localstack install
Docker Desktop for Windowsインストールする
左ペインExtentions → LocalStackを検索、install
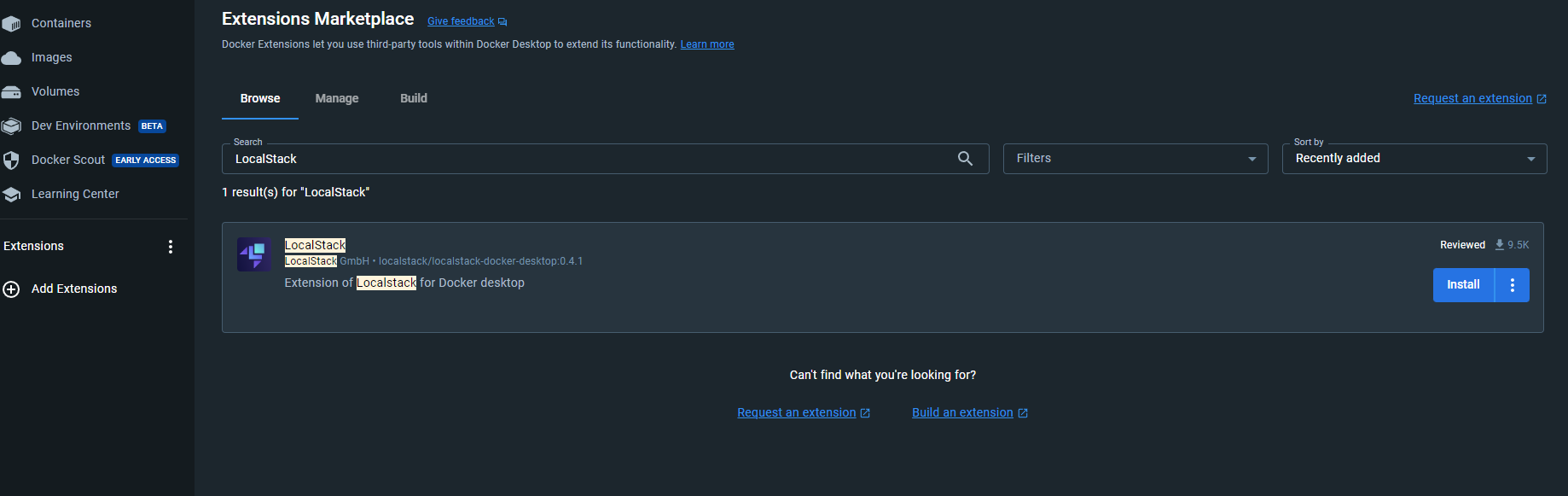
右上の歯車の設定からresource→wsl integration
使用しているOSをenableしてapply & restart
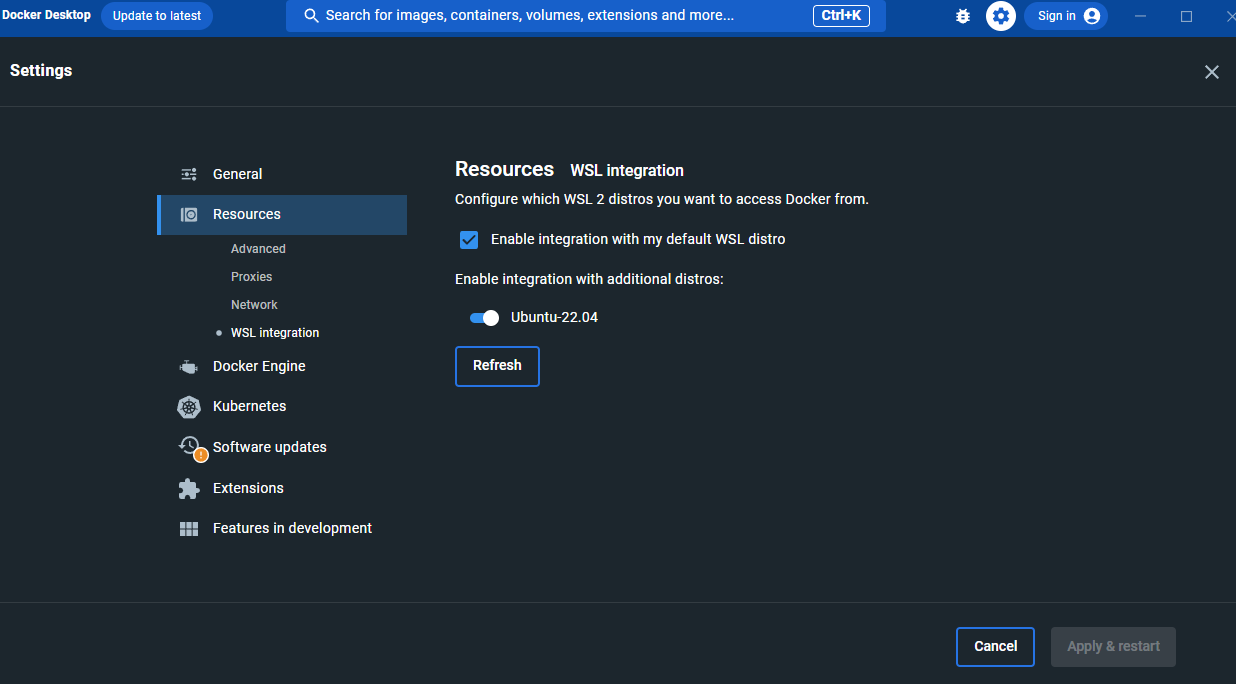
Extensionsからshow docker extensions system containersにチェックを入れとく
awscli pip awslocal localstack インストール
sudo apt install awscli
aws --version
sudo apt install pip
pip --version
sudo pip install awscli-local
awslocal --version
pip install localstack
localstack start押下
localstackが起動したら試しにaws cliでdescribe-vpcsしてみる。
デフォのvpcがいる
awslocal ec2 describe-vpcs
{
"Vpcs": [
{
"CidrBlock": "172.31.0.0/16",
"DhcpOptionsId": "dopt-7a8b9c2d",
"State": "available",
"VpcId": "vpc-53ac5cd0",
"OwnerId": "000000000000",
"InstanceTenancy": "default",
"Ipv6CidrBlockAssociationSet": [],
"CidrBlockAssociationSet": [
{
"AssociationId": "vpc-cidr-assoc-19582a07",
"CidrBlock": "172.31.0.0/16",
"CidrBlockState": {
"State": "associated"
}
}
],
"IsDefault": true,
"Tags": []
}
]
}
作成できるリソースの一覧表示
curl -s "http://127.0.0.1:4566/health" | jq .
{
"services": {
"acm": "available",
"apigateway": "available",
"cloudformation": "available",
"cloudwatch": "available",
"config": "available",
"dynamodb": "available",
"dynamodbstreams": "available",
"ec2": "running",
"es": "available",
"events": "available",
"firehose": "available",
"iam": "available",
"kinesis": "available",
"kms": "available",
"lambda": "available",
"logs": "available",
"opensearch": "available",
"redshift": "available",
"resource-groups": "available",
"resourcegroupstaggingapi": "available",
"route53": "available",
"route53resolver": "available",
"s3": "running",
"s3control": "available",
"scheduler": "available",
"secretsmanager": "available",
"ses": "available",
"sns": "available",
"sqs": "available",
"ssm": "available",
"stepfunctions": "available",
"sts": "available",
"support": "available",
"swf": "available",
"transcribe": "available"
},
"version": "2.2.1.dev"
}
terraform
main.tfに以下を追記
resource-groupsだけresourcegroupsにしないとUnsupported argumentになるので変更
endpointsのリストは以下
https://registry.terraform.io/providers/hashicorp/aws/latest/docs/guides/custom-service-endpoints
# backend
terraform {
backend "local" {}
}
# provider
provider "aws" {
access_key = "mock_access_key"
region = "us-east-1"
s3_use_path_style = true
secret_key = "mock_secret_key"
skip_credentials_validation = true
skip_metadata_api_check = true
skip_requesting_account_id = true
endpoints {
acm = "http://localhost:4566"
apigateway = "http://localhost:4566"
cloudformation = "http://localhost:4566"
cloudwatch = "http://localhost:4566"
config = "http://localhost:4566"
dynamodb = "http://localhost:4566"
dynamodbstreams = "http://localhost:4566"
ec2 = "http://localhost:4566"
es = "http://localhost:4566"
events = "http://localhost:4566"
firehose = "http://localhost:4566"
iam = "http://localhost:4566"
kinesis = "http://localhost:4566"
kms = "http://localhost:4566"
lambda = "http://localhost:4566"
logs = "http://localhost:4566"
opensearch = "http://localhost:4566"
redshift = "http://localhost:4566"
resourcegroups = "http://localhost:4566"
resourcegroupstaggingapi = "http://localhost:4566"
route53 = "http://localhost:4566"
route53resolver = "http://localhost:4566"
s3 = "http://localhost:4566"
s3control = "http://localhost:4566"
scheduler = "http://localhost:4566"
secretsmanager = "http://localhost:4566"
ses = "http://localhost:4566"
sns = "http://localhost:4566"
sqs = "http://localhost:4566"
ssm = "http://localhost:4566"
stepfunctions = "http://localhost:4566"
sts = "http://localhost:4566"
support = "http://localhost:4566"
swf = "http://localhost:4566"
transcribe = "http://localhost:4566"
}
}
以下をtrueにするとterraformの向き先がlocalstackになるみたい
s3_use_path_style = true
skip_credentials_validation = true
skip_metadata_api_check = true
skip_requesting_account_id = true
terraform init
terraform init
Initializing the backend...
Successfully configured the backend "local"! Terraform will automatically
use this backend unless the backend configuration changes.
Initializing provider plugins...
- Reusing previous version of hashicorp/aws from the dependency lock file
- Installing hashicorp/aws v4.65.0...
- Installed hashicorp/aws v4.65.0 (signed by HashiCorp)
Terraform has been successfully initialized!
You may now begin working with Terraform. Try running "terraform plan" to see
any changes that are required for your infrastructure. All Terraform commands
should now work.
If you ever set or change modules or backend configuration for Terraform,
rerun this command to reinitialize your working directory. If you forget, other
commands will detect it and remind you to do so if necessary.
適当にs3のtfを作る
resource "aws_s3_bucket" "test-bucket" {
bucket = "test-bucket"
}
terraform plan
terraform plan
Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# aws_s3_bucket.test-bucket will be created
+ resource "aws_s3_bucket" "test-bucket" {
+ acceleration_status = (known after apply)
+ acl = (known after apply)
+ arn = (known after apply)
+ bucket = "test-bucket"
+ bucket_domain_name = (known after apply)
+ bucket_prefix = (known after apply)
+ bucket_regional_domain_name = (known after apply)
+ force_destroy = false
+ hosted_zone_id = (known after apply)
+ id = (known after apply)
+ object_lock_enabled = (known after apply)
+ policy = (known after apply)
+ region = (known after apply)
+ request_payer = (known after apply)
+ tags_all = (known after apply)
+ website_domain = (known after apply)
+ website_endpoint = (known after apply)
}
Plan: 1 to add, 0 to change, 0 to destroy.
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
Note: You didn't use the -out option to save this plan, so Terraform can't guarantee to take exactly these actions if you run "terraform apply" now.
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
Note: You didn't use the -out option to save this plan, so Terraform can't guarantee to take exactly these actions if
you run "terraform apply" now.
applyしてみる
terraform apply
Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# aws_s3_bucket.test-bucket will be created
+ resource "aws_s3_bucket" "test-bucket" {
+ acceleration_status = (known after apply)
+ acl = (known after apply)
+ arn = (known after apply)
+ bucket = "test-bucket"
+ bucket_domain_name = (known after apply)
+ bucket_prefix = (known after apply)
+ bucket_regional_domain_name = (known after apply)
+ force_destroy = false
+ hosted_zone_id = (known after apply)
+ id = (known after apply)
+ object_lock_enabled = (known after apply)
+ policy = (known after apply)
+ region = (known after apply)
+ request_payer = (known after apply)
+ tags_all = (known after apply)
+ website_domain = (known after apply)
+ website_endpoint = (known after apply)
}
Plan: 1 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
aws_s3_bucket.test-bucket: Creating...
aws_s3_bucket.test-bucket: Creation complete after 2s [id=test-bucket]
Apply complete! Resources: 1 added, 0 changed, 0 destroyed.
s3 lsしてみる
awslocal s3 ls
2023-08-23 19:43:00 test-bucket
vpcもつくってみる
resource "aws_vpc" "main" {
cidr_block = "10.0.0.0/16"
}
terraform apply
terraform apply
aws_s3_bucket.test-bucket: Refreshing state... [id=test-bucket]
Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# aws_vpc.main will be created
+ resource "aws_vpc" "main" {
+ arn = (known after apply)
+ cidr_block = "10.0.0.0/16"
+ default_network_acl_id = (known after apply)
+ default_route_table_id = (known after apply)
+ default_security_group_id = (known after apply)
+ dhcp_options_id = (known after apply)
+ enable_classiclink = (known after apply)
+ enable_classiclink_dns_support = (known after apply)
+ enable_dns_hostnames = (known after apply)
+ enable_dns_support = true
+ enable_network_address_usage_metrics = (known after apply)
+ id = (known after apply)
+ instance_tenancy = "default"
+ ipv6_association_id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ ipv6_cidr_block_network_border_group = (known after apply)
+ main_route_table_id = (known after apply)
+ owner_id = (known after apply)
+ tags_all = (known after apply)
}
Plan: 1 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
aws_vpc.main: Creating...
aws_vpc.main: Creation complete after 0s [id=vpc-05f65a3e]
Apply complete! Resources: 1 added, 0 changed, 0 destroyed.
一覧に表示されない、、、
awslocal ec2 describe-vpcs
{
"Vpcs": [
{
"CidrBlock": "172.31.0.0/16",
"DhcpOptionsId": "dopt-7a8b9c2d",
"State": "available",
"VpcId": "vpc-53ac5cd0",
"OwnerId": "000000000000",
"InstanceTenancy": "default",
"Ipv6CidrBlockAssociationSet": [],
"CidrBlockAssociationSet": [
{
"AssociationId": "vpc-cidr-assoc-19582a07",
"CidrBlock": "172.31.0.0/16",
"CidrBlockState": {
"State": "associated"
}
}
],
"IsDefault": true,
"Tags": []
}
]
}
リージョン指定でdescribeしたら見れた
awslocal ec2 describe-vpcs --region us-east-1
{
"Vpcs": [
{
"CidrBlock": "172.31.0.0/16",
"DhcpOptionsId": "dopt-7a8b9c2d",
"State": "available",
"VpcId": "vpc-979681a9",
"OwnerId": "000000000000",
"InstanceTenancy": "default",
"Ipv6CidrBlockAssociationSet": [],
"CidrBlockAssociationSet": [
{
"AssociationId": "vpc-cidr-assoc-18d5b19e",
"CidrBlock": "172.31.0.0/16",
"CidrBlockState": {
"State": "associated"
}
}
],
"IsDefault": true,
"Tags": []
},
{
"CidrBlock": "10.0.0.0/16",
"DhcpOptionsId": "dopt-7a8b9c2d",
"State": "available",
"VpcId": "vpc-d024653d",
"OwnerId": "000000000000",
"InstanceTenancy": "default",
"Ipv6CidrBlockAssociationSet": [],
"CidrBlockAssociationSet": [
{
"AssociationId": "vpc-cidr-assoc-83f9a15d",
"CidrBlock": "10.0.0.0/16",
"CidrBlockState": {
"State": "associated"
}
}
],
"IsDefault": false,
"Tags": []
}
]
}
terraform destroy
terraform destroy
aws_vpc.main: Refreshing state... [id=vpc-91c2af85]
aws_s3_bucket.test-bucket: Refreshing state... [id=test-bucket]
Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following symbols:
- destroy
Terraform will perform the following actions:
# aws_s3_bucket.test-bucket will be destroyed
- resource "aws_s3_bucket" "test-bucket" {
- arn = "arn:aws:s3:::test-bucket" -> null
- bucket = "test-bucket" -> null
- bucket_domain_name = "test-bucket.s3.amazonaws.com" -> null
- bucket_regional_domain_name = "test-bucket.s3.amazonaws.com" -> null
- force_destroy = false -> null
- hosted_zone_id = "Z3AQBSTGFYJSTF" -> null
- id = "test-bucket" -> null
- object_lock_enabled = false -> null
- region = "us-east-1" -> null
- request_payer = "BucketOwner" -> null
- tags = {} -> null
- tags_all = {} -> null
- grant {
- id = "75aa57f09aa0c8caeab4f8c24e99d10f8e7faeebf76c078efc7c6caea54ba06a" -> null
- permissions = [
- "FULL_CONTROL",
] -> null
- type = "CanonicalUser" -> null
}
- versioning {
- enabled = false -> null
- mfa_delete = false -> null
}
}
# aws_vpc.main will be destroyed
- resource "aws_vpc" "main" {
- arn = "arn:aws:ec2:us-east-1:000000000000:vpc/vpc-91c2af85" -> null
- assign_generated_ipv6_cidr_block = false -> null
- cidr_block = "10.0.0.0/16" -> null
- default_network_acl_id = "acl-66d5558b" -> null
- default_route_table_id = "rtb-9432c04d" -> null
- default_security_group_id = "sg-5ee10ba16ba387283" -> null
- dhcp_options_id = "dopt-7a8b9c2d" -> null
- enable_classiclink = false -> null
- enable_classiclink_dns_support = false -> null
- enable_dns_hostnames = false -> null
- enable_dns_support = true -> null
- enable_network_address_usage_metrics = false -> null
- id = "vpc-91c2af85" -> null
- instance_tenancy = "default" -> null
- ipv6_netmask_length = 0 -> null
- main_route_table_id = "rtb-9432c04d" -> null
- owner_id = "000000000000" -> null
- tags = {} -> null
- tags_all = {} -> null
}
Plan: 0 to add, 0 to change, 2 to destroy.
Do you really want to destroy all resources?
Terraform will destroy all your managed infrastructure, as shown above.
There is no undo. Only 'yes' will be accepted to confirm.
Enter a value: yes
aws_vpc.main: Destroying... [id=vpc-91c2af85]
aws_s3_bucket.test-bucket: Destroying... [id=test-bucket]
aws_s3_bucket.test-bucket: Destruction complete after 0s
aws_vpc.main: Destruction complete after 0s
Destroy complete! Resources: 2 destroyed.