Terraformig で出たファイルでサーバを作成してみる
昨日書いたやつの続きです。
実際吐かれた Terraforming の tfファイルをそのまま使ってサーバは作れるのか?ってやつです。
出力された tf ファイル
ec2.tf
resource "aws_instance" "i-07c4faacac527c52e" {
ami = "ami-0fd02119f1653c976"
availability_zone = "ap-northeast-1a"
ebs_optimized = false
instance_type = "t2.micro"
monitoring = false
key_name = ""
subnet_id = "subnet-8fcc99c6"
vpc_security_group_ids = ["sg-8f5f16f6"]
associate_public_ip_address = true
private_ip = "172.31.38.66"
source_dest_check = true
root_block_device {
volume_type = "gp2"
volume_size = 8
delete_on_termination = true
}
tags {
}
}
なんか、このまま適用して大丈夫なのかな?という部分もありますが、まぁ、物は試しです。
とりあえず、plan
> ./terraform plan
Refreshing Terraform state in-memory prior to plan...
The refreshed state will be used to calculate this plan, but will not be
persisted to local or remote state storage.
------------------------------------------------------------------------
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
+ aws_instance.i-07c4faacac527c52e
id: <computed>
ami: "ami-0fd02119f1653c976"
arn: <computed>
associate_public_ip_address: "true"
availability_zone: "ap-northeast-1a"
cpu_core_count: <computed>
cpu_threads_per_core: <computed>
ebs_block_device.#: <computed>
ebs_optimized: "false"
ephemeral_block_device.#: <computed>
get_password_data: "false"
instance_state: <computed>
instance_type: "t2.micro"
ipv6_address_count: <computed>
ipv6_addresses.#: <computed>
key_name: <computed>
monitoring: "false"
network_interface.#: <computed>
network_interface_id: <computed>
password_data: <computed>
placement_group: <computed>
primary_network_interface_id: <computed>
private_dns: <computed>
private_ip: "172.31.38.66"
public_dns: <computed>
public_ip: <computed>
root_block_device.#: "1"
root_block_device.0.delete_on_termination: "true"
root_block_device.0.volume_id: <computed>
root_block_device.0.volume_size: "8"
root_block_device.0.volume_type: "gp2"
security_groups.#: <computed>
source_dest_check: "true"
subnet_id: "subnet-8fcc99c6"
tenancy: <computed>
volume_tags.%: <computed>
vpc_security_group_ids.#: "1"
vpc_security_group_ids.606438745: "sg-8f5f16f6"
Plan: 1 to add, 0 to change, 0 to destroy.
------------------------------------------------------------------------
Note: You didn't specify an "-out" parameter to save this plan, so Terraform
can't guarantee that exactly these actions will be performed if
"terraform apply" is subsequently run.
まぁ、問題なさげ。。。
では、apply
> ./terraform apply
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
+ aws_instance.i-07c4faacac527c52e
id: <computed>
ami: "ami-0fd02119f1653c976"
arn: <computed>
associate_public_ip_address: "true"
availability_zone: "ap-northeast-1a"
cpu_core_count: <computed>
cpu_threads_per_core: <computed>
ebs_block_device.#: <computed>
ebs_optimized: "false"
ephemeral_block_device.#: <computed>
get_password_data: "false"
instance_state: <computed>
instance_type: "t2.micro"
ipv6_address_count: <computed>
ipv6_addresses.#: <computed>
key_name: <computed>
monitoring: "false"
network_interface.#: <computed>
network_interface_id: <computed>
password_data: <computed>
placement_group: <computed>
primary_network_interface_id: <computed>
private_dns: <computed>
private_ip: "172.31.38.66"
public_dns: <computed>
public_ip: <computed>
root_block_device.#: "1"
root_block_device.0.delete_on_termination: "true"
root_block_device.0.volume_id: <computed>
root_block_device.0.volume_size: "8"
root_block_device.0.volume_type: "gp2"
security_groups.#: <computed>
source_dest_check: "true"
subnet_id: "subnet-8fcc99c6"
tenancy: <computed>
volume_tags.%: <computed>
vpc_security_group_ids.#: "1"
vpc_security_group_ids.606438745: "sg-8f5f16f6"
Plan: 1 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value:
yes ・・・と
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
aws_instance.i-07c4faacac527c52e: Creating...
ami: "" => "ami-0fd02119f1653c976"
arn: "" => "<computed>"
associate_public_ip_address: "" => "true"
availability_zone: "" => "ap-northeast-1a"
cpu_core_count: "" => "<computed>"
cpu_threads_per_core: "" => "<computed>"
ebs_block_device.#: "" => "<computed>"
ebs_optimized: "" => "false"
ephemeral_block_device.#: "" => "<computed>"
get_password_data: "" => "false"
instance_state: "" => "<computed>"
instance_type: "" => "t2.micro"
ipv6_address_count: "" => "<computed>"
ipv6_addresses.#: "" => "<computed>"
key_name: "" => "<computed>"
monitoring: "" => "false"
network_interface.#: "" => "<computed>"
network_interface_id: "" => "<computed>"
password_data: "" => "<computed>"
placement_group: "" => "<computed>"
primary_network_interface_id: "" => "<computed>"
private_dns: "" => "<computed>"
private_ip: "" => "172.31.38.66"
public_dns: "" => "<computed>"
public_ip: "" => "<computed>"
root_block_device.#: "" => "1"
root_block_device.0.delete_on_termination: "" => "true"
root_block_device.0.volume_id: "" => "<computed>"
root_block_device.0.volume_size: "" => "8"
root_block_device.0.volume_type: "" => "gp2"
security_groups.#: "" => "<computed>"
source_dest_check: "" => "true"
subnet_id: "" => "subnet-8fcc99c6"
tenancy: "" => "<computed>"
volume_tags.%: "" => "<computed>"
vpc_security_group_ids.#: "" => "1"
vpc_security_group_ids.606438745: "" => "sg-8f5f16f6"
aws_instance.i-07c4faacac527c52e: Still creating... (10s elapsed)
aws_instance.i-07c4faacac527c52e: Still creating... (20s elapsed)
aws_instance.i-07c4faacac527c52e: Still creating... (30s elapsed)
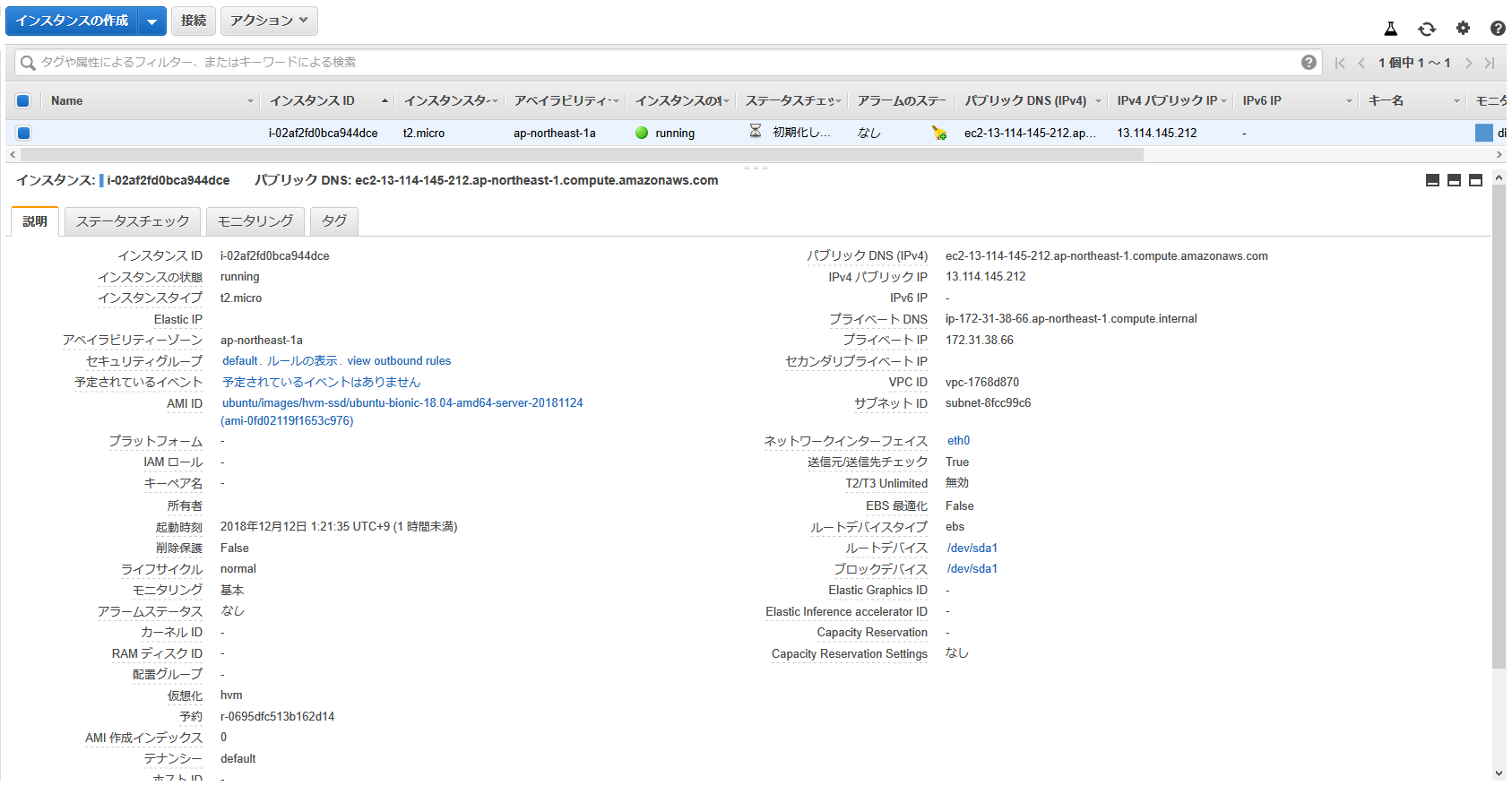
aws_instance.i-07c4faacac527c52e: Creation complete after 32s (ID: i-02af2fd0bca944dce)
Apply complete! Resources: 1 added, 0 changed, 0 destroyed.
ありゃ、普通にできましたね。
怪しいなと思ってた、プライベートIPの指定もできてますね。
まぁ、Terraforming で作った tfファイルには、リソース名にインスタンスIDがついてましたけど、これはさすがにつかないですね。
他は問題ない感じですが、プライベートIPは被ることも考えると指定しない方がよい気もします。
まとめ
EC2に関しては、意外に Terraforming で作成されるままの tfファイルでもいけるってことがわかりました。
気になるとこをちょっと修正するだけでいけそうですね。
ちょっと他のリソースに関しても試していきたいと思います。