世界一有名なCTF(諸説あり),picoCTFの年一イベントです!
glogalランキング2719位!

-宣伝-
岐阜大学では岐大生のCTFerを絶賛募集中です!!!
https://twitter.com/ProgCirGifuUni
Web
Bookmarklet
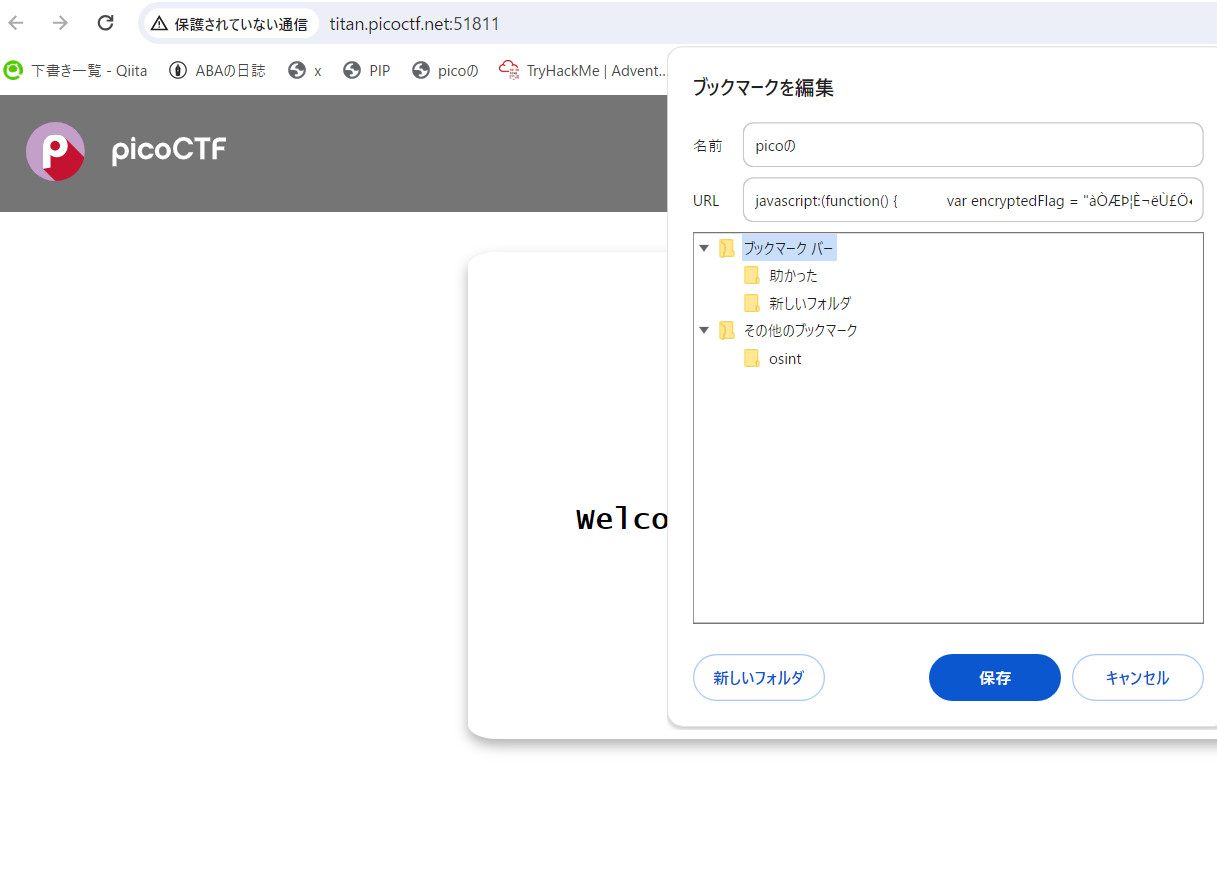
ブックマークレット面白いよね!作問者も布教したかったんじゃないかな...?
上の写真のように、ブックマークの通常URLが入力されるところにjavascriptを入れることで、ワンタップでjavascriptを実行できる便利ツール技術の一つ。
以下のように対象のページでタップするとflagが得られる!

<余談>私のよく利用しているブックマークレット
どこかのQittaか技術記事の拾い物で引用元の作者や記事を表示できないので申し訳なさすぎます!!!ごめんなさい!!
ツイッターのインプレゾンビのリプライを非表示にするブックマークレット
javascript:setInterval(()%3D>%7Bif(document.querySelectorAll(%27%5Bdata-testid%3D"like"%5D%27)%5B0%5D.innerHTML.split("万").length>1) document.querySelectorAll(%27div%5Bdata-testid%3D"cellInnerDiv"%5D%27).forEach(e%3D>%7Bif(e.querySelectorAll(%27svg%5Baria-label%3D"認証済みアカウント"%5D%27).length>0) if(e.innerHTML.split("@"+document.location.pathname.split("/")[1]).length<=1) e.innerHTML="";%7D)%7D,200);
youtubeやアマプラ、ネトフリのpicture in pictureをワンタップでできるブックマークレット
画面が何枚あっても、何かの上に重ね表示できるのは嬉しい
https://qiita.com/iHok/items/2a51a71c26c8abf820e0 記憶ないけどこの記事だったかも...?
javascript:document.querySelector("video[src]").requestPictureInPicture();
作者を忘れたままというのも気持ち悪いのでもし分かる方がいればコメント欄にお願いします!
WebDecode
view-source:http://titan.picoctf.net:54494/about.html
ここを読むと

明らかに怪しい文字列があるのでbase64で変換するとflagが得られた
Unminify
問題文から下の方の要素にflagありそう。
ソースコードを表示するとflagが得られた

Cryptography
interencdec
バイナリをstirlingで読み込み、CyberChefでbase64を2回、最後にrot13の匂いがしたので最前の文字がpになるまで変更するとflagが得られた
Forensics
Scan Surprise

これをhttps://qrcode.onl.jp/ で読み取ると

でflagゲット
Verify
与えられたshとfilesを用いてからfiles以下のものを全て試すコードを書いた。
#!/bin/bash
BASE_DIR="/home/kali/Desktop/picoCTF2024/challenge/home/ctf-player/drop-in/files"
if [ ! -d "$BASE_DIR" ]; then
echo "Error: '$BASE_DIR' does not exist."
exit 1
fi
for file in "$BASE_DIR"/*; do
if [ -f "$file" ]; then
if ! openssl enc -d -aes-256-cbc -pbkdf2 -iter 100000 -salt -in "$file" -k picoCTF; then
echo "Error: Failed to decrypt '$file'. This flag is fake! Keep looking!"
else
echo "Decrypted successfully: $file"
fi
fi
done
このコードをdec2.shと命名して
./dec2.sh > aa.txt
と
grep "picoCTF{" aa.txt
でフラグが得られた
CanYouSee
https://www.aperisolve.com/ で画像を調べると、
stringsに
JFIF
7http://ns.adobe.com/xap/1.0/
<?xpacket begin='
' id='W5M0MpCehiHzreSzNTczkc9d'?>
<x:xmpmeta xmlns:x='adobe:ns:meta/' x:xmptk='Image::ExifTool 11.88'>
<rdf:RDF xmlns:rdf='http://www.w3.org/1999/02/22-rdf-syntax-ns#'>
<rdf:Description rdf:about=''
xmlns:cc='http://creativecommons.org/ns#'>
<cc:attributionURL rdf:resource='cGljb0NURntNRTc0RDQ3QV9ISUREM05fZGVjYTA2ZmJ9Cg=='/>
</rdf:Description>
</rdf:RDF>
</x:xmpmeta>
とあり、怪しげなbase64を変換するとフラグが得られた。
Secret of the Polyglot
strings flag2of2-final.pdf > aaa33.txt
このように先頭にIHDRとIENDとpngを示すようなものが埋め込まれていたので、stirlingでpng部分のみ抽出しました。
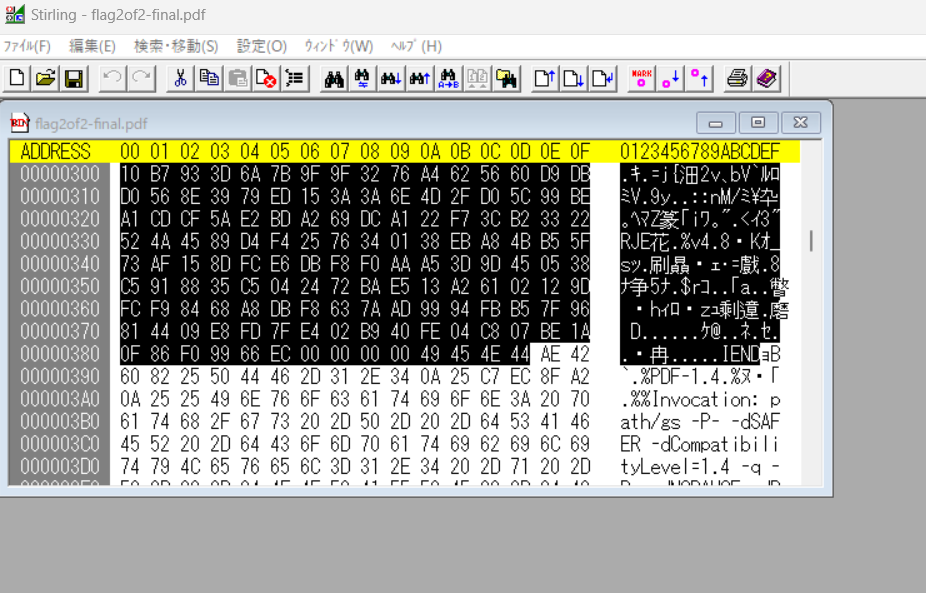
すると、

が得られるのでもともとのpdfファイルに表示されていた後半部分と繋げるとフラグが得られます。
Mob psycho
General Skills
Super SSH
┌──(kali㉿kali)-[~/Desktop]
└─$ ssh ctf-player@titan.picoctf.net -p 55352
The authenticity of host '[titan.picoctf.net]:55352 ([3.139.174.234]:55352)' can't be established.
ED25519 key fingerprint is SHA256:4S9EbTSSRZm32I+cdM5TyzthpQryv5kudRP9PIKT7XQ.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? y
Please type 'yes', 'no' or the fingerprint: yes
Warning: Permanently added '[titan.picoctf.net]:55352' (ED25519) to the list of known hosts.
ctf-player@titan.picoctf.net's password:
Welcome ctf-player, here's your flag: picoCTF{s3cur3_c0nn3ct10n_8969f7d3}
Connection to titan.picoctf.net closed.
よりフラグが得られた。
Commitment Issues
PS C:\Users\sadan\Downloads\challenge\drop-in\.git> git log
commit 3899edb7f3110d613c72ad40083fd8feeef703d0 (HEAD -> master)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:58 2024 +0000
remove sensitive info
commit 6603cb4ff0c4ea293798c03a32e0d78d5ab12ca2
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:58 2024 +0000
create flag
PS C:\Users\sadan\Downloads\challenge\drop-in\.git> git show 6603cb4ff0c4ea293798c03a32e0d78d5ab12ca2
commit 6603cb4ff0c4ea293798c03a32e0d78d5ab12ca2
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:58 2024 +0000
create flag
diff --git a/message.txt b/message.txt
new file mode 100644
index 0000000..ed59373
--- /dev/null
+++ b/message.txt
@@ -0,0 +1 @@
+picoCTF{s@n1t1z3_9539be6b}
PS C:\Users\sadan\Downloads\challenge\drop-in\.git>
でフラグが得られた
Time Machine
PS C:\Users\sadan\Downloads\challenge (1)\drop-in\.git> git log
commit 3339c144a0c78dc2fbd3403d2fb37d3830be5d94 (HEAD -> master)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:10:22 2024 +0000
picoCTF{t1m3m@ch1n3_d3161c0f}
でフラグが得られた
Blame Game
PS C:\Users\sadan\Downloads\challenge (2)\drop-in> git log -p .\message.py
commit 9ae3e1bc67ad0143c611c5f65399b79850d20983
Author: picoCTF{@sk_th3_1nt3rn_b64c4705} <ops@picoctf.com>
Date: Sat Mar 9 21:09:01 2024 +0000
optimize file size of prod code
diff --git a/message.py b/message.py
index 7df869a..326544a 100644
--- a/message.py
+++ b/message.py
@@ -1 +1 @@
-print("Hello, World!")
+print("Hello, World!"
commit f3cec26cf7f80f91b5c3d1972f14dd4e9f97ec83
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:01 2024 +0000
create top secret project
diff --git a/message.py b/message.py
new file mode 100644
index 0000000..7df869a
--- /dev/null
+++ b/message.py
@@ -0,0 +1 @@
+print("Hello, World!")
(END)
よりAuthor名にflagがあった
Collaborative Development
branchが複数あってそれぞれのlogを見る
PS C:\Users\sadan\Downloads\challenge (3)\drop-in> git branch -a
* feature/part-1
feature/part-2
feature/part-3
main
PS C:\Users\sadan\Downloads\challenge (3)\drop-in> git log
commit ad37f59bfdcb1e8052bf7e12e1d89a2adb315cf9 (HEAD -> feature/part-1)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:38 2024 +0000
add part 1
commit eb4de2a9826332633c62e44a1a130d9b1a88171a (main)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:38 2024 +0000
init flag printer
PS C:\Users\sadan\Downloads\challenge (3)\drop-in> git show ad37f59bfdcb1e8052bf7e12e1d89a2adb315cf9
commit ad37f59bfdcb1e8052bf7e12e1d89a2adb315cf9 (HEAD -> feature/part-1)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:38 2024 +0000
add part 1
diff --git a/flag.py b/flag.py
index 77d6cec..6e17fb3 100644
--- a/flag.py
+++ b/flag.py
@@ -1 +1,2 @@
print("Printing the flag...")
+print("picoCTF{t3@mw0rk_", end='')
\ No newline at end of file
PS C:\Users\sadan\Downloads\challenge (3)\drop-in> git switch feature/part-2
Switched to branch 'feature/part-2'
PS C:\Users\sadan\Downloads\challenge (3)\drop-in> git log
commit 9792a89fa347abc711f84b7208db18d164d45aca (HEAD -> feature/part-2)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:38 2024 +0000
add part 2
commit eb4de2a9826332633c62e44a1a130d9b1a88171a (main)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:38 2024 +0000
init flag printer
PS C:\Users\sadan\Downloads\challenge (3)\drop-in> git show 9792a89fa347abc711f84b7208db18d164d45aca
commit 9792a89fa347abc711f84b7208db18d164d45aca (HEAD -> feature/part-2)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:38 2024 +0000
add part 2
diff --git a/flag.py b/flag.py
index 77d6cec..7ab4e25 100644
--- a/flag.py
+++ b/flag.py
@@ -1 +1,3 @@
print("Printing the flag...")
+
+print("m@k3s_th3_dr3@m_", end='')
\ No newline at end of file
PS C:\Users\sadan\Downloads\challenge (3)\drop-in> git switch feature/part-3
Switched to branch 'feature/part-3'
PS C:\Users\sadan\Downloads\challenge (3)\drop-in> git log
commit 1308521d0d0b66df1a73e91d5d9e2d74610002e3 (HEAD -> feature/part-3)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:38 2024 +0000
add part 3
commit eb4de2a9826332633c62e44a1a130d9b1a88171a (main)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:38 2024 +0000
init flag printer
PS C:\Users\sadan\Downloads\challenge (3)\drop-in> git show 1308521d0d0b66df1a73e91d5d9e2d74610002e3
commit 1308521d0d0b66df1a73e91d5d9e2d74610002e3 (HEAD -> feature/part-3)
Author: picoCTF <ops@picoctf.com>
Date: Sat Mar 9 21:09:38 2024 +0000
add part 3
diff --git a/flag.py b/flag.py
index 77d6cec..78ac69c 100644
--- a/flag.py
+++ b/flag.py
@@ -1 +1,3 @@
print("Printing the flag...")
+
+print("w0rk_e4b79efb}")
PS C:\Users\sadan\Downloads\challenge (3)\drop-in>
繋げてpicoCTF{t3@mw0rk_m@k3s_th3_dr3@m_w0rk_e4b79efb}がflag
binhexa
──(kali㉿kali)-[~]
└─$ nc titan.picoctf.net 49152
Welcome to the Binary Challenge!"
Your task is to perform the unique operations in the given order and find the final result in hexadecimal that yields the flag.
Binary Number 1: 01110101
Binary Number 2: 01011010
Question 1/6:
Operation 1: '+'
Perform the operation on Binary Number 1&2.
Enter the binary result: 110011111
Incorrect. Try again
Enter the binary result: 11001111
Correct!
Question 2/6:
Operation 2: '&'
Perform the operation on Binary Number 1&2.
Enter the binary result: 01010000
Correct!
Question 3/6:
Operation 3: '>>'
Perform a right shift of Binary Number 2 by 1 bits .
Enter the binary result: 00101101
Correct!
Question 4/6:
Operation 4: '*'
Perform the operation on Binary Number 1&2.
Enter the binary result: 10100100100010
Correct!
Question 5/6:
Operation 5: '<<'
Perform a left shift of Binary Number 1 by 1 bits.
Enter the binary result: 11101010
Correct!
Question 6/6:
Operation 6: '|'
Perform the operation on Binary Number 1&2.
Enter the binary result: 01111111
Correct!
Enter the results of the last operation in hexadecimal: 7f
Correct answer!
The flag is: picoCTF{b1tw^3se_0p3eR@tI0n_su33essFuL_675602ae}
┌──(kali㉿kali)-[~]
でflagが得られた
Binary Search
二部探索を行う
──(kali㉿kali)-[~]
└─$ ssh -p 57992 ctf-player@atlas.picoctf.net
ctf-player@atlas.picoctf.net's password:
Welcome to the Binary Search Game!
I'm thinking of a number between 1 and 1000.
Enter your guess: 500
Lower! Try again.
Enter your guess: 250
Higher! Try again.
Enter your guess: 375
Lower! Try again.
Enter your guess: 312
Higher! Try again.
Enter your guess: 343
Congratulations! You guessed the correct number: 343
Here's your flag: picoCTF{g00d_gu355_ee8225d0}
Connection to atlas.picoctf.net closed.
flagを得られた
endianness
┌──(kali㉿kali)-[~]
└─$ nc titan.picoctf.net 50770
Welcome to the Endian CTF!
You need to find both the little endian and big endian representations of a word.
If you get both correct, you will receive the flag.
Word: zuubz
Enter the Little Endian representation: 7a6275757a
Correct Little Endian representation!
Enter the Big Endian representation: 7a7575627a
Correct Big Endian representation!
Congratulations! You found both endian representations correctly!
Your Flag is: picoCTF{3ndi4n_sw4p_su33ess_91bc76a4}
でflagが得られた
感想
Bookmarklet然り、問題を解くことを通してPCの世界にはこんな裏の動作があるんだよ!って興味を持たせてくれるめっちゃ良問と思いました。
なんだこれは!?って調べながら知れていくのいいよね!!!(時間があれば)
picoCTFお前ともっと闘いたかったよ……
就活さえなけりゃあなぁ!来年こそは...全完!
岐阜大学では岐大生のCTFerを絶賛募集中です!!!
https://twitter.com/ProgCirGifuUni