はじめに
Linuxサーバで実行されたiptablesによるパケットフィルタ設定の操作ログを分析する機会があったのでその備忘録。ログはElasticsearchとAuditbeatの構成で採取しました。
利用するソフトウェア
- OS: Ubuntu 18.04
- Elasticsearch (7.3.2)
- Kibana (7.3.2)
- Auditbeat (7.4.2)
- Apache 2.4.29
- python3 -m http.server
想定する操作ログのシナリオ
- 管理アクセス(想定)のTCPポート(Apache2: 192.168.0.10:80)をiptalbesでブロック(drop)する
- 代わりに別TCPポートでリスニングするアプリケーション(想定)を起動する
- そのアプリケーションのTCPポート(python -m http.server 192.168.0.10:8000)をiptablesで許可(pass/allow)する
Auditbeatの設定
iptablesが呼び出すシステムコール
まずサーバ上でAuditの監視対象を確認するためにiptablesコマンドが呼び出すシステムコールを列挙。
> strace -t -x iptables -A INPUT -p tcp --dport 80 -j DROP
...(略)
14:11:05 socket(AF_INET, SOCK_RAW, IPPROTO_RAW) = 4
14:11:05 fcntl(4, F_SETFD, FD_CLOEXEC) = 0
14:11:05 getsockopt(4, SOL_IP, IPT_SO_GET_INFO, "\x66\x69\x6c\x74\x65\x72\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"..., [84]) = 0
14:11:05 getsockopt(4, SOL_IP, IPT_SO_GET_ENTRIES, "\x66\x69\x6c\x74\x65\x72\x00\x20\x53\x65\x63\x75\x72\x69\x74\x79\x20\x50\x61\x79\x6c\x6f\x61\x64\x0a\x72\x6f\x68\x63\x09\x31\x34"..., [1072]) = 0
14:11:05 setsockopt(4, SOL_IP, IPT_SO_SET_REPLACE, "\x66\x69\x6c\x74\x65\x72\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"..., 1328) = 0
14:11:05 setsockopt(4, SOL_IP, IPT_SO_SET_ADD_COUNTERS, "\x66\x69\x6c\x74\x65\x72\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"..., 152) = 0
14:11:05 close(4) = 0
...(略)
※補足: iptalbesの実体は**/sbin/xtables-multi**
ということで以下のシステムコールを監視してみます。
- socket
- getsockopt
- setsockopt
代わりに実行するアプリケーションの接続監視
ここでは単純にpython3のhttp.serverを起動してみます。iptablesと同様にAuditbeatのAuditルールを作成しますが、サーバ側ソケット関連の以下のシステムコールを追加します。
- listen
- bind
- accept/accept4
※補足:Auditbeatのサンプル設定ではaccept4がないようです。
Auditbeat設定の監視ルール
auditd moduleへ以下のルールを追加してみます。書式はauditdと同じです。
-a always,exit -F arch=b64 -S socket,accept,accept4,listen,setsockopt,getsockopt,bind -F key=audit-iptables
※補足:実行ファイル名を**exe=...**で追加指定してもよいかもしれません。
###################### Auditbeat Configuration Example #########################
# This is an example configuration file highlighting only the most common
# options. The auditbeat.reference.yml file from the same directory contains all
# the supported options with more comments. You can use it as a reference.
#
# You can find the full configuration reference here:
# https://www.elastic.co/guide/en/beats/auditbeat/index.html
# ========================== Modules configuration =============================
auditbeat.modules:
- module: auditd
# Load audit rules from separate files. Same format as audit.rules(7).
audit_rule_files: [ '${path.config}/audit.rules.d/*.conf' ]
audit_rules: |
## Define audit rules here.
## Create file watches (-w) or syscall audits (-a or -A). Uncomment these
## examples or add your own rules.
...
## External access (warning: these can be expensive to audit).
#-a always,exit -F arch=b64 -S accept,bind,connect -F key=external-access
## iptables exec test (warning: these can be expensive to audit). ★★★
-a always,exit -F arch=b64 -S execve,execveat -k exec
-a always,exit -F arch=b64 -S socket,accept,accept4,listen,setsockopt,getsockopt,bind -F key=audit-iptables ★★★
...
設定内容を確認。
> auditbeat test config
OK
ログを採取
# Apache2を起動
> systemctl start apache2
# iptables操作
> iptables -A INPUT -p tcp --dport 80 -j DROP
> iptables -A INPUT -p tcp --dport 8000 -j ACCEPT
# 代わりのアプリケーションを起動
> python3 -m http.server 8000
# 管理サーバポート(想定)へのアクセス
> curl -XGET http://192.168.1.10
curl: (7) Failed to connect to 192.168.1.10 port 80: Connection refused
# 代わりに起動した別アプリケーションポート(想定)へのアクセス
> curl -XGET http://192.168.1.10:8000
...
Kibanaで確認
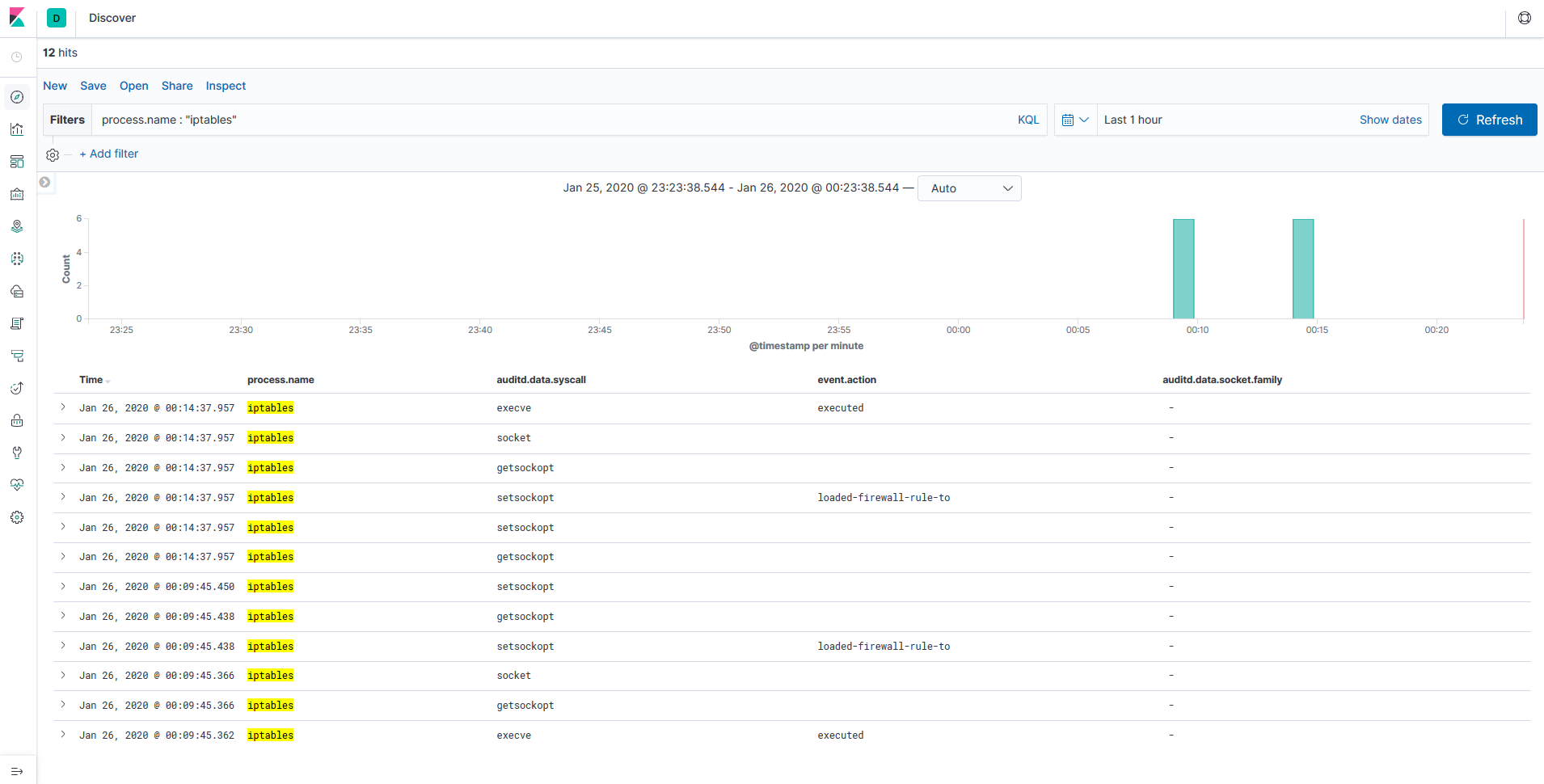 iptablesの設定操作は**event.action: loaded-firewall-rule-to**というラベルになるようですね!
また**execve**でiptables実行時に指定されたコマンド引数も記録されています(**おまけ(2)**を参照)。
iptablesの設定操作は**event.action: loaded-firewall-rule-to**というラベルになるようですね!
また**execve**でiptables実行時に指定されたコマンド引数も記録されています(**おまけ(2)**を参照)。
 listenおよびaccept/accept4のシステムコール呼び出しはそれぞれ**event.action: listen-for-connections**および**event.action: accepted-connection-from**というラベルなるようです。**source.ip**や**source.port**で接続元の情報も採取できています(**おまけ(2)**を参照)。
listenおよびaccept/accept4のシステムコール呼び出しはそれぞれ**event.action: listen-for-connections**および**event.action: accepted-connection-from**というラベルなるようです。**source.ip**や**source.port**で接続元の情報も採取できています(**おまけ(2)**を参照)。

まとめ
iptables実行をログ参照できました。
同様にして他にも例えばiptablesによるポートフォーワードを利用するMITM実行ログの参照などへも応用できそうです。
おまけ(1):AuditbeatのEventアクションの一覧
Elastic Common Schema (ECS)のEventオブジェクトのevent.actionに設定されるラベルは、LinuxカーネルのauditからNETLINKインターフェースで取得されるメッセージタイプをマッピングしたものです。Kibanaのevent.actionなどのフィールドとLinux auditのマッピングを参照したい際など以下で参照できます。
-
Linuxカーネルのaudit NETLINKメッセージタイプ定義
linux/include/uapi/linux/audit.h -
Auditbeatのマッピング定義
go-libaudit/auparse/zaudit_msg_types.go
go-libaudit/aucoalesce/normalizations.yaml
おまけ(2):採取されたログサンプル (Kibana)
{
"_index": "auditbeat-7.4.2-20xx.xx.xx-000001",
"_type": "_doc",
"_id": "xxxxxxxxxxxxxxxxxxxxxxx",
"_version": 1,
"_score": null,
"_source": {
"@timestamp": "2020-01-25T15:09:45.362Z",
"event": {
"outcome": "success",
"module": "auditd",
"category": "audit-rule",
"action": "executed"
},
"user": {
"name": "root",
"filesystem": {
"group": {
"id": "0",
"name": "root"
},
"id": "0",
"name": "root"
},
"saved": {
"name": "root",
"id": "0",
"group": {
"id": "0",
"name": "root"
}
},
"effective": {
"name": "root",
"id": "0",
"group": {
"name": "root",
"id": "0"
}
},
"audit": {
"id": "1000",
"name": "xxxxxxxxx"
},
"group": {
"id": "0",
"name": "root"
},
"id": "0"
},
"file": {
"gid": "0",
"owner": "root",
"group": "root",
"path": "/sbin/iptables",
"device": "00:00",
"inode": "786668",
"mode": "0755",
"uid": "0"
},
"host": {
"architecture": "x86_64",
"os": {
"version": "18.04.1 LTS (Bionic Beaver)",
"family": "debian",
"name": "Ubuntu",
"kernel": "4.15.0-74-generic",
"codename": "bionic",
"platform": "ubuntu"
},
"id": "xxxxxxxxx",
"containerized": false,
"name": "dmz_server",
"hostname": "dmz_server"
},
"auditd": {
"paths": [
{
"ouid": "0",
"cap_fi": "0000000000000000",
"dev": "08:02",
"name": "/sbin/iptables",
"nametype": "NORMAL",
"ogid": "0",
"mode": "0100755",
"rdev": "00:00",
"cap_fe": "0",
"cap_fp": "0000000000000000",
"cap_fver": "0",
"inode": "786668",
"item": "0"
},
{
"cap_fe": "0",
"cap_fp": "0000000000000000",
"cap_fver": "0",
"item": "1",
"mode": "0100755",
"ogid": "0",
"rdev": "00:00",
"cap_fi": "0000000000000000",
"dev": "08:02",
"inode": "136740",
"name": "/lib64/ld-linux-x86-64.so.2",
"nametype": "NORMAL",
"ouid": "0"
}
],
"message_type": "syscall",
"sequence": 406,
"result": "success",
"data": {
"exit": "0",
"a0": "55a151eef970",
"argc": "9",
"a1": "55a151ec9de0",
"a2": "55a151ece9a0",
"tty": "tty1",
"a3": "8",
"syscall": "execve",
"arch": "x86_64"
},
"session": "1",
"summary": {
"how": "/sbin/xtables-multi",
"actor": {
"secondary": "root",
"primary": "xxxxxxxxx"
},
"object": {
"primary": "/sbin/iptables",
"type": "file"
}
}
},
"process": {
"executable": "/sbin/xtables-multi",
"working_directory": "/home/xxxxxxxxx",
"args": [
"iptables",
"-A",
"INPUT",
"-p",
"tcp",
"--dport",
"80",
"-j",
"DROP"
],
"pid": 2143,
"ppid": 2025,
"title": "iptables -A INPUT -p tcp --dport 80 -j DROP",
"name": "iptables"
},
"tags": [
"exec"
],
"agent": {
"type": "auditbeat",
"ephemeral_id": "xxxxxxxxx",
"hostname": "dmz_server",
"id": "xxxxxxxxx",
"version": "7.4.2"
},
"ecs": {
"version": "1.1.0"
},
"service": {
"type": "auditd"
}
},
"fields": {
"@timestamp": [
"2020-01-25T15:09:45.362Z"
]
},
"highlight": {
"process.name": [
"@kibana-highlighted-field@iptables@/kibana-highlighted-field@"
],
"host.name": [
"@kibana-highlighted-field@dmz_server@/kibana-highlighted-field@"
]
},
"sort": [
1579964985362
]
}
{
"_index": "auditbeat-7.4.2-20xx.xx.xx-000001",
"_type": "_doc",
"_id": "xxxxxxxxxxxxxxxxxxxxxxx",
"_version": 1,
"_score": null,
"_source": {
"@timestamp": "2020-01-25T15:09:45.438Z",
"process": {
"pid": 2143,
"ppid": 2025,
"title": "iptables -A INPUT -p tcp --dport 80 -j DROP",
"name": "iptables",
"executable": "/sbin/xtables-multi"
},
"tags": [
"audit-iptables"
],
"auditd": {
"data": {
"syscall": "setsockopt",
"a1": "0",
"arch": "x86_64",
"exit": "0",
"table": "filter",
"a0": "4",
"tty": "tty1",
"a3": "558343597f70",
"family": "2",
"a2": "40",
"entries": "4"
},
"session": "1",
"summary": {
"actor": {
"primary": "xxxxxxxxx",
"secondary": "root"
},
"object": {
"type": "firewall",
"primary": "filter"
},
"how": "/sbin/xtables-multi"
},
"message_type": "netfilter_cfg",
"sequence": 413,
"result": "success"
},
"ecs": {
"version": "1.1.0"
},
"service": {
"type": "auditd"
},
"event": {
"outcome": "success",
"module": "auditd",
"category": "configuration",
"action": "loaded-firewall-rule-to"
},
"user": {
"name": "root",
"group": {
"id": "0",
"name": "root"
},
"effective": {
"id": "0",
"name": "root",
"group": {
"name": "root",
"id": "0"
}
},
"id": "0",
"filesystem": {
"group": {
"name": "root",
"id": "0"
},
"name": "root",
"id": "0"
},
"saved": {
"id": "0",
"group": {
"name": "root",
"id": "0"
},
"name": "root"
},
"audit": {
"id": "1000",
"name": "xxxxxxxxx"
}
},
"agent": {
"hostname": "dmz_server",
"id": "xxxxxxxxx",
"version": "7.4.2",
"type": "auditbeat",
"ephemeral_id": "xxxxxxxxx"
},
"host": {
"hostname": "dmz_server",
"architecture": "x86_64",
"os": {
"kernel": "4.15.0-74-generic",
"codename": "bionic",
"platform": "ubuntu",
"version": "18.04.1 LTS (Bionic Beaver)",
"family": "debian",
"name": "Ubuntu"
},
"id": "xxxxxxxxx",
"containerized": false,
"name": "dmz_server"
}
},
"fields": {
"@timestamp": [
"2020-01-25T15:09:45.438Z"
]
},
"highlight": {
"process.name": [
"@kibana-highlighted-field@iptables@/kibana-highlighted-field@"
],
"host.name": [
"@kibana-highlighted-field@dmz_server@/kibana-highlighted-field@"
]
},
"sort": [
1579964985438
]
}
{
"_index": "auditbeat-7.4.2-20xx.xx.xx-000001",
"_type": "_doc",
"_id": "xxxxxxxxxxxxxxxxxxxxxxx",
"_version": 1,
"_score": null,
"_source": {
"@timestamp": "2020-01-25T15:05:43.626Z",
"event": {
"outcome": "success",
"module": "auditd",
"category": "audit-rule",
"action": "executed"
},
"tags": [
"exec"
],
"agent": {
"type": "auditbeat",
"ephemeral_id": "xxxxxxxxx",
"hostname": "dmz_server",
"id": "xxxxxxxxx",
"version": "7.4.2"
},
"user": {
"name": "root",
"filesystem": {
"name": "root",
"group": {
"id": "0",
"name": "root"
},
"id": "0"
},
"saved": {
"id": "0",
"group": {
"name": "root",
"id": "0"
},
"name": "root"
},
"group": {
"id": "0",
"name": "root"
},
"effective": {
"group": {
"id": "0",
"name": "root"
},
"id": "0",
"name": "root"
},
"id": "0"
},
"process": {
"ppid": 2037,
"title": "/usr/sbin/apache2 -k start",
"name": "apache2",
"executable": "/usr/sbin/apache2",
"working_directory": "/",
"args": [
"/usr/sbin/apache2",
"-k",
"start"
],
"pid": 2061
},
"file": {
"mode": "0755",
"uid": "0",
"gid": "0",
"owner": "root",
"group": "root",
"path": "/usr/sbin/apache2",
"device": "00:00",
"inode": "394088"
},
"auditd": {
"sequence": 345,
"result": "success",
"data": {
"syscall": "execve",
"arch": "x86_64",
"a2": "558c84c2d698",
"a1": "558c84c2d678",
"a0": "558c84c2d610",
"tty": "(none)",
"a3": "7fb2be979810",
"argc": "3",
"exit": "0"
},
"summary": {
"actor": {
"primary": "unset",
"secondary": "root"
},
"object": {
"primary": "/usr/sbin/apache2",
"type": "file"
},
"how": "/usr/sbin/apache2"
},
"paths": [
{
"mode": "0100755",
"ouid": "0",
"inode": "394088",
"cap_fi": "0000000000000000",
"cap_fp": "0000000000000000",
"cap_fver": "0",
"dev": "08:02",
"item": "0",
"name": "/usr/sbin/apache2",
"nametype": "NORMAL",
"cap_fe": "0",
"rdev": "00:00",
"ogid": "0"
},
{
"cap_fver": "0",
"inode": "136740",
"item": "1",
"ogid": "0",
"ouid": "0",
"name": "/lib64/ld-linux-x86-64.so.2",
"nametype": "NORMAL",
"rdev": "00:00",
"cap_fe": "0",
"cap_fi": "0000000000000000",
"cap_fp": "0000000000000000",
"dev": "08:02",
"mode": "0100755"
}
],
"message_type": "syscall"
},
"service": {
"type": "auditd"
},
"ecs": {
"version": "1.1.0"
},
"host": {
"os": {
"platform": "ubuntu",
"version": "18.04.1 LTS (Bionic Beaver)",
"family": "debian",
"name": "Ubuntu",
"kernel": "4.15.0-74-generic",
"codename": "bionic"
},
"id": "xxxxxxxxx",
"containerized": false,
"hostname": "dmz_server",
"architecture": "x86_64",
"name": "dmz_server"
}
},
"fields": {
"@timestamp": [
"2020-01-25T15:05:43.626Z"
]
},
"highlight": {
"process.name": [
"@kibana-highlighted-field@apache2@/kibana-highlighted-field@"
],
"auditd.data.syscall": [
"@kibana-highlighted-field@execve@/kibana-highlighted-field@"
],
"host.name": [
"@kibana-highlighted-field@dmz_server@/kibana-highlighted-field@"
]
},
"sort": [
1579964743626
]
}
{
"_index": "auditbeat-7.4.2-20xx.xx.xx-000001",
"_type": "_doc",
"_id": "xxxxxxxxxxxxxxxxxxxxxxx",
"_version": 1,
"_score": null,
"_source": {
"@timestamp": "2020-01-25T15:05:43.898Z",
"agent": {
"type": "auditbeat",
"ephemeral_id": "xxxxxxxxx",
"hostname": "dmz_server",
"id": "xxxxxxxxx",
"version": "7.4.2"
},
"service": {
"type": "auditd"
},
"user": {
"id": "0",
"group": {
"name": "root",
"id": "0"
},
"effective": {
"id": "0",
"group": {
"name": "root",
"id": "0"
},
"name": "root"
},
"name": "root",
"filesystem": {
"id": "0",
"group": {
"name": "root",
"id": "0"
},
"name": "root"
},
"saved": {
"id": "0",
"group": {
"id": "0",
"name": "root"
},
"name": "root"
}
},
"tags": [
"audit-iptables"
],
"auditd": {
"result": "success",
"data": {
"a2": "1c",
"a0": "4",
"syscall": "listen",
"a1": "1ff",
"exit": "0",
"tty": "(none)",
"arch": "x86_64",
"a3": "1f"
},
"summary": {
"actor": {
"secondary": "root",
"primary": "unset"
},
"object": {
"type": "socket"
},
"how": "/usr/sbin/apache2"
},
"message_type": "syscall",
"sequence": 380
},
"event": {
"category": "audit-rule",
"action": "listen-for-connections",
"outcome": "success",
"module": "auditd"
},
"process": {
"name": "apache2",
"executable": "/usr/sbin/apache2",
"pid": 2061,
"ppid": 2037,
"title": "/usr/sbin/apache2 -k start"
},
"ecs": {
"version": "1.1.0"
},
"host": {
"containerized": false,
"name": "dmz_server",
"hostname": "dmz_server",
"architecture": "x86_64",
"os": {
"platform": "ubuntu",
"version": "18.04.1 LTS (Bionic Beaver)",
"family": "debian",
"name": "Ubuntu",
"kernel": "4.15.0-74-generic",
"codename": "bionic"
},
"id": "xxxxxxxxx"
}
},
"fields": {
"@timestamp": [
"2020-01-25T15:05:43.898Z"
]
},
"highlight": {
"process.name": [
"@kibana-highlighted-field@apache2@/kibana-highlighted-field@"
],
"auditd.data.syscall": [
"@kibana-highlighted-field@listen@/kibana-highlighted-field@"
],
"host.name": [
"@kibana-highlighted-field@dmz_server@/kibana-highlighted-field@"
]
},
"sort": [
1579964743898
]
}
{
"_index": "auditbeat-7.4.2-20xx.xx.xx-000001",
"_type": "_doc",
"_id": "xxxxxxxxxxxxxxxxxxxxxxx",
"_version": 1,
"_score": null,
"_source": {
"@timestamp": "2020-01-25T15:08:50.143Z",
"event": {
"category": "audit-rule",
"action": "accepted-connection-from",
"outcome": "success",
"module": "auditd"
},
"process": {
"title": "/usr/sbin/apache2 -k start",
"name": "apache2",
"executable": "/usr/sbin/apache2",
"pid": 2067,
"ppid": 2064
},
"network": {
"direction": "incoming"
},
"host": {
"architecture": "x86_64",
"os": {
"codename": "bionic",
"platform": "ubuntu",
"version": "18.04.1 LTS (Bionic Beaver)",
"family": "debian",
"name": "Ubuntu",
"kernel": "4.15.0-74-generic"
},
"id": "xxxxxxxxx",
"containerized": false,
"hostname": "dmz_server",
"name": "dmz_server"
},
"ecs": {
"version": "1.1.0"
},
"auditd": {
"sequence": 400,
"result": "success",
"data": {
"a0": "4",
"a3": "80000",
"a2": "7f583f7e5cf0",
"arch": "x86_64",
"socket": {
"family": "ipv6",
"port": "50131",
"addr": "192.168.1.1"
},
"tty": "(none)",
"a1": "7f583f7e5d10",
"syscall": "accept4",
"exit": "12"
},
"summary": {
"actor": {
"primary": "unset",
"secondary": "www-data"
},
"object": {
"primary": "192.168.1.1",
"secondary": "50131",
"type": "socket"
},
"how": "/usr/sbin/apache2"
},
"message_type": "syscall"
},
"service": {
"type": "auditd"
},
"user": {
"name": "www-data",
"effective": {
"group": {
"id": "33",
"name": "www-data"
},
"name": "www-data",
"id": "33"
},
"saved": {
"group": {
"id": "33",
"name": "www-data"
},
"id": "33",
"name": "www-data"
},
"filesystem": {
"name": "www-data",
"id": "33",
"group": {
"id": "33",
"name": "www-data"
}
},
"id": "33",
"group": {
"id": "33",
"name": "www-data"
}
},
"source": {
"port": "50131",
"ip": "192.168.1.1"
},
"tags": [
"audit-iptables"
],
"agent": {
"hostname": "dmz_server",
"id": "xxxxxxxxx",
"version": "7.4.2",
"type": "auditbeat",
"ephemeral_id": "xxxxxxxxx"
}
},
"fields": {
"@timestamp": [
"2020-01-25T15:08:50.143Z"
]
},
"highlight": {
"process.name": [
"@kibana-highlighted-field@apache2@/kibana-highlighted-field@"
],
"auditd.data.syscall": [
"@kibana-highlighted-field@accept4@/kibana-highlighted-field@"
],
"host.name": [
"@kibana-highlighted-field@dmz_server@/kibana-highlighted-field@"
]
},
"sort": [
1579964930143
]
}
{
"_index": "auditbeat-7.4.2-20xx.xx.xx-000001",
"_type": "_doc",
"_id": "xxxxxxxxxxxxxxxxxxxxxxx",
"_version": 1,
"_score": null,
"_source": {
"@timestamp": "2020-01-25T15:14:00.413Z",
"event": {
"category": "audit-rule",
"action": "executed",
"outcome": "success",
"module": "auditd"
},
"user": {
"audit": {
"id": "1000",
"name": "xxxxxxxxx"
},
"name": "root",
"id": "0",
"group": {
"id": "0",
"name": "root"
},
"filesystem": {
"group": {
"id": "0",
"name": "root"
},
"id": "0",
"name": "root"
},
"effective": {
"id": "0",
"group": {
"id": "0",
"name": "root"
},
"name": "root"
},
"saved": {
"id": "0",
"name": "root",
"group": {
"id": "0",
"name": "root"
}
}
},
"process": {
"ppid": 2025,
"title": "python3 -m http.server 8000",
"name": "python3",
"executable": "/usr/bin/python3.6",
"working_directory": "/home/xxxxxxxxx",
"args": [
"python3",
"-m",
"http.server",
"8000"
],
"pid": 2167
},
"agent": {
"hostname": "dmz_server",
"id": "xxxxxxxxx",
"version": "7.4.2",
"type": "auditbeat",
"ephemeral_id": "xxxxxxxxx"
},
"ecs": {
"version": "1.1.0"
},
"host": {
"os": {
"platform": "ubuntu",
"version": "18.04.1 LTS (Bionic Beaver)",
"family": "debian",
"name": "Ubuntu",
"kernel": "4.15.0-74-generic",
"codename": "bionic"
},
"id": "xxxxxxxxx",
"containerized": false,
"name": "dmz_server",
"hostname": "dmz_server",
"architecture": "x86_64"
},
"tags": [
"exec"
],
"service": {
"type": "auditd"
},
"auditd": {
"message_type": "syscall",
"sequence": 415,
"result": "success",
"data": {
"arch": "x86_64",
"a2": "55a151ece9a0",
"tty": "tty1",
"a1": "55a151ee9c70",
"a3": "8",
"a0": "55a151eef970",
"exit": "0",
"argc": "4",
"syscall": "execve"
},
"session": "1",
"summary": {
"actor": {
"primary": "xxxxxxxxx",
"secondary": "root"
},
"object": {
"primary": "/usr/bin/python3",
"type": "file"
},
"how": "python3"
},
"paths": [
{
"nametype": "NORMAL",
"rdev": "00:00",
"cap_fp": "0000000000000000",
"dev": "08:02",
"inode": "131352",
"item": "0",
"name": "/usr/bin/python3",
"ogid": "0",
"ouid": "0",
"cap_fe": "0",
"cap_fi": "0000000000000000",
"cap_fver": "0",
"mode": "0100755"
},
{
"cap_fe": "0",
"cap_fi": "0000000000000000",
"cap_fver": "0",
"mode": "0100755",
"name": "/lib64/ld-linux-x86-64.so.2",
"nametype": "NORMAL",
"rdev": "00:00",
"cap_fp": "0000000000000000",
"dev": "08:02",
"inode": "136740",
"item": "1",
"ogid": "0",
"ouid": "0"
}
]
},
"file": {
"group": "root",
"path": "/usr/bin/python3",
"device": "00:00",
"inode": "131352",
"mode": "0755",
"uid": "0",
"gid": "0",
"owner": "root"
}
},
"fields": {
"@timestamp": [
"2020-01-25T15:14:00.413Z"
]
},
"highlight": {
"process.name": [
"@kibana-highlighted-field@python3@/kibana-highlighted-field@"
],
"auditd.data.syscall": [
"@kibana-highlighted-field@execve@/kibana-highlighted-field@"
],
"host.name": [
"@kibana-highlighted-field@dmz_server@/kibana-highlighted-field@"
]
},
"sort": [
1579965240413
]
}
{
"_index": "auditbeat-7.4.2-20xx.xx.xx-000001",
"_type": "_doc",
"_id": "xxxxxxxxxxxxxxxxxxxxxxx",
"_version": 1,
"_score": null,
"_source": {
"@timestamp": "2020-01-25T15:14:00.557Z",
"auditd": {
"sequence": 427,
"result": "success",
"data": {
"a0": "3",
"a1": "5",
"a3": "9",
"a2": "ffffffff",
"arch": "x86_64",
"syscall": "listen",
"exit": "0",
"tty": "tty1"
},
"session": "1",
"summary": {
"actor": {
"primary": "xxxxxxxxx",
"secondary": "root"
},
"object": {
"type": "socket"
},
"how": "python3"
},
"message_type": "syscall"
},
"host": {
"containerized": false,
"hostname": "dmz_server",
"name": "dmz_server",
"architecture": "x86_64",
"os": {
"family": "debian",
"name": "Ubuntu",
"kernel": "4.15.0-74-generic",
"codename": "bionic",
"platform": "ubuntu",
"version": "18.04.1 LTS (Bionic Beaver)"
},
"id": "xxxxxxxxx"
},
"agent": {
"hostname": "dmz_server",
"id": "xxxxxxxxx",
"version": "7.4.2",
"type": "auditbeat",
"ephemeral_id": "xxxxxxxxx"
},
"service": {
"type": "auditd"
},
"event": {
"category": "audit-rule",
"action": "listen-for-connections",
"outcome": "success",
"module": "auditd"
},
"tags": [
"audit-iptables"
],
"user": {
"filesystem": {
"group": {
"id": "0",
"name": "root"
},
"id": "0",
"name": "root"
},
"id": "0",
"saved": {
"group": {
"id": "0",
"name": "root"
},
"id": "0",
"name": "root"
},
"name": "root",
"effective": {
"group": {
"id": "0",
"name": "root"
},
"id": "0",
"name": "root"
},
"audit": {
"id": "1000",
"name": "xxxxxxxxx"
},
"group": {
"id": "0",
"name": "root"
}
},
"process": {
"pid": 2167,
"ppid": 2025,
"title": "python3 -m http.server 8000",
"name": "python3",
"executable": "/usr/bin/python3.6"
},
"ecs": {
"version": "1.1.0"
}
},
"fields": {
"@timestamp": [
"2020-01-25T15:14:00.557Z"
]
},
"highlight": {
"process.name": [
"@kibana-highlighted-field@python3@/kibana-highlighted-field@"
],
"auditd.data.syscall": [
"@kibana-highlighted-field@listen@/kibana-highlighted-field@"
],
"host.name": [
"@kibana-highlighted-field@dmz_server@/kibana-highlighted-field@"
]
},
"sort": [
1579965240557
]
}
{
"_index": "auditbeat-7.4.2-20xx.xx.xx-000001",
"_type": "_doc",
"_id": "xxxxxxxxxxxxxxxxxxxxxxx",
"_version": 1,
"_score": null,
"_source": {
"@timestamp": "2020-01-25T15:16:48.105Z",
"service": {
"type": "auditd"
},
"user": {
"name": "root",
"id": "0",
"filesystem": {
"group": {
"id": "0",
"name": "root"
},
"id": "0",
"name": "root"
},
"saved": {
"name": "root",
"group": {
"id": "0",
"name": "root"
},
"id": "0"
},
"effective": {
"id": "0",
"group": {
"id": "0",
"name": "root"
},
"name": "root"
},
"group": {
"id": "0",
"name": "root"
},
"audit": {
"id": "1000",
"name": "xxxxxxxxx"
}
},
"host": {
"name": "dmz_server",
"os": {
"version": "18.04.1 LTS (Bionic Beaver)",
"family": "debian",
"name": "Ubuntu",
"kernel": "4.15.0-74-generic",
"codename": "bionic",
"platform": "ubuntu"
},
"id": "xxxxxxxxx",
"containerized": false,
"hostname": "dmz_server",
"architecture": "x86_64"
},
"auditd": {
"data": {
"exit": "4",
"a3": "80000",
"tty": "tty1",
"a1": "7fffa64c95e0",
"socket": {
"port": "50259",
"family": "ipv4",
"addr": "192.168.1.1"
},
"syscall": "accept4",
"a2": "7fffa64c95bc",
"a0": "3",
"arch": "x86_64"
},
"session": "1",
"summary": {
"actor": {
"primary": "xxxxxxxxx",
"secondary": "root"
},
"object": {
"type": "socket",
"primary": "192.168.1.1",
"secondary": "50259"
},
"how": "python3"
},
"message_type": "syscall",
"sequence": 489,
"result": "success"
},
"tags": [
"audit-iptables"
],
"event": {
"category": "audit-rule",
"action": "accepted-connection-from",
"outcome": "success",
"module": "auditd"
},
"process": {
"pid": 2191,
"ppid": 2025,
"title": "python3 -m http.server 8000",
"name": "python3",
"executable": "/usr/bin/python3.6"
},
"source": {
"ip": "192.168.1.1",
"port": "50259"
},
"ecs": {
"version": "1.1.0"
},
"agent": {
"hostname": "dmz_server",
"id": "xxxxxxxxx",
"version": "7.4.2",
"type": "auditbeat",
"ephemeral_id": "xxxxxxxxx"
},
"network": {
"direction": "incoming"
}
},
"fields": {
"@timestamp": [
"2020-01-25T15:16:48.105Z"
]
},
"highlight": {
"process.name": [
"@kibana-highlighted-field@python3@/kibana-highlighted-field@"
],
"auditd.data.syscall": [
"@kibana-highlighted-field@accept4@/kibana-highlighted-field@"
],
"host.name": [
"@kibana-highlighted-field@dmz_server@/kibana-highlighted-field@"
]
},
"sort": [
1579965408105
]
}