05:32:07 UTC+0000
. 0xfffffa80042aa430:cmd.exe 1408 1432 1 23 2019-03-22 05:34:12 UTC+0000
. 0xfffffa8005d067d0:StikyNot.exe 1628 1432 8 183 2019-03-22 05:34:42 UTC+0000
. 0xfffffa80042dbb30:chrome.exe 3248 1432 32 841 2019-03-22 05:35:14 UTC+0000
.. 0xfffffa8005442b30:chrome.exe 4232 3248 14 233 2019-03-22 05:35:17 UTC+0000
.. 0xfffffa80047beb30:chrome.exe 3244 3248 7 91 2019-03-22 05:35:15 UTC+0000
.. 0xfffffa80053306f0:chrome.exe 1816 3248 14 328 2019-03-22 05:35:16 UTC+0000
.. 0xfffffa8005300b30:chrome.exe 4156 3248 14 216 2019-03-22 05:35:17 UTC+0000
.. 0xfffffa8005419b30:chrome.exe 4240 3248 14 215 2019-03-22 05:35:17 UTC+0000
.. 0xfffffa800540db30:chrome.exe 4520 3248 10 234 2019-03-22 05:35:18 UTC+0000
.. 0xfffffa80052f0060:chrome.exe 2100 3248 2 59 2019-03-22 05:35:15 UTC+0000
.. 0xfffffa80053cbb30:chrome.exe 4688 3248 13 168 2019-03-22 05:35:19 UTC+0000
. 0xfffffa800474c060:OUTLOOK.EXE 3688 1432 30 2023 2019-03-22 05:34:37 UTC+0000
. 0xfffffa8004798320:calc.exe 3548 1432 3 77 2019-03-22 05:34:43 UTC+0000
. 0xfffffa80053d3060:POWERPNT.EXE 4048 1432 23 765 2019-03-22 05:35:09 UTC+0000
. 0xfffffa8004905620:hfs.exe 3952 1432 6 214 2019-03-22 05:34:51 UTC+0000
.. 0xfffffa8005a80060:wscript.exe 5116 3952 8 312 2019-03-22 05:35:32 UTC+0000
... 0xfffffa8005a1d9e0:UWkpjFjDzM.exe 3496 5116 5 109 2019-03-22 05:35:33 UTC+0000
.... 0xfffffa8005bb0060:cmd.exe 4660 3496 1 33 2019-03-22 05:35:36 UTC+0000
. 0xfffffa80054f9060:notepad.exe 3032 1432 1 60 2019-03-22 05:32:22 UTC+0000
. 0xfffffa8005b49890:vmtoolsd.exe 1828 1432 6 144 2019-03-22 05:32:10 UTC+0000
. 0xfffffa800474fb30:taskmgr.exe 3792 1432 6 134 2019-03-22 05:34:38 UTC+0000
. 0xfffffa80053f83e0:EXCEL.EXE 1272 1432 21 789 2019-03-22 05:33:49 UTC+0000
. 0xfffffa8004083880:FTK Imager.exe 3192 1432 6 353 2019-03-22 05:35:12 UTC+0000
0xfffffa8003c72b30:System 4 0 87 547 2019-03-22 05:31:55 UTC+0000
. 0xfffffa8004616040:smss.exe 252 4 2 30 2019-03-22 05:31:55 UTC+0000
0xfffffa80050546b0:csrss.exe 332 324 10 516 2019-03-22 05:31:58 UTC+0000
0xfffffa8005259060:wininit.exe 380 324 3 78 2019-03-22 05:31:58 UTC+0000
. 0xfffffa8005680910:services.exe 476 380 12 224 2019-03-22 05:31:59 UTC+0000
.. 0xfffffa8005409060:dllhost.exe 2072 476 13 194 2019-03-22 05:32:14 UTC+0000
.. 0xfffffa80055b0060:wmpnetwk.exe 2628 476 9 210 2019-03-22 05:32:18 UTC+0000
.. 0xfffffa800583db30:svchost.exe 1028 476 19 307 2019-03-22 05:32:05 UTC+0000
.. 0xfffffa8005775b30:svchost.exe 796 476 15 368 2019-03-22 05:32:03 UTC+0000
... 0xfffffa80059e6890:dwm.exe 1344 796 3 88 2019-03-22 05:32:07 UTC+0000
.. 0xfffffa8005508650:SearchIndexer. 2456 476 13 766 2019-03-22 05:32:17 UTC+0000
.. 0xfffffa80057beb30:svchost.exe 932 476 10 568 2019-03-22 05:32:03 UTC+0000
.. 0xfffffa800432f060:svchost.exe 3300 476 13 346 2019-03-22 05:34:15 UTC+0000
.. 0xfffffa8005478060:msdtc.exe 2188 476 12 146 2019-03-22 05:32:15 UTC+0000
.. 0xfffffa800577db30:svchost.exe 820 476 33 1073 2019-03-22 05:32:03 UTC+0000
... 0xfffffa80059cc620:taskeng.exe 1292 820 4 83 2019-03-22 05:32:07 UTC+0000
... 0xfffffa8004300620:taskeng.exe 1156 820 4 93 2019-03-22 05:34:14 UTC+0000
.. 0xfffffa80059cb7c0:taskhost.exe 1276 476 8 183 2019-03-22 05:32:07 UTC+0000
.. 0xfffffa8005b4eb30:vmtoolsd.exe 1852 476 10 314 2019-03-22 05:32:11 UTC+0000
.. 0xfffffa800570d060:svchost.exe 672 476 7 341 2019-03-22 05:32:02 UTC+0000
.. 0xfffffa8005a324e0:FileZilla Serv 1476 476 9 81 2019-03-22 05:32:07 UTC+0000
.. 0xfffffa8005c4ab30:svchost.exe 2888 476 11 152 2019-03-22 05:32:20 UTC+0000
.. 0xfffffa8005ba0620:ManagementAgen 1932 476 10 102 2019-03-22 05:32:11 UTC+0000
.. 0xfffffa80056e1060:svchost.exe 592 476 9 375 2019-03-22 05:32:01 UTC+0000
... 0xfffffa80054d2380:WmiPrvSE.exe 2196 592 11 222 2019-03-22 05:32:15 UTC+0000
... 0xfffffa8005c8e440:WmiPrvSE.exe 2436 592 9 245 2019-03-22 05:32:33 UTC+0000
... 0xfffffa80047cb060:iexplore.exe 3576 592 12 403 2019-03-22 05:34:48 UTC+0000
.... 0xfffffa80047e9540:iexplore.exe 2780 3576 6 233 2019-03-22 05:34:48 UTC+0000
.. 0xfffffa8005850a30:spoolsv.exe 864 476 12 279 2019-03-22 05:32:04 UTC+0000
.. 0xfffffa80057e4560:svchost.exe 232 476 15 410 2019-03-22 05:32:03 UTC+0000
.. 0xfffffa80058ed390:OfficeClickToR 1136 476 23 631 2019-03-22 05:32:05 UTC+0000
.. 0xfffffa8005af24e0:VGAuthService. 1768 476 3 89 2019-03-22 05:32:09 UTC+0000
.. 0xfffffa8004330b30:sppsvc.exe 3260 476 4 149 2019-03-22 05:34:15 UTC+0000
.. 0xfffffa800575e5b0:svchost.exe 764 476 20 447 2019-03-22 05:32:02 UTC+0000
. 0xfffffa80056885e0:lsass.exe 484 380 7 650 2019-03-22 05:32:00 UTC+0000
. 0xfffffa8005696b30:lsm.exe 492 380 10 155 2019-03-22 05:32:00 UTC+0000
0xfffffa8005268b30:winlogon.exe 416 364 3 110 2019-03-22 05:31:58 UTC+0000
0xfffffa800525a9e0:csrss.exe 372 364 11 557 2019-03-22 05:31:58 UTC+0000
. 0xfffffa80042ab620:conhost.exe 1008 372 2 55 2019-03-22 05:34:12 UTC+0000
. 0xfffffa8005c1ab30:conhost.exe 4656 372 2 49 2019-03-22 05:35:36 UTC+0000
0xfffffa8005be12c0:FileZilla Serv 1996 1860 3 99 2019-03-22 05:32:12 UTC+0000
Ans: UWkpjFjDzM.exe
What was the IP address of the machine at the time the RAM dump was created?
netscanを確認します。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 netscan
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Offset(P) Proto Local Address Foreign Address State Pid Owner Created
0x13e057300 UDPv4 10.0.0.101:55736 *:* 2888 svchost.exe 2019-03-22 05:32:20 UTC+0000
0x13e05b4f0 UDPv6 ::1:55735 *:* 2888 svchost.exe 2019-03-22 05:32:20 UTC+0000
0x13e05b790 UDPv6 fe80::7475:ef30:be18:7807:55734 *:* 2888 svchost.exe 2019-03-22 05:32:20 UTC+0000
0x13e05d4b0 UDPv6 fe80::7475:ef30:be18:7807:1900 *:* 2888 svchost.exe 2019-03-22 05:32:20 UTC+0000
0x13e05dec0 UDPv4 127.0.0.1:55737 *:* 2888 svchost.exe 2019-03-22 05:32:20 UTC+0000
0x13e05e3f0 UDPv4 10.0.0.101:1900 *:* 2888 svchost.exe 2019-03-22 05:32:20 UTC+0000
0x13e05eab0 UDPv6 ::1:1900 *:* 2888 svchost.exe 2019-03-22 05:32:20 UTC+0000
0x13e064d70 UDPv4 127.0.0.1:1900 *:* 2888 svchost.exe 2019-03-22 05:32:20 UTC+0000
0x13e02bcf0 TCPv4 -:49220 72.51.60.132:443 CLOSED 4048 POWERPNT.EXE
0x13e035790 TCPv4 -:49223 72.51.60.132:443 CLOSED 4048 POWERPNT.EXE
0x13e036470 TCPv4 -:49224 72.51.60.132:443 CLOSED 4048 POWERPNT.EXE
0x13e258010 UDPv4 127.0.0.1:55560 *:* 5116 wscript.exe 2019-03-22 05:35:32 UTC+0000
0x13e305a50 UDPv4 0.0.0.0:5355 *:* 232 svchost.exe 2019-03-22 05:32:09 UTC+0000
0x13e360be0 UDPv4 0.0.0.0:63790 *:* 504 2019-03-22 05:45:47 UTC+0000
0x13e490ec0 UDPv4 0.0.0.0:5355 *:* 232 svchost.exe 2019-03-22 05:32:09 UTC+0000
0x13e490ec0 UDPv6 :::5355 *:* 232 svchost.exe 2019-03-22 05:32:09 UTC+0000
0x13e5683e0 UDPv4 10.0.0.101:137 *:* 4 System 2019-03-22 05:32:06 UTC+0000
0x13e594250 UDPv4 10.0.0.101:138 *:* 4 System 2019-03-22 05:32:06 UTC+0000
0x13e597ec0 UDPv4 0.0.0.0:0 *:* 232 svchost.exe 2019-03-22 05:32:06 UTC+0000
0x13e597ec0 UDPv6 :::0 *:* 232 svchost.exe 2019-03-22 05:32:06 UTC+0000
0x13e61fb30 UDPv6 fe80::7475:ef30:be18:7807:546 *:* 764 svchost.exe 2019-03-22 05:46:23 UTC+0000
0x13e918010 UDPv4 0.0.0.0:56372 *:* 1816 chrome.exe 2019-03-22 05:45:51 UTC+0000
0x13e9cd730 UDPv4 127.0.0.1:57374 *:* 1136 OfficeClickToR 2019-03-22 05:32:18 UTC+0000
0x13ea8e6a0 UDPv4 127.0.0.1:61704 *:* 3688 OUTLOOK.EXE 2019-03-22 05:34:44 UTC+0000
0x13ead0bf0 UDPv4 127.0.0.1:55614 *:* 4048 POWERPNT.EXE 2019-03-22 05:35:15 UTC+0000
0x13ebc6c20 UDPv4 0.0.0.0:5353 *:* 3248 chrome.exe 2019-03-22 05:35:17 UTC+0000
0x13ebea890 UDPv4 0.0.0.0:5353 *:* 3248 chrome.exe 2019-03-22 05:35:17 UTC+0000
0x13ebea890 UDPv6 :::5353 *:* 3248 chrome.exe 2019-03-22 05:35:17 UTC+0000
0x13e2c6b10 TCPv4 0.0.0.0:21 0.0.0.0:0 LISTENING 1476 FileZilla Serv
0x13e2c6b10 TCPv6 :::21 :::0 LISTENING 1476 FileZilla Serv
0x13e2c7850 TCPv6 ::1:14147 :::0 LISTENING 1476 FileZilla Serv
0x13e2c96b0 TCPv4 127.0.0.1:14147 0.0.0.0:0 LISTENING 1476 FileZilla Serv
0x13e2c9be0 TCPv4 0.0.0.0:21 0.0.0.0:0 LISTENING 1476 FileZilla Serv
0x13e3a1150 TCPv4 0.0.0.0:49155 0.0.0.0:0 LISTENING 484 lsass.exe
0x13e3a1150 TCPv6 :::49155 :::0 LISTENING 484 lsass.exe
0x13e3b2010 TCPv4 0.0.0.0:49155 0.0.0.0:0 LISTENING 484 lsass.exe
0x13e430580 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 820 svchost.exe
0x13e430580 TCPv6 :::49154 :::0 LISTENING 820 svchost.exe
0x13e431820 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 820 svchost.exe
0x13e57e010 TCPv4 10.0.0.101:139 0.0.0.0:0 LISTENING 4 System
0x13e71cef0 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 672 svchost.exe
0x13e720660 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 672 svchost.exe
0x13e720660 TCPv6 :::135 :::0 LISTENING 672 svchost.exe
0x13e72f010 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 380 wininit.exe
0x13e72f6e0 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 380 wininit.exe
0x13e72f6e0 TCPv6 :::49152 :::0 LISTENING 380 wininit.exe
0x13e770240 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 764 svchost.exe
0x13e772980 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 764 svchost.exe
0x13e772980 TCPv6 :::49153 :::0 LISTENING 764 svchost.exe
0x13ebb3010 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 476 services.exe
0x13ebb3010 TCPv6 :::49156 :::0 LISTENING 476 services.exe
0x13ebcdef0 TCPv4 0.0.0.0:80 0.0.0.0:0 LISTENING 3952 hfs.exe
0x13e2348a0 TCPv4 -:49366 192.168.206.181:389 CLOSED 504
0x13e397190 TCPv4 10.0.0.101:49217 10.0.0.106:4444 ESTABLISHED 3496 UWkpjFjDzM.exe
0x13e3986d0 TCPv4 -:49378 213.209.1.129:25 CLOSED 504
0x13e3abae0 TCPv4 -:49226 72.51.60.132:443 CLOSED 4048 POWERPNT.EXE
0x13e3e7010 TCPv6 -:0 38db:7705:80fa:ffff:38db:7705:80fa:ffff:0 CLOSED 1136 OfficeClickToR
0x13e441830 TCPv6 -:0 382b:c703:80fa:ffff:382b:c703:80fa:ffff:0 CLOSED 1 ?RK????
0x13e4e4910 TCPv4 10.0.0.101:49208 52.109.12.6:443 CLOSED 504
0x13e55fae0 TCPv4 10.0.0.101:49209 52.96.44.162:443 CLOSED 504
0x13e71b540 TCPv4 -:0 104.208.112.5:0 CLOSED 1 ?RK????
0x13e73b560 TCPv4 -:49266 35.190.69.156:443 CLOSED 504
0x13e7c6010 TCPv4 10.0.0.101:49204 172.217.6.195:443 CLOSED 1816 chrome.exe
0x13ead7cf0 TCPv4 10.0.0.101:49202 172.217.10.68:443 CLOSED 1816 chrome.exe
0x13f5898a0 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 476 services.exe
0x13f5899c0 TCPv4 0.0.0.0:445 0.0.0.0:0 LISTENING 4 System
0x13f5899c0 TCPv6 :::445 :::0 LISTENING 4 System
0x13f4facf0 TCPv4 10.0.0.101:49262 52.109.12.6:443 ESTABLISHED 3688 OUTLOOK.EXE
0x13f50a010 TCPv4 -:49265 213.186.33.3:443 CLOSED 504
0x13f5289f0 TCPv4 -:49234 72.51.60.133:80 CLOSED 3688 OUTLOOK.EXE
0x13f7b4ec0 UDPv4 0.0.0.0:55707 *:* 232 svchost.exe 2019-03-22 05:45:44 UTC+0000
0x13f7e8670 UDPv4 127.0.0.1:59411 *:* 3576 iexplore.exe 2019-03-22 05:34:49 UTC+0000
0x13fc6f1b0 UDPv4 0.0.0.0:55102 *:* 232 svchost.exe 2019-03-22 05:45:36 UTC+0000
0x13fc78dc0 UDPv4 127.0.0.1:53361 *:* 1272 EXCEL.EXE 2019-03-22 05:34:03 UTC+0000
0x13f7ae010 TCPv4 10.0.0.101:49263 52.96.44.162:443 ESTABLISHED 3688 OUTLOOK.EXE
0x13fa93cf0 TCPv4 -:49173 72.51.60.132:443 CLOSED 1272 EXCEL.EXE
0x13fa95cf0 TCPv4 -:49170 72.51.60.132:443 CLOSED 1272 EXCEL.EXE
0x13fa969f0 TCPv4 -:0 56.219.119.5:0 CLOSED 1272 EXCEL.EXE
0x13fbd07e0 TCPv4 -:49372 212.227.15.9:25 CLOSED 504
0x13fc857e0 TCPv4 -:49167 72.51.60.132:443 CLOSED 1272 EXCEL.EXE
remnux@remnux:~/Downloads$
パット見わかると思います。
Ans: 10.0.0.101
Based on the answer regarding the infected PID, can you determine the IP of the attacker?
malfindで悪意のあるProcessを見つけます。(おそらくさっきのUWkpjFjDzM.exeなんでしょうが)
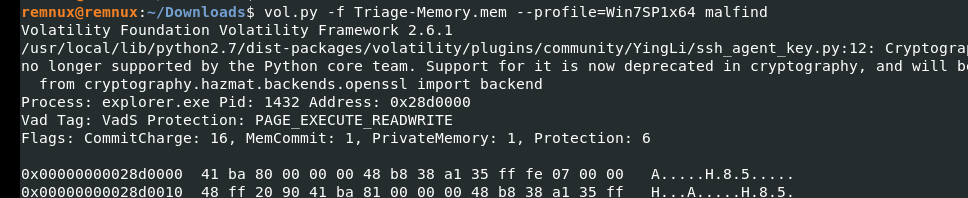

予想通りですね。此奴のProcessが3496なのでそれで先ほどのnetscanにgrepかけます。
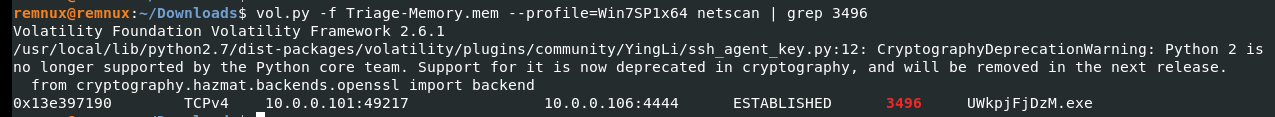
Ans: 10.0.0.106
How many processes are associated with VCRUNTIME140.dll?
dlllistを確認します。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 dlllist | grep VCRUNTIME140.dll
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
0x000007fefa5c0000 0x16000 0xffff 2019-03-22 05:32:05 UTC+0000 C:\Program Files\Common Files\Microsoft Shared\ClickToRun\VCRUNTIME140.dll
0x00000000745f0000 0x15000 0xffff 2019-03-22 05:33:49 UTC+0000 C:\Program Files (x86)\Microsoft Office\root\Office16\VCRUNTIME140.dll
0x00000000745f0000 0x15000 0xffff 2019-03-22 05:34:37 UTC+0000 C:\Program Files (x86)\Microsoft Office\root\Office16\VCRUNTIME140.dll
0x00000000745f0000 0x15000 0x3 2019-03-22 05:34:49 UTC+0000 C:\Program Files (x86)\Microsoft Office\root\Office16\VCRUNTIME140.dll
0x00000000745f0000 0x15000 0xffff 2019-03-22 05:35:09 UTC+0000 C:\Program Files (x86)\Microsoft Office\root\Office16\VCRUNTIME140.dll
Ans: 5
After dumping the infected process, what is its md5 hash?
memdumpでダンプを取ります。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 memdump -p 3496 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
************************************************************************
Writing UWkpjFjDzM.exe [ 3496] to 3496.dmp
remnux@remnux:~/Downloads$
ハッシュを確認します。
remnux@remnux:~/Downloads/out$ md5sum 3496.dmp
6654c0ab83bb8fa9cb64c9078c9c8468 3496.dmp
あれ?違う?あ、メモリじゃなくてProcessだったわ。memdumpで直接何やられたか見ること多いのでProcessをvolで取ることあまりなかったので...
さっきのmemdumpをprocdumpに変更して取ります。その後にハッシュ確認。

Ans: 690ea20bc3bdfb328e23005d9a80c290
What is the LM hash of Bob's account?
hashdumpを確認します。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 hashdump
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Bob:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Ans: aad3b435b51404eeaad3b435b51404ee
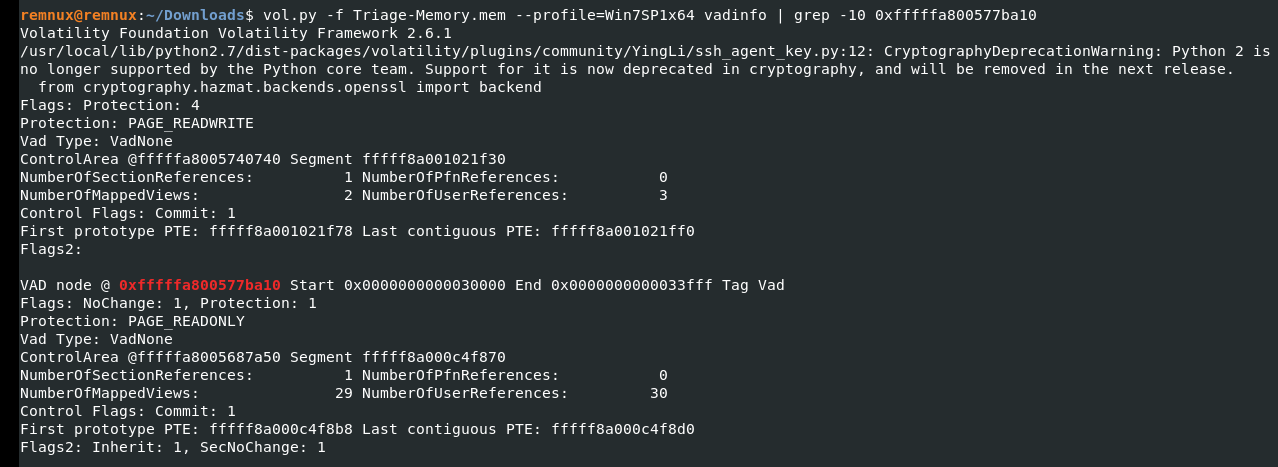
What memory protection constants does the VAD node at 0xfffffa800577ba10 have?
vadinfoを見ます。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 vadinfo | grep -10 0xfffffa800577ba10
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Flags: Protection: 4
Protection: PAGE_READWRITE
Vad Type: VadNone
ControlArea @fffffa8005740740 Segment fffff8a001021f30
NumberOfSectionReferences: 1 NumberOfPfnReferences: 0
NumberOfMappedViews: 2 NumberOfUserReferences: 3
Control Flags: Commit: 1
First prototype PTE: fffff8a001021f78 Last contiguous PTE: fffff8a001021ff0
Flags2:
VAD node @ 0xfffffa800577ba10 Start 0x0000000000030000 End 0x0000000000033fff Tag Vad
Flags: NoChange: 1, Protection: 1
Protection: PAGE_READONLY
Vad Type: VadNone
ControlArea @fffffa8005687a50 Segment fffff8a000c4f870
NumberOfSectionReferences: 1 NumberOfPfnReferences: 0
NumberOfMappedViews: 29 NumberOfUserReferences: 30
Control Flags: Commit: 1
First prototype PTE: fffff8a000c4f8b8 Last contiguous PTE: fffff8a000c4f8d0
Flags2: Inherit: 1, SecNoChange: 1
Ans: PAGE_READONLY
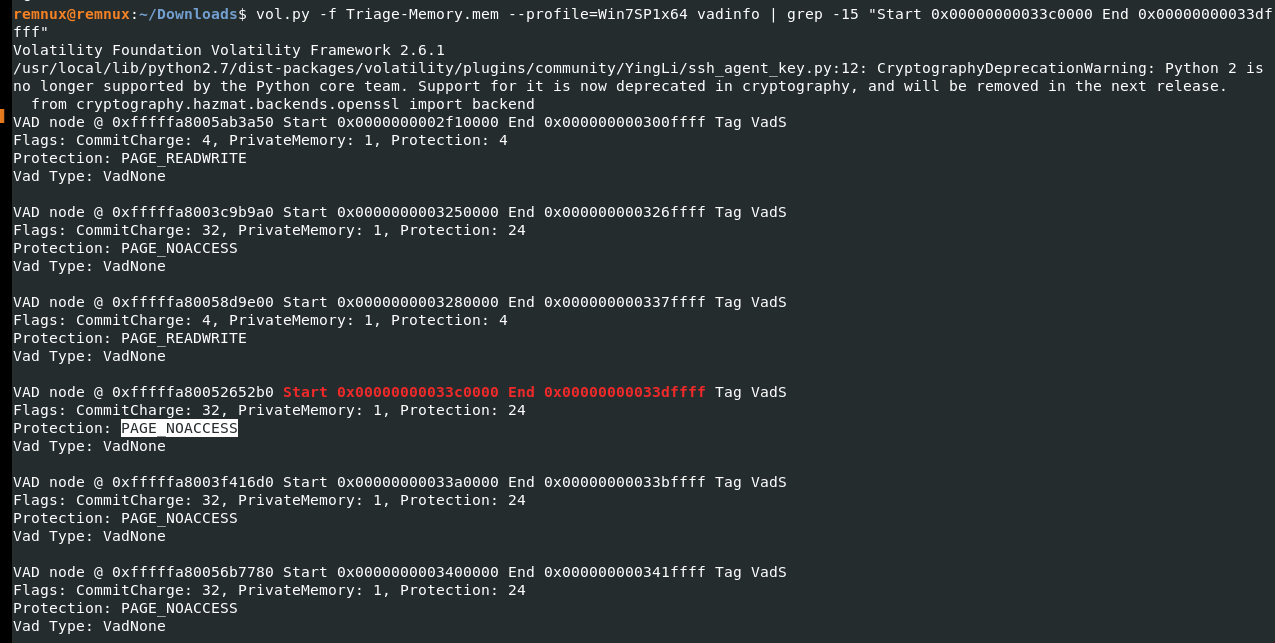
What memory protection did the VAD starting at 0x00000000033c0000 and ending at 0x00000000033dffff have?
上記と同じくですね。grepのかけ方に気を付けるだけ。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 vadinfo | grep -15 "Start 0x00000000033c0000 End 0x00000000033dffff"
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
VAD node @ 0xfffffa8005ab3a50 Start 0x0000000002f10000 End 0x000000000300ffff Tag VadS
Flags: CommitCharge: 4, PrivateMemory: 1, Protection: 4
Protection: PAGE_READWRITE
Vad Type: VadNone
VAD node @ 0xfffffa8003c9b9a0 Start 0x0000000003250000 End 0x000000000326ffff Tag VadS
Flags: CommitCharge: 32, PrivateMemory: 1, Protection: 24
Protection: PAGE_NOACCESS
Vad Type: VadNone
VAD node @ 0xfffffa80058d9e00 Start 0x0000000003280000 End 0x000000000337ffff Tag VadS
Flags: CommitCharge: 4, PrivateMemory: 1, Protection: 4
Protection: PAGE_READWRITE
Vad Type: VadNone
VAD node @ 0xfffffa80052652b0 Start 0x00000000033c0000 End 0x00000000033dffff Tag VadS
Flags: CommitCharge: 32, PrivateMemory: 1, Protection: 24
Protection: PAGE_NOACCESS
Vad Type: VadNone
VAD node @ 0xfffffa8003f416d0 Start 0x00000000033a0000 End 0x00000000033bffff Tag VadS
Flags: CommitCharge: 32, PrivateMemory: 1, Protection: 24
Protection: PAGE_NOACCESS
Vad Type: VadNone
VAD node @ 0xfffffa80056b7780 Start 0x0000000003400000 End 0x000000000341ffff Tag VadS
Flags: CommitCharge: 32, PrivateMemory: 1, Protection: 24
Protection: PAGE_NOACCESS
Vad Type: VadNone
VAD node @ 0xfffffa80045e5850 Start 0x00000000033e0000 End 0x00000000033fffff Tag VadS
Ans: PAGE_NOACCESS
There was a VBS script that ran on the machine. What is the name of the script? (submit without file extension)
cmdlistで発見できます。cmdscanと同様によく使うコマンドですね。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 cmdline
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
************************************************************************
System pid: 4
************************************************************************
smss.exe pid: 252
Command line : \SystemRoot\System32\smss.exe
************************************************************************
csrss.exe pid: 332
Command line : %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16
************************************************************************
csrss.exe pid: 372
Command line : %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16
************************************************************************
wininit.exe pid: 380
Command line : wininit.exe
************************************************************************
winlogon.exe pid: 416
Command line : winlogon.exe
************************************************************************
services.exe pid: 476
Command line : C:\Windows\system32\services.exe
************************************************************************
lsass.exe pid: 484
Command line : C:\Windows\system32\lsass.exe
************************************************************************
lsm.exe pid: 492
Command line : C:\Windows\system32\lsm.exe
************************************************************************
svchost.exe pid: 592
Command line : C:\Windows\system32\svchost.exe -k DcomLaunch
************************************************************************
svchost.exe pid: 672
Command line : C:\Windows\system32\svchost.exe -k RPCSS
************************************************************************
svchost.exe pid: 764
Command line : C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted
************************************************************************
svchost.exe pid: 796
Command line : C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted
************************************************************************
svchost.exe pid: 820
Command line : C:\Windows\system32\svchost.exe -k netsvcs
************************************************************************
svchost.exe pid: 932
Command line : C:\Windows\system32\svchost.exe -k LocalService
************************************************************************
svchost.exe pid: 232
Command line : C:\Windows\system32\svchost.exe -k NetworkService
************************************************************************
spoolsv.exe pid: 864
Command line : C:\Windows\System32\spoolsv.exe
************************************************************************
svchost.exe pid: 1028
Command line : C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork
************************************************************************
OfficeClickToR pid: 1136
Command line : "C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe" /service
************************************************************************
taskhost.exe pid: 1276
Command line : "taskhost.exe"
************************************************************************
taskeng.exe pid: 1292
Command line : taskeng.exe {E9F45B18-C0E3-42EE-9422-2FAB865F5A64}
************************************************************************
dwm.exe pid: 1344
Command line : "C:\Windows\system32\Dwm.exe"
************************************************************************
explorer.exe pid: 1432
Command line : C:\Windows\Explorer.EXE
************************************************************************
FileZilla Serv pid: 1476
Command line : "C:\Program Files (x86)\FileZilla Server\FileZilla Server.exe"
************************************************************************
VGAuthService. pid: 1768
Command line : "C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe"
************************************************************************
vmtoolsd.exe pid: 1828
Command line : "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr
************************************************************************
vmtoolsd.exe pid: 1852
Command line : "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe"
************************************************************************
ManagementAgen pid: 1932
Command line : "C:\Program Files\VMware\VMware Tools\VMware CAF\pme\bin\ManagementAgentHost.exe"
************************************************************************
FileZilla Serv pid: 1996
Command line : "C:\Program Files (x86)\FileZilla Server\FileZilla Server Interface.exe"
************************************************************************
dllhost.exe pid: 2072
Command line : C:\Windows\system32\dllhost.exe /Processid:{02D4B3F1-FD88-11D1-960D-00805FC79235}
************************************************************************
msdtc.exe pid: 2188
Command line : C:\Windows\System32\msdtc.exe
************************************************************************
WmiPrvSE.exe pid: 2196
Command line : C:\Windows\system32\wbem\wmiprvse.exe
************************************************************************
SearchIndexer. pid: 2456
Command line : C:\Windows\system32\SearchIndexer.exe /Embedding
************************************************************************
wmpnetwk.exe pid: 2628
Command line : "C:\Program Files\Windows Media Player\wmpnetwk.exe"
************************************************************************
svchost.exe pid: 2888
Command line : C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersonation
************************************************************************
notepad.exe pid: 3032
Command line : "C:\Windows\system32\notepad.exe"
************************************************************************
WmiPrvSE.exe pid: 2436
Command line : C:\Windows\system32\wbem\wmiprvse.exe
************************************************************************
EXCEL.EXE pid: 1272
Command line : "C:\Program Files (x86)\Microsoft Office\root\Office16\EXCEL.EXE"
************************************************************************
cmd.exe pid: 1408
Command line : "C:\Windows\System32\cmd.exe"
************************************************************************
conhost.exe pid: 1008
Command line : \??\C:\Windows\system32\conhost.exe "-3665641233614004741886043129-1340869214-8780857402033447618-1868066120-1609534987
************************************************************************
taskeng.exe pid: 1156
Command line : taskeng.exe {7F35D633-1462-41D2-B75C-0C83793D50AF}
************************************************************************
sppsvc.exe pid: 3260
Command line : C:\Windows\system32\sppsvc.exe
************************************************************************
svchost.exe pid: 3300
Command line : C:\Windows\System32\svchost.exe -k secsvcs
************************************************************************
OUTLOOK.EXE pid: 3688
Command line : "C:\Program Files (x86)\Microsoft Office\root\Office16\OUTLOOK.EXE"
************************************************************************
taskmgr.exe pid: 3792
Command line : "C:\Windows\system32\taskmgr.exe" /4
************************************************************************
StikyNot.exe pid: 1628
Command line : "C:\Windows\system32\StikyNot.exe"
************************************************************************
calc.exe pid: 3548
Command line : "C:\Windows\system32\calc.exe"
************************************************************************
iexplore.exe pid: 3576
Command line : "C:\Program Files (x86)\Internet Explorer\iexplore.exe" -Embedding
************************************************************************
iexplore.exe pid: 2780
Command line : "C:\Program Files (x86)\Internet Explorer\iexplore.exe" SCODEF:3576 CREDAT:79873
************************************************************************
hfs.exe pid: 3952
Command line : "C:\Users\Bob\Desktop\hfs.exe"
************************************************************************
POWERPNT.EXE pid: 4048
Command line : "C:\Program Files (x86)\Microsoft Office\root\Office16\POWERPNT.EXE"
************************************************************************
FTK Imager.exe pid: 3192
Command line : "C:\Program Files\AccessData\FTK Imager\FTK Imager.exe"
************************************************************************
chrome.exe pid: 3248
Command line : "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe"
************************************************************************
chrome.exe pid: 3244
Command line :
************************************************************************
chrome.exe pid: 2100
Command line : "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3272 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6
************************************************************************
chrome.exe pid: 1816
Command line : "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=924,2132560186875629139,18153288653831290455,131072 --lang=en-US --service-sandbox-type=network --service-request-channel-token=3848528183961585196 --mojo-platform-channel-handle=1320 /prefetch:8
************************************************************************
chrome.exe pid: 4156
Command line : "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,2132560186875629139,18153288653831290455,131072 --service-pipe-token=5128242365178584495 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=1 --service-request-channel-token=5128242365178584495 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2268 /prefetch:1
************************************************************************
chrome.exe pid: 4232
Command line : "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,2132560186875629139,18153288653831290455,131072 --service-pipe-token=16174022435611898554 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=1 --service-request-channel-token=16174022435611898554 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2528 /prefetch:1
************************************************************************
chrome.exe pid: 4240
Command line : "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,2132560186875629139,18153288653831290455,131072 --service-pipe-token=6187966837059053897 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=1 --service-request-channel-token=6187966837059053897 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2536 /prefetch:1
************************************************************************
chrome.exe pid: 4520
Command line :
************************************************************************
chrome.exe pid: 4688
Command line : "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,2132560186875629139,18153288653831290455,131072 --disable-gpu-compositing --service-pipe-token=2094820586012107996 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=1 --service-request-channel-token=2094820586012107996 --renderer-client-id=13 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3844 /prefetch:1
************************************************************************
wscript.exe pid: 5116
Command line : "C:\Windows\System32\wscript.exe" //B //NOLOGO %TEMP%\vhjReUDEuumrX.vbs
************************************************************************
UWkpjFjDzM.exe pid: 3496
Command line : "C:\Users\Bob\AppData\Local\Temp\rad93398.tmp\UWkpjFjDzM.exe"
************************************************************************
cmd.exe pid: 4660
Command line : C:\Windows\system32\cmd.exe
************************************************************************
conhost.exe pid: 4656
Command line : \??\C:\Windows\system32\conhost.exe "-2105419398-1914772985-1870609020-898984210-362940684623073995-430731961-49370805
Ans: vhjReUDEuumrX
An application was run at 2019-03-07 23:06:58 UTC. What is the name of the program? (Include extension)
shimcacheで確認します。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 shimcache
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Last Modified Path
------------------------------ ----
2019-02-09 18:22:52 UTC+0000 \??\C:\Program Files (x86)\Google\Update\GoogleUpdate.exe
2019-02-09 18:22:52 UTC+0000 \??\C:\Program Files (x86)\Google\Update\1.3.33.23\GoogleCrashHandler64.exe
2019-02-09 18:22:52 UTC+0000 \??\C:\Program Files (x86)\Google\Update\1.3.33.23\GoogleCrashHandler.exe
2009-07-14 01:39:37 UTC+0000 \??\C:\Windows\system32\SearchProtocolHost.exe
2009-07-14 01:39:46 UTC+0000 \??\C:\Windows\system32\svchost.exe
...省略
Ans: Skype.exe
What was written in notepad.exe at the time when the memory dump was captured?
3032のmemdumpを取ります。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 memdump -p 3032 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
************************************************************************
Writing notepad.exe [ 3032] to 3032.dmp
Ans: flag<REDBULL_IS_LIFE>
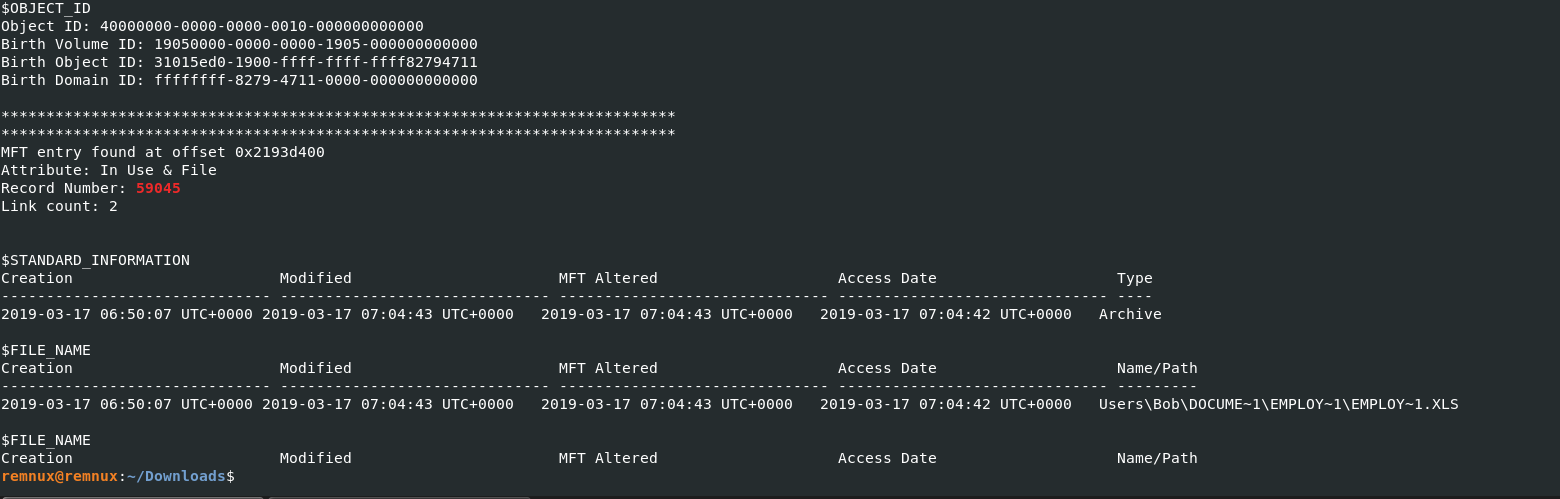
What is the short name of the file at file record 59045?
mftparserで確認します。
remnux@remnux:~/Downloads$ vol.py -f Triage-Memory.mem --profile=Win7SP1x64 mftparser | grep -15 59045
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
2019-03-21 17:11:21 UTC+0000 2019-03-21 17:11:21 UTC+0000 2019-03-21 17:11:21 UTC+0000 2019-03-21 17:11:21 UTC+0000 Archive & Content not indexed
$FILE_NAME
Creation Modified MFT Altered Access Date Name/Path
------------------------------ ------------------------------ ------------------------------ ------------------------------ ---------
2019-03-21 17:11:21 UTC+0000 2019-03-21 17:11:21 UTC+0000 2019-03-21 17:11:21 UTC+0000 2019-03-21 17:11:21 UTC+0000 Users\Bob\AppData\Local\Google\Chrome\USERDA~1\CERTIF~2\1067\_PLATF~1\all\sths\A577AC~1.STH
$FILE_NAME
Creation Modified MFT Altered Access Date Name/Path
------------------------------ ------------------------------ ------------------------------ ------------------------------ ---------
2019-03-21 17:11:21 UTC+0000 2019-03-21 17:11:21 UTC+0000 2019-03-21 17:11:21 UTC+0000 2019-03-21 17:11:21 UTC+0000 Users\Bob\AppData\Local\Google\Chrome\USERDA~1\CERTIF~2\1067\_PLATF~1\all\sths\a577ac9ced7548dd8f025b67a241089df86e0f476ec203c2ecbedb185f282638.sth
$DATA
0000000000: 7b 22 74 72 65 65 5f 73 69 7a 65 22 3a 35 33 30 {"tree_size":530
0000000010: 35 30 2c 22 74 69 6d 65 73 74 61 6d 70 22 3a 31 50,"timestamp":1
0000000020: 35 35 33 31 36 30 39 35 39 30 34 35 2c 22 73 68 553160959045,"sh
0000000030: 61 32 35 36 5f 72 6f 6f 74 5f 68 61 73 68 22 3a a256_root_hash":
0000000040: 22 53 33 42 2f 45 6f 55 38 4a 33 76 57 61 56 6d "S3B/EoU8J3vWaVm
0000000050: 51 61 36 30 2b 47 53 62 67 67 4c 70 46 68 49 47 Qa60+GSbggLpFhIG
0000000060: 38 7a 36 6c 6f 56 79 49 35 39 53 30 3d 22 2c 22 8z6loVyI59S0=","
0000000070: 74 72 65 65 5f 68 65 61 64 5f 73 69 67 6e 61 74 tree_head_signat
0000000080: 75 72 65 22 3a 22 42 41 45 42 41 45 64 61 79 49 ure":"BAEBAEdayI
0000000090: 6a 58 6f 39 45 43 77 52 2b 36 71 74 71 50 43 43 jXo9ECwR+6qtqPCC
00000000a0: 37 71 35 59 42 37 35 2b 6d 31 32 56 63 63 4c 52 7q5YB75+m12VccLR
00000000b0: 73 7a 78 68 48 52 2b 72 33 38 66 48 6a 67 38 76 szxhHR+r38fHjg8v
00000000c0: 57 78 42 2f 66 31 59 44 31 75 55 45 46 54 31 62 WxB/f1YD1uUEFT1b
00000000d0: 68 38 79 33 53 41 59 6e 61 71 57 77 6f 55 46 49 h8y3SAYnaqWwoUFI
00000000e0: 76 38 63 71 44 76 78 2b 50 79 67 71 6a 76 68 42 v8cqDvx+PygqjvhB
00000000f0: 6e 5a 45 57 31 33 6d 44 76 30 2b 6a 42 6d 35 59 nZEW13mDv0+jBm5Y
0000000100: 43 68 59 36 55 4d 4b 4f 49 64 52 35 54 4d 31 35 ChY6UMKOIdR5TM15
0000000110: 72 4a 41 54 37 41 56 79 78 69 31 46 2f 36 51 36 rJAT7AVyxi1F/6Q6
--
2019-03-08 03:05:02 UTC+0000 2019-03-08 03:05:02 UTC+0000 2019-03-08 03:05:02 UTC+0000 2019-03-08 03:05:02 UTC+0000 Users\Bob\AppData\Local\Google\Chrome\USERDA~1\SAFEBR~1\CertCsdDownloadWhitelist.store
$DATA
$OBJECT_ID
Object ID: 40000000-0000-0000-0010-000000000000
Birth Volume ID: 19050000-0000-0000-1905-000000000000
Birth Object ID: 31015ed0-1900-ffff-ffff-ffff82794711
Birth Domain ID: ffffffff-8279-4711-0000-000000000000
***************************************************************************
***************************************************************************
MFT entry found at offset 0x2193d400
Attribute: In Use & File
Record Number: 59045
Link count: 2
$STANDARD_INFORMATION
Creation Modified MFT Altered Access Date Type
------------------------------ ------------------------------ ------------------------------ ------------------------------ ----
2019-03-17 06:50:07 UTC+0000 2019-03-17 07:04:43 UTC+0000 2019-03-17 07:04:43 UTC+0000 2019-03-17 07:04:42 UTC+0000 Archive
$FILE_NAME
Creation Modified MFT Altered Access Date Name/Path
------------------------------ ------------------------------ ------------------------------ ------------------------------ ---------
2019-03-17 06:50:07 UTC+0000 2019-03-17 07:04:43 UTC+0000 2019-03-17 07:04:43 UTC+0000 2019-03-17 07:04:42 UTC+0000 Users\Bob\DOCUME~1\EMPLOY~1\EMPLOY~1.XLS
$FILE_NAME
Creation Modified MFT Altered Access Date Name/Path
Ans: EMPLOY~1.XLS
This box was exploited and is running meterpreter. What was the infected PID?
今までの流れからあのEXEファイルでしょう。中身を見てもこのようになってますし。
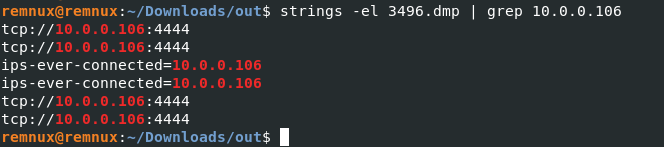
Ans: 3496
最後に
volatility2のよい復習になります。
MFT忘れてた。。。