初めに
どうも、クソ雑魚のなんちゃてエンジニアです。
本記事は CyberDefenders (以下リンク参考)の「MrRobot」にチャレンジした際のWriteupになります。
※本チャレンジについてはRed側のペネトレというよりはBlue側の分析力を問われるものになります。
Machine:Target1
What email address tricked the front desk employee into installing a security update?
とりあえず此奴のOS Profileを取っておく。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss imageinfo
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86_24000, Win7SP1x86
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : VMWareAddressSpace (Unnamed AS)
AS Layer3 : FileAddressSpace (/home/remnux/Downloads/target1/Target1-1dd8701f.vmss)
PAE type : PAE
DTB : 0x185000L
KDBG : 0x82765be8L
Number of Processors : 2
Image Type (Service Pack) : 0
KPCR for CPU 0 : 0x82766c00L
KPCR for CPU 1 : 0x807c5000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2015-10-09 12:53:02 UTC+0000
Image local date and time : 2015-10-09 08:53:02 -0400
Win7SP1x86_24000を使用することとする。
続いてpslitを確認しておく。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP1x86_24000 pslist
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
---------- -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0x83d334e8 System 4 0 94 500 ------ 0 2015-10-09 11:30:44 UTC+0000
0x84edcbf0 smss.exe 276 4 2 30 ------ 0 2015-10-09 11:30:44 UTC+0000
0x84ecbb18 csrss.exe 368 360 9 366 0 0 2015-10-09 11:30:47 UTC+0000
0x84f97628 wininit.exe 420 360 3 77 0 0 2015-10-09 11:30:48 UTC+0000
0x855f6d40 csrss.exe 432 412 11 366 1 0 2015-10-09 11:30:48 UTC+0000
0x8561d030 winlogon.exe 480 412 3 115 1 0 2015-10-09 11:30:48 UTC+0000
0x84e979f8 services.exe 528 420 9 200 0 0 2015-10-09 11:30:48 UTC+0000
0x8583b030 lsass.exe 536 420 9 851 0 0 2015-10-09 11:30:48 UTC+0000
0x8583d960 lsm.exe 544 420 10 163 0 0 2015-10-09 11:30:48 UTC+0000
0x8586fd40 svchost.exe 644 528 11 351 0 0 2015-10-09 11:30:48 UTC+0000
0x84e01448 svchost.exe 720 528 6 276 0 0 2015-10-09 11:30:50 UTC+0000
0x85935030 svchost.exe 796 528 19 446 0 0 2015-10-09 11:30:51 UTC+0000
0x85969030 svchost.exe 836 528 17 405 0 0 2015-10-09 11:30:52 UTC+0000
0x85978940 svchost.exe 864 528 30 1036 0 0 2015-10-09 11:30:52 UTC+0000
0x859cc2c0 svchost.exe 1008 528 13 650 0 0 2015-10-09 11:30:52 UTC+0000
0x85a138f0 svchost.exe 1124 528 16 484 0 0 2015-10-09 11:30:53 UTC+0000
0x8582c8d8 spoolsv.exe 1228 528 12 273 0 0 2015-10-09 11:30:53 UTC+0000
0x85a55d40 svchost.exe 1256 528 17 304 0 0 2015-10-09 11:30:53 UTC+0000
0x85ae3030 vmtoolsd.exe 1432 528 8 274 0 0 2015-10-09 11:30:54 UTC+0000
0x85976318 svchost.exe 1784 528 5 99 0 0 2015-10-09 11:30:54 UTC+0000
0x85ae0cb0 dllhost.exe 1888 528 13 196 0 0 2015-10-09 11:30:54 UTC+0000
0x858b69e8 msdtc.exe 1980 528 12 145 0 0 2015-10-09 11:30:55 UTC+0000
0x85c09968 dwm.exe 2088 836 3 93 1 0 2015-10-09 11:31:04 UTC+0000
0x85c1e5f8 explorer.exe 2116 2060 23 912 1 0 2015-10-09 11:31:04 UTC+0000
0x85c39030 taskhost.exe 2252 528 7 150 1 0 2015-10-09 11:31:04 UTC+0000
0x859281f0 vmtoolsd.exe 2388 2116 7 164 1 0 2015-10-09 11:31:04 UTC+0000
0x8598c920 SearchIndexer. 2544 528 13 670 0 0 2015-10-09 11:31:10 UTC+0000
0x85d0d030 iexplore.exe 2996 2984 6 463 1 0 2015-10-09 11:31:27 UTC+0000
0x85cd3d40 OUTLOOK.EXE 3196 2116 22 1678 1 0 2015-10-09 11:31:32 UTC+0000
0x85d01510 svchost.exe 3232 528 9 131 0 0 2015-10-09 11:31:34 UTC+0000
0x85b43a58 sppsvc.exe 3900 528 4 153 0 0 2015-10-09 11:32:54 UTC+0000
0x83eb5d40 cmd.exe 2496 2116 1 22 1 0 2015-10-09 11:33:42 UTC+0000
0x83e5cd40 conhost.exe 916 432 3 83 1 0 2015-10-09 11:33:42 UTC+0000
0x83f105f0 cmd.exe 1856 2996 1 33 1 0 2015-10-09 11:35:15 UTC+0000
0x83f13d40 conhost.exe 1624 432 3 81 1 0 2015-10-09 11:35:15 UTC+0000
0x83fb86a8 cmd.exe 3064 2116 1 22 1 0 2015-10-09 11:37:32 UTC+0000
0x83fa9030 conhost.exe 676 432 3 83 1 0 2015-10-09 11:37:32 UTC+0000
0x83fb2d40 cmd.exe 3784 2196 1 24 1 0 2015-10-09 11:39:22 UTC+0000
0x83fc7c08 conhost.exe 1824 432 3 85 1 0 2015-10-09 11:39:22 UTC+0000
0x84013598 TeamViewer.exe 2680 1696 28 632 1 0 2015-10-09 12:08:46 UTC+0000
0x84017d40 tv_w32.exe 4064 2680 2 83 1 0 2015-10-09 12:08:47 UTC+0000
0x858bc278 TeamViewer_Des 1092 2680 16 405 1 0 2015-10-09 12:10:56 UTC+0000
0x83f1ed40 mstsc.exe 2844 2116 11 484 1 0 2015-10-09 12:12:03 UTC+0000
remnux@remnux:~/Downloads/target1$
OUTLOOK.EXEが動いていたみたいなので此奴のメモリダンプを取ってみる。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP1x86_24000 memdump -p 3196 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
************************************************************************
Writing OUTLOOK.EXE [ 3196] to 3196.dmp
remnux@remnux:~/Downloads/target1$
このダンプからFrom:のアドレスがあるか確認してみる。

見えた。これが回答だ。
※Defangしてます。
Ans: th3wh1t3r0s3@gmail[.com
What is the filename that was delivered in the email?
先ほどのメモリダンプからファイル拡張子を探索します。
exeを探してみたらありました!

Ans: AnyConnectInstaller.exe
What is the name of the rat's family used by the attacker?
まずは先ほど回答したファイルがどのアドレスにあるか確認するため、filescanを実施します。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP1x86_24000 filescan | grep AnyConnectInstaller.exe
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
0x000000003df12dd0 2 0 RW-rwd \Device\HarddiskVolume2\Users\anyconnect\AnyConnect\AnyConnectInstaller.exe
0x000000003df1cf00 4 0 R--r-d \Device\HarddiskVolume2\Users\anyconnect\AnyConnect\AnyConnectInstaller.exe
0x000000003e0bc5e0 7 0 R--r-d \Device\HarddiskVolume2\Users\frontdesk\Downloads\AnyConnectInstaller.exe
0x000000003e2559b0 8 0 R--rwd \Device\HarddiskVolume2\Users\frontdesk\Downloads\AnyConnectInstaller.exe
0x000000003e2ae8e0 8 0 RWD--- \Device\HarddiskVolume2\Users\anyconnect\AnyConnect\AnyConnectInstaller.exe
0x000000003ed57968 4 0 R--r-d \Device\HarddiskVolume2\Users\frontdesk\Downloads\AnyConnectInstaller.exe
2つの階層パターンにありそうなので2つのファイルダンプを取得します。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP1x86_24000 dumpfiles -Q 0x000000003df12dd0 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
DataSectionObject 0x3df12dd0 None \Device\HarddiskVolume2\Users\anyconnect\AnyConnect\AnyConnectInstaller.exe
remnux@remnux:~/Downloads/target1$
remnux@remnux:~/Downloads/target1$
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP1x86_24000 dumpfiles -Q 0x000000003e0bc5e0 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
ImageSectionObject 0x3e0bc5e0 None \Device\HarddiskVolume2\Users\frontdesk\Downloads\AnyConnectInstaller.exe
DataSectionObject 0x3e0bc5e0 None \Device\HarddiskVolume2\Users\frontdesk\Downloads\AnyConnectInstaller.exe
remnux@remnux:~/Downloads/target1$
ダンプが完了したらこのファイルのハッシュ値を計算します。
remnux@remnux:~/Downloads/target1/out$ sha256sum file.None.0x85d0ed60.dat file.None.0x858aef78.dat
34358161d294cab2aac611ec14754204737b50c32bc2e74ec17b4c54b96a9c7a file.None.0x85d0ed60.dat
94a4ef65f99c594a8bfbfbc57f369ec2b6a5cf789f91be89976086aaa507cd47 file.None.0x858aef78.dat
remnux@remnux:~/Downloads/target1/out$
このハッシュ値をクラウドサンドボックスで検索します。
以下のサイトを参考に検索すればいいと思います。
file.None.0x85d0ed60.datのほうは以下のように検知がされませんでした。

file.None.0x858aef78.datのほうを検索してみます。

でてきました。
このRATファミリーの名前が記載されているシグネチャを確認します。

これが回答ですね!
Ans: XTREMERAT
The malware appears to be leveraging process injection. What is the PID of the process that is injected?
以下のTriageのサンドボックスサイトでProcessを確認します。

iexplore.exeにInjectしてますね。
このPIDについては過去に確認したpslistでみます。
Ans: 2996
What is the unique value the malware is using to maintain persistence after reboot?
さっきと同じようにTriageでPersistenceの項目についてレジストリを確認します。
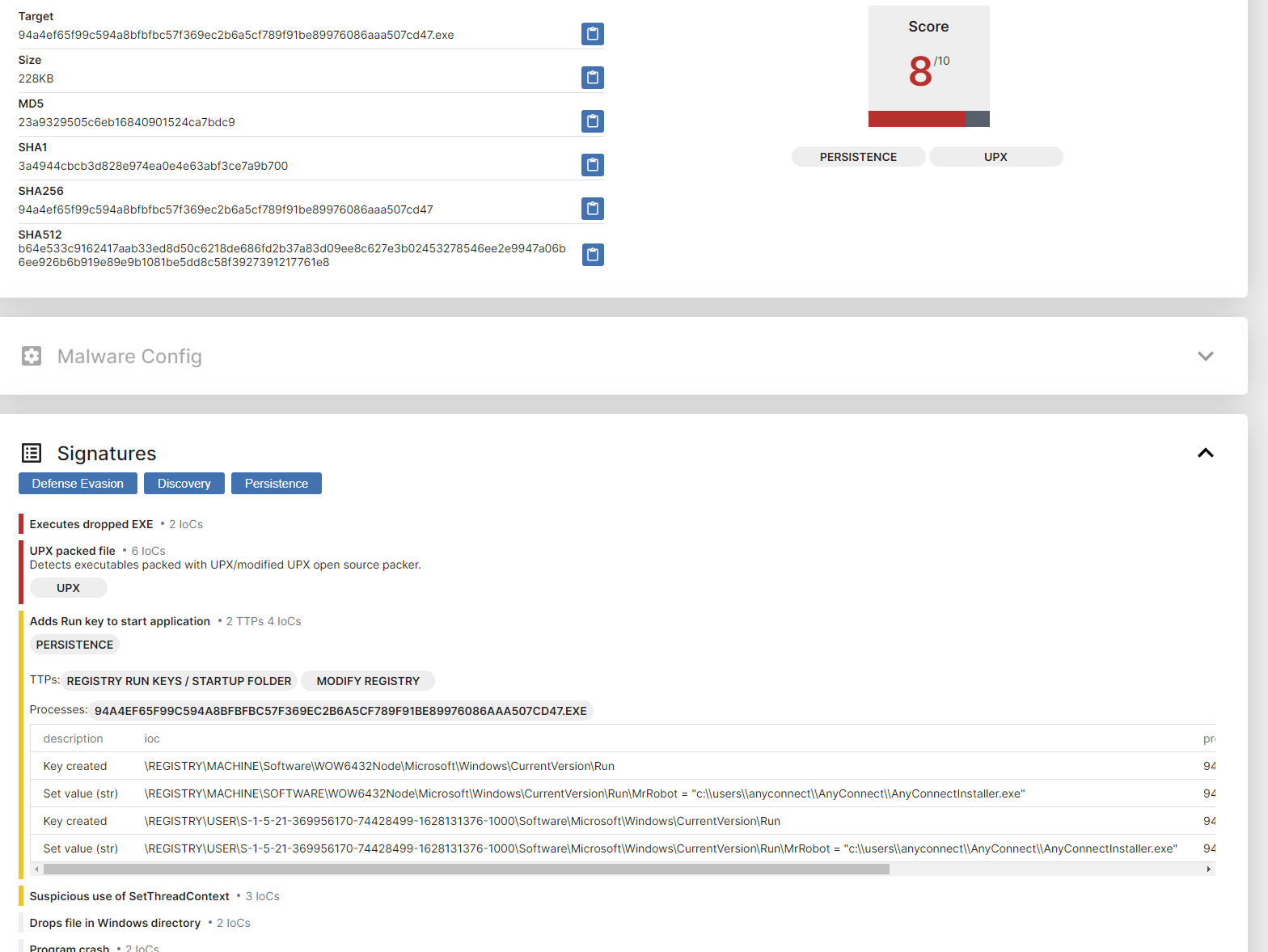
Keyが見えるので回答します。
Ans: MrRobot
Malware often uses a unique value or name to ensure that only one copy runs on the system. What is the unique name the malware is using?
さっきと同じようにTriageでMutexの項目を確認します。
datで検索すると答えがみえます。

Ans: fsociety0.dat
It appears that a notorious hacker compromised this box before our current attackers. Name the movie he or she is from.
誰やねんってなります。とりあえずUser名を列挙しときます。ChatGPTさんに簡単に正規表現をつくってもらいました。

この正規表現を使ってfilescanからUser名を絞り込みます。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP0x86 filescan | grep -oP '(?<=\\Users\\)[^\\]+' | sort -u
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Administrator.front-desk-PC
anyconnect
desktop.ini
FRONTD~1
front-desk
frontdesk
gideon
Public
zerocool
remnux@remnux:~/Downloads/target1$
gideon, zerocool辺りが気になるのでここら辺で検索かけました。
※おそらくgideonはMr.Robot側の出演者ですが(笑)
Googleで出てきたのは以下の映画でした。
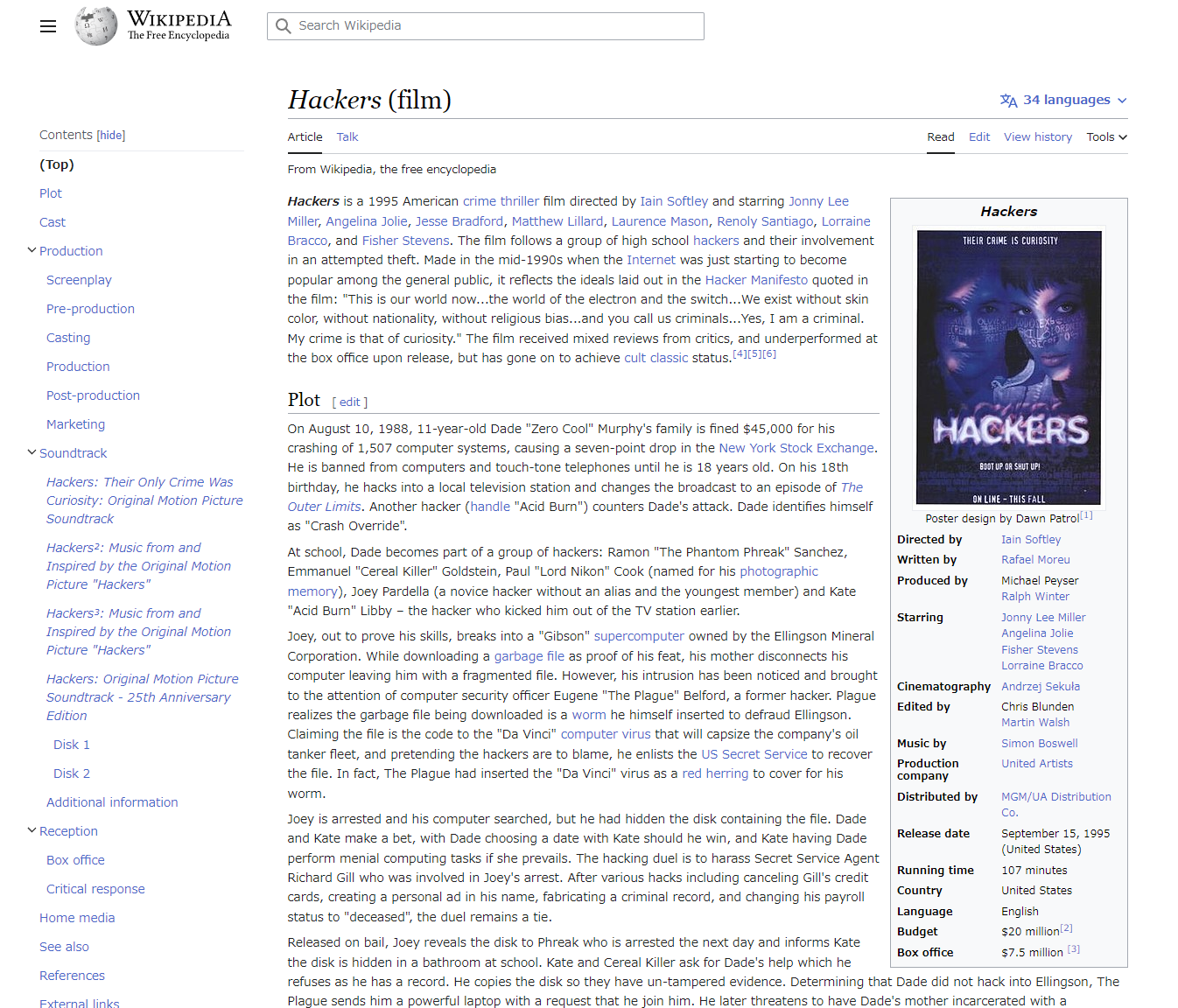
Ans: Hackers
What is the NTLM password hash for the administrator account?
単にハッシュを取ればいいだけなので以下のコマンドを打ち込みます。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP0x86 hashdump
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Administrator:500:aad3b435b51404eeaad3b435b51404ee:79402b7671c317877b8b954b3311fa82:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
front-desk:1000:aad3b435b51404eeaad3b435b51404ee:2ae4c526659523d58350e4d70107fc11:::
remnux@remnux:~/Downloads/target1$
NT見えました!!
Ans: 79402b7671c317877b8b954b3311fa82
The attackers appear to have moved over some tools to the compromised front desk host. How many tools did the attacker move?
Temp階層にあるexeファイルを洗い出しました。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP0x86 filescan | grep '\\Windows\\Temp' | grep "exe"
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
0x000000003df31038 8 0 R--r-- \Device\HarddiskVolume2\Windows\Temp\wce.exe
0x000000003e1eee10 7 0 R--r-d \Device\HarddiskVolume2\Windows\Temp\getlsasrvaddr.exe
0x000000003e25eca8 5 0 R--r-d \Device\HarddiskVolume2\Windows\Temp\wce.exe
0x000000003fa633f0 1 0 R--rw- \Device\HarddiskVolume2\Windows\Temp\Rar.exe
0x000000003fc3fb80 6 0 R--r-d \Device\HarddiskVolume2\Windows\Temp\nbtscan.exe
0x000000003fc5af80 7 0 R--r-d \Device\HarddiskVolume2\Windows\Temp\Rar.exe
0x000000003fdd4ca0 7 0 R--r-- \Device\HarddiskVolume2\Windows\Temp\nbtscan.exe
remnux@remnux:~/Downloads/target1$
wce.exe, getlsasrvaddr.exe, Rar.exe, 'nbtscan.exe'の4つがあるので4と回答するとFailとなります。
よくよくこれらのToolを調べると以下のリポジトリがヒットしました。
getlsasrvaddr.exeはwce.exeの補助Tool的立ち位置のようです。
よって3つと回答します。
Ans: 3
What is the password for the front desk local administrator account?
consolesを確認します。このコマンドはcmdscanよりは打ったコマンド内容を出力結果含めてScreenshotとして表示してくれるので、Passwordが紛れてたりします。プロセスとの関係性を見たいならcmdscanが良かったりしますが。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP0x86 consoles
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
**************************************************
ConsoleProcess: conhost.exe Pid: 916
Console: 0x1381c0 CommandHistorySize: 50
HistoryBufferCount: 2 HistoryBufferMax: 4
OriginalTitle: cmd
Title: Administrator: cmd
AttachedProcess: cmd.exe Pid: 2496 Handle: 0x5c
----
CommandHistory: 0x2fa238 Application: wce.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x2f9098 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 5 LastAdded: 4 LastDisplayed: 4
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x5c
Cmd #0 at 0x2efe98: cd ..
Cmd #1 at 0x2efeb0: cd Temp
Cmd #2 at 0x2f58a0: dir
Cmd #3 at 0x2f6bb8: wce.exe -w
Cmd #4 at 0x2fe400: wce.exe -w > w.tmp
----
Screen 0x2dfeb0 X:80 Y:300
Dump:
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd ..
C:\Windows>cd Temp
C:\Windows\Temp>dir
Volume in drive C has no label.
Volume Serial Number is FE0F-F423
Directory of C:\Windows\Temp
10/09/2015 07:29 AM <DIR> .
10/09/2015 07:29 AM <DIR> ..
10/09/2015 01:27 AM 0 DMIE58D.tmp
10/09/2015 06:57 AM 50,176 getlsasrvaddr.exe
10/09/2015 02:02 AM 7,572 MpCmdRun.log
10/09/2015 12:07 AM 4,636 MpSigStub.log
10/09/2015 03:37 AM <DIR> MPTelemetrySubmit
10/09/2015 06:45 AM 36,864 nbtscan.exe
10/09/2015 06:44 AM 503,800 Rar.exe
10/09/2015 01:28 AM 180,224 TS_A16D.tmp
10/09/2015 01:28 AM 196,608 TS_A3BF.tmp
10/09/2015 01:28 AM 376,832 TS_A42D.tmp
10/09/2015 01:28 AM 114,688 TS_A528.tmp
10/09/2015 01:28 AM 425,984 TS_A5C5.tmp
10/09/2015 01:28 AM 131,072 TS_A807.tmp
10/09/2015 01:28 AM 655,360 TS_A911.tmp
10/09/2015 01:28 AM 114,688 TS_AA79.tmp
10/09/2015 01:28 AM 180,224 TS_AF79.tmp
10/08/2015 11:43 PM <DIR> vmware-SYSTEM
10/09/2015 07:16 AM 0 w.tmp
10/09/2015 06:45 AM 199,168 wce.exe
17 File(s) 3,177,896 bytes
4 Dir(s) 22,602,948,608 bytes free
C:\Windows\Temp>wce.exe -w
WCE v1.42beta (Windows Credentials Editor) - (c) 2010-2013 Amplia Security - by
Hernan Ochoa (hernan@ampliasecurity.com)
Use -h for help.
frontdesk\ALLSAFECYBERSEC:THzV7mpz
FRONT-DESK-PC$\ALLSAFECYBERSEC:o0&77qj:^zctL2T]ljn3<niK2Kbqi`(:LeBoO7zE>'d8<>J"P
K;\*5IS@Oxg:rC:P:z Y!%fUiIX0y_J& uNUTJ?%:Y;qJY,xq/:)%5^f&zDK.)F%H;V?.^Z'
C:\Windows\Temp>wce.exe -w > w.tmp
C:\Windows\Temp>
**************************************************
ConsoleProcess: conhost.exe Pid: 1624
Console: 0x1381c0 CommandHistorySize: 50
HistoryBufferCount: 4 HistoryBufferMax: 4
OriginalTitle: C:\Program Files\Internet Explorer\iexplore.exe
Title: Administrator: C:\Program Files\Internet Explorer\iexplore.exe
AttachedProcess: cmd.exe Pid: 1856 Handle: 0x64
----
CommandHistory: 0x1c0e80 Application: at.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x1c0cd0 Application: net1.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x1c0ba8 Application: net.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x1c0ab0 Application: cmd.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x64
----
Screen 0x1afeb0 X:80 Y:300
Dump:
**************************************************
ConsoleProcess: conhost.exe Pid: 676
Console: 0x1381c0 CommandHistorySize: 50
HistoryBufferCount: 3 HistoryBufferMax: 4
OriginalTitle: %SystemRoot%\System32\cmd.exe
Title: Administrator: C:\Windows\System32\cmd.exe
AttachedProcess: cmd.exe Pid: 3064 Handle: 0x5c
----
CommandHistory: 0x34a338 Application: runas.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x34a130 Application: wce.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x349ff8 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 5 LastAdded: 4 LastDisplayed: 4
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x5c
Cmd #0 at 0x33fe58: cd ..
Cmd #1 at 0x33fe70: cd Temp
Cmd #2 at 0x3477a8: wce.exe -w
Cmd #3 at 0x3487b8: runas /profile /user:Administrator
Cmd #4 at 0x34e500: runas /profile /user:Administrator cmd
----
Screen 0x32fe70 X:80 Y:300
Dump:
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd ..
C:\Windows>cd Temp
C:\Windows\Temp>wce.exe -w
WCE v1.42beta (Windows Credentials Editor) - (c) 2010-2013 Amplia Security - by
Hernan Ochoa (hernan@ampliasecurity.com)
Use -h for help.
frontdesk\ALLSAFECYBERSEC:THzV7mpz
FRONT-DESK-PC$\ALLSAFECYBERSEC:o0&77qj:^zctL2T]ljn3<niK2Kbqi`(:LeBoO7zE>'d8<>J"P
K;\*5IS@Oxg:rC:P:z Y!%fUiIX0y_J& uNUTJ?%:Y;qJY,xq/:)%5^f&zDK.)F%H;V?.^Z '
C:\Windows\Temp>runas /profile /user:Administrator
RUNAS USAGE:
RUNAS [ [/noprofile | /profile] [/env] [/savecred | /netonly] ]
/user:<UserName> program
RUNAS [ [/noprofile | /profile] [/env] [/savecred] ]
/smartcard [/user:<UserName>] program
RUNAS /trustlevel:<TrustLevel> program
/noprofile specifies that the user's profile should not be loaded.
This causes the application to load more quickly, but
can cause some applications to malfunction.
/profile specifies that the user's profile should be loaded.
This is the default.
/env to use current environment instead of user's.
/netonly use if the credentials specified are for remote
access only.
/savecred to use credentials previously saved by the user.
This option is not available on Windows 7 Home or Windows 7
Starter Editions
and will be ignored.
/smartcard use if the credentials are to be supplied from a
smartcard.
/user <UserName> should be in form USER@DOMAIN or DOMAIN\USER
/showtrustlevels displays the trust levels that can be used as arguments
to /trustlevel.
/trustlevel <Level> should be one of levels enumerated
in /showtrustlevels.
program command line for EXE. See below for examples
Examples:
> runas /noprofile /user:mymachine\administrator cmd
> runas /profile /env /user:mydomain\admin "mmc %windir%\system32\dsa.msc"
> runas /env /user:user@domain.microsoft.com "notepad \"my file.txt\""
NOTE: Enter user's password only when prompted.
NOTE: /profile is not compatible with /netonly.
NOTE: /savecred is not compatible with /smartcard.
C:\Windows\Temp>runas /profile /user:Administrator cmd
Enter the password for Administrator:
Attempting to start cmd as user "FRONT-DESK-PC\Administrator" ...
C:\Windows\Temp>
**************************************************
ConsoleProcess: conhost.exe Pid: 1824
Console: 0x1381c0 CommandHistorySize: 50
HistoryBufferCount: 2 HistoryBufferMax: 4
OriginalTitle: cmd (running as FRONT-DESK-PC\Administrator)
Title: Administrator: cmd (running as FRONT-DESK-PC\Administrator)
AttachedProcess: cmd.exe Pid: 3784 Handle: 0x60
----
CommandHistory: 0x2d92a8 Application: wce.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x2d90d0 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 5 LastAdded: 4 LastDisplayed: 4
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #0 at 0x2cfe88: cd ..
Cmd #1 at 0x2cfea0: cd Temp
Cmd #2 at 0x2d6de0: dir
Cmd #3 at 0x2d67f0: wce.exe -w
Cmd #4 at 0x2bbc10: wce.exe -w > w.tmp
----
Screen 0x2bfea0 X:80 Y:300
Dump:
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd ..
C:\Windows>cd Temp
C:\Windows\Temp>
C:\Windows\Temp>dir
Volume in drive C has no label.
Volume Serial Number is FE0F-F423
Directory of C:\Windows\Temp
10/09/2015 07:29 AM <DIR> .
10/09/2015 07:29 AM <DIR> ..
10/09/2015 01:27 AM 0 DMIE58D.tmp
10/09/2015 06:57 AM 50,176 getlsasrvaddr.exe
10/09/2015 02:02 AM 7,572 MpCmdRun.log
10/09/2015 12:07 AM 4,636 MpSigStub.log
10/09/2015 03:37 AM <DIR> MPTelemetrySubmit
10/09/2015 06:45 AM 36,864 nbtscan.exe
10/09/2015 06:44 AM 503,800 Rar.exe
10/09/2015 01:28 AM 180,224 TS_A16D.tmp
10/09/2015 01:28 AM 196,608 TS_A3BF.tmp
10/09/2015 01:28 AM 376,832 TS_A42D.tmp
10/09/2015 01:28 AM 114,688 TS_A528.tmp
10/09/2015 01:28 AM 425,984 TS_A5C5.tmp
10/09/2015 01:28 AM 131,072 TS_A807.tmp
10/09/2015 01:28 AM 655,360 TS_A911.tmp
10/09/2015 01:28 AM 114,688 TS_AA79.tmp
10/09/2015 01:28 AM 180,224 TS_AF79.tmp
10/08/2015 11:43 PM <DIR> vmware-SYSTEM
10/09/2015 07:34 AM 333 w.tmp
10/09/2015 06:45 AM 199,168 wce.exe
17 File(s) 3,178,229 bytes
4 Dir(s) 22,603,194,368 bytes free
C:\Windows\Temp>wce.exe -w
WCE v1.42beta (Windows Credentials Editor) - (c) 2010-2013 Amplia Security - by
Hernan Ochoa (hernan@ampliasecurity.com)
Use -h for help.
Administrator\front-desk-PC:flagadmin@1234
frontdesk\ALLSAFECYBERSEC:THzV7mpz
FRONT-DESK-PC$\ALLSAFECYBERSEC:o0&77qj:^zctL2T]ljn3<niK2Kbqi`(:LeBoO7zE>'d8<>J"P
K;\*5IS@Oxg:rC:P:z Y!%fUiIX0y_J& uNUTJ?%:Y;qJY,xq/:)%5^f&zDK.)F%H;V?.^Z '
C:\Windows\Temp>wce.exe -w > w.tmp
C:\Windows\Temp>
remnux@remnux:~/Downloads/target1$
後半のほうにパスワードらしきものが見えます。
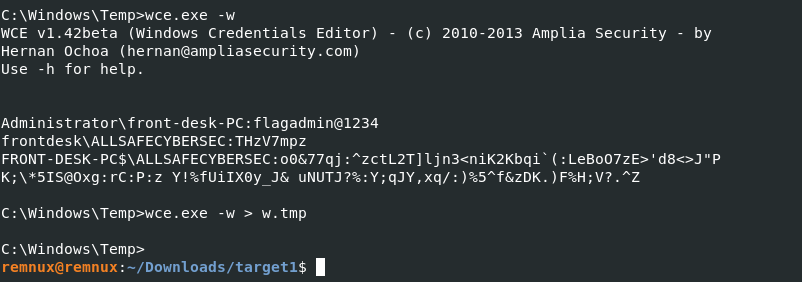
これを回答します。
Ans: flagadmin@1234
What is the std create data timestamp for the nbtscan.exe tool?
timelinerコマンドの出力からnbtscanでフィルタする。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP0x86 timeliner | grep 'nbtscan'
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
2015-10-09 10:45:12 UTC+0000|[SHIMCACHE]| \??\C:\Windows\Temp\nbtscan.exe|
remnux@remnux:~/Downloads/target1$
Ans: 2015-10-09 10:45:12 UTC
The attackers appear to have stored the output from the nbtscan.exe tool in a text file on a disk called nbs.txt. What is the IP address of the first machine in that file?
nbs.txtがどこにあるかをfilescanで確認する。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP0x86 filescan | grep "nbs.txt"
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
0x000000003fdb7808 8 0 -W-r-- \Device\HarddiskVolume2\Windows\Temp\nbs.txt
remnux@remnux:~/Downloads/target1$
アドレスを確認できたので、ファイルダンプを行う。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP1x86_24000 dumpfiles -Q 0x000000003fdb7808 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
DataSectionObject 0x3fdb7808 None \Device\HarddiskVolume2\Windows\Temp\nbs.txt
Ans: 10.1.1.2
What is the full IP address and the port was the attacker's malware using?
netscanからこのマシンのIP10.1.1.20で絞り込む。
remnux@remnux:~/Downloads/target1$ vol.py -f Target1-1dd8701f.vmss --profile=Win7SP1x86_24000 netscan | grep '10.1.1.20'
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
0x3deba9a0 UDPv4 10.1.1.20:56813 *:* 3232 svchost.exe 2015-10-09 11:32:55 UTC+0000
0x3e143978 UDPv4 10.1.1.20:1900 *:* 3232 svchost.exe 2015-10-09 11:32:55 UTC+0000
0x3e25bc60 UDPv4 10.1.1.20:138 *:* 4 System 2015-10-09 11:30:49 UTC+0000
0x3e2b0f50 UDPv4 10.1.1.20:137 *:* 4 System 2015-10-09 11:30:49 UTC+0000
0x3e2b08a8 TCPv4 10.1.1.20:139 0.0.0.0:0 LISTENING 4 System
0x3de98df8 TCPv4 10.1.1.20:49261 10.1.1.21:445 ESTABLISHED 4 System
0x3e0d0df8 TCPv4 10.1.1.20:49208 10.1.1.3:80 ESTABLISHED 3196 OUTLOOK.EXE
0x3e0eedf8 TCPv4 10.1.1.20:49205 180.76.254.120:22 ESTABLISHED 2996 iexplore.exe
0x3e1e5008 TCPv4 10.1.1.20:49330 10.1.1.2:139 CLOSED 4 System
0x3e1f0df8 TCPv4 10.1.1.20:49207 10.1.1.3:80 ESTABLISHED 3196 OUTLOOK.EXE
0x3e1fadf8 TCPv4 10.1.1.20:49314 10.1.1.3:443 CLOSED 3196 OUTLOOK.EXE
0x3fa4dbf8 TCPv4 10.1.1.20:49333 10.1.1.3:443 CLOSED 3196 OUTLOOK.EXE
0x3fa8d1d8 TCPv4 10.1.1.20:49336 10.1.1.3:443 CLOSED 3196 OUTLOOK.EXE
0x3fa95df8 TCPv4 10.1.1.20:49297 192.96.201.138:5938 ESTABLISHED 2680 TeamViewer.exe
0x3fb7a560 TCPv4 10.1.1.20:49301 10.1.1.21:3389 ESTABLISHED 2844 mstsc.exe
0x3fc426a8 TCPv4 10.1.1.20:49291 107.6.97.19:5938 ESTABLISHED 2680 TeamViewer.exe
remnux@remnux:~/Downloads/target1$
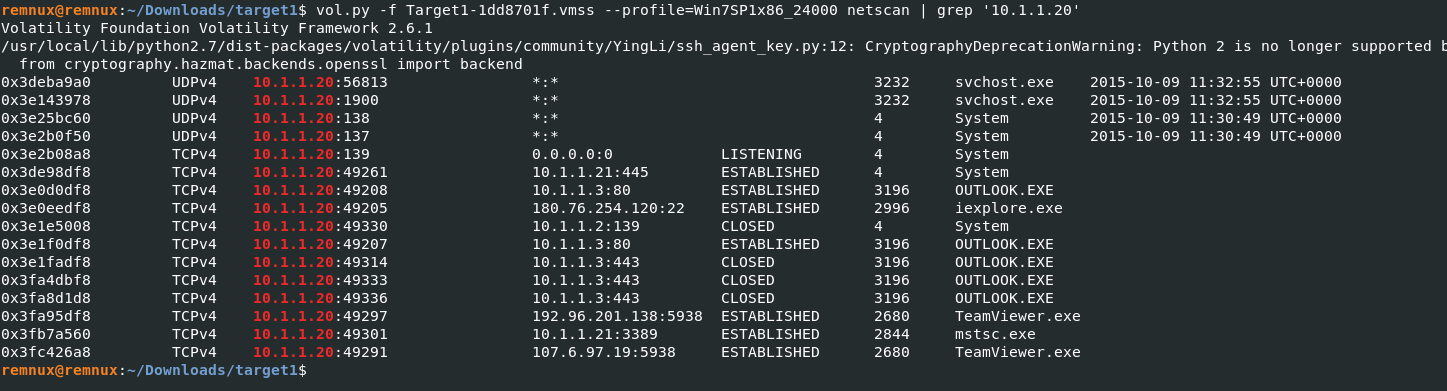
パット見でSSHのポートで外部IPと通信が成立しているやつを回答する。
Ans: 180.76.254.120:22
It appears the attacker also installed legit remote administration software. What is the name of the running process?
pslistを見れば気づいていると思う。TeamViewerがPID 2680で存在していることを。
Ans: TeamViewer.exe
It appears the attackers also used a built-in remote access method. What IP address did they connect to?
RDPのポート3389でつながっている先を見ればよい。netscanの出力で確認できる。
Ans: 10.1.1.21
Machine:Target2
It appears the attacker moved latterly from the front desk machine to the security admins (Gideon) machine and dumped the passwords. What is Gideon's password?
まずはimageinfoコマンドでプロファイルを確認しておく。
remnux@remnux:~/Downloads/target2$ vol.py -f target2-6186fe9f.vmss imageinfo
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86_24000, Win7SP1x86
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : VMWareAddressSpace (Unnamed AS)
AS Layer3 : FileAddressSpace (/home/remnux/Downloads/target2/target2-6186fe9f.vmss)
PAE type : PAE
DTB : 0x185000L
KDBG : 0x82730be8L
Number of Processors : 2
Image Type (Service Pack) : 0
KPCR for CPU 0 : 0x82731c00L
KPCR for CPU 1 : 0x807c5000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2015-10-09 12:53:12 UTC+0000
Image local date and time : 2015-10-09 08:53:12 -0400
remnux@remnux:~/Downloads/target2$
上記プロファイルWin7SP1x86_24000を用いる。とりあえずconsolesのコマンドで打たれてないか確認する。
remnux@remnux:~/Downloads/target2$ vol.py -f target2-6186fe9f.vmss --profile=Win7SP1x86_24000 consoles
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
**************************************************
ConsoleProcess: conhost.exe Pid: 2888
Console: 0x4a81c0 CommandHistorySize: 50
HistoryBufferCount: 2 HistoryBufferMax: 4
OriginalTitle: %SystemRoot%\system32\cmd.exe
Title: C:\Windows\system32\cmd.exe
AttachedProcess: cmd.exe Pid: 3488 Handle: 0x60
----
CommandHistory: 0x2da180 Application: ipconfig.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x2d9ff0 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 1 LastAdded: 0 LastDisplayed: 0
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #0 at 0x2d77a0: ipconfig
----
Screen 0x2bfe68 X:80 Y:300
Dump:
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\gideon.ALLSAFECYBERSEC>ipconfig
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.1.1.21
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.1.1.1
Tunnel adapter isatap.{AB3D4E7F-B62F-4398-A77C-057C31081A47}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
C:\Users\gideon.ALLSAFECYBERSEC>
**************************************************
ConsoleProcess: conhost.exe Pid: 3048
Console: 0x4a81c0 CommandHistorySize: 50
HistoryBufferCount: 4 HistoryBufferMax: 4
OriginalTitle: Command Prompt
Title: Administrator: Command Prompt
AttachedProcess: cmd.exe Pid: 416 Handle: 0x60
----
CommandHistory: 0xea408 Application: Rar.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0xea5f8 Application: net.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0xea500 Application: whoami.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0xe9198 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 18 LastAdded: 17 LastDisplayed: 17
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #0 at 0xe6030: cd C:\Users
Cmd #1 at 0xe6ea8: dir
Cmd #2 at 0xee3d0: wce.exe -w > gideon/w.tmp
Cmd #3 at 0xe0170: who ami
Cmd #4 at 0xe0188: whoami
Cmd #5 at 0xea3c8: net use z: \\10.1.1.2\c$
Cmd #6 at 0xe01b8: cd z:
Cmd #7 at 0xe6ed8: dir
Cmd #8 at 0xe6070: cd gideon
Cmd #9 at 0xe6ef8: dir
Cmd #10 at 0xe6f08: z:
Cmd #11 at 0xe6f18: dir
Cmd #12 at 0xf2418: copy c:\users\gideon\rar.exe z:\crownjewels
Cmd #13 at 0xe0cb8: cd crownjewels
Cmd #14 at 0xe6f28: dir
Cmd #15 at 0xe6f38: rar
Cmd #16 at 0xf2478: rar crownjewlez.rar *.txt -hp123qwe!@#
Cmd #17 at 0xf24d0: rar a -hp123!@#qwe crownjewlez.rar *.txt
----
Screen 0xd0038 X:80 Y:300
Dump:
wce.exe -w > gideon/w.tmpのコマンドでクレデンシャル出力をファイルに落としているみたいだ。このw.tmpのアドレスをfilescanで確認しておく。
remnux@remnux:~/Downloads/target2$ vol.py -f target2-6186fe9f.vmss --profile=Win7SP1x86_24000 filescan | grep w.tmp
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
0x000000003fcf2798 8 0 -W-r-- \Device\HarddiskVolume2\Users\gideon\w.tmp
remnux@remnux:~/Downloads/target2$
このファイルをダンプする。
remnux@remnux:~/Downloads/target2$ vol.py -f target2-6186fe9f.vmss --profile=Win7SP1x86_24000 dumpfiles -Q 0x000000003fcf2798 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
DataSectionObject 0x3fcf2798 None \Device\HarddiskVolume2\Users\gideon\w.tmp
remnux@remnux:~/Downloads/target2$ cd out
remnux@remnux:~/Downloads/target2/out$ ls -lta
total 12
-rw-rw-r-- 1 remnux remnux 4096 Jun 17 06:12 file.None.0x85a35da0.dat
drwxrwxr-x 2 remnux remnux 4096 Jun 17 06:12 .
drwxrwxr-x 3 remnux remnux 4096 Jun 17 06:03 ..
Ans: t76fRJhS
Once the attacker gained access to "Gideon," they pivoted to the AllSafeCyberSec domain controller to steal files. It appears they were successful. What password did they use?
これはconsolesの後半のコマンドを見ればわかる。
rar crownjewlez.rar *.txt -hp123qwe!@#
後は文字を合わせればいいだけ。
Ans: 123qwe!@#
What was the name of the RAR file created by the attackers?
これも以下のconsolesのコマンドを見ればわかる。
Cmd #12 at 0xf2418: copy c:\users\gideon\rar.exe z:\crownjewels
Cmd #13 at 0xe0cb8: cd crownjewels
Cmd #14 at 0xe6f28: dir
Cmd #15 at 0xe6f38: rar
Cmd #16 at 0xf2478: rar crownjewlez.rar *.txt -hp123qwe!@#
Ans: crownjewlez.rar
How many files did the attacker add to the RAR archive?
cmdscanでRARをいじくってるPIDを確認する。
remnux@remnux:~/Downloads/target2$ vol.py -f target2-6186fe9f.vmss --profile=Win7SP1x86_24000 cmdscan
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
**************************************************
CommandProcess: conhost.exe Pid: 2888
CommandHistory: 0x2d9ff0 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 1 LastAdded: 0 LastDisplayed: 0
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #0 @ 0x2d77a0: ipconfig
Cmd #1 @ 0x2d0031: ???
Cmd #12 @ 0x2d0032: ???
Cmd #17 @ 0x2d0035: ?
Cmd #36 @ 0x2a00c4: -?-?*???*
Cmd #37 @ 0x2d6be0: -?*???????-
**************************************************
CommandProcess: conhost.exe Pid: 3048
CommandHistory: 0xe9198 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 18 LastAdded: 17 LastDisplayed: 17
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #0 @ 0xe6030: cd C:\Users
Cmd #1 @ 0xe6ea8: dir
Cmd #2 @ 0xee3d0: wce.exe -w > gideon/w.tmp
Cmd #3 @ 0xe0170: who ami
Cmd #4 @ 0xe0188: whoami
Cmd #5 @ 0xea3c8: net use z: \\10.1.1.2\c$
Cmd #6 @ 0xe01b8: cd z:
Cmd #7 @ 0xe6ed8: dir
Cmd #8 @ 0xe6070: cd gideon
Cmd #9 @ 0xe6ef8: dir
Cmd #10 @ 0xe6f08: z:
Cmd #11 @ 0xe6f18: dir
Cmd #12 @ 0xf2418: copy c:\users\gideon\rar.exe z:\crownjewels
Cmd #13 @ 0xe0cb8: cd crownjewels
Cmd #14 @ 0xe6f28: dir
Cmd #15 @ 0xe6f38: rar
Cmd #16 @ 0xf2478: rar crownjewlez.rar *.txt -hp123qwe!@#
Cmd #17 @ 0xf24d0: rar a -hp123!@#qwe crownjewlez.rar *.txt
Cmd #36 @ 0xb00c4: ??
???
Cmd #37 @ 0xe5d48: ?
???????
remnux@remnux:~/Downloads/target2$
PIDが3048だと判明。メモリダンプする。
remnux@remnux:~/Downloads/target2$ vol.py -f target2-6186fe9f.vmss --profile=Win7SP1x86_24000 memdump -p 3048 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
************************************************************************
Writing conhost.exe [ 3048] to 3048.dmp
remnux@remnux:~/Downloads/target2$
consolesで最後のコマンドでtxtファイルを追加していたのがわかるので、txtファイルでフィルタする。
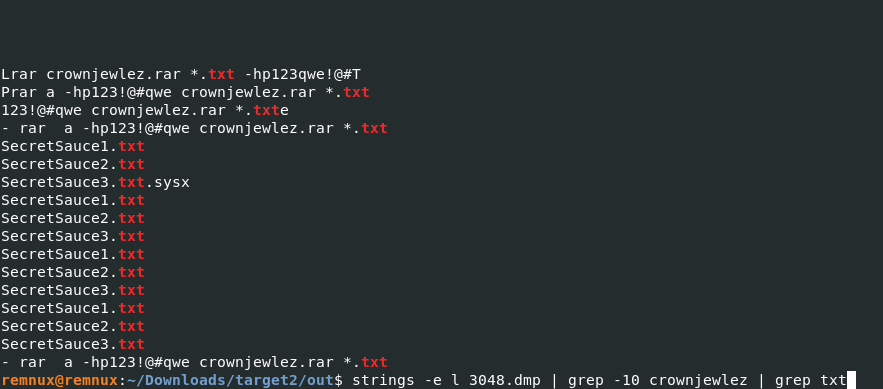
remnux@remnux:~/Downloads/target2/out$ strings -e l 3048.dmp | grep -10 crownjewlez | grep txt
Ans: 3
The attacker appears to have created a scheduled task on Gideon's machine. What is the name of the file associated with the scheduled task?
System32\Taskの階層を確認します。
remnux@remnux:~/Downloads/target2$ vol.py -f target2-6186fe9f.vmss --profile=Win7SP1x86_24000 filescan | grep 'System32\\Tasks'
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
0x000000003d86af80 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\WindowsColorSystem\Calibration Loader
0x000000003d8a5d58 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Task Manager\Interactive
0x000000003db79318 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\PBDADiscoveryW2
0x000000003dddb160 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\mcupdate
0x000000003dddb6a0 8 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\GoogleUpdateTaskMachineUA
0x000000003decdda0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\SideShow\SessionAgent
0x000000003e022998 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\ReindexSearchRoot
0x000000003e037340 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\PvrScheduleTask
0x000000003e077c20 8 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\CertificateServicesClient\UserTask-Roam
0x000000003e08d820 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Multimedia\SystemSoundsService
0x000000003e0ae7a8 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\PerfTrack\BackgroundConfigSurveyor
0x000000003e15ebb0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\MemoryDiagnostic\DecompressionFailureDetector
0x000000003e165f80 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Autochk\Proxy
0x000000003e16b428 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Time Synchronization\SynchronizeTime
0x000000003e193320 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Active Directory Rights Management Services Client\AD RMS Rights Policy Template Management (Manual)
0x000000003e347488 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Windows Filtering Platform\BfeOnServiceStartTypeChange
0x000000003e367bf0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Windows Error Reporting\QueueReporting
0x000000003e3fe420 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows Defender\MP Scheduled Scan
0x000000003ec30448 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Application Experience\ProgramDataUpdater
0x000000003edad5c0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\PBDADiscoveryW1
0x000000003f06ce28 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\NetTrace\GatherNetworkInfo
0x000000003f4029e0 8 0 R--rwd \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\RAC\RacTask
0x000000003f42c498 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Office\Office 15 Subscription Heartbeat
0x000000003f4506a8 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\AppID\PolicyConverter
0x000000003fa00278 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\SideShow\SystemDataProviders
0x000000003fa0c658 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\Consolidator
0x000000003fa43d60 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Shell\WindowsParentalControls
0x000000003fa45af8 8 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Offline Files\Background Synchronization
0x000000003fa7f2c0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\WDI\ResolutionHost
0x000000003fa803a0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\RegisterSearch
0x000000003fa98510 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\DispatchRecoveryTasks
0x000000003faa4398 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\DiskDiagnostic\Microsoft-Windows-DiskDiagnosticResolver
0x000000003faa6758 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\MobilePC\HotStart
0x000000003fac7f80 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Shell\WindowsParentalControlsMigration
0x000000003fae5ef0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\SystemRestore\SR
0x000000003fae6480 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Application Experience\AitAgent
0x000000003faeaeb8 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Windows Media Sharing\UpdateLibrary
0x000000003faf0ba0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Maintenance\WinSAT
0x000000003fafbc40 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Tcpip\IpAddressConflict2
0x000000003fb007e8 8 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Active Directory Rights Management Services Client\AD RMS Rights Policy Template Management (Automated)
0x000000003fb10408 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\CertificateServicesClient\UserTask
0x000000003fb21e88 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\TextServicesFramework\MsCtfMonitor
0x000000003fb37bc0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\User Profile Service\HiveUploadTask
0x000000003fb395d8 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\SqlLiteRecoveryTask
0x000000003fb587c0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Power Efficiency Diagnostics\AnalyzeSystem
0x000000003fb58ec8 8 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\RemoteAssistance\RemoteAssistanceTask
0x000000003fb5b470 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\RecordingRestart
0x000000003fb92038 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Office\OfficeTelemetryAgentLogOn
0x000000003fb92708 8 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\CertificateServicesClient\SystemTask
0x000000003fbaef80 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Tcpip\IpAddressConflict1
0x000000003fbb7e00 8 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\GoogleUpdateTaskMachineCore
0x000000003fbb7f80 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\MUI\LPRemove
0x000000003fc399b8 8 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\At1
0x000000003fc436a8 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\MediaCenterRecoveryTask
0x000000003fc447b0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\KernelCeipTask
0x000000003fc4af80 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\UpdateRecordPath
0x000000003fc64f40 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\SideShow\GadgetManager
0x000000003fc6a498 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\InstallPlayReady
0x000000003fc6c2e8 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\UPnP\UPnPHostConfig
0x000000003fc7a360 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTask
0x000000003fc81f38 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\AppID\VerifiedPublisherCertStoreCheck
0x000000003fc8f518 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\PBDADiscovery
0x000000003fc91ca8 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Office\OfficeTelemetryAgentFallBack
0x000000003fc9b468 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Offline Files\Logon Synchronization
0x000000003fcafc48 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\PvrRecoveryTask
0x000000003fcb7bf0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\MemoryDiagnostic\CorruptionDetector
0x000000003fccab08 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\SideShow\AutoWake
0x000000003fccb520 8 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\WindowsBackup\ConfigNotification
0x000000003fcdb038 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Registry\RegIdleBackup
0x000000003fd1ba10 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\ConfigureInternetTimeService
0x000000003fd44960 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\PeriodicScanRetry
0x000000003fd69730 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\DiskDiagnostic\Microsoft-Windows-DiskDiagnosticDataCollector
0x000000003fd77af0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\OCURDiscovery
0x000000003fd88748 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Location\Notifications
0x000000003fd89c38 8 0 -W-r-- \Device\HarddiskVolume2\Windows\System32\Tasks\OfficeSoftwareProtectionPlatform\SvcRestartTask
0x000000003fd97990 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\UsbCeip
0x000000003fdaa2f0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Ras\MobilityManager
0x000000003fdb4990 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\ehDRMInit
0x000000003fdb7ab8 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\ObjectStoreRecoveryTask
0x000000003fdba358 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\OCURActivate
0x000000003fdbca40 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Defrag\ScheduledDefrag
0x000000003fdc6ab8 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Diagnosis\Scheduled
0x000000003fdfdde0 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Media Center\ActivateWindowsSearch
0x000000003ffde470 2 0 R--r-d \Device\HarddiskVolume2\Windows\System32\Tasks\Microsoft\Windows\Bluetooth\UninstallDeviceTask
remnux@remnux:~/Downloads/target2$
一つ異質なAt1がいるのがわかると思う。このファイルをダンプする。
remnux@remnux:~/Downloads/target2$ vol.py -f target2-6186fe9f.vmss --profile=Win7SP1x86_24000 dumpfiles -Q 0x000000003fc399b8 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
DataSectionObject 0x3fc399b8 None \Device\HarddiskVolume2\Windows\System32\Tasks\At1
remnux@remnux:~/Downloads/target2$ cd out/
remnux@remnux:~/Downloads/target2/out$ ls -la
total 171952
drwxrwxr-x 2 remnux remnux 4096 Jun 17 06:39 .
drwxrwxr-x 3 remnux remnux 4096 Jun 17 06:03 ..
-rw-rw-r-- 1 remnux remnux 176062464 Jun 17 06:24 3048.dmp
-rw-rw-r-- 1 remnux remnux 4096 Jun 17 06:12 file.None.0x85a35da0.dat
-rw-rw-r-- 1 remnux remnux 4096 Jun 17 06:39 file.None.0x85a86af0.dat
この中身を確認する。
remnux@remnux:~/Downloads/target2/out$ cat file.None.0x85a86af0.dat
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.0" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo />
<Triggers>
<TimeTrigger>
<StartBoundary>2015-10-09T08:00:00</StartBoundary>
</TimeTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<UserId>@AtServiceAccount</UserId>
<LogonType>InteractiveTokenOrPassword</LogonType>
<RunLevel>HighestAvailable</RunLevel>
</Principal>
</Principals>
<Actions Context="Author">
<Exec>
<Command>c:\users\gideon\1.bat</Command>
</Exec>
</Actions>
</Task>
remnux@remnux:~/Downloads/target2/out$
<Command>の項目を確認すると答えが見える。
Ans: 1.bat
Machine:POS
What is the malware CNC's server?
まずはimageinfoコマンドでプロファイルを決定する。
remnux@remnux:~/Downloads/pos01$ vol.py -f POS-01-c4e8f786.vmss imageinfo
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86_24000, Win7SP1x86
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : VMWareAddressSpace (Unnamed AS)
AS Layer3 : FileAddressSpace (/home/remnux/Downloads/pos01/POS-01-c4e8f786.vmss)
PAE type : PAE
DTB : 0x185000L
KDBG : 0x82763be8L
Number of Processors : 2
Image Type (Service Pack) : 0
KPCR for CPU 0 : 0x82764c00L
KPCR for CPU 1 : 0x807c5000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2015-10-09 12:52:56 UTC+0000
Image local date and time : 2015-10-09 08:52:56 -0400
remnux@remnux:~/Downloads/pos01$
プロファイルをWin7SP1x86_24000に決定する。
さて、本題に入るか!
netscanコマンドを確認する。
remnux@remnux:~/Downloads/pos01$ vol.py -f POS-01-c4e8f786.vmss --profile=Win7SP1x86_24000 netscan
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Offset(P) Proto Local Address Foreign Address State Pid Owner Created
0x3e00bf50 UDPv4 127.0.0.1:63206 *:* 3544 svchost.exe 2015-10-09 12:18:42 UTC+0000
0x3e15daf0 UDPv4 127.0.0.1:51984 *:* 3376 OUTLOOK.EXE 2015-10-09 06:21:39 UTC+0000
0x3e17f008 UDPv6 ::1:1900 *:* 3544 svchost.exe 2015-10-09 12:18:41 UTC+0000
0x3e2262c0 UDPv4 0.0.0.0:0 *:* 536 lsass.exe 2015-10-09 03:38:56 UTC+0000
0x3e2262c0 UDPv6 :::0 *:* 536 lsass.exe 2015-10-09 03:38:56 UTC+0000
0x3e22aec0 UDPv4 0.0.0.0:0 *:* 536 lsass.exe 2015-10-09 03:38:56 UTC+0000
0x3e236e20 UDPv4 127.0.0.1:56547 *:* 536 lsass.exe 2015-10-09 03:38:56 UTC+0000
0x3e23d6e8 UDPv4 127.0.0.1:61346 *:* 3740 WINWORD.EXE 2015-10-09 05:21:28 UTC+0000
0x3e256580 UDPv4 0.0.0.0:0 *:* 536 lsass.exe 2015-10-09 03:38:56 UTC+0000
0x3e256580 UDPv6 :::0 *:* 536 lsass.exe 2015-10-09 03:38:56 UTC+0000
0x3e2569c0 UDPv4 0.0.0.0:0 *:* 536 lsass.exe 2015-10-09 03:38:56 UTC+0000
0x3e2e4378 UDPv4 127.0.0.1:49798 *:* 900 svchost.exe 2015-10-09 03:39:04 UTC+0000
0x3e33cc10 UDPv4 127.0.0.1:59590 *:* 1116 svchost.exe 2015-10-09 03:38:58 UTC+0000
0x3e3b36c8 UDPv4 0.0.0.0:0 *:* 1008 svchost.exe 2015-10-09 03:39:01 UTC+0000
0x3e3b9d98 UDPv4 0.0.0.0:0 *:* 1008 svchost.exe 2015-10-09 03:39:01 UTC+0000
0x3e3b9d98 UDPv6 :::0 *:* 1008 svchost.exe 2015-10-09 03:39:01 UTC+0000
0x3e0773d0 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 736 svchost.exe
0x3e078af8 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 736 svchost.exe
0x3e078af8 TCPv6 :::135 :::0 LISTENING 736 svchost.exe
0x3e07f008 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 432 wininit.exe
0x3e07f008 TCPv6 :::49152 :::0 LISTENING 432 wininit.exe
0x3e0816c8 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 432 wininit.exe
0x3e092bf0 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 824 svchost.exe
0x3e092bf0 TCPv6 :::49153 :::0 LISTENING 824 svchost.exe
0x3e092d50 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 824 svchost.exe
0x3e0ca170 TCPv4 0.0.0.0:49179 0.0.0.0:0 LISTENING 536 lsass.exe
0x3e0cb028 TCPv4 0.0.0.0:445 0.0.0.0:0 LISTENING 4 System
0x3e0cb028 TCPv6 :::445 :::0 LISTENING 4 System
0x3e0cb0d0 TCPv4 0.0.0.0:49169 0.0.0.0:0 LISTENING 528 services.exe
0x3e0cb240 TCPv4 0.0.0.0:49169 0.0.0.0:0 LISTENING 528 services.exe
0x3e0cb240 TCPv6 :::49169 :::0 LISTENING 528 services.exe
0x3e6cf058 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 900 svchost.exe
0x3e6cf058 TCPv6 :::49154 :::0 LISTENING 900 svchost.exe
0x3e6cf270 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 900 svchost.exe
0x3e0f90e8 TCPv4 10.1.1.10:64532 10.1.1.3:80 ESTABLISHED 3376 OUTLOOK.EXE
0x3e135df8 TCPv4 10.1.1.10:58751 54.84.237.92:80 CLOSE_WAIT 3208 iexplore.exe
0x3e24c7d0 TCPv4 10.1.1.10:49201 23.203.149.112:443 CLOSE_WAIT 2464 jusched.exe
0x3e611b10 TCPv4 -:49887 108.162.232.200:49155 CLOSED 536 lsass.exe
0x3e6fe830 TCPv4 10.1.1.10:64530 10.1.1.3:80 ESTABLISHED 3376 OUTLOOK.EXE
0x3ec374e8 UDPv4 127.0.0.1:65038 *:* -1 2015-10-09 11:05:05 UTC+0000
0x3ecc27f0 UDPv4 10.1.1.10:137 *:* 4 System 2015-10-09 12:18:41 UTC+0000
0x3ef65098 UDPv6 ::1:63204 *:* 3544 svchost.exe 2015-10-09 12:18:42 UTC+0000
0x3f069af8 UDPv4 127.0.0.1:57778 *:* 1 2015-10-09 12:35:49 UTC+0000
0x3f092008 UDPv4 10.1.1.10:63205 *:* 3544 svchost.exe 2015-10-09 12:18:42 UTC+0000
0x3ef37d50 TCPv4 0.0.0.0:49179 0.0.0.0:0 LISTENING 536 lsass.exe
0x3ef37d50 TCPv6 :::49179 :::0 LISTENING 536 lsass.exe
0x3f098a88 TCPv4 10.1.1.10:139 0.0.0.0:0 LISTENING 4 System
0x3ecfc6a0 TCPv4 10.1.1.10:64531 10.1.1.3:80 ESTABLISHED 3376 OUTLOOK.EXE
0x3ed37490 TCPv4 -:58752 23.3.96.251:80 CLOSED 1116 svchost.exe
0x3f12ba78 TCPv4 10.1.1.10:58757 10.1.1.3:443 CLOSED 3376 OUTLOOK.EXE
0x3f1461d8 TCPv4 -:58753 108.162.232.201:80 CLOSED 1116 svchost.exe
0x3f14f988 TCPv4 10.1.1.10:64533 10.1.1.3:80 ESTABLISHED 3376 OUTLOOK.EXE
0x3f4158d0 UDPv4 0.0.0.0:123 *:* 1008 svchost.exe 2015-10-09 12:18:41 UTC+0000
0x3f4158d0 UDPv6 :::123 *:* 1008 svchost.exe 2015-10-09 12:18:41 UTC+0000
0x3f4413a8 UDPv4 10.1.1.10:138 *:* 4 System 2015-10-09 12:18:41 UTC+0000
0x3f4fe358 UDPv4 0.0.0.0:5355 *:* 1116 svchost.exe 2015-10-09 12:18:41 UTC+0000
0x3f5e0120 UDPv4 10.1.1.10:1900 *:* 3544 svchost.exe 2015-10-09 12:18:41 UTC+0000
0x3fcd7f50 UDPv4 0.0.0.0:0 *:* 1116 svchost.exe 2015-10-09 12:18:41 UTC+0000
0x3fcd7f50 UDPv6 :::0 *:* 1116 svchost.exe 2015-10-09 12:18:41 UTC+0000
0x3fce2c68 UDPv4 127.0.0.1:1900 *:* 3544 svchost.exe 2015-10-09 12:18:41 UTC+0000
0x3fd87e50 UDPv4 0.0.0.0:65420 *:* 1116 svchost.exe 2015-10-09 12:36:20 UTC+0000
0x3fde2b28 UDPv4 0.0.0.0:123 *:* 1008 svchost.exe 2015-10-09 12:18:41 UTC+0000
0x3fc35da8 TCPv4 10.1.1.10:58759 10.1.1.2:445 CLOSED 4 System
remnux@remnux:~/Downloads/pos01$
malfindコマンドも確認しておく。
remnux@remnux:~/Downloads/pos01$ vol.py -f POS-01-c4e8f786.vmss --profile=Win7SP1x86_24000 malfind
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Process: svchost.exe Pid: 1828 Address: 0x45f0000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 128, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x00000000045f0000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000045f0010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000045f0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000045f0030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000045f0000 0000 ADD [EAX], AL
0x00000000045f0002 0000 ADD [EAX], AL
0x00000000045f0004 0000 ADD [EAX], AL
0x00000000045f0006 0000 ADD [EAX], AL
0x00000000045f0008 0000 ADD [EAX], AL
0x00000000045f000a 0000 ADD [EAX], AL
0x00000000045f000c 0000 ADD [EAX], AL
0x00000000045f000e 0000 ADD [EAX], AL
0x00000000045f0010 0000 ADD [EAX], AL
0x00000000045f0012 0000 ADD [EAX], AL
0x00000000045f0014 0000 ADD [EAX], AL
0x00000000045f0016 0000 ADD [EAX], AL
0x00000000045f0018 0000 ADD [EAX], AL
0x00000000045f001a 0000 ADD [EAX], AL
0x00000000045f001c 0000 ADD [EAX], AL
0x00000000045f001e 0000 ADD [EAX], AL
0x00000000045f0020 0000 ADD [EAX], AL
0x00000000045f0022 0000 ADD [EAX], AL
0x00000000045f0024 0000 ADD [EAX], AL
0x00000000045f0026 0000 ADD [EAX], AL
0x00000000045f0028 0000 ADD [EAX], AL
0x00000000045f002a 0000 ADD [EAX], AL
0x00000000045f002c 0000 ADD [EAX], AL
0x00000000045f002e 0000 ADD [EAX], AL
0x00000000045f0030 0000 ADD [EAX], AL
0x00000000045f0032 0000 ADD [EAX], AL
0x00000000045f0034 0000 ADD [EAX], AL
0x00000000045f0036 0000 ADD [EAX], AL
0x00000000045f0038 0000 ADD [EAX], AL
0x00000000045f003a 0000 ADD [EAX], AL
0x00000000045f003c 0000 ADD [EAX], AL
0x00000000045f003e 0000 ADD [EAX], AL
Process: explorer.exe Pid: 2200 Address: 0x31e0000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x00000000031e0000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000031e0010 00 00 1e 03 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000031e0020 10 00 1e 03 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000031e0030 20 00 1e 03 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000031e0000 0000 ADD [EAX], AL
0x00000000031e0002 0000 ADD [EAX], AL
0x00000000031e0004 0000 ADD [EAX], AL
0x00000000031e0006 0000 ADD [EAX], AL
0x00000000031e0008 0000 ADD [EAX], AL
0x00000000031e000a 0000 ADD [EAX], AL
0x00000000031e000c 0000 ADD [EAX], AL
0x00000000031e000e 0000 ADD [EAX], AL
0x00000000031e0010 0000 ADD [EAX], AL
0x00000000031e0012 1e PUSH DS
0x00000000031e0013 0300 ADD EAX, [EAX]
0x00000000031e0015 0000 ADD [EAX], AL
0x00000000031e0017 0000 ADD [EAX], AL
0x00000000031e0019 0000 ADD [EAX], AL
0x00000000031e001b 0000 ADD [EAX], AL
0x00000000031e001d 0000 ADD [EAX], AL
0x00000000031e001f 0010 ADD [EAX], DL
0x00000000031e0021 001e ADD [ESI], BL
0x00000000031e0023 0300 ADD EAX, [EAX]
0x00000000031e0025 0000 ADD [EAX], AL
0x00000000031e0027 0000 ADD [EAX], AL
0x00000000031e0029 0000 ADD [EAX], AL
0x00000000031e002b 0000 ADD [EAX], AL
0x00000000031e002d 0000 ADD [EAX], AL
0x00000000031e002f 0020 ADD [EAX], AH
0x00000000031e0031 001e ADD [ESI], BL
0x00000000031e0033 0300 ADD EAX, [EAX]
0x00000000031e0035 0000 ADD [EAX], AL
0x00000000031e0037 0000 ADD [EAX], AL
0x00000000031e0039 0000 ADD [EAX], AL
0x00000000031e003b 0000 ADD [EAX], AL
0x00000000031e003d 0000 ADD [EAX], AL
0x00000000031e003f 00 DB 0x0
Process: WINWORD.EXE Pid: 3740 Address: 0x365b0000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 16, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x00000000365b0000 e3 8f 8c 30 ce ef a7 86 94 db 11 d3 de 6e e0 15 ...0.........n..
0x00000000365b0010 78 a5 6c 88 01 b2 41 db c4 3d 9c 96 78 06 6d a7 x.l...A..=..x.m.
0x00000000365b0020 1f 1a 74 87 70 77 5a 6f 2e 06 6a 9c 78 30 0d 75 ..t.pwZo..j.x0.u
0x00000000365b0030 1b ef d9 71 2e 19 e0 4e a1 1b 79 14 8c 28 cb dd ...q...N..y..(..
0x00000000365b0000 e38f JECXZ 0x365aff91
0x00000000365b0002 8c DB 0x8c
0x00000000365b0003 30ce XOR DH, CL
0x00000000365b0005 ef OUT DX, EAX
0x00000000365b0006 a7 CMPSD
0x00000000365b0007 8694db11d3de6e XCHG [EBX+EBX*8+0x6eded311], DL
0x00000000365b000e e015 LOOPNZ 0x365b0025
0x00000000365b0010 78a5 JS 0x365affb7
0x00000000365b0012 6c INS BYTE [ES:EDI], DX
0x00000000365b0013 8801 MOV [ECX], AL
0x00000000365b0015 b241 MOV DL, 0x41
0x00000000365b0017 dbc4 FCMOVNB ST0, ST4
0x00000000365b0019 3d9c967806 CMP EAX, 0x678969c
0x00000000365b001e 6d INS DWORD [ES:EDI], DX
0x00000000365b001f a7 CMPSD
0x00000000365b0020 1f POP DS
0x00000000365b0021 1a748770 SBB DH, [EDI+EAX*4+0x70]
0x00000000365b0025 775a JA 0x365b0081
0x00000000365b0027 6f OUTS DX, DWORD [ESI]
0x00000000365b0028 2e06 PUSH ES
0x00000000365b002a 6a9c PUSH -0x64
0x00000000365b002c 7830 JS 0x365b005e
0x00000000365b002e 0d751befd9 OR EAX, 0xd9ef1b75
0x00000000365b0033 712e JNO 0x365b0063
0x00000000365b0035 19e0 SBB EAX, ESP
0x00000000365b0037 4e DEC ESI
0x00000000365b0038 a11b79148c MOV EAX, [0x8c14791b]
0x00000000365b003d 28cb SUB BL, CL
0x00000000365b003f dd DB 0xdd
Process: explorer.exe Pid: 1836 Address: 0x530000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x0000000000530000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000000530010 00 00 53 00 00 00 00 00 00 00 00 00 00 00 00 00 ..S.............
0x0000000000530020 10 00 53 00 00 00 00 00 00 00 00 00 00 00 00 00 ..S.............
0x0000000000530030 20 00 53 00 00 00 00 00 00 00 00 00 00 00 00 00 ..S.............
0x0000000000530000 0000 ADD [EAX], AL
0x0000000000530002 0000 ADD [EAX], AL
0x0000000000530004 0000 ADD [EAX], AL
0x0000000000530006 0000 ADD [EAX], AL
0x0000000000530008 0000 ADD [EAX], AL
0x000000000053000a 0000 ADD [EAX], AL
0x000000000053000c 0000 ADD [EAX], AL
0x000000000053000e 0000 ADD [EAX], AL
0x0000000000530010 0000 ADD [EAX], AL
0x0000000000530012 53 PUSH EBX
0x0000000000530013 0000 ADD [EAX], AL
0x0000000000530015 0000 ADD [EAX], AL
0x0000000000530017 0000 ADD [EAX], AL
0x0000000000530019 0000 ADD [EAX], AL
0x000000000053001b 0000 ADD [EAX], AL
0x000000000053001d 0000 ADD [EAX], AL
0x000000000053001f 0010 ADD [EAX], DL
0x0000000000530021 005300 ADD [EBX+0x0], DL
0x0000000000530024 0000 ADD [EAX], AL
0x0000000000530026 0000 ADD [EAX], AL
0x0000000000530028 0000 ADD [EAX], AL
0x000000000053002a 0000 ADD [EAX], AL
0x000000000053002c 0000 ADD [EAX], AL
0x000000000053002e 0000 ADD [EAX], AL
0x0000000000530030 2000 AND [EAX], AL
0x0000000000530032 53 PUSH EBX
0x0000000000530033 0000 ADD [EAX], AL
0x0000000000530035 0000 ADD [EAX], AL
0x0000000000530037 0000 ADD [EAX], AL
0x0000000000530039 0000 ADD [EAX], AL
0x000000000053003b 0000 ADD [EAX], AL
0x000000000053003d 0000 ADD [EAX], AL
0x000000000053003f 00 DB 0x0
Process: explorer.exe Pid: 1836 Address: 0x2b80000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 2, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x0000000002b80000 b0 00 eb 70 b0 01 eb 6c b0 02 eb 68 b0 03 eb 64 ...p...l...h...d
0x0000000002b80010 b0 04 eb 60 b0 05 eb 5c b0 06 eb 58 b0 07 eb 54 ...`...\...X...T
0x0000000002b80020 b0 08 eb 50 b0 09 eb 4c b0 0a eb 48 b0 0b eb 44 ...P...L...H...D
0x0000000002b80030 b0 0c eb 40 b0 0d eb 3c b0 0e eb 38 b0 0f eb 34 ...@...<...8...4
0x0000000002b80000 b000 MOV AL, 0x0
0x0000000002b80002 eb70 JMP 0x2b80074
0x0000000002b80004 b001 MOV AL, 0x1
0x0000000002b80006 eb6c JMP 0x2b80074
0x0000000002b80008 b002 MOV AL, 0x2
0x0000000002b8000a eb68 JMP 0x2b80074
0x0000000002b8000c b003 MOV AL, 0x3
0x0000000002b8000e eb64 JMP 0x2b80074
0x0000000002b80010 b004 MOV AL, 0x4
0x0000000002b80012 eb60 JMP 0x2b80074
0x0000000002b80014 b005 MOV AL, 0x5
0x0000000002b80016 eb5c JMP 0x2b80074
0x0000000002b80018 b006 MOV AL, 0x6
0x0000000002b8001a eb58 JMP 0x2b80074
0x0000000002b8001c b007 MOV AL, 0x7
0x0000000002b8001e eb54 JMP 0x2b80074
0x0000000002b80020 b008 MOV AL, 0x8
0x0000000002b80022 eb50 JMP 0x2b80074
0x0000000002b80024 b009 MOV AL, 0x9
0x0000000002b80026 eb4c JMP 0x2b80074
0x0000000002b80028 b00a MOV AL, 0xa
0x0000000002b8002a eb48 JMP 0x2b80074
0x0000000002b8002c b00b MOV AL, 0xb
0x0000000002b8002e eb44 JMP 0x2b80074
0x0000000002b80030 b00c MOV AL, 0xc
0x0000000002b80032 eb40 JMP 0x2b80074
0x0000000002b80034 b00d MOV AL, 0xd
0x0000000002b80036 eb3c JMP 0x2b80074
0x0000000002b80038 b00e MOV AL, 0xe
0x0000000002b8003a eb38 JMP 0x2b80074
0x0000000002b8003c b00f MOV AL, 0xf
0x0000000002b8003e eb34 JMP 0x2b80074
Process: notepad.exe Pid: 2700 Address: 0x3d70000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x0000000003d70000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000003d70010 00 00 d7 03 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000003d70020 10 00 d7 03 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000003d70030 20 00 d7 03 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000003d70000 0000 ADD [EAX], AL
0x0000000003d70002 0000 ADD [EAX], AL
0x0000000003d70004 0000 ADD [EAX], AL
0x0000000003d70006 0000 ADD [EAX], AL
0x0000000003d70008 0000 ADD [EAX], AL
0x0000000003d7000a 0000 ADD [EAX], AL
0x0000000003d7000c 0000 ADD [EAX], AL
0x0000000003d7000e 0000 ADD [EAX], AL
0x0000000003d70010 0000 ADD [EAX], AL
0x0000000003d70012 d7 XLAT BYTE [EBX+AL]
0x0000000003d70013 0300 ADD EAX, [EAX]
0x0000000003d70015 0000 ADD [EAX], AL
0x0000000003d70017 0000 ADD [EAX], AL
0x0000000003d70019 0000 ADD [EAX], AL
0x0000000003d7001b 0000 ADD [EAX], AL
0x0000000003d7001d 0000 ADD [EAX], AL
0x0000000003d7001f 0010 ADD [EAX], DL
0x0000000003d70021 00d7 ADD BH, DL
0x0000000003d70023 0300 ADD EAX, [EAX]
0x0000000003d70025 0000 ADD [EAX], AL
0x0000000003d70027 0000 ADD [EAX], AL
0x0000000003d70029 0000 ADD [EAX], AL
0x0000000003d7002b 0000 ADD [EAX], AL
0x0000000003d7002d 0000 ADD [EAX], AL
0x0000000003d7002f 0020 ADD [EAX], AH
0x0000000003d70031 00d7 ADD BH, DL
0x0000000003d70033 0300 ADD EAX, [EAX]
0x0000000003d70035 0000 ADD [EAX], AL
0x0000000003d70037 0000 ADD [EAX], AL
0x0000000003d70039 0000 ADD [EAX], AL
0x0000000003d7003b 0000 ADD [EAX], AL
0x0000000003d7003d 0000 ADD [EAX], AL
0x0000000003d7003f 00 DB 0x0
Process: notepad.exe Pid: 2700 Address: 0x3d90000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 2, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x0000000003d90000 b0 00 eb 70 b0 01 eb 6c b0 02 eb 68 b0 03 eb 64 ...p...l...h...d
0x0000000003d90010 b0 04 eb 60 b0 05 eb 5c b0 06 eb 58 b0 07 eb 54 ...`...\...X...T
0x0000000003d90020 b0 08 eb 50 b0 09 eb 4c b0 0a eb 48 b0 0b eb 44 ...P...L...H...D
0x0000000003d90030 b0 0c eb 40 b0 0d eb 3c b0 0e eb 38 b0 0f eb 34 ...@...<...8...4
0x0000000003d90000 b000 MOV AL, 0x0
0x0000000003d90002 eb70 JMP 0x3d90074
0x0000000003d90004 b001 MOV AL, 0x1
0x0000000003d90006 eb6c JMP 0x3d90074
0x0000000003d90008 b002 MOV AL, 0x2
0x0000000003d9000a eb68 JMP 0x3d90074
0x0000000003d9000c b003 MOV AL, 0x3
0x0000000003d9000e eb64 JMP 0x3d90074
0x0000000003d90010 b004 MOV AL, 0x4
0x0000000003d90012 eb60 JMP 0x3d90074
0x0000000003d90014 b005 MOV AL, 0x5
0x0000000003d90016 eb5c JMP 0x3d90074
0x0000000003d90018 b006 MOV AL, 0x6
0x0000000003d9001a eb58 JMP 0x3d90074
0x0000000003d9001c b007 MOV AL, 0x7
0x0000000003d9001e eb54 JMP 0x3d90074
0x0000000003d90020 b008 MOV AL, 0x8
0x0000000003d90022 eb50 JMP 0x3d90074
0x0000000003d90024 b009 MOV AL, 0x9
0x0000000003d90026 eb4c JMP 0x3d90074
0x0000000003d90028 b00a MOV AL, 0xa
0x0000000003d9002a eb48 JMP 0x3d90074
0x0000000003d9002c b00b MOV AL, 0xb
0x0000000003d9002e eb44 JMP 0x3d90074
0x0000000003d90030 b00c MOV AL, 0xc
0x0000000003d90032 eb40 JMP 0x3d90074
0x0000000003d90034 b00d MOV AL, 0xd
0x0000000003d90036 eb3c JMP 0x3d90074
0x0000000003d90038 b00e MOV AL, 0xe
0x0000000003d9003a eb38 JMP 0x3d90074
0x0000000003d9003c b00f MOV AL, 0xf
0x0000000003d9003e eb34 JMP 0x3d90074
Process: OUTLOOK.EXE Pid: 3376 Address: 0x365b0000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 16, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x00000000365b0000 64 74 72 52 00 00 00 00 f8 01 5b 36 00 00 00 00 dtrR......[6....
0x00000000365b0010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000365b0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000365b0030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000365b0000 647472 JZ 0x365b0075
0x00000000365b0003 52 PUSH EDX
0x00000000365b0004 0000 ADD [EAX], AL
0x00000000365b0006 0000 ADD [EAX], AL
0x00000000365b0008 f8 CLC
0x00000000365b0009 015b36 ADD [EBX+0x36], EBX
0x00000000365b000c 0000 ADD [EAX], AL
0x00000000365b000e 0000 ADD [EAX], AL
0x00000000365b0010 0000 ADD [EAX], AL
0x00000000365b0012 0000 ADD [EAX], AL
0x00000000365b0014 0000 ADD [EAX], AL
0x00000000365b0016 0000 ADD [EAX], AL
0x00000000365b0018 0000 ADD [EAX], AL
0x00000000365b001a 0000 ADD [EAX], AL
0x00000000365b001c 0000 ADD [EAX], AL
0x00000000365b001e 0000 ADD [EAX], AL
0x00000000365b0020 0000 ADD [EAX], AL
0x00000000365b0022 0000 ADD [EAX], AL
0x00000000365b0024 0000 ADD [EAX], AL
0x00000000365b0026 0000 ADD [EAX], AL
0x00000000365b0028 0000 ADD [EAX], AL
0x00000000365b002a 0000 ADD [EAX], AL
0x00000000365b002c 0000 ADD [EAX], AL
0x00000000365b002e 0000 ADD [EAX], AL
0x00000000365b0030 0000 ADD [EAX], AL
0x00000000365b0032 0000 ADD [EAX], AL
0x00000000365b0034 0000 ADD [EAX], AL
0x00000000365b0036 0000 ADD [EAX], AL
0x00000000365b0038 0000 ADD [EAX], AL
0x00000000365b003a 0000 ADD [EAX], AL
0x00000000365b003c 0000 ADD [EAX], AL
0x00000000365b003e 0000 ADD [EAX], AL
Process: OUTLOOK.EXE Pid: 3376 Address: 0x90000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 10, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x0000000000090000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000000090010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000000090020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000000090030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000000090000 0000 ADD [EAX], AL
0x0000000000090002 0000 ADD [EAX], AL
0x0000000000090004 0000 ADD [EAX], AL
0x0000000000090006 0000 ADD [EAX], AL
0x0000000000090008 0000 ADD [EAX], AL
0x000000000009000a 0000 ADD [EAX], AL
0x000000000009000c 0000 ADD [EAX], AL
0x000000000009000e 0000 ADD [EAX], AL
0x0000000000090010 0000 ADD [EAX], AL
0x0000000000090012 0000 ADD [EAX], AL
0x0000000000090014 0000 ADD [EAX], AL
0x0000000000090016 0000 ADD [EAX], AL
0x0000000000090018 0000 ADD [EAX], AL
0x000000000009001a 0000 ADD [EAX], AL
0x000000000009001c 0000 ADD [EAX], AL
0x000000000009001e 0000 ADD [EAX], AL
0x0000000000090020 0000 ADD [EAX], AL
0x0000000000090022 0000 ADD [EAX], AL
0x0000000000090024 0000 ADD [EAX], AL
0x0000000000090026 0000 ADD [EAX], AL
0x0000000000090028 0000 ADD [EAX], AL
0x000000000009002a 0000 ADD [EAX], AL
0x000000000009002c 0000 ADD [EAX], AL
0x000000000009002e 0000 ADD [EAX], AL
0x0000000000090030 0000 ADD [EAX], AL
0x0000000000090032 0000 ADD [EAX], AL
0x0000000000090034 0000 ADD [EAX], AL
0x0000000000090036 0000 ADD [EAX], AL
0x0000000000090038 0000 ADD [EAX], AL
0x000000000009003a 0000 ADD [EAX], AL
0x000000000009003c 0000 ADD [EAX], AL
0x000000000009003e 0000 ADD [EAX], AL
Process: OUTLOOK.EXE Pid: 3376 Address: 0x28b0000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 1, PrivateMemory: 1, Protection: 6
0x00000000028b0000 c2 6f fb b8 ab 53 00 01 ee ff ee ff 00 00 00 00 .o...S..........
0x00000000028b0010 a8 00 8b 02 a8 00 8b 02 00 00 8b 02 00 00 8b 02 ................
0x00000000028b0020 40 00 00 00 88 05 8b 02 00 00 8f 02 3f 00 00 00 @...........?...
0x00000000028b0030 01 00 00 00 00 00 00 00 f0 0f 8b 02 f0 0f 8b 02 ................
0x00000000028b0000 c26ffb RET 0xfb6f
0x00000000028b0003 b8ab530001 MOV EAX, 0x10053ab
0x00000000028b0008 ee OUT DX, AL
0x00000000028b0009 ff DB 0xff
0x00000000028b000a ee OUT DX, AL
0x00000000028b000b ff00 INC DWORD [EAX]
0x00000000028b000d 0000 ADD [EAX], AL
0x00000000028b000f 00a8008b02a8 ADD [EAX-0x57fd7500], CH
0x00000000028b0015 008b0200008b ADD [EBX-0x74fffffe], CL
0x00000000028b001b 0200 ADD AL, [EAX]
0x00000000028b001d 008b02400000 ADD [EBX+0x4002], CL
0x00000000028b0023 0088058b0200 ADD [EAX+0x28b05], CL
0x00000000028b0029 008f023f0000 ADD [EDI+0x3f02], CL
0x00000000028b002f 0001 ADD [ECX], AL
0x00000000028b0031 0000 ADD [EAX], AL
0x00000000028b0033 0000 ADD [EAX], AL
0x00000000028b0035 0000 ADD [EAX], AL
0x00000000028b0037 00f0 ADD AL, DH
0x00000000028b0039 0f8b02f00f8b JNP 0x8d9af041
0x00000000028b003f 02 DB 0x2
Process: EXCEL.EXE Pid: 2092 Address: 0x2aa0000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 10, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x0000000002aa0000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000002aa0010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000002aa0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000002aa0030 00 00 00 00 00 00 00 00 56 33 f6 89 70 04 8b 83 ........V3..p...
0x0000000002aa0000 0000 ADD [EAX], AL
0x0000000002aa0002 0000 ADD [EAX], AL
0x0000000002aa0004 0000 ADD [EAX], AL
0x0000000002aa0006 0000 ADD [EAX], AL
0x0000000002aa0008 0000 ADD [EAX], AL
0x0000000002aa000a 0000 ADD [EAX], AL
0x0000000002aa000c 0000 ADD [EAX], AL
0x0000000002aa000e 0000 ADD [EAX], AL
0x0000000002aa0010 0000 ADD [EAX], AL
0x0000000002aa0012 0000 ADD [EAX], AL
0x0000000002aa0014 0000 ADD [EAX], AL
0x0000000002aa0016 0000 ADD [EAX], AL
0x0000000002aa0018 0000 ADD [EAX], AL
0x0000000002aa001a 0000 ADD [EAX], AL
0x0000000002aa001c 0000 ADD [EAX], AL
0x0000000002aa001e 0000 ADD [EAX], AL
0x0000000002aa0020 0000 ADD [EAX], AL
0x0000000002aa0022 0000 ADD [EAX], AL
0x0000000002aa0024 0000 ADD [EAX], AL
0x0000000002aa0026 0000 ADD [EAX], AL
0x0000000002aa0028 0000 ADD [EAX], AL
0x0000000002aa002a 0000 ADD [EAX], AL
0x0000000002aa002c 0000 ADD [EAX], AL
0x0000000002aa002e 0000 ADD [EAX], AL
0x0000000002aa0030 0000 ADD [EAX], AL
0x0000000002aa0032 0000 ADD [EAX], AL
0x0000000002aa0034 0000 ADD [EAX], AL
0x0000000002aa0036 0000 ADD [EAX], AL
0x0000000002aa0038 56 PUSH ESI
0x0000000002aa0039 33f6 XOR ESI, ESI
0x0000000002aa003b 897004 MOV [EAX+0x4], ESI
0x0000000002aa003e 8b DB 0x8b
0x0000000002aa003f 83 DB 0x83
Process: EXCEL.EXE Pid: 2092 Address: 0x3c20000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 1, PrivateMemory: 1, Protection: 6
0x0000000003c20000 a5 d8 7c dc 51 e2 00 01 ee ff ee ff 00 00 00 00 ..|.Q...........
0x0000000003c20010 a8 00 c2 03 a8 00 c2 03 00 00 c2 03 00 00 c2 03 ................
0x0000000003c20020 40 00 00 00 88 05 c2 03 00 00 c6 03 3f 00 00 00 @...........?...
0x0000000003c20030 01 00 00 00 00 00 00 00 f0 0f c2 03 f0 0f c2 03 ................
0x0000000003c20000 a5 MOVSD
0x0000000003c20001 d87cdc51 FDIVR DWORD [ESP+EBX*8+0x51]
0x0000000003c20005 e200 LOOP 0x3c20007
0x0000000003c20007 01ee ADD ESI, EBP
0x0000000003c20009 ff DB 0xff
0x0000000003c2000a ee OUT DX, AL
0x0000000003c2000b ff00 INC DWORD [EAX]
0x0000000003c2000d 0000 ADD [EAX], AL
0x0000000003c2000f 00a800c203a8 ADD [EAX-0x57fc3e00], CH
0x0000000003c20015 00c2 ADD DL, AL
0x0000000003c20017 0300 ADD EAX, [EAX]
0x0000000003c20019 00c2 ADD DL, AL
0x0000000003c2001b 0300 ADD EAX, [EAX]
0x0000000003c2001d 00c2 ADD DL, AL
0x0000000003c2001f 034000 ADD EAX, [EAX+0x0]
0x0000000003c20022 0000 ADD [EAX], AL
0x0000000003c20024 8805c2030000 MOV [0x3c2], AL
0x0000000003c2002a c6033f MOV BYTE [EBX], 0x3f
0x0000000003c2002d 0000 ADD [EAX], AL
0x0000000003c2002f 0001 ADD [ECX], AL
0x0000000003c20031 0000 ADD [EAX], AL
0x0000000003c20033 0000 ADD [EAX], AL
0x0000000003c20035 0000 ADD [EAX], AL
0x0000000003c20037 00f0 ADD AL, DH
0x0000000003c20039 0f DB 0xf
0x0000000003c2003a c203f0 RET 0xf003
0x0000000003c2003d 0f DB 0xf
0x0000000003c2003e c2 DB 0xc2
0x0000000003c2003f 03 DB 0x3
Process: EXCEL.EXE Pid: 2092 Address: 0x365b0000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 16, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x00000000365b0000 64 74 72 52 00 00 00 00 f8 01 5b 36 00 00 00 00 dtrR......[6....
0x00000000365b0010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000365b0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000365b0030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00000000365b0000 647472 JZ 0x365b0075
0x00000000365b0003 52 PUSH EDX
0x00000000365b0004 0000 ADD [EAX], AL
0x00000000365b0006 0000 ADD [EAX], AL
0x00000000365b0008 f8 CLC
0x00000000365b0009 015b36 ADD [EBX+0x36], EBX
0x00000000365b000c 0000 ADD [EAX], AL
0x00000000365b000e 0000 ADD [EAX], AL
0x00000000365b0010 0000 ADD [EAX], AL
0x00000000365b0012 0000 ADD [EAX], AL
0x00000000365b0014 0000 ADD [EAX], AL
0x00000000365b0016 0000 ADD [EAX], AL
0x00000000365b0018 0000 ADD [EAX], AL
0x00000000365b001a 0000 ADD [EAX], AL
0x00000000365b001c 0000 ADD [EAX], AL
0x00000000365b001e 0000 ADD [EAX], AL
0x00000000365b0020 0000 ADD [EAX], AL
0x00000000365b0022 0000 ADD [EAX], AL
0x00000000365b0024 0000 ADD [EAX], AL
0x00000000365b0026 0000 ADD [EAX], AL
0x00000000365b0028 0000 ADD [EAX], AL
0x00000000365b002a 0000 ADD [EAX], AL
0x00000000365b002c 0000 ADD [EAX], AL
0x00000000365b002e 0000 ADD [EAX], AL
0x00000000365b0030 0000 ADD [EAX], AL
0x00000000365b0032 0000 ADD [EAX], AL
0x00000000365b0034 0000 ADD [EAX], AL
0x00000000365b0036 0000 ADD [EAX], AL
0x00000000365b0038 0000 ADD [EAX], AL
0x00000000365b003a 0000 ADD [EAX], AL
0x00000000365b003c 0000 ADD [EAX], AL
0x00000000365b003e 0000 ADD [EAX], AL
Process: iexplore.exe Pid: 3208 Address: 0x50000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 11, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x0000000000050000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 MZ..............
0x0000000000050010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0x0000000000050020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000000050030 00 00 00 00 00 00 00 00 00 00 00 00 d8 00 00 00 ................
0x0000000000050000 4d DEC EBP
0x0000000000050001 5a POP EDX
0x0000000000050002 90 NOP
0x0000000000050003 0003 ADD [EBX], AL
0x0000000000050005 0000 ADD [EAX], AL
0x0000000000050007 000400 ADD [EAX+EAX], AL
0x000000000005000a 0000 ADD [EAX], AL
0x000000000005000c ff DB 0xff
0x000000000005000d ff00 INC DWORD [EAX]
0x000000000005000f 00b800000000 ADD [EAX+0x0], BH
0x0000000000050015 0000 ADD [EAX], AL
0x0000000000050017 004000 ADD [EAX+0x0], AL
0x000000000005001a 0000 ADD [EAX], AL
0x000000000005001c 0000 ADD [EAX], AL
0x000000000005001e 0000 ADD [EAX], AL
0x0000000000050020 0000 ADD [EAX], AL
0x0000000000050022 0000 ADD [EAX], AL
0x0000000000050024 0000 ADD [EAX], AL
0x0000000000050026 0000 ADD [EAX], AL
0x0000000000050028 0000 ADD [EAX], AL
0x000000000005002a 0000 ADD [EAX], AL
0x000000000005002c 0000 ADD [EAX], AL
0x000000000005002e 0000 ADD [EAX], AL
0x0000000000050030 0000 ADD [EAX], AL
0x0000000000050032 0000 ADD [EAX], AL
0x0000000000050034 0000 ADD [EAX], AL
0x0000000000050036 0000 ADD [EAX], AL
0x0000000000050038 0000 ADD [EAX], AL
0x000000000005003a 0000 ADD [EAX], AL
0x000000000005003c d800 FADD DWORD [EAX]
0x000000000005003e 0000 ADD [EAX], AL
Process: iexplore.exe Pid: 3136 Address: 0x50000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 11, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x0000000000050000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 MZ..............
0x0000000000050010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0x0000000000050020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000000050030 00 00 00 00 00 00 00 00 00 00 00 00 d8 00 00 00 ................
0x0000000000050000 4d DEC EBP
0x0000000000050001 5a POP EDX
0x0000000000050002 90 NOP
0x0000000000050003 0003 ADD [EBX], AL
0x0000000000050005 0000 ADD [EAX], AL
0x0000000000050007 000400 ADD [EAX+EAX], AL
0x000000000005000a 0000 ADD [EAX], AL
0x000000000005000c ff DB 0xff
0x000000000005000d ff00 INC DWORD [EAX]
0x000000000005000f 00b800000000 ADD [EAX+0x0], BH
0x0000000000050015 0000 ADD [EAX], AL
0x0000000000050017 004000 ADD [EAX+0x0], AL
0x000000000005001a 0000 ADD [EAX], AL
0x000000000005001c 0000 ADD [EAX], AL
0x000000000005001e 0000 ADD [EAX], AL
0x0000000000050020 0000 ADD [EAX], AL
0x0000000000050022 0000 ADD [EAX], AL
0x0000000000050024 0000 ADD [EAX], AL
0x0000000000050026 0000 ADD [EAX], AL
0x0000000000050028 0000 ADD [EAX], AL
0x000000000005002a 0000 ADD [EAX], AL
0x000000000005002c 0000 ADD [EAX], AL
0x000000000005002e 0000 ADD [EAX], AL
0x0000000000050030 0000 ADD [EAX], AL
0x0000000000050032 0000 ADD [EAX], AL
0x0000000000050034 0000 ADD [EAX], AL
0x0000000000050036 0000 ADD [EAX], AL
0x0000000000050038 0000 ADD [EAX], AL
0x000000000005003a 0000 ADD [EAX], AL
0x000000000005003c d800 FADD DWORD [EAX]
0x000000000005003e 0000 ADD [EAX], AL
remnux@remnux:~/Downloads/pos01$
malfindのPIDtと、netscanで外部の宛先と通信しているPIDを突合する。
PID3208の以下のnetscanの項目が当てはまるはずだ。
0x3e135df8 TCPv4 10.1.1.10:58751 54.84.237.92:80 CLOSE_WAIT 3208 iexplore.exe
Ans: 54.84.237.92
What is the common name of the malware used to infect the POS system?
malfindで見つけたPID3208をダンプする。
※malfindでダンプしている理由は、このプロセスはiexplore.exeで正規のプロセスのように見える。恐らくProcess Injectionを受けていると考えるため、Malciousの部分のみ抜き出すためである。
remnux@remnux:~/Downloads/pos01$ vol.py -f POS-01-c4e8f786.vmss --profile=Win7SP1x86_24000 malfind -p 3208 -D out
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
Process: iexplore.exe Pid: 3208 Address: 0x50000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 11, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x0000000000050000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 MZ..............
0x0000000000050010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0x0000000000050020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x0000000000050030 00 00 00 00 00 00 00 00 00 00 00 00 d8 00 00 00 ................
0x0000000000050000 4d DEC EBP
0x0000000000050001 5a POP EDX
0x0000000000050002 90 NOP
0x0000000000050003 0003 ADD [EBX], AL
0x0000000000050005 0000 ADD [EAX], AL
0x0000000000050007 000400 ADD [EAX+EAX], AL
0x000000000005000a 0000 ADD [EAX], AL
0x000000000005000c ff DB 0xff
0x000000000005000d ff00 INC DWORD [EAX]
0x000000000005000f 00b800000000 ADD [EAX+0x0], BH
0x0000000000050015 0000 ADD [EAX], AL
0x0000000000050017 004000 ADD [EAX+0x0], AL
0x000000000005001a 0000 ADD [EAX], AL
0x000000000005001c 0000 ADD [EAX], AL
0x000000000005001e 0000 ADD [EAX], AL
0x0000000000050020 0000 ADD [EAX], AL
0x0000000000050022 0000 ADD [EAX], AL
0x0000000000050024 0000 ADD [EAX], AL
0x0000000000050026 0000 ADD [EAX], AL
0x0000000000050028 0000 ADD [EAX], AL
0x000000000005002a 0000 ADD [EAX], AL
0x000000000005002c 0000 ADD [EAX], AL
0x000000000005002e 0000 ADD [EAX], AL
0x0000000000050030 0000 ADD [EAX], AL
0x0000000000050032 0000 ADD [EAX], AL
0x0000000000050034 0000 ADD [EAX], AL
0x0000000000050036 0000 ADD [EAX], AL
0x0000000000050038 0000 ADD [EAX], AL
0x000000000005003a 0000 ADD [EAX], AL
0x000000000005003c d800 FADD DWORD [EAX]
0x000000000005003e 0000 ADD [EAX], AL
remnux@remnux:~/Downloads/pos01$
sha256でハッシュ値を取る。
remnux@remnux:~/Downloads/pos01/out$ sha256sum process.0x83f324d8.0x50000.dmp
bf067ffc68f3f1c23bc3402e4494d83e738cc6e158c4f57176b4f5def412e056 process.0x83f324d8.0x50000.dmp
remnux@remnux:~/Downloads/pos01/out$
このファイルハッシュ値をVirusTotalで検索する。

回答が見えてる!
Ans: Dexter
In the POS malware whitelist. What application was specific to Allsafecybersec?
このファイルでexeでフィルタる。
remnux@remnux:~/Downloads/pos01/out$ strings process.0x83f324d8.0x50000.dmp | grep .exe
allsafe_protector.exe
svchost.exe
iexplore.exe
explorer.exe
smss.exe
csrss.exe
winlogon.exe
lsass.exe
spoolsv.exe
alg.exe
wuauclt.exe
.exe;.bat;.reg;.vbs;
iexplore.exe
lHost.exe
remnux@remnux:~/Downloads/pos01/out$
答えが分かった。
Ans: allsafe_protector.exe
What is the name of the file the malware was initially launched from?
これはiehistoryのコマンドを打っていれば見つけることができる。
remnux@remnux:~/Downloads/pos01$ vol.py -f POS-01-c4e8f786.vmss --profile=Win7SP1x86_24000 iehistory
Volatility Foundation Volatility Framework 2.6.1
/usr/local/lib/python2.7/dist-packages/volatility/plugins/community/YingLi/ssh_agent_key.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
from cryptography.hazmat.backends.openssl import backend
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1c05000
Record length: 0x100
Location: Visited: pos@file:///C:/Users/Administrator/Desktop/AllSafeCustomers.csv
Last modified: 2015-10-09 05:30:00 UTC+0000
Last accessed: 2015-10-09 05:30:00 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0xb4
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1c05100
Record length: 0x100
Location: Visited: pos@file:///C:/Users/Administrator/Desktop/AllSafeCustomerData.txt
Last modified: 2015-10-09 05:30:12 UTC+0000
Last accessed: 2015-10-09 05:30:12 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0xb4
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1c05200
Record length: 0x100
Location: Visited: pos@file:///C:/Users/Administrator/Desktop/AllSafeCustomerData.csv
Last modified: 2015-10-09 09:47:21 UTC+0000
Last accessed: 2015-10-09 09:47:21 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0xb4
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1c05300
Record length: 0x100
Location: Visited: pos@http://54.84.237.92/allsafe_update.exe
Last modified: 2015-10-09 12:35:55 UTC+0000
Last accessed: 2015-10-09 12:35:55 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x9c
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1c05400
Record length: 0x100
Location: Visited: pos@http://54.84.237.92/allsafe_update.exe
Last modified: 2015-10-09 12:35:57 UTC+0000
Last accessed: 2015-10-09 12:35:57 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x9c
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1db5000
Record length: 0x100
Location: :2015100920151010: pos@file:///C:/Users/Administrator/Desktop/AllSafeCustomers.csv
Last modified: 2015-10-09 01:30:00 UTC+0000
Last accessed: 2015-10-09 05:30:00 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x0
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1db5100
Record length: 0x100
Location: :2015100920151010: pos@:Host: Computer
Last modified: 2015-10-09 01:30:00 UTC+0000
Last accessed: 2015-10-09 05:30:00 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x0
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1db5200
Record length: 0x100
Location: :2015100920151010: pos@file:///C:/Users/Administrator/Desktop/AllSafeCustomerData.txt
Last modified: 2015-10-09 01:30:12 UTC+0000
Last accessed: 2015-10-09 05:30:12 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x0
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1db5300
Record length: 0x100
Location: :2015100920151010: pos@file:///C:/Users/Administrator/Desktop/AllSafeCustomerData.csv
Last modified: 2015-10-09 05:47:21 UTC+0000
Last accessed: 2015-10-09 09:47:21 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x0
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1db5400
Record length: 0x100
Location: :2015100920151010: pos@http://54.84.237.92/allsafe_update.exe
Last modified: 2015-10-09 08:35:55 UTC+0000
Last accessed: 2015-10-09 12:35:55 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x0
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1db5500
Record length: 0x100
Location: :2015100920151010: pos@:Host: 54.84.237.92
Last modified: 2015-10-09 08:35:55 UTC+0000
Last accessed: 2015-10-09 12:35:55 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x0
**************************************************
Process: 1836 explorer.exe
Cache type "URL " at 0x1db5600
Record length: 0x100
Location: :2015100920151010: pos@http://54.84.237.92/allsafe_update.exe
Last modified: 2015-10-09 08:35:57 UTC+0000
Last accessed: 2015-10-09 12:35:57 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x0
**************************************************
Process: 1836 explorer.exe
Cache type "DEST" at 0x510182b
Last modified: 2015-10-09 08:35:57 UTC+0000
Last accessed: 2015-10-09 12:35:58 UTC+0000
URL: pos@http://54.84.237.92/allsafe_update.exe
**************************************************
Process: 1836 explorer.exe
Cache type "DEST" at 0x5101b93
Last modified: 2015-10-09 08:35:57 UTC+0000
Last accessed: 2015-10-09 12:35:58 UTC+0000
URL: pos@http://54.84.237.92/allsafe_update.exe
**************************************************
Process: 3376 OUTLOOK.EXE
Cache type "URL " at 0x3a85000
Record length: 0x100
Location: Visited: pos@file:///C:/Users/Administrator/Desktop/AllSafeCustomers.csv
Last modified: 2015-10-09 05:30:00 UTC+0000
Last accessed: 2015-10-09 05:30:00 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0xb4
**************************************************
Process: 3376 OUTLOOK.EXE
Cache type "URL " at 0x3a85100
Record length: 0x100
Location: Visited: pos@file:///C:/Users/Administrator/Desktop/AllSafeCustomerData.txt
Last modified: 2015-10-09 05:30:12 UTC+0000
Last accessed: 2015-10-09 05:30:12 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0xb4
**************************************************
Process: 3376 OUTLOOK.EXE
Cache type "URL " at 0x3a85200
Record length: 0x100
Location: Visited: pos@file:///C:/Users/Administrator/Desktop/AllSafeCustomerData.csv
Last modified: 2015-10-09 09:47:21 UTC+0000
Last accessed: 2015-10-09 09:47:21 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0xb4
**************************************************
Process: 3376 OUTLOOK.EXE
Cache type "URL " at 0x3a85300
Record length: 0x100
Location: Visited: pos@http://54.84.237.92/allsafe_update.exe
Last modified: 2015-10-09 12:35:55 UTC+0000
Last accessed: 2015-10-09 12:35:55 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x9c
**************************************************
Process: 3376 OUTLOOK.EXE
Cache type "URL " at 0x3a85400
Record length: 0x100
Location: Visited: pos@http://54.84.237.92/allsafe_update.exe
Last modified: 2015-10-09 12:35:57 UTC+0000
Last accessed: 2015-10-09 12:35:57 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0x9c
remnux@remnux:~/Downloads/pos01$
後半にOUTLOOK.EXEのプロセスでみることが可能。
Ans: allsafe_update.exe